Timeline and Details of the Change Healthcare Breach
Discover how this healthcare breach unfolds and learn crucial defense strategies. Dive into our expert analysis for actionable insights.

Important Note: This article is not for the purpose of blame and shame on Change Healthcare or any other named persons or companies. The purpose is to track a major breach, highlight several details, and provide lessons learned. The impact of this breach continues to be highlighted because there was more news every time I went to write more about it. Even as of this writing, there was another bit of news, so I added that.
A Timeline Story of Change Healthcare Breach
It’s February 12, 2024. Using leaked credentials, criminals exploit the Change Healthcare Citrix portal and gain remote desktop access.
Then, on March 14, 2024, we discovered that the Change Healthcare hack might affect billing and care authorization portals, leading to prescription backlogs and missed revenue, posing threats to paychecks and patient care.
On April 8, 2024, we learn of a second round of ransomware attacks. "RansomHub claimed responsibility for attacking Change Healthcare in the last few hours, saying it had 4 TB of the company's data containing personally identifiable information (PII) belonging to active US military personnel and other patients, medical records, payment information, and more. The miscreants demanded a ransom payment from the healthcare IT business within 12 days, or its data would be sold to the highest bidder."
(Relevant side note: on March 22, 2024, it’s believed that ALPHV may have turned into RansomHub – see https://socradar.io/dark-web-profile-ransomhub)
On April 19, people asked:
"Is OCR’s [Office for Civil Rights] 2016 ransomware guidance applicable to the Change Healthcare cyberattack?"
The answer? Yes.
"OCR’s ransomware guidance provides specific information on the steps covered entities and business associates should take to determine if a ransomware incident is a HIPAA breach. A breach, under the HIPAA Rules, is defined as, ‘…the acquisition, access, use, or disclosure of [PHI] in a manner not permitted under the [HIPAA Privacy Rule] which compromises the security or privacy of the PHI.’ See 45 CFR 164.402. Whether the presence of ransomware would be a breach under the HIPAA Rules is a fact-specific determination."
Customers and those affected are looking for a response from someone, anyone, and soon.
On April 22, 2024, Change admitted it paid the $22 million ransomware payment.
Then on April 30, Tom Kellerman (SVP of cyber strategy at Contrast SecurityOn April 30, Tom Kellerman (SVP of cyber strategy at Contrast Security) said, “It’s extremely frustrating to have one of the largest companies in the world failing to meet its obligations under existing law to adequately protect some of our most sensitive personal information.”
Multifactor authentication (MFA) was not enabled. Requiring MFA is considered Security 101 - "This underscores pure negligence on the part of UnitedHealth."
On May 2, 2024, UnitedHealth Group’s (Change is a subsidiary) CEO Andrew Witty "… estimated that data belonging to a substantial portion of the U.S. population could be at risk, although he noted that the exact number of affected individuals is still being determined.”
Now we come to May 6. where we read 5 key lessons learned:
“1. Legacy tech at Change amplified attack’s impact
2. Stolen credentials unlocked access'
3. Incident response cavalry called in
4. Response and recovery snags
5. Multifactor authentication wasn’t turned on”
(Source: https://www.cybersecuritydive.com/news/unitedhealth-change-attack-tech-takeaways/715200/ )
On May 13, the impact has grown. “ALPHV’s cyber attack on Change Healthcare is one of the most impactful in history. Change Healthcare is one of the world's largest health payment processing companies, and it is a subsidiary of United Healthcare. As a clearing house for 15 billion medical claims yearly, it makes up nearly 40% of all claims.”
Now we’re up to May 20, and we see the following complaints from groups about the lack of notifications, especially when it’s a) this late in the game and b) things seem to be getting worse:
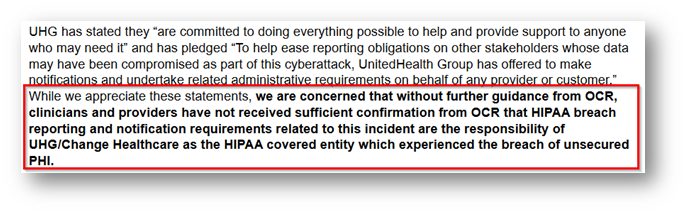
On May 21, 2024, we read that "More than 100 medical associations and industry groups representing tens of thousands of U.S. doctors and healthcare professionals have banded together to urge federal regulators to hold Change Healthcare responsible for breach notifications related to a massive February ransomware attack." (https://www.databreachtoday.com/100-groups-urge-feds-to-put-uhg-on-hook-for-breach-notices-a-25285)
We’re up to June 20, and “…Change will begin to notify health care providers, insurance companies, and other customers that their patients’ data was stolen in the company’s February cyberattack…” https://www.statnews.com/2024/06/20/change-healthcare-cyberattack-patient-data-stolen-notification/ (this link has a handy brief timeline of the main events)
Some details and analysis (or back to regular writing)
In February 2024, a soon-to-be-realized devastating ransomware attack crippled Change Healthcare's systems, disrupting critical healthcare functions nationwide. The BlackCat/ALPHV hacking group exploited vulnerabilities to freeze the company's billing, prescribing, and data portals used by thousands of providers. This cyberattack impacted one-third of U.S. patient records, delaying care and creating financial havoc as claims went unprocessed. The fallout prompted pleas for government intervention and a renewed focus on cybersecurity across the healthcare industry. This article examines the timeline of events, immediate repercussions, guidance for impacted organizations, and key lessons to prevent future attacks of this magnitude.
The Cyberattack
The cybercriminals exploited vulnerabilities in the company's Active Directory infrastructure to gain initial access and move laterally across the network.
Once inside, the hackers deployed their virulent ransomware strain, encrypting critical data and systems used by over 30,000 healthcare providers located in the United States. Change Healthcare's claims processing, revenue cycle management, and clinical communications platforms were paralyzed.
The BlackCat/ALPHV group is a Russian-based cybercrime syndicate known for its "double extortion" tactics, which involve encrypting data and exfiltrating sensitive information to extort victims (more about this group below). In this attack, they claimed to have stolen over 1 terabyte of data from Change Healthcare before activating the ransomware.
The impact was immediate and far-reaching. Providers were locked out of systems needed for prior authorizations, e-prescribing, scheduling, and billing. The enormous patient data flow disruption in the U.S. created massive operational challenges.
Change Healthcare took systems offline to contain the attack, but the damage was done. Healthcare organizations scrambled for workarounds as the company raced to investigate, recover backups, and negotiate with the ransomware gang.
Who is ALPHV/BlackCat?
ALPHV/BlackCat is a ransomware group that develops and uses ransomware of the same name to attack organizations. When organizations get hit by ALPHV/BlackCat ransomware, they must obtain a decryption tool from the ransomware developers (decryption keys) to recover their encrypted data. (obligatory warning about the dangers of paying ransoms). ALPHV may have turned into RansomHub, noted by SOCRadar: https://socradar.io/dark-web-profile-ransomhub/
What are their tactics? I'm glad you asked! The MITRE ATT&CK Navigator has great guidance on protecting yourself from the group in particular and ransomware in general.
The Navigator is found here: https://mitre-attack.github.io/attack-navigator/
Below is a very small image of the matrix (only 11 of the 14 tactics), but to see the real thing, just go to the Attack Navigator, search for BlackCat, go to Software, select All, then choose the Background color you want (it doesn't always have to be the blood-pressure-raising red!)
How did the $22 million ransom payment impact ALPHV/BlackCat's operations?
The alleged $22 million ransom payment from UnitedHealth Group's Change/Optum subsidiary to the ALPHV/BlackCat ransomware group following the attack on Change Healthcare had a major impact on the group's operations:
1. An ALPHV/BlackCat affiliate claimed that after Change/Optum paid the $22 million ransom, ALPHV suspended the affiliate's account and kept all the ransom money for themselves instead of paying the affiliate their cut. This affiliate, known as "Notchy," said they still had the stolen data from Change Healthcare despite the ransom payment.
2. The accusation from the disgruntled affiliate seems to have prompted ALPHV/BlackCat to shut down its operations entirely in what appears to be an "exit scam." They put up a fake law enforcement seizure notice on its darknet site, but security researchers determined this was staged.
(Notice the .onion address in the image below. Another necessary warning – be very wary when perusing the dark web).
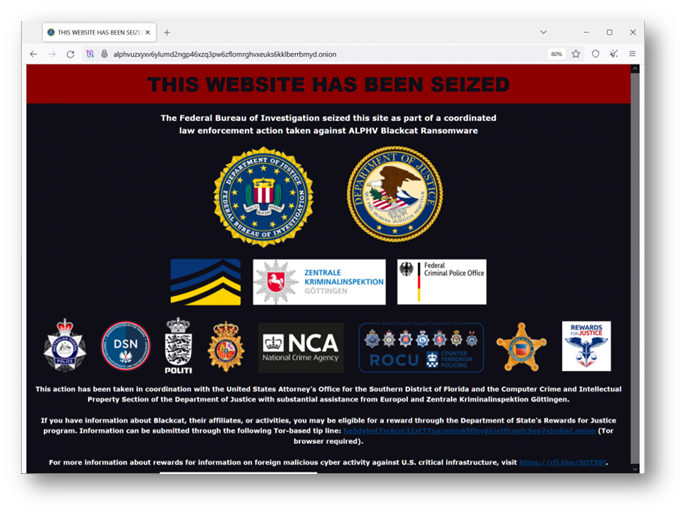
(Image source: https://www.bleepingcomputer.com/news/security/blackcat-ransomware-shuts-down-in-exit-scam-blames-the-feds/ )
3. ALPHV/BlackCat representatives blamed the feds and intended to sell their ransomware source code for $5 million before disappearing.
4. Security experts assessed that rather than being taken down by law enforcement, ALPHV/BlackCat was likely conducting an exit scam by abruptly closing up shop while keeping all the recent ransom payments, including the $22 million from Optum, without paying affiliates their cuts. (I wonder: to what law enforcement or other agencies do criminals go to report unpaid wages?)
5. The alleged $22 million ransom may have provided a lucrative opportunity for ALPHV/BlackCat to cash out and rebrand under a new name, burning bridges with affiliates in the process after making off with a huge payment.
The massive, alleged ransom from Optum appears to have backfired, leading ALPHV/BlackCat to turn on their affiliates, stage a shutdown, and potentially conduct an exit scam while keeping the $22 million ransom entirely for themselves before a potential rebrand.
Patient Impact and Notifications
The Change Healthcare breach had significant implications for patients across the United States. The cyberattack disrupted critical systems used for activities like prior authorizations, prescribing, and claims processing. This disruption created delays and backlogs that directly impacted patient care and service access. The U.S. Department of Health and Human Services' Office for Civil Rights (OCR) issued guidance reminding healthcare entities of their obligations under HIPAA to provide timely breach notifications to affected individuals. Entities were advised to work closely with their business associates, like Change Healthcare, to determine if patient data was involved. UnitedHealth Group, one of the nation's largest health insurers, is committed to notifying patients on behalf of the thousands of provider organizations impacted. They aimed to streamline the notification process and provide clear information to patients about the incident and the steps being taken. Healthcare organizations also had to be vigilant about potential scams targeting patients. Cybercriminals will capitalize on high-profile breaches through phishing emails and calls claiming to be from any affected company. Patients were warned to be cautious of any unsolicited communications asking for personal or financial information. Timely breach notifications and patient outreach were crucial for maintaining trust and allowing individuals to take appropriate precautions to monitor for any misuse of their data resulting from the Change Healthcare attack. Individual notification began on June 20, 2024.
Government Response
Faced with the far-reaching disruptions caused by the Change Healthcare attack, the U.S. government took action to support the impacted healthcare organizations. The Department of Health and Human Services (HHS) and its Centers for Medicare & Medicaid Services (CMS) took several steps to mitigate the fallout.
Change Healthcare and HHS issued special guidance and Frequently Asked Questions to provide flexibility to healthcare providers unable to meet certain regulatory requirements due to the cyberattack. This included extending deadlines for quality data submissions and adjusting Medicare payment policies. See the following for the FAQs: https://www.hhs.gov/hipaa/for-professionals/special-topics/change-healthcare-cybersecurity-incident-frequently-asked-questions/index.html and (https://www.unitedhealthgroup.com/ns/health-data-breach.html )
To address cash flow issues caused by delayed claims processing, CMS established an Advance Payment Program, allowing eligible providers to request upfront payments for anticipated Medicare reimbursements. This provided much-needed financial relief during the crisis.
HHS also compiled resources from major health insurers like Anthem, Humana, and UnitedHealthcare to help providers reconnect to insurer portals and applications impacted by the Change Healthcare outage. This centralized information sharing was critical for restoring operations.
While the government response aimed to ease the burden, it also highlighted gaps in the healthcare sector's cyber resilience when a major vendor like Change Healthcare is compromised. Policymakers called for increased collaboration between public and private entities to enhance cybersecurity preparedness going forward.
How can healthcare organizations protect themselves?
It’s no good to review what happened without having some lessons to learn. What can healthcare organizations (and almost every other) do to mitigate, if not prevent, cyber-attacks? Below is a fairly generic list, but also realize that the thought put into one’s security program is necessary because there’s no one-size-fits solution, and each organization is truly unique. Also, remember that stopping an attack at any point along the way (before network intrusion, before host intrusion, before account takeover, etc.) generally stops the entire attack chain. (Yes, attackers often think in graphs and can pivot to try another tactic, but many criminals take the path of least resistance. Organizations should stop them in their tracks to avert the continuation of the current attack. No one said infosec is easy!)
Perform Regular Risk Assessments
- Conduct risk assessments to identify vulnerabilities and define an appropriate risk appetite for your organization
- US healthcare organizations have the HIPAA Security and Privacy Rules to help provide guidance on what's expected. As always, guidance doesn't equate to actionable steps, which is where creativity and project management come into play.
For other organizations, using frameworks (e.g., NIST Cybersecurity Framework (CSF), CIS Controls (not a true business framework, but a terrific infosec/cybersec guidance!), ISO 27001) to evaluate inherent and residual risk levels can go a long way in setting up a baseline
- Implement security controls strategically to reduce residual risk below the defined risk appetite
Develop a Robust Cybersecurity Program
- Establish a comprehensive cybersecurity program tailored to the unique cyber threats of your healthcare organization
- Remember that key threats include ransomware attacks and disruptions in critical systems/operations. Phishing education and redundancy go a long way in this category.
- Implement recommended controls and best practices for mitigating major threat vectors (here’s a good presentation on the topic for healthcare: https://www.hhs.gov/sites/default/files/web-application-attacks-in-healthcare.pdf)
Enhance Incident Response and Recovery
- Have a tested incident response plan and business continuity strategy in place (if you want to go straightforward and fun, an annual tabletop exercise (TTX) is an option)
- Be prepared to disconnect from affected systems during an incident until safe reconnection
- Follow guidance from HHS, FBI, CISA and information-sharing groups like H-ISAC on the latest threats (H-ISAC membership benefits: https://h-isac.org/h-isac-membership/)
Improve Cyber Hygiene and Awareness
- Provide cybersecurity training to clinicians and other staff on risks and best practices. It should always be role-appropriate; otherwise, your coworkers will not like you as much as they did before the modules got rolled out.
- Implement multi-factor authentication, patching, backups, access controls
- Utilize government and industry resources for small practices (e.g. HHS 405(d) program - https://405d.hhs.gov/)
Increase Collaboration and Information Sharing
- Participate in information-sharing groups like H-ISAC for threat intelligence (H-ISAC membership benefits: https://h-isac.org/h-isac-membership/)
- Leverage HHS's "one-stop shop" (when it’s ready) for incident response support and services (https://federalnewsnetwork.com/cybersecurity/2024/04/hhs-looks-to-create-one-stop-shop-for-healthcare-cybersecurity/)
- Follow guidance from healthcare associations like AHA during major incidents (https://www.aha.org/cybersecurity/cybersecurity-incident-preparedness-and-response)
What’s Next?
There’s always hope. Do the next thing, and the next thing will follow. The next thing is often the first in a list of 100 or 1,000 things to do, but that’s what professionals get paid for – do it, do it right, do it right now. Best wishes in your journey of securing your organization!
Sources, References, and Further Reading (not in any particular order)
https://www.upguard.com/blog/ultimate-cybersecurity-guide-for-healthcare
https://aspr.hhs.gov/cyber/Documents/Health-Care-Sector-Cybersecurity-Dec2023-508.pdf
https://h-isac.org/latest-news/
https://www.ama-assn.org/practice-management/sustainability/physician-cybersecurity
https://www.scmagazine.com/brief/alphv-blackcats-ransom-laundering-escalates
https://blog.barracuda.com/2024/03/06/alphv-blackcat-ransomware-goes-dark
https://thehackernews.com/2024/03/exit-scam-blackcat-ransomware-group.htm l
https://blog.barracuda.com/2024/03/06/alphv-blackcat-ransomware-goes-dark
https://en.wikipedia.org/wiki/BlackCat_%28cyber_gang%29
https://securityscorecard.com/research/deep-dive-into-alphv-blackcat-ransomware/
https://www.techtarget.com/whatis/feature/The-Change-Healthcare-attack-Explaining-how-it-happened
https://www.nationalregister.org/change-healthcare-breach-information-and-resources/
https://www.theregister.com/2024/05/08/unitedhealths_egregious_negligence/

