How To Train Your Social Team To Deal With Security Researchers
A guide for leaders who want to train their social media teams to deal with researchers reporting cyber security issues.

This article is a guide for business leaders who need to train their social media teams to properly deal with security researchers reporting vulnerabilities. Over the last few years I have seen these interactions botched so badly that they sometimes burst into flames, burning your brand, social media presence and team in the process.
The Hills Are Alive with The Hum Of Scanners
In 2019 the internet is alive with security researchers scanning the internet with tools like Censys and Shodan to find vulnerable servers and devices which are exposed to the internet. They use these tools to automate the search for your stuff, the stuff that you put on the internet and which you did not secure properly.
If you put stuff on the internet and fail to properly secure it, these automated toolsets will find it one day and alert the researcher, it's just a matter of time. If your online stuff is important enough and the security vulnerability is serious enough, the security researcher will usually reach out and try to contact you.
It is a good thing that a friendly white-hat security researcher found your unsecured stuff online before a black-hat security researcher did. If a black hat found it first you would not be contacted, instead you would see your data on the dark net for sale, or the vulnerability exploited for criminal gain. It could also be sold on through established vulnerability markets like Zerodium or 0dayToday to the highest bidder.
A lot of the time the cyber attacks and data breaches you read about in the news were not caused by fiendishly clever hackers who hacked your secure IT system to get at your stuff, they are caused by your team leaving something unsecured online.
This happens a lot more than you would think, businesses globally have this really bad habit of putting their stuff online without properly securing it and it is only a matter of time before it is discovered. The news is littered with examples of this, like the recent 'data leak' by 63Red which exposed the personal details of its users and who I will use as an example later on in this article. But that is just one example, I see organizations putting their stuff online and fail to secure it all the time.
What Do The Security Researchers Want?
99% of the time they will be trying to tell you that they found some of your stuff online, be it an online data base, a data archive, an app, an insecure web server or some sort of online service which contains an obvious and public facing vulnerability.
They are trying to warn you about it in the hope that you do something about it before somebody who is criminally minded does something about it for you. Most of the time they contact you via social media because you have not made it easy for them to contact you elsewhere, or you ignored their emails in the hope they went away.
If you had a security email address ([email protected]) publicly available on your website, they would be using that to notify you instead. If you had your social media accounts setup to receive direct messages from anyone, they would be using that to contact you instead. Most of the time they have to resort to social media because it is a legitimate point of contact for you when no other point of contact exists, that or you have blatantly ignored their emails and failed to acknowledge them.
They want to warn you and are trying to help and you need to acknowledge that.
How Should You Deal With Security Researchers?
Before considering your next move you should really know what sort of people you are dealing with. If they contact you to warn you they will be white-hat hackers trying to help you, but at the same time they come from a place that has seen it all before, a place where everything is on fire and almost everyone has been burned. So many times before we have seen security researchers threatened with legal action when they try to warn organizations about their security vulnerabilities.
We have seen security researchers attacked, sued, slurred, accused and arrested when they try to tell organizations about their security vulnerabilities, too often do organizations lash out and try to shoot the messenger. So often that we are wary of reporting vulnerabilities and wary of the way an organization will respond.
You have to understand that most of the time your security vulnerability is just another blip that has appeared on the researchers scanner, hardly ever have they 'hacked' you and if they did they would not be trying to warn you about it.
Checkout this guide on how to deal with security researchers who find a hole in your security, when read in combination with this article, it serves as a how-to guide.
In a nutshell, do not treat the researchers like an enemy when they are trying to help, the vast majority of researchers just want you to fix your obvious security issue.
When Public Social Media Is Their Only Point Of Contact
If you have left the security researcher no other choice but to contact you publicly on social media, then that is your fault and not theirs. They are not trying to embarrass you, they are trying to warn you and are probably already frustrated that you made it hard for them. If you are one of those organizations who completely ignores emails from security researchers, or who does not provide clear contact details on your website, you leave them no other choice. How do they know you got the warning?
Nobody is going to ignore a serious vulnerability for long even if you want to and if your only point of contact is Twitter, that is where you will first hear about it.
How To Respond To Researchers On Social Media
This is actually quite simple and based on common courtesy, train your social team to thank the researcher for responsibly disclosing your security vulnerability and take their contact details so that you can follow up if necessary. Assure them that you will forward the disclosure to your IT or security team who can understand it.
It is the same approach that you would take when anyone friendly approached you to warn you of something. "Thank you for that warning, we really appreciate it, how can we contact you in case we need to talk to you more about it?"
Then all you have to do is make sure that the social team passes it to the right people so that they can fix the issue before it impacts your business or customers.
What Not To Do
For gods sake do not belittle, mock, or dismiss the security researchers on twitter like Käthe from T-Mobile did shortly before they suffered a catastrophic data breach.
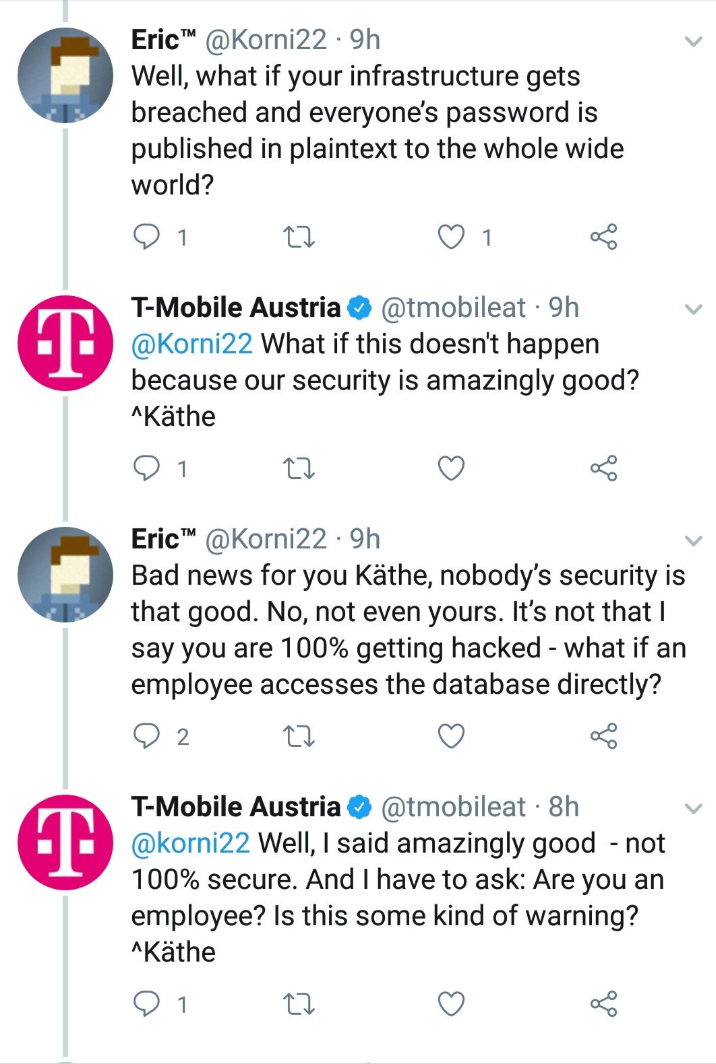
T-Mobile responding like this to a security researcher on social media made them look incompetent, especially when a couple of months later they suffered a huge data breach affecting two million users. It makes them look like complete clowns.
Whatever you do, do not belittle warnings that your security is not up to scratch.
Whatever you do, do not angrily and publicly attack the researcher like 63Red did when security researcher Elliot Anderson told them that their app was wide open.
TL;DR: No lost passwords, no breach of database, no data changed, minor problem fixed. We’re angry by the attempt, FBI notified.https://t.co/v59DExCI0F
— 63red (@63red) March 12, 2019
63Red responded to the vulnerability disclosure by attacking the researcher publicly and accusing him of being a politically motivated hacker and very obviously not having a clue just how insecure their mobile application really was. They also lied to their users and told them that the 'minor problem' had been fixed when it was quite clear to anyone who bothered to look that their application was still wide open for exploitation by anyone who wanted their users personal details. Do not be like 63Red engaging in a very public freakout or Atrient who issue press releases containing a pack of lies attacking the security researchers who were trying to help.
Almost every case of an organization or brand botching the initial contact with a security researcher ends in public ridicule and negative press attention. When you go on the attack it attracts anger from the cybersecurity space and the attention of black hat hackers who just know you are ripe to exploit criminally. You may as well paint a target on your back and ask cybercriminals to hack you.
The Helme-Gibbs Scale Of Response
The graphic below was created by security researchers as a guide to the damage you can cause your brand by botching your response to vulnerability disclosures.
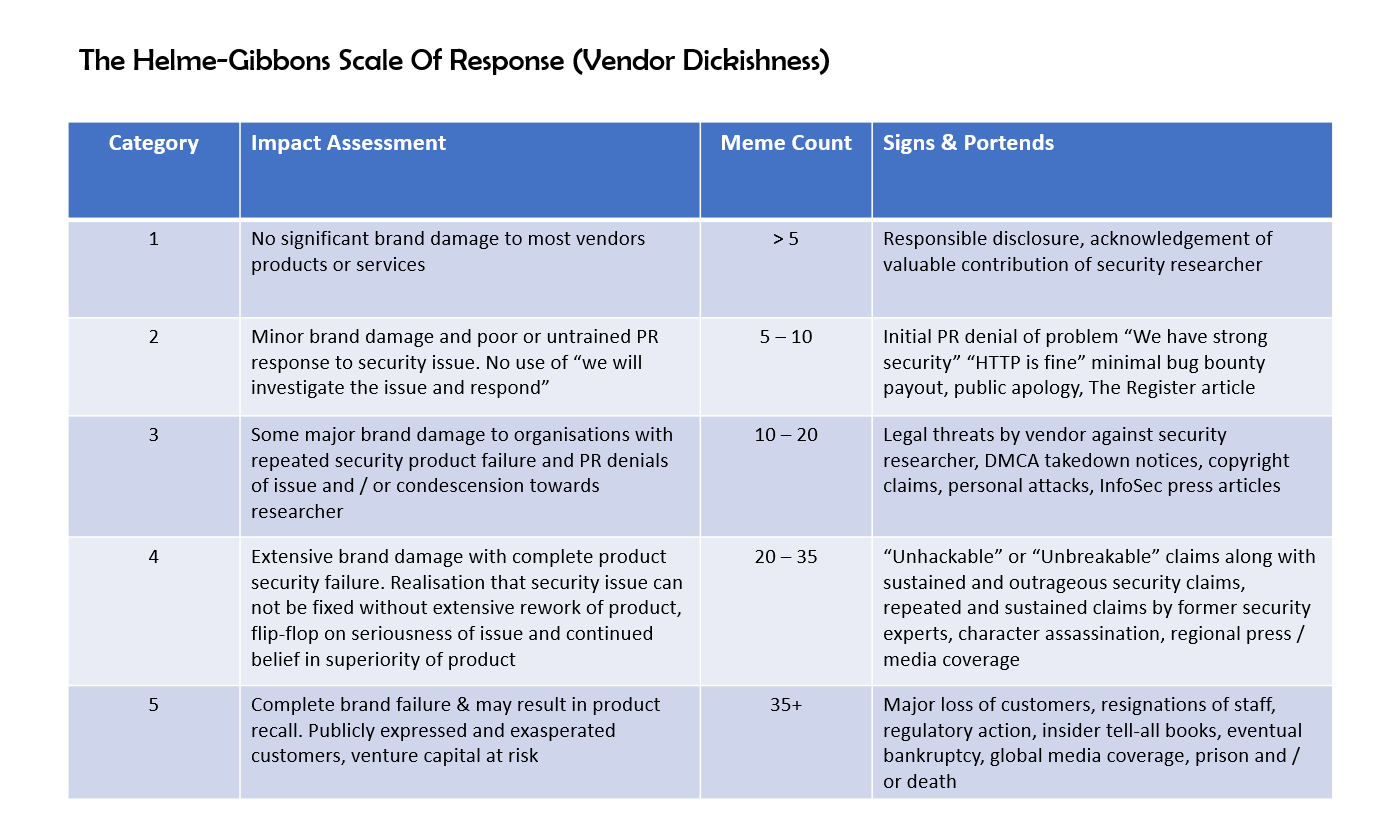
As you can see it ranges from a category one with no significant damage because you acknowledged the researchers contribution, to category three when you issue legal threats and personal attacks, all the way through to category five which results in a major loss of customers, the global media ridiculing you and affect investments.
Both Helme and Gibbons have been responsible for pointing out many vulnerabilities to vendors over the years. The scale allows us to gauge their response and score it. - Mike Thompson a.k.a @AppsecBloke
This graphic is meant to be a tongue in cheek guide created by Mike Thompson and Ian Thornton-Trump, based on comments from Scott Helme and Andrew Tierney, but it is still very accurate from what I have seen over the last few years in the cybersecurity space. You want to always inhabit category one if possible.
Don't be a dick.
Too Long, Didn't Read
In 2019 you are expected to take security seriously and this includes treating security researchers with respect when they go out of their way to warn you of a potentially serious vulnerability instead of exploiting it criminally, or selling it on the open market.
Responsible disclosure following a scan of your infrastructure is nowhere near an illegal act, so please do not act like it is. It is the infosec equivalent of being warned your vehicles brake lights out and warning you to fix them before you have an accident.
Remember that no security researcher would be foolish enough to do something illegal and then tell you about it on social media. They want to help and they want you to improve your security before one of the bad guys finds the hole and uses it.
If you are still struggling with this concept and still think you are being shaken down by a hacker, read my last article on this subject on how to deal with it.
The best thing you can do is thank the researcher, pass on their report and send them a $50 Amazon gift card, or a nice thank you letter, if it turns out that their report did help you improve the cybersecurity of your business and IT infrastructure.
What's that? You like the cut of my jib? Follow me on Twitter then!