DDoS Boss
Learn about the power and strength of botnet driven DDoS attacks with DDoS boss Ryan Jackson, formerly leader of the New Worlds Hackers Group.

As the former leader of the New World Hackers group, I once had the power to decide who would feel the power of a 1 Terabit/s DDoS botnet attack. With DDoS attack volumes rising, hackers often refer to “low and slow stealthy offensives" which allow thousands of onlookers to witness the strength and power of a particular hacker group, in this case my old hacker group. New World Hackers were responsible for taking down XBOX website, Donald Trump sites, and the BBC website using botnet powered DDoS attacks of this size and strength.
If you want to learn more about DDoS botnets, check out this excellent Cloudflare resource which outlines and educates around the subject.
DDoS Attacks are on the verge of expansion. With more than 200,000 attacks occurring each year, an ever increasing number of websites & servers are falling victim to such cyber attacks and we are seeing botnets leveraged to further accelerate and boost the power of these attacks. The Athena botnet was discovered by a New World Hackers member known as 'Prophet' and it infected over 100,000 devices in Eastern Asia. This is nothing compared to the size of the attacks that occur against cooperative banks, and wide-spread mobile networks.
With botnets consisting of hundreds of thousands of PC's, Smart TV's and mobile devices, a botnet of large enough size could hold a dynamic carrier such as AT&T offline for a long period of time. The New World Hackers used such attacks to take down large social media sites and insecure offshore government agency websites in order to spread Anonymous propaganda. I saw hundreds of Anonymous supporters engaged in online riots, openly guided by Twitter accounts like @YourAnonNews & @YourAnonCentral and it was a glorious campaign of madness.
The most commonly used attack methods being used were DNS, NTP, SSDP, CLDAP, Chargen and other protocols used to maximize the scalability of attacks.
An attack method known as 'JSBypass' completely destroys websites due to java script errors and thousands of websites were forced to show a 403 error or were subject to defacement during the Anonymous riots. For many attackers DDoSing a website is a way of highlighting security faults and most of the time attackers choose a specific application rather than a whole website. App developers are now beginning to code end-to-end encrypted applications to prevent such these attacks.
But if you have a botnet, Wireshark, and XSS knowledge, you are able to infiltrate multiple versions of software applications without the developers knowledge in order to infiltrate VPS servers or gather information without permission. Hackers will even go as far as DDoSing a website after they have breached the software, or database in which the files were securely stored.
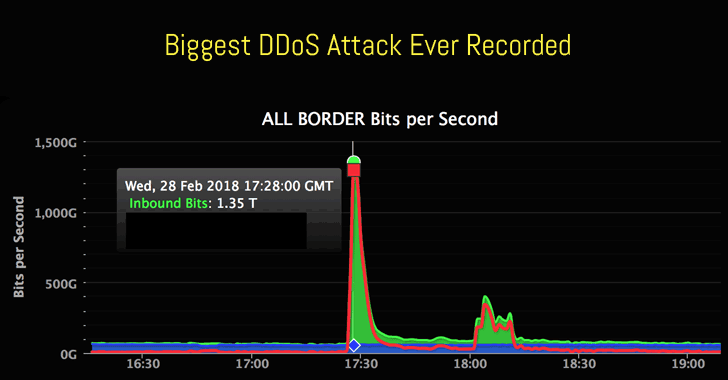
When you see DDoS attacks this big, the only groups capable of withstanding them are Google & Cloudflare. Cloudflare had to open up the 1.1.1.1 DNS which reflects the enormous amount of traffic throughout that day. Most of these attacks were coming from Eastern Asia according to map.norsecorp.com.
The only difference between CFBypass and JSBypass is that CFBypass routes through cache whereas JSBypass routes though javascript. This leaves hackers a 50/50 chance of taking down a website and closing the gate when it comes to unexpected website errors.
DDoS specialists Sucuri is a great choice if you are looking to protect your infrastructure and website against these kinds of attacks. Without a doubt your security is a risk if you do not proactively protect against DDoS attacks and it is best to get protected, in front and ahead of these attacks before they draw attention to your poor security practices.


