The Apperta Data Breach Fiasco
The Apperta Foundation seems to be embroiled in a very public data breach fiasco of their own making.

The Apperta Foundation, a non-profit organization originally created by NHS England and funded by taxpayer money, seems to be embroiled in a very public data breach fiasco of their own making. In a classic case of 'shoot the messenger' they are threatening the individual who first notified them of the breach with legal action.
When Peter Coates, NHS England's Open Source Program Manager and now the Managing Director of Apperta, told Digital Health News that Apperta would "be fully transparent with information published online", nobody thought that he meant Apperta would put their confidential data into publicly available repositories on Github.
The Apperta Foundation allegedly kept public repos full confidential data on Github, freely available for anyone to download. We are not sure exactly what was in those public repositories, but the researcher who first discovered the data online disclosed that "the foundation had two public repos on GitHub full of secrets" and alarmingly this included databases, source code, usernames, passwords and API keys.
What Is The Apperta Foundation?
Apperta promote open systems and standards for digital health and social care, providing governance, support and funding to programs which further their mission of transforming health and social care through open systems, standards and data. Supported by NHS Digital, a branch of the UK's National Health Service, they "show how the delivery of health and social care can be transformed when data, information and knowledge in IT systems is open, shareable and computable".
Led by Managing Director Peter Coates, Professor Bamrah and Professor Morgan, and describing themselves as clinician-led, Apperta oversee all sorts of open-source, big data and technology programs for the National Health Service. Despite being a seemingly technically literate organization, Apperta seems to have voluntarily inflicted this data breach upon themselves and it is deeply worrying that Apperta can be so sloppy with their security practices, yet be trusted with private medical data.
Who Discovered The Data Breach?
Open source enthusiast Rob Dyke works in the UK's IT sector and has worked with Apperta in the past on a number of different open-source projects (1, 2, 3). Rob is an active member of the open-source community and works on the NHoS project that builds a free and open-source operating system for the National Health Service.
In late February Rob discovered that Apperta's private and confidential information was publicly available on Github and so he followed industry best practice when it came to disclosing security vulnerabilities and after verifying the contents and taking screenshots, Rob sent a private security advisory to the repositories owner.
This is known as an 'ethical, or responsible data breach disclosure'.
This is exactly what Rob should have done in these circumstances, upon discovering the data online he quickly notified those responsible in an ethical way and initially Apperta thanked him for disclosing the breach and took steps to remediate the issue, taking their publicly available confidential data offline.
So far, so good, but then suddenly things started to turn bad for Rob Dyke.
Shooting The Messenger
On Monday the 8th of March Rob received legal correspondence from Apperta's lawyers stating that they considered Dyke's actions to be "unlawful". He was also contacted by a Northumbria Police cyber investigator in relation to a report of "Computer Misuse" from Apperta, forcing him to hire his own solicitors to respond and represent him. Rob was obviously surprised by this, he knew the team over at Apperta from having previously worked with them before and did not expect this from them.
I unfortunately have seen this sort of behavior too many times before and I can tell you that threatening researchers with legal action for responsibly disclosing a data breach or a security vulnerability is part of a worrying trend of organizations trying to save face by launching legal threats against those who tried to help them.
For years now organizations have been using lawsuits against researchers who responsibly disclose major security issues to them, they do it to shift blame away from themselves and the impact of this legal action has had a "chilling effect" on the wider information security community. Security researchers are now wary about reporting security issues to organizations in case they expose themselves to legal action.
Taking legal action against ethical researchers for responsibly disclosing security vulnerabilities runs counter to information security industry best practices and demonstrates a worrying lack of awareness of disclosure practice, doubly so when an organization with access to private or confidential medical data is concerned.
Apperta's behavior runs counter to advice from the US National Institute of Standards and Technology (NIST) who recognize in their Cybersecurity Framework that responsible vulnerability disclosure is an important aspect of any effective cybersecurity program. Shooting the messenger is an act of desperation, engaged in by organizations with weak cybersecurity practices. Apperta is not only punishing the person who first warned them of their self inflicted data breach in an effort to cover it up, they are also announcing to the wider world that they place no real value on responsible disclosure and broadcasting their general lack of cybersecurity and data privacy sophistication.
You can read Rob's take on the matter here and the story was briefly covered by technology reporter Ax Sharma over at Bleeping Computer, but other than that there has been absolutely zero coverage of the story from the mainstream press. Despite Apperta being a publicly funded organization, despite them having access to confidential National Health Service data, despite spending taxpayer money on frivolous legal action and despite their confidential data being exposed in a self inflicted data breach, so far and somehow Apperta have managed to avoid media and regulatory attention.
Apperta are seemingly getting away with a horrific privacy blunder, seemingly trying to brush a data breach under the rug and seemingly spending public funds on legal vendettas against the person who responsibly disclosed their obvious lack of data security practices to them. Appalling behavior for a publicly funded non-profit.
The Response From Apperta
An Apperta Foundation spokesperson issued a statement in response to questions from reporters and the wider information security community (extract).
On or about 26 February 2021, it is understood that an unauthorised individual or individuals breached a private portal to access financial information related to The Apperta Foundation. We can assure the community that personal data was not targeted or accessed about individuals. The Foundation’s directors have a responsibility to protect its confidential information, including data and intellectual property owned by the Apperta Foundation.
All I can say about their statement is that Rob really doesn't need authorization to browse a public website and discover Apperta's publicly available confidential data on it, I can also tell you that describing a publicly available repository on Github as a "a private portal" is an obvious untruth and that the Foundation's directors have obviously failed in their responsibility to protect the data and IP owned by the Foundation.
A Community Funded Legal Defense
The information security community is quite rightly outraged at the way that Rob is being treated and the fact that public money is being spent on frivolous legal action. the community has rallied to Rob's cause and hundreds of people have generously donated to a GoFundMe campaign set up to help Rob defend himself legally against Apperta's actions, raising just half of the money he needs to successfully defend himself.

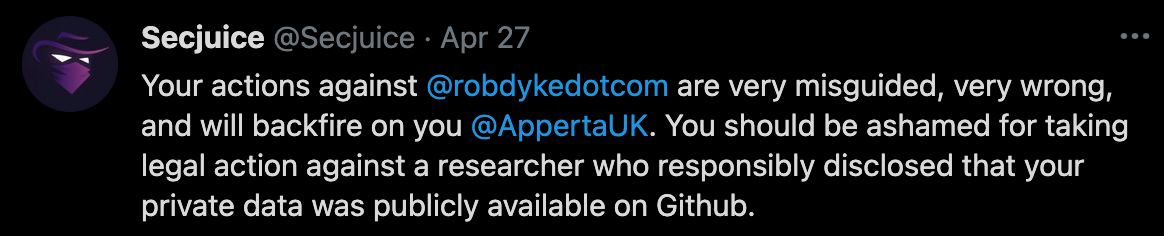
As well as donating to Rob's legal case, security professionals from across the information security industry have publicly stated their support for Rob's case, I have pasted a number of these public messages of support below this article.
Those who have donated to Rob's campaign and those who have publicly voiced support for Rob's case share in common a belief that the legal action taken by Apperta against Rob is a direct threat to the wider principle of responsible disclosure.
We all believe that those who engage in the responsible disclosure of security vulnerabilities and data breaches should be afforded legal protection, we all believe that organizations who take legal action against those who responsibly disclose are indirectly encouraging cybercrime. In general, if you make it hard for security researchers to responsibly disclose, you make it easier for them to sell your data to cybercriminals or auction off your security vulnerability to places like Zerodium.
This is why I am asking you to support Rob's case if you think its right and donate a little to his legal campaign if you can. It isn't right that Rob is being forced to incur tens of thousands in legal costs because Apperta are failing to do the right thing. Help us defend responsible disclosure and support Rob if you can.
What Does Information Security Industry Think?
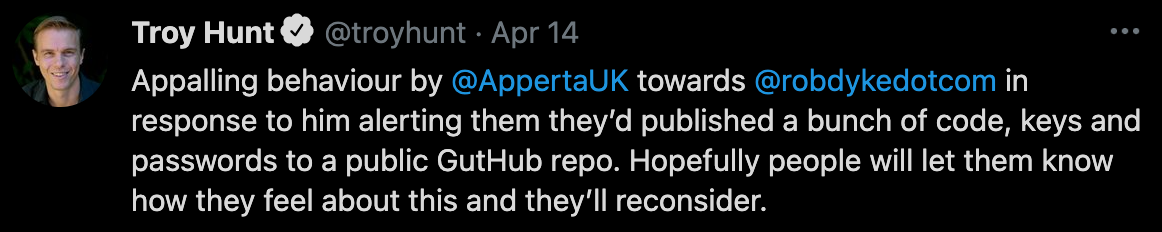
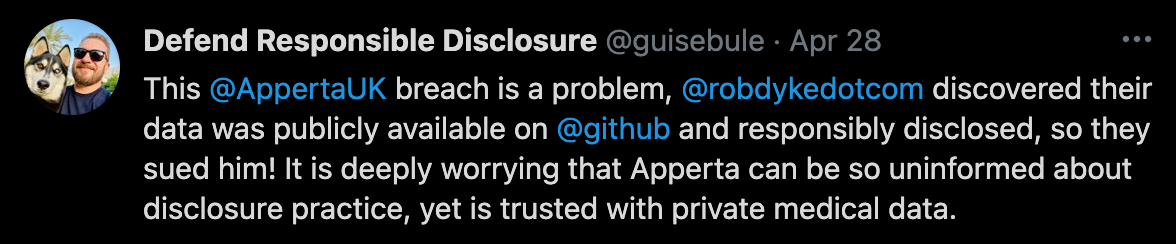
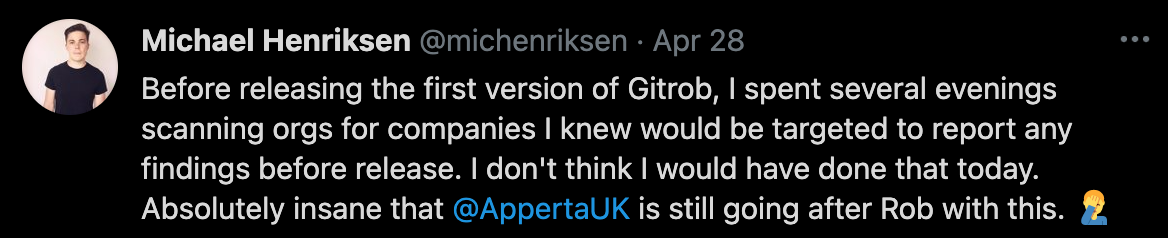
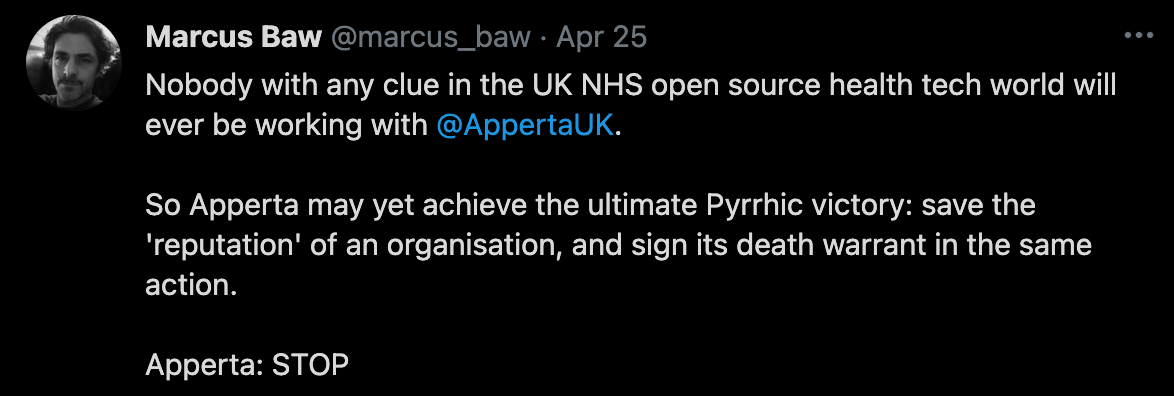
About The Author: Guise Bule has been involved in real world responsible disclosures that have gone bad, and written a number of different articles on the subject of responsible disclosure, he is the founder of Secjuice and an Advocate with the non-profit Hacking Is Not A Crime group, of which Secjuice is an Affiliate.



