APT-Style Spearphishing: How Is It Used To Target High Value Individuals?
Learn about APT style spear phishing and how it can be used in attacks against high value individuals, in our latest article from security researcher Max Bishop.

74% of security incidents were a result of an end user mistake.
Introduction
What is spearphishing? Kaspersky Labs defines it as, “an email or electronic communications scam targeted towards a specific individual, organization or business.”
If you aren’t too familiar, know that in the last year, a poll of 263 IT and InfoSec professionals reported that 74% of security incidents were a result of an end user in that organization downloading an attachment in an email, or clicking a link. With a success rate like that; its no wonder why threat actors haven’t progressed to a more complex model -- don’t fix what’s not broken.
What is Phishing?
What kinds of emails are these threat actors using to compromise these various business networks? Here’s an example of a low quality phishing email with minimal effort exerted to stylize the email contents to appear like the sender the phisher is posing as:
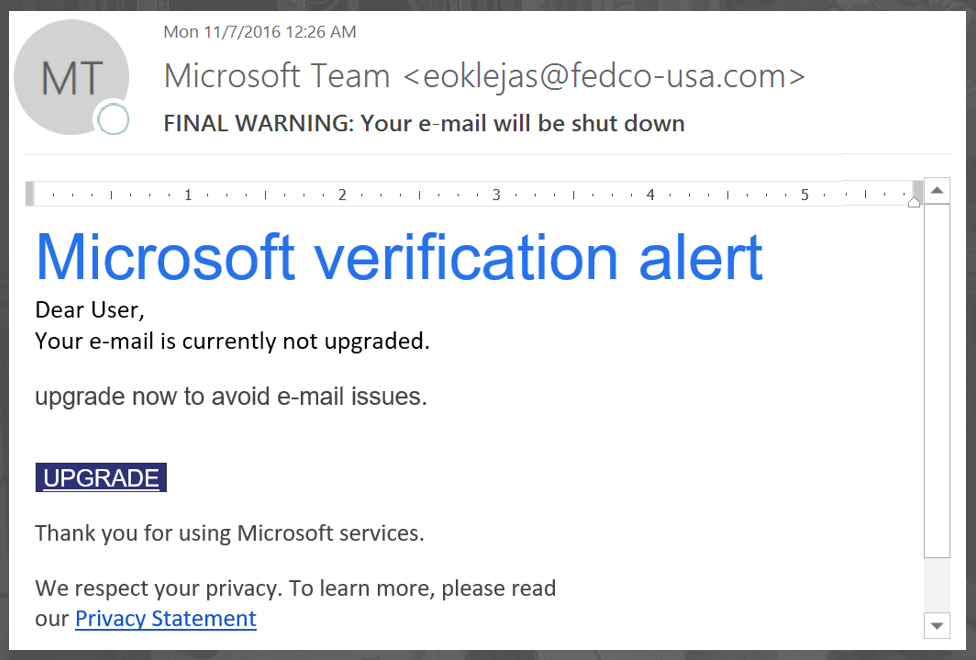
Is this clever or well crafted enough to trick an end user into “upgrading their email” to unwittingly navigate to the phisher’s malicious link? Maybe for some older end users or for some end users who aren’t too tech proficient; but for most of us, it’s doubtful.
What is Spearphishing?
Then we arrive to questions such as, “So how is a good phishing campaign run?”, “What would a well-crafted email contain to trick the end user?” and, “What sort of angle should be used to trigger a more emotional, less logical reaction in the end user?”, plus many more. In fact, that brings me to the difference between good ol’ regular phishing and spearphishing.
General phishing is usually automated and performed by scraping email addresses from the Web, ala “theHarvester” (which we’ll be getting to shortly) or alternate methods, and then scripting code to send out very generic phishing messages to each user, probably much like is pictured above. The idea is that if you mass email a thousand end users; a generic phishing email might trick anywhere from 10 to 100 (just throwing out rough numbers to illustrate a point.)
Meanwhile; a spearphishing effort targets a “specific individual, organization or business; usually focusing on a single gullible-seeming individual to serve as the primary point of entry into the business network. To provide some better context; let’s examine the 2016 spearphishing attack on John Podesta’s Gmail account.
2016 Democratic Campaign Spearphishing
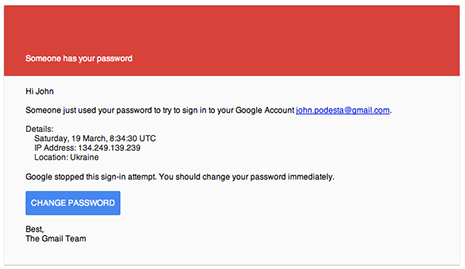
This is probably very close to what the staffers who initially discovered the message saw. From what I’ve read; it was moderately well constructed to mimic the format and style of a real Gmail security alert. There are a few ways in which this differs from the standard kind of phishing we touched on above.
How Does Spearphishing Differ From Phishing?
First and foremost; you can readily see the message is specifically addressed to John Podesta; the Chairman of Hillary Clinton’s 2016 presidential campaign, certainly someone who would have potentially sensitive or interesting information that their party wouldn’t want released.
Next; you can see the emotional appeal the spearphisher is playing on to try and egg Podesta or his staff into actually clicking the provided malicious link, “Change Password”. They crafted this email to mimic a real Gmail security alert warning end users of someone attempting to log into their account, and did a careful job of it.
However, the emotional appeal doesn’t end there. The message specifically states that someone had already obtained Podesta’s password, which would be very concerning as the head of a campaign and an already well established political incumbent. This is to further goade Podesta or his staff into rushing into action without thinking about the legitimacy of the message.
Lastly; the third, and more subtle component. The fraudulent Gmail alert specified that the login attempt using Podesta’s password originated from Ukraine; certainly a region of the world too close to rival foreign governments for comfort; and close enough to stoke Cold War-esque fears of eastern European meddling to make the message even more compelling.
What Happened Next?
Now here’s where things got interesting for Podesta, his staffers, and the phisher. The staffers relayed the message to an IT professional working for the campaign; who did a mostly poor job at responding; failing to perform one of his critical functions as the person responsible for cybersecurity at the campaign.
“This is a legitimate email. John needs to change his password immediately, and ensure that two-factor authentication is turned on his account.
He can go to this link: https://myaccount.google.com/security to do both. It is absolutely imperative that this is done ASAP.
If you or he has any questions, please reach out to me at [redacted]”
So obviously his big mistake is identifying this message as a legitimate email. Without having insider information; my best guess is that an IT professional working on a presidential campaign was probably more than swamped with various security tasks and oversight -- enough that he probably wasn’t firing on all cylinders when responding, and maybe he didn’t even take an actual look at the message.
While it was helpful to reply with the https://myaccount.google.com/security link to the staffers; offering them a secure and effective way to deal with this potential breach; the staffers didn’t stand much a chance of mitigating this phishing attack with their cybersecurity professional confirming that the email is legitimate. Again, this drives home the point that end users click and button mash; they don’t critically assess their usage of a computer system, and if you tell them that something is legitimate, they will assume that you are an authority who knows best.
So, with the spear phishing message confirmed as “legitimate” by the cybersecurity professional in the campaign, the staffers neglected to treat the message with any care, skepticism, or critical thinking; instead electing to ignore the direct link their cybersecurity expert provided and just use the “Change Password” link provided in the initial email. Consequently, whoever took the time to craft the message was provided with assumedly unfettered access to the Podesta Gmail records.
Advanced Spearphishing
It’s worth noting that even in this highly successful attempt on a high ranking politician, the actual message contents could be considered very generic. I consider this spearphishing because of it’s very specific scope (John Podesta’s Gmail account), but an even more complex and compelling effort could be crafted; given the time and the information necessary.
Like I said earlier; emotional appeals tend to work best. Let’s conjure an imaginary scenario in which a generic Gmail security alert from a login attempt from Ukraine wasn’t enough to fool the cybersecurity pro. Let’s assume that message was properly handled; meaning deleted without clicking links or downloading attachments. Let’s assume we still have a spearphisher intent on compromising Podesta’s email account.
A clever spearphisher can ply emotional leverage to prompt a quicker reaction from his end user target. The spearphisher might devise a scenario in which Podesta’ family member approaches him with an emotional trigger requiring the clicking of a link or downloading of an attachment.
Some quick Google-fu will provide the names of John Podesta’s spouse, daughter, brother, and Clinton’s doctor at the time of the campaign. Using your creativity, it’s pretty easy to think of some social engineered phishing relying on an injured or endangered daughter with an attached medical bill, or a warning from a doctor with attached or linked instructions for things to look out for.
The point I’m trying to make is that it only required a half assed (perhaps even quarter assed?) effort at spearphishing; with no complex emotional appeal, to compromise what should have been one of the most secured Gmail accounts out there.
Spearphishing Tools
I would be remiss to describe the process of forging a believable sounding cover story or angle for why your target end user ought to click your attachment or link if I didn’t mention Maltego. Maltego is a tool for enumerating the relationships between people, groups of people, companies, organizations, websites, and more!
Maltego comes ready out-of-the-box with Kali Linux; so I’d recommend that you get your start there, especially since Linux will have other useful tools we may employ later to bolster our effort. I won’t go too in-depth on how to utilize Maltego for network reconnaissance here; as I suspect it may be the subject of a future article & tutorial, but just know that by crawling through a domain; Maltego enables you to enumerate persons and email addresses associated with that domain; in other words, employees or members of an organization that a spearphisher might pose as.
Once you’ve established a comprehensive footprint of the network using Maltego; it should be easy to determine which person the spearphishing email should originate from in order to most likely to result in a breach. You might pose as the local IT staffer if the organization is small, and a single person is trusted to keep the company safe. If the organization is of medium size; try to enumerate their entire IT department; and if possible determine the most senior or highest ranked employee’s email address to pose as.
Conclusion
Computer experts have known for a while now that end users are often the weakest link in a computer network’s various components. The only surefire way to prevent being spearphished is to take the task of educating your end users about security seriously; which unfortunately too few organizations strive for or accomplish.
If there’s any lesson to be learned from APT spearphishing; its that we could all use a refresher on verifying the authenticity of emails; avoiding links and attachments unless absolutely positive of their integrity, and remembering the current threat landscape: phishing dominated.

