How & Why You Should Remove Yourself From Windows Local Admin
Members of the admin club are allowed to do anything on a system, but you do not need to wield these godly powers for everyday browsing.

The first question people ask me when they find out I work in cyber security is "How do I stop myself from getting hacked?" The answer is often too lengthy to explain in the pub so, in this series of posts I hope to highlight changes you can make to your home computer in order to increase its security. Bear in mind we are not trying to keep out nation states or targeted well funded attackers. We are instead aiming to keep out the common hacker. Browser exploits, malvertising, exploit kits, account take over and commodity malware.
In this part of the series we will be looking at removing Windows local administrator rights in order to operate day to day with as little privileges as possible. This is known as the Least Privilege Model.
What Are Administrative Rights Anyway?
Windows controls who can do what on a system via groups. Your user account belongs to one or more groups each granting you permission to perform certain actions. Here's a list of these groups, the names are (hopefully) self explanatory:
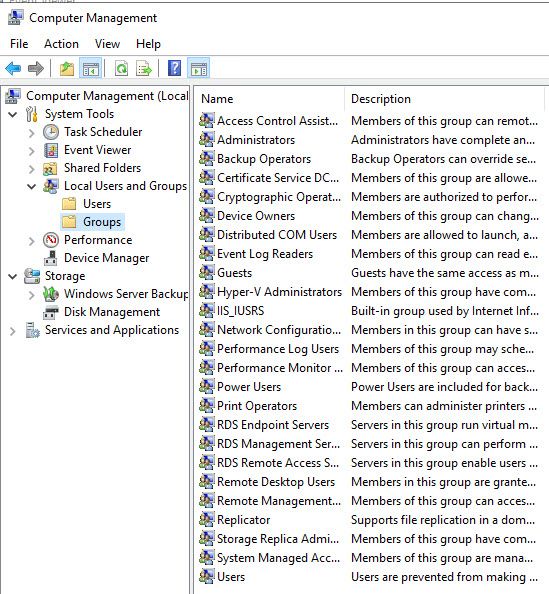
Why Would I Want To Revoke My Privilege's?
The most powerful group a regular user can be a member of is, you guessed it, the Administrators. Members of this prestigious club are allowed to do almost anything on the system including but not limited to installing software, taking control of files and fiddling with important settings. You do not need to wield these godly powers for every day browsing, checking your emails, banking and scrolling Facebook.
It's like putting on a white tuxedo for a dog walk through a forest during winter. If malicious code is executed on a system it will assume the identity of the user it was executed under. In your case being a proud tuxedo wearing member of the admins group, the malware assumes high administrator privileges and wreaks havoc, installing persistence mechanisms and accessing sensitive areas of the file system that a normal user account would not be able to. Before you know it your a member of a botnet and being forced to send spam eMails for a hacker in his parents basement.
Please don't take my word for it, look at these resources from world renowned cyber security experts who advise controlling administrative access in some form or another:
Won't I Get Bombarded With Password Prompts All Day?
A common argument against relinquishing administrative privileges is the fear of constant UAC prompts bogging down productivity. Unless you are changing an important setting or installing system wide software you will not see a UAC prompt. If you are a Windows super god who for some reason makes system changes constantly throughout the day, okay, this configuration isn't for you, be careful out there, but for the average user it won't be a problem. They will not notice the lack of powerful system wide privileges.
Okay I Give In, How Do I Surrender My Permissions?
We won't actually be removing your permissions entirely, we will just be moving them elsewhere for use as and when they are required. Kind of like only taking a hammer from the toolbox when you need to bang in a nail, instead of carrying one around all day.
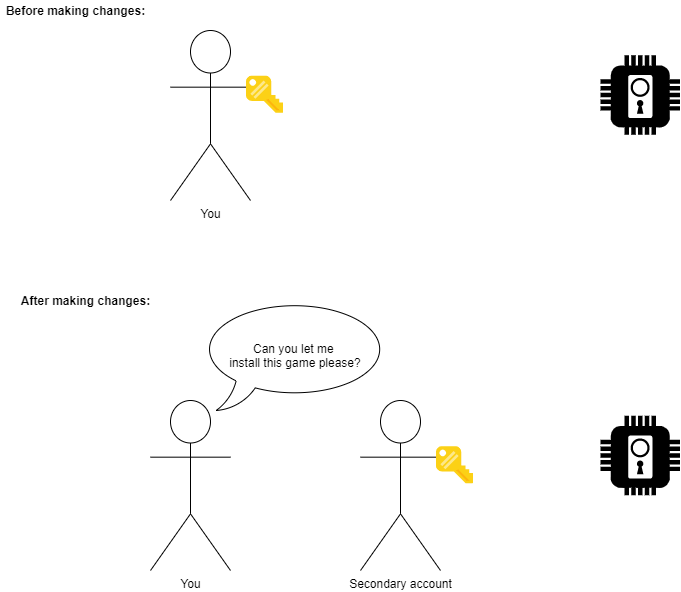
We will be handing our white tuxedo and administrators badge to another account and then placing ourselves into the standard users group instead so that in the event we do get infected with malware its abilities and access will be limited or in some cases unable to execute at all. If we do need to install software or change a setting, we can do so by assuming the privileges of the new administrator account. For the visual learners among us, below is an accurate, technical illustration that Bill Gates has personally approved:
No, I Really Give In. How Do I Remove My Administrators Access?
Firstly, it's important you follow these steps to the letter and in order. Missing a step could be very bad, you could lock yourself out of your own computer and then id have to write a guide on how to remove the administrator password or something. Please be careful and again, follow the steps closely.
1) Add yourself to the Users group.
Before we go any further we need to add our current user to the users group (crazy I know) because if we point blank remove ourselves from the administrators group we wont belong to any groups and therefore have no rights to the system, casting ourselves into oblivion.
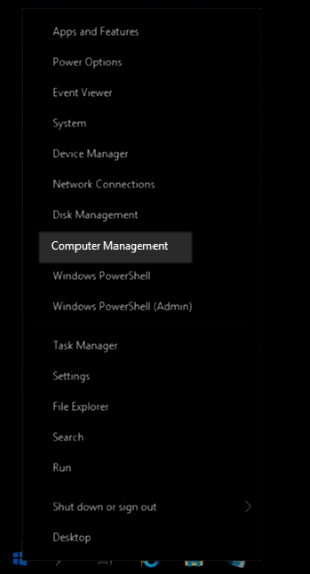
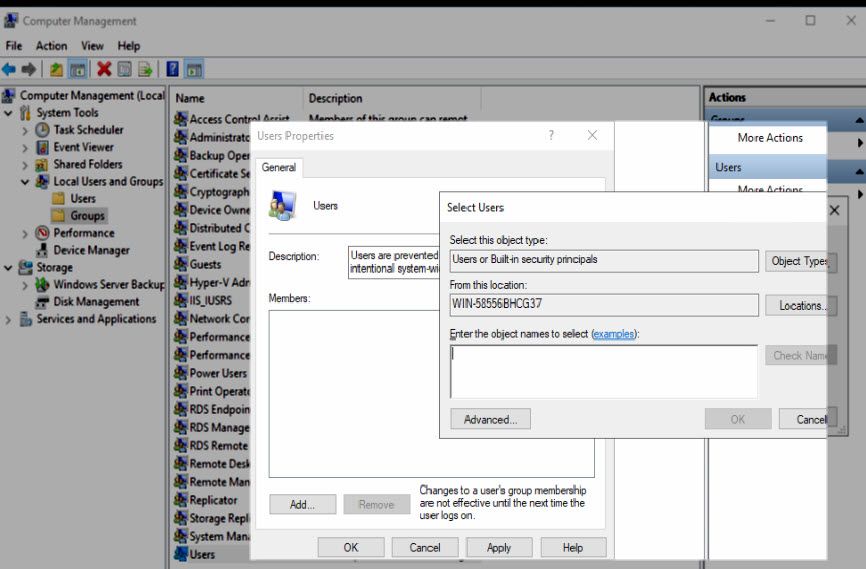
To grant yourself user permissions right click on the start button and open Computer Management:
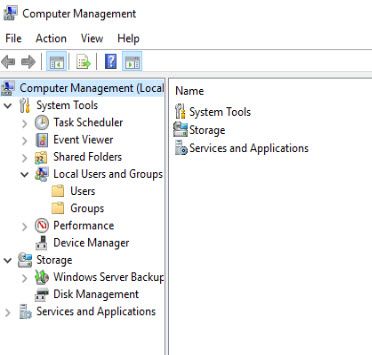
In the newly opened window use the left hand navigation pane to select; Local users and groups > groups:
On the next screen double click the users group and add yourself there. If you are not sure what your username is use the command whoami in cmd to find it.
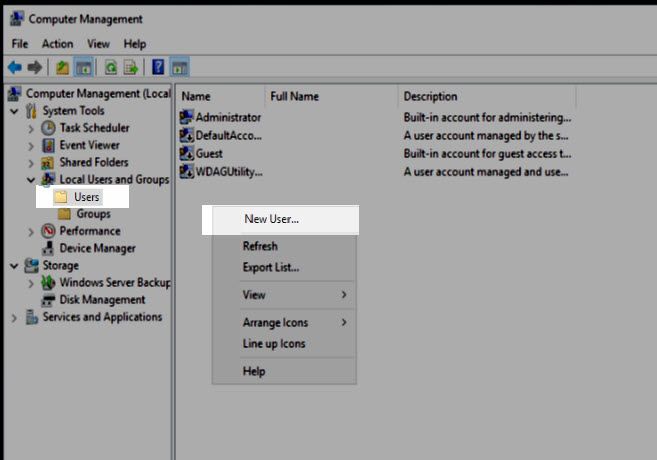
2) Creating a new account
Now we will provision the account you will use when performing administrative actions. Go back to the users folder and right click to create a new user.
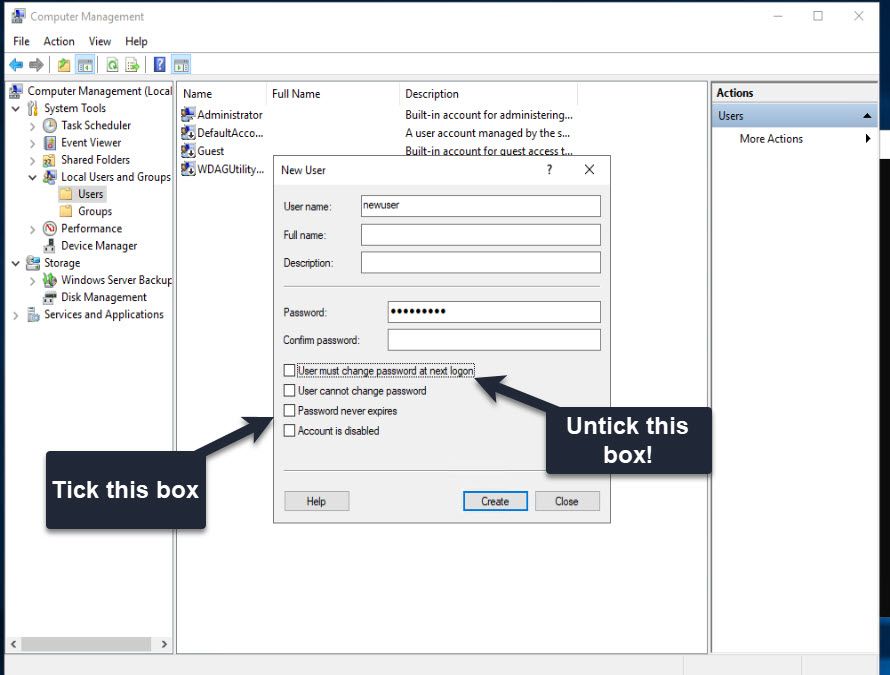
In the next dialog fill the information for your new user. Call it whatever you like but make it memorable. You should consider writing down the password and storing it somewhere safe, just incase you forget it.
Its also important to untick User must change password at next logon AND tick Password never expires.
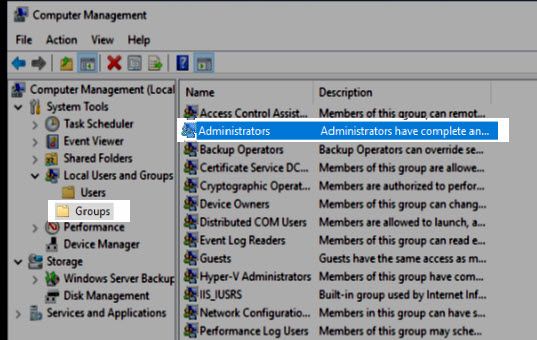
3) Setting the administrators group
Now we will be adding your new user to the administrators group and removing your original account which completes the task.
Head back to the Groups folder but this time double click the Administrators group.
In the new window add your newly created account and select apply. It's important to add your new account first so there is never a point where you don't have administrative access.
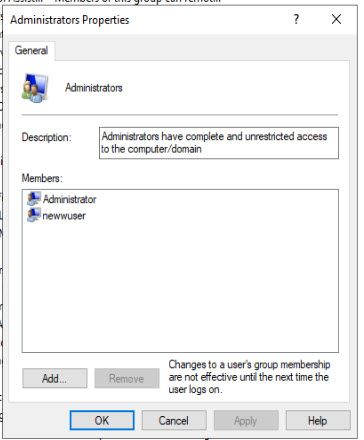
Now remove all other accounts in the administrators group apart from your new account. Be sure to select apply when done.
The group should look like this:
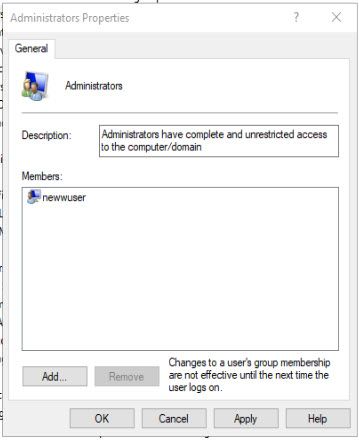
Now what?
From this point onwards every time you need to elevate your privileges, Windows will prompt you for credentials. When it does you should enter your new account credentials, therefore temporarily elevating your permissions for that particular action. The dialogue will look similar to this:

You may need to select Use A different account.
Thank you for taking the time to read this post, if you disagree with my thought process or in someway find this advice incorrect id be interested in hearing from you @secprentice and will endeavour to update the article accordingly.
About The Art Used In This Article
The awesome artwork used in this article is the work of Zaki Abdelmounim. He is a 25-year-old Moroccan 3D generalist living in Qatar and working in the TV industry. This project is called Hardcoding:Redshift Study, Zaki started the project after watching the movie Chappie, he really liked the concept of the command chair that was done by George Hull, and wanted to recreate something similar in 3D for the sake of practice and fun, resulting in what we think is the worlds best hacker desk design. Learn more about this project here.


