Hacking Is NOT A Crime! (Part 1)
Mars Groves spoke to the founding team over at HINAC to find out about their mission and what makes them tick.

Hacking Is NOT A Crime (@hacknotcrime on Twitter) is a non-profit organization founded in 2018 at @BSidesDFW by cybersecurity leaders Bryan McAninch (@bryanmcaninch), Chloé Messdaghi (@chloemessdaghi), and Phillip Wylie (@PhillipWylie) who, along with the rest of the HINAC team, work to build a safer world for information security researchers.
I sat down and interviewed the HINAC leadership speaking to both Bryan McAninch and Phillip Wylie who told me the never-before-revealed history and roots of Hacking Is Not A Crime, diving deep into the heart and soul of their mission and getting up-close-and-personal with the hacker issues that matter to them.
I also speak to the world-renowned hacker and BISO, Alyssa Miller (@AlyssaM_InfoSec), the first hacker sent to prison in Uruguay, Alberto Daniel Hill (@ADanielHill) and Secjuice founder Guise Bule (@guisebule) for their perspective.
My choice was deliberate and crucial in gaining perspectives from two opposite views: the corporate business standpoint vs. the security researcher's standpoint, or more specifically, the security researcher who is facing legal action taken against them over disclosing a vulnerability that was done in good-faith.
Because I recognized how important the mission of Hacking Is NOT A Crime is, I decided to talk to a special guest who is not affiliated with Hacking Is NOT A Crime, the excellent data and privacy lawyer @PrivacyLawyerD who was delighted to discuss the legal issues that security researchers may face concerning vulnerability disclosures. Having worked for many years in Washington D.C. in the legal space of the Cybersecurity domain, he was certainly well-qualified to share his personal opinions about how and why businesses treat security researchers poorly.
After peering into the lives of real-life hackers engaged in with the corporate and legal world, I was truly grateful for the experience of being enlightened by their insights and personal stories. I was educated in a profound way about the true meaning of the hacker way of life, and the perspective of the business world which gave me a greater understanding into why some businesses automatically attack security researchers.
The History of Hacking Is NOT A Crime (HINAC)
I interviewed the co-founder of Hacking Is NOT A Crime (HINAC), Bryan McAninch (@bryanmcaninch), and asked him about the history of HINAC and how it all got started. He willingly and openly shared the details of the never-before-revealed history and roots of the birthing of Hacking Is NOT A Crime.

Q: Why did you start HINAC? What sparked the idea?
Bryan McAninch: I grew up skateboarding in the 80's. Skateboarding is Not a Crime stickers was on my stickers because police would harass me as a kid for skateboarding. One night, the founder of the Dallas Hackers Association (@DHAhole), was having beers with old school hackers as myself. They talked about the public perception of how hackers are seen as bad.
So, they decided hacking is not a crime just like skateboarding is not a crime. That is when the idea came to create Hacking is NOT A Crime, and was when I co-founded HINAC with Chloe Messaghdhi. So for DEFCON 26, I made Hacking is NOT A Crime stickers, and 500 of those were handed out. The following year, I gave out 5,000 of those stickers at DEFCON 27 in 2019! I didn’t go to a single talk. I just gave out stickers! It was nice! In DEFCON 28, we had 1,500 followers around that time. Now we have 14,600 followers today.
Q: When HINAC first came out, was there a lot of support?
Bryan McAninch: I had a lot of friends doing BSides organizing in Dallas, San Antonio, and Austin. Our original intent was to sell stickers for $2-$3 or whatever amount people wanted to donate, and donate it to non-profit hacker organizations. 99.99% of people agreed to it. It resonated well with them.
It wasn't until last year in 2020 when we gained media attention outside of the hacker community. Some of our growth was due to outreach from Chloe Messaghdhi. I've done a lot of talks and had sponsorships as well. Up until recently, we've had attractors to our message. Most people felt a personal thing with the brand as far as the malicious part of it.
Let's take a look at the original inspiration, the Skateboarding Is NOT A Crime sticker.

Now check out the new take on the original inspiration for the Hacking is NOT A Crime sticker. I'm loving it! 😊

The Mission
I asked HINAC managing director, Phillip Wylie (@PhillipWylie), who is also the host of The Hacker Maker podcast streaming on Twitch, founder of The Pwn School Project, co-author of The Pentester Blueprint, ethical hacker and web application teacher at Dallas College, mentor, and accomplished penetration tester—gosh, what can't this man do?—on what he feels about the mission of HINAC.
Hacking Is NOT A Crime (@hacknotcrime) advocates, Alyssa Miller (@AlyssaM_InfoSec), and Daniel Alberto Hill (@ADanielHill) also shared what the HINAC mission means to them, and how it is dear to their hearts.
The mission statement of Hacking Is NOT A Crime is:
Hacking is NOT a Crime a non-profit organization advocating global policy reform to recognize and safeguard hacker rights. We seek to raise awareness about the pejorative use of the terms "hacker" and "hacking" throughout the media and popular culture. Specifically, the negative stereotype with which the terms are so often associated. Hackers are often vilified and portrayed as unethical individuals with malicious intent. Because of this, many hackers refrain from publicly disclosing privacy and security vulnerabilities they discover for fear of legal retaliation. Consequently, this is creating an increasingly hostile digital frontier for everyone. The only viable remedy is to provide safeguards for hackers conducting good-faith privacy and security research.
Q: What do you feel is important about HINAC’s mission?

Phillip Wylie: The important part is the awareness of the community to the media and public sources, and to let 'em know it’s a skill and not exactly an illegal skill. Just like lockpicking. One of the main missions and reasons I'm passionate about it is because I'm an ethical hacker and I teach ethical hacking. I let you know how to hack when you have permission only. It’s a legitimate skillset.
The media tries to make it sound good and hypes “hacker" this and that instead of "cybercriminal.” If journalists add more detail, it makes the pieces better. At the same time, you can’t blame them for making hackers look like bad guys because “hackers are bad guys” got repeated to them. Those are things they learn from others. We can’t really blame the media. It’s back to the awareness. You can’t blame them.
At the end of the day, it’s all about awareness. Awareness is most important. The real need is to find people outside of the InfoSec community who don't work in tech and educate them about hackers and hacking.

Alyssa Miller: From my perspective, I think raising awareness is crucial if we want to continue to get better at cybersecurity. Certainly, it's become better and more mainstream knowledge that hackers are employed in organizations around the globe to help cybersecurity weaknesses and leverage them. The pejorative use of the terms hacker and imagery around it like dark hoodies and spaceless figures—all it does is serve to continually make people afraid of hackers. So, creating a fear and negative impressions of hackers kind of counteracts all the good that hackers do.
Q: I read the Conduct page on the HINC website where it says the terms "white hat" and "black hat" are inappropriate.
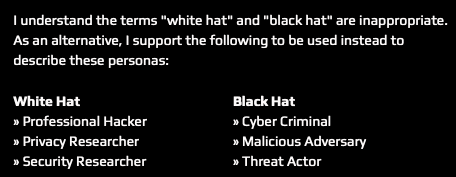
Since the terms "white hat" and "black hat" are widely used in the Cybersecurity community, can you elaborate on why they are inappropriate to anyone who’s reading this?
Bryan McAninch: That kind of stems from GitHub, they faced stuff with the master and slave thing, and deemed it as inappropriate. They felt the same with white hat and black hat. The terminology originated from the InfoSec community, not the hacker community.
It’s not very fitting in our modern era. We want to be as inclusive as possible.
Age, gender identity, race, ethnicity, sexual orientation etc—we want to be as inclusive as possible because we believe diversity breeds innovation.
Q: Why is HINAC's mission important to you?

Guise Bule: HINAC's mission is important because HINAC is one of the few non-profit organizations working on this problem from a global policy perspective, working directly with the community, the legal industry and the corporate world to help move the needle on this issue. I became a HINAC advocate and enrolled Secjuice as a HINAC affiliate because their mission immediately resonated with us as a group and perfectly aligned with our position on responsible disclosure.
We have hundreds of security researchers at Secjuice and a lot of the time I am the first port of call when they get into trouble, because of this I have been involved in responsibility disclosures that have gone bad. Two recent incidents spring to mind, the first incident involved the FBI, the police and violence against a security researcher, a second involved legal action taken against a security researcher engaged in good faith disclosure. Both of these incidents could have been avoided if the organizations involved were a little more cyber aware and did not automatically assume that the researchers responsibly disclosing a vulnerability to them were trying to extort them.
HINAC works to mitigate against this problem by working to solve the root cause, the negative perception most businesses and the general public have of hackers, that is why their work is important, and that is why their mission is one worth supporting.

Alberto Daniel Hill: It is important to me because I have had an experience in my country in Uruguay where I reported a security problem in the system of a medical provider. I found it once. I reported it. I found it twice. I reported it. Then, the medical provider was hacked and I was accused of committing the crime, and I was sent to prison.
Basically, it was the incompetence of the media and police—they were unable to completely handle a case involving high-technology somehow. They couldn't understand it. The media with the press releases painted an image of me as a hacker who was a cyber terrorist. They didn't see me the hacker as a person, but said I used my knowledge of computers in order to commit crimes because of all the devices they found here. I was treated as a cyber terrorist in my country.
I loved computers since I was a child. I collected devices of all kinds since I was a kid and all hacking tools that were available to me, but they're any tool that security researchers would have, in order to do research and understand how things work. It’s the curiosity of how things work. We are not bad guys who commit crimes. We are the curious good guys. Think of it like this. It's like a bad guy using a gun to rob a bank, but a good guy like a cop uses the same gun to stop the crime. Same gun, but different purpose.
Hackers != Criminals
Hacking Is NOT A Crime states that hackers are not criminals, but criminals are criminals. Read that again. I already know what some of you are thinking. "But hackers can be good, and hackers can be bad, can't they? What do you mean hackers are not criminals? Are you saying that none of them are criminals at all?"
This may confuse some people. So to gain more clarity, I asked the co-founder of Hacking is NOT A Crime, Bryan McAninch, who is also the founder of Prevade Cybersecurity (@prevadellc), for his answer to my question.
Q: Are all hackers the same?
Bryan McAninch: The answer can get a little nuanced. The Hacking Is NOT A Crime thing really starting off with the purpose: We want to advocate global policy reform to safeguard hacker rights, giving security privacy researchers the right to conduct their research without fear of legal retaliation, because they don’t release the shit they find sometimes due to this crap. And if nation-states exploit something that is not well known, it can be an issue.
When we say Hacking Is NOT A Crime, we do mean it’s NOT a crime! Number one, it’s a bit of guerrilla marketing campaign. It gets conversations starting. When you drill down a little bit deeper, it means all hackers are implicitly ethical. The word "ethical" as a pre-fix to "hacker" just doesn't make sense because we don't do that with our doctors or dentists. We already know they're ethical so there is no need for the prefix. It's like saying 'I'm going to see my ethical doctor' or 'I'm going to see my ethical dentist.' That sounds weird. We believe all hackers are good. All hackers are implicitly ethical.
We focus on ethical intent. Intent being a paramount within our movement. Implicitly ethical. Then there is ethical and legal. Ethical and illegal. It can get a bit nuanced.
Q: How do you think we can change the image of a hacker into a more positive one? Do you even think it’s possible for us to view them as heroes?
Phillip Wylie: I think it is possible. It’s like a lot of other things. We need to start sharing stories that are positive. Like hackers finding solutions to fix things… or finding vulnerabilities that can lead to data breaches. People focus too much on the negative. The positive needs much attention as the negative does. Start educating people younger, children in school about these things. Teach them to be secure, and teach them what hackers do and bring awareness there. Sometimes, when they’re older it’s harder.
What is a Hacker?
Phillip Wylie: The original term for "hacker" was related to programming, inventors, and people who could take out devices and enhance those capabilities. People like Steve Wozniak were the original hackers. The hacker mindset really relates to people who can take things apart and make them better. There are even hackathons that have nothing to do with coding.
Bryan McAninch: When I was 8, my grandfather was a middle school science and math teacher, who sat me in front of an Apple IIe and gave me a Choose Your Own Adventure book in 1984. I was hooked on technological concepts ever since, and looking back at it, I came to the conclusion that being a hacker is an identity.

It's something I have been my entire life. My friend Stök Fredrik (@stokfredrik) said, "Don't learn to hack. Hack to learn," and that's how I think. How I think, how I tweak things, how I am curious... that's the hacker mindset.
In the Dot Com era in the 90's, hackers had to go out and make a living at some point. Some chose it as a hobby, and others chose it as a lifestyle. It was a right opportunity to make a killer living doing what I love to do in the 90's.
Back then, it was mostly defense, I-want-to-stop-the-bad-guys stuff. I've been coding since age 8. But pen testing back then is not anything like what it is today right? As time evolved, the InfoSec community has become “less hackerish” and more policy-oriented (GRC type of stuff). The hacker and InfoSec communities have a different vibe to them.
I identify with the hacker community more personality-wise. Goofball, corny, dark-humored type of stuff. The InfoSec community is more business-oriented in an office setting, and are a little bit more corporate type of people. It's not bad, everyone has to make a living. I have some great friends there.
Being a hacker is more of an identity for me. You’re either a “hacker” or you’re not. You either think that way or you don’t. I think it’s possible to think like a hacker or do what they do, but it’s a lot more difficult for you if you don’t already think that way. It’ll just naturally be more difficult for you to think that way. It’s like asking, "Can you think like a dog?" I know dogs like to eat, sleep, but I’m not a dog. So I don’t know how a dog feels or a cat, or whatever else.
Alyssa Miller: My personal view on it is that hackers are really creative folks who like to deconstruct things, figure out how they work, and make them all better. It’s all based on passion and wanting to see technology grow and improve. I’ve got a tattoo on my back shoulder that says, "Artists and inventors NOT criminals and freaks." I got it from Jayson Street (@jaysonstreet) when he gave a keynote speech during GrrCON in 2014. It really sums up the approach that people see people as that... They want to see how things work.

Alberto Daniel Hill: Being a hacker is an honor. It’s a title that you can't buy or get with your studies or experience. You become a hacker when other people in the circle start calling you a hacker, and it’s an honor that makes me proud. My mother only understood the term hacker as negative in related to the crime. Being a hacker is actually something that I'm proud of.
In Spanish, the definition of hacker used to be a pirate who used technology to enter systems without authorization to hack a system. A few years ago, a hacker named Chema Alonso was able to petition the Real Academia de Española (RAE) who was in charge of definitions of the Spanish dictionary, to add another meaning of hacker. So now, the definition of hacker in the Spanish dictionary is either a pirate or a person with high skills who can identify problems and improve systems. The definition evolved in both kinds of hackers, thanks to Chema Alonso.
The general society has a misconception that hacker means criminal. It does not. Hacking Is NOT A Crime is very important to me because I want to change the meaning of the word "hacker." The message I want to deliver is very important.
I want people to understand that both good and bad hackers are a part of an ecosystem where we share the same cyber space, and we share our knowledge and tools in different ways depending upon our ethics, whereas, someone in society may use the knowledge for good or for bad. We have to make that clear for the people, but it’s not an easy task.
I think the respect among all hackers is something in common among all of us. So that’s why I'm a part of this organization, and that's why it's important because I have suffered a high level by the media. I was on the cover of the newspaper on my country as the first hacker sent to prison in my country.
When I was introduced to Hacking Is NOT A Crime, it meant a lot to me. It’s amazing!
And it’s really sad that people are so ignorant, and they can only see one meaning of the word hacker and link it to something negative, but it’s incredible they want to talk about it. I really don't want to miss any opportunity I have to explain and express all things involved with this, and correct the perception of the people in general of this. So it’s important for me—the information and the facts—that hackers are not bad, and we are people like everybody else. We have good people and bad people, and people who do certain things that are questionable… and there are others who are not.
Becoming A HINAC Advocate
I asked the co-founder of HINAC, Bryan McAninch on how to become a Hacking Is NOT A Crime (@hacknotcrime) advocate, and here was his answer.
Bryan McAninch: We don’t have hard qualifiers such as requiring certifications, do IT, or anything like that. Anyone can become an advocate. But when we started the advocacy concept, we were a small group of people, and everyone had a web of trust. The web of trust expanded as they grew. There’s a certain balance of quality control. There’s a high likelihood that someone will infiltrate us or become a mole since we are becoming bigger. So now, we are only accepting advocates by “referral only” now.
It’s more of a case of “Do you know this person?” It’s about the chain of trust. Black Lives Matters got infiltrated. Even the Occupy Wallstreet movement and others. Any organization that becomes highly visible and are activists tend to get people that are not one. So we just want to weed that out. We've been accused of gatekeeping, but that’s absolutely not the case. Some people who are advocates have only been in InfoSec for 2-3 years. We want to be as inclusive as possible, with a balance of a certain level of secure quality controls.
So, there you have it! You can become an advocate by referral only from someone who is already a @hacknotcrime advocate, simply because HINAC wants to maintain their web of trust. Who could blame them?
Why Do People Become Advocates?
I wanted to know how @hacknotcrime advocates felt about being one and why they became one, so I asked Alyssa Mille, Alberto Daniel Hill and Guise Bule how they felt about being advocates. They were all passionate!
Alyssa Miller: The reason I got involved is because it’s something I feel strongly about, a cause I feel strongly about. We are very reliant to how hackers help us. I’ve been there as a pentester for many years. I’ve been a hacker all my life. I’ve seen the damage that can be done with that problematic view of hackers, so when Bryan asked me to be an advocate it made perfect sense as it’s something that needs to be addressed. Thankfully, I don’t have a story with legal action against me.
The vulnerabilities I've typically discovered as a consultant or was hired to test—to that end though—some time back when I was working for large financial services company, I recall a security researcher discovering a vulnerability found and the CIO freaked out. I had to talk the CIO off the ledge and needed to sit down with him and tell him that we should be thanking him for disclosing it. If we go against him, it’s sending the absolutely wrong message, adversarial.
Guise Bule: I became a HINAC advocate because my work at Secjuice involves volunteering with our 200+ members, most of whom are security researchers, and over the last few years I have seen the same sort of incidents happening repeatedly. I keep seeing organizations react badly when a security researcher tries to tell them about a security vulnerability, often taking jerk legal action against them. It's an appalling practice used against security researchers acting in good faith and the only real way to mitigate against it is to raise awareness of the good work that security researchers do and work to create a safer space for them to operate in. The work Bryan, Chloé and Phillip do over at HINAC is important, essential and appreciated by the whole community and the whole team here at Secjuice, I signed up to help them any way I can because I believe in the mission.
Alberto Daniel Hill: I was honored by the founder of Hacking Is NOT A Crime who contacted me to be a part of the organization where you normally enter only by invitation or another member. It was gratifying to be recognized for what I lived through and my efforts, and to try to clarify to society the meaning and misconception of the term "hacker", "hacking", and the meaning that the media/pop culture had given to those words.
When I did a podcast with Darknet Diaries and gave 40 minutes of my life talking to chat, it opened me to the doors of the world to tell my story. By now, half a million have listened to my story. The reviews began to boom. Now, it’s the best hacking podcast in the world. People who contact me in the hacker community and InfoSec give me support and condemn the situation that I had to live through. Being able to get support from people in the industry is something priceless that means a lot to me.
Here in Uruguay, I have all the hate from the police and system treating me like I was a cyber terrorist. So getting so much understanding from people who really understand the technologies who understand crime and things like that is comforting.
I have suffered health and mental health issues, which is common in the hacking world. Mental health issues is very common which should be of concern for many people trying to create awareness of that.
Because it’s a field of work that implies a lot of pressure and responsibility, and the work of a hacker involves endless curiosity and can be obsessive in some ways, it can affect your mental health.
*If you haven't learned about Alberto Daniel Hill's story, I strongly urge you to hear or read about it on Darknet Diaries for a more detailed account on how he became the first hacker to go to prison in Uruguay!
How Can You Volunteer for HINAC
Bryan shared how we can volunteer for Hacking Is NOT A Crime.
"Volunteers are a bit more engaged. It’s a different type and level of commitment.
Everyone at HINAC are volunteering. Clearly, they’re volunteering. You don’t need to pay membership dues, pass an entrance exam, certs etc… you promote the message out of goodwill.
When it comes to physical volunteers, Chloe and I volunteer. We mostly do marketing stuff like designing stickers and art, stuff like that. Investigatorchic (@investigatorchi) deals with project management. We have people helping with social media management.
Some advocates are volunteers. You can become an advocate then volunteer. As we continue to grow, we may be reaching into international markets. We have at least 91 advocates in 6 continents and 22 countries. For horizontal growth, we setting up local and regional chapters to build momentum there. Each country has a CFA policy reform type of stuff. Vertically, we’ll have to start delegating stuff. As an example, a couple of volunteers are under marketing.
Volunteering is not open to the public right now, but after COVID-19 we may have some outreach volunteering opportunities available.
Last year, I volunteered for Habitat of Humanity with a group of hackers doing local community outreach and more. Hackers were hacking food at a pantry and organizing furniture on the ground with our boots on. We wanted to show we are actively helping the community as well. We’re getting there. It’s just a timing thing. Hopefully, COVID-19 will go away."
Vulnerability Disclosure Resources
For security researchers who need guidance or help in responsibly disclosing vulnerabilities they have found, you can reach out to Hacking Is NOT A Crime's partner, Disclose IO.
Bryan McAninch shares, "Disclose IO (@disclose_io) is another non-profit organization, co-founded by Casey Ellis (@caseyjohnellis), also chairman and founder of Bugcrowd (@Bugcrowd). They have great VDP (vulnerable disclosure policy).
They put you in touch with the big guys or people who can guide you with your situation if you want to avoid legal issues. An example of this is when a security researcher found vulnerabilities in Gardzilla's camera, and was placed in touch with Rapid7 (@Rapid7) to disclose the vulnerability by proxy.
When a security researcher discloses a vulnerability by proxy with an organization like Rapid7, it has a bigger name and reputation, and isn't some independent researcher. This can be safer. The basic premise of legal retaliation is whether it’s deemed authorized or unauthorized access.
When in doubt ask about. If you’re not sure if you’re authorized to do it, ask about it and get written permission. It’s better to be on the safe side with legal permission. Asking for forgiveness rather than permission doesn’t always work well. If you did found something, but you don’t know how the exploit you found could be interpreted, reach out to Disclosure IO for guidance or ask them to partner you with an organization by proxy such as Rapid7 etc."
Phillip Wylie adds, "I recommend for them to go to disclose.io and get guidance there, and reach out to the Bug Bounty companies on how to disclose it. They deal with those laws all the time."
*To learn more as a security researcher on how to properly handle legalities regarding vulnerability disclosures, please read part 2 of this Hacking Is NOT A Crime series to gain further in-depth information.
Summary
There are multiple ways to support HINAC by purchasing stickers here or by donating to DonorBox, Patreon, or their GoFundMe. You can periodically subscribe on DonorBox and Patreon as well. Currently, there are no opportunities to physically volunteer for HINAC until further notice post-COVID19. For security researchers who need guidance on how to disclose a vulnerability found, you can reach out to HINAC's partner, Disclose IO, and tell them that HINAC sent you.
👉Last but not least, you can follow the interviewees on Twitter and show them support as well: Alyssa Miller (@AlyssaM_InfoSec), Bryan McAninch (@bryanmcaninch), Phillip Wylie (@PhillipWylie), Alberto Daniel Hill (@ADanielHill), D (@PrivacyLawyerD).
*Note: Because I want to bring focus and attention on the LEGAL issues that security researchers may face when disclosing a vulnerability that are absolutely critical for every security researcher to know, I have decided to divide this article into a two-part series. Part two of this article solely focuses on legal issues stemming around vulnerability disclosures—the important serious stuff.
👉 P.S. If you enjoyed this article, follow me on Twitter @marsgroves_
☕️ You can also buy me a coffee to show some support. ♥️
