Buffer Overflow #1: Introduction
Welcome to part one in Gurkirat Singh's buffer overflow series where he gently introduces the subject.

Welcome to the first in a series of articles I have planned around the concept of a Buffer Overflow, the most hyped and important concept in cyber security for finding flaws in applications and a fundamental of exploit development. In this series you will learn how an allocated chunk of memory is overflown which can affect other running programs, and how to detect and mitigate buffer overflow.
Lets jump right in! In this first chapter you will learn about what a buffer is, and why programmers use it even though they know it may be overflown..
Buffer is a region of a physical memory storage used to temporarily store data while it is being moved from one place to another, typically in the computer’s memory (RAM). Usually the lifetime of buffer is the lifetime of program. This means that the buffer allocated to the program will be destroyed whenever the program ends up.
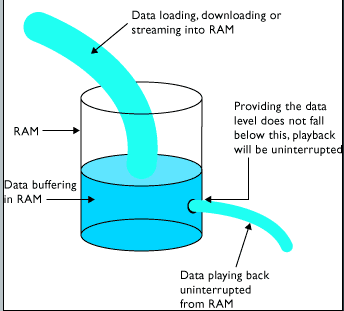
Why Do We Need These Buffers ?
Because they can increase application performance by allowing synchronous operations such as file reads or writes to complete quickly instead of blocking while waiting for hardware interrupts to access a physical disk. This is because the processes of reading and writing data to a disk are relatively slow.
Where Is Buffering Used ?
- Streaming videos over the internet. For example, YouTube uses buffering to play their videos.
- As we have discussed, disk operations are slow so VLC like media players also uses buffer to read — store — view video.
Whenever a buffer is used in any software, it is usually to provide memory can be manipulated and also to provide data from the section that is stored in disk,
How does a buffer looks like in program?
Let me show you how does a typical buffer look. It uses a special type of data structure, Stack (aka LIFO).
Here I wrote a C program with comments demonstrating stack buffer.
Stack has two main operations, and they are
- Push operation representing, the read operation from disk and writing temporarily to RAM aka Buffer
- Pop operation representing, the read operation from Buffer then after it can be either used to perform some computation or save back data to file in disk
The I/O operations associated with hard drive are the slowest one, if an application will not use any buffering it may consist a bit more latency than others. READ MORE
Note: Any operation (not only disk) can use buffer. For example network related operations and requests and database system like SQL Server use buffer to prevent load on server and enhancing the speed.
What is Buffer Overflow, and How it does look like in Memory?
Buffer Overflow is a situation in programming when the program usually tends to write data to outside the allocated buffer to another programs. For example
A program is designed to store 8 character password. And if data entered in the buffer less than equal to 8 length is within the reserved buffer.
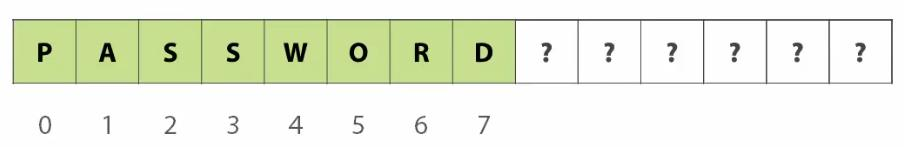
However if somehow the data is being entered beyond the buffer storage space, it tends to write to these “?” marks which may sometime corresponds to other program data

Why do buffer overflow ?
Now you might be wondering why this buffer even overflow.
The basic reason why buffer is overflow, improper memory management or intentionally exceeding the buffer storage memory in order to write adjacent blocks
Improper memory management, is the carelessness of the programmer when he/she doesn’t validate buffer memory allocation and unintentionally user tends to overflow buffer by entering more data. This is usually seen in forms that are not validated before being stored in database
Intentionally, when the attacker tends to enter long input data so as to exploit the system.
What happens when a buffer overflow ?
- Denial of service manages to make resources unavailable for user. This is done intentionally.
- Improper / Wrong output aka Information Corruption, if stored in file or database then whole system can be down due to Denial of Service on all systems using that database
- Change in information, change in program flow. Sometime information not handled properly, thus allowing attacker to change the flow and bypass security parameters
- Arbitrary Code Execution is an attacker’s ability to execute arbitrary commands or code on a target machine.
- Elevated Privileges Command Execution, is the situation application using elevated privileges (higher level) and the Buffer Overflow data may be the executable code is used to run some tasks that need root privileges to be done
What can an attacker do with buffer overflow ?
- Arbitrary code execution
- Giving attacker the control of the computer
- Entering network, or attacking other hosts on network
- Data stealing
- Information Corruption, (includes encrypting data and asking for ransom)
- Denial of Service (by crashing program / operating system)
This whole scenario (intentional buffer overflow) comes under Command and Control which means to gain access and then backdooring the maintain control over the computers. These is achieved by dropping malware and botnets into the compromised system.