Data Destruction 101
This article will teach you everything you need to know to cover your digital traces when using Windows.
In today’s digital age, data destruction is considered an integral part of any high quality data management program. The majority of jurisdictions in developing countries requires organizations and companies who handle private data to destroy it securely to protect individuals -and businesses- privacy from the potential impact of a data breach or inadvertent disclosure.
Windows is still dominating the market share of desktop/laptop computers with over 80% of global market share in this segment. This article will teach you everything you need to know to cover your digital traces when using the most used OS on earth, Windows.
The following areas will be covered:
- Data destruction techniques, both software and hardware techniques to wipe clean your data on hard drives.
- How to configure Windows to stop recording your previous actions when using it.
- Tools and advice to minimize the amount of data created as a part of your daily computing activities.
For individuals, you can consider this article as a fast guide on how to improve your digital privacy when using Windows, it will also draw user attention to the amount of digital traces left behind after using Windows machines.
Data Destruction
Data destruction is concerned with making your data/remnant data unreadable and impossible to recover. There are three types of hard disk destruction techniques: Physical, degaussing and logical destruction (Sanitizing). Before beginning describing each technique, let us first talk about the different types of hard drive already in use.
There are mainly two types of hard drives used in computers:
- Hard disk drive (HDD): This is the traditional (mechanical) hard disk drive, it uses a metal platter/s made of glass or aluminum coated with magnetic material to store data.
- Solid State Drive (SSD): This is a more advanced version of HDD, it does not contain any moving parts and store data on small microchips unites similar to USB flash drives. Data can be accessed in SSD even when the electricity is not powered on. SSD is faster than HDD, but it is more expensive.
In terms of data recovery, recovering data from the HDD is relatively easy and can be achieved with free tools. For instance, the majority of deleted files can be recovered in the Windows OS if you manage to recover them fast enough before Windows writes new data to the same disk holding them.
So, when Windows deletes a file, all it really does is mark the space on the hard drive that your deleted file occupied as free, thus it only deletes the pointer to this file. This operation helps to speed up the deletion process and saves valuable time. For example, deleting a 10 GB file needs time equal to writing 10 GB of data to your hard drive. By removing only, the pointer to the deleted file, its space will be freed up immediately (theoretically of course); however, data that belong to deleted file blocks will remain on the disk and will not be removed until Windows needs to write new data in their place.
The previous discussion is applicable to HDD only, recovering data from SSD is more difficult than HDD and impossible in many cases, for instance, SSD uses a different mechanism when handling deleted files. All modern SSDs utilize the TRIM command, when enabled. This command will remove deleted file data blocks instantly allowing for another file to take its space. The SSD uses this technique to speed the writing process next time the OS needs to write data onto drive. There are many approaches to implementing TRIM on SSD devices, which vary according to the OS in use. Some operating systems will execute TRIM instantly after each file deletion, while others will execute TRIM at regular intervals. Windows® 7 and all its successors support TRIM with SSD drives, as do Mac® OS X 10.6.8+ and Android 4.3+.
Recovering data from SSD with the TRIM command enabled is considered extremely difficult and in many situations it is impossible to achieve it completely. Data can be recovered from such drives by using specialized tools, but in order to make the recovery possible, the device should be turned off immediately after the accidental deletion of the file, which may not be the case when investigating suspected devices for incriminating data. After we have a fair understanding of the difference between HDD and SSD, we can move to our main article idea, how to destroy data completely when using both drive types. The following techniques are used to achieve this.
Physical destruction: In this type, digital storage media (Like hard drives, memory sticks, magnetic tapes, CDs, DVDs and Blu-ray discs, credit cards) are destroyed physically to avoid recovery. This technique is usually used in the intelligence agencies and business organizations to assure safe disposal of storage devices and avoid any possible recovery of classified data. The equipment used to destroy these devices are called “Hard Drive Shredders & Destroyers”.
Degaussing: This technique works by exposing HDD or any magnetic storage devices into the powerful magnetic field of a degausser to destroy stored data magnetically. Degaussing works on magnetic storage devices only, a degausser will prove ineffective when used to destroy data on the SSD or USB flash memory as data in such devices is not stored in magnetic coating material like its HDD counterpart. SSD devices should be destroyed physically to assure safe destruction of stored data. Devices exposed to degaussing cannot be reused again to store data.
Logical Destruction (Sanitizing): This is the most used technique by individuals -and many organizations- to assure safe destruction of data. It works by using a specialized software to cover the old data -and remnant of data- with random characters supplied by the wiping tool. There are many techniques already used to destroy data digitally in this way, some are more secure than others.
However, what you should know when using such technique to destroy data, is that it cannot guarantee 100% removal of all data existed on your drive. Some advanced recovery techniques -hardware based- are still able to capture your old data -or at least parts of it- but doing so is costly and time consuming.
The main advantage of software wiping is that your storage device can be used again to store data unlike the previous two methods. Software wiping tools come with some disadvantages, for instance, it needs time to finish as it must write random data multiple times (several passes) over all available sectors on the hard drive, beside, this technique assumes that your hard drive is working and writable in order to write the random data into. Another challenge to wiping software comes when using it to wipe data stored using RAID technology. This technology offers fault tolerance by spreading same data into multiple disk drives in different locations. In such a situation, the wiping tool should be run whenever data are located across all enterprise storage servers. This will cost more money and time.
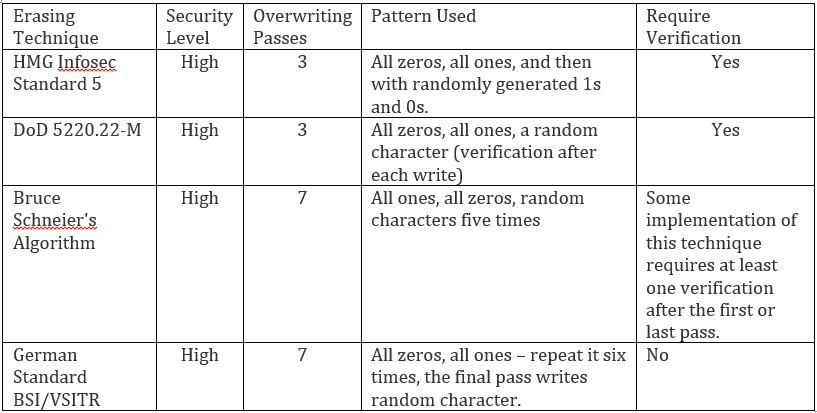
There are different standards developed to wipe clean data (Logical data destruction) on hard drives, the following table shows the most popular one:
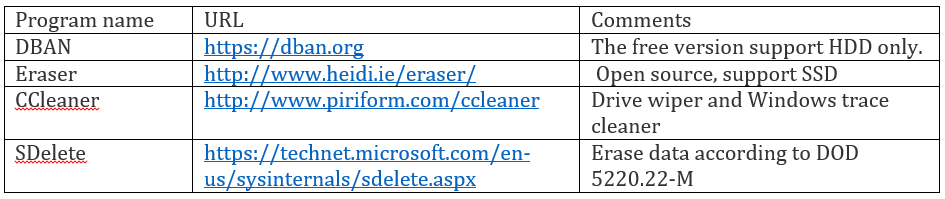
Different programs exist to wipe clean your hard drives, the majority support more than one wiping standard. The following are the most popular one (we list free tools only):
Another great technique to securely erase your important data is to encrypt it first using Full Disk Encryption (you can use BitLocker on Windows or VeraCrypt encryption program), after then format the drive. This will make recovering your previous data extremely difficult and costly.
For SSD drives, the majority of SSD manufactures offer utilities to erase data securely from their drives. You can check your SSD drive manufacture website for such utilities, the following table gives direct links to some of them:

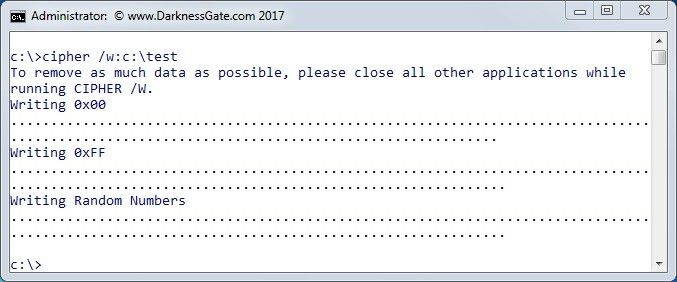
Windows provides a built-in command line utility used to overwrite deleted data to avoid future recovery. All data that is not allocated to files or folders is overwritten using three passes, the first pass writes all zeros (0x00), second pass all 255 (0xFF), and finally a random number. To launch this tool, open a command prompt elevated as Admin and type cipher /w and then specify the driver/folder that identifies that location of the deleted data that you want to overwrite (see Figure 1).
Metadata is data about data. Metadata can contain a considerable amount of technical information about the digital file itself and the author and machine used to create this file. We should not forget digital files’ metadata when talking about digital data destruction. Users are highly advised to clean their digital file’s metadata before sending it through email or posting it online. MS Office provides a way to clean its metadata. For MS Office 2010, 2013, and 2016, you can check document metadata by going to the File ≫ Info, the properties panel will be on the right side. In MS Office® 2007 you need to click Microsoft Office Button ≫ Prepare ≫ Properties.
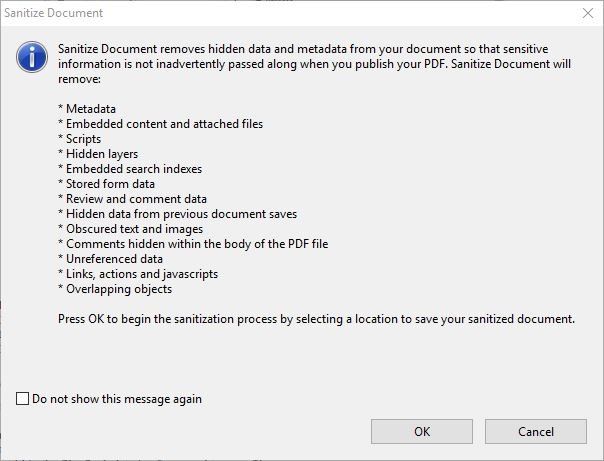
For PDF files, you can use the Sanitize feature -not available in all Acrobat editions- by going to Tools >> Protection >> Hidden Information >> Sanitize Document. The PDF will display a prompt (see Figure 2) showing you the data that will be removed as a part of the Sanitization process.
Stop Recording Your Activities
The next section in our article will discuss how to configure Windows to stop recording our activities when using it. Windows records -almost- any task we do when using it, for instance, installing and uninstalling programs, launching a web browser to surf or to check emails, conducting searches for file/folder, errors generated from Windows and other software (e.g. memory dump) and many more are all recorded somewhere on the hard drive. There are many privacy programs that can perform automatic checks of Windows digital traces in order to delete it, a good privacy tool for Windows is BleachBit | https://www.bleachbit.org , in addition to its main task in deleting user traces in Windows, it has the ability to wipe clean your traces in thousands of applications (including all major web browsers).
Automated tools are perfect for the majority of users and offer an easy way to get rid of your digital traces when using Windows, however, many IT professionals prefer to use manual configurations in addition to the privacy tools to force Windows stop recording many of their important activities. The following covers the main privacy configurations needed in Windows to stop recording our private data and usage activities.
Disable Recycle Bin
When deleting files in Windows, it will move the deleted file to the recycle bin, to force Windows to delete the file directly -without sending it to recycle bin- do the following: Right click on Recycle Bin (usually it resides on the Windows desktop) >> Properties >> tick the option “Don’t move files to the Recycle Bin. Remove files immediately when deleted.”, then click the “Ok” button. Bear in mind that this technique does not guarantee secure removal of deleted files, you still need to use one of the tools already mentioned to overwrite deleted files sector area on the hard drive.
Disable UserAssist
Windows keep tracks of all programs launched on your PC since its installation date, including the number of launch time and other attributes. To disable UserAssist go to the registry and delete all entries under the following key:
HKEY_CURRENT_USER\Software\Microsoft\ Windows\CurrentVersion\Explorer\UserAssist
Note: You can access the Windows registry editor by pressing Windows key + R button and type regedit in the Run dialog then press Enter.
Delete previously Connected USB devices
Windows keeps a history of all connected USB removable storage devices (thumb drives, iPods, digital cameras, external HDD, etc.) in the following registry keys. Each key offers a different set of information about each connected USB device, in order to get rid of them, you should delete each key entries (sub keys – don’t delete the key itself).
HKEY_LOCAL _MACHINE\SYSTEM\CURRENTCONTROLSET\ENUM\USBSTOR
HKEY_LOCAL _MACHINE\SYSTEM\MOUNTEDDEVICES
HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\MOUNTPOINTS2
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\USB
Check this file at C:\Windows\inf\setupapi.dev.log for Windows® Vista, 7, 8, and 10. On Windows® XP this file will be located at C:\Windows\setupapi.log. This file will contain information about each connected USB device and when it was first connected to the system. If you want to view all this info -in addition to many useful USB device manipulations functions- in one location, use a free portable tool from nirsoft, it’s called USBDeview.
Disable Windows Prefetch Feature
This feature boosts Windows performance by predicting which application a user is likely to launch and then works by loading the necessary files to RAM memory to increase the launch time. A copy of each pre-fetched application will remain in the following folder C:\Windows\Prefetch, access this folder and delete everything in it. You can also disable the Prefetch feature by doing the following steps:
Press Windows key + R key, type services.msc in the run dialog and press ENTER. Search for a service named Superfetch and double click to access it. Go to “Startup type” and change it to “Disabled”. Then click the “Ok” button.
Disable Windows Thumbnail Cache
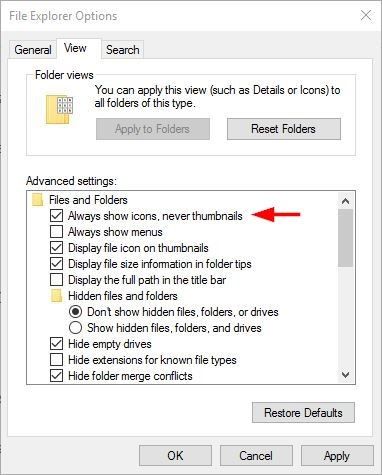
Windows stores thumbnails of major graphics file types in a thumbnail cache file called thumbs.db within each folder that contains such files. This file can reveal information about previous files existed on your system even though you have deleted them. To disable this feature, go to Control Panel >> Folder Options (in Windows 10 it called File Explorer Options” >> View tab >> check the option “Always show icons, never thumbnails” and click the “Ok” button (See Figure 3)
Disable Windows Restore Points and File History
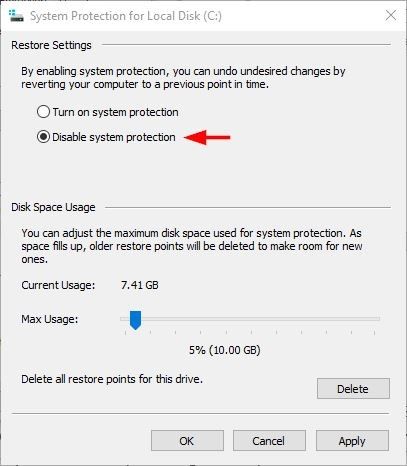
Windows restore points contains backup data and other previously deleted files/folders. Such data can be easily recovered. To disable Windows restore point, go to Control Panel >> System >> System Protection >> select the partition you want to stop generating restore point for it and click “Configure” button. In the new window tick the option “Turn off system protection” (in Windows 10 this option called “Disable system protection”) (see Figure 4).
In Windows 8 and 10, you need also to disable File History, which is a modern Windows feature that backup all your default and custom libraries, Contacts, Documents, Music, Pictures, Videos, Desktop and the OneDrive files available offline on your PC. This feature is disabled by default in Windows and it only saves its backup copies to external drives. In case it is enabled, follow these steps to disable it: Go to Control Panel >> File History If it is already enabled, click Turn Off.
Disable Windows Virtual Memory (Paging file)
Windows uses the paging file to compensate for the shortcut of RAM memory when it becomes full. Paging is considered a security risk for many reasons. For example, if you have a file stored in an encrypted container, and you want to read it, then you need first to decrypt it. Depending on the Windows state, this decrypted file can reside on the Windows virtual memory without your knowledge. An attacker with good IT skills can extract this file and other important data -like encryption keys and passwords- from the paging file. To counter for such risk, it is advisable to disable paging file.
To disable Paging file on Windows, go to Control Panel >> System >> Advanced system settings >> Advanced tab >> from the Performance pane, choose Settings… >> Advanced tab >> Virtual memory section then click the Change… button. From this menu, you can select the drive where you want to disable the paging file by checking the option “No paging file” and then clicking “Set” (see Figure 5).
Disabling this feature will not bring any performance degradation in Windows as the majority of modern computers have adequate RAM memory -more than 4 GB.
Disable Memory Dump
When the system crashes, Windows create a memory dump file which contains information that can help us to understand the reasons of a system crash. This file can contain important unencrypted data and it is highly advised to disable it. To disable this feature, go to Control Panel >> System >> Advanced system settings >> Advanced tab >> Click “Settings…” button in the Startup and Recovery section >> Write debugging information section, select “none” from the drop down menu >> Click the “Ok” button then “Ok” to close the second window and you are done.
Disable Windows Hibernation Feature
Hibernate file (Hiberfil.sys) is a hidden system file located in the root folder of the drive where the operating system is installed. It stores a copy of computer RAM memory at certain times on the hard drive. This file can contain important information like encryption keys, web browsing history, emails and anything that was running or opened in a computer at the time the hibernation done. To disable this feature, launch a command prompt elevated as Administrator and type the following: Powercfg -hibernate off and press the ENTER button.
Disable Windows Logging
Windows events logs store a considerable amount of information about our PC usage, for instance, it records specific events when they happened within the Windows OS. For example, when a user halts an application, an error event will be recorded in the application log. In the same way, when a user fails to log into Windows another event will be saved in the security log event. Windows has a special console that present these events to the end user in a user-friendly way. You can access the event viewer from Control Panel >> Administrative tools >> Event Viewer. To disable Windows Event log, do the following:
Press Windows + R, type services.msc in the Run dialog then click ENTER. Locate “Windows Event Log” and double click to open it. In the General tab, change the Startup type into “Disabled”, then click “OK”.
If you prefer to use automated tools to clean your event logs and other traces in Windows®, there is a portable tool from nirsoft called CleanAfterMe | http://www.nirsoft.net/utils/clean_after_me.html it allows you to clean the majority of your digital traces created by the Windows® OS during your regular computer work. Automated tools are a simple and fast choice that requires no advanced IT skills, although it is also necessary to know what Windows logs your actions. It is essential to know where these logs are stored in order to assist those with security concerned users to check manually for any traces left on their machines even after using automated tools to clear traces.
In the last section of this article, we will give some advice and best practices to minimize our digital footprint when using Windows OS.
- Use bootable USB token or live CD/DVD when working on sensitive documents. Running Tails OS in offline mode is a great practice. There are many tools can help you to create bootable USB/CD. The following list some:
• Windows USB/DVD download tool | https://wudt.codeplex.com
• Rufus | https://rufus.akeo.ie
• Universal USB Installer | https://www.pendrivelinux.com/universal-usb-installer-easy-as-1-2-3
• WinBuilder | http://winbuilder.net - Use virtualization technology to enhance your privacy and protect your host machine from malware and other security risks. Popular virtual machines include: VirtualBox | https://www.virtualbox.org and VMware Workstation Player | http://www.vmware.com/products/player/playerpro-evaluation.html.
- Use portable applications which can run without the need to install them into the system. This will effectively reduce our digital footprint, although some traces will remain in Windows OS after executing such tools (e.g traces in Windows Prefetch folder and maybe in registry). Some popular portable App suites:
• PortableApps.com | http://portableapps.com/suite
• Liberkey, 295 Apps | http://www.liberkey.com/en
• Pendriveapps | https://www.pendriveapps.com - Use encryption and data concealment techniques to protect your data.
- Clear your previous activities on Windows using the tools already mentioned.
If your main aim is to protect your digital privacy when using Windows, this article should draw your attention to where you should start, however, the topic of digital privacy is more complicated and intercept other subjects like anonymity, cryptography and steganography in addition to best practices when using social networking sites. For expert computer forensics investigators, this article should enrich their thinking about possible places where data can be found when investigating previous suspect computer usage.
Summary
If your main aim is to protect your digital privacy when using Windows while conducting your OSINT investigations, this article should draw your attention to where you should start, however, the topic of digital privacy is more complicated and intercept other subjects like anonymity, cryptography and steganography in addition to best practices when using social networking sites. For expert computer forensics investigators, this article should enrich their thinking about possible places where data can be found when investigating previous suspect computer usage.
Additional Reading
- Author Book *Digital Privacy and Security Using Windows: A Practical Guide* and Defense 1st Edition, Publisher: Apress; 1 edition, ISBN-10: 1484227980
ISBN-13: 978-1484227985 - Author Book Open Source Intelligence Methods and Tools: A Practical Guide to Online Intelligence, Publisher: Apress; 1 edition, ISBN 978-1-4842-3212-5 By Nihad A. Hassan
About The Author: Nihad A. Hassan (@DarknessGate) is an independent information security consultant, digital forensics and cybersecurity expert, online
blogger, and book author. He has been actively conducting research on different areas of information security for more than a decade. His current work focuses on cyber OSINT, digital forensics, antiforensics techniques and digital privacy. Nihad is the author of a number of books on digital forensics, open source intelligence, digital security, ransomware and cybersecurity.