Simple Defenses vs Advanced Malware
Defending your systems from advanced malware does not have to be difficult and costly. Learn how to improve your domain security with simple changes to tools you already own.

If like me you follow security researchers and bug bounty hunters over on Twitter, then every day your feed will bubble with newly discovered vulnerabilities and malware. At dinner this week I was showing an infosec friend my feed and pointed out a researcher who had just posted a brilliant write up on Emotet. My infosec friend took a deep breath and sighed, he is worried about malware like Emotet because he feels his tools and staff were inadequately prepared to catch and defend against it. He said that he would need an expensive EDR suite and hours of staff training. But this got me wondering, does he really need all of that? How true is his thinking?
Is Defending Against Advanced Malware Difficult & Costly?
The answer is no. You can vastly improve your Windows domain security by making some simple changes to the tools that you definitely already own.
Firstly lets take a look at a kill chain for an emotet infection and understand how we can detect it (these configurations will protect your network from various common exploit techniques not just emotet).
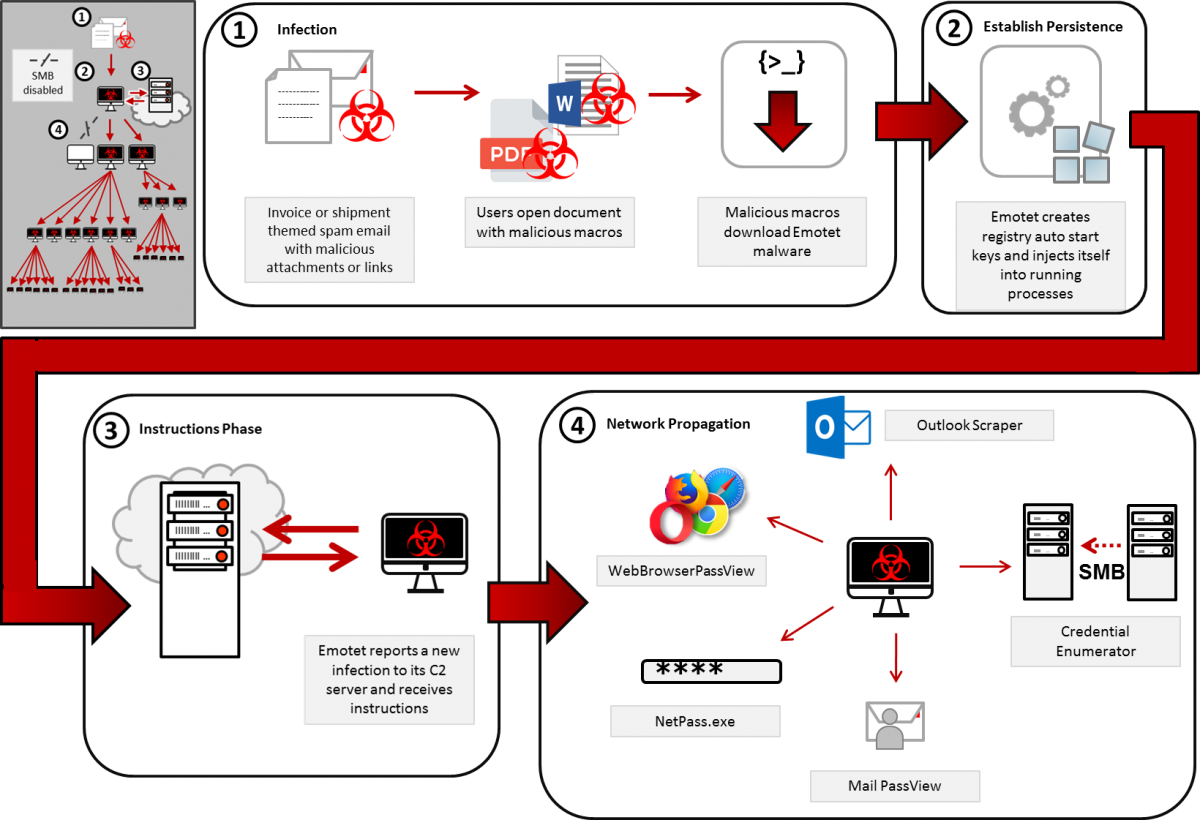
We want to stop the attack as early as possible, ideally preventing infection at all.
Section 1 of the diagram shows this malware (like almost all malware of this type) is delivered primarily via phishing with a malicious attachment. Of course the first thing I am obligated to advise is user training. If this attachment makes it through your email gateway your staff should be trained to identify the red flags and report the message. However nobody's perfect, a perfect system does not exist and malspam can be very convincing.
Phase 1
Block Encrypted Email Attachments
Attackers use encrypted attachments to sneak malicious files into your network. Therefore you should consider using your email gateway to block or hold them.
Obviously this is not feasible if your staff regularly receive legitimate encrypted attachments. Luckily in our environment they are rare so we hold the attachment at the gateway and only release to the end user once we are sure it is legitimate.
Block Internet Macros GPO
This group policy neuters most phishing attachments by disabling externally crafted macros. It does not effect internal users ability to craft and use macros.
With the macro blocked we have stopped this attack vector at stage 1.
User configuration > Administrative templates > Microsoft Word 20xx > Word options > Security > Trust Center
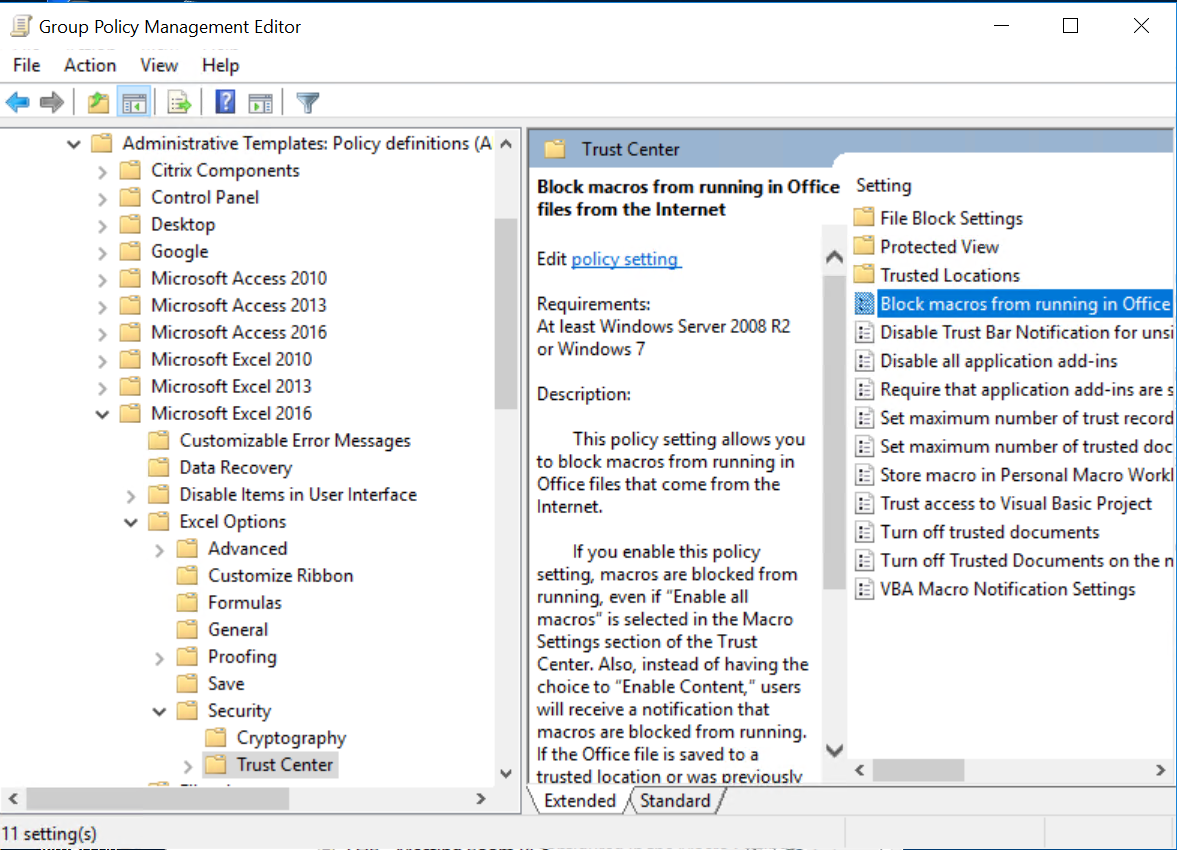
You will need to enable this GPO for Excel, PowerPoint and Word. Be sure to enable it for the correct version of office that you are running (2010,2013 etc). We have a small group of users that require regular interaction with external macros so we created an AD group to exclude them from the group policy. Excluded users should be extensively trained on the dangers of enabling macros.
PowerShell Logging
By configuring PowerShell logging we are protecting ourselves from a myriad of threats. Emotet and many others are using PowerShell to drop and execute code on victim machines. We will also be protected from PSEmpire and Powersploit.
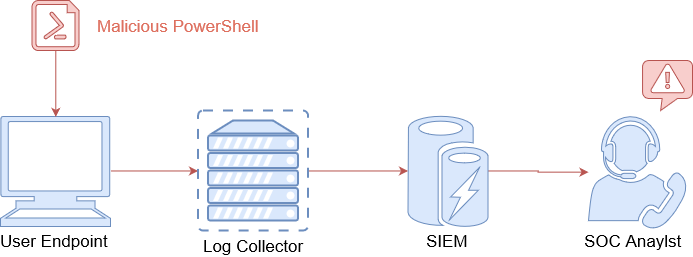
To enable this protection we need to use some handy Windows GPOs.
Enable"Turn on Module Logging" and "Script Block Logging" to create a nice verbose PowerShell log for SIEM ingestion.
Computer Configuration > Policies > Administrative Templates > Windows Components > Powershell > Turn on Module LoggingComputer
Configuration > Policies > Administrative Templates > Windows Components > Powershell > Turn on PowerShell Script Block Logging
I do not have enough space for a deep dive on PowerShell logging in this post.
👉 Click here for a detailed guide. 👈
Phase 2/3
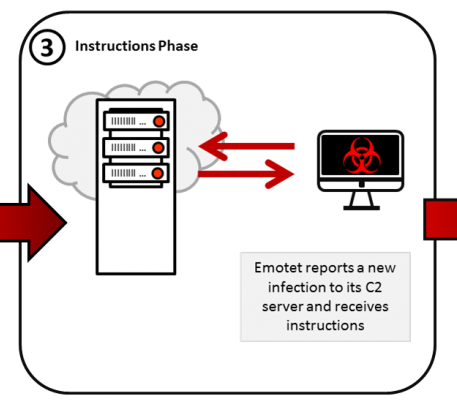
Threat Intelligence Feeds
There is an army of hobbyist and professional malware researchers out there who reverse engineer the latest malware and spam campaigns to gather intelligence about them. Researchers publish this intelligence to Threat Intel Feeds usually in a standardized format ready for SIEM ingestion. Subscribing to one or more of these feeds to help you spot malware command and control traffic when no other protection technology has. Abuse.ch provide great threat intel completely free. You can pull down their data with simple PowerShell scripts.
Applying the above protections should cost nothing more than wage-hours and will vastly improve your endpoint defenses. Good luck!