Controlling Dwell Time Is About Much More Than Compliance
Breach detection and controlling dwell time is about much more than compliance argues Robert MacMillan.

Image: Pink Radar by Joey Grillo
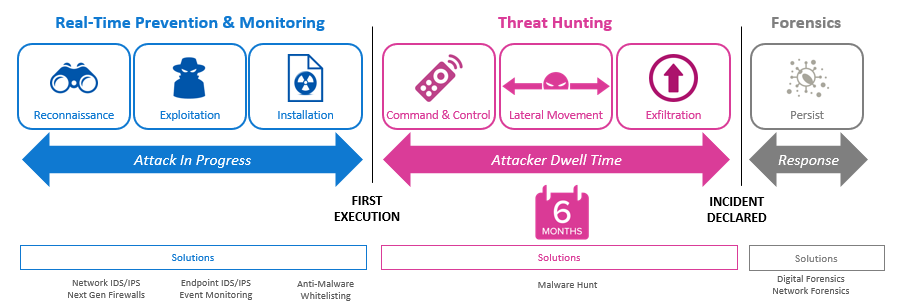
Dwell time, or the breach detection gap, are cybersecurity terms used to describe the period of time between malware executing within an environment and it being detected. Detection can be achieved through a variety of security procedures and solutions, however it seems to often occur when an enterprise is notified of suspicious banking activity or a data breach.
Recent weeks have publicly outed a new batch of victims — companies from Equifax and Deloitte to Sonic Drive In restaurants have been the latest to suffer. Further fallout from older successful attacks has also made the news, specifically FedEx who announced that a cyberattack this past June which disrupted its TNT Express business, dented its Q3 earnings by a third to the tune of roughly $300 million.
Dwell Time and its Implications
So what’s happening here? Companies invest significant amounts of money into defenses to protect enterprise assets, yet malware and APTs continue to breach. Not only does it breach, it lurks undetected for long periods of time. The statistics are not encouraging; per the latest M-Trend reports the global dwell time average is 99 days. The EMEA and Asia Pacific regions fare even worse, averaging 106 days for Europe, Middle East and Africa, rising to a stunning 172 days in Asia.
These lengthy dwell times afford attackers ample opportunity to do everything from silently siphon funds and access proprietary or personal information to observe and record user behavior to enable further illegal activity. Most critically, dwell time is the window of time attackers need to seed secondary malware, RATs, backdoors and other APTs. This type of lateral movement enables a host of damaging activities, such as gaining access to other endpoints, escalating credentials and data exfiltration.
Examining the Deloitte breach a little further, recent leaks have shed light on some details about the hack. Deloitte relies heavily on self-signed certificates for security, and in this case it was the certification server that was compromised — leading to all admin accounts being compromised. In addition, the customer account credentials were compromised, lending credence to the position that, contrary to official company statements, a lot more than just 6 clients were impacted. Citing unnamed sources, The Guardian reported some 350 clients were in fact affected, including U.S. government agencies and large corporations.
The Deloitte breach dates to the fall of 2016, but wasn’t reported until September 2017. Equifax was breached in mid-May 2017 and not discovered until July 29, 2017. There is one correlation in these incidents that is undeniable, the longer the dwell time, the more impactful the breach.
Big breaches, big problems
Dwell time is quickly emerging as one of the top security concerns for boards, executives, and IT security professionals . The issue is relevant to all parties, and impacts everyone — it’s far more than a compliance concern.
As we’ve seen, the fallout from breaches with lengthy dwell times include lost capital, theft of assets, negative customer perception, drops in share price, and impact on earnings to name a few.
In addition to those business concerns, lengthy dwell time has emerged as an actionable legal issue. The class action suit filed against Noodles & Co last year was premised in part on the liability the company had for allowing malware to persist undetected for such a long period of time, in that case the dwell time was approximately 5 months.
The lawsuit was ultimately dismissed because the losses incurred by the financial institutions, which were the plaintiffs, were covered under contracts with VISA and MasterCard. The fundamental underlying liability was not addressed. We can predict the liability will be raised in the future in different legal circumstances.
Companies can lose lucrative contracts, customers, market share and more, if management does not fully accept and appreciate that dwell time is a key security concern that can be managed and controlled.
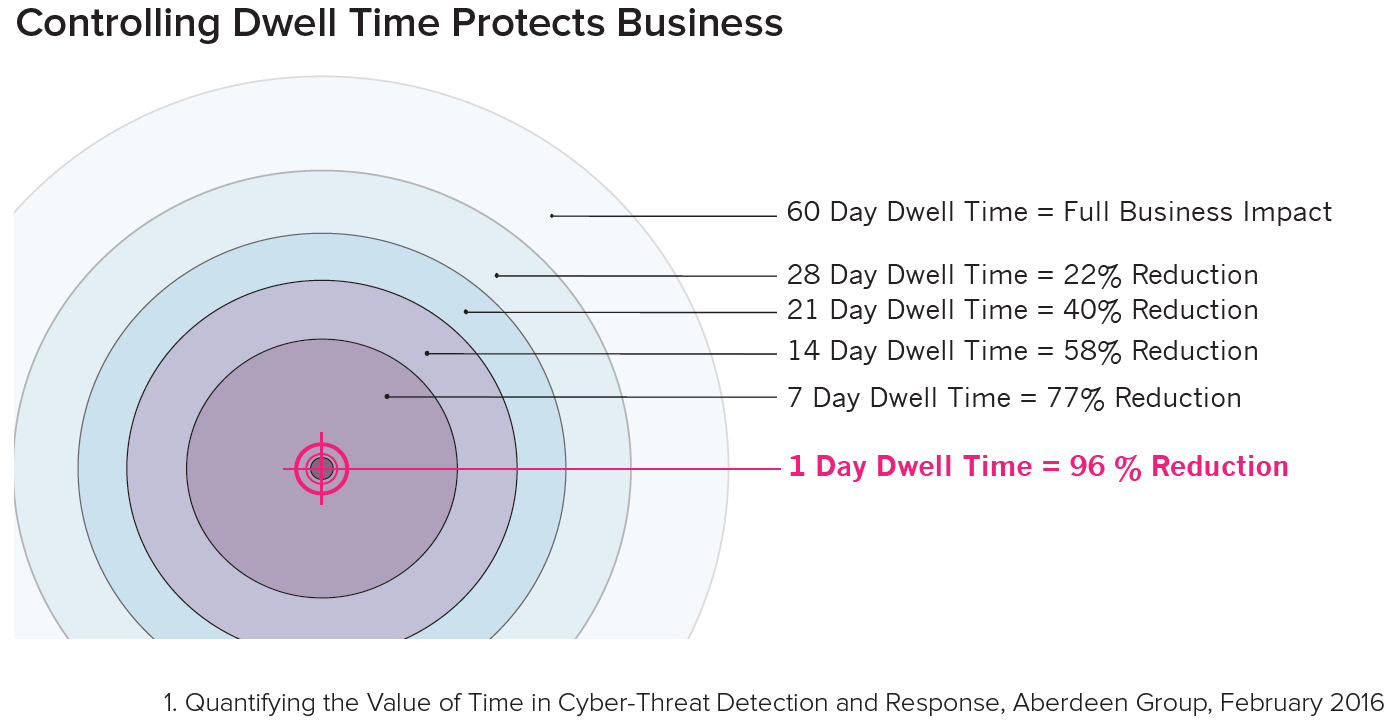
The impact on business has been studied in a 2016 research report by the Aberdeen Group, which determined that simply limiting dwell time to 30 days results in a reduction of the impact on business by 23%. Further compression of dwell time delivers even stronger results for business — when dwell time is confined to 7 days the impact is reduced by 77%, taking it down to 1 day virtually eradicates the impact with a 96% reduction of business impact.
Managing Dwell Time — Why it’s the Goal
As businesses mature their understandings and expectations about cybersecurity, the new best practice must be to control and manage dwell time. It is unrealistic to expect to achieve 100% security using defensive solutions; this simply does not and will not work. Malware and APTs evolve so rapidly there simply is no defense that can protect against all existing and future threats. Likewise, there is no existing solution on the market that can catch every threat as they overcome defenses.
Forward thinking organizations will accept that malware is going to breach their defenses, and therefore must acquire the ability to proactively and iteratively hunt down the malware used by successful cyberattackers.
This is what Infocyte HUNT offers. Using agentless surveys to scan endpoints, the Infocyte platform provides enterprises with the opportunity to effectively control exactly how long any unknown malware are allowed to persist. Scheduling regular scans daily for example, results in a possible dwell time of 24 hours.
This is a reasonable and achievable goal. There is no magic bullet that will protect an enterprise from malicious actors, but there is a tool that puts the control back in the hands of business.
Authors: Robert MacMillan and Jouda Christine Seghair
