Cyber Threat Intelligence
Get a peak into Ross Moore's guide on Cyber Threat Intelligence (CTI), exploring its vital role in reshaping modern cybersecurity strategies.

Creating Things
Lately, I've been doing woodworking. I've made my own desk, laptop riser, a stool, drinking cups, and some other things. But don't expect pictures! These are just for me and the family. I'm not trying to make any money, or share designs, or anything like that. I need something, so I make it if possible.
Also, the wood is from trees that we felled and milled. So, from beginning to end, the projects are made from materials that I have available. There’s nothing at all wrong about buying wood or pre-made items, but we have a budget (as is anybody DOESN’T have a budget)
What does this have to do with Cyber Threat Intelligence (CTI)? CTI has to be what's relevant to you and your org. Like so many other things in business, Threat Intelligence solutions are abundant, but finding or making a solution that actually works for your business takes trial-and-error, especially if the budget is 0. And it doesn't have to be pretty and win awards or be ready to share with others - it has to fit the business and be agreeable to your boss.
You'll have to put in the time to learn, use what you have and what you're able to find, and all without expecting to be certified or noted as an expert. Do what you can, with what you have, where you are. Maybe you'll end up getting certified or gaining notoriety as an expert, or asked to speak or teach, but don't go into it expecting to be lauded as a great CTI analyst right away, or any time soon. If you go in with a humble attitude of "I'm doing this to help the company/clients, I'll learn and improve along the way as I try things," then you'll end up learning and doing more (upskilling) than if there's any immediate contingency other than being a better practitioner. And who knows where that will lead!
CTI is currently an open field, even down to the definition. There are no complete ready-made programs, and that causes issues when one goes looking for how to create a CTI program: there are no pre-created ways to do it. The program has to be internal and personal; you have to make it yours.
This doesn’t mean there are no tools, nor does it mean that there’s no assistance or people trying to help. There’s a lot out there, and lots of individuals and companies working hard to provide tools, resources, and training. The end of this article provides a fraction of the resources available to help on the journey to implementing a CTI program.
Caveat Emptor/Disclaimer/Full Disclosure/etc. - None of this is intended to promote or recommend any particular vendor, nor am I suggesting to any readers that they must sign up for anything like a particular PDF or service. Choose your own adventure, have fun toying with various technologies, and work with applications that work for you.
What is CTI?
While there is no official Webster’s Dictionary definition, this is what I’ll use here: CTI involves collecting, processing, and analyzing data to understand the motives, targets, and attack behaviors of threat actors. (think of describing CTI for your org rather than defining it). CTI enables organizations to make faster, more informed, data-backed security decisions, and change the behavior of data defenders from reactive to proactive and responsive in the fight against threat actors.
This is from arcX’s (free!) CTI 101 training: “The usefulness of cyber threat intelligence is predominantly based on its actionability from an organisational standpoint.”
This standpoint provides both liberty and frustration – you’re free to make it how you like, BUT what in the world is the organization looking for (if they’re even looking for anything, which makes it more like a Herculean, or even Sisyphean, task – trying to provide a service to an org that doesn’t even know it needs).
Types of CTI
There are four types of cyber threat intelligence – Strategic, Tactical, Technical, and Operational.
· Strategic CTI focuses on long-term trends and potential threats and informing high-level decision-making for proper allocation of resources.
· Tactical CTI provides short- to medium-term insights, aiding in defensive and incident response.
· Operational CTI provides real-time (or near-real-time) information, and is useful for immediate responses.
You’ll often find just these first 3, but there are many more recent references that include Technical, so I’ll added it here.
· Technical CTI "provides detailed insight for the security team about vulnerabilities, attack vectors, IoCs, TTPs of a threat actor and even includes steps to create a defense strategy." https://www.tripwire.com/state-of-security/introduction-cyber-threat-intelligence-key-concepts-and-principles
Due to how quickly malicious IPs and URLs change, communicating technical intelligence at the right time is vital.
Here’s a useful image from SOCRadar (source here: https://socradar.io/what-is-technical-cyber-threat-intelligence-and-how-to-use-it/)
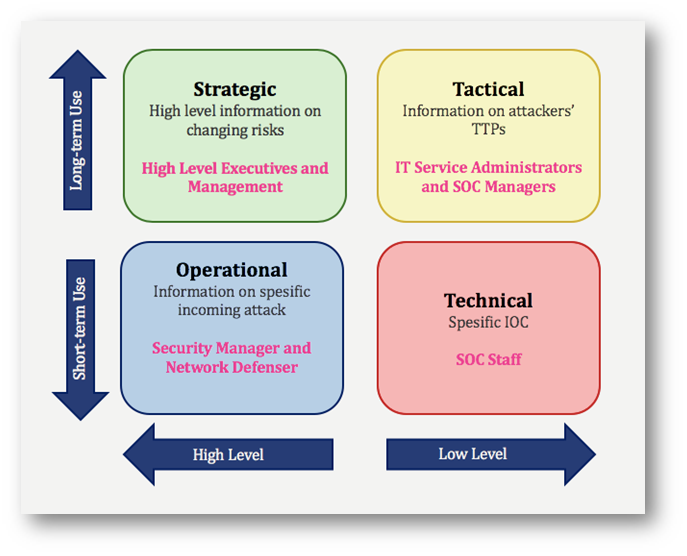
CTI Sources and Categories
Where can organizations get cyber threat intelligence? There are many sources of cyber threat intelligence, including:
- Government agencies
- Private companies
- Open-source intelligence
- Social media
- Dark web (but proceed with caution and pay attention)
When looking for Threat Intelligence sources, knowing the categories will help narrow the search. Oft-used categories (not exhaustive) are:
- Open-source intelligence (OSINT)
- Geospatial intelligence (GEOMINT)
- Human intelligence (HUMINT)
- Technical intelligence (TECHINT)
- Social Intelligence (SOCMINT)
- Signal Intelligence (SIGINT)
Knowing what your goal is will direct you to what type of INT to go for. E.g., if you’re looking for information on an Advanced Persistent Threat (APT), you might waste time asking your coworkers what they know (HUMINT), unless they’re experts on that particular APT.
The Importance and Benefits of CTI
Why is cyber threat intelligence important for organizations? What are the benefits of using cyber threat intelligence?
The Role of CTI in Cybersecurity
With appropriate CTI, cybersecurity practitioners can provide the following in some form to their business:
· Proactive threat detection
· Incident response enhancement
· Vulnerability management
· Patch management
· Risk assessment and management
I say “in some form” because, as mentioned before, CTI is business-specific, so the detail and involvement that’s required, defended, and supported by the business will vary widely from biz-to-biz.
Benefits for Businesses
CTI helps businesses identify threats, mitigate risks, better security resource allocation and effective attack response.
CTI helps organizations save money by identifying and prioritizing the most critical threats that need immediate attention. This can help security teams focus their efforts and resources on the most important security threats, reducing the overall cost of security operations.
CTI also helps security teams work more efficiently by identifying threats and providing actionable intelligence. This can help teams focus on priority security threats, reducing the time and effort required to investigate and respond to security incidents.
How CTI can be used
Security Operation Centers (SOCs) can use CTI to discover IoCs; Incident Response teams can respond appropriately to attacks; Vuln Management teams and tools can prioritize remediations; Business Risk Management can include CTI as part of their information security risk assessment (cybersecurity and information security aren’t the ONLY risks - security and IT practitioners must keep this in mind! - but they are definite risks to include in risk assessments.
The Diamond Model of Intrusion Analysis
The Diamond Model, developed in 2013, is a popular model for that provides guidance in analyzing incidents and threats, gathering threat intel, and mitigating future attacks.
It’s an interconnected workflow that displays how the different actors and aspects connect.
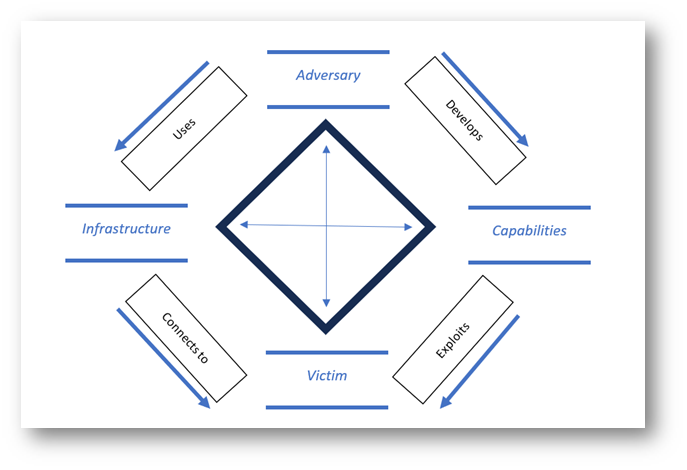
CTI Programs
What are the different components of a cyber threat intelligence program?
Components include:
· Intelligence gathering objectives
· Data sources
· Database repository
· Intelligence/Data Analysis
· Action plans
· Distribution of intel
· Feedback
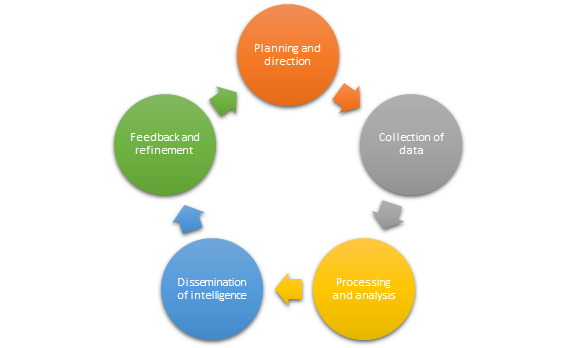
· CTI lifecycle
o This is a key aspect of CTI. There are different models, but the general idea is:
- Planning and direction
- Collection of data
- Processing and analysis
- Dissemination of intelligence
- Feedback and refinement
Guidance for Getting Started
EC-Council has guidance on creating a CTI program: https://www.eccouncil.org/cybersecurity/what-is-cyber-threat-intelligence/ (look down the page for the video "Creating a threat intelligence function that provides measurable value")
A couple other of the multitude of resources out there are:
"How to Set Up a Threat Hunting and Threat Intelligence Program" on HackerNews

and
"Six Key Principles To Building An Effective Cyber Threat Intelligence Program" on Forbes:

In their research “Adopting and integrating cyber-threat intelligence in a commercial organization,” Kotsias, Ahmad, and Scheepers talk about 9 criteria for quality threat intel:
(1) Accurate (presents objective reality),
(2) Relevant (supports the decision-makers conceptualisation of the problem)
(3) Complete (contains essential components required for decision-making),
(4) Precise (provides the level of detail and complexity required for decision-making),
(5) Timely (is presented as early as possible for decision-making),
(6) Usable (is easily understood and meaningful to the decision-maker),
(7) Reliable (presents trustworthy content),
(8) Predictive (anticipates future events significant to decision-maker) and
(9) Tailored (supports and satisfies decision-maker priorities).
Another set of similar checks for quality are presented below under the CREST heading.
Keep these in mind when developing the program. It’s always good to pick something, get it going, see what does and doesn’t work, and refine the process. It sound difficult, but it’s really a natural process.
Measuring Program Maturity
As of this writing, very recently (yesterday as of when I’m typing this) Slavkey published a CTI Maturity Model “to help intel Subject Matter Experts (SMEs), their key stakeholders, and business owners, design, develop, and mature CTI capabilities in a structured and systemic way. Therefore this model is more meant to drive the CTI development than provide a formal assessment tool (like CREST CTI Maturity Assessment Tools: https://www.crest-approved.org/cyber-threat-intelligence-maturity-assessment-tools/).”
CREST CTI – Intelligence Principles
CREST has an excellent PDF about CTI, here: https://www.crest-approved.org/wp-content/uploads/2022/04/CREST-Cyber-Threat-Intelligence.pdf
In it, they have a nice diagram of Intelligence Principles, or what the discerning intelligence analyst looks for in the data given.
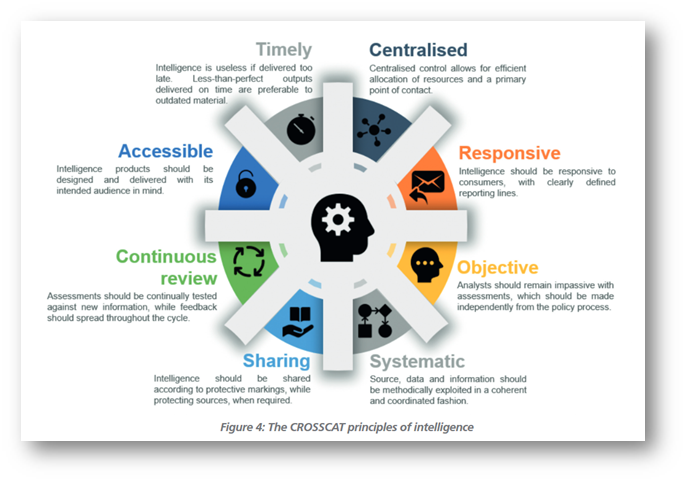
Tools
Gartner’s “Market Guide for Security Threat Intelligence Products and Services” has good guidance on choosing tools and vendors.
One excellent tool for starting is OpenCTI, found here: https://github.com/OpenCTI-Platform/opencti
For any tool, handling all the data ingested will take some robust RAM, drive space, and CPU. But for OpenCTI, if you have a decent laptop you can get started and learn without the need for a LOT of resources.
MISP (Malware Information Sharing Platform) is another free and open source tool: https://www.misp-project.org/ - but it's a little complex and bulky in its requirements, so make sure you're aware of what you have vs. what it requires.
Because many of the free tools are quite limited - often in requiring a paid subsription to get alerts - you'll probably just need to start with local testing and the free online dashboards to get a feel for CTI. It's completely understandable that the subscription is required for more advanced , but realize that going in. When getting started, it's the learning and navigating the tools, and matching the information with your business needs, that counts. So, the lack of advanced functions is fine for getting started.
Pulsedive has a free browser plug-in that analyzes a website for things like WHOIS data, risks, and technologies used. Chrome here, Firefox here.
With a free Mandiant Advantage subscription you can get the Mandian browser plugin for Chrome, Edge, and Firefox.
There are many, many others - try them out.
MITRE
The MITRE group has a lot of materials for the intel community. All of them are relevant (well, depending on what intel you need), but the 4 I’d like to reference here are:
ATT&CK Knowledge : https://attack.mitre.org/
“The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community.”
ATT&CK Navigator: https://mitre-attack.github.io/attack-navigator/
“The ATT&CK Navigator is a web-based tool for annotating and exploring ATT&CK matrices. It can be used to visualize defensive coverage, red/blue team planning, the frequency of detected techniques, and more.”
MITRE D3FEND: https://d3fend.mitre.org/
“A knowledge graph of cybersecurity countermeasures”
Top ATT&CK Techniques: https://top-attack-techniques.mitre-engenuity.org/calculator
“Using our Methodology, along with an additional analysis of 22 ransomware groups over the past three years, the Center for Threat-Informed Defense created a Top 10 ATT&CK Techniques list for ransomware. This list can serve as a starting point for prioritizing ATT&CK techniques when planning to defend against ransomware attacks. This list is based on criteria that we identified as important and is not definitive for all defenders.”
Links and Resources
Here’s a list of some of the resources available. As with any venture or change, start with one. Pick a resource; try out a tool.
Censys - https://search.censys.io/
Shodan - https://www.shodan.io/
DomainTools WhoIs - https://whois.domaintools.com/
VirusTotal - https://www.virustotal.com/
URLhaus - https://urlhaus.abuse.ch/)
ATT&CK Workbench - https://medium.com/mitre-engenuity/att-ck-workbench-2-0-your-bench-your-team-your-most-relevant-ttps-5b9620457ef4
Awesome Threat Intelligence - https://github.com/hslatman/awesome-threat-intelligence
SOCRadar (free tier) – https://socradar.io
Recorded Future - several free tools: https://www.recordedfuture.com/free-products
Recorded Future University - free Intelligence Fundamentals course: https://university.recordedfuture.com/
Study Plan - https://klrgrz.medium.com/cyber-threat-intelligence-study-plan-c60484d319cb
ArcX - Free 101 course: https://arcx.io/courses/cyber-threat-intelligence-101
Anomali Weekly Threat Briefing - https://www.anomali.com/learn/wtb-ff
“Visual Threat Intelligence,” (book) by Thomas Roccia
--I don't often recommend buying things, but I highly recommend this resource. I don't know the author, nor do I get anything for any purchase you make (I didn't put a link to the book, so no trickery here). Thomas did an excellent in bringing resources, training, and his expertise to the field. I learned a long time ago that spending some money on the condensed expertise of authors who spent a good part of their lives over many months or more writing to train and help others is an investment, not an expense).
https://attack.mitre.org/resources/training/cti/
https://threatconnect.com/blog/diamond-model-threat-intelligence-star-wars/
https://chrissanders.org/training/cuckoosegg/
http://veriscommunity.net/howto.html
https://www.cisecurity.org/insights/blog/a-new-vision-for-cyber-threat-intelligence-at-the-ms-isac
https://start.me/p/wMrA5z/cyber-threat-intelligence
https://www.crowdstrike.com/cybersecurity-101/threat-intelligence/
https://www.gartner.com/doc/reprints?id=1-2DI2ON9F&ct=230505&st=sb
https://www.sans.org/webcasts/sans-2022-cyber-threat-intelligence-survey/
https://www.eccouncil.org/cybersecurity/what-is-cyber-threat-intelligence/
https://en.wikipedia.org/wiki/Cyber_threat_intelligence
VERIS (Vocabulary for Event Recording and Incident Sharing) (From Verizon) - https://github.com/vz-risk/VCDB
Mandiant - https://www.mandiant.com/intelligence/cyber-threat-intelligence
The Future
Don’t give up, keep learning, continue researching, and create!



